Int'l J. of Communications, Network and System Sciences
Vol.3 No.6(2010), Article ID:2007,9 pages DOI:10.4236/ijcns.2010.36074
Performance of Multirate Multicast in Distributed Network
Department of Computer Engineering (College of Computer and Information Sciences), King Saud University, Riyadh, Saudi Arabia
E-mail: {sasit, siraj}@ksu.edu.sa
Received March 11, 2010; revised April 19, 2010; accepted May 22, 2010
Keywords: Throughput, Performance, Distributed Network, Cluster, Multicast, Session, Multirate Multicast, Queue
Abstract
The number of Internet users has increased very rapidly due to the scalability of the network. The users demand higher bandwidth and better throughput in the case of on demand video, or video conference or any real time distributed network system. Performance is a great issue in any distributed networks. In this paper we have shown the performance of the multicast groups or clusters in the distributed network system. In this paper we have shown the performance of different users or receivers belongs to the multicast group or cluster in the distributed network, transfer data from the source node with multirate multicast or unirate multicast by considering packet level forwarding procedure in different sessions. In this work we have shown that how the throughput was effected when the number of receiver increases. In this work we have considered the different types of queue such as RED, Fair queue at the junction node for maintaining the end to end packet transmission. In this work we have used various congestion control protocol at the sender nodes. This paper we have shown the performance of the distributed cluster network by multirate multicast.
1. Introduction
The users i.e. the receivers are connected to the source for transferring data or exchanging information. Here the source and the receivers are forming a network, that network is scalable i.e., in the network any new user or receiver can join. According to the real world scenario any number of existing user or receiver can leave from the cluster network can join different cluster or group. Each cluster be from a distributed network and well connected with other network. For any particular multicast group in the distributed network, the consist members of the group run different application program and required different packet size and data rate.
The performance of the distributed network in heterogeneous system, obtained by markovian model [1] and the queuing processing delay at the junction node.
Sending packets to the destination node with the minimum cost transmission delay, multicast session network coding techniques scheme used [2]. The end to end packet transmission in a set of active elastic sessions over a network, the session traffic [3] routed to the destination node through different path. The collision free broadcasting technique used [4] to minimize the latency and the number of transmissions in the broadcast network for end to end packet transmission in the distributed cluster network. The alternative ways for end to end packet forwarding used minimal congestion feed back signals from the router [5] and split the flow between each source destination pair. In end to end packet transmission, the random delay and TCP–congestion control [6] in the network is a issue. Receiver adjusts the rate based on the congestion level in Multicast Network [7] to reduce the congestion. In the real life scenario multicast traffic can cause more packet loss than uncast traffic for example in internet. The resource allocation by the Max –min fairness [8,9] and proportional fairness can reduce the traffic load in the network. The control multicast in the Network by using TCP [10,11] reduce the traffic load in the network. The inverted tree structure implemented in IP based network with the multicast session [12,13] to achieve better performance. The TCP congestion and the effect of that on the throughput of Multicast Group have greater impact in the system network [14]. Since the data packet be transferred between the source and receiver for end to end connection. The path between the source and receiver is not peer to peer, there be at least one junction node in between them .Due to limited bandwidth in the connecting paths, and queuing delay, data packet may be loss. The packet processing delay at the junction node (it is random service time) and the propagation time in the link be consider, the packet transmission delay at the junction node be negligible. The different receivers take data packet from the source node via the junction node (there may be more than one junction nodes in the source to receiver link). Now different receivers taken data packet with different rate in the multicast group of the distributed network in a multicast session. It is called the multirate multicast .If all the receiver node taken data packet with same rate it is called unirate multicast. Each multicast session is the collection of virtual session [15,16].
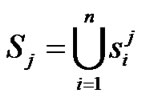 where
where 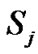 is the jth multicast session, and n is the number of node ( receiver) clearly, cardinality(
is the jth multicast session, and n is the number of node ( receiver) clearly, cardinality(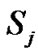 )
)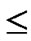 n because in a particular session all receiver may not received data packet .
n because in a particular session all receiver may not received data packet . 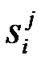 is the virtual session in the j-th multicast session for the ith receiver node in the multicast group. Different type of tree formed in the cluster of the distributed network like the Figures 1,2,3.
is the virtual session in the j-th multicast session for the ith receiver node in the multicast group. Different type of tree formed in the cluster of the distributed network like the Figures 1,2,3.
In Figure 1 there is one multicast group and one junction node, In Figure 2 there are two multicast group and two junction node In Figure 3 three multicast group and three junction node. The receiver node takes data packet from the source node via the junction node through the source to receiver link path. The different types of queue like RED, FQ, SFQ attach at the junction node to capture the packet loss and measure the delay for the multicast group in the multirate multicast session. Figure 4 represent the junction node [17].
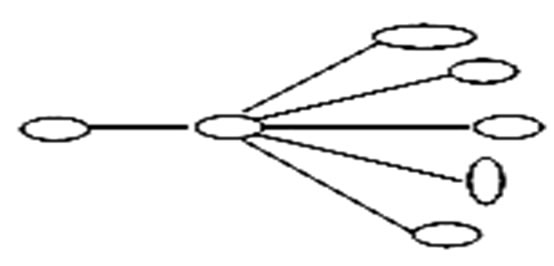
Figure 1. One multicast group.
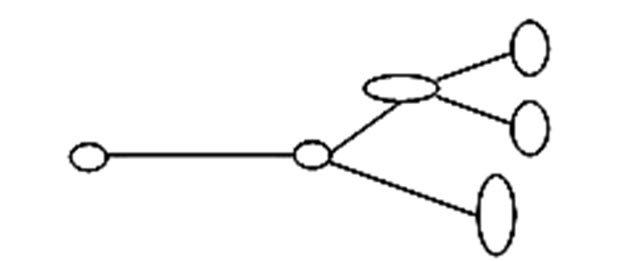
Figure 2. Two multicast group.

