Paper Menu >>
Journal Menu >>
 Wireless Sensor Network, 2009, 2, 61-121 doi:10.4236/wsn.2017 lished Online July 2009 (http://www.SciRP.org/journal/wsn/). Copyright © 2009 SciRes. Wireless Sensor Network, 2009, 2, 61-121 009.12 Pub A Novel DSA-Driven MAC Protocol for C o g ni t i v e Radio Networks Hua SONG, Xiaola LIN School of Information Science and Technology, Sun Yat-sen University, Guangzhou, China Email: songhua@mail2.sysu.edu.cn, linxl@mail.sysu.edu.cn Received February 19, 2009; revised April 29, 2009; accepted May 6, 2009 Abstract With the deployment of more wireless applications, spectrum scarcity becomes an issue in many countries. Recent reports show that the reason for this spectrum shortage is the underutilization of some spectrum re- sources. Fortunately, the emergence of open spectrum and dynamic spectrum assess (DSA) technology in cognitive radio networks relieves this problem. In this paper, we propose a novel DSA-driven cognitive MAC protocol to achieve highly efficient spectrum usage and QoS provisioning. In the proposed protocol, secondary users are divided into several non-overlapping groups, and all leftover channels are allocated among groups taking the groups’ bandwidth requirements into consideration. Moreover, the allocation of vacant channels can be adjusted dynamically when members join/leave groups or primary users return/leave the current network. Simulations show that the proposed MAC protocol greatly improves the quality of ser- vice for secondary users and maximizes the utilization ratio of spectrum resources. Keywords: Cognitive Radio, DSA-Driven MAC Protocol, QoS Provisioning, Dynamic Spectrum Access 1. Introduction The deployment of wireless services and devices has been increasing rapidly in recent years, but current us- able spectrum has almost been allocated to various spec- trum-based services, which greatly blokes the develop- ment of wireless communication. However, extensive reports indicate that the reason for this spectrum shortage is not the scarcity of the radio spectrum, but the low utilization (only 6%) of the licensed radio spectrum in most of the time [1]. This underutilization of spectrum resources has prom- pted the emergence of cognitive radio. In 2003, Federal Communications Commission (FCC) suggested a new concept/policy for dynamically allocating the spectrum [2]. Thus, a promising implementation technique called cognitive radio is proposed to alleviate the scarcity of spectrum bandwidth. Based on cognitive radio, open spectrum and dynamic spectrum access (DSA) technolo- gies have shown great interest recently [3]. In this tech- nology, primary users (licensed users) have high priority to use their spectrum; secondary users (unlicensed users) are allowed to opportunistically access the spectrum only when the spectrum is not used by primary users. Although the research community has proposed sev- eral cognitive MAC protocols to address various issues in cognitive network [4-8], commonly, they pay more attention to save the number of transceivers, and improve throughput of the whole system or decrease session de- lays. However, all these protocols do not lay emphasize on quality of service for secondary users and high usage of leftover spectrum with dynamically adjusting alloca- tion. For instance, in [5], a decentralized protocol, called hardware-constrained cognitive MAC protocol (HC- MAC), for managing and coordinating spectrum access is proposed. Under HC-MAC, a pair of secondary users can use several channels to communicate simultaneously after they have sensed the vacant channels, but if the leftover spectrum allocated to the pair of secondary users is more than they can utilize, this part of surplus spec- trum is wasted and cannot be used by other users whose * This work was supported in part by NSFC under Projects 60773199, U0735001, and 985 II fund under Project 3171310.  H. SONG ET AL. 113 Copyright © 2009 SciRes. Wireless Sensor Network, 2009, 2, 61-121 bandwidth requirements have not been satisfied. To effectively provide QoS for secondary users and achieve highly efficient spectrum usage, in this paper, we propose a novel DSA-driven MAC protocol which is of significant importance in ad hoc cognitive network to guarantee the QoS requirements of secondary users. Dif- ferent from the existing cognitive MAC protocols, the main advantages of the proposed MAC protocol include: 1) Maximizing the u tilization ratio of spectrum resources; 2) Using bonding/aggregation and dynamical channel allocation techniques to guarantee the QoS requirements of secondary users; 3) Ensuring the fairness of channel allocation for groups. The rest of the paper is organized as follows. Related work is discussed in Section 2. The preliminaries and system model is introduced in Section 3. The proposed MAC protocol is presented in Section 4. Performance of the proposed MAC protocol is evaluated by experiments in Section 5. Fi nally, conclusi on is drawn in Secti o n 6. 