Int'l J. of Communications, Network and System Sciences
Vol.6 No.5(2013), Article ID:31336,9 pages DOI:10.4236/ijcns.2013.65028
Advanced Border Intrusion Detection and Surveillance Using Wireless Sensor Network Technology
Computer Engineering Department, College of Computing and Information Systems, Makkah, KSA
Email: eafelemban@uqu.edu.sa
Copyright © 2013 Emad Felemban. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Received February 14, 2013; revised March 14, 2013; accepted April 14, 2013
Keywords: Wireless Sensor Network; Intrusion Detection Border Surveillance; Perimeter Surveillance; Remote Monitoring
ABSTRACT
Wireless Sensor Network (WSN) has been emerging in the last decade as a powerful tool for connecting physical and digital world. WSN has been used in many applications such habitat monitoring, building monitoring, smart grid and pipeline monitoring. In addition, few researchers have been experimenting with WSN in many mission-critical applications such as military applications. This paper surveys the literature for experimenting work done in border surveillance and intrusion detection using the technology of WSN. The potential benefits of using WSN in border surveillance are huge; however, up to our knowledge very few attempts of solving many critical issues about this application could be found in the literature.
1. Introduction
Wireless Sensor Network (WSN) has been emerging in the last decade as a powerful tool for connecting the physical and digital worlds. The great interest of WSN motivated hundreds of applications in many domains, such as healthcare, emergency responses, intelligent traffic control, and military applications. A wireless sensor network consists of a large number of unattended tiny devices equipped with different sensors to perform certain tasks [1,2]. They can be used in challenging places where it is inconvenient for human to be present. The sensors on the devices extract physical information from the environment, such as temperature through a temperature sensor, pressure through a barometer, noise through a microphone, and even an image through a camera or thermal camera. The collected data then are sent over to the control command for further processing.
There has been a great interest to utilize WSN for military applications and especially in border protection [3,4]. To reach its full proposed functionality, researchers of WSN used in border protection have to solve many interesting challenges, such as energy efficiency [5,6], communication and hardware reliability and security issues [7]. In this paper, we will present the state-of-the-art technology and deployment prototypes of WSN used in border surveillance and intrusions detection through surveying the literature for the current deployments and real-life experimentations. Also, we will list the requirements of such mission-critical application’s common challenges and possible solutions to overcome them. Very few attempts have been made to tackle this application, which opens the opportunity wide to the researchers to pursue research in this area.
The paper is organized as follows: Section 2 gives a brief background on the concept of wireless sensor networking and its applications. Section 3 lists the current projects and deployments of WSN in border protection and surveillance. Section 4 lists the challenges and research opportunities of WSN in the border surveillance field. Finally, Section 5 concludes the paper.
2. Background
One of the key advantages of wireless sensor networks (WSN) is their ability to bridge the gap between the physical and logical worlds, by gathering certain useful information from the physical world and communicating that information to more powerful logical devices that can process it. WSN will eventually eliminate the need for human intervention in many information gathering and monitoring applications, especially in confined or dangerous spaces.
The low-cost and small size features of WSN will enable the deployment of hundreds of nodes in any field of interest. Such huge density allows more dense collection of data in spatial and temporal domains. Sensor nodes contains of three main parts: 1) Processing unit; 2) RF transceiver; and 3) Energy source. Multiple sensor nodes self-form themselves to form a network to exchange information and deliver data to a common node called the sink node.
WSN has been applied in many applications [8], such as habitat monitoring [9], Point of Interest Building monitoring [10], pipeline monitoring [11], smart agriculture [12], and smart electrical grid [13]. Researchers, also, have extended the concept of land WSN into marine sensor network [14,15]. Because RF signals do not work under water, acoustic signals are used for communication. Marine wireless sensor networks offer an unmatched option to a wide range of different domains, such as monitoring coral reefs, fish habitats, and oil leaks from offshore facilities.
