Int'l J. of Communications, Network and System Sciences
Vol. 5 No. 8 (2012) , Article ID: 21933 , 6 pages DOI:10.4236/ijcns.2012.58059
A Dynamic Multiple Watermarking Algorithm Based on DWT and HVS
1Information Engineering College, Shenzhen University, Shenzhen, China
2Shenzhen City of Modern Communication and Information Processing Laboratory, Shenzhen, China
Email: wzhangli@szu.edu.cn, yanxilan32@163.com, 84331623@qq.com, mrchen@szu.edu.cn
Received June 14, 2012; revised July 31, 2012; accepted August 12, 2012
Keywords: Dynamic Multiple Watermarking; JND
ABSTRACT
In this paper, a dynamic robust multiple watermarking algorithm is proposed based on Discrete Wavelet Transform (DWT) and Human Visual System (HVS). Watermark image is transformed by Arnold transform. Original image is divided into blocks with 8 by 8 and each block is transformed by DWT. By adopting the Just Noticeable Difference (JND) of HVS and changing low frequency coefficients, binary string message can be embedded into the decomposed original image. Watermark can be extracted blindly. Experimental results have shown that the proposed watermarking has robust against many attacks such as JPEG compressing, cropping, additive noise, line removal, median filter and related attacks with sinStirMark.
1. Introduction
Digital watermarking is a new technology of information hiding and it has effective effect for Copyright Protection. The conception of digital watermarking appeared firstly in the conference of image processing in 1994. Many experts made a lot of research for digital watermarking based on spatial [1] and transform domain [2,3].
From the view of image processing, embedding watermark information can be seemed that a puny signal overlap in a strength signal. Human will not feel the existence of information if the embed strength is lower than the threshold of HVS [4,5].
Robustness of watermarking is important for many applications. Compared with spatial domain methods, transform domain methods have stronger robust. Watermarking based on DWT [6] is an important transform domain method. Compared with the Discrete Cosine Transform (DCT), DWT has a better performance. Firstly, it has good time-frequency decomposition in accordance with the characteristic of HVS. Moreover, DWT has good compatibility for JPEG compression. Embedding watermark information in the DWT domain [7] has better robust against JPEG compression.
In this paper, an algorithm for data hiding by using DWT and JND model of HVS is proposed. It is a dynamic multiple blind watermarking algorithm, since more than one watermarks can be embedded into the original image. Original image is divided into 8*8 blocks and each block is transformed by DWT. A visual model [8] is used to calculate JND threshold. Watermark can be embedded by changing the LL-coefficient of original image.
The paper is organized as follows: Related work is introduced in Section 2. In Section 3 the proposed watermarking algorithm is discussed in detail. Section 4 is experimental results and at last conclusions are drawn.
2. Related Work
JND is defined as a measure referring to the capability of a human observer to detect noise or distortion in the field of view. It is related to characteristics of HVS and adaptive to contents of visual signal under consideration. With a HVS model, accessory information can be embedded in the regions with the least HVS sensitivity to the incurred changes. JND model in the essay of Podilchuk [9] is used. Original image of size M × N is first divided into 8 × 8 blocks (Bm) and each block is decomposed by DWT (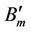 ). The formula is as follow:
). The formula is as follow:
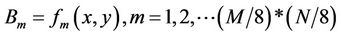 (1)
(1)
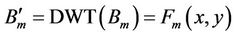 (2)
(2)
Contrast sensitivity can be calculated in DWT domains by the formula following:
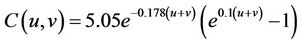 (3)
(3)
where u, v is frequency. Noise sensitive visual can be calculated by using Contrast Sensitivity. The formula is as follow:
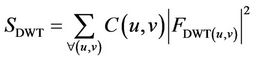 (4)
(4)
where FDWT is DWT of each block. JND can be calculated by:
 (5)
(5)
where 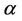 is strength which can be obtained by experiment.
is strength which can be obtained by experiment.
