Communications and Network
Vol.07 No.02(2015), Article ID:56140,12 pages
10.4236/cn.2015.72012
Comparative Study of Proactive, Reactive and Geographical MANET Routing Protocols
Muthana Najim Abdulleh1, Salman Yussof1, Hothefa Shaker Jassim2
1College of Information Technology, Universiti Tenaga Nasional, Kajang, Malaysia
2College of Engineering, Komar University of Science and Technology, Sulaymaniyah, Iraq
Email: mut.n707@yahoo.com, salman@uniten.edu.my, hothefa.shaker@komar.edu.iq
Copyright © 2015 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 7 March 2015; accepted 3 May 2015; published 6 May 2015
ABSTRACT
Mobile Ad-hoc Network (MANET) is defined as a combination of mobile nodes that lack a fixed infrastructure and is quickly deployable under any circumstances. These nodes have self-aware architecture and are able to move in multiple directions, which renders it dynamic topology. Its dynamicity makes routing in MANET rather challenging compared to fixed wired networks. This paper aims to perform a comparative study on the three categories of MANET routing protocol by comparing their characteristics and operations, as well as their strength and weaknesses.
Keywords:
MANET, Proactive Routing, Reactive Routing, Geographical Routing

1. Introduction
Mobile Ad-hoc Network (MANET) is defined as a combination of mobile nodes that can keep in touch with one another despite the lack of a core centralized administrator or fixed infrastructure [1] . MANET possesses a dynamic temporary network topology, which makes it rapidly deployable in a situation whereby setting the wired network is almost impossible, such as in the battlefields and natural disaster areas. Due to its dynamic topology, wireless nodes in MANET function both as a host and a router to keep the internal communications network active. The wireless nodes within MANET move in an arbitrary fashion and organize themselves in a random manner. Direct communication between wireless nodes happens if they are within the range of radio transmission. If not, communication is established via intermediate nodes, which forward packets and recognize MANET as a multi-hop network [2] . MANET also has a lower bandwidth than that of wired network and since it is operating on batteries, its operation must be energy efficient to maximize the life span of the nodes [3] .
Over the years, there are many different routing protocols that have been developed for MANET. In general, these protocols can be categorized into three types: proactive, reactive and geographical routing protocols. This paper presents a comparative study of these three categories of MANET routing protocols. The presentation of the paper is organized as follows. Section 2 classifies multiple MANET routing protocols and provides a brief overview of several protocols in each category. Section 3 presents a comparison between the MANET routing protocols. An analysis of MANET routing protocols in terms of their characteristics, operation, strengths and weaknesses is presented in this section. It also highlights the drawbacks of these routing protocols to identify the areas that can be improved. Section 4 concludes the present comparative study of routing protocols in mobile ad-hoc networks.
2. Classification of Routing Protocols in MANET
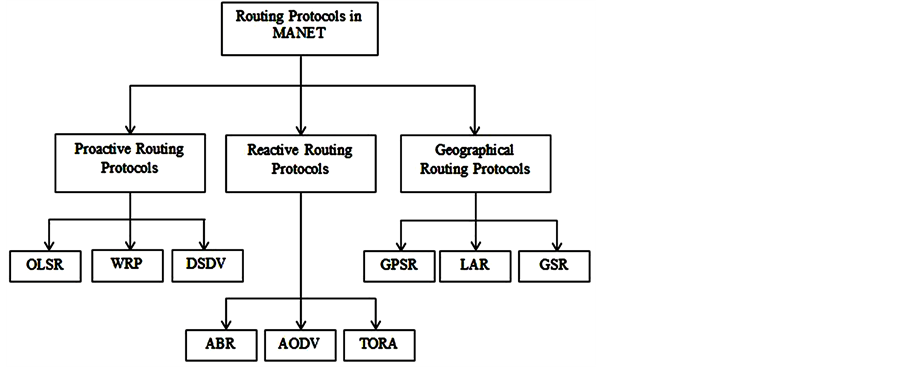
In MANET, routing protocols can be classified into Proactive Routing Protocols, Reactive Routing Protocols, and Geographical Routing Protocols [4] [5] . Figure 1 displays the basic classification of the routing protocols for MANET.
2.1. Proactive Routing Protocols
Proactive or table-driven routing protocols aim to keep up-to-date routing information flowing throughout a network between all nodes. As a means of preserving a consistent network connection, proactive routing protocols require every node to support at least one table which contains routing information. These nodes then react to the variations in the topology of the network by distributing the most current information through the network. This type of protocols is unique compared to others in term of the manner which the alterations to the network’s structure are transmitted and also the amount of routing-related tables that are required. The benefit of proactive routing protocols is the median delay time per packet that can be decreased. In these protocols, route information is present and accessible in the table whenever it is required. Nevertheless, in maintaining up-to-date routing information, proactive protocols uninterruptedly employ a significant share of network capacity. This makes such routing protocols unsuitable for reconfigurable mobile ad-hoc networks [6] [7] . Additionally, further network capacity wastage occurs as the majority of stored routing information actually may never be used, and the node activity is fast and the variations in topology are more regular than the actual requests for route information. A summary of the variety of proactive routing protocols will be given in subsequent sections.
