 Wireless Sensor Network, 2009, 3, 163-170 doi:10.4236/wsn.2009.13022 ctober 2009 (http://www.SciRP.org/journal/wsn/). Copyright © 2009 SciRes. WSN Published Online O ContSteg: Contourlet-Based Steganography Method Hedieh SAJEDI, Mansour JAMZAD Computer Engineering Department, Sharif University of Technology, Tehran, Iran E-mail: A_sajedi@ce.sharif.edu, Jamzad@sharif.edu Received April 26, 2009; revised May 20, 2009; accepted May 25, 2009 Abstract A category of techniques for secret data communication called steganography hides data in multimedia me- diums. It involves embedding secret data into a cover-medium by means of small perceptible and statistical degradation. In this paper, a new adaptive steganography method based on contourlet transform is presented that provides large embedding capacity. We called the proposed method ContSteg. In contourlet decomposi- tion of an image, edges are represented by the coefficients with large magnitudes. In ContSteg, these coeffi- cients are considered for data embedding because human eyes are less sensitive in edgy and non-smooth re- gions of images. For embedding the secret data, contourlet subbands are divided into 4×4 blocks. Each bit of secret data is hidden by exchanging the value of two coefficients in a block of contourlet coefficients. Ac- cording to the experimental results, the proposed method is capable of providing a larger embedding capacity without causing noticeable distortions of stego-images in comparison with a similar wavelet-based steg- anography approach. The result of examining the proposed method with two of the most powerful steganaly- sis algorithms show that we could successfully embed data in cover-images with the average embedding ca- pacity of 0.05 bits per pixel. Keywords: Information Hiding, Steganography, Steganalysis, Contourlet Transform 1. Introduction Steganography methods hide the secret data in a cover carrier so that the existence of the embedded data is un- detectable. The cover carrier can be different kinds of digital media such as text, image, audio, and video [1]. In a successful steganography method the carrier medium does not attract attentions. The security of the steg- anography methods is mostly influenced by the kind of cover media, the method for selection of places within the cover that might be modified, the type of embedding operation, and the number of embedding changes that is a quantity related to the length of the embedded data. The aim of the steganography methods is to commu- nicate securely in a completely undetectable manner. As the steganography techniques progress, there is an in- creased interest in steganalysis algorithms which their main goal is detecting the presence of hidden data. Many steganography methods have been proposed and several stego-products have been developed (e.g., EzS- tego [2]) in which an innocuous-looking image is used as the cover-image to conceal the secret data. In these me- thods, the secret data is embedded into the cover-image by modifying the cover-image to form a stego-image. Some image hiding systems use uncompressed images (e.g., BMP) or lossless compressed images (e.g., GIF) as