Advances in Remote Sensing
Vol.05 No.01(2016), Article ID:64471,22 pages
10.4236/ars.2016.51005
A WSN-Based System for Country Border Surveillance and Target Tracking
Noureddine Boudriga
CN&S Research Lab., SUPCOM, University of Carthage, Ariana, Tunisia

Copyright © 2016 by author and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 7 January 2016; accepted 11 March 2016; published 14 March 2016
ABSTRACT
Target tracking using wireless sensor networks offers multiple challenges because it usually involves intensive computation and requires accurate methods for tracking and energy consumption. Above all, scalability, energy optimization, efficiency, and overhead reduction are some among the key tasks for any protocol designed to perform target tracking using large scale sensor networks. Border surveillance systems, on the other side, need to report border crossings in a real time manner. They should provide large coverage, lower energy consumption, real time crossing detection, and use efficient tools to report crossing information. In this paper, we present a scheme, called Border Cooperative and Predictive Tracking protocol (BCTP), capable of energy- aware surveillance and continuous tracking of objects and individuals’ crossing a country border and anticipating target motion within a thick strip along the border and estimating the target exit zone and time.
Keywords:
Wireless Sensor Networks, Country Border Surveillance, Target Tracking, Sensor Deployment

1. Introduction
The large scale evolution in wireless sensor network technology makes it possible to implement wireless sensor networks (WSNs) within a wide range of applications including healthcare monitoring, battlefield surveillance, and physical or environmental conditions observation [1] [2] . In particular, sensors are able to gather information about a target moving in a region of interest and collaborate to report their measurements/information to an analysis center, where tracking capabilities are provided.
A target is an entity (a moving object, individual, or animal) whose state and activity are of interest for an application. Identifying a target while crossing a border by its particular features, detecting its path over a period of time and predicting its moves and positions in the future constitute the major hard tasks to address in tracking targets. In addition, tracking using sensor networks is complex due to the processing, scheduling, communication, and energy constraints it faces. In particular, the sensors should share data and cooperate to perform data fusion and event relaying appropriately.
To accomplish target tracking, the WSNs have implemented several techniques including: a) data acquisition techniques achieving the monitoring task by sampling data and measuring characteristics related to target locations and activities over time; b) scheduling techniques allowing an optimized use of energy while allowing larger sensor lifetime; and c) maintenance techniques offering an interesting level of tracking quality. One can notice that these techniques, as published in the literature, were based on the assumption that there are enough sensors that are capable of sampling targets’ features across time. Nevertheless, studies on WSNs have shown that this assumption does not hold all the time because of initial deployment weaknesses, energy consumption modes, or external factors including sensor failures and physical attacks [3] - [5] .
Since target tracking is a realistic and dynamic estimation scheme, in its general form, an efficient tracking needs to lay down a “theory” capable of controlling the measurements, the estimation and the errors experienced within the processes of prediction and approximation. Moreover, target tracking systems in border surveillance systems should be able to comply with more constraining features, such as operating under real conditions, collaborating to help efficient interception of trespassers, and providing surveillance continuity and protection. One can notice, however, that most of the proposed solutions do not provide all this and handle only some parts of it.
In this paper, we propose a distributed and prediction capable scheme, called Border Cooperative Predictive Tracking protocol (BCTP), to accurately track mobile targets within a given area, which has the form of large thin strip along a borderline. The scheme provides a technique to deploy wireless sensor networks in the strip under a mathematically controlled random mode. The latter assumption is realistic since a similar scheme has been made available, in general, along with a mathematical control of the coverage they allow [6] . Our protocol provides power conservation as one of the key design guidelines and controls the continuity of tracking. The protocol assumes that most of the sensor nodes, except a line (or a few lines) parallel to the border, stay in a sleep mode (with their transmitting and sensing function shutdown) for most of the time, waiting for a wake up signal.
The contribution of this paper is three-fold: a) Given the number of targets to detect, the protocol provides a distributed mechanism for determining the set of sensors to wake up in the vicinity of the future positions of the detected targets, until complete area crossing; b) to minimize the energy consumption during tracking, the protocol reduces the number of sensors to only some among those that are expected to have the target in their range at the moment of wakeup; c) a mathematical model is developed to control tracking continuity and estimate the exit time and exit segment of any target from the strip built along the frontier; and d) a mathematical model is built to control the deployment scheme of the WSN capable of guaranteeing a high probability of tracking continuity.
The remaining part of this paper is organized as follows. Section 2 discusses the limits of the existing target tracking solutions for border surveillance and reviews the tracking techniques developed for WSNs. Section 3 develops the requirements for an efficient tracking system. Section 4 presents the Border Cooperative Predictive Tracking scheme. Section 5 builds the mathematical models for target tracking. Section 6 defines estimation techniques for exit segment determination. Section 7 constructs a mathematical model capable of determining the probability of target tracking continuity. Section 8 discusses numerical experiments of the protocol and mathematical model. Section 9 concludes this paper.
2. State of the Art
