Technology and Investment
Vol.1 No.4(2010), Article ID:3213,10 pages DOI:10.4236/ti.2010.14033
Case Study on Business Risk Management for Software Outsourcing Service Provider with ISM*
1School of Business Administration, South China University of Technology, Guangzhou, China
2Institute of Emerging Industrialization Development South China University of Technology, Guangzhou, China
E-mail: scutwjp@126.com, dandanwan42@126.com, shidelan@163.com
Received September 9, 2010; revised October 10, 2010; accepted October 15, 2010
Keywords: Software Outsourcing, Project Management, Risk Factor, Interpretive Structural Modeling, Empirical Analysis
Abstract
This paper identifies the risks of CN Group which is working at software outsourcing projects between HongKong and Guangdong, discovers the causal relationships among the risk factors, and constructs corresponding risk structure model with Interpretive Structural Modeling. Five original risk factors are identified, including contracts risk, requirements definition and change, lack of communication, political and legal environment differences, and exchange rate fluctuations. Finally, a risk management model of CN Group is put forward and three advices are proposed for software outsourcing business operation: project planning, project requirements, and communication.
1. Introduction
Software outsourcing is a major characteristic of economic globalization, a new form of innovation networks and strategic alliances, and also a strategic instrument for nurturing and promoting enterprises’ core competitiveness. Outsourcing service providers who undertake software outsourcing face both opportunities and challenges [1]. With an increasingly competitive outsourcing market, it has been the industry’s top priority to explore the risk management for China’s software outsourcing business. The widespread failures of software outsourcing projects have attracted scholars to focus on the risks of the software outsourcing project [1]. Kliem & Ralph had discovered six risk factors leading to the failure [2].
However, these studies only implement isolated risk management in limited processes, without comprehensive consideration from the enterprises’ operation level. In this context, issues studied in this thesis include: 1) What risks do software outsourcing enterprises confront? 2) How do software outsourcing enterprises respond to these risks? 3) Have there been appropriate risk management models for software outsourcing enterprises to effectively carry out risk management? 4) How do software outsourcing enterprises guarantee the correct implementation of these risk management models?
There are many risks in the course of risk management of the software outsourcing enterprise, the risk factors contact each other and store each other, forming a multilevel, multi-link network structure. Therefore, the risk management of software outsourcing actually covers the whole process of the software life cycle; the risks can not be seen independently. Interpretive Structural Modeling (ISM) is the most practical technology of the structure modeling, and is most widely used in analyzing software outsourcing risks in the system with many variables, complex relationships and unclear structure. In this paper, we constructed a risk structure model for CN Group which is working software outsourcing projects between HongKong and Guangdong, and then found out some original risks to propose several solutions.
2. Software Risk Management
Literature 3 shows the comparison of 6 risk management models (Table 1). The core of Boehm’s risk management theory is to maintain and update a list of the top ten risks [4]. Software risk management principles of CRM (Continuous Risk Management), include a comprehensive view, positive strategies, open communication environment, integrated management, continuous process, a common goal and coordinative working. CRM model proposed by SEI demands to pay close attention to risk identification and management in all stages of project life cycle [5]. Riskit method can provide systematic risk management processes and technologies of early stage, aimed at completely indicating and managing the causes of risk, the trigger events and their impacts, and assessing risk with reasonable steps. Riskit method provides the detail implementation template to each activity of the risk management [6]. SoftRisk model is proposed by Keshlaf and Hashim. The core of this model is to continuously identify and control risk, and manage risk through updating and maintaining the list of top ten risks which are based on Boehm theory [7]. IEEE risk management standard defines risk management processes during software development life cycle [8]. It systematically describes and manages the risks emerging in product or service life cycle, including the following activities: planning and implementing risk management, managing project risk list, analyzing risk, monitoring risk, handling risk, and evaluating risk management process. Software Risk Management process area is the third level of CMMI [9], which is to identify potential factors that could jeopardize key objectives so that countermeasures can be planned and implemented when necessary to ease the negative impact and eventually realize the organizational goals.
The practice of software risk management involves two primary steps each with three subsidiary steps by Bohem is illustrated in Figure 1 [4].
The first primary step, risk assessment, involves risk identification, risk analysis, and risk prioritization: 1) Risk identification produces lists of the project-specific risk items likely to compromise a project’s success. Typical risk identification techniques include checklists, examination of decision drivers, comparison with experience (assumption analysis), and decomposition. 2) Risk analysis assesses the loss probability and loss magnitude for each identified risk item, and it assesses compound risks in risk item interactions. Typical techniques include performance models, cost models, network analysis, statistical decision analysis, and quality-factor (like reliability, availability, and security) analysis. 3) Risk prioritization produces a ranked ordering of the risk items identified and analyzed. Typical techniques include risk-exposure analysis, risk-reduction leverage analysis (particularly involving cost-benefit analysis), and Delphi or group-consensus techniques.
The second primary step, risk control, involves riskmanagement planning, risk resolution, and risk monitoring: 1) Risk-management planning helps prepare you to address each risk item (for example, via information buying, risk avoidance, risk transfer, or risk reduction), including the coordination of the individual risk-item plans with each other and with the overall project plan. Typical techniques include checklists of risk-resolution techniques, cost benefit analysis, and standard risk management plan outlines, forms, and elements. 2) Risk resolution produces a situation in which the risk items are eliminated or otherwise resolved (for example, risk avoidance via relaxation of requirements). Typical techniques include prototypes, simulations, benchmarks, mission analyses, key-personnel agreements, design-tocost approaches, and incremental development. 3) Risk monitoring involves tracking the project’s progress toward resolving its risk items and taking corrective action where appropriate. Typical techniques include milestone tracking and a top-10 risk-item list that is highlighted at each weekly, monthly, or milestone project review and followed up appropriately with reassessment of the risk item or corrective action.