cover-images. These images potentially contain visual redundancy so that they can provide large capacity to hide secret data. For reducing transmission bandwidth and storing space, the JPEG is currently the most common format for images that are used on the Internet. Therefore, embedding techniques in Discrete Cosine Transform (DCT) domain are popular because of the large usage of JPEG images. Although modifications of properly se- lected DCT coefficients during embedding process will not cause noticeable visual artifacts, nevertheless they cause detectable statistical degradations. Various steg- anography methods like F5 [3], Outguess [4], Model- based (MB) [5], Perturbed Quantization (PQ) [6], and YASS [7] have been proposed with the purpose of mini- mizing the statistical artifacts which are produced by modifications of DCT coefficients. On the other hand, some steganography methods based on wavelet transform have been presented. In [8], a steganography method based on wavelet and modulus function is proposed. In this method, the capacity of a 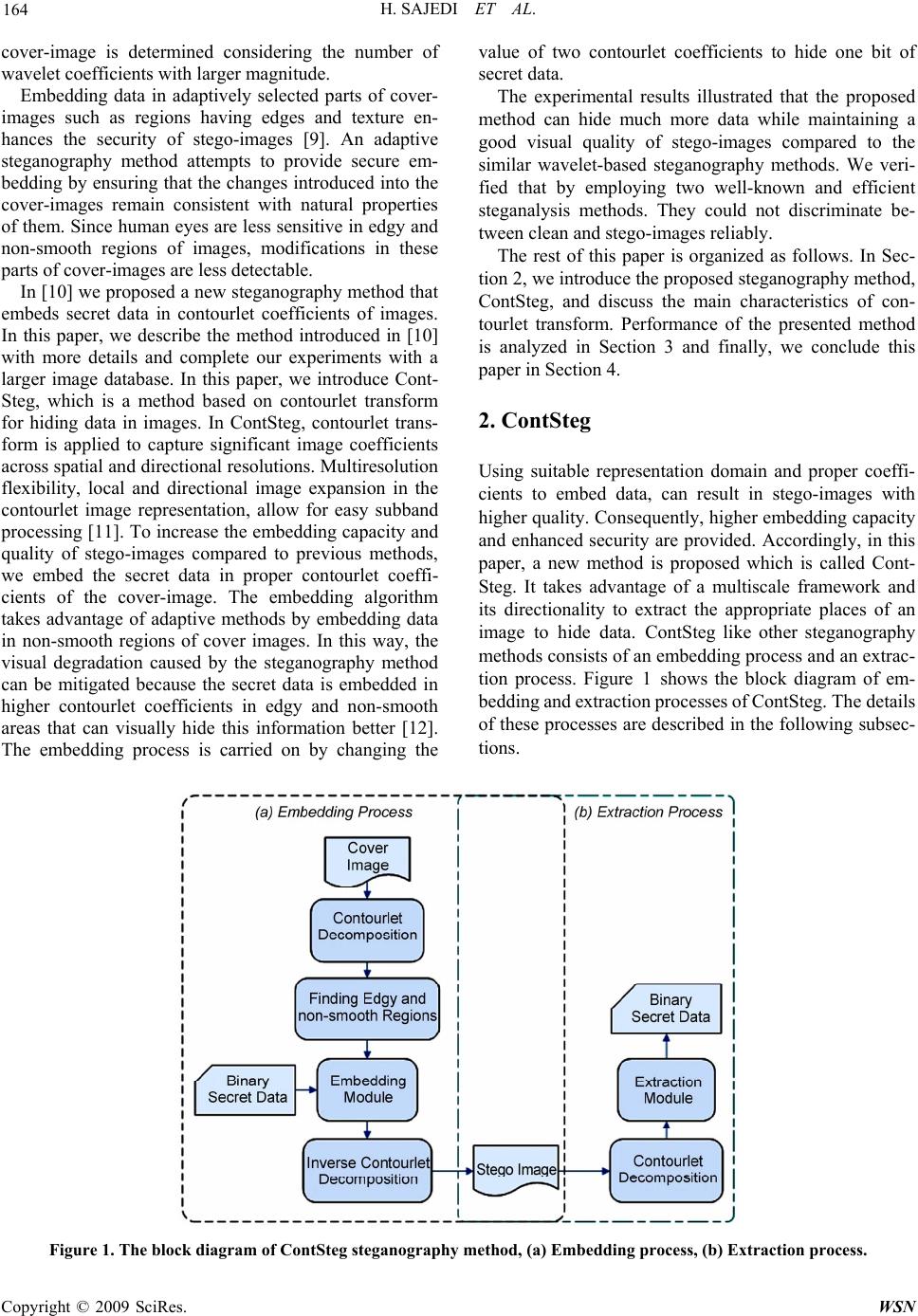 H. SAJEDI ET AL. 164 cover-image is determined considering the number of wavelet coefficients with larger magnitude. Embedding data in adaptively selected parts of cover- images such as regions having edges and texture en- hances the security of stego-images [9]. An adaptive steganography method attempts to provide secure em- bedding by ensuring that the changes introduced into the cover-images remain consistent with natural properties of them. Since human eyes are less sensitive in edgy and non-smooth regions of images, modifications in these parts of cover-images are less detectable. In [10] we proposed a new steganography method that embeds secret data in contourlet coefficients of images. In this paper, we describe the method introduced in [10] with more details and complete our experiments with a larger image database. In this paper, we introduce Cont- Steg, which is a method based on contourlet transform for hiding data in images. In ContSteg, contourlet trans- form is applied to capture significant image coefficients across spatial and directional resolutions. Multiresolution flexibility, local and directional image expansion in the contourlet image representation, allow for easy subband processing [11]. To increase the embedding capacity and quality of stego-images compared to previous methods, we embed the secret data in proper contourlet coeffi- cients of the cover-image. The embedding algorithm takes advantage of adaptive methods by embedding data in non-smooth regions of cover images. In this way, the visual degradation caused by the steganography method can be mitigated because the secret data is embedded in higher contourlet coefficients in edgy and non-smooth areas that can visually hide this information better [12]. The embedding process is carried on by changing the value of two contourlet coefficients to hide one bit of secret data. The experimental results illustrated that the proposed method can hide much more data while maintaining a good visual quality of stego-images compared to the similar wavelet-based