International Journal of Communications, Network and System Sciences
Vol.10 No.08(2017), Article ID:78321,12 pages
10.4236/ijcns.2017.108B002
Quantum Secret Broadcast for Wireless Quantum Networks
Tao Shang, Gang Du, Jianwei Liu
School of Electronic and Information Engineering, Beihang University, Beijing, China




Received: March 10, 2017; Accepted: August 11, 2017; Published: August 14, 2017
ABSTRACT
In wireless quantum networks, nodes communicate by means of pre-distri- bution for entangled pairs and relay path establishment for quantum teleportation. However, simple point-to-point communication seriously restricts the efficiency of quantum communication. Inspired by sharing idea of quantum secret sharing (QSS), which is based on three collaborative nodes with pre-shared GHZ (Greenberger-Horne-Zeilinger) states, we propose a quantum secret broadcast scheme to improve network performance. In a cluster network cored on three parties of QSS, three cluster heads with pre-shared GHZ states are senders, while cluster members are receivers. One cluster head encodes secret messages on auxiliary particles by performing certain operations on them with GHZ particles, then three cluster heads measure their own particles and broadcast measurement results honestly. Based on the specific correlation of measurement results and secret messages, all receivers can recover the secret messages. Furthermore, to prevent eavesdropping, cluster heads can update an encoding key periodically. Analysis shows the proposed scheme is more efficient than previous schemes in wireless quantum networks, especially when the number of receivers is larger. Besides, in the proposed scheme, attacks on quantum channel based on GHZ state can be detected, and eavesdroppers cannot recover messages correctly for lack of suitable decoding key.
Keywords:
Quantum Secret Sharing, Quantum Secret Broadcast, Cluster Network

1. Introduction
Since the first quantum key distribution (QKD) protocol BB84 [1] was proposed, quantum communication has attracted much attention in the filed of infor- mation security. In order to meet the demand of adaptive quantum communi- cation, quantum communication in the area of wireless network has been exploited. Cheng et al. [2] made the first attempt in wireless quantum networks (WQN) and proposed a quantum routing mechanism, which allows teleporting a quantum state from a node to another node. Li et al. [3] designed a framework for distributed wireless quantum networks. In 2013, Cao et al. [4] applied a cluster mesh structure and addressed the problems of EPR resources and quantum channel establishment. The above researches gradually enhance the feasibility of wireless quantum networks. However, there are still a problem in WQN, that is inefficient, i.e., a source node will consume relay nodes’ resources , and it can only send a message to one destination node once instead of several nodes.
Quantum secret sharing (QSS) is an important branch of quantum crypto- graphy, which is a generalization of the classical secret sharing into the quantum domain. Since the first QSS protocol was presented by Hillery et al. [5], various QSS schemes have been proposed [6] [7] [8] [9]. In a typical three-party QSS scheme [8], a sender, Alice, splits a secret message into two shares and dis- tributes the shares to two receivers, Bob and Charlie, so that none of them can recover the secret from their own shares. Only if Bob and Charlie publish their own measurement results honestly, can they read out the secret message cor- rectly.
Inspired by the feature of QSS that more than one party can receive secret message each time, we introduce the idea of QSS into a wireless quantum network, and propose a quantum secret broadcast scheme to solve the troubling efficiency problem. In a cluster network cored on three parties of QSS, three cluster heads, Alice, Bob, and Charlie will collaborate honestly to broadcast messages to cluster members by using pre-shared GHZ states. The communi- cation mode can be whole-network broadcast or intra-cluster broadcast. Furthermore, to prevent illegal eavesdropping, three cluster heads will perio- dically update a encoding key Y. Consequently, illegal nodes cannot read out the message correctly for lack of suitable decoding key.
2. Related Works
2.1. Wireless Quantum Networks
Wireless quantum networks (WQN) has been studied by many groups [2] [3] [4] [10] to exploit quantum communication into the area of wireless network. The basic method of communication between nodes in WQN is quantum tele- portation. Figure 1 shows an example of wireless quantum network, where dotted line represents quantum channel based on EPR pairs. We assume node A is a source node and node E is a destination node. A possible routing path is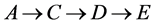 , which means the relay node C and D will also consume their EPR pairs and classical bits to assist this communication.
, which means the relay node C and D will also consume their EPR pairs and classical bits to assist this communication.
Although WQN has been explored further in the aspects of EPR-pair allo- cation [3], routing optimization, network architecture construction [4] [10], and so on, the basic issues of the WQN are still EPR-pair distribution and quantum
Figure 1. Wireless quantum network.
relay path establishment.
2.2. Three-Party QSS
In 2009, Liu et al. [8] proposed a three-party QSS scheme with pre-shared GHZ states, which uses an auxiliary EPR pair to encode two secret message bits.
By convention, the sender is denoted as Alice (A), and the receivers is denoted as Bob (B) and Charlie (C). First, they share three-particle GHZ states, each of which is:
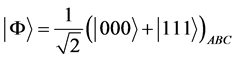 (1)
(1)
After eavesdropping check to ensure the security of quantum channel (GHZ states), Alice prepares an EPR pair in the state:
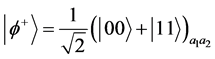 (2)
(2)
Four unitary operators are defined as: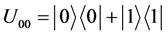 ,
, 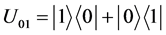 ,
, 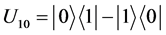 ,
,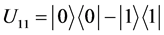 .
.
The system state after encoding can be expressed as:
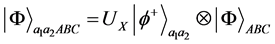 (3)
(3)
where 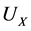 is one of four operations
is one of four operations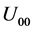 ,
, 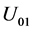 ,
, 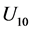 ,
, 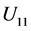 , which encodes a two-bit message “00”, “01”, “10”, and “11”, respectively.
, which encodes a two-bit message “00”, “01”, “10”, and “11”, respectively.
Next, Alice applies a controlled-NOT (CNOT) gate on both particle 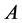 and particle
and particle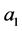 , here
, here 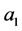 is the controller and
is the controller and 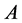 is the target. Then she sends the particle
is the target. Then she sends the particle 