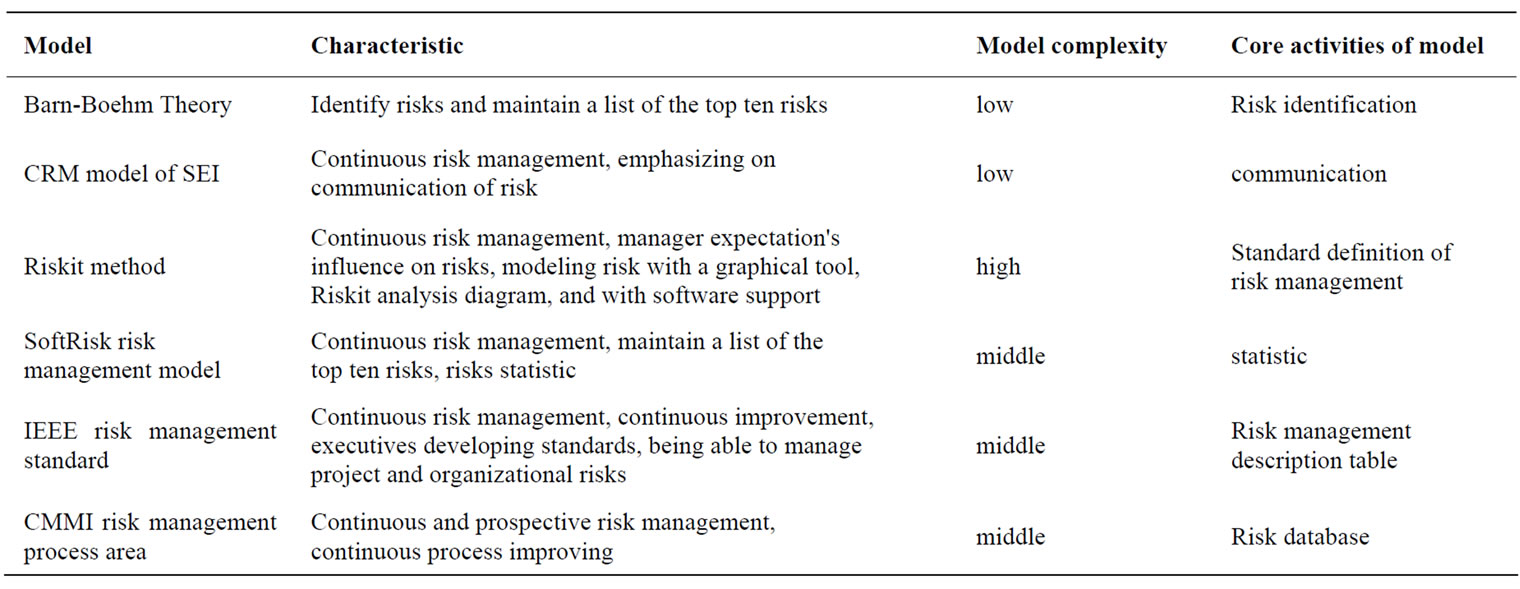
Table 1. Comparison of risk management models.
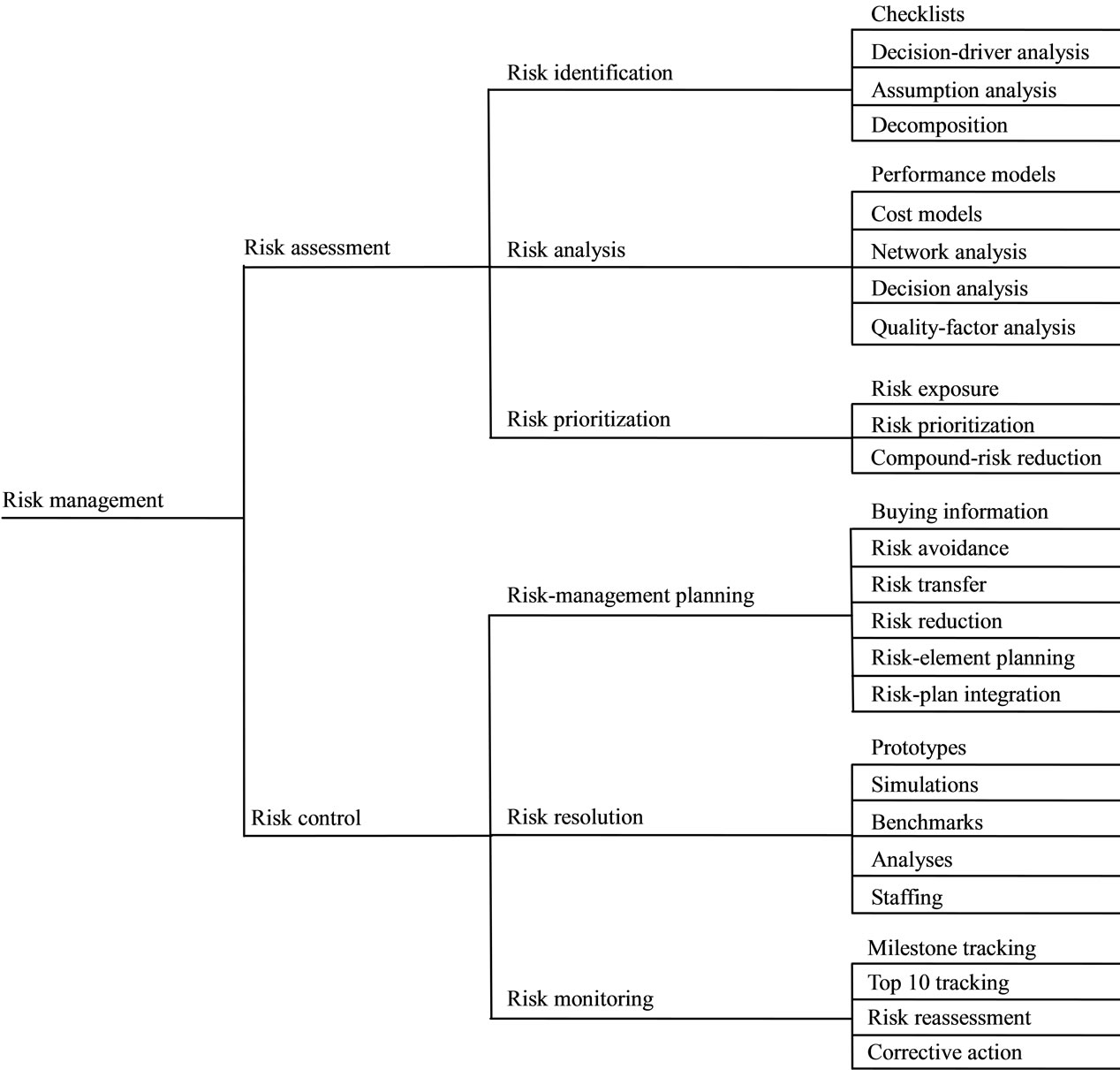
Figure 1. Software risk management steps.