The efficiency of WSN-based surveillance systems highlights two major objectives to achieve: first, it should build on a deployment scheme capable of offering total coverage of the area under monitoring so that any target entering the area is detected. Second, it should be able to track moving objects of interest in the area. Both goals have received an extensive attention during the last decade. Efficiency also needs that sensors should optimize the energy consumption, since the aim of an efficient tracking should ensure both continuous monitoring and energy conservation. To this end, the sensors should be able to dynamically move between a sleeping status and an active status. In a target tracking application, for instance, the sensors that can detect a target, appearing in the sensor’s vicinity at a particular time, must be in an active state.
2.1. WSN-Based Border Surveillance Systems
Several recent works have discussed the design of country border surveillance systems based on WSNs. A majority of the proposed solutions have displayed the WSN nodes as a linear network, so that every movement going over the barrier (or line) of the sensors is detected [7] - [9] . Compared to full coverage, the barrier coverage provided by a perfect linear deployment requires only a few sensor nodes, but experiences more radio disconnections, due to sensor failure and energy depletion. In addition, this kind of linear architecture presents two drawbacks: first, it does not permit the tracking of intruders, since the intruders are only detected when they cross the line of sensors and their future movements cannot be tracked. Second, the sensor nodes are not able to locally determine whether the barrier full coverage is ensured.
On the other hand, solutions using k-barrier coverage require that all crossing paths in the monitored region around a spatial line are covered by at least k distinct sensor nodes. Such solutions include the 3-layered hybrid network architecture for border patrol, called Bordersense that has been proposed in [10] . Bordersense deploys advanced sensor networking technologies utilizing multimedia sensor nodes, mobile sensor nodes, and scalar sensors, which could be installed underground or above the ground. The high cost of the deployment of multimedia sensors (including cameras) makes Bordersense hard to deploy for larger borders and the uniformity of sensor distribution difficult to achieve, except when an appropriate deployment scheme is designed taking into consideration the environment complexity.
The case of border surveillance when sensors are randomly and uniformly deployed has been also investigated in a few works. Even though uniform sensor deployment is useful in theoretical scenarios, it remains unrealistic in the real cases, where a non-uniform placement is experienced due to several environmental features such as dense vegetation and rough terrain. In addition, most of the published works do not provide a mathematical control of the sensing coverage, so that coverage hole can be detected and repaired.
On the hand, the authors in [11] presented the design of border surveillance solutions using wireless sensor networks while providing the following contributions: first, a global network architecture for border surveillance based on three types of components operating in a thick line architecture was set up along the border. Second, a deployment strategy that copes with many constraints on the WSN operation, coverage maintenance, connectivity preservation, and routing quality of service was designed. Finally, a mechanism of routing management to ensure efficient data relaying and reporting between the different node layers. Even though target tracking and target moves prediction were not addressed in [11] , the solution presents interesting aspects such the mathematical control of the sensing and communication coverage quality.
On the other hand, one can see that some other proposed frameworks for border surveillance assumed that a line- (or a thick-line) based WSN offering barrier or k-barrier coverage is provided. Under this assumption, the solutions attempted to reduce the number of needed sensors to monitor the crossing of a given border; but, the improvement is obtained at the expense of efficiency reduction and tracking limitation. In other words, line- based deployment at best ensures the detection of all intrusion attempts, but will not allow to take an internal decision about tracking the intruders. Furthermore, the coverage provided by these solutions is not realistic due to environmental factors and sensors dropping techniques (air-dropping or manned dropping, for example). Another limitation of the proposed models is the silence they observe about the connectivity and prompt reactivity issues.
In addition, one can see that target tracking under surveillance systems presents very special constraints with respect to the common WSN-based monitoring of two dimensional areas. Indeed, tracking in border surveillance should be done in real-time mode, should be available all the time, should be continuous, and should be able to help predicting the exit time and zone for the monitored area. The objectives of the next subsection are to survey the works performed in WSN-based target tracking approaches and to discuss their limits with regards to the aforementioned differences.
2.2. WS-Based Target Tracking Solutions
We can classify the target tracking techniques into several categories, based on the sensor activation modes, the network topologies and the sensor partition techniques they use. Node activation can be naïve, randomized, selective, based on trajectory prediction, or duty cycled [12] . Naïve activation based tracking techniques, where all nodes are in active (or tracking) mode all the time, are among the simplest and general tracking techniques. In such context, the sensing nodes report their local measurements to the sink node. The latter follows the target motion in relation with the reported measurement and attempts to predict the target positions in the future. Naive activation ensures high tracking quality; but, it offers the worst energy consumption and provides heavy communication to the sink node, since sensors are all the time sensing, estimating, reporting, or data relaying.
Tracking methods using naïve activation are not robust because the WSN they use is more prone to energy depletion, traffic congestion, sensor failure, and even security attacks. In the following, we consider the other solutions and mainly discuss two major overlapping categories; namely, the hierarchical and prediction-based classes of tracking [13] [14] . We also analyze their drawbacks with respect to border surveillance requirements.
2.2.1. Hierarchical Tracking Methods
In a hierarchical tracking method, the WSN is organized in such a way where sensors in the vicinity of a target must be able to detect it and report back to the sink node using the network hierarchy. Therefore, the sensors should be able to relay the messages of other sensor nodes, by acting as repeaters, and to support data processing results on behalf of the other senor nodes, when needed. Hierarchical tracking methods can be classified into three categories: tree-based tracking, cluster-based tracking, and hybrid methods.