Then Alice applies a Bell-state measurement on both particles 




Their measurement results will be correlated in certain forms according to different encoding operation 
3. The Proposed Scheme
In Liu’s QSS scheme [8], the correlation between the measurement results and secret message play a important role in decoding. Assume that other nodes are also aware of the correlation, they can also recover the secret messages.
The main idea of our scheme is that in a cluster network cored on three parties of QSS, Alice (A), Bob (B), and Charlie (C) are cluster heads. In each communication period, one cluster head plays the role of a message sender, other two cluster heads are assistants to help sender broadcast messages. Moreover, we design two types of communication modes, namely whole- network broadcast and intra-cluster broadcast, to meet different requirement of a sender.
The quantum secret broadcast scheme is described as follows:
Step 0: Initializing
Figure 2 shows initializing phase of the scheme. We apply a cluster structure for network, three cluster heads A, B, and C, own three-party GHZ states, each GHZ state is:

where





Before communication, quantum channel of GHZ states should be checked for potential attacks, the GHZ among A, B and C can be rewritten as:
Figure 2. Initializing phase.

where

performs measurement under basis 






Step 1: Encoding key updating. When each communication period begins, three cluster heads generate a two-bit “encoding key” 
Assume that it is A’s turn to produce the “encoding key”
qubits for B and C, respectively, in which the state 

represented 
When B, C both receive the encoding key
After that, the whole network knows the latest encoding key. So the encoding key updating phase is completed.
Step 2: Communication mode selecting. To meet different requirement of cluster heads, the communication mode can be selected to whole-network broadcast or intra-cluster broadcast.
If a cluster head needs to broadcast messages to the whole network, it will announce an application in this step. Then three cluster heads discuss to select one appropriate cluster heads to be the sender of whole-network broadcast. Otherwise, the communication switches into the mode of intra-cluster broadcast if no cluster heads announce an application.
1) Whole-network broadcast
Step 3: Message encoding. Assume that cluster head A is chosen to be the sender. For each shared GHZ state, she prepares an auxiliary EPR state as follows:

