Energy and Power Engineering
Vol.09 No.04(2017), Article ID:75335,8 pages
10.4236/epe.2017.94B073
A Method of Auxiliary Planning for Intelligent Substation Access System Based on Security Region
Gao Yi1, Songtao Zhang2, Chao Qin2, Yuan Zeng2, Yang Yang2, Yingying Liu1, Shengwei Li1
1State Grid Tianjin Power Economics & Technology Research Institute, Tianjin, China
2Key Laboratory of Smart Grid of Ministry of Education, Tianjin University, Tianjin, China




Received: March 10, 2017; Accepted: March 30, 2017; Published: April 6, 2017
ABSTRACT
This paper presents an auxiliary planning method for intelligent substation access system based on security region. Firstly, the method of resolving the static voltage security region is proposed. Secondly, the method of constructing the optimal index of substation accession is given, which is used to describe the priority of the node into the substation. Finally, a complete set of intelligent substation access system auxiliary planning strategy is given, which takes into account the constraints of the normal operation of the grid on the voltage amplitude.
Keywords:
Substation, the Static Security Region, Optimized Index of Substation Accession

1. Introduction
Intelligent substation as the physical basis of smart grid, will go through the smart grid construction process [1]. With the continuous development of social and economic progress, all walks of life power users of the basic requirements of the power system has been to a more secure, more reliable, more economic change, substation as a particularly important part of the power system, and the most important energy transmission point in the distribution equipment [2]. Whether the substation planning and design is reasonable and whether it can adapt to the violent fluctuation of the load and meet the load development demand in the next few years is extremely important. Therefore, the optimization analysis and evaluation technology of the substation access system is an important content in the power system planning research.
In paper [3], the safety of the typical access system scheme of the two substations is compared. In paper [4], the main technical scheme of the typical design of 220 kV and 110 kV substations and the technical characteristics of each module are analyzed. In paper [5] According to the principle of minimizing the cost and maximizing the efficiency of the project, and achieving the goal of minimizing the life cycle cost of the project in the whole life, while ensuring the quality of the design, and realizing the maximum economic efficiency and the maximum social benefit of the project construction. At present, at home and abroad in the substation program design method, in addition to the economic comparison phase of the introduction of life cycle cost (Life Cycle Cost, LLC), and not much improvement [6] [7].
In this paper, we use the security region method, which can give the relative position of the current operating point in the domain to characterize the security and stability margin of the whole system [8] [9]. By the stability margin information, the weak link of the system is obtained. Based on the boundary coefficient of the security region of the node, the auxiliary decision making scheme for the substation access system is provided.
2. Construction of Static Voltage Security Region
The mathematical description of the static security region is as follows: For a given network topology, the static security region is a set of all system operating points in the decision space that satisfy the power flow equation 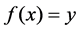 and the static security constraint
and the static security constraint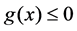 . The mathematical expressions of the static security domain in the decision space:
. The mathematical expressions of the static security domain in the decision space:
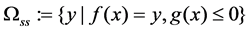 (1)
(1)
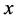 denotes the state variable vector of the system, including the voltage phase angle of the generator and the load bus and the voltage amplitude of the load bus,
denotes the state variable vector of the system, including the voltage phase angle of the generator and the load bus and the voltage amplitude of the load bus, 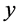 denotes the complex power injection vector of the bus, and
denotes the complex power injection vector of the bus, and 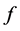 is determined by the system network structure.
is determined by the system network structure.
2.1. Node Power Injection Equation Linearization Processing
Assuming that the system has n − 1 nodes and nb branches, where node 0 is the equilibrium node, there are g + 1 generator nodes; G is used to denote the set of generator nodes except the equilibrium node; L is the load node A set of all branches.
According to the node power injection equation:
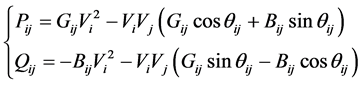 (2)
(2)
Using the method in paper [10] to linearize the node power injection equation. Written in matrix form:
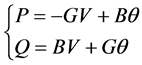 (3)
(3)
In the formula, 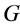 is the real part of the admittance matrix,
is the real part of the admittance matrix, 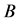 is the imaginary part of the admittance matrix, and all are constants.
is the imaginary part of the admittance matrix, and all are constants.
2.2. Static Voltage Security Region
The decision space of the static voltage safety domain defined in this paper includes the active power injection of the node and the reactive power injection of the load node, and increases the voltage amplitude of the generator node.
In general, the power system operates in a small neighborhood of the point (V = 1, θ = 0), and the mapping from the V − θ space to the P − Q space is mapped one by one. Therefore, in the V − θ space, the inverse mapping of the Equation (2) exists in a neighborhood of the run point (V = 1, θ = 0).
Assume that the system has 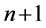 node, where node 0 is a balanced node and has
node, where node 0 is a balanced node and has 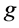 PQ nodes. The set of PV nodes is denoted by G, and L is the set of PQ nodes. The Equation (3) can be written as:
PQ nodes. The set of PV nodes is denoted by G, and L is the set of PQ nodes. The Equation (3) can be written as:
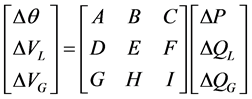 (4)
(4)
In the formula, Where the PV node and the PQ node are separated. A, B, C, D, E, F, G, H and I are the block matrix, the order is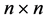 ,
, 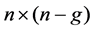 ,
, 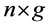 ,
, 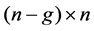 ,
, 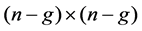 ,
, 