3. WSN in Border Surveillance
The role of WSN in border surveillance, as in most WSN applications, focuses on information gathering from various types of sensors, such as seismic, camera, thermal camera, and motion detectors. Some advanced WSN process these raw data and send an abstracted alarm or aggregated data to the command center, which, in turn, takes the appropriate defense action. Many researchers from different organizations have suggested solutions for border surveillance problems. In this section, we will survey the literature to list the projects in this regards. A summary of all surveyed literature is provided in Table 1.
3.1. Stealth Detection of Mobile Targets [16]
Researchers at the University of Virginia and Carnegie-Mellon University have developed an energy-efficient WSN system for detecting moving vehicles through a passage line in a stealthy manner. Figure 1 shows a picture of the deployment field and a diagram about the setup. The authors deployed 70 MICA2 sensor nodes running Tiny OS along a 280-feet-long perimeter. The sensor nodes were equipped with a magnetometer, as well as acoustic and photo sensors. Stealth capabilities were achieved by minimizing RF transmission and exposure to minimal.
To achieve its goal, the proposed system needs localization and time synchronization modules. In this project, localization is done through simple static configuration, assuming that the nodes’ locations are known priori. The time of all nodes is synchronized with respect to the base station.
The key performance measurement of the deployment is the Degree Of Aggregation (DOA) representing the sensitivity of the system. DOA is defined as “the minimum number of reports about an event that a leader of a group waits to receive from its group members, before reporting the event’s location to the base station”. The DOA could be dynamically configured for a performance evaluation. As the DOA increases, the number of tracking reports and false alarm decreases; however, the reporting time increases. Therefore, an optimization problem would be how to select the optimal DOA to achieve certain latency and minimize the number of reports and false alarms.
3.2. Evaders Detection with the Help of WSN [17]
Researchers the University of California at Berkeley proposed to deploy WSN to help pursuers detect and track evaders. The concept is based on a Pursuer-Evaders Game (PEG), wherein two teams, Pursuers and Evaders, compete. The WSN is used to locate enemy units and direct

Table 1. A summary of experimental setup of surveyed literature.

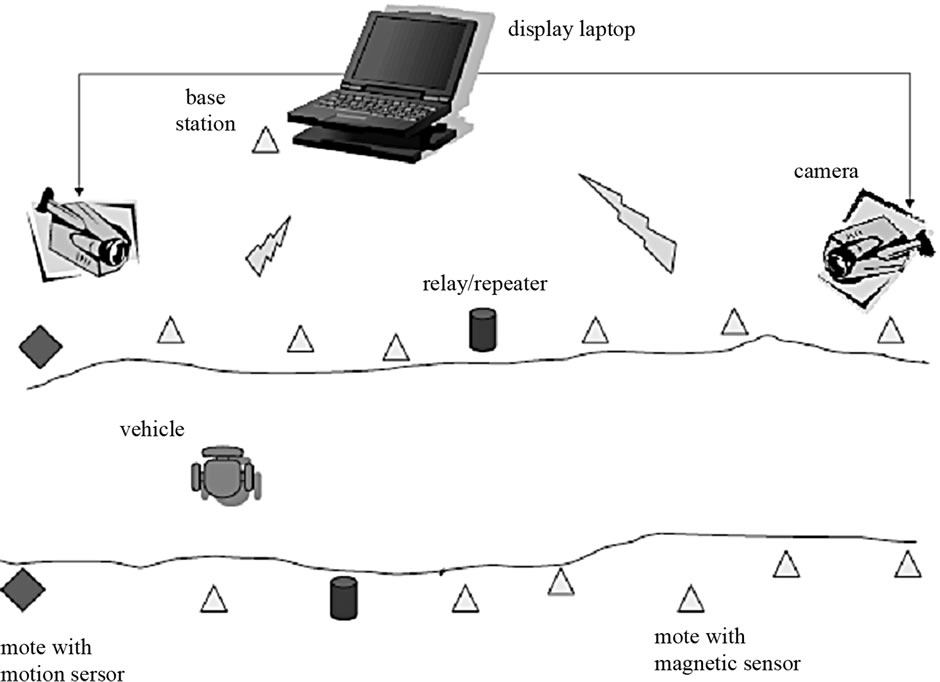
Figure 1. Actual deployment in the test field and a high level diagram of the topology [16].
pursuer team members to catch them. All game units and actions are done in a distributed manner with no central command.