Figure 3(a) shows the system states before encoding, where




Figure 3. System state of whole-network broadcast.
state.
We define four unitary operators:

Step (3.1) A encodes message on EPR state with two operators 


where 

For convenience, we assume the encoding key 




Step (3.2) A applies a CNOT gate on both particles 



Step (3.3) A performs a Hadamard gate on 





System state after encoding is as shown in Figure 3(b), where the original entangled GHZ state 





Step4: Measurement result broadcasting. Sender A performs Bell-state mea- surement on both particles 




Step 5: Message decoding.
Step (5.1) All the cluster members consider three cluster heads’ measurement results and can read out A’s messages 
Step (5.2) As 




Let us take an example to illustrate how the mode of whole-network broadcast works. At first, we assume that the encoding key 



Table 1. Correlation of measurement results and messages in whole-network mode.
to read out massages 



2) Intra-cluster broadcast
Assume that no cluster heads announce an application, the communication will switch into the mode of intra-cluster broadcast, in which three cluster heads can send messages to their own cluster members. We take A as an example to illustrate this mode.
Step 3: Message encoding. Similarly, based on the idea of QSS, A randomly selects two cluster members (denote as 


As is shown in Figure 4(a), A holds particle 1 and 3, while 

We define two unitary operators for encoding:

A encodes one bit message on particle 1 with two operators 


where 





For convenience, we assume “


Figure 4. System state of intra-cluster broadcast.
From Equations (21)-(22), system state is changed as shown in Figure 4(b), where the two original entangled pairs are all destroyed, and particle 1 and 3 form a new entangled state, 2 and 4 form a new entangled state.
Step 4: Measurement result Broadcasting. A performs a Bell-state mea- surement on both particles 1 and 3, 


Step 5: Message decoding.
Step (5.1) A’s cluster members consider three parties’ results and read out message 
Step (5.2) 




We take an example of A cluster to illustrate how intra-cluster mode works. Assume that the encoding key 










4. Scheme Analysis
4.1. Network
Our scheme aims to achieve message broadcast in WQN, which attempts to extend communication mode and improve network performance. Different from conventional schemes based on quantum teleportation [2] [3] [4] [10], we apply the method of QSS instead of teleportation.
For the reason of applying QSS, our scheme has differences with conventional schemes which are based on quantum teleportation in many aspects. Our scheme transmits classical messages by broadcast, while previous ones transmit quantum state by teleportation. Our scheme makes a attempt to achieve message broadcast, the number of receivers can be 


Table 2. Correlation of measurement results and messages in intra-cluster mode.
nodes as assistants to build a routing path from source to destination, the farther distance between source and destination is, the more assistant nodes are needed. we denote 
Table 3 gives a summary of comparison between our scheme and con- ventional schemes.
4.2. Efficiency
The efficiency in our quantum communication protocol can be defined as:

where 


We make a comparison between our scheme and Cao’s scheme [4], for the latter is a typical research of previous schemes and it also uses a cluster structure for WQN.
Consider a situation that a cluster head sends messages to his and other cluster heads’ members. In our scheme, 






Table 4 makes a comparison between our scheme and Yang’s scheme.
We can see from Table 4 that the performance of our scheme is better than Yang’s scheme, especially when the number of receivers 

Table 3. Comprehensive comparison.
Table 4. Efficiency comparison.
4.3. Security
In the proposed scheme, no qubits carrying messages are transmitted directly, so quantum channel only exists in the GHZ states. If an eavesdropper Eve cannot escape from the security check at the phase of Step 0: Initializing, our scheme is secure. The security check method of our scheme is the same as QSS schemes in [7] [8], which assumes Eve’s attack 