In tree-based target tracking, sensor nodes are organized in a hierarchical tree (or sometime in a graph), where nodes are sensors and edges are links between sensors that can directly communicate with each other. In particular, in STUN (Scalable tracking using networked sensors), a tree-based approach in which a cost is assigned to each link, computed on the Euclidean distance between the two communicating nodes, is used [15] . The leaf nodes serve for tracking the targets and sending the collected data to the sink through intermediate nodes on the tree. Intermediate nodes keep a record on the detected target and send updated information to the sink, whenever there is a change in that record. Moreover, in [16] , Zhang et al proposed a tracking technique, called Dynamic Convoy Tree-Based Collaboration (DCTC), where spanning trees are used to detect and track the mobile targets and monitor their surrounding area. The tree is dynamically configured to add nodes and exclude other nodes as they become far away from the related target. One can observe that STUN and DCTC experience high costs in builds and maintaining the trees.
Various other tree-based techniques have been developed [17] . Some of these works present limitations such as the dependence on the tree structure for the network topology. In particular, organizing sensor nodes in logical trees, location updating, and querying may present unacceptable costs. Moreover, when a target is discovered, the source sends a wake request to sensor nodes and the nodes in the vicinity to the target replies back. To detect moving target continuously, the spatial neighbors of near sensor node are wake up.
On the other hand, cluster-based tracking methods assume that the WSN is partitioned into clusters to support collaborative tracking processes using cluster heads. Three categories of cluster-based methods can be distinguished; they are: the static clustering, dynamic clustering, and space time clustering. In the static clustering methods, the nodes are partitioned into clusters on network deployment. The cluster size, cluster head, and cluster members are static. The main advantage of a static clustering method is its simplicity. Its major disadvantage stems from the fact that it is not fault tolerant. For example, if a cluster head is out of energy, all the sensors belonging to its cluster will not be able to operate until a new cluster head is elected.
Low-Energy Adaptive Clustering Hierarchy (LEACH) was developed with the desire to reduce energy consumption in the WSN [18] [19] . A sensor node in LEACH detecting a target sends its data to its cluster-head. The latter aggregates and compresses the data it collects and sends it to the sink node. Since a cluster head requires more energy during operation than the other sensors belonging to its cluster, LEACH allows random rotation of cluster heading to balance energy consumption in every cluster in the WSN.
Alternatively, the Continuous Object Detection and Tracking (CODA) mechanism considers that the WSN uses a static backbone comprising a number of static clusters built during the initial network deployment step. In each cluster, any sensor detecting the moving targets in its vicinity transmits the detecting information directly to the cluster head [20] . Two advantages characterize CODA: the communication overhead is substantially reduced and an explicit header election scheme is not required.
Unlike static clustering approaches, dynamic clustering methods allow the formation of a cluster on the occurrence of certain events of interest such as the approaching of a target to the area of a group of sensors. Examples of dynamic cluster-based tracking include information-driven sensor querying (IDSQ), RARE, and DELTA [21] - [23] . IDSQ supposes that each node in the network can locally estimate the cost of sensing, processing and data communication to the other sensors. It also allows to determine dynamically which sensor is most appropriate to perform target detection.
RARE approach reduces the number of sensors contributing in tracking by preventing remote sensors from taking part in the tracking operation. It diminishes redundant information by identifying overlapping sensors; whereas DELTA builds a distributive algorithm to track a target moving at constant speed by dynamically forming a cluster and selecting the CH to reliably monitor moving targets based on light measurement.
While DELTA main drawback stems from the fact that it does not consider varying target speed, the tree- based and cluster-based methods suffer from the fact that the sensing task is usually performed by several nodes at a time. This causes heavy computation on the root node, for the tree-based schemes, and on the CH, for the others. It also makes the tree- or cluster-based WSN tracking systems lack of robustness in the case of root and CH failures.
2.2.2. Prediction-Based Approaches
In recent years many target tracking protocols have been proposed to provide prediction-based methods, where the next position of the target is predicted. The authors in [24] proposed a prediction-based energy aware scheme, referred to as PES. PES built three components: a) a prediction model that is able to help selecting the sensor nodes that are expected to take in charge the tracking; b) a heuristic-based mechanisms that decides which sensor should be activated and when; and c) a recovery mechanism that can be triggered when a tracking disconnection is experienced. Since energy is considered to be the most critical resource, PES assumes that a sensor node remains in a sleeping state as long as possible.
In [13] an algorithm called Dual prediction-based reporting (DPR) was developed. It aimed at reducing the energy needed by the WSN by keeping the sensor in a sleeping mode most of the time and requesting that the computation of target position is performed locally at the sensor nodes and globally at the sink node. Transmissions of sensor messages are escaped as long as the predictions are consistent with each other. DPR achieves energy efficiency by judiciously trading off multi-hop transmissions of the messages between sensors and the sink node.
In [14] , an energy efficient prediction-based algorithm was proposed assuming that the moves of the targets are predictable. The algorithms attempts simply to reduce the transmission distance between the communicating nodes and the number of messages to transmit. The main idea in this algorithm is to use a tri-lateration algorithm, carried out locally by the sensors, for the localization of a target. This makes the cluster head not involved in the needed communications, and thus reduces the energy consumption.