3. Analysis on Risks of CN Group
CN summarized its risks having the following characteristics.
1) The objectivity and universality of risk. As the uncertainty of loss, a considerable part of the risk of CN Group can not completely controlled. These objective risks exist not only in software outsourcing project life cycle, but also in the operations of CN group. Although the CN group wishes to fully understand and control risk, but until now it can only change the conditions of risk existence and occurrence, reduces risk frequency and mitigates risk damage in limited space and time, but cannot eliminate it.
2) The contingency of a particular risk and inevitability of a number of risks. In the software outsourcing projects of CN Group, the occurrence of any specific risk is caused by many risk factors and other factors together, thus it is a random phenomenon. However, some risks can be controlled and forecasted through observation and statistical analysis of substantial risk accident data.
3) The variability of risk. This refers to the various risks changing in terms of quality and quantity in the entire project process. As the project goes on, some risks will be controlled, some will occur and get handled, and at the same time new risks may rise in every stage of the project. Especially in large projects, due to more risk factors, the variability of risk is much more pronounced.
4) The diversity and multi-level of risk. CN Group is a software outsourcing company, and responsible for several large software outsourcing projects. These software outsourcing projects have long life cycle, large-scale, broad scope and numerous risk factors of various types, resulting in that various risks will be confronted in its entire life cycle. Furthermore the intrinsic relationships between risk factors are complex, and cross-impacts of various risk factors between and external factors endow the multilevel risks.
4. Construct Software Outsourcing Risks Structure Model of CN Group with ISM
4.1. Identify the Risks of the Software Outsourcing Project
The major event sequence of ISM is in the following [10]: 1) Theme is selected. 2) Developer is identified. 3) Elements and contextual relation are identified. 4) Leader is identified. 5) ISM program is entered in computer. 6) Adequate computer time is allocated. 7) Facilities are ready. 8) Session plan is complete. 9) Computer contains elements and contextual relation. 10) Session can begin. 11) Element set is edited. 12) Reachable matrix is complete. 13) Total structure is available. 14) Amendments are complete. 15) Final structure is satisfactory.
According to major event sequence of ISM, We organized eight experts to form an ISM panel. Because of the consideration for confidentiality, eight experts all come from CN Group. ISM panel set problems and identified risk factors regularly (every three months). After several discussions, the members of ISM panel reached a consensus. Finally, 21 major risk factors of software outsourcing projects were found out. These risks can be illustrated in Table 2.
4.2. Construct Concept Model and Reachable Matrix
The concept model is constructed according to risk factors. After analysis, we propose a reasonable schedule of the relationships among risk factors of CN Group. It is illustrated in Table 3.