3. Proposed Watermarking Algorithm
Original image is decomposed into four sub-band images by DWT. Approximate sub-image (LL) is stable since it contains the majority of image energy. In order to gaining a better robustness, the watermark is embedded into approximate sub-image.
3.1. Watermark Embedding Process
By altering coefficients of approximate sub-image blocks, watermark is embedded. Watermark embedding is implemented through the following procedures.
Step 1: Generate watermark In our scheme, two binary images are used as original watermarks W. It is transformed into  by Arnold transform.
by Arnold transform.  is scanned on-line and then transformed into one-dimensional sequence
is scanned on-line and then transformed into one-dimensional sequence 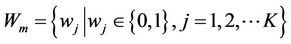 , where K is the number of watermark sequence. Two watermarks are considered for embedded labeled as watermark1
, where K is the number of watermark sequence. Two watermarks are considered for embedded labeled as watermark1  and watermark 2
and watermark 2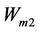 .
.
Step 2: Divide original image Original image of size M × N is divided into 8 × 8 blocks which are scanned into one-dimensional horizontal blocks (Bk).
Step 3: Calculate JND
JND calculation for the coefficient in the low-frequency domains can be finished according to the Formula (5).
Step 4: Generate number sequence Put a secure key X into a random number generator to produce random number sequence I. 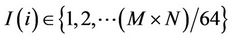 , if i = k, then I(i) = I(k).
, if i = k, then I(i) = I(k).
Step 5: choose image blocks to be embedded Transform each block into DWT coefficient matrix block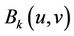 . Sub-block
. Sub-block 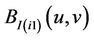 is selected to embed
is selected to embed 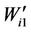 and
and 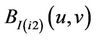 is selected to embed
is selected to embed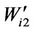 .
.
Step 6: Embed Watermarking Let 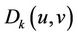 denotes LL sub-band coefficient of sub-block
denotes LL sub-band coefficient of sub-block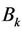 , Coefficients
, Coefficients 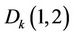 and
and 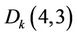 are selected to be embedded. Embedding rule is:
are selected to be embedded. Embedding rule is:
If 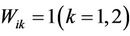 and
and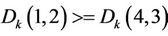 , exchange coefficients of
, exchange coefficients of 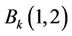 and
and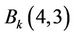 . Else if
. Else if 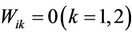 and
and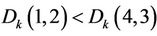 , exchange coefficients of
, exchange coefficients of 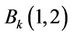 and
and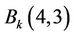 .
.
Embedding is done as Equations (6) and (7):
If 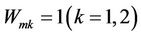 and
and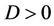
 (6)
(6)
where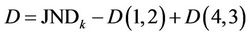 .
.
If 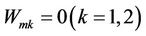 and
and 
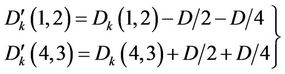 (7)
(7)
where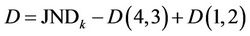 .
.
Where  is JND value of
is JND value of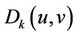 .
. 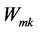 is watermarking signals.
is watermarking signals.
Step 7: Obtain watermarked image Inverse DWT(IDWT) is applied to obtain the watermarked image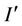 .
.
Watermark embedding procedure is shown in Figure 1.
Step 8: Dynamic watermark embedding By using the same watermark Embedding process as Step 1 - Step 7, more than one watermarks can be embedded into original image at any time, which can achieve the dynamic watermarking embedding.
3.2. Watermark Extraction Process
Watermark can be extracted blindly without original image. The steps are as follows.
Step 1: Apply DWT Divide watermarked image 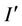 into 8 × 8 sub-blocks. Each block is scanned and sorted as embedding process. DWT is done to obtain decomposed sub-block
into 8 × 8 sub-blocks. Each block is scanned and sorted as embedding process. DWT is done to obtain decomposed sub-block .
.
Step 2: Regenerate number sequences Regenerate number sequences using the same key to select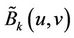 .