Other target tracking schemes have assumed that the sensor nodes are mobile and the sensing coverage is not full. The main idea in these schemes is to predict the future position of the target and select one among the sensor nodes close to that position and order it to move closer to it. In particular, the authors in [25] proposed a tracking framework based on Voronoi tessellations. A mobility model was proposed to control the coverage degree according to the target presence. The objective is to establish a non-uniform coverage within the monitored zone to allow detecting the target by multiple sensor nodes. Moreover, the authors introduced an algorithm to discover overlapping nodes without providing additional communication cost. This algorithm was shown to be effective in reducing the energy consumption.
3. Target Tracking under Surveillance System
We discuss in this section special requirements of the surveillance process in terms of tracking efficiency and task scheduling.
3.1. Requirements for Efficient Surveillance
WSN-based surveillance applications features are characterized by the nature of the environment where the applications take place and the degree of the tracking efficiency required for the applications. In the following, we discuss the most important WSN characteristics needed to achieve efficient mobile target tracking in a hazardous environment. Some of these characteristics have been discussed in [10] and [6] .
Communication infrastructure: as mentioned before, two common types of WSN communication models are currently used to achieve surveillance: the hierarchical and the flat networks. While the first structure allows the existence of nodes, called cluster heads, capable of performing sophisticated operations and having more energy than simple sensor nodes, the nodes in the flat structure have the same capabilities and should collaborate to relay any report from the generating node to the sink node. In both models, surveillance should be able to optimize the energy consumption and keep connectivity. While hierarchical infrastructures should reduce the relaying activity within clusters, the flat architecture should reduce the number of sensors involved in event collection and target tracking.
Deployments cheme: The deployment of sensor nodes in a surveillance application in an irregular environment cannot be accomplished according to a deterministic choice. Due to the hostility of the physical environment, direct human control of the sensor nodes serving the surveillance application may be hard to achieve, and might be impossible in certain situations. Typically, sensor nodes are dropped from manned/unmanned aircrafts in a given area and should provide total sensing coverage, in some sense. Therefore, a control mechanism should be attached to the deployment scheme to allow measuring the required level of coverage any time. The control may use a large set of parameters that can be effectively monitored, including node density, sensor range, and k-coverage capability.
Energy management: The energy resources of a sensor node are limited because of the sensor size and cost constraints. In fact, localization, sensing functions, and communication techniques could not be performed without taking into consideration energy constraints. In addition, high-resolution information about the monitored area is often needed, requiring the use of energy-aware techniques. Energy is the most important factor occurring in the determination of the WSN lifetime. The required lifetime in the surveillance context should last as long as possible. Therefore, the sensors should be able to be automatically recharged after their amount of energy is consumed, or they should be replaced upon energy depletion or failure. Moreover, to provide surveillance continuity, the system should be able to estimate energy consumption for every sensor and determine in advance the energy failure moment to provide sensor replacement.
Mobile target tracking: Three major requirements have to be fulfilled by sensors in a surveillance system: First, the sensors should be unnoticeable, meaning that their positions should be hard to determine by non-autho- rized parties and their size should be limited. Second, the sensor nodes should be able to locate targets moving under a reasonable speed v in the monitored area (generally,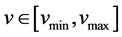 ). Third, the sensor nodes should be able to collaborate with each other to construct the path followed by a target and predict its exit zone from the monitored area.
). Third, the sensor nodes should be able to collaborate with each other to construct the path followed by a target and predict its exit zone from the monitored area.
Monitored area coverage: The sensor nodes in a surveillance application should collaborate to achieve sensing coverage of the whole area in order to collect useful events when they occur and to build continuously the path followed by any target trying to cross the area. In addition, the WSN needs to be connected so that any collected event or target related information is forwarded to the sink node, via the other nodes if needed. Since the communication coverage of a single sensor node is basically dependent on the sensing range of the sensors attached to it, the communication requirements of the surveillance system should depend heavily on the sensor sensitivity to track targets. The WSN must be able to minimize the errors related to mobile target detection and feature measurements.
3.2. Deployment/Scheduling Objectives for Energy-Aware Surveillance
The deployment of sensors for border surveillance may be made in a strip along the borderline of a country with a width sufficiently large. The system should be able to track mobile targets (including individuals, animals, and vehicles), help following their paths, and estimate their exit points from the strip. To this end, the deployment schemes and scheduling activity of the WSN may need comply with two categories of rules: the density controlling rules and the scheduling rules. In the following, we discuss some of these rules.
Density related requirements. It is obvious that the quality of target detection and tracking depends on the number of deployed sensors and the surface of the given strip. An efficient deployment scheme should guarantee that every point in the strip, where a target can be, is sensed by at least one active sensor. However, knowing that the target enters the strip from one edge of the strip and exits it from the other edge, this condition can be achieved by the following rules:
Monitoring line rule: At least one sensing line should be active to detect the beginning of a crossing action. The sensing line is nothing but a sequence of sensors separated by at most twice the sensing range of the sensors. This line should be parallel (in some sense) to the borderline so that an object crossing the strip should traverse it. Furthermore, to provide premature detection, the sensing line should be close to the borderline. The number