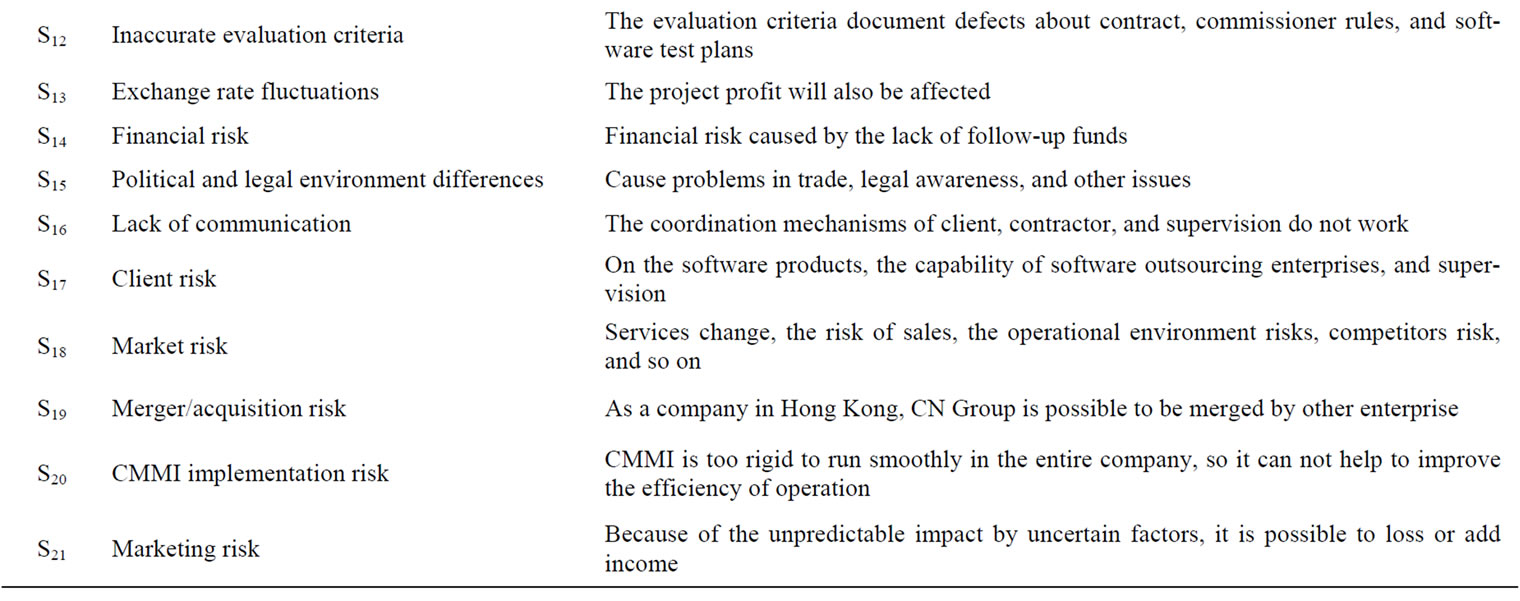
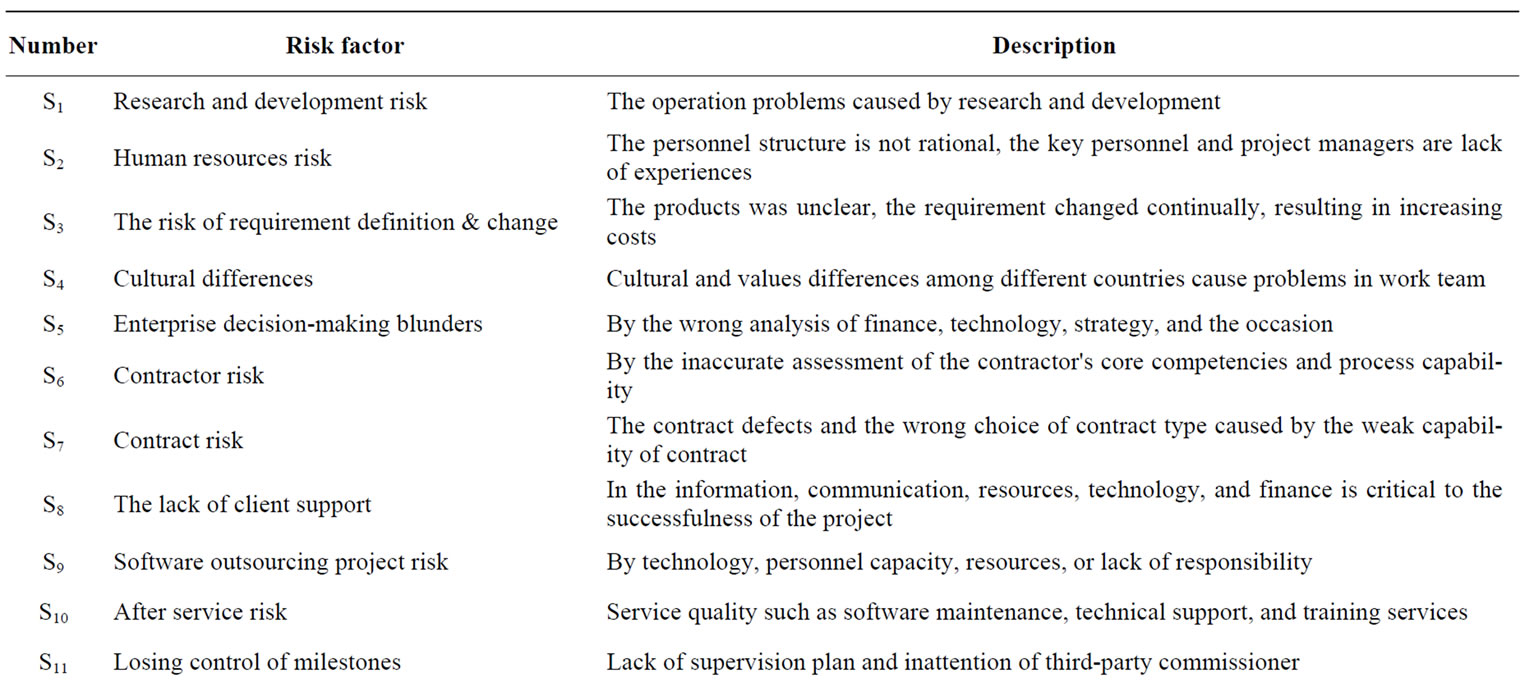
Table 2. Major risks software outsourcing of CN group.

There into: ①V denotes the row factor has effected on the column factor (the row factor result in the column factor); ②A denotes the column factor has effected on the row factor; ③blank denotes the row factor and the column factor are unrelated.
Table 3. Relationship among major risks software outsourcing business of CN group.
4.3. Establish a Re-Order Reachable Matrix After the Class Division
Class division means dividing different risk factors into different levels for the purpose of providing a risk factors structural framework with good hierarchy and causal relationships for risk analysis and risk management.
1) Reachable matrix shows all the direct or indirect impact relationships between different factors. 2) Reachable set R (Si). The reachable set of Si is a set of system elements those can be reached by Si in Reachable matrix or directed graph, denotes as R (Si). 3) Antecedence set A (Si). The antecedence set of Si is a set of system elements those can reach to Si in Reachable matrix or directed graph, denotes as A (Si).