Figure 3. Three multicast group.
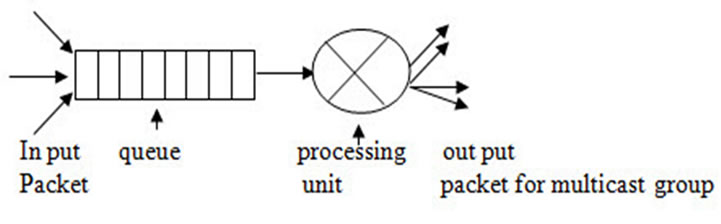
Figure 4. Junction node.
Figure 4 represents the junction node of the network. The packets approach the junction node randomly and the queue stored the packets. The packets stored into the queue in the order n + 1, n, n – 1… i.e., the 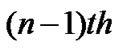 packet be forwarded to the processing unit after that the
packet be forwarded to the processing unit after that the 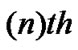 and
and 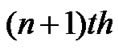 be forwarded to the processing unit. In side the queue there be waiting time for each packet and each packet have random service time or processing time according to the size of the packet and the destination multicast group. By using the packet level simulation we check how the throughput, delay, packet loss how the throughput be effected by increasing the number of receiver in the multicast group. The paper is structured as follows Section 1 is introduction, Section 2 presents Proposed model Section 3 presents the algorithms for the mathematical models, Section 4 and 5 represents simulation results and the conclusion.
be forwarded to the processing unit. In side the queue there be waiting time for each packet and each packet have random service time or processing time according to the size of the packet and the destination multicast group. By using the packet level simulation we check how the throughput, delay, packet loss how the throughput be effected by increasing the number of receiver in the multicast group. The paper is structured as follows Section 1 is introduction, Section 2 presents Proposed model Section 3 presents the algorithms for the mathematical models, Section 4 and 5 represents simulation results and the conclusion.
2. Proposed Model for Multirate Multicast Virtual Session
2.1. Assumption 1
Let L be the set of links and 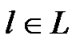 be a particular link path. The maximum capacity of the link
be a particular link path. The maximum capacity of the link 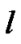 is
is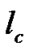 . Let
. Let 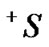 be the set of all session, such that s
be the set of all session, such that s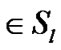 be the a particular session through link
be the a particular session through link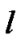 , where
, where 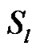 be the set of session passing through the link
be the set of session passing through the link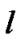 . Clearly
. Clearly 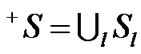 and
and 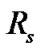 be the set of receiver at the particular session s for the multicast group.
be the set of receiver at the particular session s for the multicast group.
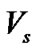 be the set of virtual session that using the link
be the set of virtual session that using the link 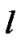 at the session s. If
at the session s. If 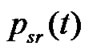 be the rate at which the data be transferred at session s to the receiver r at the time (t).
be the rate at which the data be transferred at session s to the receiver r at the time (t).
Then, 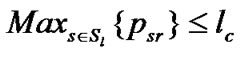 briefly we can write
briefly we can write 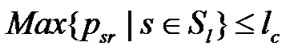 means we consider the maximum flow through the link path
means we consider the maximum flow through the link path 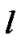 for the set of session
for the set of session 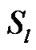 within the threshold limit of the link capacity
within the threshold limit of the link capacity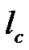 . According to the Figure 5, There were the two sessions for sending data packet from the source node A to the receiver node C and the source node D to the receiver node C . Now the maximum data packet be transferred through the junction node B to the receiver node C be within the capacity of the link for the set of sessions.
. According to the Figure 5, There were the two sessions for sending data packet from the source node A to the receiver node C and the source node D to the receiver node C . Now the maximum data packet be transferred through the junction node B to the receiver node C be within the capacity of the link for the set of sessions.
In the 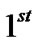 session data packet be transferred like A->B->C and A->B->D and in the
session data packet be transferred like A->B->C and A->B->D and in the 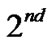 session data packet be transferred like D->B->C. Here nodes {D,B,C} forming a multicast group for the network of nodes { A,B,C,D}.
session data packet be transferred like D->B->C. Here nodes {D,B,C} forming a multicast group for the network of nodes { A,B,C,D}.
Our objective is to maximize the flow within the congestion threshold window size at the source end by consider the multirate multicast. The basic objective goes to maximize the data flow from the source to the multicast group in presence of queue size and random service at the junction node or the random processing time at the junction node.
2.2. Assumption 2
Let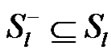 . Where
. Where  be the set of all session passing through the link
be the set of all session passing through the link 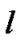 at time (t). here
at time (t). here  a countable finite is set and
a countable finite is set and 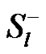 is the finite subset of
is the finite subset of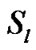 .
.
The total flow through the link 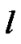 at time t be
at time t be 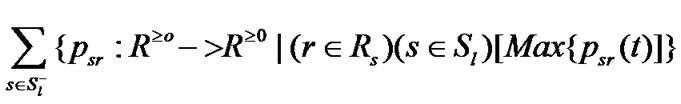
The above expression is the sum of the set of values for all session through link 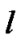 at time t. where
at time t. where 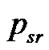 be a real valued function from the time domain to the real valued data rate where the suffix r and s are belongs to the set of receivers of the multicast group and s is the session through l link such that r and s belongs to sets
be a real valued function from the time domain to the real valued data rate where the suffix r and s are belongs to the set of receivers of the multicast group and s is the session through l link such that r and s belongs to sets 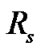 and
and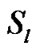 .
.
Here we consider only the maximum data rate at different session at time t for the receiver r.