2. Related Work Over the past several years there have been increasing interests in cognitive radio. In addition, wireless MAC protocol has a principal part in spectrum reuse and effi- ciency management. Therefore, various cognitive MAC protocols have been proposed for more flexible and effi- cient use of spectrum resources [4-8]. Hamdaoui and Shin [4] propose the OS-MAC protocol. This protocol divides the secondary users into several groups, at each Opportunistic Spectrum Period, the channel used by a group can be adjusted dynamically according to the channels' states of the whole system. The OS-MAC protocol also discusses the non-coopera- tive mode between primary users and secondary users, but it does not give a feasible solution (we will present our solution on this problem in subsequent paper). Fur- thermore, as only one channel can be used in a group at anytime, the spectrum resources cannot be used to the maximum with taking secondary users’ QoS into consid- eration. Jia et al. [5] present the HC-MAC protocol. This pro- tocol uses k-stage look-ahead method to sense unused channels with high efficiency and takes hard- ware-constraints into consideration (including sensing constraint and transmission constraint). Besides the flaw mentioned in Section 1, there is a problem called sensing exposed terminal problem in this protocol. That is, if a secondary pair senses unused channels while their neighbors who didn't receive the C-RTS/C-CTS packets are performing their operations freely, this pair of users can not sense the vacant channels accurately. Su and Zhang [6] propose the cross-layer based op- portunistic MAC protocols. In the protocols two sensing policies, the random sensing policy and the negotia- tion-based sensing policy, are presented. Like [5], the protocols also use bonding/aggregation technique to transmit data through several channels. In essence, the main contribution of their work is to reveal the tradeoff between throughput and delay, which provides the guidelines to support the different QoS requirements over cognitive radio based wireless networks. But, at anytime, only a pair of secondary users can use vacant channels, thus the leftover channels cannot be used effi- ciently. Thoppian et al. [7] propose a CSMA-Based MAC protocol. In the protocol, each node maintains a list of favorable channels for each of its neighbors based on the previous history of communication on each of the chan- nels, and a secondary pair chooses the most favorable channel for communication. As it does not consider the channels’ utility of the whole system, it also cannot use the radio spectrum resources efficiently. Similarly, the methods in [9-12] all do not address the issues of the QoS of secondary users and the spectrum resources’ utility of the entire system. 3. Preliminaries and System Model We first present an introduction to the channel bond- ing/aggregation technique and the main framework of the system. 3.1. Channel Bounding/Aggregation Technique From the definition of channel bonding/aggregation tech- nique in [13] we can see that ch annel bonding is used for contiguous channels, but channel aggregation is for dis- crete ones. So, if several contiguous channels can be used, channel bonding is the appropriate technique. Oth- erwise, we can adopt channel aggregation technique. In MAC perspective, channel bonding incurs no addi- tional overhead as all control messages are transmitted only once, and an access point (AP) with channel bond- ing also has much greater control and more freedom on resource allocation and transmit power. In contrast, with channel aggregation, the overhead increases considerably with the number of channels used, and for an effective channel aggregation solution, features such as sophisti- cated scheduling, load balancing and channel manage- ment are needed. Figure 1(a) and Figure 1(b) compare the aggregate throughput and efficiency of the two techniques respec- tively. From Figure 1, we can see that channel aggrega- tion incurs much more overhead than channel bonding and these two techniques are designed for medium-high loads. Also, this figure presents that ch annel bonding can offer much better channel utilization with less overhead. In [5], hardware con strains of bonding/aggreg ation are pointed out: spect rum used by a secondary user has maxi-  H. SONG ET AL. 114 Copyright © 2009 SciRes. Wireless Sensor Network, 2009, 2, 61-121 10 15 20 25 30 35 40 45 50 55 10 20 30 40 50 60 Aggregate throughput (Mbps) Overall load (Mbps) 2 aggregated channels 3 aggregated channels 2 bonded channels 3 bonded channels (a) Aggregate throughput against overload. 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 10 20 30 40 50 60 Efficiency Overall load (Mbps) 2 aggregated channels 3 aggregated channels 2 bonded channels 3 bonded channels (b) Efficiency against overload. Figure 1. Channel bonding vs. channel aggregation. mum bandwidth limit and maximum fragmentation number limit. For convenience, we will not take these constrains into consideration presently, but they are in- cluded in our future research plan. 3.2. Secondary Users’ Devices The whole available radio spectrum in a CR network is divided into a number of non-overlapping data channels (DCs) and a common control channel (CC), for transmit- ting data information and control information respec- tively. Further, we assume the CR network is a wireless ad hoc network formed by a great many secondary users, each of which is equipped with two wireless transceivers. One is called data transceiver used to sense leftover DCs and exchange data through these channels, but this transceiver is not able to operate in sensing and transmit- ting mode concurrently. The other transceiver is called control transceiver used to send or receive messages from CC. Note that, the transceivers are half-duplex, thu s they are not able to send and receive messages simulta- neously. We also assume that every secondary user can use aggregated spectrum and has full spectrum sensing ability. 