Table 4 is illustrated the first level of Reachable set and antecedence set of risks in CN Group.
Using Boolean algebra operational rules on the adjacency matrix, we can get a Reachable set. Because R(S0) = R(S0)∩A(S0), the highest factors set of the first layer L1 = {S0}. By redlining the corresponding rows and columns, we can get the Reachable set and antecedence set of the second layer. In the same way, the highest factors set of the second layer L2 = {S9, S19, S21}; the highest factors set of the third layer L3 = {S1, S4, S5, S10, S11, S18}; the highest factors set of the fourth layer L4 = {S2, S6, S8, S12, S13, S14, S15, S17, S20}; the factors set of the lowest layer L5 = {S3, S7, S16}. The re-order Reachable matrix is as follows (Figure 2).
4.4. Construct the Structural Model
According to the re-order reachable matrix, we can construct the risk structural model of CN Group. They can be illustrated by Figure 3 (There are 50 pairs of relationships here).
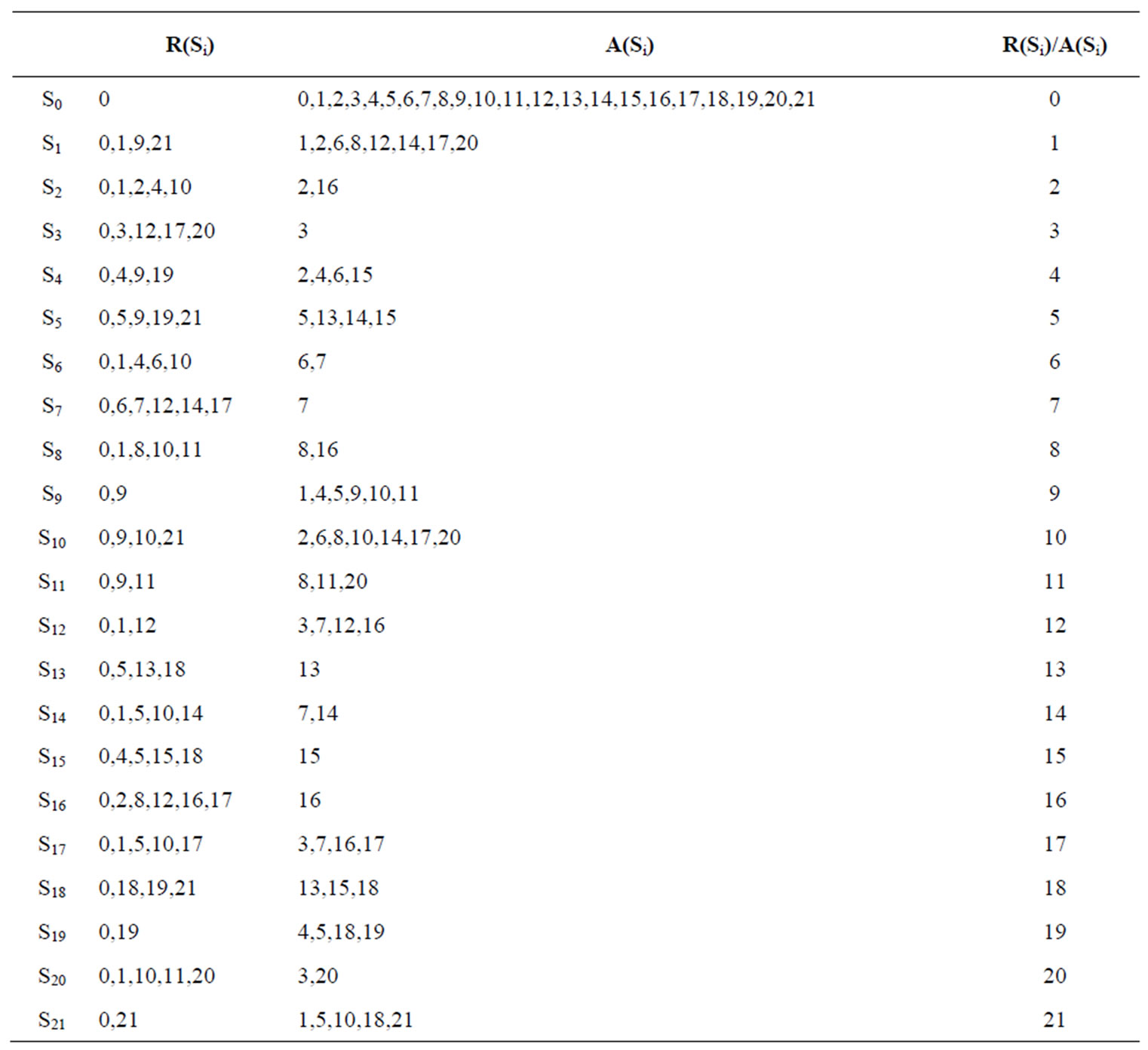
Table 4. The reachable set and antecedence of the first layer.

Figure 2. The re-order reachable matrix R’.