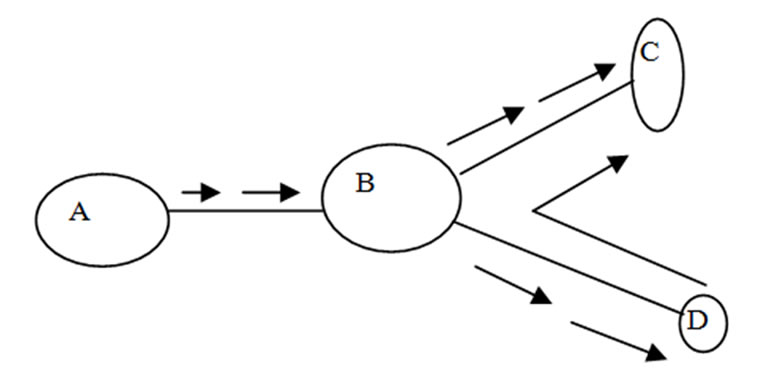
Figure 5. Distributed nodes.
3. Proposed Algorithm for the Packet Level Forwarding
It is possible to store information of all packet for all the multirate multicast session through the link path (source to receiver).
Here the proposed algorithms for selected single packet forwarding time computation from source to a receiver (that belongs to multicast group) per session that belongs to multirate multicast session.
Algorithm:
//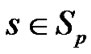 ,
, 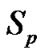 be the set of all session passing through path p ( source to receiver)
be the set of all session passing through path p ( source to receiver)
// k = cardinality (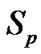 )
)
// m be any selected packet for any session
// n be the number of nodes required for the link path source to receiver r.
// n 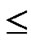 dimension of network
dimension of network
//  be the random service or processing time for the
be the random service or processing time for the 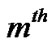 packet at the
packet at the 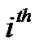 junction
junction
// node.
// 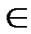
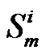 A[1.. k,1…n] in 2D space
A[1.. k,1…n] in 2D space
// 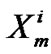 be the forwarding time for the
be the forwarding time for the 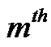 packet at the
packet at the 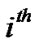 junction node
junction node
// 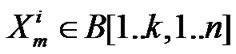 in 2D space.
in 2D space.
// 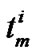 be the propagation time of the
be the propagation time of the  packet between the junction nodes ( i – 1) and ( i )
packet between the junction nodes ( i – 1) and ( i )
// 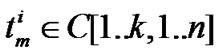 in 2D space.
in 2D space.
Var
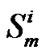 ,
,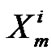 ,
,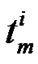 : float Var
: float Var
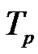 , T: integer //
, T: integer // 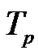 be total propagation time one selected packet per session,
be total propagation time one selected packet per session,
// source to receiver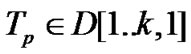 . k
. k
// numbers of rows and 1 column.
// T be the total time one packet per session // 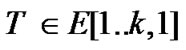
Var
sum = 0 : integer
2sum = 0 : integer function : f ( float a, float b)
{ if ABS(a) > ABS(b)
// ABS(a) is || a || in normed space
return (a)
if ABS(a) < ABS(b)
return(b)
if ABS(a) = = ABS(b)
return(a)
}
for i = 1 to k do begin for j = 1 to n do begin
A[i, j] = 0
B[i, j] = 0
C[i, j] =0
end // loop 1
end // loop 2 for j=1 to n do begin
D[j, 1] = 0;
E[j, 1] = 0;
end // loop for j begin for j = 1 to k do begin
// repeat the process one packet per session
// selected  packet for the
packet for the 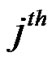 session for i=1 to n do begin
session for i=1 to n do begin
// n be node index for the 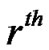 receiver for a session if ( i = = 1 ) // i = 1 is the source node
receiver for a session if ( i = = 1 ) // i = 1 is the source node
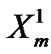 =
= 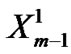 +
+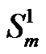 ;
;
// value of 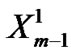 is B[j–1,1] and B[1,1] is the // starting clock time
is B[j–1,1] and B[1,1] is the // starting clock time
B[j, 1] = 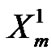 ;
;
if ( i > 1 && i < r )
// r is the receiver node index
{
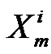 = f (
= f ( ,
,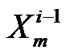 ) +
) +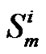 ;
;
// forwarding time of 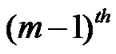 packet at
packet at 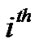
// junction node and
// 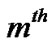 packet at
packet at 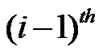 junction node
junction node
B[j, I] =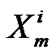 ;
;
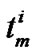 =
= 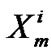 –
–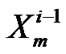 –
–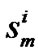 ; // where
; // where 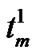 =0 sum = sum +
=0 sum = sum + ;
;
} // end if block if ( i = = n )
{
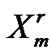 =
= 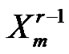 +
+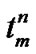 ;
;
// r is the sink node, no further forward is
// required.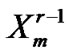 = B [j, r–1]
= B [j, r–1]
B[ j, r] =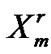 ;
;
// Approximate value of 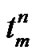 is
is 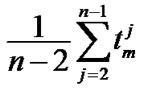 as
as
// the sample mean of size (n – 2)
} // end if block sum = sum + 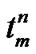
end // loop for i
sum = D[j, 1]
2sum = 0 for i = 1 to n do begin 2sum = 2sum + B [j, i]
end // loop for i 2sum = E [j, 1]
end // loop for j end // Algorithm
By solving the number of computation of the proposed algorithm, the time complexity of the proposed algorithms belongs to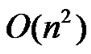 .
.
4. Experimental Result and Discussion
The Figure 6 shows the result corresponding to the diagram Figure 1 where the data transferred from the source node through the junction node in a session. The receivers build a single cluster with a cluster head. The cluster has n–numbers of receiver nodes. The cluster members gradually connected to the source node i.e. it is gradually expands from the time 0.25 second (in a session ) and gradually release resources i.e. the size of the cluster reduce from the 0.32 second (in other session). It shown from the Figure 6 that when the number of nodes (receivers) increase in the cluster, the throughput decreases as in the receiver side, the packet loss increase i.e. packet delay increase. When the number of nodes in cluster decrease, i.e., the member node leaves the group, the packet receive rate increase. As well as the throughput increases for the group as it is indicated in between the time (0.32, 0.35).
