Journal of Applied Mathematics and Physics
Vol.02 No.13(2014), Article ID:52519,5 pages
10.4236/jamp.2014.213140
A Multi-Secret Sharing Scheme with Many Keys Based on Hermite Interpolation
Tomoko Adachi1, Chie Okazaki2
1Department of Information Sciences, Toho University, Funabashi, Japan
2Kowa Electric Industry Co., Ltd., Kawasaki, Japan
Email: adachi@is.sci.toho-u.ac.jp
Copyright © 2014 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 10 November 2014; revised 1 December 2014; accepted 7 December 2014
ABSTRACT
A secret sharing scheme is one of cryptographies. A threshold scheme, which is introduced by Shamir in 1979, is very famous as a secret sharing scheme. We can consider that this scheme is based on Lagrange's interpolation formula. A secret sharing scheme has one key. On the other hand, a multi-secret sharing scheme has more than one keys; that is, a multi-secret sharing sche- me has 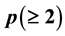 keys. Dealers distribute shares of keys among
keys. Dealers distribute shares of keys among 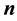 participants. Gathering
participants. Gathering  participants, keys can be reconstructed. In this paper, we give a scheme of a
participants, keys can be reconstructed. In this paper, we give a scheme of a 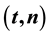 multi-secret sharing based on Hermite interpolation, in the case of
multi-secret sharing based on Hermite interpolation, in the case of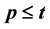 .
.
Keywords:
Secret Sharing Scheme, Multi Secret Sharing Scheme, Hermite Interpolation

1. Introduction
A secret sharing scheme is one of cryptographies. A secret sharing scheme was introduced by Shamir in 1979 [1] and Blakley in 1979 [2] independently. A secret sharing scheme has been studied by many scientists until today. Now, a secret sharing scheme has some important application to several areas of the information security.
The secret sharing scheme is a method to distribute shares of a secret value―we call it a key, too―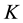 among a set of participants
among a set of participants 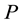 such a way that only the qualified subsets of
such a way that only the qualified subsets of 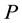 are able to reconstruct the value of
are able to reconstruct the value of 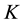 from their shares. In 1979, Shamir [1] introduced the secret sharing scheme which was based on Lagrange’s interpolation formula. This scheme is called Shamir’s threshold scheme. In 1987, Feldman [3] studied a verifiable scheme in distributing system. In 1992, Pedersen [4] applied a verifiable secret sharing scheme to Shamir’s threshold scheme.
from their shares. In 1979, Shamir [1] introduced the secret sharing scheme which was based on Lagrange’s interpolation formula. This scheme is called Shamir’s threshold scheme. In 1987, Feldman [3] studied a verifiable scheme in distributing system. In 1992, Pedersen [4] applied a verifiable secret sharing scheme to Shamir’s threshold scheme.
A secret sharing scheme has one key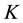 . On the other hand, a multi-secret sharing scheme has more than one keys; that is, a multi-secret sharing scheme has
. On the other hand, a multi-secret sharing scheme has more than one keys; that is, a multi-secret sharing scheme has 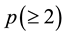 keys
keys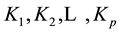 . Dealers distribute shares of keys
. Dealers distribute shares of keys
among 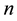 participants. Let a set of participants
participants. Let a set of participants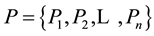 . Gathering
. Gathering 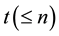 participants, keys can be reconstructed.
participants, keys can be reconstructed.
Various schemes are proposed about a multi-secret sharing scheme. In 1994, Jackson et al. [5] studied a multi-secret sharing scheme for a matroid. A multi-secret sharing scheme by utilizing a one-way function is studied by He and Dawson [6] in 1994, and by Harn [7] in 1995. A multi-secret sharing scheme by utilizing a two variables one-way function is studied by He and Dawson [8] in 1995. A multi-secret sharing scheme by utilizing a linear block code is studied by Chien et al. [9] in 2000, and by Pang and Wang [10] in 2005. A multi- secret sharing scheme based on Lagrange’s interpolation is studied by Yang et al. [11] in 2004, and by Pang and Wang [10] in 2005. Recently, Adachi [12] studies a secret sharing scheme with two keys based on Hermite interpolation.
In this paper, we give a scheme of a 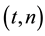 multi-secret sharing based on Hermite interpolation, in the case of
multi-secret sharing based on Hermite interpolation, in the case of









2. Lagrange’s Interpolation and Hermite Interpolation
In this section, we describe two famous interpolation formula, that is, Lagrange’s interpolation and Hermite interpolation. In numerical analysis, Lagrange’s interpolation and Hermite interpolation is a method of interpolating data points as a polynomial function.
2.1. Lagrange’s Interpolation
Suppose that a function 

























Here, we can get an 

where an 

Let


2.2. Hermite Interpolation
Hermite interpolation is an extension of Lagrange’s interpolation. When using divided differences to calculate the Hermite polynomial of a function
Suppose that a function 



