steganography methods. We veri- fied that by employing two well-known and efficient steganalysis methods. They could not discriminate be- tween clean and stego-images reliably. The rest of this paper is organized as follows. In Sec- tion 2, we introduce the proposed steganography method, ContSteg, and discuss the main characteristics of con- tourlet transform. Performance of the presented method is analyzed in Section 3 and finally, we conclude this paper in Section 4. 2. ContSteg Using suitable representation domain and proper coeffi- cients to embed data, can result in stego-images with higher quality. Consequently, higher embedding capacity and enhanced security are provided. Accordingly, in this paper, a new method is proposed which is called Cont- Steg. It takes advantage of a multiscale framework and its directionality to extract the appropriate places of an image to hide data. ContSteg like other steganography methods consists of an embedding process and an extrac- tion process. Figure 1 shows the block diagram of em- bedding and extraction processes of ContSteg. The details of these processes are described in the following subsec- tions. Figure 1. The block diagram of ContSteg steganography method, (a) Embedding process, (b) Extraction process. Copyright © 2009 SciRes. WSN  H. SAJEDI ET AL. 165 (a,b) (c,d) (c) (a) (b) Figure 2. Embedding data in contour let coefficients of an image, (a) Original input image, (b)Visualization of contourle t de- composition of an image into one pyramidal level and sixteen directional subbands, (c) A 4×4 block of contourlet coefficients and the place of two coefficients for embedding. 2.1. Hiding Data in Contourlet Coefficients Contourlet transform is one of several transforms devel- oped in recent years, aimed at improving the representa- tion sparsity of images over the wavelet transform. The main feature of this transform is the potential to handle 2-D singularities efficiently, i.e. edges, unlike wavelet, which can deal with point (i.e.1-D) singularities exclu- sively [13]. Contourlet transform is a directional exten- sion of wavelet transform that fixes the wavelet sub- band-mixing problem and improves its directionality. Two-dimensional wavelet transform produces one ap- proximation subband, and three details subbands, corre- sponding to the horizontal, vertical, and diagonal direc- tions. The diagonal subband mixes the directional infor- mation oriented at 45◦ and 135◦. The main idea of con- tourlet is to find some directional extensions to divide further each detail subband of the wavelet into a number of directions. This transform is based on a double filter bank structure by combining the Laplacian pyramid with a directional filter bank [14]. Figure 2 shows an image that is decomposed into one pyramidal level and sixteen directional subbands (higher coefficients are colored white). Because of the subband-mixing problem in wavelet transform, manipulating one coefficient in diagonal sub- band affects the value of other relevant coefficients in other directions. We used the effectiveness of contourlet transform in image decomposition to separate