The Figure 7 shows the result corresponds to the diagram Figure 2, initially the Network have two cluster of two different size. In a session up to 0.31 second member connected to the source node via the junction nodes and the receive packets After 0.31 second in the new session one group leave from the network, i.e. release the resources the Figure 7 shows the effect that on the throughput.
In Figure 8 and Figure 9 the effect on the overall throughput when the one cluster leaves the network (smaller in number of nodes) and a comparatively bigger cluster connect to the network in other session. Figure 10 and Figure 11 represent how the load increased in junction nodes that connected to the two clusters. Figure 12 and Figure 13 represent the traffic pattern that pass through the two junction nodes that connected to the two different clusters.
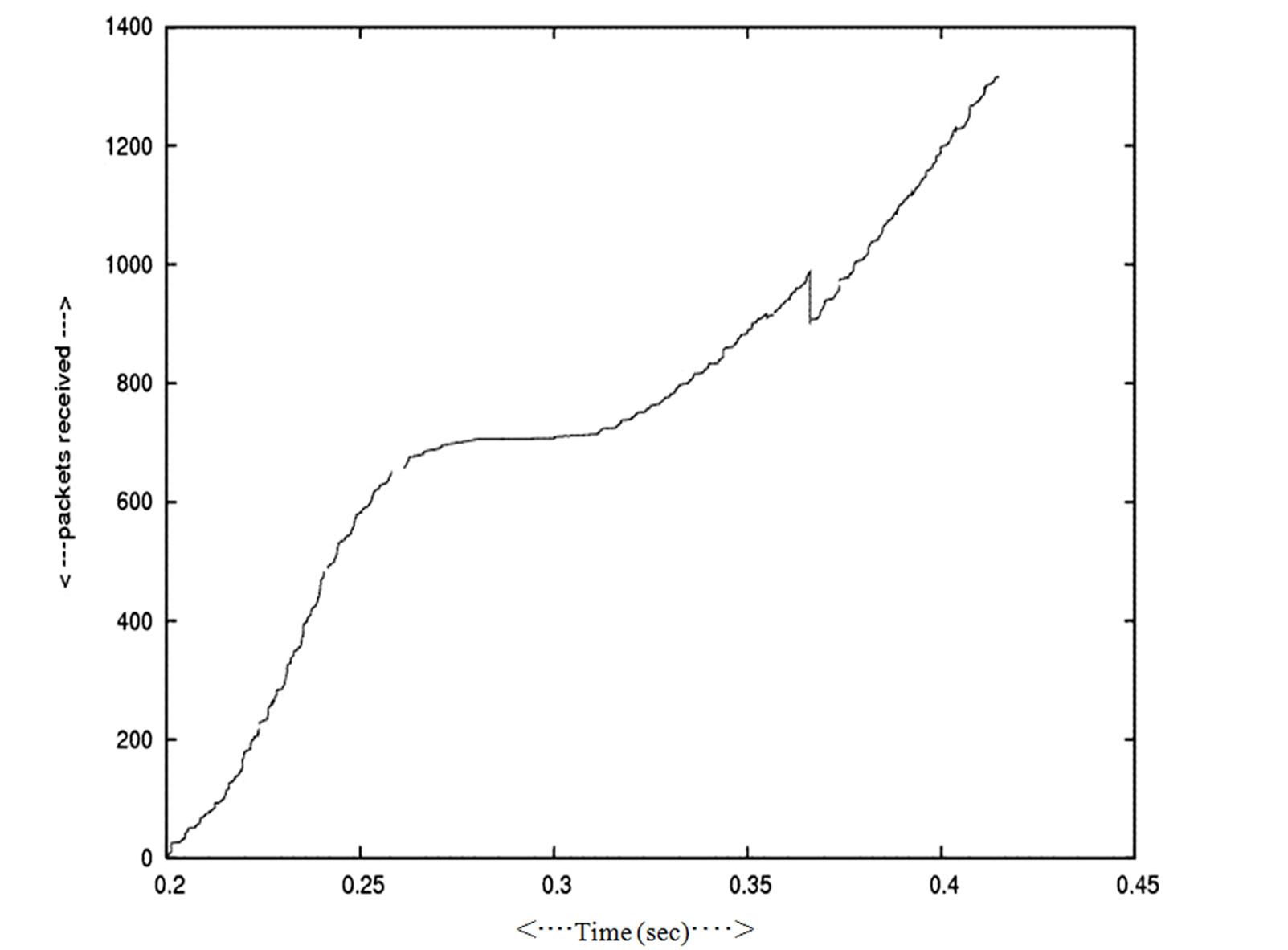
Figure 6. Packet received—Time.

Figure 7. Throughput—Decrease cluster number time.