The error rate involved in Eve is
Considering that receivers read out messages according to the three cluster head’s measurement results, another secure problem is that if an eavesdropper also knows the correlation between messages and measurement results, it can obtain messages. To solve this problem, our scheme generates an encoding key 
In the whole-network mode, by randomly selecting a key, an eavesdropper will recover a message with the error rate 75%, while in the intra-cluster mode, the error rate is 50%. So our scheme uses security check for quantum channel and key updating for secret messages to ensure security.
5. Conclusion
In this paper, a quantum secret broadcast scheme was proposed to solve efficiency problem in WQN, where each two bits are encoded in an auxiliary EPR states. The proposed scheme constructs a cluster network cored on three- party QSS, three cluster heads share three-party GHZ states, and each cluster head shares EPR pairs with its own cluster members. For different requirement of cluster heads, the scheme can be selected into whole-network broadcast, in which one cluster head is message sender and other two cluster heads are assistants to help broadcast messages to whole network, or intra-cluster broad- cast, in which each cluster head chooses two cluster members as assistants to help broadcast messages to its intra-cluster members. Furthermore, a wireless quantum network with more than three cluster heads needs to be investigated for extensive application.
Acknowledgements
This project was supported by the National Natural Science Foundation of China (No. 61571024) and the National Key Research and Development Program of China (No. 2016YFC1000307) for valuable helps.
Cite this paper
Shang, T., Du, G. and Liu, J.W. (2017) Quantum Secret Broadcast for Wireless Quantum Networks. Int. J. Communications, Network and System Sciences, 10, 7-18. https://doi.org/10.4236/ijcns.2017.108B002
References
- 1. Bennett, C.H. and Brassard, G. (1984) Quantum Cryptography: Public-Key Distribution and Tossing. Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, IEEE Press, 175-179.
- 2. Cheng, S.T., Wang, C.Y. and Tao, M.H. (2005) Quantum Communication for Wireless Wide-Area Networks. IEEE Journal on Selected Areas in Communications, 23, 1424-1432. https://doi.org/10.1109/JSAC.2005.851157
- 3. Li, J.S. and Yang, C.F. (2009) Quantum Communication in Distributed Wireless Sensor Networks. IEEE 6th International Con-ference, Macau, 12-15 Oct. 2009, 1024-1029. https://doi.org/10.1109/MOBHOC.2009.5337016
- 4. Cao, Y., Yu, X.Y. and Cai, Y.X. (2013) Wireless Quantum Communication Networks with Mesh Structure. IEEE 3rd International Conference on Information Science and Technology, Yangzhou, 23-25 March 2013, 1485-1489. https://doi.org/10.1109/ICIST.2013.6747818
- 5. Hillery, M., Buzek, V. and Berthiaume, A. (1999) Quantum Secret Sharing. Physical Review A, 59, 1829-1834. https://doi.org/10.1103/PhysRevA.59.1829
- 6. Deng, F.G., Zhou, H.Y. and Long, G.L. (2005) Bidirectional Quantum Secret Sharing and Secret Splitting with Polarized Single Photons. Physics Letters A, 337, 329-334. https://doi.org/10.1016/j.physleta.2005.02.001
- 7. Wang, J., Zhang, Q. and Tang, C.J. (2007) Multiparty Quantum Se-cret Sharing of Secure Direct Communication Using Teleportation. Communications in Theoretical Physics, 47, 454-458. https://doi.org/10.1088/0253-6102/47/3/015
- 8. Liu, Y. and Xu, C. (2009) Three-Party Quantum Secret Sharing Based on Secret Direct Communication. International Forum on Information Technology and Applications, 1, 126-130.
- 9. Hwang, T., Hwang, C.C. and Li, C.M. (2011) Multiparty Quantum Secret Sharing Based on GHZ States. Physica Scripta, 83, 045004. https://doi.org/10.1088/0031-8949/83/04/045004
- 10. Nguyen, T.M.T., Sfaxi, M.A. and Ghernaouti-Helie, S. (2006) Integration of Quantum Cryptography in 802.11 Networks. Proc. 1st Int. Conf. on Availability, Reliability and Security, Vi-enna, 20-22 April 2006, 116-123. https://doi.org/10.1109/ARES.2006.75
- 11. Zhou, J.D., How, G. and Wu, S.J. (2007) Controlled Teleportation of an Arbi-trary Multi-Qudit State in a General Form with d-Dimensional Greenberger-Horne-Zei- linger States. Chinese Physics Letters, 24, 1151-1153. https://doi.org/10.1088/0256-307X/24/5/007