According to the Equation (4):


From the Equation (5), Equation (6) can be obtained:










The above equation can be organized as:

Thus, the static security region of the upper limit of the load node voltage can be defined as:

Similarly, the static safety region of the lower limit of the load node voltage can be defined as:

The static voltage safety region of the whole system is the intersection of the static voltage safety region where the upper and lower limits of the voltage of all nodes are satisfied.

3. Strategy of Auxiliary Planning for Intelligent Substation Access
This paper uses the stability margin of the security region to quantify the system security level, to find the node that is closest to the security region boundary under the current operating conditions. This paper presents the optimized index of substation access (OISA), and describes the auxiliary planning strategy of substation access system in detail.
3.1. Stability Margin and Safety
The calculation equation for the stability margin of the load node j is as follows:


The equation of the stability margin of the system (SRM):

3.2. Auxiliary Planning Strategy of Substation Access
According to the optimized index of substation access (OISA), forming appropriate planning.

The specific method is as follows:
1) The stability margin analysis of the system is carried out to find the node with the smallest stability margin, meanwhile, obtaining the corresponding domain boundary coefficient information of the node;
2) Sorting the optimized index of substation access(OISA), the larger the index value of the node, give priority to the node into the substation;
3) Replace the PQ node with the PV node in the position obtained in step 2);
4) Recalculate the security region of different schemes and the corresponding system stability margin. By comparison, the optimal access scheme is obtained.
Auxiliary planning strategy of substation access’s flow chart, as shown in Figure 1.
4. Template
The following is an example of the IEEE 118 node system. The system has a total
Figure 1. Auxiliary planning strategy of substation access’s flow chart.
of 55 PV nodes, 63 PQ nodes, and node 69 is the balance node. The voltage constraint is
According to the current power system network topology data, and the corresponding constraints, in the decision space of the system, obtain the corresponding static voltage security region in the current situation. Select the two- dimensional cross-section of the security region boundary corresponding to load node 9 on P11 and Q11.As shown in Figure 3.
In this paper, different load levels were selected for stability margin analysis. The results are shown in Table 1.
From the analysis of Table, the system load increases, the system's stability margin decreases. As the installed capacity of the system is sufficient, the increase of load has little effect on the system stability margin. The current operating point is closest to the security region boundary of BUS 9.
Figure 2. IEEE 118 node system.
Figure 3. Security region boundary corresponding to load node 9 on P11 and Q11.
According to the information on the security region boundary of BUS 9, Sorting the optimized index of substation access (OISA). Part of the data shown in Table 2.