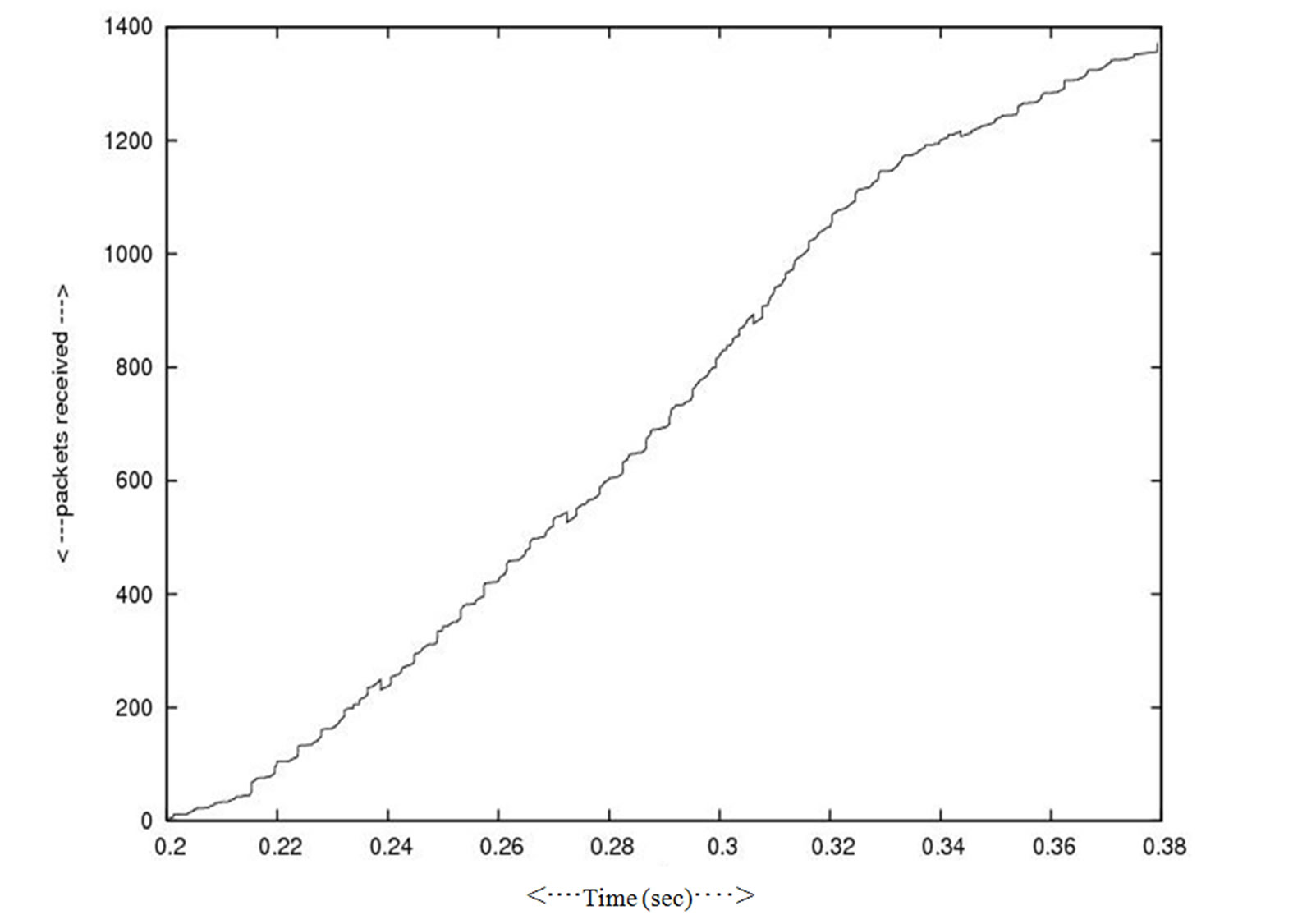
Figure 8. Packet receive.
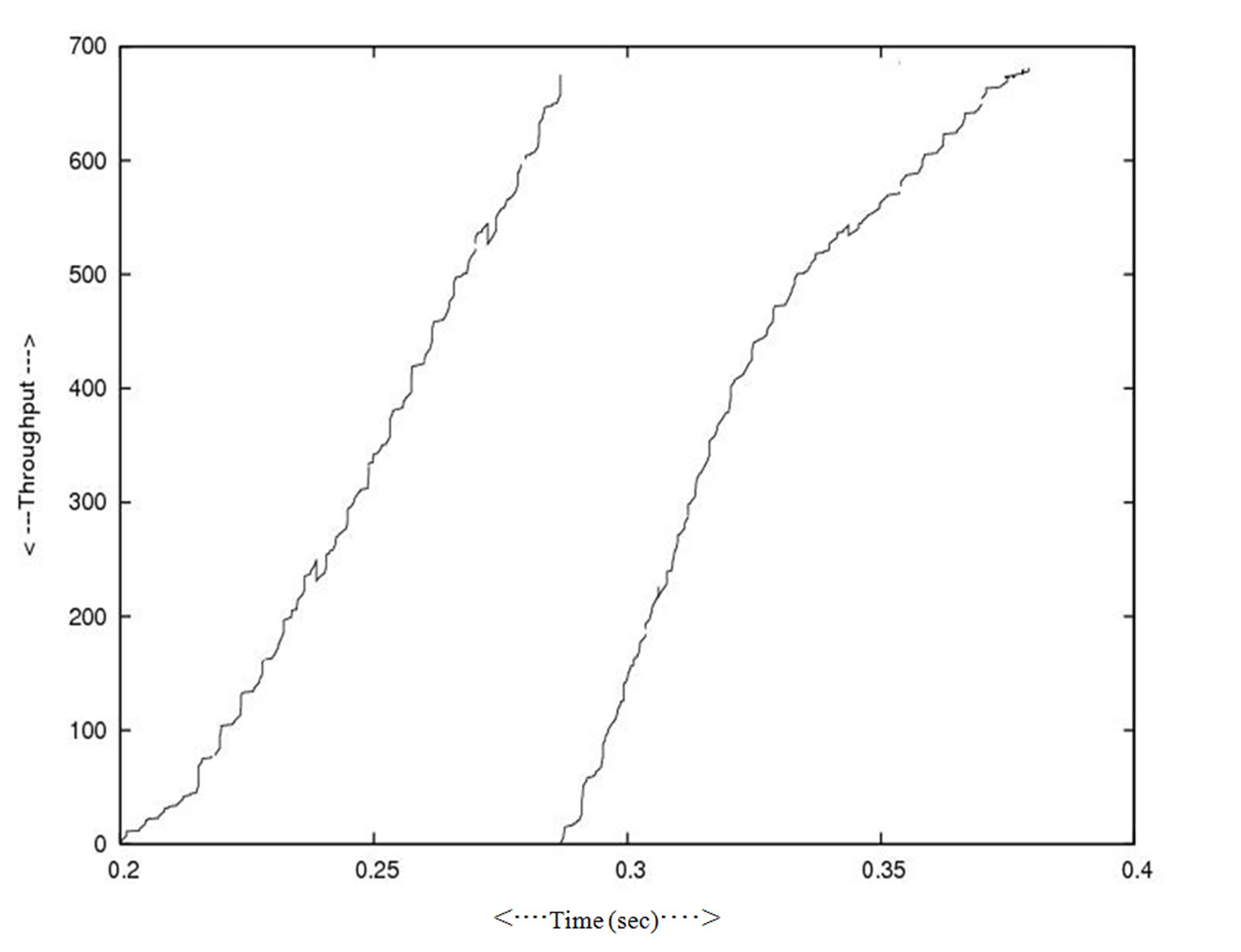
Figure 9. Throughput two different size clusters.