of sensors that form the sensing line should be higher than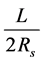 , where
, where 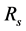 is the sensing range of the sensors and L is the length of the borderline. Most of the time the sensing line is physically a broken line requiring many more sensors than
is the sensing range of the sensors and L is the length of the borderline. Most of the time the sensing line is physically a broken line requiring many more sensors than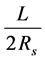 .
.
Density rule: More generally, if the coverage of every point in the strip is required, the number should be higher than
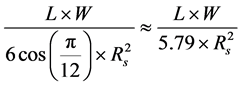
where W is the width of the strip. The formula assumes that the strip is bounded with a surface equal 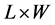 and that any sensor, except those on the border of the strip, has at least 6 sensor neighbors (i.e., the traditional pavement in cellular networks). This rule guarantees he high probability that every point in the strip is covered by a sensor, provided that the deployment is uniform.
and that any sensor, except those on the border of the strip, has at least 6 sensor neighbors (i.e., the traditional pavement in cellular networks). This rule guarantees he high probability that every point in the strip is covered by a sensor, provided that the deployment is uniform.
Scheduling constraints. It can be easily seen that the scheduling scheme within surveillance systems should be able to comply with two contradictory objectives. They are the sensor lifetime and the sensing continuity. Three rules can be distinguished.
Lifetime rule: The lifetime of the sensors should be as long as possible, assuming that the energy consumption should be reduced for all sensors and that any target crossing should be detected. This means that the scheduling operation should handle sensor sleeping, target detection, and target tracking tasks with different strategies. The first sensors in charge of target detection should belong to at least one established line of surveillance, for instance; and in that case, the line should be maintained to provide energy reduction and modified from time to time. On the other hand, sensors in charge of tracking must be awakened only when needed.
Prediction Awake rule: Sensors in charge of tracking are awakened when the detected target occurs in their vicinity. Awake sensors in charge of tracking an active target should collaborate to predict the next positions (in the next time slot) of the detected target and reduce the number of the sensors to wake up upon target detection. The prediction of the next positions should be able to help determining which sensor(s) to wake up in the next time slot. Position prediction must take into consideration the geographic nature of the monitored area and the history of target motion.
Tracking continuity rule. Only a few sensors should be awakened to provide continuous target tracking so that targets can be monitored properly (at any time slot) until exit time. Since the time is slotted, we assume here that continuous tracking means that the surveillance system is able to locate the target at any time slot after its/his first detection. Let us notice, however, that this definition can be reduced by changing the expression “any time slot” by the expression “every n time slots”, for small values of n.
4. Border Cooperative Predictive Tracking Scheme
For the sake of simplicity, we suppose in this section that a WSN-based surveillance system is deployed uniformly in a thick strip along a country border, or randomly deployed with a mathematical control such as in [24] , where sensing and radio coverage of the strip were provided. We also assume that a target is crossing the area following an unknown path. Our objective in this section is to construct a tracking scheme, referred to as the Border Cooperative Predictive Tracking (BCPT) scheme. The scheme is a three-step process. In the first step, the target is detected as soon as it enters the strip. In the second step, BCPT wakes up appropriate sensors to follow the crossing target while predicting its next positions. In the final step, it estimates the exit time and exit points (or segment).
The first step can be achieved assuming that a line of active sensors is configured along (and close to) the border. As soon as the target arrives to cross the line, a sensor detects it. The detection can be certainly achieved if the distance between two successive sensors in the line is smaller that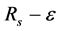 , where ε is a positive number commensurate with the maximum speed of the target and the way the sensor performs its function.
, where ε is a positive number commensurate with the maximum speed of the target and the way the sensor performs its function.
The second step is iterative. A sensor s detecting a target at time slot 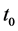 determines the positions of the target at the following time slots
determines the positions of the target at the following time slots 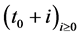 until it leaves its sensing area. Let
until it leaves its sensing area. Let 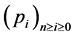 be all the positions of the target observed by sensor s at the following time slots. The number n of these positions is obviously finite and depends on the path of the target, since the latter moves to the exit edge of the strip.
be all the positions of the target observed by sensor s at the following time slots. The number n of these positions is obviously finite and depends on the path of the target, since the latter moves to the exit edge of the strip.
Let  be the position of sensor s. At the beginning of time slot
be the position of sensor s. At the beginning of time slot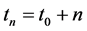 , sensor s estimates the next position
, sensor s estimates the next position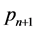 , builds a message containing the type of the detected target (or its features, as collected), the two last observed positions (if any), the new position, and the time duration of observation, say
, builds a message containing the type of the detected target (or its features, as collected), the two last observed positions (if any), the new position, and the time duration of observation, say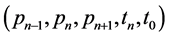 . Then, it sends the message to the sink node and to its neighbors located, out of its tracking range, in the sector centered on
. Then, it sends the message to the sink node and to its neighbors located, out of its tracking range, in the sector centered on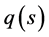 , using segment
, using segment 