.
Step 3: Extract Watermark Let 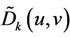 denotes LL sub-band coefficient of subblock
denotes LL sub-band coefficient of subblock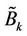 . Extract the one-dimensional sequence
. Extract the one-dimensional sequence 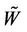 as:
as:
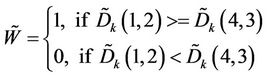 (8)
(8)
Step 4: Obtain the perfect watermarks Transform 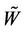 into two-dimensional watermark image. The perfect watermarks are obtained after Arnold transform.
into two-dimensional watermark image. The perfect watermarks are obtained after Arnold transform.
Watermark Extraction process procedure is shown in Figure 2.
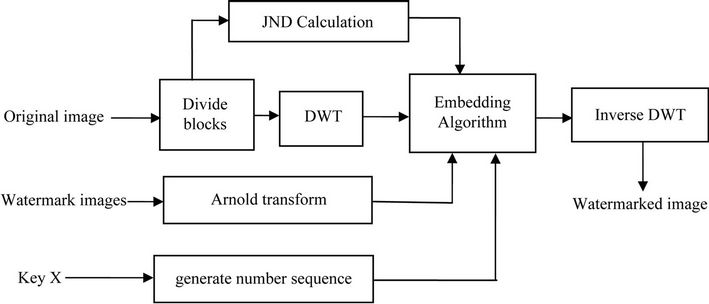
Figure 1. Watermark embedding procedure.
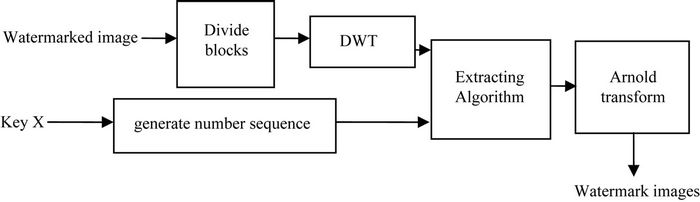
Figure 2. Watermark embedding procedure.
4. Experimental Results
Experimental results are simulated by programming in Matlab. Different cover images are used as original images and two binary watermark images for the test. Experimental results with 256 × 256 of original Lena image are given. Original image and watermark images are shown in the Figure 3. Embedded and extracted watermarks are shown in the Figure 4.
4.1. Robustness
This section examines the robustness against some attacks. Normative Correlation (NC) is employed to measure the similarity of extracted and original watermark defined as:
 (9)
(9)
where W is original watermark and 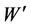 is extracted watermark with size M × N. The bigger NC is, the better similarity between W and
is extracted watermark with size M × N. The bigger NC is, the better similarity between W and 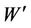 is.
is.
Performance analysis results are cited in Table 1. The proposed method is compared to the method of Reference [10] based on DCT and HVS. From the Table 1 we see that the proposed method performs well against JPEG compression with quality factor of 40, the quality
 (a)
(a) (b)
(b) (c)
(c)
Figure 3. (a) Original image; (b) Watermark 1; (c) Watermark 2.
 (a)
(a) (b)
(b) (c)
(c)
Figure 4. (a) Watermarked image; (b) Extracted watermark 1; (c) Extracted watermark 2.