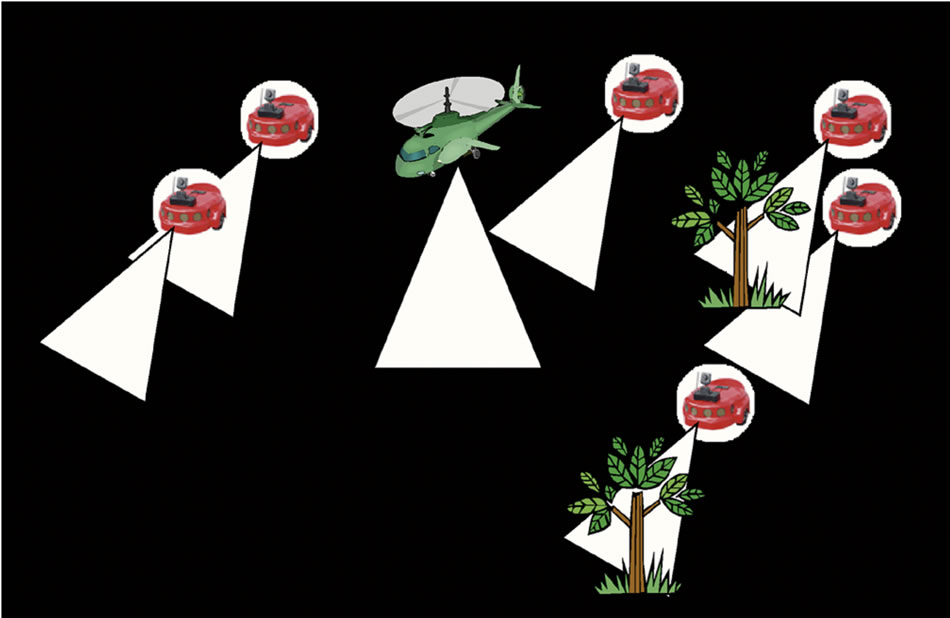
The use of a deployed WSN greatly improved the overall performance of a PEG. Pursuers have a relatively small detection range. They employ limited capability sensing techniques, such as computer vision or ultrasonic sensing; however, with the help of WSN, complete visibility of the field and communication over a long radius becomes possible. Figure 2(a) shows the visibility capability to pursuers in a traditional PEG, while Figure 2(b) shows the enhancements of visibility with the usage of WSN.
The authors have deployed a miniature test bed with 25 motes running Tiny OS and a remote controlled car. They assumed that the nodes are time synchronized and
 (a)
(a)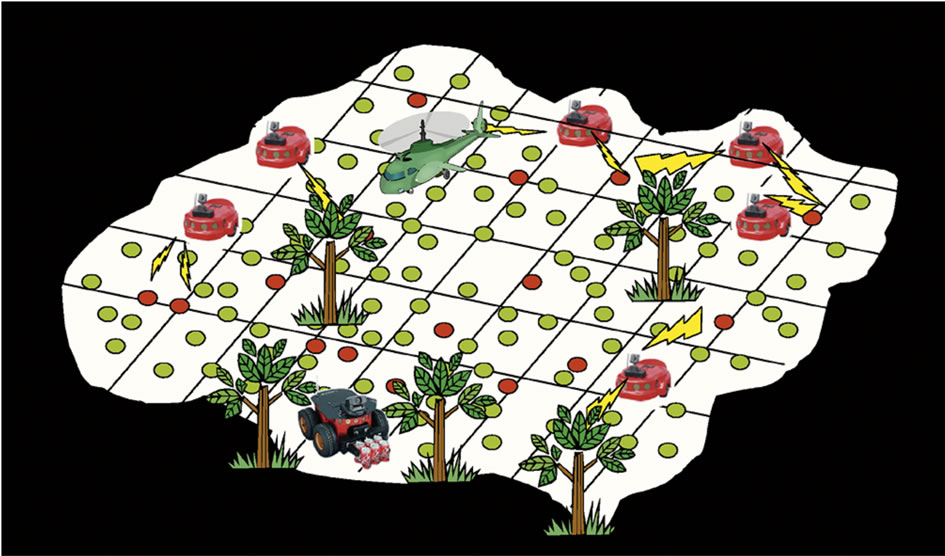 (b)
(b)
Figure 2. (a) What pursuers really see a PEG; (b) WSN increase visibility to pursuers.
