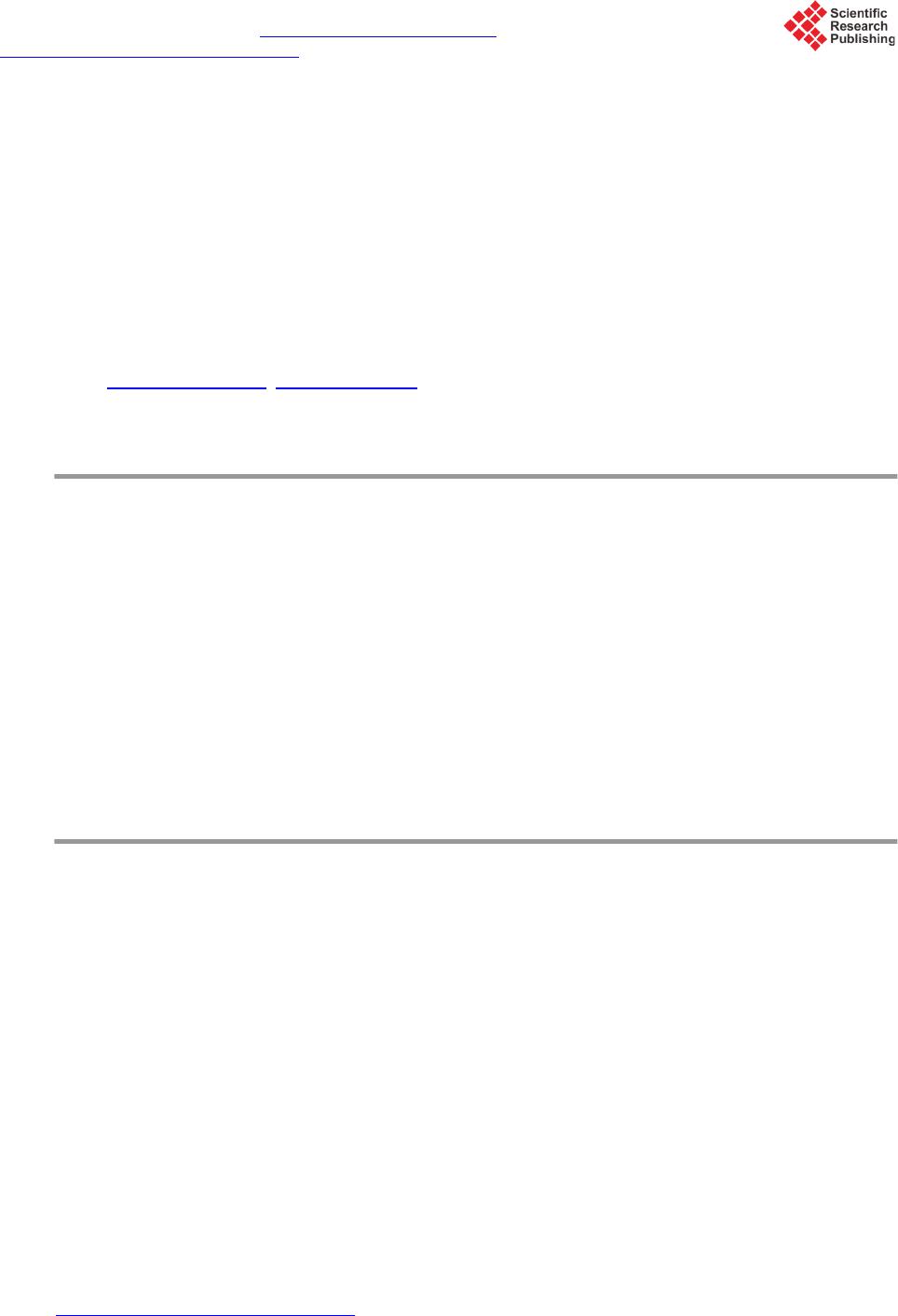
 Int. J. Communications, Network and System Sciences, 2015, 8, 70-78 Published Online April 2015 in SciRes. http://www.scirp.org/journal/ijcns http://dx.doi.org/10.4236/ijcns.2015.84009 How to cite this paper: Wang, P. and Zhang, X.J. (2015) Local Gateway Assisted Handover Key Derivation in Enterprise Femtocell Network. Int. J. Communications, Network and System Sciences, 8, 70-78. http://dx.doi.org/10.4236/ijcns.2015.84009 Local Gateway Assisted Handover Key Derivation in Enterprise Femtocell Network Peng Wang1, Xiaojuan Zhang2 1Bell Labs, Shanghai, China 2School of Computer Science, Qinghai Normal University, Xining, China Email: wp3891@seu.edu.cn, zhxj@qhnu.edu.cn Received March 2015 Abstract With the dense deployment of femtocells in enterprise femtocell network and the small coverage of femtocells, handover in enterprise femtocell network will be frequent. The general handover key derivation method which is used in handover procedures in LTE is not suitable for handover in this scenario because of its long time cost and the weak security. To solve this problem, this pa- per has proposed a new local gateway assisted handover key derivation schema in enterprise femtocell network. It can meet the fast derivation and good forward/backward key secrecy re- quirement of handover key derivation in enterprise femtocell network. The simulation result has verified that the proposed handover key derivation schema works better than the existing me- thod. Keywords Femtocell Network, Key Derivation, Mobility Management, Handover, Local Gateway 1. Introduction Enterprise Femtocell Network (EFN) is a novel and very promising application concept of femtocells [1]-[4]. It is defined as a group of femtocells that are able to form a partially autonomous network under the administration of a Local Network Operator (LNO). EFN is conceived as a complementary solution to existing macrocell dep- loyments in order to improve network coverage and capacity, offload traffic from the Evolved Packet Core (EPC), and provide new services to mobile subscribers. EFN can be deployed for many scenarios, such as shop- ping malls, corporate environments, convention centers, or university campuses. The handover key derivation method used in EFN is the same with the general one used in handover proce- dures in LTE [5]-[7]. There is no specific handover key derivation methods for Enterprise Femtocell Network (EFN). In recent years, a lot of researches on handover authentication for eNBs have been proposed [8]-[13]. But this general handover key derivation methods in LTE is not suitable for EFN. There are two different key derivation ways for X2-based handover and S1-based handover in LTE. In X2-based handover situation, the new key for target HeNB K*eNB is generated from the old communication key KeNB between UE and source HeNBs. The source HeNB may derive K*eNB by KeNB . So K*eNB is not forward secure. In S1-based handover sit- uation, the key K*eNB is derived from the KASME by MME. This provides good key backward/forward secrecy. 