of the extracted watermarks are good, this performance is better than the method in [10]. To demonstrate proposed method resistance to noise, gaussian niose was added. The experimental results in Table 1 show that the algorithm can resist this noise attack very well. It can also be
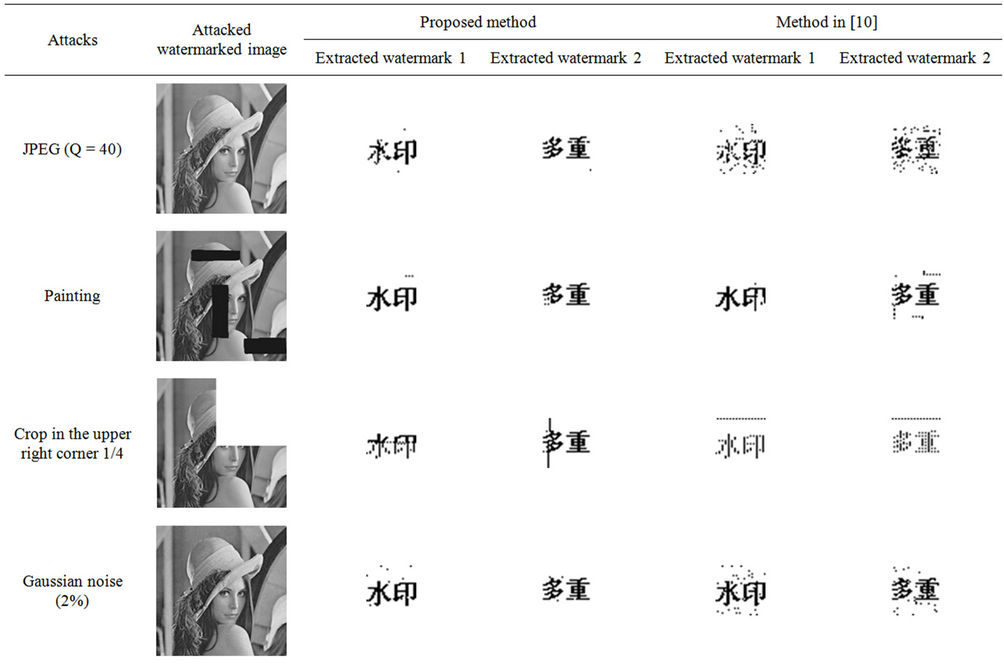

Table 1. The performance results for the proposed method and the method in [10].
observed from Table 1 that the proposed method outperforms in many cases. The proposed method provides better results in painting, line removal, histogram equalization, median filtering and cropping attack.
4.2. Invisibility
Peak signal noise ratio (PSNR) is used to evaluate the invisibility which is given in Equation (10):
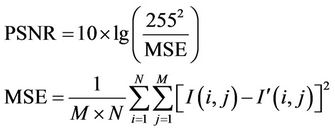 (10)
(10)
where 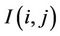 and
and 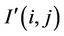 stand for the pixel values of
stand for the pixel values of
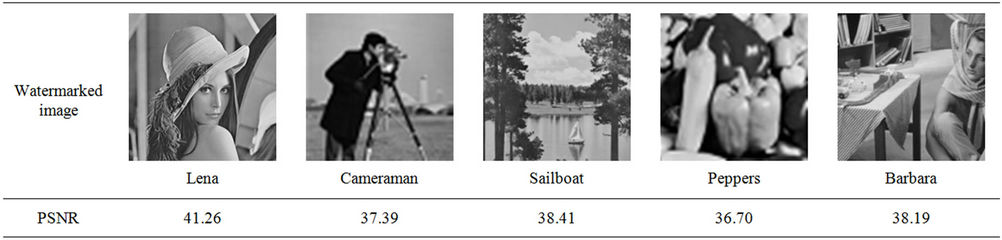
Table 2. PSNR values of proposed method with different original image (db).
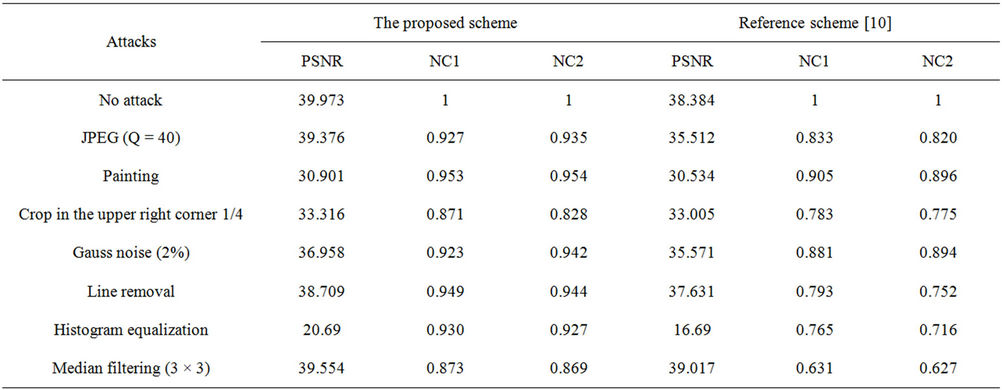
Table 3. Comparison between the proposed scheme and the scheme of reference [10].