that the location is provided to simplify the experiments.
3.3. Line in the Sand [18,19]
Ohio State University researchers have deployed 90 sensor motes with metal object detection capabilities. The objective of the project is to detect and classify moving metallic objects, such as armed vehicles and tanks. They used a combination of magnetometer and micro-power impulse radar sensors. The sensor nodes self-form into a network, and once an object passes through the network, nodes collaborate together to classify the passing object as a metallic object or nonmetallic object. Figure 3 shows

Figure 3. An enclosed mote used in Line in the Sand Project.
a sample enclosed mote used in the project.
The authors considered a surveillance scenario of breaching a perimeter or within a region. The system should provide target detection, classification, and tracking for moving metallic and nonmetallic objects. The concept used in this project is the “influence field,” which can be defined as the number of sensors that hear an object. Moreover, the proposed system tries to capture the shape of the influence for detection, classification, and tracking.
The authors required accurate time synchronization with no difference more than 5 ms at any time. Nodes are synchronized with the help of periodic time values sent by a distinguished node. Routing and localization is done by a simple algorithm called Logical Grid Routing Protocol. For implementation, the authors used 90 MICA motes equipped with magnetic sensor nodes packaged in a sealed enclosure, as shown in Figure 3 arranged in 1500 square feet space.
3.4. Border Sense [20]
Researchers from Georgia Tech, King Saud University, and University of Nebraska have proposed a hybrid approach to achieve coherent border patrol applications. Combining multimedia wireless sensor network, ground sensor networks with different sensing capabilities, underground sensor networks, and mobile sensor networks, Border Sense provides several advantages compared with the traditional WSN border surveillance techniques mentioned above. Figure 4 shows a simplified diagram of the suggested framework with all different sensing capabilities. New and challenging research issues appear as a result of this hybrid architecture, such as coordination between all nodes tracking a single object and unified data framework for exchanging data.
3.5. Marine Surveillance Using Underwater/ Wireless Sensor Networks
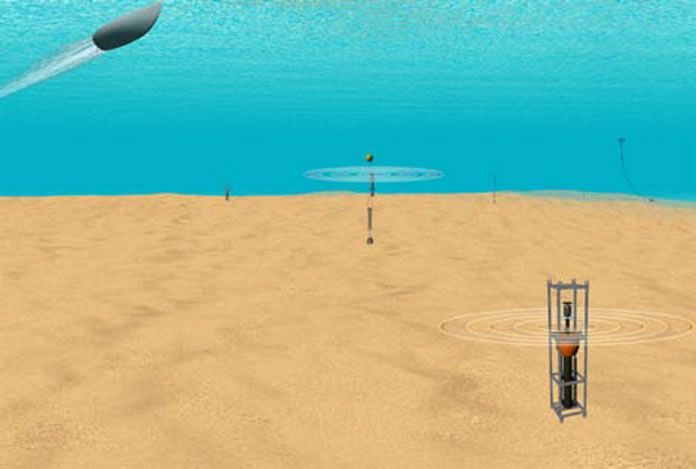
The same application of border surveillance of ground sensor networks can be applied in marine surveillance and marine border protection. In [15], the researchers have demonstrated an underwater surveillance system to detect enemy watercraft by deploying acoustic sensor nodes in shallow water as shown in Figure 5.
Some challenges of underwater sensor networks include slow bandwidth, noisy channel, unreliable links, and lack of energy efficiency.