2.1.1. Optimized Link State Routing Protocol (OLSR)
The OLSR is an optimized pure link state algorithm with proactive nature which allows it to ensure the availability of the routes when required. Hop-by-hop mechanism is utilized to forward packets, which is one of the main characteristics of any MANET routing protocol [6] [7] . Being a link-state routing algorithm, OLSR needs to keep up-to-date information about the nodes in the network and the route to each of these nodes. This is done by having the nodes to periodically broadcast link-state update messages. These updates may cause a large
Figure 1. Classification of routing protocols.
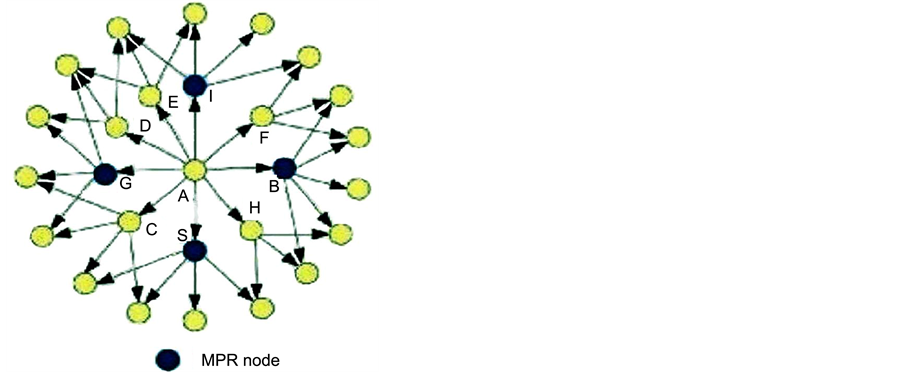
amount of traffic to be generated, which may take up network resources and reduce the performance of the network. Multi Point Rely (MPR) is a unique feature of MPR that is able to minimize the number of rebroadcasting nodes and, in turn, reduce the number of control messages generated during an update. With MPR, nodes are able to exchange topological information in a periodical manner without having to generate a large amount of traffic [6] . Figure 2 shows how update messages are transmitted with the use of MPR. Notice that the updated messages are only forwarded via selected nodes [8] . A route, from the given source to the destination is also created by the MPR. The process of neighbor detection is carried out by the periodical broadcast of HELLO messages by each node that are linked. These nodes sense each other, and in cases of symmetrical links, will regard each other as neighbors. Furthermore, link sensing and MPR selection process can also be carried out by the HELLO messages. All information pertaining to the relevant node that sent the HELLO message and its neighboring node will be found in the HELLO message. Each node is updated and recalculated when the updated information is received [9] . The TC message broadcasts topological information throughout the network, but these messages are only forwarded through MPR nodes. The MPR strategy functions better in large networks, which also positions OLSR as a better choice for large and dense networks.
1-and-1 hop symmetrical information is used by the MPR selection process to recalculate the MPR set. When a change in 1 or 2 hop neighborhood’s topology is detected, then the MPR recalculation will occur. The route to each known destination is recalculated and updated when the updated information is received [10] . MPR functions better in larger networks, which means that OLSR is better suited for large and dense networks [11] .
2.1.2. Destination-Sequenced Distance-Vector (DSDV)
Perkins and Bhagwat introduced Destination-Sequenced Distance-Vector (DSDV) [12] , which is regarded as the premier ad hoc routing protocols, similar to many distance-vector routing protocols [13] . It was expanded from the classical Bellman-Ford routing mechanism [14] -[16] , with the inclusion of destination address, sequence number and the number of hops rendering which it suitable for MANET operations. Each node possesses a routing table equipped with one route entrance to each goal, where the shortest path route (based on the number of hops) is recorded. A destination sequence number is utilized for the purpose of eschewing routing loops. A node increases its sequence whenever an alteration occurs in its vicinity. To maintain routing table consistency, routing changes are constantly passed throughout the network. There are two types of updates that are used; full dump and incremental. A full dump passes the whole routing table to its neighbors and is capable of acquiring many network protocol data units (NPDUs). Incremental updates are minuscule (must fit in a single packet) and transmits entries from routing tables that are altered during the previous full dump update. When the network is stabilized, updates are passed on, with full dumps seldom occurring. However, full dumps are common in a quick paced network. On top of the information being provided by the routing table, every route update packet possesses a unique sequence number that was assigned by the transmitter. The routes being labelled are frequently updated (highest number) using sequence number. The shortest route will be automatically selected if
Figure 2. OLSR multipoint relay shows how update messages are transmitted with the use of MPR [11] .
any two routes share a similar sequence number [13] . When there are multiple routes to a destination, a node will choose a route with the highest destination sequence number. This guarantees the utilization of routes that contains updated information [17] . Updated route broadcast will post the address of the destination, the number of hops to reach the destination, the sequence number of the destination and a new unique sequence number to broadcast; a route that is assigned an updated sequence number is regarded as a new route. However, if the sequence numbers are discovered to be similar, then a superior metric will be chose [14] .