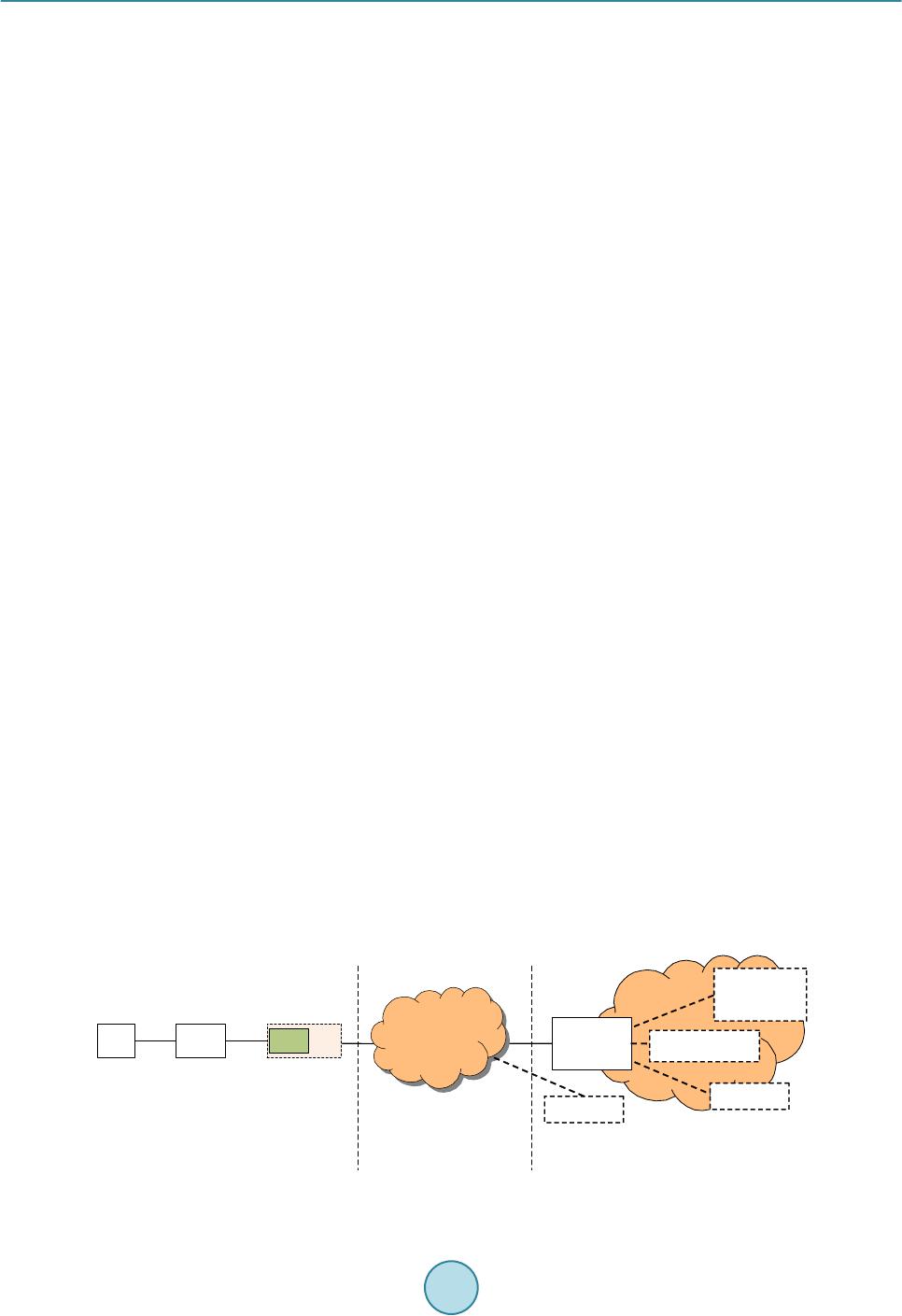 P. Wang, X. J. Zhang But because MME is far away from HeNB of EFN, this method will take a lot of time. With the dense deploy- ment of HeNB in EFN and the small coverage of HeNB, handover in EFN will be frequent. S1-based key deri- vation method will not be efficient enough for EFN. This paper is to solve the handover key derivation problem in EFN. To meet the fast derivation and good for- ward/backward key secrecy requirement of handover key derivation in EFN, a local key derivation device, named Local Key Distributor (LKD), is added into Enterprise Femtocell Gateway (EFGW). When UE hands its connection over to EFN, the MME (Mobility Management Entity) issues delegation power to the LKD. Then LKD uses a key KLKD, which is derived from KASME by MME, to generate new keys for target HeNBs in han- dover process in EFN. This helps to reduce the time of key derivation greatly. Meanwhile, it provides good key forward/backward secrecy, because the source HeNB can’t derive the new key for target eNB without knowing the key KLKD. The rest of this paper is organized as follows: In Section 2, we will introduce how to deploy a local key dis- tributor into EFN. In Section 3, we will detail the local gateway assisted handover key derivation schema in EFN. And the performance analysis will be presented in Section 4. 2. The Deployment of Local Key Distributor into EFN In order to provide EPC functionalities within the EFN and to keep data and signalling traffic within the local network, there was a new element introduced in the network architecture: Enterprise Femtocell Gateway (EFGW). In the literatures [1]-[4]. From the logical point of view, the EFGW is located in the edge of the EFN and acts as a network manager for local mobility, traffic management, access control, authentication, power management, and fault management. And it can also provide Local IP Access (LIPA) or Selected IP Traffic Of- fload (SIPTO) services, which are particularly relevant in femtocell networks [5]. Local Key Distributor (LKD) can be deployed separately or integrated into EFGW. Fig ure 1 presents the evolved system architecture with the deployment of the LKD integrated into EFGW. LKD will use the standard S1 interface to communicate with entities in EPC (Evolved Packet Core). The LKD behaves towards the EPC (Evolved Packet Core) like a standard eN B. And LKD communicates with HeNB in EFN with enhanced S1 in- terface. The details of the enhancement will be explained later in this proposal. 3. The Proposed Local Gateway Assisted Handover Key Derivation Schema Handover key derivation problem in EFN has three sub problems, including how to generate new keys during hand-in process (handover process from an eNB/HeNB out of EFN to a HeNB in EFN), how to generate new keys during inter-HeNB handover process in EFN, and how to generate new keys during hand-out process (handover process from a HeNB in EFN to an eNB/HeNB out of EFN. The key derivation procedures