where 




Figure 1 depicts the sector where, sensor neighbors should be able to receive the message. We call this process the L-wakeup process.
When 








Distance 

If the sink node receives a messages from sensors 

and reporting on the positions of the target


Positions’ correlation: if the reported positions correspond to the same time slots then these position are compared. If they are different, then a new position is computed to replace the reported position (as the middle of these positions, for example) and the predicted position are revisited.
Dropping messages: the receiving sensor, say



Figure 1. Wake up zone after prediction.
that sensor 




Let us now discuss some important features of the cooperative predictive tracking scheme. In particular, let us study the tracking continuity property of the scheme. Establishing this property requires three major constraints; namely, the sensor sensing continuity, the sensing granularity, and the target path visibility. Sensor sensing continuity assumes that every awake sensor senses its area at least once per time slot. This constraint can be reduced by requesting that the sensor should sense every m time slots (



Finally, Target path visibility constraint assumes that, if the crossing time is larger than n time slots, then the path followed by the tracked target includes more than n detected positions. This assumption guarantees that, if the time passed by a target to cross the area monitored by a sensor s is longer than a time slot, then the sensor will detect the target more than once. More generally, if the target spends more than m slots to cross the area controlled by s, then it will be detected at least m times.
The following result shows that the tracking continuity property can be achieved when the target mobility and sensing range cope with the strip width, the place of the surveillance line, and the time slot duration. The result involves a discussion on the angle 


Proposition 1 (tracking continuity). Assume a target is crossing the border strip with a speed 
1) The quantity 

2) The width and angle 

・ the deployment density is higher than
・ The width L, angle




Proof.
The first condition states that the target should be detected by one sensor on the active thick line (barrier) characterized by a certain width w. Figure 2 depicts such a thick line. If the distance between two neighbors in that line is lower than
Since an active sensor senses once in a time slot, the target speed should not exceed 2w. Therefore, 

One can see that once a target is detected, the detecting sensor, say s, follows it until it gets out of its sensing area

Figure 2. Thick active line.
where 


Finally, the last inequality guarantees that the diagonal 



The third condition implies that to provide detection of the target by a sensor in



Hence, we deduce that the WSN is able to construct the target path, from the moment it is detected until the moment it leaves the strip, provided that the two conditions of the theorem are satisfied.
Let us inform that the second condition in the theorem imposes a constraint on




5. Predicting Target Exit
In this section, we first develop a mobility model for a generic target crossing the strip. Then we establish the major features of our prediction scheme based on this model. Finally, we describe how our algorithm predicts the exit time and exit zone of the target.
5.1. Target Modeling and Assumptions
To be detected, the target should move at a speed (counted in meters per time slot) higher than a given minimum speed 

Target mobility rules. Assuming that the target is at position p at time slot t, a mobility rule supposes that the new position 






bility rule of the target. The angle 

The distances 





Figure 3. Target motion modeling.
with sensing range, the sensor sensitivity, and the slot duration. In particular, when 


Target path rules: Several rules can be reasonably used to model the target path. A first rule assumes that the target approaches the exit edge of the strip with at least 



This rule states again that 

where 




where n is the number of time slots used to observe the target, 




Let 




and
since 




Thus, we have the following result.
Proposition 2. Assume that the aim of a target is to reach the exit edge of the border strip and that the monitoring line active has detected him/it at time slot 
1) The path modeling process converges in a finite time, meaning that the target will reach the exit edge in a time shorter than a maximum time given by
2) The maximum length l of the path followed by the target between its detection point and time termination is given by
Proof.
The process has been shown to terminate by providing the computation of the maximum time to reach the exit edge


Computing the length of the target path travelled until time slot k is given by
The inequalities can be easily stated using the mobility and target path rules, knowing that
5.2. Prediction Features
Let us now study the sequence 





During step n, the predicted position of the target is replaced by the observed position




Let us now show how the sink node predicts the exit time of a target along with its exit segment, as it is kept informed by the target motion. To this end, we consider the following notations: Let 










Let us compute the different segment using 



・
・
・
・
・
・
where 

The following result studies the evolution of the potential exit time and exit segment of the target, assuming that the distance separating the target from the exit edge decreases of at least 