3.3. Control Mechanism Based on distributed environment, we divide secondary users into several non-overlapping groups, and each gro- up has a leader (the leader can be adjusted dynamically) who is responsible for group members' management, group channel's management and group channels' appli- cation. Moreover, there is a manager in the whole wire- less ad hoc network who is elected among leaders and is used to manage all the leftover channels and allocate these channels to groups fairly. The manager communi- cates with leaders through CC, and the control messages in a group are exchanged through DCs. So the common control channel (CC) is light loaded and will not be the bottleneck of the network. As the manager and leaders can be changed dynamically, each of them is impossible to become a single failure point. Thus, the system is pro- vided good scalability and extensibility. 4. Our Proposed DSA-Driven MA C Protocol In this section, we present the design of our proposed DSA-driven MAC protocol for cogn itive radio networks. 4.1. Definitions and Notations In order to present the proposed MAC protocol more clearly, we would now like to introduce so me definitions and notations here. 1) Tables: These tables are used for the management of the whole network. GroupTable: This table is maintained by the man- ager. It contains the group number, the leader and members in the group. MemberTable: This table is maintained by the leader. It contains the list of group members. Note that each member has a MemberTable. 2) Control frames: These frames are used for the con- trol of protocol's realization. The first five frames are sent through CC, the LeaveReq frame is sent through DC and the last one can be sent through CC or DC. Invite: It contains the manager's id. JoinReq: It contains the id of a secondary user whom the request user wants to communicate with. JoinACK: It contains the leader's id of chosen group. Sense: It contains the group number and the sensing range of channels. Allocate: It contains the group number and a list of channels. LeaveReq: A member uses this frame to apply for leaving the current group. Notify: It contains ManagerChanged and Leader- Changed fields. 3) Timers: These timers are used for the maintenance of the whole system. ManagerHeartBeatTimer: This timer is started at the manager when it broadcasts the Invite frame on CC. In essence, ManagerHeartBeatTimer has two functions, the first one is to let secondary users  H. SONG ET AL. 115 Copyright © 2009 SciRes. Wireless Sensor Network, 2009, 2, 61-121 know who is the manager currently and the other one is to make leaders assure the manager is still alive. ManagerFailureTimer: This timer is started at a leader when it receives an Invite frame on CC. If this timer expires before the leader receives another Invite frame, it knows that the manager is failed. LeaderHeartBeatTimer: This timer is started at a leader when it broadcasts the LeaderHeartBeat frame on DC in a group. As soon as members re- ceive the LeaderHeartBeat frames they know that the leader is alive. LeaderFailureTimer: This timer is started at a member when it receives a LeaderHeartBeat frame from DC. If this timer expires before the member receives another LeaderHeartBeat frame, it knows that the leader is failed. 4.2. Overview There are two kinds of control frames in our proposed MAC protocol: inter -g roup co n trol fr ame and in tr a-gr oup control frame. Inter-group control frames are transmitted between the leaders and manager through CC, while in- tra-group control frames are exchanged between the leader and members through DCs in a group. If several leaders want to send messages to the manager, they must negotiate with each other via the contention-based algo- rithms, such as IEEE 802.11 Distributed Coordination Function (DCF) [14] and p-persistent Carrier Sense Mul- tiple Access (CSMA) protocols [15]. In order to guaran- tee reliable transmission, we use acknowledge mecha- nism in control messages’ exchange. Figure 2 shows the principle of our proposed MAC protocol. It divides time into Periods and each of which consists of three consecutive phases: Sensing Phase, Al- locating Phase and Transmitting Ph ase. At any time, only one pair of members in a group can exchange informa- ti on. In order to let all membe rs in the same group use ch- Period Sensing Phase Allocating Phase Transmitting Phase DC DC CC 12 m … 1 n t Data Channels unused by primary users Common Control Channel Managing group members’ joining and leaving Reelecting the leaders and manager if needed Manager allocates channels for each group Manager coordinates all groups sensing vacant channels Each leader divides this phase into