For analysis of OISA, in the Table 2, it is advisable to put substations at node 11 and node 13. Option 1: Substation is installed at load node 11; Option 2: Substation is installed at load node 13.
In the case of input substation parameters consistent, the stability margin analysis for Option 1and Option 2 is shown in Figure 4.
From the table can conclude that, access substation in the BUS 11 and BUS 13 can improve system stability margin. However, BUS 11 access substation’s effect of Stability margin improvement is more obvious.
Figure 4. The margin information of different access scheme.
Table 1. System stability analysis with different load levels.
Table 2. The coefficient of Node 9 security region boundary t, and OISA sorting information.
5. Conclusion
In this paper, the direct construction method of static voltage safety domain is proposed. For the first time, the idea of “domain” is applied to the auxiliary planning of intelligent substation. This paper presents a set of complete intelligent substation access system program auxiliary planning method.
Acknowledgements
This work is supported by the National Science Foundation of China (No.51507108) and the project of State Grid Tianjin Electric Power Company (KJ15-1-08).
Cite this paper
Yi, G., Zhang, S.T., Qin, C., Zeng, Y., Yang, Y., Liu, Y.Y. and Li, S.W. (2017) A Method of Auxiliary Planning for Intelligent Substation Access System Based on Security Region. Energy and Power Engineering, 9, 675-682. https://doi.org/10.4236/epe.2017.94B073
References
- 1. Song, X.K., Han, L. and Huang, J. (2016) Research on the Development of Smart Grid Technology in China. Electric Power Con-struction, 3, 1-11. https://doi.org/10.1109/TPEL.2016.2636882
- 2. Song, X.K., Li, J.R., Xiao, Z.H., Lin, H.Y., Li, Z.Y., Zou, G.H., Bao, Y. and Huang, Y.L.(2012) A New Generation of Intelligent Substation overall Design. Power Construction, 11, 1-6.
- 3. Pan, H.B. (2004) Comparison of Security of Two Kinds of Access System Schemes for Terminal Substation. Electric Power Safety Technology, 8, 20-22.
- 4. Guo, C.C., Xu, Z.Z. and Xu, X.J. (2007) Study and Application of Typical Design of 220kV and 110kV Substation. Power System Technology, 6, 23-30.
- 5. Li, S.H. and Lu, X.M.(2010) Application of Life Cycle Cost Analysis in Digital Substation Planning and Design. Electric Power Construction, 2, 8-9.
- 6. Li, R.S., Li, Y.B. and Zhou, F.Q.(2010)Intelligent Substation Func-tional Architecture and Design Principles. 2010 China Smart Grid Symposium, 24-27.
- 7. Wu, J.K. (1994) Two Problems of Com-puter Mechanics Program System. Proceedings of Finite Element Analysis and CAD, Peking University Press, Beijing, 9-15.
- 8. Li, J., Xue, A.C., Cao Z.B., Bi, T.S. (2011) On Impact of the Different Models of Generation System to Power System Dynamic Security Region. Power and Energy Engineering Conference (APPEEC), 2011 Asia-Pacific. https://doi.org/10.1109/appeec.2011.5748696
- 9. Almeida, F. C. B., Passos Filho, J. A., Pereira, J. L. R., Marcato, A. L. M. and E. J. de Oliveira. Assessment of the Generator Remote Voltage Control through Static Security Regions. Power and Energy Society General Meeting, 24-29, July 2011, 1-7.
- 10. Wu, Y.J. (2014) Application of a Static Approximation Static Security Domain for Power System Based on Hyperplane and Its Solution. Journal of Electrical Engineering, S1, 374-383.