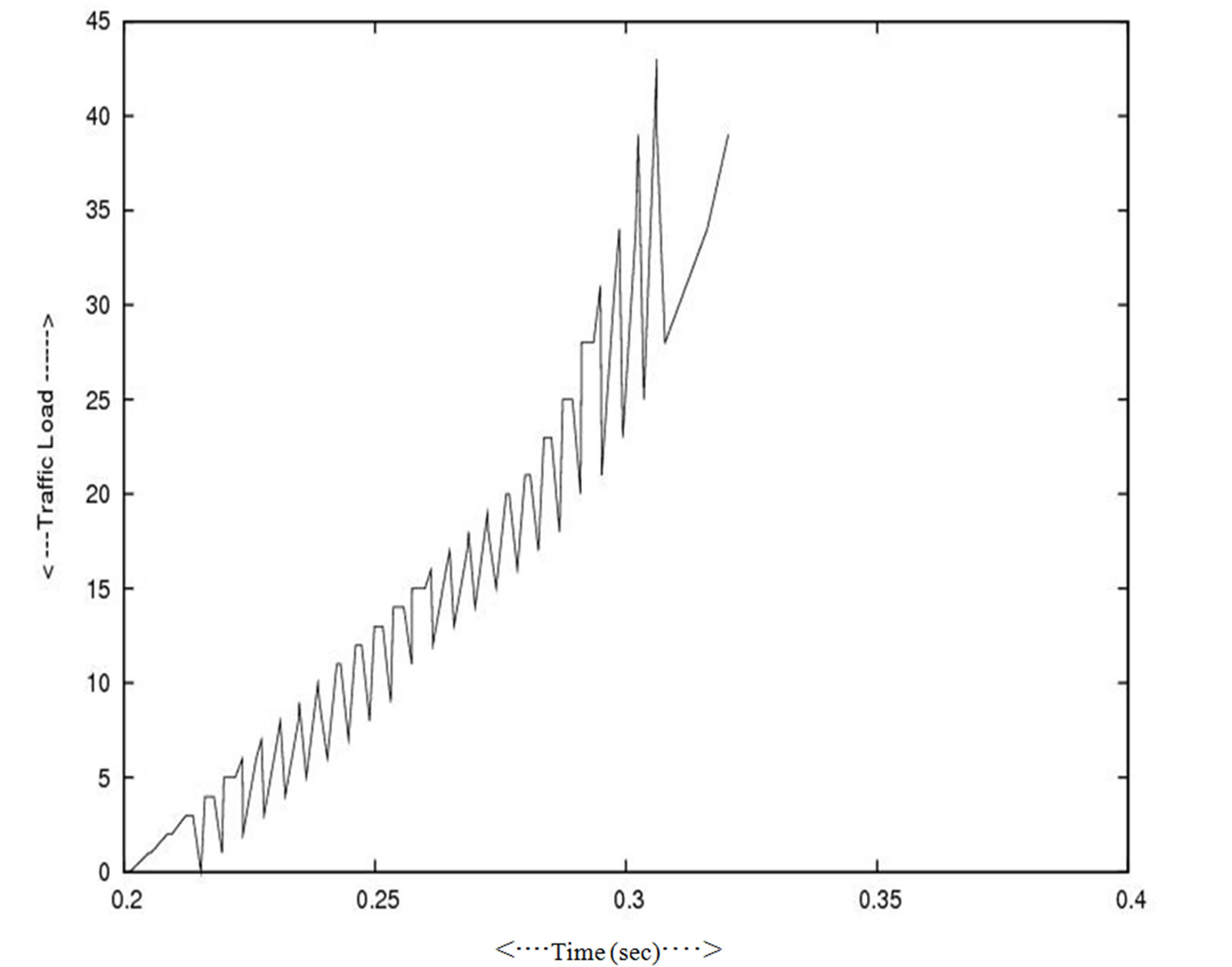
Figure 10. Traffic load in side the small cluster.