In [21], the authors proposed innovative ship intrusion detection with wireless sensor networks near a harbor facility. The solution depends on exploiting the V-Shaped wave generated by ship movement on the water surface. They have used three-axis accelerometer sensors with iMote2 on buoys on the sea surface. Figure 6 shows the real deployment.
The deployment uses a grid topology with predefined locations. Sensor nodes were time synchronized before deployment. Accelerometers are used to measure the movements of buoys during waves; these readings are then elaborated to detect passing ships and their speeds. With additional signal and computational processing, nodes can detect the movements of ships around their deployments.
3.6. WSN and Neural Networks for Border Protection [22]
The researchers from New Mexico Tech [22] proposed the usage of artificial neural networks along with WSN for border detection. The key idea of using ANN is to discover patterns that describe an intrusion activity and train the ANN to discover them. The proposed system uses a set of 32 MicaZ sensor nodes equipped with microphones and light sensors collected at the base station. The nodes were distributed along a perimeter to detect single and group intrusion.
The experimental results show that when using both light and sound sensors, the networks were able to detect intrusion in very limited time with higher probability.
3.7. FleGSens: A Wireless Sensor Network for Border Surveillance [23]
Researchers in Germany [23] developed a sensor network prototype consisting of 200 wireless sensor nodes
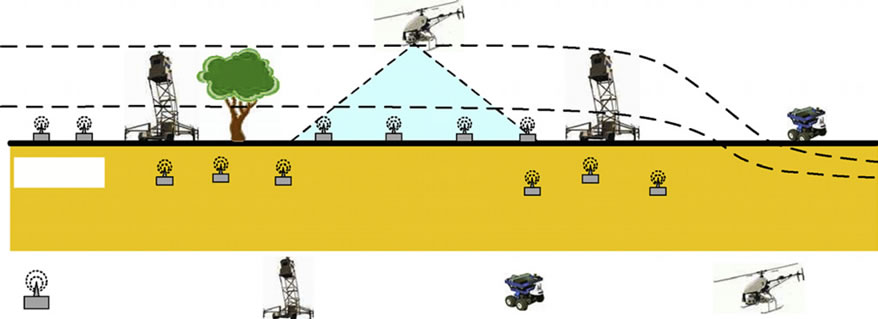
Figure 4. Hybrid combination of multimedia, ground, mobile, and underground sensors for border patrol.
 (a)
(a) (b)
(b)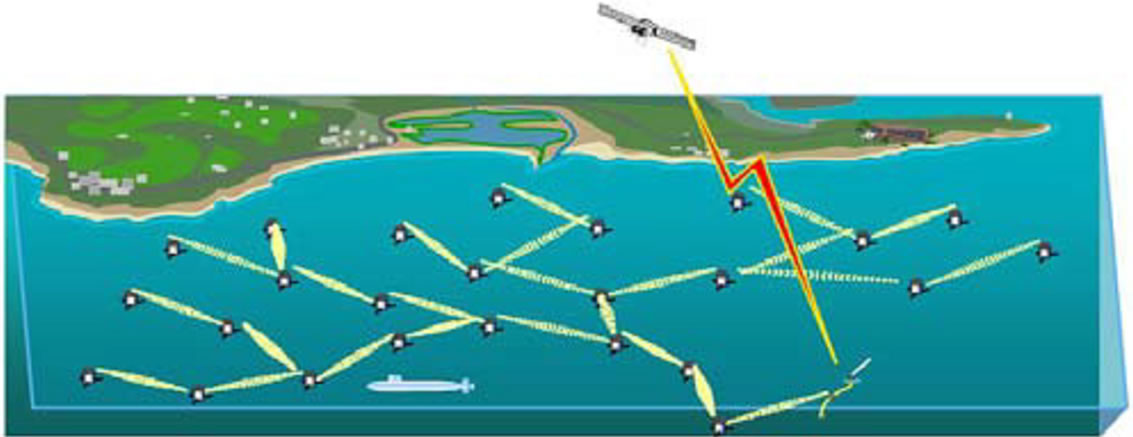 (c)
(c)
Figure 5. (a) A simplified diagram of the underwater sensor network to detect enemy water craft; (b) A detailed diagram of an underwater acoustic sensor node; (c) An overview of the whole underwater acoustic sensor network.