in these three scenarios are as follows: 3.1. Key Derivation Procedure in Hand-In Process Except generating new key for target HeNB, the other propose of this procedure is to derive a delegation key for LKD, which LKD will use to generate new keys for target HeNBs in place of MME in later intra-HeNB han- dover in EFN. The key derivation process is shown as Figure 2. Figure 1. Evolved system architecture of enterprise Femtocell network with addition of LKD. LKD EFGW HeNB UE SeGW Insecure link HeNB-GW H(e)MS H(e)MS MME/HSS Operator’s security domain Enterprise Femtocell Network Internet  P. Wang, X. J. Zhang Figure 2. Key Derivation during Hand-in process. The message sequence of key derivation during hand-in procedure into EFN is as follows: 1. UE sends Measurement Report message to the source eNB (S-eNB) in macrocell network. 2. S-eNB computes K*eNB with Key Derivation Function (KDF). 3. S-eNB sends Handover Required to MME K*eNB will be included in the Handover Required message. 4. MME computes K*+eNB and NH*+NCC 5. MME sends Handover Request message to LKD K*+eNB and NH*+NCC are included in the Handover Request message. K*+eNB will be sent to LKD, and used as the key KLKD. 6. When LKD receives K*+eNB and NH*+NCC from MME, it sets KLKD = K*+eNB, and then computes K*#eNB and NH*#NCC by K*#eNB = KDF (KLKD, NH*+NCC) and NH*#NCC= KDF (KLKD, K*#eNB). 7. LKD sends Handover Request message to T-HeNB 8. If T-HeNB can accept this handover, it sends Handover Request Acknowledge message to LKD 9. T-HeNB stores NH*#NCC and computes K*&eNB = KDF(K*#eNB, PCI, EARFCN-DL), and derive KUPenc, KRRCint, KRRCenc 10. LKD sends Handover Request Acknowledge message to MME 11. MME sends Handover Command message to S-eNB 12. S-eNB sends Handover Command message to UE 13. UE derives new keys for communication with T-HeNB, and then derive Kupenc, KRRCint, KRRCenc 14. UE sends Handover Confirm message to T-HeNB. 15. T-HeNB sends Handover Notify message to LKD. 16. LKD relays the Handover Notify message to MME. 3.2. Key Derivation Procedure of Inter-HeNB Handover in the EFN In the inter-HeNB handover process in EFN, the new keys for target HeNB are generated by LKD in this paper. The handover key derivation functionality of MME under the control of the EPC is transferred to LKD in the UE S-eNB T-HeNBLKD MME 1.Measurement Report 2.K *eNB =KDF(NH NCC , PCI,EARFCN-DL)3.Handover Required (K *eNB ) 5.Handover Request (K *+eNB ,NH *+NCC ) 4.K *+eNB =KDF(K ASME , K *eNB ) NH *+NCC = KDF(K ASME , K *+eNB ) 6. K LKD =K *+eNB K *#eNB =KDF(K LKD ,NH *+NCC ) NH *#NCC = KDF(K PKD , K *#eNB ) 7.Handover Request (K *#eNB ,NH *#NCC ) 9.Store NH NCC = NH *#NCC , and compute K *&eNB = KDF(K *#eNB , PCI, EARFCN-DL), and derive K UPenc , K RRCint , K RRCenc 8.Handover Request Acknowledge 10. Handover Request Acknowledge 11. Handover Command 12.Handover Command 13. derive K *eNB , K *+eNB, K *#eNB , K *&eNB, and NH *#NCC ,derive K upenc , K RRCint , K RRCenc 14.Handover Confirm15.Handover Notify16.Handover Notify 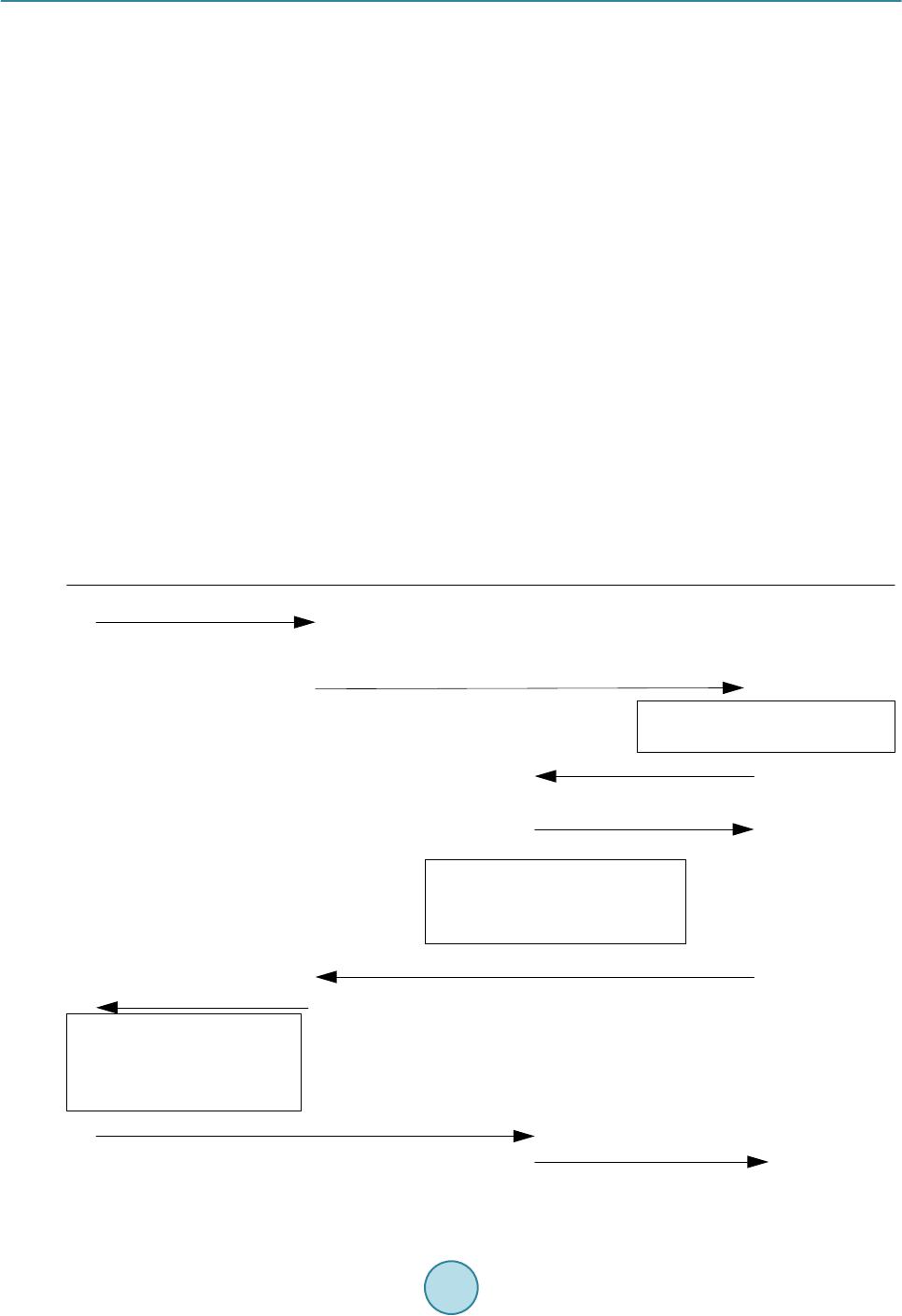 P. Wang, X. J. Zhang EFN. This helps to reduce the time for generating new keys for target HeNB. The inter-HeNB handover key de- rivation process in EFN is shown as Figure 3. The concrete procedures are as follow: 1. UE sends Measurement Report message to the source HeNB (S-HeNB) in macrocell network. 