directions. Hence, manipulating the value of a coefficient in the contourlet subbands has less effect in the quality of the image than changing a coefficient in wavelet subbands. Furthermore, most of the current existing steganalysis algorithms are limited to the domain of spatial, wavelet, and DCT transform. Therefore, distinguishing cover- images from stego-images (constructed by embedding data into their contourlet coefficients) is not easy by these steganalysis algorithms. Accordingly, considering the fact that higher embedding efficiency translates into better steganographic security, more secure stego-images are achieved using the proposed method. 2.2. Embedding Process The embedding process is done in the following steps: Step 1: The cover-image is decomposed with one py- ramidal level and sixteen directional contourlet transform. Step 2: The regions of the subbands in which the data can be embedded are identified. Then the embedding process determines higher contourlet coefficients in these regions that can be used for embedding. Step 3: According to Kerckhoffs’ principle [15], the embedding algorithm is supposed to be known to the public. Therefore, the embedding process may use an embedding key so that only the legal user can successfully extract the embedded data by using the corresponding extraction key in the extraction process. Accordingly, a key that is a seed for gener- ating a random sequence is considered to provide the embedding location addresses of 4×4 blocks. C opyright © 2009 SciRes. WSN 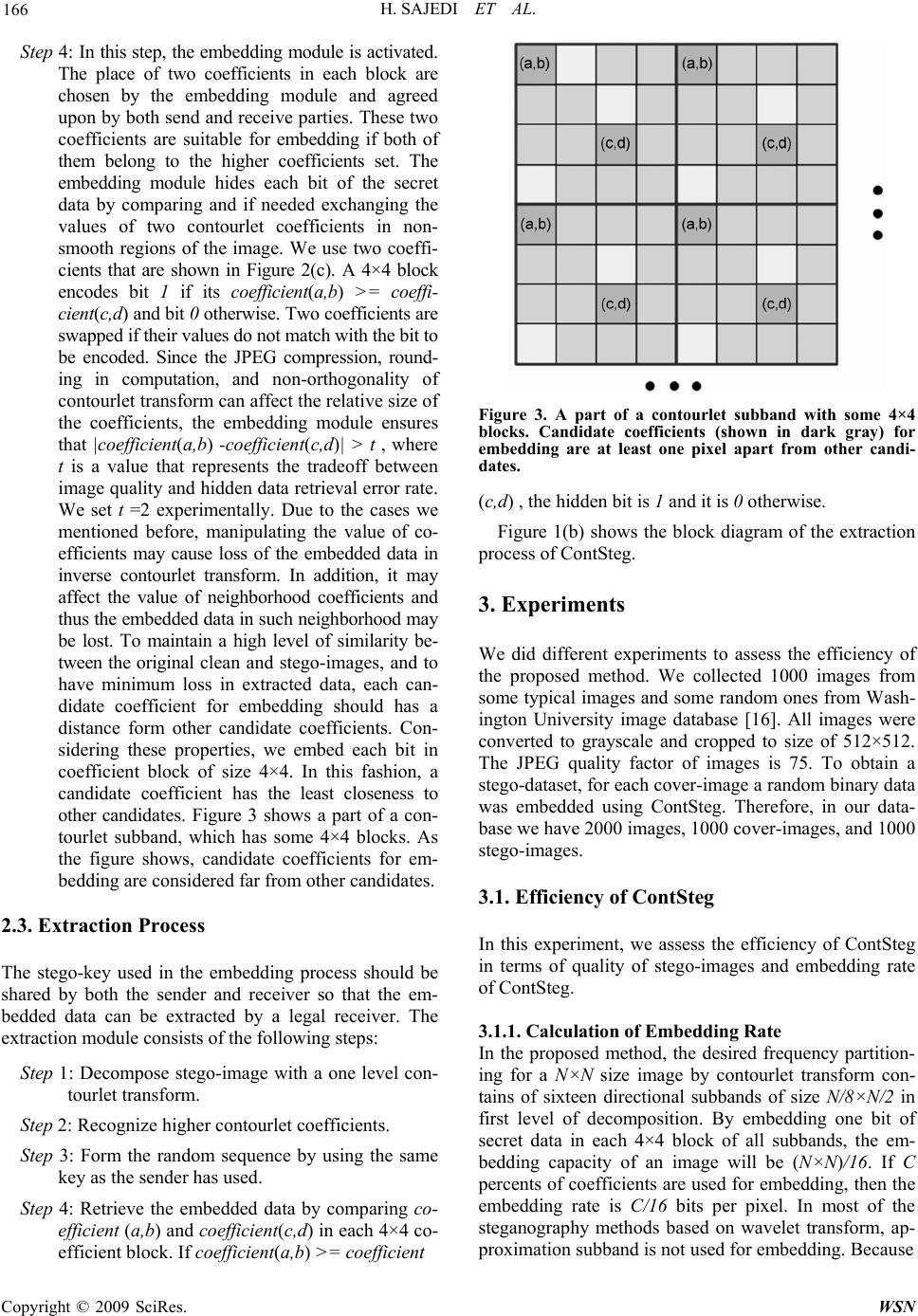 H. SAJEDI ET AL. 166 Step 4: In this step, the embedding module is activated. The place of two coefficients in each block are chosen by the embedding module and agreed upon by both send and receive parties. These two coefficients are suitable for embedding if both of them belong to the higher coefficients set. The embedding module hides each bit of the secret data by comparing and if needed exchanging the values of two contourlet coefficients in non- smooth regions of the image. We use two coeffi- cients that are shown in Figure 2(c). A 4×4 block encodes bit 1 if its coefficient(a,b) >= coeffi- cient(c,d) and bit 0 otherwise. Two coefficients are swapped if their values do not match with the bit to be encoded. Since the JPEG compression, round- ing in computation, and non-orthogonality of contourlet transform can affect the relative size of the coefficients, the embedding module ensures that |coefficient(a,b) -coefficient(c,d)| > t , where t is a value that represents the tradeoff between image quality and hidden data retrieval error rate. We set t =2 experimentally. Due to the cases we mentioned before, manipulating the value of co- efficients may cause loss of the embedded data in inverse contourlet transform. In addition, it may affect the value of neighborhood coefficients and thus the embedded data in such neighborhood may be lost. To maintain a high level of similarity be- tween the original clean and stego-images, and to have minimum loss in extracted data, each can- didate coefficient for embedding should has a distance form other candidate coefficients. Con- sidering these properties, we embed each bit in coefficient block of size 4×4. In this fashion, a candidate coefficient has the least closeness to other candidates. Figure 3 shows a part of a con- tourlet subband, which has some 4×4 blocks. As the figure shows, candidate coefficients for em- bedding are considered far from other candidates. 