Figure 6. Experimental Sensor network deployment for detecting ship movements [21].
called iSense, which was equipped with Passive InfraRed (PIR) sensors covering a 500 m-long land strip. The objective is to ensure the integrity and authenticity of generated alarms and availability when intruders are present.
Two protocols were developed in this work. The first one is the trespasser detection protocol, which utilizes the PIR sensors to detect movements within the strip space covered. To ensure accurate detection, local PIR signals are grouped and verified before the network is flooded with the messages. The second protocol is the node failure detection protocol, which ensures the integrity of the sensor network, avoiding any breach in the coverage. This is done by selecting a random number of nodes called buddies to listen to other nodes’ heartbeats.
4. Challenges, Requirements and Research Problems
WSN has many challenging features that should be accounted for while designing the desired applications, such as low processing power, low memory storage, low bandwidth, and battery life and communication reliability. These challenges are magnified when WSN is used in mission-critical applications, such as in border surveillance. The following subsections list and discuss the main challenges facing the adoption of WSN in missioncritical applications, such as border surveillance.
4.1. Energy Efficiency
Surveillance missions usually last for an extended period of time. Due to the criticality of the mission, manual replenishing of batteries might not be practical or possible. Thus, an optimized and energy-aware operation should be considered in designing such applications, which can extend the lifetime of the sensor devices and the network in general.
The usage of directional antennas in wireless communication offers many advantages, such as increasing communication range and reducing communication energy consumption. However, the usage of directional antennas with sensor network requires a very intelligent and complicated network stack [24].
In addition, researchers are now heavily investigating energy harvesting with sensor nodes. Researchers in [25] have developed a prototype of a solar-powered sensor nodes. A big question would big how can we utilize those technologies to extend the life of a mission-critical sensor network?
4.2. Stealthness and Security
It is important for a border surveillance system to have a very low probability of being detected, which will affect the success probability of the mission. Moreover, any transmitted and stored information should be encrypted, secured, and protected against interception from enemy communication devices.
There is a fundamental tradeoff between security level and energy consumption. In addition, some techniques to increase stealthness might suggest reducing communication energy and bandwidth.
The importance of providing integrity and security service for the border monitoring network has been firstly introduced in [23]. However, more research should be done to tackle many issues, such as providing security for different topologies and different kinds of sensor networks.
4.3. Accuracy
False alarms will render the surveillance mission into failure. Thus, the accuracy of detection, tracking, and classification of trespassing objects is very important. Hence, methods of aggregate alarms and in-network processing can be used to minimize false alarms. Moreover, as mentioned before, the integrity of the network is very important in reducing the false alarms and increasing the accuracy of the whole system.
4.4. Quality of Service
Timeliness and reliability of detecting the intrusion is another important factor of successful surveillance missions. QoS provisioning on communication should be applied when an intrusion alarm is issued [26]. However, some networks, especially underwater sensor networks, cannot utilize the same quality of service measurements and protocols due to the nature of the application.
4.5. Quality of Coverage
Providing the full coverage of a surveillance field is a very important aspect of the success of the surveillance mission. Providing a full coverage while minimizing the cost has been an active area of research in the operational research field. In order to reduce coverage overlap between sensors, optimization methods should be used to select the best placement of the sensor nodes in the field [27-29]. J. He and H. Shi [30] developed a distributed algorithm to optimize the location of sensor nodes along a barrier to minimize the cost of the full coverage. In [31], the authors examined how to reposition a mobile sensor network efficiently within a specified region to recover a security hole and prevent intruders from exploiting this hole. Yang and Qiao proposed a multi-round approach to deploy sensor nodes to guarantee barrier coverage [32].