2. S-HeNB computes K*eNB with Key Derivation Function (KDF). K*eNB = KDF (NHNCC, PCI, EARFCN-DL), K*eNB is a material for generating new key of target HeNB, KDF must be a one-way function (e.g. a hash function like SHA256). 3. S-eNB sends Handover Required message to LKD K*eNB is included in the Handover Required message. 4. LKD computes K*#eNB and NH*#NCC by K*#eNB = KDF (KLKD, K*eNB) and NH*#NCC = KDF (KLKD, K*#eNB ). In this step, LKD acts as a proxy MME using KLKD to generate new key K*#eNB for target HeNBs. And NH*#NCC is a parameter used for next handover. 5. LKD sends Handover Request message to T-HeNB K*#eNB and NH*#NCC are included in the Handover Request message. 6. If T-HeNB can accept this handover, it sends Handover Request Acknowledge message to LKD 7. T-HeNB stores NH*#NCC and computes K*&eNB = KDF (K*#eNB, PCI, EARFCN-DL), and derive KUPenc, KRRCint, KRRCenc NH*#NCC will be used in next handover key derivation. KUPenc, KRRCint, KRRCenc are generated from K*&eNB, and the algorithms are presented in 3GPP TS 33.401. 8. LKD sends Handover Command message to S-HeNB 9. S-eNB sends Handover Command message to UE 10. UE derives new keys for communication with T-HeNB, and then derives KUPenc, KRRCint, KRRCenc UE generates new keys by K*eNB = KDF (NHNCC, PCI, EARFCN-DL), K*#eNB = KDF (KLKD, K*eNB), NH*#NCC Figure 3. Key Derivation during Inter-HeNB Handover in EFN. UE S-HeNB T-HeNB LKD 1.Measurement Report 2.K *eNB =KDF(NH NCC , PCI,EARFCN-DL)3.Handover Required (K *eNB ) 4.K *#eNB =KDF(K LKD ,K *eNB ) NH *#NCC = KDF(K LKD ,K *#eNB ) 5.Handover Request (K *#eNB ,NH *#NCC ) 7.Store NH NCC =NH *#NCC , K *&eNB =KDF(K *#eNB , PCI, UEID), and derive K UPenc , K RRCint , K RRCenc 6.Handover Request Acknowledge 8. Handover Command 9.Handover Command 10. derive K *eNB , K *#eNB , K *&eNB, and NH NCC =NH *#NCC ,derive K UPenc , K RRCint , K RRCenc 11.Handover Confirm 12.Handover Notify 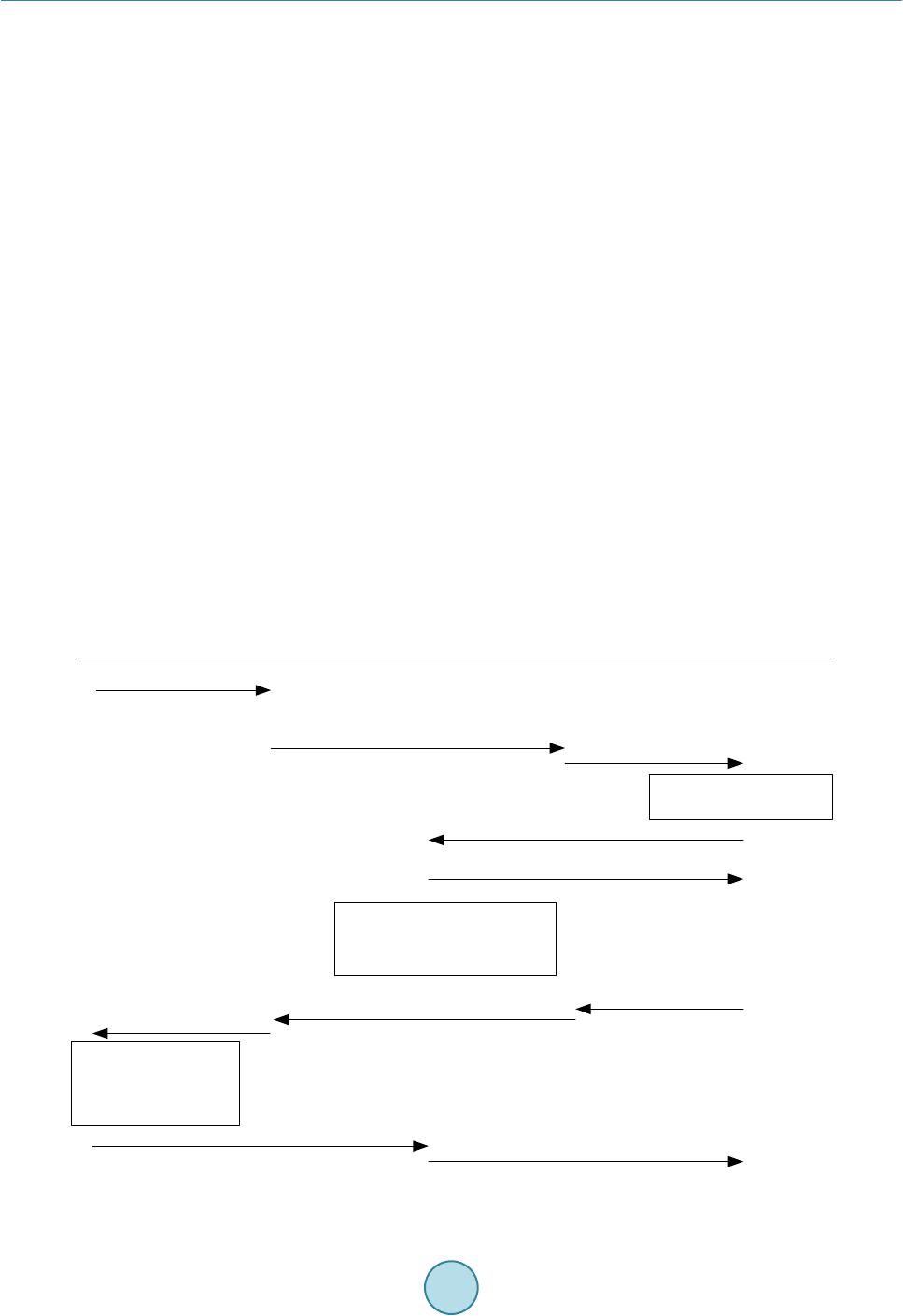 P. Wang, X. J. Zhang = KDF (KLKD, K*#eNB), K*&eNB = KDF(K*#eNB,PCI,EARFCN-DL), and derive KUPenc, KRRCint, KRRCenc from K*&eNB, and the algorithms are presented in 3GPP TS 33.401. 11. UE sends Handover Confirm message to T-HeNB 12. T-HeNB sends Handover Notify message to LKD 3.3. Key Derivation Procedure of Hand-Out Process The key derivation procedure of hand-out process is almost the same with that in handover between eNBs in LTE, as shown in Figure 4. The LKD just acts as a relayer to transmit messages between source HeNB (S- HeNB) and MME when LKD finds the target eNB (T-eNB) is not in EFN. The concrete procedures are as fol- lows: 1. UE sends Measurement Report message to the source HeNB (S-HeNB) in macrocell network. 