2.1.3. Wireless Routing Protocol (WRP)
WRP is regarded as a part of the general class of path-finding algorithms [12] [18] [19] , and defined as a collection of distributed shortest path algorithms that determines the paths via information on the length and second- to-last hop of the shortest path to every destination. WRP decreases the number of cases whereby a temporary routing loop might occur. Wireless Routing Protocol is a table-based protocol with the intention of keeping routing information secured between the nodes of the network. Every node is tasked with maintaining four tables [3] [15] [20] [21] :
• Distance table
• Routing table
• Link-cost table
• Message retransmission list (MRL) table
WRP utilizes periodic update message transmissions adjacent to a node. The nodes in the response list of new messages (which is formed using MRL) should in turn acknowledge it. If there are no changes from the previous update, then the nodes in the response list will send an idle HELLO message to confirm connectivity. A node is empowered to decide whether or not to update its routing table post-receiving an updated message from nearby while looking for a superior path with the updated information it receives. In case the node obtains a superior path, this information will be relayed to the original node for table updates. After being acknowledged, the original node will proceed to update its MRL. Every time the consistency of the routing information is being examined by the nodes present in the protocol, it helps reduce routing loops and determine the best routing solution within the network [22] .
2.2. Reactive Routing Protocols
Reactive routing is also known as on-demand routing protocols. These protocols lack routing information or routing activity on the nodes in the network when communication is lacking or dismal. Unused routes are maintained with less overhead. Unfortunately, more time delays may be experienced initially. A route is searched for by the reactive protocol in an on-demand manner if a node intends to pass on a packet to another node. The packet is received and transmitted after forming a connection. Then, the request packets are dispersed within the networks, leading to a discovery of routes. There are two categories of reactive protocol; source routing and hop-by-hop routing. A complete source to the designated address is carried by the source routed on-demand protocols. The information contained in the header of each packet will be evaluated by every intermediate node when forwarding these packets. The intermediate nodes are not required to maintain updated routing data for each active route. In addition, neighbor connectivity through periodic beaconing messages is also not required in the database of the nodes. As each node has the potential to update its routing table in the presence of fresher topology information, the routes are therefore adaptable to the changing environment, which takes place dynamically in the MANETs. The data packets are forwarded over better and fresher routes this way [23] -[25] . The protocols under this category are detailed below.
2.2.1. Associativity-Based Routing (ABR)
The ABR [26] [27] protocol is responsible for detailing a unique routing metric called “degree of association stability” for mobile ad-hoc networks. It is assumed to lack loops, deadlock, and packet duplicates. In ABR, routes are chosen based on the links between the states of nodes. The chosen nodes are expected to last long enough. Each node gives off periodic beacons as a mark of its existence. When an adjacent node detects a beacon, it will promptly update its associated tables. Each beacon received will result in an increment to the node. In this case, association stability also means the connection stability of a node towards another at the same time and space. A higher value of associativity ticks with a node indicates a low state of node mobility, and vice versa. Associativity ticks revert to normal when the neighbors or the nodes move beyond their respective reach. The fundamental objective of ABR is to seek out longer-lived routes for ad hoc mobile networks, which are Route discovery, Route reconstruction (RRC), and Route deletion [3] [28] .
1) Route discovery phase: The route discovery phase is a broadcast query and await-reply (BQ-REPLY) cycle. The source node broadcasts a BQ message seeking nodes possessing a route to the destination. A node will only pass a BQ request once. Upon receiving the BQ message, an intermediate node alters both the address and associativity ticks of the query packet. The upcoming node will delete the upstream nodes of its neighbors’ associativity tick entries while keeping the entry that is associated with itself and its corresponding upstream node. Every packet that reaches the destination will possess the associativity ticks of the nodes along the route, all the way from the source to the destination. Now, the destination can freely choose the best route via analysing the associativity ticks associated with each path. In the case of multiple paths possessing similar degree of association stability, the route having the least amount of hops will be chosen. Once a path has been determined, the destination passes forth a REPLY packet back to the source on this path. The nodes that the REPLY packet adhere to will serve to validate their respective routes, while other routes remain inactive, eschewing any chances of duplicated packets reaching the destination as well [28] .
2) Route reconstruction (RRC) phase: RRC phase consists of partial route discovery, invalid route erasure, valid route updates, and new route discovery, depending on which node(s) along the route move. The movement of source nodes will precipitate a unique BQ-REPLY process due to the fact that the routing protocol is source- initiated. The route notification (RN) message deletes entries associated with routes and downstream nodes. When the destination moves, its immediate upstream node deletes its corresponding routes. A localized query (LQ [H]) process, where H refers to the hop count from the upstream node to the destination, will start for the purpose of confirming whether or not the node can be reached. If the destination gets the LQ packet, it will be prompted to choose the best partial route and REPLYs; otherwise, the initiating node times out and backtrack to the next upstream node. An RN message is dispatched to the adjacent upstream node to delete invalid routes and also inform it that the node must initiate the LQ [H] process. However, if the backtracking exceeds halfway to the source, the LQ process is terminated, and the source will restart the BQ process all over again [28] .
3) Route deletion phase: When a route is no longer required, the source node will start a route delete (RD) broadcast. Each node present on the route will remove the route’s entry from their respective routing tables. The RD message is broadcasted indirectly, as the source node might be unaware of any alteration to its route during RRCs [28] .