Proposition 3. a target crossing the border strip and 

1) The length 

2) The two sequences 


3) If position 

Figure 4. Example of potential exit segments.
Proof.
First, let us notice that using the mobility rule we can show that the inclusion 

Figure 5 depicts the segments 

This function is continuous. Let 






where:

Second, one can deduce from the first statement that 
The two series are finite since at every step the target approaches the edge by at least 


The number of elements in these series is thus lower than 
Third, it has been shown in Subsection 5.1 that if the target is detected at a position p then it reaches the edge before a maximum time 
One can also easily show that the target will arrive after a time
Figure 5. Bounding
Applying these inequalities, when



Various methods can be utilized to estimate the time of exist. One could estimate
Another method computes the average distance per slot travelled by the target and set, at time slot k, an estimation of the exit time by:
6. An ad hoc Deployment for Target Tracking
Without loss of generality, we assume in this section that the strip to monitor along the country border is a rectangle of length L and width W positioned between points


On each line the quadcopter is assumed to drop a sensor at each instant 

stant when the quadcopter is at point
Taking into consideration the environment conditions of dropping and assuming that the quadcopter keeps a constant speed equal to V meters per second, one can state that the landing point of a sensor dropped at time 
where 



In the following we assume that







Figure 6. BCPT-based deployment.
Theorem 4. Let 


・ 
・ 
・
Proof.
First, let us notice that all the rectangles around 

This inequality states that 



Second, continuity imposes that the speed of the target 
Finally, let s be a sensor tracking the target and that at time slot n, sensor realizes that the target is in position p and that it will be in a position p’ out of its tracking range. Let us consider the zone 



contains a sensor. An easy computation shows that under this condition, 
More generally, for given



7. Performance Evaluation
In this section, we present the results of the simulations we have conducted. The aim of these simulations was to evaluate the performance of the target tracking method we proposed to show its efficiency, in terms of energy consumption and the exit time and zone estimation. We also evaluate respectively the scheduling messages overhead, the deployment coverage in terms of tracking continuity, and the network lifetime.
7.1. The Simulation Model
The simulation model is built by considering that the area to be monitored is of size 








gy consumption. For this, we will conduct simulations by varying 



Three major objectives will be studied in the sequel. First, the quality of coverage (including the barrier) will be discussed. Second, the discontinuity ratio will be analyzed as a function of important factors including


7.2. Numerical Experiments
7.2.1. The Deployment Efficiency
Simulations have been conducted to evaluate our deployment scheme and the quality of coverage of the barrier (i.e., the first line of surveillance along the border). The evaluation of the scheme is made by measuring the proportion of uncovered points in the area, while 

One can notice that the loss of coverage for our scheme decreases when the sensing range of the sensors range increases and that all points are covered when 


Figure 8 depicts the level of barrier coverage for different values of 



7.2.2. Tracking Overhead
In a first series of simulations, we evaluate the wake up protocol overhead and measured it through the number
Figure 7. Deployment efficiency.
Figure 8. Barrier continuity.
of additional messages due to the proposed scheduling and tracking scheme. For the deployment, we fixed the
sensing range 



number x of targets per time slot from 1 to 10 and measured, for each value of the arrival number, the average number of messages generated by the sensors tracking the targets during 500 time slots. In addition, without loss
of generality, we assumed that the trespassers travel through the shortest path or the longest paths (for 

The variation of the messages rate is illustrated in Figure 9, where it can be seen that overhead does not ex-
ceed 60 messages for 

Figure 9. Communication overhead.
targets attempt to cross the strip. This can be explained by the fact that a target induces the generation of 10 to 12 messages when, 

7.2.3. The Tracking Continuity
The tracking continuity is studied here for width of the wake up zone equal to



Finally, we assume that during simulation a large number of targets attempt to cross the strip from random
points on the border, and that these targets follow straight lines with directions varying randomly in 
Figure 10 depicts de average distance walked by a target towards the exit edge before a tracking disconnection is observed, knowing that the width of the strip is equal to 125 meters. When 
side of the squares where sensors are deployed, the tracking is guaranteed until exit when
7.2.4. The Estimation Efficiency
The final set of experiments discuss the size variation of the exit segment length report for the crossing targets with respect to the sensing range of the sensors and the angle
tice that, for