2.3. Extraction Process The stego-key used in the embedding process should be shared by both the sender and receiver so that the em- bedded data can be extracted by a legal receiver. The extraction module consists of the following steps: Step 1: Decompose stego-image with a one level con- tourlet transform. Step 2: Recognize higher contourlet coefficients. Step 3: Form the random sequence by using the same key as the sender has used. Step 4: Retrieve the embedded data by comparing co- efficient (a,b) and coefficient(c,d) in each 4×4 co- efficient block. If coefficient(a,b) >= coefficient Figure 3. A part of a contourlet subband with some 4×4 blocks. Candidate coefficients (shown in dark gray) for embedding are at least one pixel apart from other candi- dates. (c,d) , the hidden bit is 1 and it is 0 otherwise. Figure 1(b) shows the block diagram of the extraction process of ContSteg. 3. Experiments We did different experiments to assess the efficiency of the proposed method. We collected 1000 images from some typical images and some random ones from Wash- ington University image database [16]. All images were converted to grayscale and cropped to size of 512×512. The JPEG quality factor of images is 75. To obtain a stego-dataset, for each cover-image a random binary data was embedded using ContSteg. Therefore, in our data- base we have 2000 images, 1000 cover-images, and 1000 stego-images. 3.1. Efficiency of ContSteg In this experiment, we assess the efficiency of ContSteg in terms of quality of stego-images and embedding rate of ContSteg. 3.1.1. Calcul a t i on of Em bed di n g R ate In the proposed method, the desired frequency partition- ing for a N×N size image by contourlet transform con- tains of sixteen directional subbands of size N/8×N/2 in first level of decomposition. By embedding one bit of secret data in each 4×4 block of all subbands, the em- bedding capacity of an image will be (N×N)/16. If C percents of coefficients are used for embedding, then the embedding rate is C/16 bits per pixel. In most of the steganography methods based on wavelet transform, ap- proximation subband is not used for embedding. Because Copyright © 2009 SciRes. WSN  H. SAJEDI ET AL. Copyright © 2009 SciRes. WSN 167 (a) Cover-image (b) Embedding Locations (c) Stego-im age a nd its PSNR PSNR= 46.45 (dB) PSNR= 44.88 (dB) PSNR= 43.95 (dB) PSNR= 44.28 (dB) Figure 4. Computing the quality of stego-images, (a) Cover-image, (b) Proper locations for embedding are colored white, (c) Stego-image with its PSNR. changing the coefficients in approximation subband im- poses a large distortion in the stego images. Hence, in this case the embedding rate should be very low. There- fore, for a N×N image, in the first level of decomposition, the number of contourlet coefficients is (N×N)/4 more than wavelet