5. Conclusion
WSN is an emerging wireless technology that is used in many applications for collecting information from a field of interest. Two of the promising application spans are the border surveillance and intrusion detection applications. The main advantage of using WSN in such applications is the high spatial and temporal data resolution results from deploying hundreds of low-cost sensor nodes along borders. This paper presents a literature survey of current experimentation and deployment research work done in this application area. In addition, we have listed the technical requirements of the surveillance applications and some challenging aspects of using WSN in mission-critical applications, such as border surveillance. To our knowledge, there are very few experimentations and real deployments of such applications.
REFERENCES
- I. Akyildiz, W. Su, et al., “A Survey on Sensor Networks,” IEEE Communications Magazine, Vol. 40, No. 8, 2002, pp. 102-114. doi:10.1109/MCOM.2002.1024422
- M. Vieira, C. Coelho, et al., “A Survey on Wireless Sensor Network Devices,” IEEE Conference on Emerging Technologies and Factory Automation, Lisbon, 16-19 September 2003, pp. 537-544.
- H. Luo, K. Wu, Z. Guo, et al., “Ship Detection with Wireless Sensor Networks,” IEEE Transaction on Parallel and Distributed Systems, 2011.
- B. Essendorfer, E. Monari and H. Wanning, “An Integerated System for Border Surveillance,” IEEE Fourth International Conference on Systems (ICONS 09), Gosier, 1-6 March 2009.
- V. Thattil and N. Vasantha. “Energy Efficient Approach to Intruder Detection in Militarily Sensitive Border Using Wireless Sensor Networks,” IEEE Conference on Electronics Computer Technology, 2011.
- D. Yuping, H. Chang, Z. Zou and S. Tang, “Energy Aware Routing Algorithm for WSN Applications in Border Surveillance,” 2010 IEEE International Conference on Technologies for Homeland Security, Wltham, 8-10 November 2010, pp. 530-535.
- E. Onur, C. Ersoy, H. Delic and L. Skaru, “Surveillance Wireless Sensor Networks: Deployment Quality Analysis,” IEEE Network, Vol. 21, No. 6, 2007, pp. 48-53. doi:10.1109/MNET.2007.4395110
- T. Arampatzis, J. Lygeros and S. Manesis, “A Survey of Applications of Wireless Sensors and Wireless Sensor Networks,” 13th Mediterranean Conference on Control and Automation Limassol, Cyprus, 27-29 June 2005, pp. 889-895.
- F. M. Sabri, “Wireless Sensor Networks for Swift Bird Farms Monitoring,” International Conference on UltraModern Telecommunications & Workshops, St. Petersburg, 12-14 October 2009.
- D. Abruzzese, M. Angelaccio, B. Buttarazzi, R. Giuliano, L. Miccoli and A. Vari, “Long Life Monitoring of Historical Monuments via Wireless Sensors Network,” 6th International Symposium on Wireless Communication Systems, Tuscany, 7-10 September 2009.
- I. Stoianov, L. Nachman and S. Madden, “PIPENET: A Wireless Sensor Network for Pipeline Monitoring,” The 6th International Conference on Information Processing in Sensor Networks (IPSN’07), Cambridge, 25-27 April 2007.
- T. Wark, P. Corke, P. Sikka, L. Klingbeil, Y. Guo, C. Crossman, P. Valencia, D. Swain and G. Bishop-Hurley, “Transforming Agriculture through Pervasive Wireless Sensor Networks,” IEEE Pervasive Computing, White Plains, 19-23 March 2007. doi:10.1109/MPRV.2007.47
- V. Gungor, L. Bin and G. Hancke, “Opportunities and Challenges of Wireless Sensor Networks in Smart Grid,” IEEE Transactions on Industrial Electronics, Vol. 57, No. 10, 2010, pp. 3557-3564. doi:10.1109/TIE.2009.2039455
- J. Rice, et al., “Maritime Surveillance in the Intracoastal Waterway Using Networked Underwater Acoustic Sensors Integrated with a Regional Command Center,” 2010 International Waterside Security Conference (WSS), Carrara, 3-5 November 2010, pp. 1-6.
- A. Mahdy, “Marine Wireless Sensor Networks: Challenges and Applications,” 7th International Conference on Networking, Cancun, 13-18 April 2008, pp. 530-535.