2.2.2. Temporally Ordered Routing Algorithm (TORA)
TORA is an adaptive routing protocol for highly dynamic mobile multi hop networks that are source initiated and based on link reversal algorithms [29] . This protocol is able to rapidly build routes and reduce communication overhead via the localization response to topological alterations as much as they can [30] . TORA uses the “direction of the next destination” to send data, instead of using the concept of the shortest path to determine routes. This means less processing and less bandwidth usage. The source node uses one or two paths to the destination through several intermediate neighboring nodes [31] . The three main processes in the TORA protocol are route creation, route maintenance and route erasure. The route creation process uses query and UDP packets. For route creation, a height metric is used, where the height of the destination node is set to 0, while all of the others are set to NULL. The source node will then proceed to transmit a query packet containing the destination node’s ID. Nodes that possess a non-NULL height will respond using a UDP packet that is made up of its height. The node receiving the UDP packet is set at a height that’s higher, and is regarded as being “upstream” and vice versa. This results in the construction of a direct acyclic graph (DAG), from source to destination. The route formation process is realized by sending a request from the source, and receiving replies from its intended destination. During mobility, the DAG is broken, and route maintenance will then work to restore a DAG that is routed at the destination [32] .
2.2.3. Ad-Hoc on Demand Distance Vector Routing Protocol (AODV)
Ad-hoc On-Demand Distance Vector Routing Protocol (AODV) [33] -[36] is a unicast reactive routing protocol. Basically this implies that the routes are formed when they are needed. The AODV protocol contains four control packets; HELLO messages, route requests (RREQs), route replies (RREPs) and route error messages (RERRs). These control packets are used in the two protocol mechanisms which are route discovery and route maintenance. In the AODV protocol, all nodes maintain a routing table that stores information regarding active routes. The information stored are destination, next hop, number of hops, sequence number for the destination, active neighbors for a route and the expiration time for a route table entry. Route entry timeout are updated upon usage. To prevent looping in distance vector routing, a sequence number is sent with RREQs and RREPs, both of which are stored in the routing table. A larger sequence number is indicative of the fact that recent updated route information and the one with the highest sequence number will be utilized. If two routes possess the same sequence number, the one with the fewer number of hops (a shorter route) will be used.
Route discovery mechanism begins when no valid route is found within the routing table of the source node. Route requests (RREQs) are sent to the network to search for the route to the destination. Receiving nodes create reverse routing entries towards the source for the purpose of sending possible reply packets later. A route reply (RREP) is dispatched by either the destination or intermediate node that is a validated route towards the destination. Nodes that received RREPs also create reverse routing entries towards the nodes that sent the RREPs. Often, each of the nodes along an active route will transmit HELLO messages to the neighboring nodes. If no HELLO message or data is received from a neighboring node after a period of time, the link is regarded as broken. If the destination of the route using this link is nearby the next hop from the neighbor, then a local repair process may be used to repair the route. If not, then a route error (RERR) message is sent to neighboring nodes, which then broadcasts the RERR message towards other nodes that may have routes affected by the broken link. If the route is needed by the affected source, the route discovery process will then be repeated [36] .
2.3. Geographical Routing Protocols
Geographical routing [37] [38] utilizes information derived from a location for the purpose of formulating and optimizing the searching route towards the destination. Geographical routing suits sensor networks, especially where data aggregation remains a useful technique in the minimization of transmission to the base station via the elimination of redundancy between packets from multiple sources [39] . There is also a higher possibility for big multi-hop wireless network topology to change frequently. Geographical routing needs only the propagation of single-hop topology information such as the optimal neighbor to decide accurately on forwarding. The way it localizes its approach decreases the requirement of maintaining the routing tables, which in turn decreases the control’s overhead, and eliminated the need for flooding. The nodes that are within the marked forwarding zones are capable of forwarding data packets. This marked region can be defined by the source or intermediate nodes to exclude nodes that might precipitate a detour in the course of forwarding the data packet. The second property associated with geographical routing is position-based routing. In this case, a node only needs to know where its direct neighbor is located. The mechanism that is involved in this case is the greedy mechanism whereby each node forwards a packet to an adjacent node. The Euclidean distance to the destination will be utilized as a metric. Position-based routing protocols are capable of reducing the overhead and energy because flooding for node discovery and state propagation is localized within a single hop [39] . The network density, accurate localization of nodes, and the forwarding rule are the deciding factors for the efficiency of the scheme [40] .
2.3.1. Greedy Perimeter Stateless Routing (GPSR)
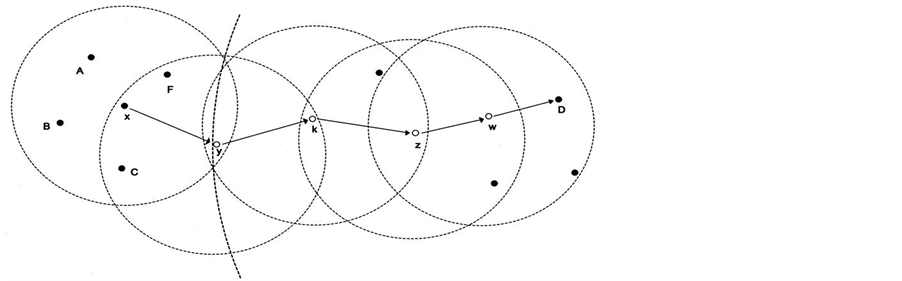
Greedy Perimeter Stateless Routing (GPSR) is a novel routing protocol for wireless datagram networks that utilizes the location of the routers and its destination to decide on forwarding. GPSR decides on greedy forwarding decisions by utilizing the information regarding a router’s adjacent neighbors within the network’s topology. When a packet reaches a region within which greedy forwarding becomes impossible, the algorithm recovers itself via routing adjacent to the perimeter of the region. By remaining close to the local topology, the GPSR scales better in per-router state than shortest-path and ad-hoc routing protocols as the number of network destinations increases. Under the mobility’s frequent topological changes, Figure 3 shows that the GPSR can utilize local topology information to discover accurately new routes faster. The local topology information can be used by GPSR to search for the new routes immediately, even under constantly changing topology due to node mobility. When choosing a packet’s next hop, a forwarding node can make a local greedy choice optimally. This is because the initiator has marked the packet with the location of its destination under GPSR. The GPSR protocol utilizes extensive simulation of mobile wireless networks for the purpose of comparing its performance with that of Dynamic Source Routing [41] .