coefficients. Therefore, more embedding rate can be archived in this domain. For a 512×512 size image, the number of contourlet coefficients is 262144. This number is equal to the number of image pixels. If we keep 50 percent of higher coefficients, we have 131072 coefficients. If one bit is embedded in each 4×4 block, the maximum rate for embedding is about 0.03 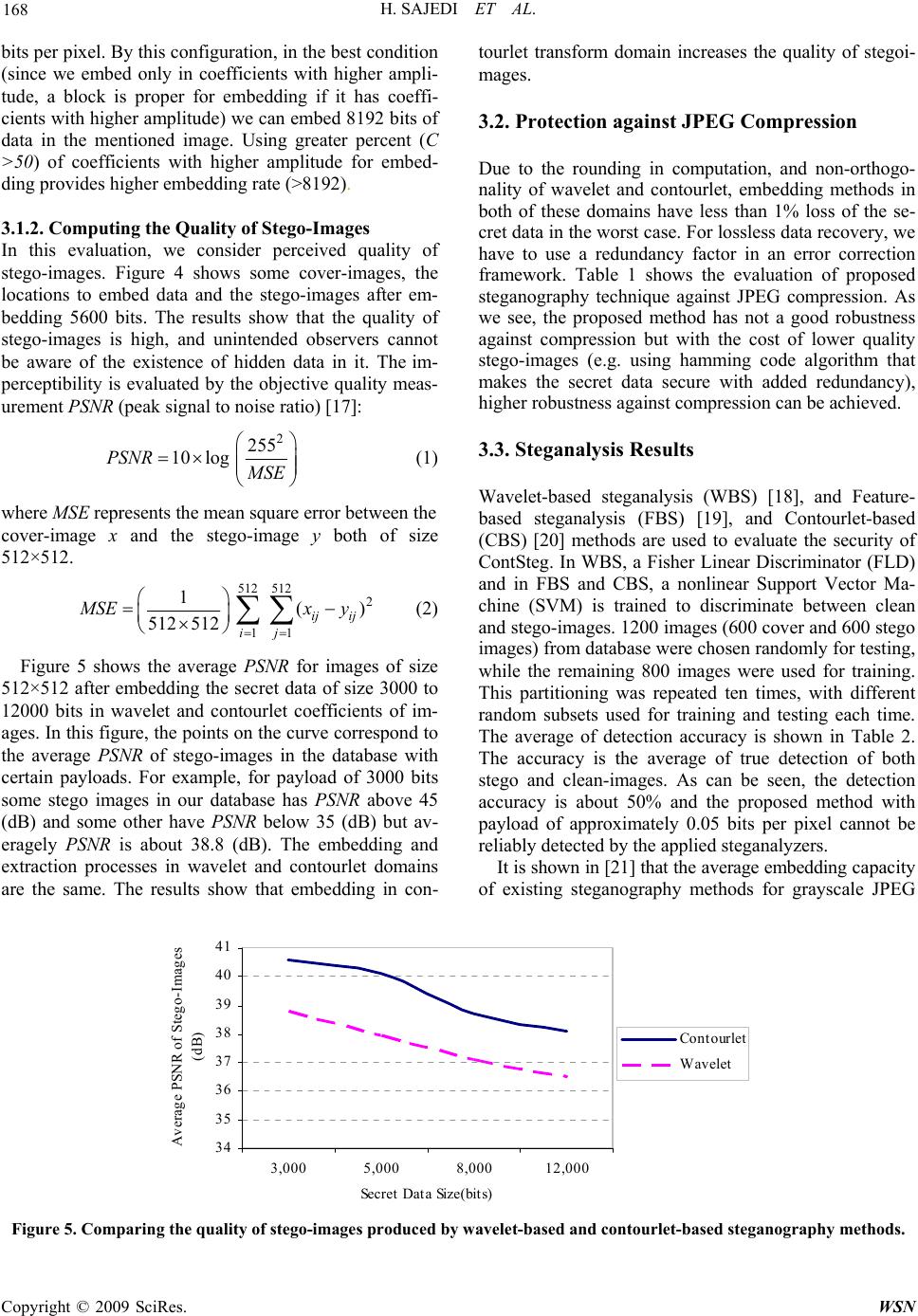 H. SAJEDI ET AL. 168 bits per pixel. By this configuration, in the best condition (since we embed only in coefficients with higher ampli- tude, a block is proper for embedding if it has coeffi- cients with higher amplitude) we can embed 8192 bits of data in the mentioned image. Using greater percent (C >50) of coefficients with higher amplitude for embed- ding provides higher embedding rate (>8192). 3.1.2. Comp uting the Quality of Ste go-Imag es In this evaluation, we consider perceived quality of stego-images. Figure 4 shows some cover-images, the locations to embed data and the stego-images after em- bedding 5600 bits. The results show that the quality of stego-images is high, and unintended observers cannot be aware of the existence of hidden data in it. The im- perceptibility is evaluated by the objective quality meas- urement PSNR (peak signal to noise ratio) [17]: 2 255 10 logPSNR SE (1) where MSE represents the mean square error between the cover-image x and the stego-image y both of size 512×512. 512 512 2 11 1( 512 512ij ij ij ) SEx y (2) Figure 5 shows the average PSNR for images of size 512×512 after embedding the secret data of size 3000 to 12000 bits in wavelet and contourlet coefficients of im- ages. In this figure, the points on the curve correspond to the average PSNR of stego-images in the database with certain payloads. For example, for payload of 3000 bits some stego images in our database has PSNR above 45 (dB) and some other have PSNR below 35 (dB) but av- eragely PSNR is about 38.8 (dB). The embedding and extraction processes in wavelet and contourlet domains are the same. The results show that embedding in con- tourlet transform domain increases the quality of stegoi- mages. 3.2. Protection against JPEG Compression Due to the rounding in computation, and non-orthogo- nality of wavelet and contourlet, embedding methods in both of these domains have less than 1% loss of the se- cret data in the worst case. For lossless data recovery, we have to use a redundancy factor in an error correction framework. Table 1 shows the evaluation of proposed steganography technique against JPEG compression. As we see, the proposed method has not a good robustness against compression but with the cost of lower quality stego-images (e.g. using hamming code algorithm that makes the secret data secure with added redundancy), higher robustness against compression can be achieved. 3.3. Steganalysis Results Wavelet-based steganalysis (WBS) [18], and Feature- based steganalysis (FBS) [19], and Contourlet-based (CBS) [20] methods are used to evaluate the security of ContSteg. In WBS, a Fisher Linear Discriminator (FLD) and in FBS and CBS, a nonlinear Support Vector Ma- chine (SVM) is trained to discriminate between clean and stego-images. 