Here, it is known that we can get an unique 

where two 


and
This is called Hermite interpolation.
3. A Multi-Secret Sharing Scheme Based on Lagrange’s Interpolation
In this section, we describe a multi-secret sharing scheme based on Lagrange’s interpolation, which is proposed by Yang et al. in 2004. We refer to [11] . We refer to the part of Yang’s scheme in [10] , too.
In Yang et al.’s scheme, for secret distribution, the secret are distributed in two separate cases, 





1) System parameters. Let 





Here, we use 

2) Secret distribution. In the case of
2a) Construct a 






2b) Randomly choose an integer 


2c) Publish 
3) Secret reconstruction. In the case of












4. Our Scheme: A Multi-Secret Sharing Scheme Based on Hermite Interpolation
In this section, we describe our new scheme, that is, a multi-secret sharing scheme based on Hermite interpolation in the case


In the case of
Theorem 1. [12] Suppose that we have two keys (secrets), 



We expand this theorem. In our scheme, at first, we prepare system parameters which we need. Secondly, we describe secret distribution. Finally, we describe secret reconstruction.
1) System parameters. Let 










Here, we use 

2) Secret distribution. In the case of
2a) He constructs a 






2b) He computes 


2c) He publishes 
3) Secret reconstruction. In the case of

3a) They pool their pseudo shadows



3b) They compute 


3c) They compute 


3d) By Hermite interpolation polynomial, with the knowledge of 




From the obtained polynomial 






As stated above, we obtain the following theorem.
Theorem 2. Suppose that 




Corollary 1. Suppose that 


Proof. In the case 
(Q.E.D.)
Corollary 2. Theorem 2 contains Theorem 1.
Proof. In the case 
(Q.E.D.)
5. Computational Complexity
In this section, we compare computational complexity of our scheme which we describe in Section 4, and that of Yang et al.’s scheme which we describe in Section 3.
As regards phase 1) system parameters, the both schemes have the same amount of parameters.
As regards phase 2) secret distribution, computational complexity of our scheme is twice of that of Yang et al.’s scheme. Since, in our scheme, there are 

As regards phase 3) secret reconstruction, computational complexity of our scheme is twice of that of Yang et al.’s scheme. Since, in 3b) of our scheme, there are 

are not only 




Hence, computational complexity of our scheme is twice of that of Yang et al.’s scheme. This is suitable, since computational complexity of Hermite interpolation is twice of that of Lagrange’s interpolation.
6. Conclusion
We can propose a new scheme of a multi-secret sharing scheme with many keys based on Hermite interpolation. Hermite interpolation is a higher precision analysis and needs more complex computation than Lagrange’s interpolation. The merit on our scheme is that we can use many keys with fine distinctions. On the other hand, the demerit on our scheme is that its computation is complex for participants.
Acknowledgements
We thank the editor and the referee for their comments.
References
- Shamir, A. (1979) How to Share a Secret. Communications of the ACM, 22, 612-613. http://dx.doi.org/10.1145/359168.359176
- Blakley, G.R. (1979) Safeguarding Cryptographic Keys. AFIPS Conference Proceedings, 48, 313-317.
- Feldman, P. (1987) A Practical Scheme for Non-Interactive Verifiable Secret Sharing. Proceedings of 28th IEEE Symposium on Foundations of Computer Science, Los Angeles, 12-14 October 1987, 427-437.
- Pedersen, T.P. (1992) Non-Interacive and Information-Theoretic Secure Verifiable Secret Sharing. Advances in Cryptology CRYPTO ’91, 129-140.
- Jackson, W.A., Martin, K.M. and O’Keefe, C.M. (1995) On Sharing Many Secrets. Advances in Cryptology― ASIACRYPT’94, 917, 42-54.
- He, J. and Dawson, E. (1994) Multistage Secret Sharing Based on One-Way Function. Electronics Letters, 30, 1591-1592. http://dx.doi.org/10.1049/el:19941076
- Harn, L. (1995) Comment: Multistage Secret Sharing Based on One-Way Function. Electronics Letters, 31, 262. http://dx.doi.org/10.1049/el:19950201
- He, J. and Dawson, E. (1995) Multisecret Sharing Scheme Based on One-Way Function. Electronics Letters, 31, 93-94. http://dx.doi.org/10.1049/el:19950073
- Chien, H.Y., Jan, J.K. and Tseng, Y.M. (2000) A Practical (t,n) Multi-Secret Sharing Scheme. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, E83, 2762-2765.
- Pang, L.J. and Wang, Y.M. (2005) A New (t,n) Multi-Secret Sharing Scheme Based on Shamir’s Secret Sharing. Applied Mathematics and Computation, 167, 840-848. http://dx.doi.org/10.1016/j.amc.2004.06.120
- Yang, C.C., Chang, T.Y. and Hwang, M.S. (2004) A (t,n) Multi-Secret Sharing Scheme. Applied Mathematics and Computation, 151, 483-490. http://dx.doi.org/10.1016/S0096-3003(03)00355-2
- Adachi, T. (Submitted) A Secret Sharing Scheme with Two Keys Based on Hermite Interpolation.

