several slots according to the number of users in the group, and only a pair of users can communicate in a slot Each group switches to the allocated channels Secondary users start sensing vacant channels Figure 2. The principle of our proposed MAC protocol. annels fairly, the Transmitting Phase is divided into sev- eral time slots according to the number of users. Fur- thermore, a few of time slots are reserved for intra-group control frames exchang e. In Sensing Phase, manager coordinates all groups sensing vacant channels (it's an efficient method to check all unused channels in a short time). Then, based on the feedback of sensing results and bandwidth requirements from all groups, the manager calculates out a best alloca- tion scheme and allocates the available channels to each group in Allocating Phase. When groups gain their new allocated channels, they switch to these channels imme- diately and begin to transmit information in Transmitting Phase. 4.3. Details of the Proposed MAC Protocol In the proposed MAC protocol, each secondary user in the network will be in one of the follo wing phases at any given time. 1) Initialization Phase: If a secondary user is not in- volved in any group and seeks channels to transmit in- formation, it will listen to CC. a) If the secondary user receives an Invite frame from CC, it sends a JoinReq control frame to apply for joining a group. After receiving the JoinReq frame, the manager looks up its GroupTable to decide which group this user should join in according to the user's request. If the manager finds an appropriate group, it updates its GroupTable with a JoinACK control frame to send back. When the secondary user receives the JoinACK frame, it communicates with the leader of the chosen group through CC and tunes its data transceiver to the accord- ing DCs. However, the manager may not find a suitable group for the secondary user to join in, then it checks whether it's possible to establish a new group for this user. If so, the manager creates a new group and makes this secondary user a leader; otherwise a REJ control frame is responded. b) If the ManagerFailureTimer expires before the sec- ondary user receives an Invite frame, the user knows that it is the only secondary user in the network. Then it es- tablishes a new group, makes itself a leader and manager, creates a MemberTable and a GroupTable, and broad- casts an Invite frame on CC. 2) Sensing Phase: all secondary users cooperate to sense the channels unused by primary users. a) The manager allocates sensing channels among all groups according to GroupTable, and sends a Sense frame to each leader via CC. b) Each group senses vacant channels whose range is indicated by the Sense frame. c) Leaders report sensing results to the manager through CC. 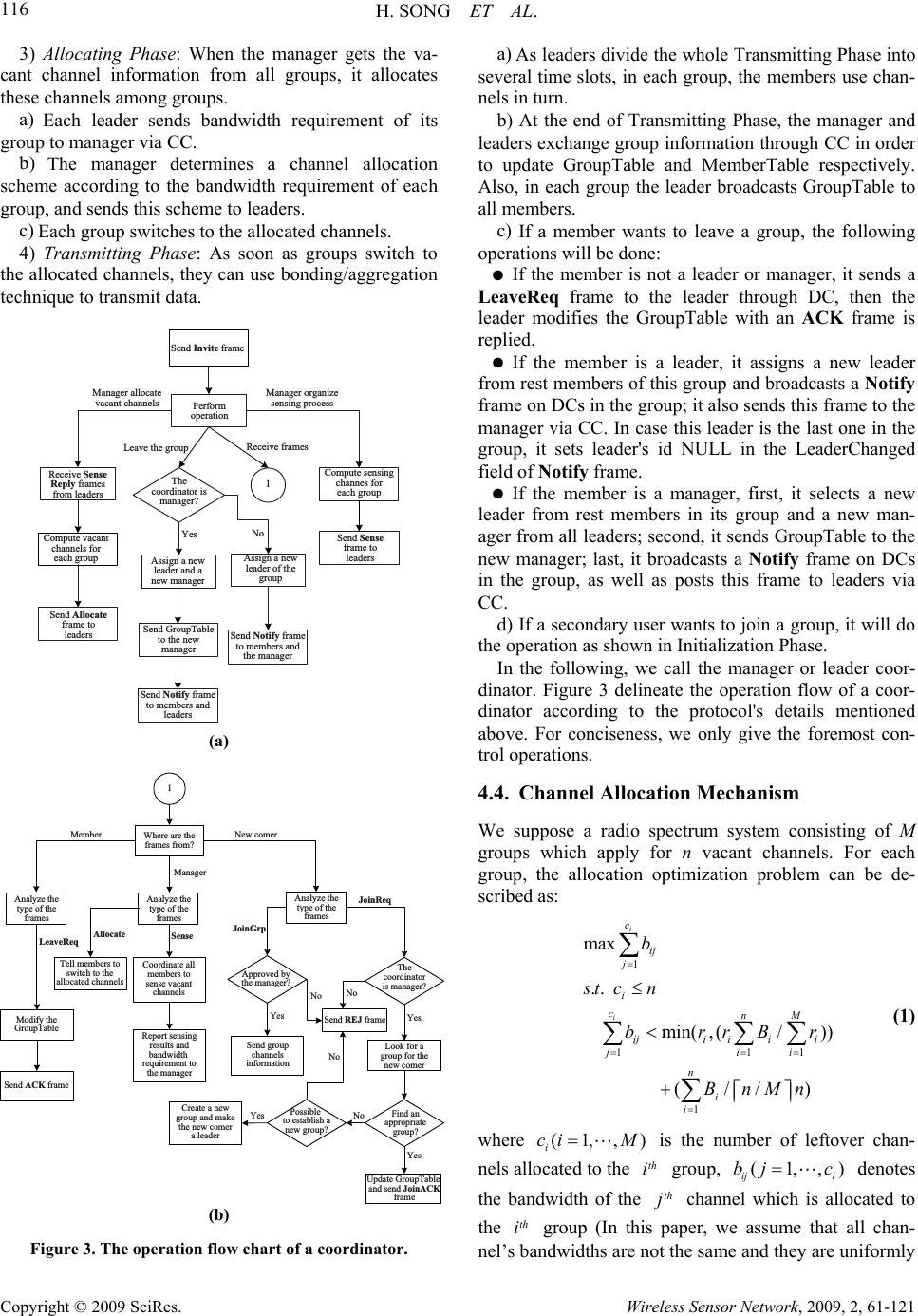 H. SONG ET AL. 116 Copyright © 2009 SciRes. Wireless Sensor Network, 2009, 2, 61-121 3) Allocating Phase: When the manager gets the va- cant channel information from all groups, it allocates these channels among groups. a) Each leader sends bandwidth requirement of its group to manager via CC. b) The manager determines a channel allocation scheme according to the bandwidth requirement of each group, and sends this scheme to leaders. c) Each group switches to the allocated channels. 4) Transmitting Phase: As soon as groups switch to the allocated channels, they can use bonding/aggr egation technique to transmit data. Send Invite frame Perform operation Manager allocate vacant channels Receive Sense Reply frames from leaders Compute vacant channels for each group Send Allocate frame to leaders Leave the group The coordinator is manager? Yes Assign a new leader and a new manager Send GroupTable to the new manager Send Notify frame to members and leaders Receive frames 1 No Assign a new leader of the group Send Notify frame to members and the manager Manager organize sensing process Compute sensing channes for each group Send Sense frame to leaders (a) 1 Member Where are the frames from? Analyze the type of the frames LeaveReq Modify the GroupTable Send ACK frame Allocate Sense Manager Tell members to switch to the allocated channels Coordinate all members to sense vacant channels Report sensing results and bandwidth requirement to the manager Analyze the type of the frames New comer Analyze the type of the frames JoinReq JoinGrp Approved by the manager? Yes Send group channels information No No Send REJ frame No The coordinator is manager? Yes Look for a group for the new comer Find an appropriate group? Yes Update GroupTable and send JoinACK frame Possible to establish a new group? Create a new group and make the new comer a leader NoYes (b) Figure 3. The operation flow chart of a coordinator. a) As leaders divide the whole Transmitting Phase into several time slots, in each group, the members use chan- nels in turn. b) At the end of Transmitting Phase, the manager and leaders exchange group information through CC in order to update GroupTable and MemberTable respectively. Also, in each group the leader broadcasts GroupTable to all members. c) If a member wants to leave a group, the following operations will be done: ● If the member is not a leader or manager, it sends a LeaveReq