1200 images (600 cover and 600 stego images) from database were chosen randomly for testing, while the remaining 800 images were used for training. This partitioning was repeated ten times, with different random subsets used for training and testing each time. The average of detection accuracy is shown in Table 2. The accuracy is the average of true detection of both stego and clean-images. As can be seen, the detection accuracy is about 50% and the proposed method with payload of approximately 0.05 bits per pixel cannot be reliably detected by the applied steganalyzers. It is shown in [21] that the average embedding capacity of existing steganography methods for grayscale JPEG 34 35 36 37 38 39 40 41 3,000 5,000 8,00012,000 Secret Data Size bit s Average PSNR of Stego-Images (dB) Contourlet Wavelet Figure 5. Comparing the quality of stego-images produced by wavelet-based and contourlet-based steganography methods. Copyright © 2009 SciRes. WSN  H. SAJEDI ET AL. 169 Table 1. Retrieval error rate of hidden data after JPEG compression. Secret Data Size (bits) Quality Factor Retrieval Error Rate (%) 5,000 90 , 70 , 50 10 , 14 , 20 10,000 90 , 70 , 50 13 , 18 , 26 Table 2. Accuracy of WBS, FBS, and CBS steganalysis methods on detection of stego-images produced by ContSteg. Secret Data Size (bits) Steganalysis Method Average Detection Accuracy (%) 5,000 WBS 51 FBS 53 CBS 59 10,000 WBS 53 FBS 54 CBS 63 15,000 WBS 58 FBS 61 CBS 68 images with quality factor of 70 is approximately 0.05 bits per non-zero AC DCT coefficient. For a 512×512 image, 4096 blocks of size 8×8 is existed. Usually 20 AC DCT coefficients are considered non-zero. Therefore, we have 4096×20=81920 non-zero coefficients. Hence, the capacity is 81920×0.05=4096 which is 4096/ (512×512) =0.015 bits per pixel. We see that our pro- posed method has higher embedding capacity. 4. Conclusions Steganography that is a branch of information hiding technology aims to hide a secret data securely in a cover media for transmission. Embedding rate and stego-image quality are two important criteria in evaluating a steg- anography method. In this paper, a new secure and adap- tive steganography is presented which is called ContSteg. It embeds a secret data in contourlet transform coeffi- cients of an image. Since embedding data in non-smooth and edgy regions of the image causes less delectability, these regions of the image are identified in contourlet domain and the secret data is embedded in the corre- sponding coefficients. According to the experimental results, in comparison with wavelet domain approach, the proposed steganography method increases embed- ding rate and image quality of the stego-images by hid- ing the secret data in contourlet coefficients correspond- ing to high frequencies. The results of our experiments show that employing two of powerful steganalyzers on stego-images produced by our method, they could not discriminate between stego and clean-images reliably. In general, ContSteg is a secure steganography method that provides high embedding capacity and high image quality. 