- T. He, S. Krishnamurthy, J. A. Stankovic, T. Abdelzaher, L. Luo, R. Stoleru, T. Yan, L. Gu, J. Hui and B. Krogh, “An Energy-Efficient Surveillance System Using Wireless Sensor Networks,” 2nd International Conference on Mobile Systems, Applications and Services, Boston, 6-9 June 2004.
- B. Sinopoli, C. Sharp, L. Schenato, S. Shaffert and Sh. S. Sastry, “Distributed Control Applications Within Sensor Networks,” Proceeding of the IEEE, August 2003.
- http://www.cse.ohiostate.edu/siefast/nest/nest_webpage/ALineInTheSand.html
- A. Arora, et al., “A Line in the Sand: A Wireless Sensor Network for Target Detection, Classification, and Tracking,” Journal Computer Networks, Vol. 46, No. 5, 2004.
- Z. Sun, et al., “BorderSense: Border Patrol through Advanced Wireless Sensor Networks,” Ad Hoc Networks, 2011, pp. 468-477.
- H. Luo, et al., “Ship Detection with Wireless Sensor Networks,” IEEE Transactions on Parallel and Distributed Systems, Vol. 23, No. 7, 2012, pp. 1336-1343. doi:10.1109/TPDS.2011.274
- A. Mishra, K. Sudan and H. Soliman, “Detecting Border Intrusion Using Wireless Sensor Network and Artificial Neural Network,” IEEE DCOSS 2010, Santa Barbara, 21- 23 June 2010.
- P. Rothenpieler, D. Kruger, D. Pfisterer, S. Fischer, D. Dudek, C. Haas, A. Kuntz and M. Zitterbart, “Flegsens: Secure Area Monitoring Using Wireless Sensor Networks,” Proceedings of the 4th Safety and Security Systems in Europe, 2009.
- E. Felemban, S. Vural, et al., “SAMAC: A Cross-Layer Communication Protocol for Sensor Networks with Sectored Antennas,” IEEE Transactions on Mobile Computing, Vol. 9, No. 8, 2010, pp. 1072-1088. doi:10.1109/TMC.2010.61
- J. He, R. A. Norwood, M. Fallahi and N. Peyghambarian, “Solar-Powered Ad-Hoc Wireless Sensor Network for Border Surveillance,” SPIE Defense, Security, and Sensing, 2012.
- E. Felemban, C. Gun and E. Ekici, “MMSPEED: Multipath Multi-SPEED Protocol for QoS Guarantee of Reliability and Timeliness in Wireless Sensor Networks,” IEEE Transactions on Mobile Computing, Vol. 5, No. 6, 2006.
- K. Kordari and G. L. Blankenship, “Perimeter Coverage with Wireless Sensor Networks,” IEEE Military Communications Conference, San Diego, 2008.
- E. Onur, C. Ersoy, H. Delic and L. Akarun, “Surveillance Wireless Sensor Networks: Deployment Quality Analysis,” IEEE Network, Vol. 21, No. 6, 2007, pp. 48-53. doi:10.1109/MNET.2007.4395110
- Y. T. Hou, T. C. Lee, B. C. Jeng and C. M. Chen, “Optimal Coverage Deployment for Wireless Sensor Networks,” The 8th International Conference on Advanced Communication Technology, Phoenix Park, 20-22 February 2006.
- J. He and H. Shi, “Constructing Sensor Barriers with Minimum Cost in Wireless Sensor Networks,” Journal of Parallel Distributed Computing, Vol. 72, No. 12, 2012, pp. 1654-1663. doi:10.1016/j.jpdc.2012.07.004
- B. Bhattacharya, et al., “Optimal Movement of Mobile Sensors for Barrier Coverage of a Planar Region,” Theoretical Computer Science, Elsevier, 2009, pp. 5515-5528.
- G. Yang and D. Qiao “Multi-Round Sensro Deployment for Guranteed Barrier Coverage,” IEEE INFOCOM 2010.