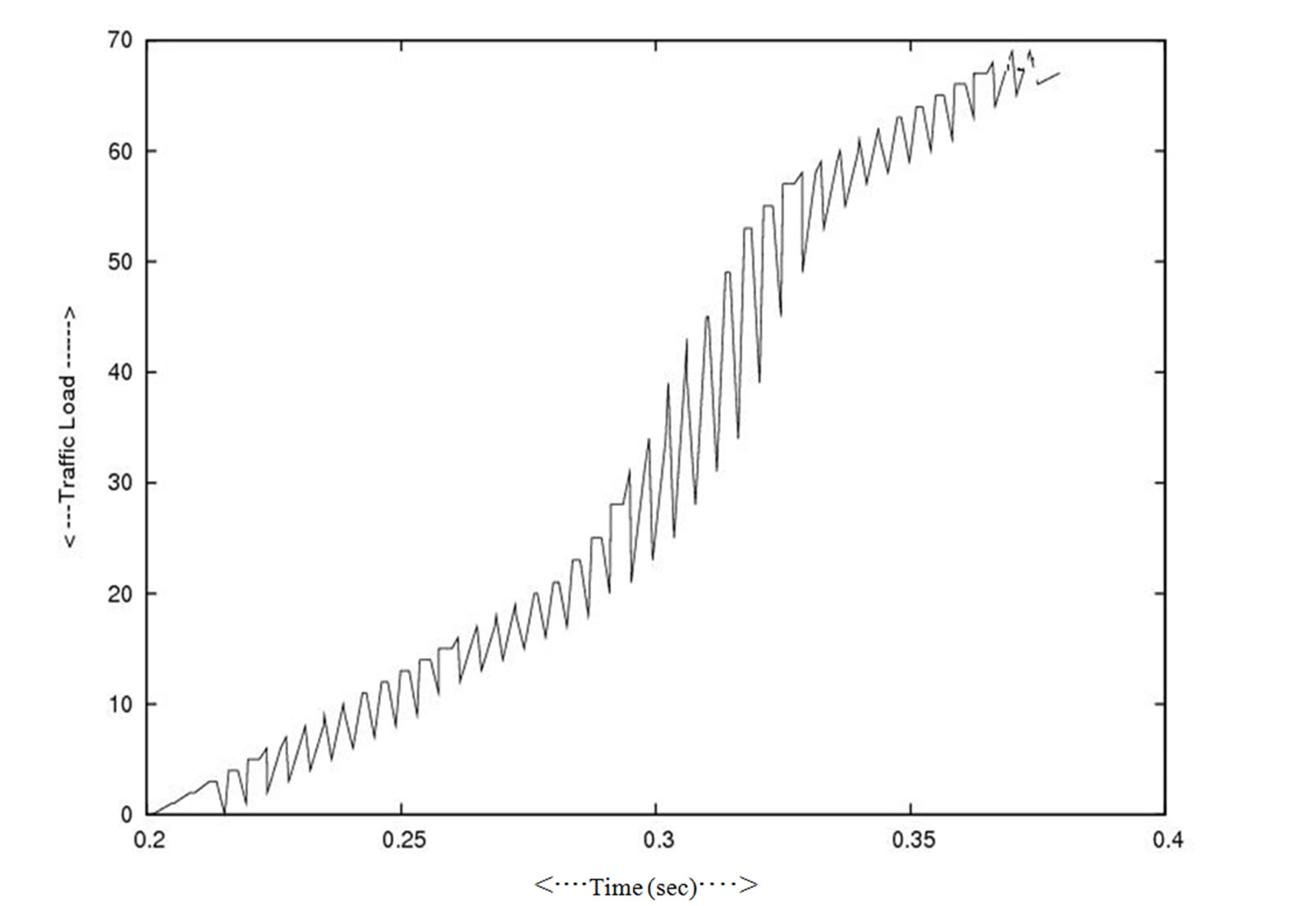
Figure 11. Traffic load in side big cluster.

Figure 12. Packet received at receiver small cluster.
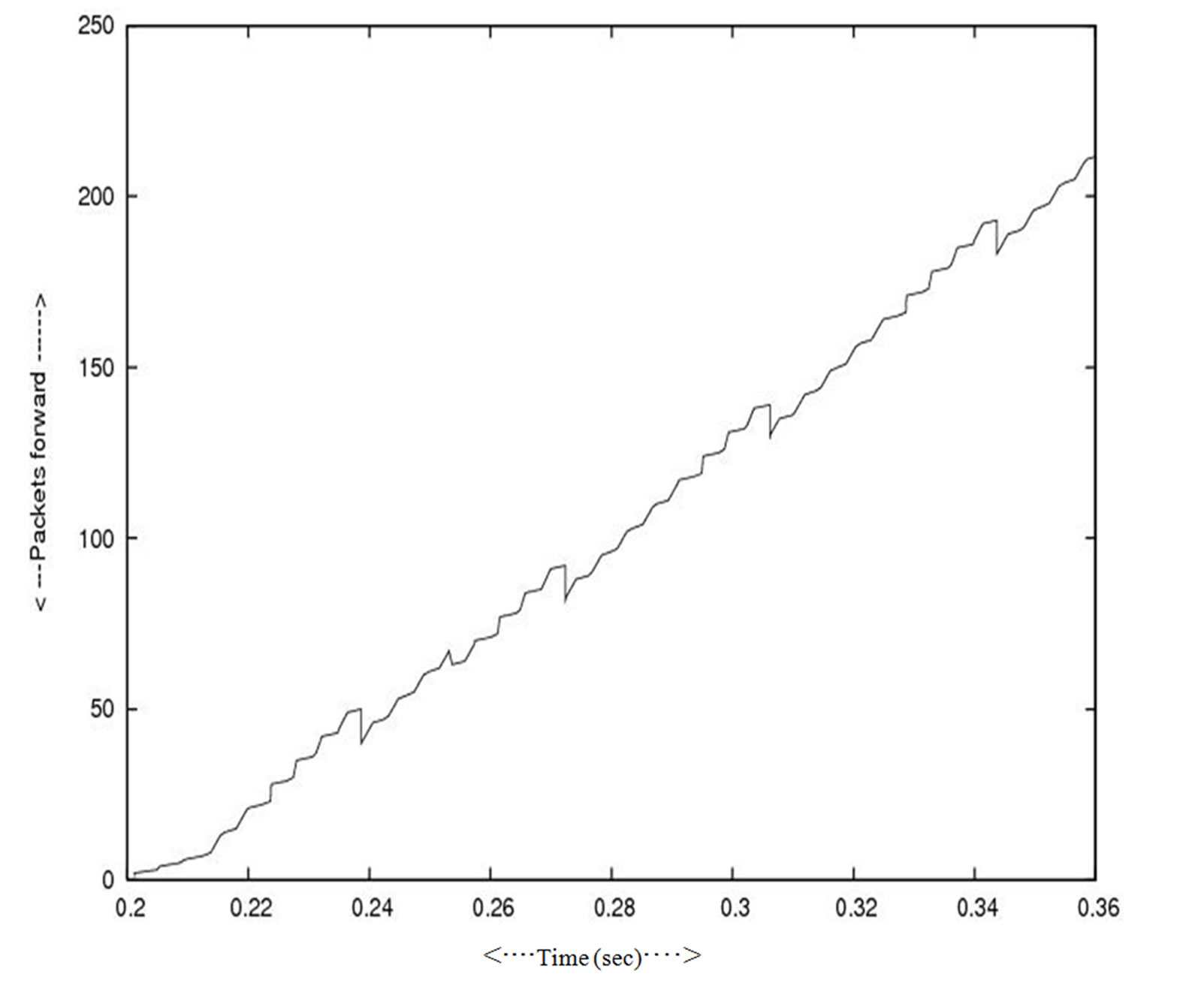
Figure 13. Packet received at receiver big cluster.