Figure 3. Greedy perimeter stateless routing [41] .
2.3.2. Location Aided Routing (LAR)
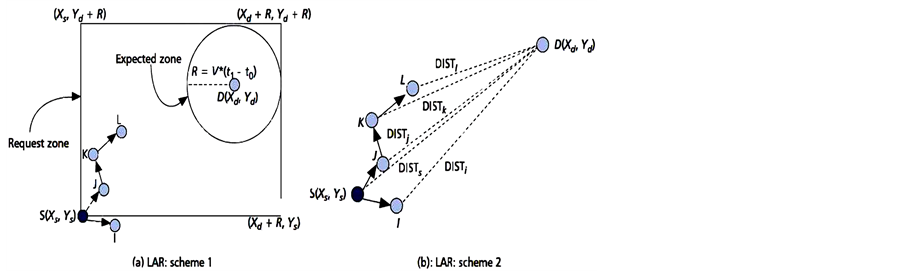
The location aided routing protocol fails to confirm a location-based routing protocol and proposed the usage of position information to improve the route discovery phase of reactive ad-hoc routing approaches. The location information is obtained by GPS by utilizing two flooding regions; forwarded and expected. The decrease in the search space will inevitably result in lesser route messages. When a source node intends to dispatch a data packet, it will first request for the location of the destination from the location service which causes contacting and tracking problems [42] . Figure 4 as shown in the two LAR algorithms being proposed; LAR Scheme 1 and LAR Scheme 2 [43] . LAR Scheme 1 utilizes the expected location of the destination to confirm the requested zone during route discovery. The requested zone is rectangular both at the source and at the expected zone of destination. Its sides are parallel to both the x and y-axis. In route discovery phase, source transmits the route request message including four corners of the requested zone and an intermediate node decides whether to transmit the message or not. Using the position from scheme LAR, Scheme 2 uses distance to define the requested zone. The intermediate node transmits if it is adjacent to the destination’s previous location than the node transmitting the request packet; it is repeated until it is not received by its intended recipient [4] [44] .
2.3.3. Geography Source Routing (GSR)
In GSR, source node computes the shortest path to the destination using dijkstra’s algorithm based on distance metrics. It computes the distance from the source to intermediate nodes through which data is to be forwarded [45] . The source node queries for the location and floods the packet to the nodes, which wastes bandwidth. Spatially Aware Routing: It uses the GSR packet forwarding strategy to overcome the problem of recovery strategy in GPSR. It calculates the shortest path using dijkstra’s algorithm. Source sets GSR consists of a list of intermediate nodes embedded in the header of all data packets by a source. Each forwarding node maps the position of its neighbors into graph nodes and chooses the next node having the shortest path from the destination, and then the packet will be forwarded to the next hop, which moves the data closer to the destination [4] .
3. Analysis of MANET Routing Protocols
In this section, an analysis of the reviewed MANET routing protocols in terms of their characteristics, operation, strengths and weaknesses is presented. This section also highlights the drawbacks of these routing protocols to identify the areas that can be improved
3.1. Comparisons between MANET Routing Protocols
This subsection presents the comparison between the routing protocols reviewed in Section 2 above. Table 1 presents a general comparison between the three categories of MANET routing protocols, while Tables 2-4 present the comparison between the proactive, reactive and geographical MANET routing protocols respectively. Table 1 summarizes the comparison between the Proactive, Reactive and Geographical MANET routing protocols discussed in this section. The comparison is done with respect to routing structure, availability of route, traffic control volume, periodic updates, control overhead, route acquisition delay, storage requirements, bandwidth requirement, power requirement, scalability problem, handling effects of mobility and quality of service support.
Figure 4. LAR: limited flooding of route request: a) scheme 1: expected zone; b) scheme 2: closer distances [43] .
Table 1. Comparison between proactive, reactive and geographical MANET routing protocols.
Table 2 summarizes the comparison between the three proactive routing protocols. The comparison is done with respect to Multicast, number of routing tables used, and the frequency of updates
Table 3 summarizes the comparison between the three reactive routing protocols. The comparison is done with respect to multiple routes, route metric method, and the route reconfiguration strategy.
Table 4 summarizes the comparison between the three geographical routing. The comparison is done with respect to routing structure, number of routing tables used, and the frequency of updates.
Table 2. Comparison between proactive routing protocols [46] .
Table 3. Comparison between of reactive routing protocols [29] .
Table 4. Comparison between Geographical routing protocols [10] [29] .
3.2. Drawbacks of MANET Routing Protocols
Many researches have compared and analysed the characteristics and functionality of MANET routing protocols within these three categories. They observe that proactive routing protocols are unsuitable for reconfigurable wireless ad-hoc network environment due to the excessive use of the network capacity to maintain an up-to-data topological map on the entire network during the movement of nodes and network topology changes. In OLSR, the overhead for the control message increases when the numbers of mobile nodes increase. It will also need higher processing power compared to other protocols when trying to look for other routes [47] . OLSR [48] -[50] , depends on the synchronized clocks among the nodes in the ad-hoc network. The reliance of this protocol upon the intermediate lower layers for selected functionalities assumes that the connected status sensing and neighbor discovery that are needed for packet delivery and address resolution are all readily available.