frame to the leader through DC, then the leader modifies the GroupTable with an ACK frame is replied. ● If the member is a leader, it assigns a new leader from rest members of this group and broadcasts a Notify frame on DCs in the group; it also sends this frame to the manager via CC. In case this leader is the last one in the group, it sets leader's id NULL in the LeaderChanged field of Notify frame. ● If the member is a manager, first, it selects a new leader from rest members in its group and a new man- ager from all leaders; second, it sends GroupTab le to the new manager; last, it broadcasts a Notify frame on DCs in the group, as well as posts this frame to leaders via CC. d) If a secondary user wants to jo in a group, it will do the operation as shown in Initialization Phase. In the following, we call the manager or leader coor- dinator. Figure 3 delineate the operation flow of a coor- dinator according to the protocol's details mentioned above. For conciseness, we only give the foremost con- trol operat i o ns. 4.4. Channel Allocation Mechanism We suppose a radio spectrum system consisting of M groups which apply for n vacant channels. For each group, the allocation optimization problem can be de- scribed as: 1 11 1 max .. min( ,(/)) (//) i i c ij j i cnM iji iii ji n i i b st cn brrB BnMn 1 i r (1) where (1,,) i ci M th i is the number of leftover chan- nels allocated to the group, denotes the bandwidth of the channel which is allocated to the group (In this paper, we assume that all chan- nel’s bandwidths are not the same and they are uniformly (1,, ij i bj c) th j th i  H. SONG ET AL. 117 Copyright © 2009 SciRes. Wireless Sensor Network, 2009, 2, 61-121 distributed), is the bandwidth require- ment of the group, and is the band- width of the vacant channels. The last constraint indicates that the bandwidth allocated to each group cannot exceed a certain upper bound which is defined as . The augend of the upper bound represents each group’s de- served bandwidth according to its requirement and the addend is an adjusting factor which guarantees the chan- nel allocation is accurate and even. (1,,) i ri M th i th i 11 / )) nM i i ii B r 1 {, ,} t Px x } (1,,) (1,,) i Bi n 1 (/ / n i i B n ()tt n min( ,() ii rr Mn {0,1 i The object of problem (1) is to maximize the utility of vacant channels. For this kind of problems, branch and bound algori thm [16 , 17 ] is an eff ectiv e meth od to search the optimal solutions. In this paper, we propose a branch and bound algorithm, which is more suitable for the channel allocation optimization problem in cognitive radio networks than the general one. For each group, the detail steps are as follows: 1) Initialization: The feasible solution can be pre- sented as, Whereis the number of available vacant channels for the current group, and x it. If the value of i x is 1, it means that the channel is allocated to the current group. We define. In this algorithm, the channels are sorted by which is the band- width of the channel, that is,; because the channel with higher bandwidth has larger impact to the optimal solution. Let to indicate the initial feasible set and initialize . The initial lower and upper bound of the optimal solution can be represented as th i 0{0,0,P i Bi th i 00 ,0} (1,,)t jk BB 0 {S 1k ,,jk 0 }P ,jk I 01 t i 1k PS k (2) i B (3) 2) Branching: Based on the characteristics of the chan- nel allocation optimization problem, the branching method puts each in duplicate to setand set the value of k S x . (1) {|PP (2) {|PP 0,} kk xxP 1,} kk xxP (4) (5) 3) Bound ing: The lower bound of the optimal solu tion in a set can achieve by a greedy method. In this method, the channel with high bandwidth has the priority to be chosen in order to achieve the optimal capacity. Thus, the lower and upper bound of the optimal value in P is 1 () k ii i Px B (6) 11 () kt ii i iik PxB B (7) The lower and upper bounds of the optimal solution in the entire feasible region D are max( ) k kPS P (8) max( ) k kPS P (9) 4) Pruning: For k PS , it should be pruned if one of the following conditions is satisfied: a) The constraints are violated. b) The upper bound of this set is smaller than the maximum lower bound, which is () k P . In this step, many subsets are pruned to accelerate the searching speed. 5) Convergence: In this step, examine whether it is the iteration. th ta) If ,1ktk k and go to the branching step. b) Ifkt , the optimal solutions of all the unpruned subsets are confirmed. In the convergence step of the iteration, end the iteration and enumerate the optimal solutions of all un- pruned subsets in to search the global optimal solu- tion. th t t P 6) Return: After getting the optimal solution for cur- rent group, the algorithm returns to calculate for the next group. Thus, the channels allocated to the current group will be excluded in the next round, and the number of available channels t will also be modified. 