original and watermarked image respectively. M and N are height and width of image.
Table 2 shows PSNR of the proposed scheme for different watermarked images. Table 3 represents PSNR of watermarked attacked images and NC values of extracted watermark1 and extracted watermark 2 between the proposed method and the method of Reference [10].
5. Conclusion
In this paper, an effective robust dynamic multiple blind watermarking algorithm is presented based on DWT domain. Robust is guaranteed because watermark is embedded into low-frequency with JND model of DWT. Experiment results show that the watermark algorithm can provide a high tolerance to noise, compression, cropping, painting, histogram equalization, filtering, noise attacks. Compared with the scheme of Reference [9], our method shows greater robustness against these attacks.
6. Acknowledgements
This work is partly supported by Shenzhen Internet industry to develop special fund (C201005250085A) and National Nature Science Foundation of China (Grant NO.61005049).
REFERENCES
- S. W. Weng, et al., “Reversible Watermarking Based on Invariability and Adjustment on Pixel Pairs,” Signal Processing Letters, Vol. 15, 2008, pp. 721-724. doi:10.1109/LSP.2008.2001984
- S. K. Bhagyashri and M. Y. Joshi, “All Frequency Band DWT-SVD Robust Watermarking Technique for Color Images in YUV Color Space,” IEEE International Conference on CSAE, Vol. 3, 2011, pp. 295-299.
- J. C. Patra, A. K. Kishore and C. Bornand, “Improved CRT-Based DCT Domain Watermarking Technique with Robustness against JPEG Compression for Digital Media Authentication,” 2011 IEEE International Conference on Systems, Man, and Cybernetics, Anchorage, 9-12 October 2011, pp. 2940-2945,
- S. Zhu and L. Jianming, “A Novel Adaptive Watermarking Scheme Based on Human Visual System and Particle Swarm Optimization,” Springer-Verlag, Berlin, 2009, pp. 136-146.
- Y. Zhang, “Blind Watermark Algorithm Based on HVS and RBF Neural Network in DWT Domain,” WSEAS Transactions on Computers, Vol. 8, No. 1, 2009, pp. 174- 183.
- J. N. Yang, X. L. Zhou and Y. X. Ge, “A Robust Content-Based Digital Image Watermarking Technique,” 2010 Chinese Conference on CCPR, Chongqing, 21-23 October 2010.
- A. Salama, R. Atta, R. Rizk and F. Wanes, “A Robust Digital Image Watermarking Technique Based on Wavelet Transform,” 2011 IEEE International Conference on System Engineering and Technology, Shah Alam, 27-28 June 2011, pp. 100-105. doi:10.1109/ICSEngT.2011.5993429
- S. Zhu and J. M. Liu, “A Novel Adaptive Watermarking Scheme Based on Human Visual System and Particle Swarm Optimization,” Springer-Verlag, Berlin, 2009, pp. 136-146.
- P. Christine and W. J. Zeng, “Image-Adaptive Watermaking Using Visual Models,” IEEE Journal on Selected Areas in Communications, Vol. 16, No. 4, 1998, pp. 525- 539. doi:10.1109/49.668975
- K. X. Yi, “Research on Digital Image Encryption and Digital Watermarking,” Ph.D. Thesis, Zhejiang University, Hangzhou, 2001, pp. 89-105.