2. S-HeNB computes K*eNB with Key Derivation Function (KDF). K*eNB = KDF (NHNCC, PCI, EARFCN-DL), K*eNB is a material for generating new key of target HeNB, KDF must be a one-way function (e.g. a hash function like SHA256). 3. S-HeNB sends Handover Required message to LKD K*eNB will be included in the Handover Required message. 4. LKD relays this Handover Required message to MME 5. MME computes K*+eNB and NH*+NCC K*+eNB = KDF (KASME, K*eNB), NH*+NCC= KDF (KASME, K*+eNB). K*+eNB and NH*+NCC will be transferred to target eNB directly, and NH*+NCC will be used for generating K*eNB in next handover. 6. MME sends Handover Request message to T-eNB K*+eNB and NH*+NCC are included in the Handover Request message. 7. If T-eNB can accept this handover, it sends Handover Request Acknowledge message to MME 8. T-eNB stores NH*#NCC, K*#eNB = K*+eNB, and computes K*&eNB = KDF(K*#eNB, PCI, EARFCN-DL), and de- rive KUPenc, KRRCint, KRRCenc NH*#NCC will be used in next handover key derivation. And KUPenc, KRRCint, KRRCenc are generated from K*&eNB, Figure 4. Key derivation during hand-out process. UE S-HeNB T-eNB LKDMME 1.Measurement Report 2.K *eNB =KDF(NH NCC , PCI,EARFCN-DL)3.Handover Required (K *eNB ) 6.Handover Request (K *+eNB ,NH *+NCC ) 5.K *+eNB =KDF(K ASME , K *eNB ) NH *+NCC = KDF(K ASME , K *+eNB ) 4.Handover Required (K *eNB ) 8.Store NH *#NCC =NH *+NCC , K *#eNB =K *+eNB , and compute K *&eNB =KDF(K *#eNB , PCI, UEID) , derive K upenc , K RRCint , K RRCenc 7.Handover Request Acknowledge 9. Handover Command 11.Handover Command 12. derive K *eNB , K *+eNB, K *#eNB , K *&eNB, and NH *#NCC ,derive K upenc , K RRCint , K RRCenc 13.Handover Confirm 14.Handover Notify 10. Handover Command  P. Wang, X. J. Zhang and the algorithm is presented in 3GPP TS 33.401. 9. MME sends Handover Command message to LKD EFN-Flag = 0 is included in Handover Command message. 10. LKD relays the Handover Command message to S-eNB 11. S-eNB sends Handover Command message to UE 12. UE derives new keys for communication with T-eNB, and then derive Kupenc, KRRCint, KRRCenc UE generates new keys by K*eN B = KDF (NHNCC, P CI, EA RF CN -DL), 13. UE sends Handover Confirm message to T-eNB 14. LKD relays the Handover Notify message to MME. 4. Performance Analysis In the following parts, the performance of this paper is analyzed in terms of communication time cost and com- putational time cost, by comparing it with previous LTE methods in 3GPP TS 33.401. And the forward/bac k- ward secrecy of this solution is analyzed theoretically. 4.1. Key Derivation Cost Analysis There are two parts of key derivation cost, computation cost and communication cost. The communication cost includes the delay of delivery between the eNB/HeNB and the MME , the communication cost between the UE and the eNB , the cost between eNB/HeNB , the communication cost between HeNB and LKD , the communication cost between LKD and MME . Since MME is far away from eNB/HeNB, is range in . And because LKD and HeNBs are connected with each other in the same way (like Ethernet) in EFN, and can be considered to be equ a l . With the deployment of LKD in EFN, the HeNB communi- cates with MME through LKD, then . Since LKD is far away from MME, and it communicates with MME by an Internet link, is always far bigger than . Table 1 presents the communication costs of different method in different handover process. Table 1 shows that comparing with the previous key derivation method in LTE, LKD-based method reduces the key derivation time greatly in inter-HeNB handover in EFN without introducing extra communication cost in hand-in and hand-out process. To test the computation cost of key derivation, the time used for the primitive cryptography operations has been measured by using C/C++ OPENSSL library tested on an Celeron 1.1 GHz processor as an UE, Dual-Core 2.6 GHz as an eNB, a LKD and a MME. The computation cost of generating a key of UE is 0.0356 ms, and computation cost of generating a key of LKD, eNB or MME is 0.0121 ms. To show the performance of this paper visually, we gives a simulation example of communication cost as follows: The one-way latency of the LTE radio access is modelled to fit normal distribution . The broadband link transmission delay in EFN is modelled to fit normal distribution . The communica- tion delay of Internet backhaul and mobile operator networks is modelled to fit normal distribution . And the load-dependent queuing delay is modelled as an M/D/1 system. Figures 5-7 presents the performance of different method in inter-HeNB handover, hand-in and hand-out process in EFN. Table 1. Compare of Communication Cost in inter-HeNB handover in EFN. Inter-HeNB handover key derivation in EFN Previous X2-based method of LTE 3 223 22*() 324 δελ δααβ δα ++ =+ ++ >+ Previous S1-based method of LTE () 3535 355 δλ δαβ δα +=+∗ + >+ LKD-based method of this paper Hand-in key derivation of EFN Previous S1-based method of LTE LKD-based method of this paper Hand-out key derivation of EFN Previous S1-based method of LTE LKD-based method of this paper 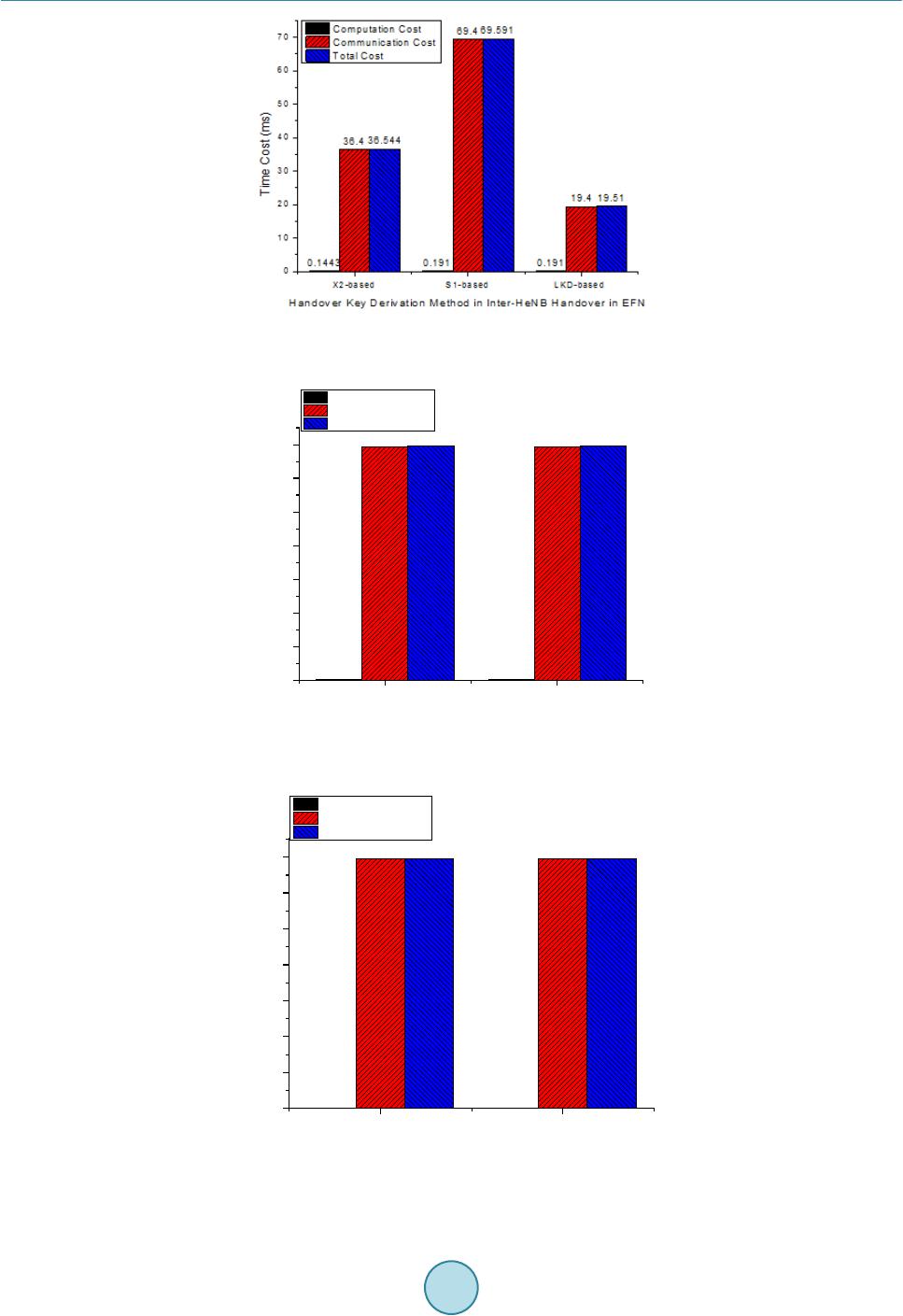 P. Wang, X. J. Zhang Figure 5. The Time Cost of Handover Key Derivation Methods in Inter-HeNB Handover Process in EFN. Figure 6. Time cost of handover key derivation methods in hand-in process. Figure 7. The time cost of handover key derivation methods in hand-out process. 0.191 0.2865 69.4 69.4 69.591 69.6865 S1-basedLKD-based 0 10 20 30 40 50 60 70 Time Cost(ms) Handover Key Derivation Method in Hand-in Process Computation Cost Communication Cost Total Cost 0.191 0.191 69.4 69.4 69.591 69.591 S1-based LKD-based 0 10 20 30 40 50 60 70 Time Cost (ms) Handover Key Derivation Method in Hand-out Process Computation Cost Communication Cost Total Cost  P. Wang, X. J. Zhang Figure 5 presents the inter-HeNB handover key derivation time cost of the previous LTE X2-based method, previous LTE S1-based method and our LKD-based method (this paper). Figure 5 shows that computation cost is nearly zero, and the communication cost accounts for the main parts of total cost. And it shows that this paper greatly reduces the communication