4.5. Election Mechanism If the coordinator is crashed, members must elect a new one. In our proposed MAC protocol, we use a simple and high efficient algorithm to realize the election mecha- nism. When any member notices the coordinator is not func- tioning, it sends an Election frame on CC/DCs (manager election frame on CC and leader election frame on DCs) to apply for becoming the new coordinator. If several members detect the coordinator's malfunction concur- rently, they have to compete for the CC/DCs through the IEEE 802.11 random access scheme. Recall that for a successful transmission, an ACK frame will be sent back to the sender. Under our proposed MAC protocol, as all members are listening to CC/DCs at all times, each member is able to receive this Election frame, and if anyone replies, the ACK frame will be heard by all members. The member who is the first to successfully  H. SONG ET AL. 118 Copyright © 2009 SciRes. Wireless Sensor Network, 2009, 2, 61-121 deliver an Election frame is automatically appointed as the new coordinator. Therefore, upon receiving an ACK frame notifying a successful reception, this member con- siders itself the new leader. Also, any other members who hear the ACK frame, and hence would know that someone else is appointed to be the new leader and need not send its own acknowledgem ent. In Figure 4, an example of election algorithm is given. The group consists of eight processes, numbered from 0 to 7. Member 7 is the coordinator which has ju st crash ed. Member 4 is the first one to notice this, so it sends an Election frame on CC/DCs. After hearing the Election frame from Member 4, Member 6 affirms Member 7’s malfunction and replies with an ACK frame. Upon re- ceiving this ACK frame, Member 4 knows that it has been permitted to be the new coordinator. Furthermore, because the rest members in the same group all can hear the Election and ACK frames, they are also aware of Member 7’s crash, as well as the new coordinator's gen- eration. Note that the election mechanism is very efficient, it exploits the already existing ACK mechanism and does not require any extra message exchange, thus incurring no bandwidth overhead. 5. Simulation and Performance Evaluation In this section, we present the simulation results for the performance evaluation of the protocol. The simulations are performed using the network simulator ns-2 [18]. The used parameters are presented in Table1. In the simulation, the proposed MAC protocol is com- pared with the following existing MACs: OS-MAC and CO-MAC. 1) OS-MAC: OS-MAC [4] is an opportunistic spec- trum MAC. It divides time into periods each of which is called OSP (Opportunistic Spectrum Period) and consists of three consecutive phases: Select, Delegate, and Up- date. Select Phase: Each SUG (Secondary User Group) selects a “best” DC, and uses it for communication until the end of the current OSP. Delegate Phase: On each DC, a DSU is appointed among members to represent the group during the Update Phase. 1 7 03 46 5 2 Election 1 7 03 46 5 2 ACK (a) (b) Figure 4. Election algorithm. Table 1. Parameters used in the simulations. Parameter Value Number of secondary user group 5, 8 Number of DCs 30 Bandwidth of each DC (not the same) 1~1.5Mbps Required bandwidth of eac h group 4.5Mbps Transmit power 0.01W Transport protoc o l UDP Update Phase: All DSUs switch to CC to update each other about their channel conditions while all non-DSUs continue communicating on their DCs. 2) CO-MAC: Lik e OS-MAC, CO-MAC [6], an oppor- tunistic MAC protocol, uses two transceivers, a dedi- cated CC, and N DCs. The time is divided into a number of periodical time slots and each slot is divided into two phases, namely, Reporting Phase and Negotiating Phase. Reporting phase can be further divided into n mini-slots, each of them corresponding to one of the n licensed channels. Reporting Phase: Each secondary user is equipped with one SDR transceiver, and by using this trans- ceiver only one of n licensed channels can be sensed. Thus the secondary user is unable to accu- rately know the states of all the channels by itself. However, the goal of the Reporting Phase is to em- power the secondary users to have a large picture of all the channels’ states through their cooperatio n. In particular, each secondary user senses a channel in corresponding mini-slot, if the channel is idle, the user sends a beacon during this mini-slot over the control channel. Otherwise, no beacon is posted. Negotiating Phase: the secondary users use the control transceivers to negotiate about the data channels among the secondary users by exchanging request-to-send (RTS) and clear-to-send (CTS) packets over the control channel. Meanwhile, the only secondary user which is the winner in con- tending for the data channels during the last time slot uses the SDR transceiver to transmit data pack- ets over all the unused licensed channels in the cur- rent time slot. For conciseness, we define the unused channels’ per- centage in the entire system as, where N is the number of channels licensed to primary users. / n pnN 5.1. Throughput Analysis In this section, we analyze the throughput with different numbers of unused channels under three protocols: the proposed MAC, OS-MAC and CO-MAC. The through- put allows us to evaluate the protocols’ performance, that is, the higher throughput, the higher performance. 