WRP updates the message transmission to its adjacent neighbors, and the nodes within the response list of the updated message will acknowledge its receipt to the class of path algorithm. WRP provides the faster route convergence [51] . DSDV [27] [52] , requires constant updating to its routing tables which needs battery power and small amount of bandwidth, despite the network being idle. Upon alteration of the topology of the network, a unique sequence number is needed prior to network converging which renders DSDV unsuitable for highly dynamic networks.
Reactive routing protocols have high latency due to the need to look for a route to the destination before data can be sent. Flooding can lead to network clogging, while RREP, RREQ & RERR messages lead to control overheads [53] -[55] . TORA is able to rapidly build routes and decrease the communication overheads via the localization of the response to topological changes [30] , which results in decreased processing and bandwidth usage of TORA protocol in terms of route creation, route maintenance and route erasure. In AODV, the intermediate nodes might result in inconsistent routes if the source sequence number is very old and the intermediate nodes have a higher, but not the latest destination sequence number, thereby having stale entries. Furthermore, the generation of many RREP packets in response to a single RREQ packet might lead to heavy control overheads. Another limitation of AODV is the fact that periodic beaconing result in excessive bandwidth consumption [56] [57] .
Geographical routing is suitable for sensor networks, where data aggregation is utilized to minimize transmissions to base station via the elimination of redundancy between packets from multiple sources. GPSR has low overhead for data forwarding and local maximums are easily found. The GSR and the source node compute the shortest path to the destination using Dijkstra’s algorithm, based on distance metrics [38] . It computes distance from the source to intermediate nodes through which data is to be forwarded. In LAR, when the source node intends to dispatch a data packet, it will first request for the location of the destination which might create contacting or tracking problem [44] .
4. Conclusion
This paper presents a comparative study of routing protocols in mobile ad-hoc networks. These protocols are divided into three: proactive or table-driven, reactive or on-demand, and geographical routing protocols. For each of these classes, we have reviewed several representative protocols. Each routing protocol has unique features. The main factor that distinguishes the protocols is the method of determining routes within source destination pairs. The drawbacks, strengths and weaknesses of each protocol have also been examined in this paper. Reactive routing protocols suffer from longer delays and proactive routing protocols have higher overhead. The geographical routing protocol is very suitable for sensor networks whereby data aggregation is effective in minimizing transmission towards the base station via the elimination of redundancy among packets of multiple sources.
References
- Singh, G. and Singh, A. (2012) Performance Evaluation of Aodv and Dsr Routing Protocols for Vbr Traffic for 150 Nodes in MANETs. International Journal of Computational Engineering Research (ijceronline. com), 2, 1583-1587.
- Kaur, R. and Rai, M.K. (2012) A Novel Review on Routing Protocols in MANETs. Undergraduate Academic Research Journal (UARJ), 1, 103-108.
- Dhenakaran, S.S. and Parvathavarthini, A. (2013) An Overview of Routing Protocols in Mobile Ad-Hoc Network. International Journal of Advanced Research in Computer Science and Software Engineering, 3, 251-259.
- Malhotra, S. and Gill, N.S. (2014) Analysing Geographic Based Routing Protocols in MANETs. International Journal of Computer Science and Mobile Computing, 3, 1068-1073
- Panda, I. (2012) A Survey on Routing Protocols of MANETs by Using Qos Metrics. International Journal of Advanced Research in Computer Science and Software Engineering, 2, 120-129.
- Abolhasan, M., Wysocki, T. and Dutkiewicz, E. (2004) A Review of Routing Protocols for Mobile Ad Hoc Networks. Ad Hoc Networks, 2, 1-22. http://dx.doi.org/10.1016/S1570-8705(03)00043-X
- Mbarushimana, C. and Shahrabi, A. (2007) Comparative Study of Reactive and Proactive Routing Protocols Performance in Mobile Ad Hoc Networks. 21st International Conference on Advanced Information Networking and Applications Workshops, AINAW’07, Niagara Falls, 21-23 May 2007, 679-684.
- BR, A.K., Reddy, L.C. and Hiremath, P.S. (2008) Performance Comparison of Wireless Mobile Ad-Hoc Network Routing Protocols. IJCSNS International Journal of Computer Science and Network Security, 8, 337-343.
- Guo, J. and Wang, A. (2014) Study on Integration OLSR Protocol in Mobile Ad Hoc Network. Proceedings of the 9th International Symposium on Linear Drives for Industry Applications, 4, 701-708.
- Bali, S., Steuer, J. and Jobmann, K. (2008) Capacity of Ad Hoc Networks with Line Topology Based on UWB and WLAN Technologies. Wireless Telecommunications Symposium, Pomona, 24-26 April 2008, 17-24. http://dx.doi.org/10.1109/WTS.2008.4547538
- Lol, W.G. (2008) An Investigation of the Impact of Routing Protocols on MANETs Using Simulation Modelling. Auckland University of Technology, Auckland.