cost, comparing to the previous X2-based method and S1-based method in LTE. This is because LKD localizes the key derivation signaling in EFN, not like the previous S1-based or X2-based method in LTE. Figure 6 presents the handover key derivation time cost of previous S1-based method and LKD-based me- thod (this paper) in hand-in process. Figure 6 shows that this paper only increases 0.0955 ms in total. This is because LKD-based method only adds one step to the process of previous S1-based method to compute keys for target HeNBs. This result shows that LKD-based key derivation method generates keys for the target HeNB in EFN, with almost the same performance of previous S1-based method, meanwhile it helps the LKD get its proxy key KLKD from MME. This is very meaningful because this paper introduces very little cost to allocate proxy key for LKD, which will reduce the communication cost in later inter-HeNB handover in EFN. Figure 7 presents the handover key derivation time cost of previous S1-based method and LKD-based me- thod (this paper) in hand-out process. The results show that the costs of the two methods are the same. This is because LKD only acts as a relay for the delivery of key derivation signaling messages. 4.2. Forward/Backward Secrecy Analysis Based on the knowledge of forward/backward secrecy of S1-based handover key derivation, the forward/back- ward secrecy of the LKD-based handover key derivation method (this paper) is analyzed as follows: In the hand-in case, the MME generates KLKD and NH*+NCC (KLKD = K*+eNB = KDF(KASME, K*eNB), NH*+NCC = KDF (KASME, K*+eNB)) for LKD by KAMSE, so KLKD and NH*+NCC are not known to both the source eNB and the target HeNB, and then LKD uses the KLKD and NH*+NCC to generate new keys K*#eNB and NH*#NCC (K*#eNB = KDF(KLKD, NH*+NCC), NH*#NCC = KDF(KLKD , K*#eNB)) for target HeNB, so the keys K*#eNB and NH*#NCC are also not known to source eNB. Then the target HeNB computes K*&eNB = KDF (K*#eNB, PCI, EARFCN-DL). So K*&eNB can’t be derived from the known parameters by the source eNB. The key forward secrecy is provided in hand-in case.In the inter-HeNB handover case, the LKD generates new keys K*#eNB and NH*#NCC (K*#eNB = KDF(KLKD,K*eN B), NH*#NCC = KDF(KLKD, K*#eNB)) for target HeNB. Because source HeNB don’t know KLKD, K*#eNB and NH*#NCC are not known to source HeNB. Then target derives its new key K*&eNB = KDF (K*#eNB, PCI, UEID) by which is also not known to source HeNB. So the key forward secrecy is provided in in ter-HeNB han- dover case. In the hand-out case, the new key derivation process in LKD-based method is similar with that in S1-based handover in LTE. So the key forward secrecy is provided in hand-out case. Besides, the target HeNB knows nothing about the key materials and the key of source eNB (HeNB) in all the process, so the key back- ward secrecy is provided in LKD-based handover key derivation method in this paper. In conclusion, good key forward/backward secrecy is provided in LKD-based handover key derivation method in this paper. Acknowledgements