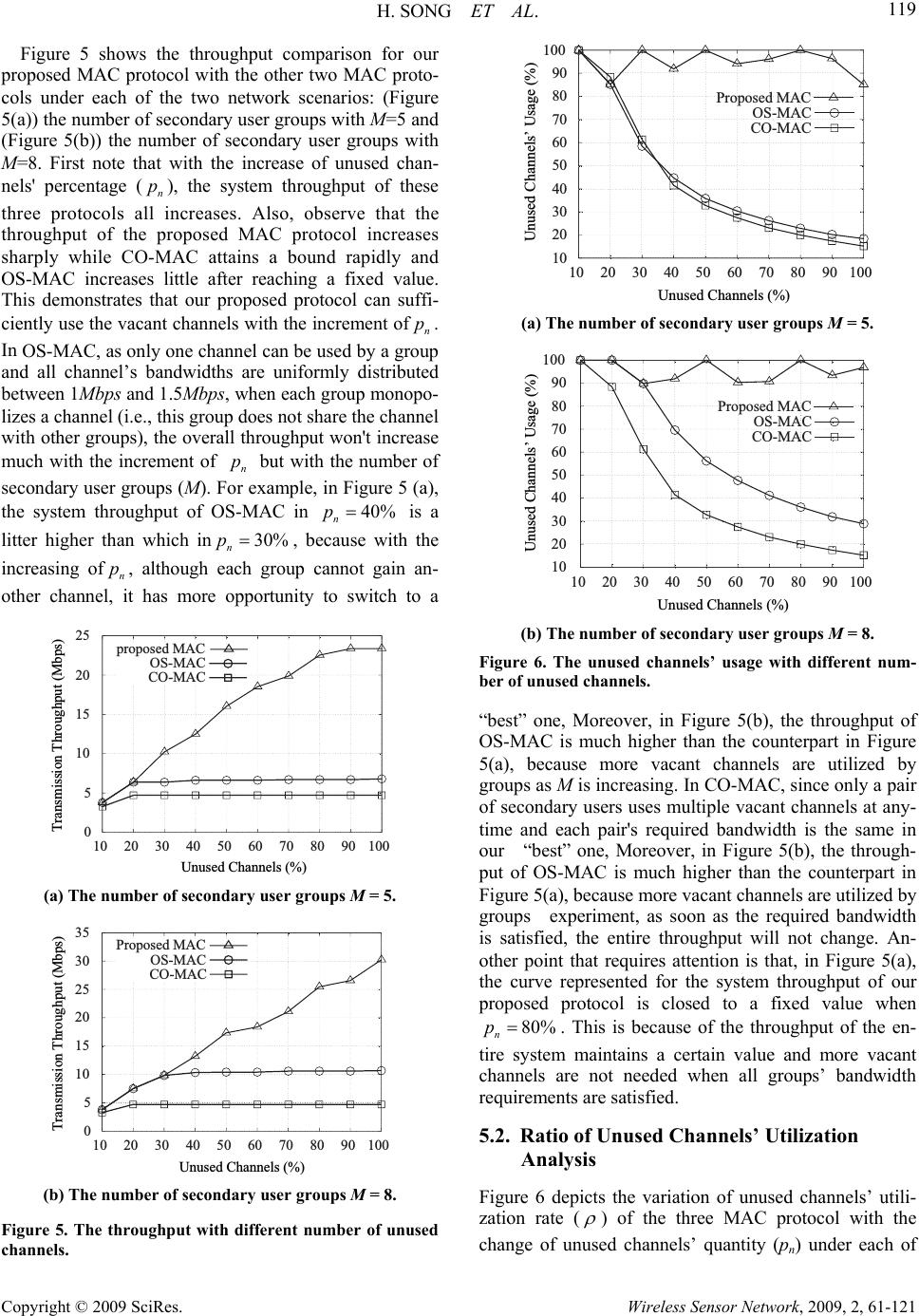 H. SONG ET AL. 119 Copyright © 2009 SciRes. Wireless Sensor Network, 2009, 2, 61-121 Figure 5 shows the throughput comparison for our proposed MAC protocol with the other two MAC proto- cols under each of the two network scenarios: (Figure 5(a)) the number of secondary user groups with M=5 and (Figure 5(b)) the number of secondary user groups with M=8. First note that with the increase of unused chan- nels' percentage (), the system throughput of these three protocols all increases. Also, observe that the throughput of the proposed MAC protocol increases sharply while CO-MAC attains a bound rapidly and OS-MAC increases little after reaching a fixed value. This demonstrates that our proposed protocol can suffi- ciently use the vacant channels with the increment of. In OS-MAC, as only one channel can be used by a group and all channel’s bandwidths are uniformly distributed between 1Mbps and 1.5Mbps, when each group monopo- lizes a channel (i.e., this group does not share the channel with other groups), the overall throughput won't increase much with the increment of but with the number of secondary user groups (M). For example, in Figure 5 (a), the system throughput of OS-MAC in is a litter higher than which in n p n p n p n p 40% n p 30% , because with the increasing of, although each group cannot gain an- other channel, it has more opportunity to switch to a n p 0 5 10 15 20 25 10 20 30 40 50 60 70 80 90 100 Transmission Throughput (Mbps) Unused Channels (%) proposed MAC OS-MAC CO-MAC (a) The number of secondary user gr oups M = 5. 0 5 10 15 20 25 30 35 10 20 30 40 50 60 70 80 90 100 Transmission Throughput (Mbps) Unused Channels (%) Proposed MAC OS-MAC CO-MAC (b) The number of secondary user groups M = 8. Figure 5. The throughput with different number of unused channels. 10 20 30 40 50 60 70 80 90 100 10 20 30 40 50 60 70 80 90 100 Unused Channels’ Usage (%) Unused Channels (%) Proposed MAC OS-MAC CO-MAC (a) The number of secondary user gr oups M = 5. 10 20 30 40 50 60 70 80 90 100 10 20 30 40 50 60 70 80 90 100 Unused Channels’ Usage (%) Unused Channels (%) Proposed MAC OS-MAC CO-MAC Proposed MAC o O S d A A A (b) The number of secondary user groups M = 8. Figure 6. The unused channels’ usage with different num- ber of unused channels. “best” one, Moreover, in Figure 5(b), the throughput of OS-MAC is much higher than the counterpart in Figure 5(a), because more vacant channels are utilized by groups as M is increasing. In CO-MAC, since only a pair of secondary users uses multiple vacant channels at any- time and each pair's required bandwidth is the same in our “best” one, Moreover, in Figure 5(b), the through- put of OS-MAC is much higher than the counterpart in Figure 5(a), because more vacant channels are utilized by groups experiment, as soon as the required bandwidth is satisfied, the entire throughput will not change. An- other point that requires attention is that, in Figure 5(a), the curve represented for the system throughput of our proposed protocol is closed to a fixed value when 80% n p . This is because of the throughput of the en- tire system maintains a certain value and more vacant channels are not needed when all groups’ bandwidth requirements are satisfied. 5.2. Ratio of Unused Channels’ Utilization Analysis Figure 6 depicts the variation of unused channels’ utili- zation rate ( ) of the three MAC protocol with the change of unused channels’ quantity (pn) under each of 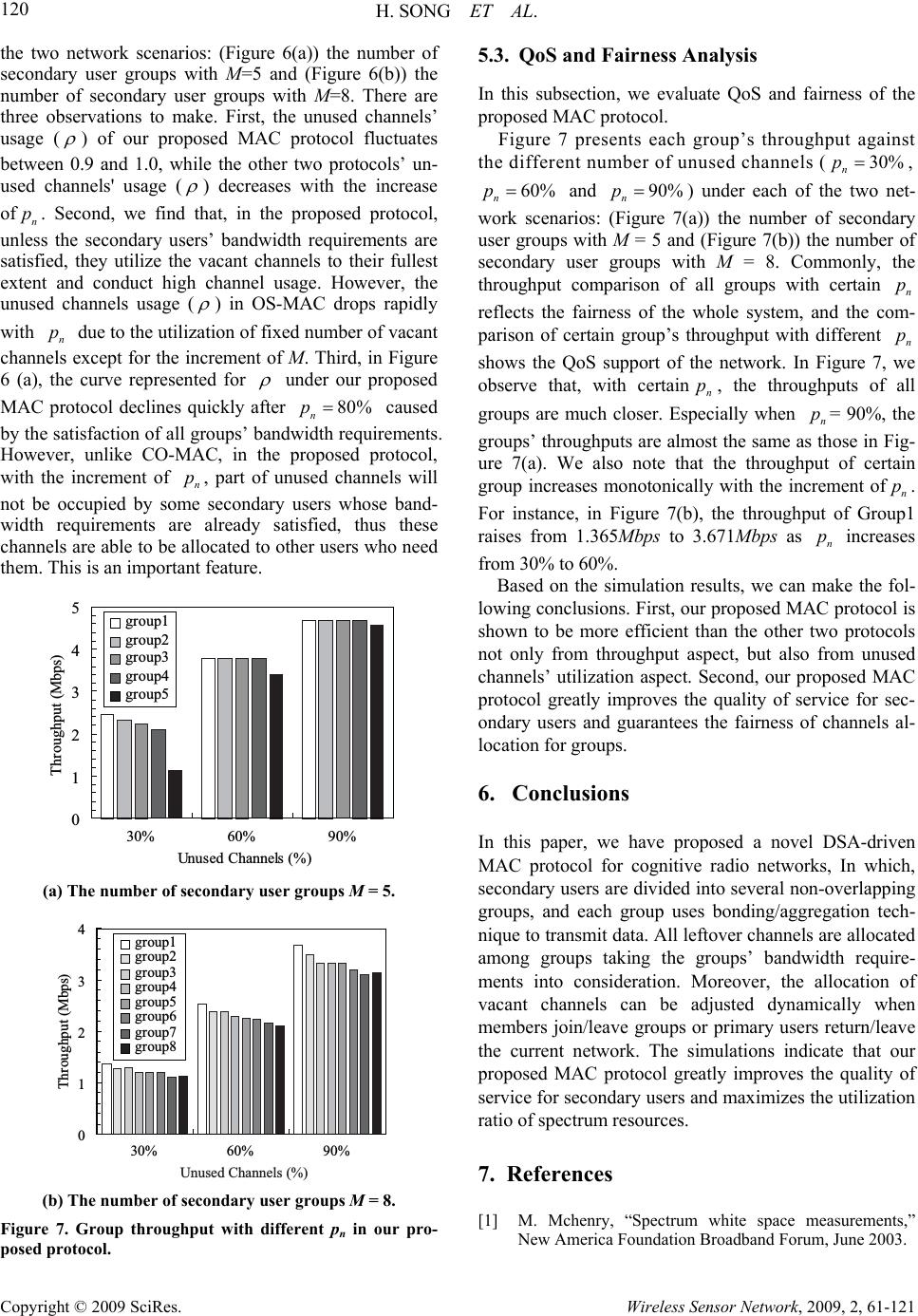 H. SONG ET AL. 120 Copyright © 2009 SciRes. Wireless Sensor Network, 2009, 2, 61-121 the two network scenarios: (Figure 6(a)) the number of secondary user groups with M=5 and (Figure 6(b)) the number of secondary user groups with M=8. There are three observations to make. First, the unused channels’ usage ( ) of our proposed MAC protocol fluctuates between 0.9 and 1.0, while the other two protocols’ un- used channels' usage ( ) decreases with the increase of . Second, we find that, in the proposed protocol, unless the secondary users’ bandwidth requirements are satisfied, they utilize the vacant channels to their fullest extent and conduct high channel usage. However, the unused channels usage ( n p ) in OS-MAC drops rapidly with due to the utilization of fixed number of vacant channels except for the increment of M. Third, in Figure 6 (a), the curve represented for n p under our proposed MAC protocol declines quickly after caused by the satisfaction of all groups’ bandwidth requirements. However, unlike CO-MAC, in the proposed protocol, with the increment of , part of unused channels will not be occupied by some secondary users whose band- width requirements are already satisfied, thus these channels are able to be allocated to other users who need them. This is an important feature. 80% n p n p 0 1 2 3 4 5 30% 60% 90% Unused Channels (%) Throughput (Mbps) group1 group2 group3 group4 group5 (a) The number of secondary user gr oups M = 5. 0 1 2 3 4 30% 60% 90% Throughput (Mbps) group1 group2 group3 group4 group5 group6 group7 group8 Unused Channels (%) (b) The number of secondary user groups M = 8. Figure 7. Group throughput with different pn in our pro- posed protocol. 