- Perkins, C.E. and Bhagwat, P. (1994) Highly Dynamic Destination-Sequenced Distance-Vector Routing (DSDV) for Mobile Computers. ACM SIGCOMM Computer Communication Review, 24, 234-244.
- Boukerche, A., Turgut, B., Aydin, N., Ahmad, M.Z., Bölöni, L. and Turgut, D. (2011) Routing Protocols in Ad Hoc Networks: A Survey. Computer Networks, 55, 3032-3080. http://dx.doi.org/10.1016/j.comnet.2011.05.010
- Bakht, H. (2011) Survey of Routing Protocols for Mobile Ad-Hoc Network. International Journal of Information and Communication Technology Research, 1, 258-207.
- Royer, E.M. and Toh, C.K. (1999) A Review of Current Routing Protocols for Ad Hoc Mobile Wireless Networks. IEEE Personal Communications, 6, 46-55. http://dx.doi.org/10.1109/98.760423
- Wan, T., Kranakis, E. and Van Oorschot, P.C. (2004) Securing the Destination-Sequenced Distance Vector Routing Protocol (S-DSDV). In: Information and Communications Security, Springer, Berlin, 358-374.
- Dhenakaran, D.S. and Parvathavarthini, A. (2013) An Overview of Routing Protocols in Mobile Ad-Hoc Network. International Journal of Advanced Research in Computer Science and Software Engineering, 3, 251-259.
- Humblet, P.A. (1991) Another Adaptive Distributed Shortest Path Algorithm. IEEE Transactions on Communications, 39, 995-1003. http://dx.doi.org/10.1109/26.87189
- Rajagopalan, B. and Faiman, M. (1991) A Responsive Distributed Shortest-Path Routing Algorithm within Autonomous Systems. Journal of Internetworking: Research and Experience, 2, 51-69.
- Chowdhury, S. A., Uddin, M. A., and Al Noor, S. (2012) A Survey on Routing Protocols and Simulation Analysis of WRP, DSR and AODV in Wireless Sensor Networks.
- de Morais Cordeiro, C. and Agrawal, D.P. (2011) Ad Hoc and Sensor Networks: Theory and Applications. World Scientific, Singapore. http://dx.doi.org/10.1142/8066
- Kumar, G.V., Reddyr, Y.V. and Nagendra, D.M. (2010) Current Research Work on Routing Protocols for MANET: A Literature Survey. International Journal on Computer Science and Engineering, 2, 706-713.
- Bhat, M.S., Shwetha, D. and Devaraju, J. (2011) A Performance Study of Proactive, Reactive and Hybrid Routing Protocols using Qualnet Simulator. International Journal of Computer Applications, 28, 10-17.
- Khatri, P., Rajput, M., Shastri, A. and Solanki, K. (2010) Performance Study of Ad-Hoc Reactive Routing Protocols. Journal of Computer Science, 6, 1159-1163. http://dx.doi.org/10.3844/jcssp.2010.1159.1163
- Mewada, S. and Kumar, U. (2011) Measurement Based Performance of Reactive and Proactive Routing Protocols in WMN. International Journal of Advanced Research in Computer Science and Software Engineering, 1, 1-6
- Toh, C.K. (1996) A Novel Distributed Routing Protocol to Support Ad-Hoc Mobile Computing. Proceedings of the 1996 IEEE Fifteenth Annual International Phoenix Conference on Computers and Communications, Scottsdale, 27-29 March 1996, 480-486.
- Khiavi, M.V., Jamali, S. and Gudakahriz, S.J. (2012) Performance Comparison of AODV, DSDV, DSR and TORA Routing Protocols in MANETs. International Research Journal of Applied and Basic Sciences, 3, 1429-1436.
- Misra, P. (1999) Routing Protocols for Ad Hoc Mobile Wireless Networks. Courses Notes. http://suraj.lums.edu.pk/~cs678/papers/17_routing_for_ad_hoc.pdf
- Islam, M.S., Riaz, M.A. and Tarique, M. (2012) Performance Analysis of the Routing Protocols for Video Streaming over Mobile Ad Hoc Networks. International Journal of Computer Networks & Communications (IJCNC), 4, 133-150. http://dx.doi.org/10.5121/ijcnc.2012.4310
- Pragati, E. and Nath, D.R. (2012) Performance Evaluation of AODV, LEACH & TORA Protocols through Simulation. International Journal of Advanced Research in Computer Science and Software Engineering, 2, 85-89.
- Aujla, G.S. and Kang, S.S. (2013) Comprehensive Evaluation of AODV, DSR, GRP, OLSR And TORA Routing Protocols with Varying Number of Nodes and Traffic Applications over MANETs. IOSR Journal of Computer Engineering, 9, 54-61. http://dx.doi.org/10.9790/0661-0935461
- Som, D.S. and Singh, D. (2012) Performance Analysis and Simulation of AODV, DSR and TORA Routing Protocols in MANETs. International Journal of Recent Technology and Engineering (IJRTE), 1, 122-127.
- Chakeres, I.D. and Belding-Royer, E.M. (2004) AODV Routing Protocol Implementation Design. 24th International Conference on Distributed Computing Systems Workshops, 23-24 March 2004, 698-703. http://dx.doi.org/10.1109/ICDCSW.2004.1284108
- Das, S.R., Belding-Royer, E.M. and Perkins, C.E. (2003) Ad Hoc On-Demand Distance Vector (AODV) Routing. http://www.ietf.org/rfc/rfc3561
- Etorban, A.A. (2012) The Design and Performance Evaluation of a Proactive Multipath Routing Protocol for Mobile Ad Hoc Networks. Heriot-Watt University, Edinburgh.