5. References [1] C. Liu and S. Liao, “High-performance JPEG steg- anography using complementary embedding strategy,” Pattern Recognition, Vol. 41, pp. 2945–2955, 2008. [2] EzStego, http://www.securityfocus.com/tools/586. [3] A. Westfeld, “F5-a steganographic algorithm: High ca- pacity despite better steganalysis,” Proceeding of 4th In- ternational Workshop on Information Hiding, 2001. [4] N. Provos, “Defending against statistical steganalysis,” Proceeding of 10th USENIX Security Symposium, pp. 323–336, 2001. [5] P. Sallee, “Model-based steganography,” Proceeding of International Workshop on Digital Watermarking, Seoul, Korea, 2003. [6] J. Fridrich, M. Goljan, and D. Soukal, “Perturbed quanti- zation steganography with wet paper codes,” Proceeding of ACM Multimedia Workshop, Germany, 2004. [7] K. Solanki, A. Sarkar, and B. S. Manjunath, “YASS: Yet another steganographic scheme that resists blind stegana- lysis,” Proceeding of 9th International Workshop on In- formation Hiding, June 2007. [8] K. Zhiwei, L. Jing, and H. Yigang, “Steganography based on wavelet transform and modulus function,” Journal of C opyright © 2009 SciRes. WSN  H. SAJEDI ET AL. 170 Systems Engineering and Electronics, Vol. 18, No. 3, pp. 628–632, 2007. [9] J. Fridrich and R. Du, “Secure steganographic methods for palette images,” Proceeding of 2nd International In- formation Hiding Workshop. LNCS, Vol. 1768, pp. 47– 60, 2000. [10] H. Sajedi and M. Jamzad, “Adaptive steganography method based on contourlet transform,” Proceedings of 9th International Conference on Signal Processing (ICSP’08), October 26–29, 2008. [11] M. Do and M. Vetterli, “Contourlets: A directional mul- tiresolution image representation,” Proceedings of ICIP, 2002. [12] N. Kaewkamnerd and K. R. Rao, “Wavelet based image adaptive watermarking scheme,” Electronic Letters, Vol. 36, pp. 312–313, 2000. [13] B. Matalon, M. Elad, and M. Zibulevsky, “Image denois- ing with the contourlet transform,” Proceeding of SPIE Conference Wavelets, 2005. [14] Y. Lu and M. N. Do, “A directional extension for multi- dimensional wavelet transforms,” IP EDICS: 2-WAVP (Wavelets and Multiresolution Processing), 2005. [15] J. Seberry and J. Pieprzyk, “CRYPTOGRAPHY: An introduction to computer security,” Prentice-Hall, New York, 1989. [16] http://www.cs.washington.edu/research/imagedatabase. [17] A. K. Jain, “Fundamentals of digital image processing,” Prentice-Hall, New Jersey, 1989. [18] S. Lyu and H. Farid, “Detecting hidden messages using higher-order statistics and support vector machines,” Proceeding of 5th International Workshop on Information Hiding, 2002. [19] J. Fridrich, “Feature-based steganalysis for JPEG images and its implications for future design of steganographic schemes,” Proceeding of 6th Information Hiding Work- shop, Toronto, 2004. [20] H. Sajedi and M. Jamzad, “A steganalysis method based on contourlet transform coefficients,” Proceeding of 4th International Conference on Intelligent Information Hid- ing and Multimedia Signal Processing, 2008. [21] J. Fridrich, T. Pevný, and J. Kodovský, “Statistically undetectable JPEG steganography: Dead ends, challenges, and opportunities,” MM&Sec, ACM, Dallas, USA, 2007. Copyright © 2009 SciRes. WSN
|