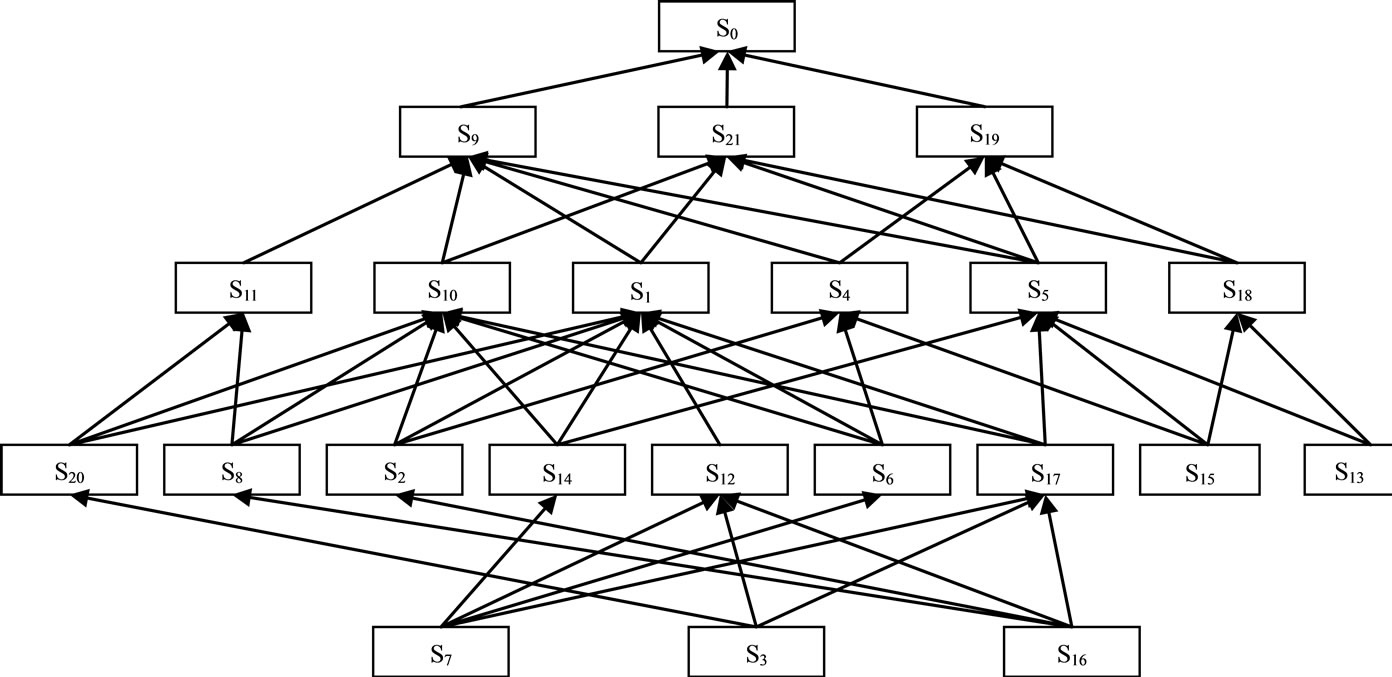
Figure 3. ISM based business risk structural model for CN Group.
It can be seen from Figure 4 that this model is a directed five-level hierarchical structure model, and that the bottom-line arrows indicate low-level factors affecting high-level factors. By replacing risk factors code with the actual risk factors, the interpretative structure model of CN’s software outsourcing business risk is established.
5. Analyze the Interpretive Structural Model
After the analysis, we discover the software outsourcing business risks of CN Group constitute of factors in five level structures (Figure 4).
1) The lowest level constitute of contract risk, lack of communication, and the risk of requirement definition and change. They are the key factors affecting the successfulness of software outsourcing projects; although political and legal environment differences and exchange rate fluctuations are in the fourth layer, they are the bottom of the risks of CN Group; especially, the factors contract risk, lack of communication, and the risk of requirement definition and change occur in the early stages of operation of software outsourcing projects, having significant impact on the successfulness of CN Group’s project.
2) The factors of the second layer is the direct risk factors resulting CN Group to crisis, including software outsourcing project risk, merger/acquisition risk, and marketing risk. Three risks separately belong to the project management, marketing management and enterprise management, but they are significant and correlative closely.
3) The software outsourcing project risk mainly due to losing control of milestones, research and development risk, after service risk, cultural differences, and enterprise decision-making blunders risk. The deeper reasons are CMMI implementation risk, the lack of client support, human resources risk, contract risk, financial risk, inaccurate evaluation criteria, contractor risk, and client risk. The original risks are contract risk, lack of communication, and the risk of requirement definition and change.
4) Marketing risk mainly due to enterprise decision-making blunders risk, market risk, research and development risk, and after service risk. The deeper reasons are financial risk, human resources risk, client risk, political and legal environment differences, and exchange rate fluctuations.
5) Merger/acquisition risk mainly due to cultural differences, enterprise decision-making blunders risk, and market risk.
6. Risk Management Model of CN Group
The existing risk management process in CN Group has included general processes for risk warning, analysis, plan, response and tracking in the outsourcing risk management model (Figure 5).
Risk early warning is the regular or irregular action of software outsourcing enterprises. CN Group needs to appoint a risk warning manager, being solely responsible for the work of risk warning. Risk warning manager reports directly to the CEO.