- Perkins, C.E. and Royer, E.M. (1999) Ad-Hoc On-Demand Distance Vector Routing. Second IEEE Workshop on Mobile Computing Systems and Applications, Proceedings, WMCSA’99, New Orleans, 25-26 February 1999, 90-100.
- Karkazis, P., Leligou, H., Orphanoudakis, T. and Zahariadis, T. (2012) Geographical Routing in Wireless Sensor Networks. 2012 International Conference on Telecommunications and Multimedia (TEMU).
- Kumar, P., Chaturvedi, A. and Kulkarni, M. (2012) Geographical Location Based Hierarchical Routing Strategy for Wireless Sensor Networks. 2012 International Conference on Devices, Circuits and Systems (ICDCS), Coimbatore, 15-16 March 2012, 9-14.
- Sohraby, K., Minoli, D. and Znati, T. (2007) Wireless Sensor Networks: Technology, Protocols, and Applications. John Wiley & Sons, Hoboken. http://dx.doi.org/10.1002/047011276X
- Battula, R.S. and Khanna, O. (2013) Geographic Routing Protocols for Wireless Sensor Networks: A Review. International Journal of Engineering and Innovative Technology (IJEIT), 2, 39-42.
- Karp, B. and Kung, H.T. (2000) GPSR: Greedy Perimeter Stateless Routing for Wireless Networks. Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, Boston, 6-11 August 2000, 243-254. http://dx.doi.org/10.1145/345910.345953
- Ko, Y.B. and Vaidya, N.H. (2000) Location-Aided Routing (LAR) in Mobile Ad Hoc Networks. Wireless Networks, 6, 307-321. http://dx.doi.org/10.1023/A:1019106118419
- Mikki, M.A. (2009) Energy Efficient Location Aided Routing Protocol for Wireless MANETs. arXiv preprint arXiv:0909.0093.
- Hong, X., Xu, K. and Gerla, M. (2002) Scalable Routing Protocols for Mobile Ad Hoc Networks. IEEE Network, 16, 11-21. http://dx.doi.org/10.1109/MNET.2002.1020231
- Liu, L., Wang, Z. and Jehng, W.K. (2008) A Geographic Source Routing Protocol for Traffic Sensing in Urban Environment. IEEE International Conference on Automation Science and Engineering, CASE 2008, Arlington, 23-26 August 2008, 347-352.
- Mohseni, S., Hassan, R., Patel, A. and Razali, R. (2010) Comparative Review Study of Reactive and Proactive Routing Protocols in MANETs. 4th IEEE International Conference on Digital Ecosystems and Technologies (DEST), Dubai, 13-16 April 2010, 304-309. http://dx.doi.org/10.1109/DEST.2010.5610631
- Hassnawi, L., Ahmad, R., Yahya, A., Aljunid, S. and Elshaikh, M. (2012) Performance Analysis of Various Routing Protocols for Motorway Surveillance System Cameras’ Network. International Journal of Computer Science Issues, 9, 7-21.
- Clausen, T., Jacquet, P., Adjih, C., Laouiti, A., Minet, P., Muhlethaler, P., Viennot, L., et al. (2003) Optimized Link State Routing Protocol (OLSR). http://dx.doi.org/10.17487/rfc3626
- Johnson, D.B. (1994) Routing in Ad Hoc Networks of Mobile Hosts. First Workshop on Mobile Computing Systems and Applications, WMCSA 1994, Santa Cruz, 8-9 December 1994, 158-163.
- Reddy, P.N., Vishnuvardhan, C. and Ramesh, V. (2013) An Overview on Reactive Protocols for Mobile Ad-Hoc Networks. International Journal of Computer Science and Mobile Computing, 2, 368-375.
- Srivastava, S., Yadav, A. and Kumar, A. (2013) Impact of Node Mobility of Routing Protocols on MANET. International Journal of Scientific & Engineering Research, 4, 1424-1431.
- Janakiraman, G., Raj, T.N. and Suresh, R. (2013) AODV, DSDV, DSR Performance Analysis with TCP Reno, TCP New Reno, TCP Vegas on Mobile Ad-Hoc Networks Using NS2. International Journal of Computer Applications, 72, 1-7.
- Gupta, A.K., Sadawarti, H. and Verma, A.K. (2011) A Review of Routing Protocols for Mobile Ad Hoc Networks. SEAS Transactions on Communications, 10, 331-340.
- Gupta, A.K., Sadawarti, H. and Verma, A.K. (2011) Review of Various Routing Protocols for MANETs. International Journal of Information and Electronics Engineering, 1, 251-259. http://dx.doi.org/10.7763/IJIEE.2011.V1.40
- Gupta, N. and Shrivastava, M. (2013) An Evaluation of MANET Routing Protocol. International Journal of Advanced Computer Research, 3, 165-170.
- Gupta, A. and Pradhan, M. (2013) A Comparative Study of Current Routing Protocol in Wireless Ad-Hoc Network. International Journal of Engineering Research and Technology, 2, 144-148.
- Malhotra, R. and Kaur, S. (2011) Comparative Analysis of AODV and DSR Protocols for Mobile Adhoc Networks. International Journal of Computer Science & Engineering Technology, 1, 330-335.