5. Concluding Remarks
In this paper we develop the novel algorithms, the packet level forwarding in multicast session and on the basis of that we simulate the real problem in the lab environment. When the cluster size increases the throughput decreases. We consider a single cluster that expands in a session and reduces in other session as some nodes join in the cluster in a session and some node leaves as in other session.
We also study when the network is composed of multiple cluster and some cluster expands in number and some cluster reduces in number in different sessions. We experiment that with respect to real scenarios.
The work can be further extended for the problem arise in the next generation Network (NGN). In the case of IP based video on demand problem. In that case in spite of bandwidth limited constraint the number of receiver connected to the main video server as getting the clips Video –on-demand as IP data packets (datagram), the receiver forms single or more than one multicast groups .The receiver get the data packet as in the multicast session to the receiver as for the views particular (channel) that is related channel to a particular frequency.
6. References
[1] S. Kanrar and M. Siraj, “Performance of Heterogeneous Network,” International Journal of Computer Science and Network Security, Vol. 9, No. 8, 2009, pp. 255-261.
[2] Y. F. Xi and E. M. Yeh, “Distributed Algorithms for Minimum Cost Multicast with Network Coding,” IEEE/ ACM Transaction on Networking, Vol. 18, No. 2, 2009, pp. 379-392.
[3] J. Nair and D. Manjunath, “Distributed Iterative Optimal Resource Allocation with Concurrent Updates of Routing and Flow Control Variables,” IEEE/ACM Transaction on Networking, Vol. 17, No. 4, 2009, pp. 1312-1325.
[4] R. Gandhi, A. Mishra and S. Parthasarathy, “Minimizing Broadcast Latency and Redundancy in Ad Hoc Networks,” IEEE/ACM Transaction on Networking, Vol. 16 No. 4, 2008, pp. 840-851.
[5] H. Han, S. Shakkottai, C. V. Hollot, R. Srikant and D. Towsley, “Multi-Path TCP: A Joint Congestion Control and Routing Scheme to Exploit Path Diversity in the Internet,” IEEE/ACM Transaction on Networking, Vol. 14, No. 6, 2006, pp. 1260-1271.
[6] S. J. Golestani and K. K. Sabanani, “Fundamental Observations on Multicast Congestation Control in The Internet,” Proceedings of IEEE INFOCOM, New York, Vol. 2, March 1999, pp. 990-1000.
[7] X. Li, S. Paul and M. Ammar, “Layered Video Multicast with Retransmission (LVMR): Evaluation of Hierarchical Rate Control,” Proceedings of IEEE INFOCOM, San Francisco, Vol. 3, June 1998, pp. 1062-1072.
[8] A. Mankin, A. Romanow, S. Bradner and V. Paxon, “IETF Criteria for Evaluating Reliable Multicast Transport and Application Protocols,” Networking Working Group, Internet Draft, RFC 2357, 1998.
[9] J. Mo and J. Walrand, “Fair End to End Windows Based Congestion Control,” IEEE/ACM Transaction on Networking, Vol. 8, No. 5, October 2000, pp. 556-557.
[10] F. P. Kelly, “Charging and Rate Control for Elastic Traffic,” European Transactions on Telecommunications, Vol. 8, No. 1, 1998, pp. 33-37.
[11] M. Handley and S. Floyd, “Strawman Congestion Control Specifications,” Internet Research Task Force (IRTF), Reliable Multicast Research Group (RMRG), 1998. http:// www.aciri.org/mjh/rmcc.ps.gz
[12] L. Rizzo, L. Vicisano and J. Crowcroft, “TCP Like Congestion Control for Layered Multicast Data Transfer,” Proceedings of IEEE INFOCOM, San Francisco, Vol. 3, March 1998, pp. 996-1003.
[13] I. Stoica, T. S. E. Ng and H. Zhang, “REUNITE: A Recursive Unicast Approach to Multicast,” Proceedings of IEEE INFOCOM, Tel Aviv, Vol. 3 March 2000, pp. 1644-1653.
[14] S. Bhattacharyya, D. Towslay and J. Kurose, “The Loss Path Multiplicity Problem in Multicast Congestion Control,” Proceedings of IEEE INFOCOM, New York, Vol. 2, March 1999, pp. 856-863.
[15] A. Chaintreau, F. Baccelli and C. Doit, “Impact of TCP-Like Congestion Control on the Throughput of Multicast Grouph,” IEEE/ACM Transaction on Networking, Vol. 10, No. 4, 2002, pp. 500-512.
[16] S. Deb and R. Srikant “Congestion Control for Fair Resource Allocation in Networks with Multicast Flow,” IEEE/ACM Transaction on Networking, Vol. 12, No. 2, 2004, pp. 274-285.
[17] R. C. Chalmers and K. C. Almeroth, “Modeling the Branching Characteristics and Efficiency Gains of Global Multicast Tree,” Proceedings of IEEE INFOCOM, Anchorage, Vol. 1, April 2001, pp. 449-458.