Risk identification is an attempt to determine risk factors that threat software outsourcing business with a systematic approach. CN Group should start with focusing on the issue that what scope, schedule, cost and quality problems could possibly emerge in the risks they face,
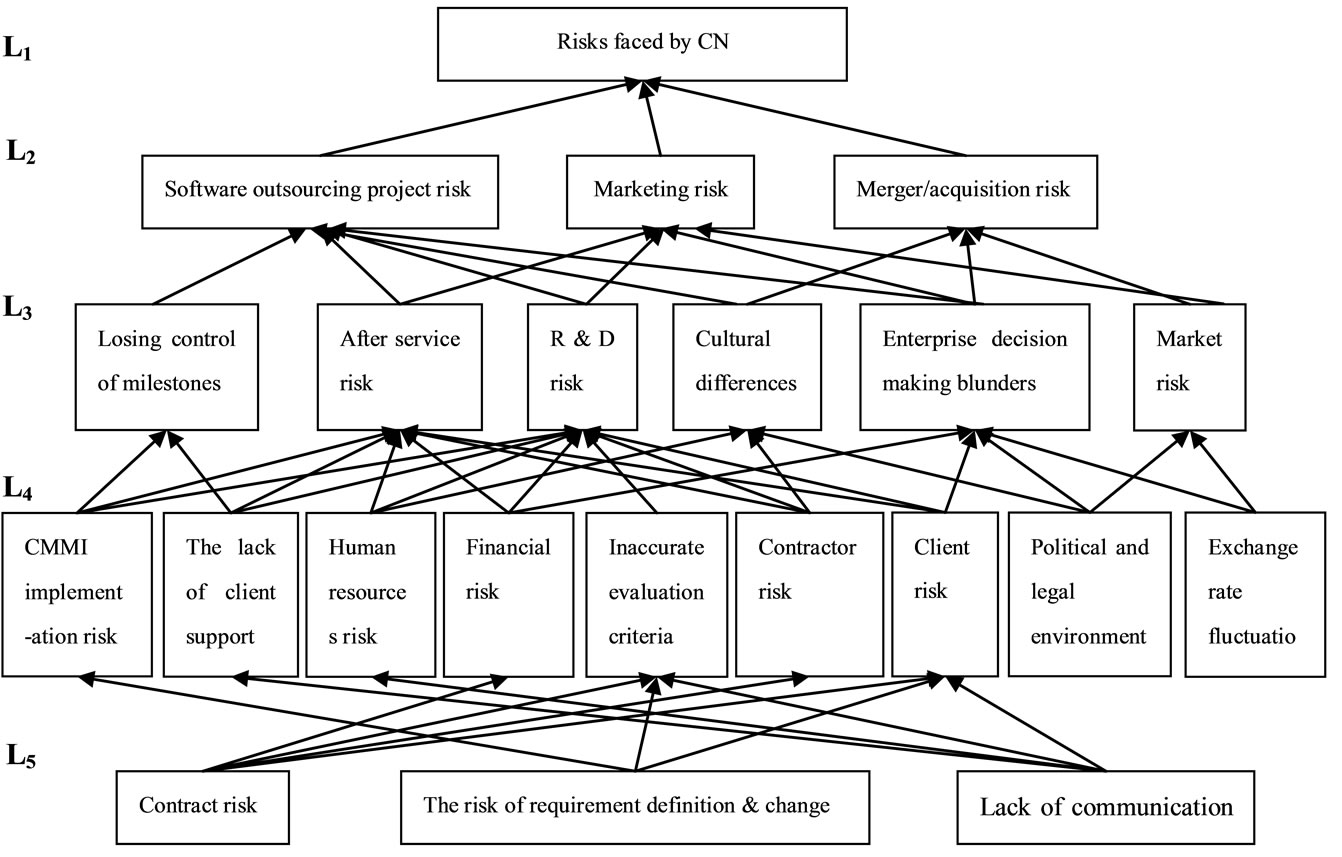
Figure 4. Interpretive structure model of CN’s software outsourcing business risk.
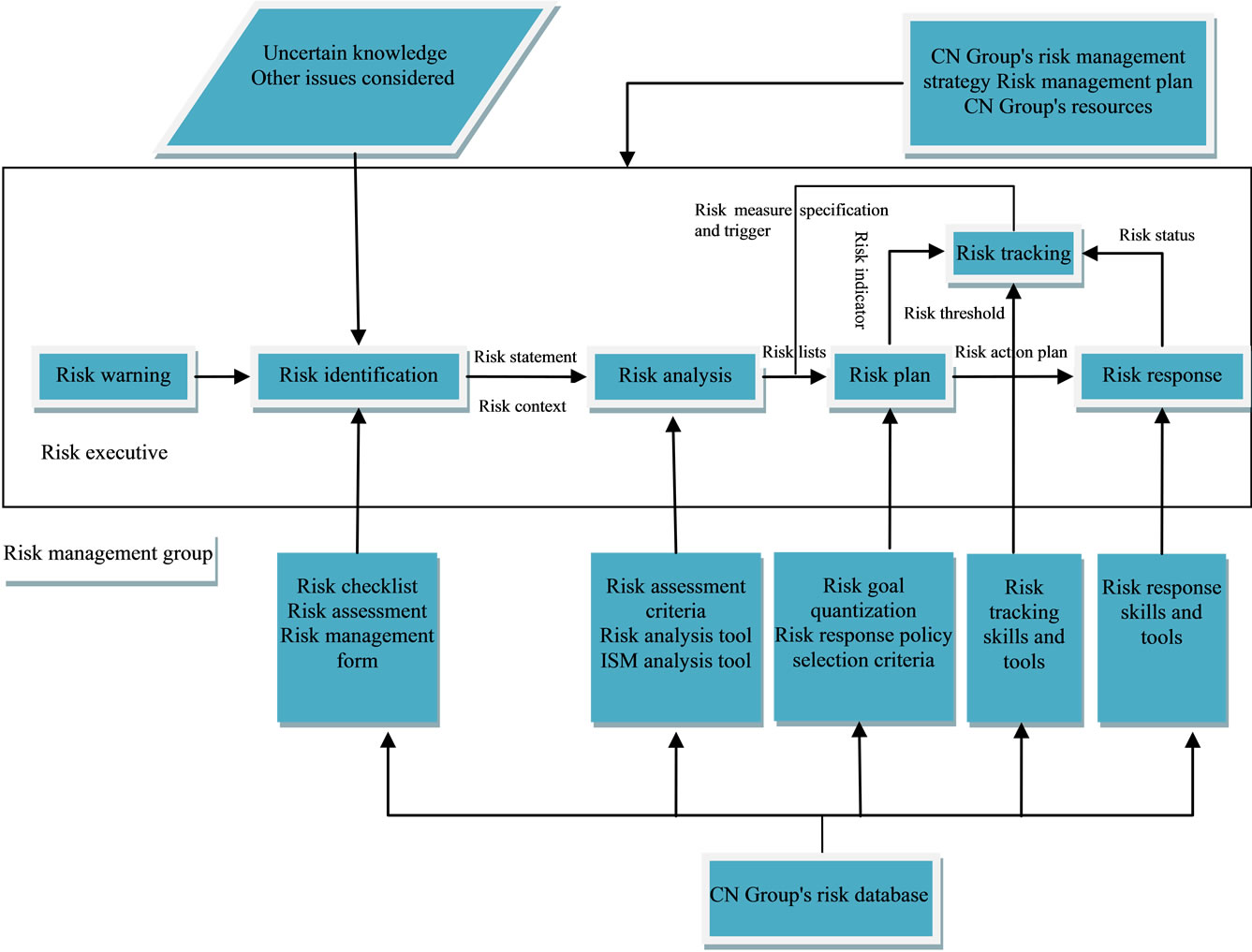
Figure 5. Risk Management of CN Group.