This work is supported by China Scholarship Council (CSC) and by National Natural Science Foundation of China (No.6126104) and by the Science and Technology Project Foundation of Qinghai Province (No. 2013-Z- 605 and No.2011-Z-719). References [1] Jaime, F., Josep, M.B., José, N.M. and Frank, Z. (2012) Traffic and Mobility Management in Networks of Femtocells. Mobile Networks and Applications, 17, 662-673. http://dx.doi.org/10.1007/s11036-012-0396-9 [2] Broadband Evolved FEMTO Networks (BeFEMTO) Project (2011) The BeFEMTO System Architecture. http://www.ict-befemto.eu/publications/deliverables.html [3] Zdarsky, F., Maeder, A., Al-Sabea, S. and Schmid, S. (2011) Localization of Data and Control Plane Traffic in Enter- prise Femtocell Networks. Proceedings of IEEE 73rd Vehicular Technology Conference (VTC Spring 2011), Budapest, 15-18 May 2011. http://dx.doi.org/10.1109/VETECS.2011.5956622 [4] 3rd Generation Partnership Project (2012) Technical Specification Group Service and System Aspects; 3GPP System Architecture Evolution (SAE); Security Architecture (Rel 12) 3GPP TS 33.401 V12.6.0. [5] 3rd Generation Partnership Project (2011) Technical Specification Group Services and System Aspects; General Pack-  P. Wang, X. J. Zhang et Radio Service (GPRS) Enhancements for Evolved Universal Terrestrial Radio Access Network (E-UTRAN) Access (Rel 10), 3GPP TS 23.401 V10.5.0. [6] 3rd Generation Partnership Project (2011) Technical Specification Group Radio Access Network; Evolved Universal Terrestrial Radio Access (E-UTRA) and Evolved Universal Terrestrial Radio Access Network (E-UTRAN); Overall description; (Rel 10), 3GPP TS 36.300 V10.4.0. [7] Forsberg, D. (2010) LTE Key Management Analysis with Session Keys Context. Computer Communications, 33, 1907-1915. http://dx.doi.org/10.1016/j.comcom.2010.07.002 [8] Bohk, A., Buttyn, L. and Dra, L. (2007) An Authentication Scheme for Fast Handover between WiFi Access Points. Proceeding of ACM Wireless Internet Conference (WICON 2007), October, 22-24. http://dx.doi.org/10.4108/wicon.2007.2282 [9] Cai, L., Machiraju, S. and Chen, H. (2010) CapAuth: A Capability-Based Handover Scheme. Proceedings of IEEE INFOCOM 2010, USA, March, 1-5. http://dx.doi.org/10.1109/INFCOM.2010.5462208 [10] Jin, C., Hui, L., Maode, M., Yueyu, Z. and Chengzhe, L. (2012) A Simple and Robust Handover Authentication be- tween HeNB and eNB in LTE Networks. Computer Networks, 56, 2119-2131. http://dx.doi.org/10.1016/j.comnet.2012.02.012 [11] Choi, J. and Jung, S. (2010) A Handover Authentication Using Credentials Based on Chameleon Hashing. IEEE Communications Letters, 14, 54-56. http://dx.doi.org/10.1109/LCOMM.2010.01.091607 [12] Roh, H. and Jung, S. (2010) RSA-Based Proxy Signature for Media Independent Handover. Proceeding of the First International Conference on Smart IT Applications (SITA 2010), September. [13] Qi, J., Zhang, Y., Fu, A. and Liu, X. (2011) A Privacy Preserving Handover Authentication Scheme for EAP-Based Wireless Networks. Proceeding of GLOBECOM 2011, December, 1-6.
|