5.3. QoS and Fairness Analysis In this subsection, we evaluate QoS and fairness of the proposed MAC protocol. Figure 7 presents each group’s throughput against the different number of unused channels (30% n p , 60% n p and 90% n p ) under each of the two net- work scenarios: (Figure 7(a)) the number of secondary user groups with M = 5 and (Figure 7(b)) the number of secondary user groups with M = 8. Commonly, the throughput comparison of all groups with certain reflects the fairness of the whole system, and the com- parison of certain group’s throughput with different shows the QoS support of the network. In Figure 7, we observe that, with certain, the throughputs of all groups are much closer. Especially when = 90%, the groups’ throughputs ar e almost the same as those in Fig- ure 7(a). We also note that the throughput of certain group increases monotonically with the increment of. For instance, in Figure 7(b), the throughput of Group1 raises from 1.365Mbps to 3.671Mbps as increases from 30% to 60%. n p n p n p n p n p n p Based on the simulation results, we can make the fol- lowing conclusions. First, our proposed MAC protocol is shown to be more efficient than the other two protocols not only from throughput aspect, but also from unused channels’ utilization aspect. Second, our proposed MAC protocol greatly improves the quality of service for sec- ondary users and guarantees the fairness of channels al- location for groups. 6. Conclusions In this paper, we have proposed a novel DSA-driven MAC protocol for cognitive radio networks, In which, secondary users are divided into several non-overlapping groups, and each group uses bonding/aggregation tech- nique to transmit data. All leftover channels are allocated among groups taking the groups’ bandwidth require- ments into consideration. Moreover, the allocation of vacant channels can be adjusted dynamically when members join/leave groups or primary users return/leave the current network. The simulations indicate that our proposed MAC protocol greatly improves the quality of service for secondary users and maximizes the utilization ratio of spectrum resources. 7. References [1] M. Mchenry, “Spectrum white space measurements,” New America Foundation Broadband Forum, June 2003.  H. SONG ET AL. 121 Copyright © 2009 SciRes. Wireless Sensor Network, 2009, 2, 61-121 [2] FCC, “Et docket no. 03-237,” November 2003. http://hraunfoss.fcc.gov/edocs public/attachmatch/FCC- 03-289A1.pdf [3] I. F. Akyildiz, W. Y. Lee, M. C. Vuran, and S. Mohanty, “Next generation/dynamic spectrum access/cognitive ra- dio wireless networks: A survey,” Computer Networks, 2006. [4] K. G. Shin and B. Hamdaoui, “OS-MAC: An efficient MAC protocol for spectrum-agile wireless networks,” Transactions on Mobile Computing, 2007. [5] J. Jia, Q. Zhang, and X. Shen, “HC-MAC: A hard- ware-constrained cognitive MAC for efficient spectrum management,” IEEE Journal on Selected Areas in Com- munications, Vol. 26, No. 1, pp. 106–117, January 2008. [6] H. Su and X. Zhang, “Cross-layer based opportunistic MAC protocols for QoS provisionings over cognitive ra- dio wireless networks,” IEEE Journal on Selected Areas in Communications, Vol. 26, No. 1, pp. 118–129, January 2008. [7] T. Mansi, V. S., and P. Ravi, “CSMA-based MAC pro- tocol for cognitive radio networks,” World of Wireless, Mobile and Multimedia Networks, IEEE International Symposium, pp. 1–8, June 2007. [8] A. Mishra, “A multi-channel MAC for opportunistic spectrum sharing in cognitive networks,” Proceedings of MILCOM 2006, October 2006. [9] L. Ma, X. Han, and C. C. Shen, “Dynamic open spectrum sharing MAC protocol for wireless ad hoc networks,” in IEEE International Symposium on New Frontiers in Dy- namic Spectrum Access Networks, pp. 203–213, 2005. [10] J. So and N. Vaidya, “Multi-channel MAC for ad-hoc networks: Handling multi-channel hidden terminals using a single transceiver,” in ACM Proceedings of MOBIHOC, 2004, pp. 222–233. [11] J. Zhao, H. Zheng, and G. H. Yang, “Distributed coordi- nation in dynamic spectrum allocation networks,” in IEEE International Symposium on New Frontiers in Dy- namic Spectrum Access Networks, pp. 259–268, 2005. [12] N. Nie and C. Comaniciu, “Adaptive channel allocation spectrum etiquette for cognitive radio networks,” in IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, pp. 269–278, 2005. [13] C. Corderio, K. Challapali, D. Birru, and S. Shankar, “IEEE 802.22: An introduction to the first wireless stan- dard based on cognitive radios,” Journal of Communica- tions, Vol. 1, No. 1, pp. 38–47, April 2006. [14] IEEE Standard 802.11 – 1999, “Wireless LAN medium access control (MAC) and physical layer (PHY) specifi- cations,” November 1999. [15] L. Kleinrock and F. Tobagi, “Packet switching in radio channels: Part I - carrier sense multiple-access modes and their throughput-delay characteristics,” IEEE Transac- tions on Communications, No. 23, pp. 1400–1416, De- cember 1975. [16] P. Apkarian and H. D. Tuan, “Robust control via concave minimization local and global algorithms,” IEEE Trans- actions on Automatic Control, Vol. 45, No. 2, pp. 299– 305, February 2000. [17] W. Wang, T. Peng, and W. Wang, “Optimal power con- trol under interference temperature constraints in cogni- tive radio network,” Wireless Communications and Net- working Conference, WCNC 2007 IEEE, pp. 116–120, March 11–15, 2007. [18] The network simulator (ns-2). http://www.isi.edu/nnsnam/ns/. |