mainly to discuss and list the possible risks.
Risk analysis is divided into qualitative risk analysis and quantitative risk analysis. Qualitative risk analysis is a process to assess the impact of the identified risks and their likelihood. For example, we can clearly find out the causal relationship of risks involved in software outsourcing process through structural analysis on the risk of CN group with ISM model. Thus we can determine the root of the important risks from the complex risk signs.
Risk action plan should contain the following elements: responsibility, resources, time, activities, response measures, results and person in charge.
CN Group can choose the following types of risk-response strategies: 1) controlling risk. 2) accepting risk. 3) transferring risk. 4) avoiding risk. It should adopt different response strategies according to different conditions, different environment or different issues of software outsourcing process.
The role of risk tracking is to monitor the status of the risk and check the validity of risk counter measures and whether tracking mechanisms are in operation, continue to identify new risks and develop strategies to provide the basis for active risk control.
7. The Countermeasures for the Risk Management of Software Outsourcing Enterprises
We advise the enterprises working at software outsourcing projects between Guangdong and Hong Kong should pay attention to the following aspects for managing risks:
1) Project requirement. A clear project requirement is the fundamental of the right project planning and implementation, so the contractor should gain some insight into the client’s requirement before the project implementation, and discuss uncertain requirement with client. For the changes in the process of implementation, all participants should reach a consensus in the end. In requirement analysis, the contractor should carefully analyze the client’s requirement, and then collect the client’s complete requirement through business modeling, conversation, questionnaires, and requirement meeting.
2) Project planning. Prior to the implementation of the project, the client usually puts forward the draft of the implementation plan of the project, project managers should confer with client on the integrity and feasibility of the project plan, project process, workload, resource allocation and project milestones.
3) Communication. The implementation of the software outsourcing project is a cooperation process of both. It is necessary to establish an effective communication channel to ensure the outsourcing business to be carried out successfully. The contractor must confirm with client on which communication tools (telephone, fax, e-mail, online conversation, etc.) should be used under given circumstance, then determine format (for example, weekly format) and form of communication (for example, on spot, telephone, both project linkman).
8. Conclusions
This paper identifies the software outsourcing business risks of CN Group, and discovers the causal relationships among risk factors, and constructs corresponding risk structure model with ISM. Five original risk factors are found, including contracts risk, the risk of requirements definition and change, lack of communication, political and legal environment differences, and exchange rate fluctuations. Finally, risk management model is put forward for CN Group, and three advices are proposed: project requirement, project planning and communication to help software outsourcing providers between Guangdong and HongKong to find effective ways for software outsourcing project’s success.
9. Acknowledgements
Thank for helpful discussion with Mr. Kevin Kuang, Dr. CK Wong, Mr. Chan Zening, Mr. An Yuguo, Mrs Huang Huajie and Mrs Hou Jianhua etc.
10. References
[1] Y. Qin, W. J. Li and C. D. Pan, “The Development of Services Outsourcing in Multinational Companies and China’s Countermeasures,” Science and Technology Progress and Policy, Vol. 23, No. 4, April 2006, pp. 131- 132.
[2] R. Kliem, “Managing the Risks of Offshore IT Development Project,” Information Systems Management, Vol. 21, No. 3, March 2004, pp. 21-27.
[3] M. Z. Mao and X. W. Ge, “Analysis and Research on Risk and Management,” Science and Technology Management Research, Vol. 24, No. 6, June 2005, pp. 148- 151.
[4] B. W. Boehm, “Software Risk Management: Principles and Practices,” IEEE Software, Vol. 8, No. 1, August 1991, pp. 32-41.
[5] V. Scoy and L. Roger, “Software Development Risk: Opportunity, Not Problem,” Technical Report, CMU/ SEI-92-TR-30, September 1992.
[6] J. Kontio, “Risk Management in Software Development: A Technology Overview and the Riskit Method,” The Proceedings of ICSE, Los Angles, May 1999, pp. 679- 680.
[7] A. A. Keshlaf and K. Hashim, “A Model and Prototype Tool to Manage Software Risks,” Proceedings of the First Asia–Pacific Conference on Quality Software, October 2000, pp. 297-305.
[8] “IEEE Standard for Software Life Cycle Processes-Risk Management,” IEEE Standard, Vol. 1504, 2001, pp. 1- 24.
[9] CMMI Product Team, “Capability Maturity Model Integration V1. 1 for Software Engineering,” CMU/SEI, August 2002.
[10] J. N. Warfield, “The Mathematics of Structure,” AJAR, Publishing Company, 2003.
NOTES
*This research was supported by Key Project of Guangdong Province Education Office (06JDXM63002), NSF of China (70471091), and QualiPSo (ISTFP6-IP-034763)