On the other hand, the segment length is lower than 


Figure 10. Average walked distance to exit.
Figure 11. Average exit segment length.
8. Conclusions
Border surveillance systems should comply with very constraining features to be efficient. In particular, they should provide immediate detection of trespassers and guarantee tracking continuity. The system presented in this paper includes various thick lines of surveillance along the country border. It reduced the energy consumption of tracking processes by reducing properly the number of sensors to wake up for tracking. It also provides a prediction technique capable of estimating the exit time and zone of crossing targets.
The results developed within this work can be extended to encompass the security of the monitoring network, sensor fault tolerance, and coverage holes. It also can be extended to various applications such as battlefields and mining.
Acknowledgements
The author is thankful to the Tunisian Ministry for High Teaching and Scientific Research for funding the research presented in this paper.
Cite this paper
Noureddine Boudriga, (2016) A WSN-Based System for Country Border Surveillance and Target Tracking. Advances in Remote Sensing,05,51-72. doi: 10.4236/ars.2016.51005
References
- 1. He, T., Krishnamurthy, S., Luo, L., Gu, L., Stoleru, R., Zhu, G., Sao, Q., Vicaire, P., Stankovic, J.A. and Abdelzaher, T. (2006) Vigilnet: An Integrated Sensor Network System for Energy Efficient Surveillance. ACM Transactions on Sensor Networks, 2, 1-38.
http://dx.doi.org/10.1145/1138127.1138128 - 2. Bhatti, S. and Xu, J. (2009) Survey of Target Tracking Protocols Using Wireless Sensor Network. Proceedings of the 5th International Conference on Wireless and Mobile Communications (IWCMC’09), Cannes, 23-29 August 2009, 110-115.
http://dx.doi.org/10.1109/icwmc.2009.25 - 3. Brooks, R.R., Ramanathan, P. and Sayeed, A.M. (2003) Distributed Target Classification and Tracking in Sensor Networks. Proceedings of the IEEE, 91, 1163-1171.
http://dx.doi.org/10.1109/JPROC.2003.814923 - 4. Li, X.R. and Jilkov, V.P. (2003) Survey of Maneuvering Target Tracking. Part I: Dynamic Models. IEEE Transactions on Aerospace and Electronic Systems, 39, 1333-1364.
http://dx.doi.org/10.1109/TAES.2003.1261132 - 5. Hieu, H.Q. and Thanh, V.D. (2006) Ground Mobile Target Tracking by Hidden Markov Model. Journal of Science and Technology Development, 9, 5-12.
- 6. Boudriga, N. (2014) On a Controlled Random Deployment WSN-Based Monitoring System Allowing Fault Detection and Replacement. International Journal of Distributed Sensor Networks, 2014, Article ID: 101496.
http://dx.doi.org/10.1155/2014/101496 - 7. Saipulla, A., Westphal, C., Liu, B. and Wang, J. (2009) Barrier Coverage of Line-Based Deployed Wireless Sensor Networks. Proceedings of the IEEE INFOCOM, Rio de Janeiro, 19-25 April 2009, 127-135.
http://dx.doi.org/10.1109/infcom.2009.5061914 - 8. Su, K.F., Wang, W.T., Wu, F.K. and Wu, T.T. (2009) K-Barrier Coverage with a Directional Sensing Model. International Journal on Smart Sensing and Intelligent Systems, 2, 75-93.
- 9. Chitnis, M., Liang, Y., Zheng, J.Y., Pagano, P., Lipari, G. (2009) Wireless Line Sensor Network for Distributed Visual Surveillance. Proceedings of the 6th ACM Symposium on Performance Evaluation of Wireless ad Hoc, Sensor, and Ubiquitous Networks, Tenerife, 26-30 October 2009, 71-78.
http://dx.doi.org/10.1145/1641876.1641890 - 10. Sun, Z., Wanga, P., Vuran, M.C., Al-Rodhaan, M.A., Al-Dhelaan, A.M., Akyildiz, I.F. (2011) Border Sense: Border Patrol through Advanced Wireless Sensor Networks. Ad Hoc Networks, 9, 468-477.
http://dx.doi.org/10.1016/j.adhoc.2010.09.008 - 11. Bellazreg, R., Boudriga, N. and An, S. (2013) Border Surveillance Using Sensor Based Thick-Lines. International Conference on Information Networking (ICOIN 2013), Bangkok, 28-30 January 2013, 221-226.
http://dx.doi.org/10.1109/ICOIN.2013.6496380 - 12. Pattem, S., Poduri, S. and Krishnamachari, B. (2003) Energy-Quality Tradeoffs for Target Tracking in Wireless Sensor Networks. Proceedings of the 2nd Workshop on Information Processing in Sensor Networks, IPSN’03, Palo Alto, 22-23 April 2003, 32-46.
http://dx.doi.org/10.1007/3-540-36978-3_3 - 13. Xu, Y., Winter, J., Lee, W.-C. (2004) Dual Prediction-Based Reporting for Object Tracking Sensor Networks. Proceedings of the 1st Mobile and Ubiquitous Systems (MOBIQUITOUS 2004), Boston, 22-26 August 2004, 154-163.
- 14. Dayana Pravin, V. and Vijeyakumar, K.N. (2012) Target Tracking in Sensor Networks Using Energy Efficient Prediction Based Clustering Algorithm. Procedia Engineering, 38, 2070-2076.
http://dx.doi.org/10.1016/j.proeng.2012.06.249 - 15. Kung, H.T. and Vlah, D. (2003) Efficient Location Tracking Using Sensor Networks. Proceedings of the IEEE Wireless Communications and Networking (WCNC’03), New Orleans, 16-20 March 2003, 1954-1962.
http://dx.doi.org/10.1109/wcnc.2003.1200686 - 16. Zhang, W. and Cao, G. (2004) DCTC: Dynamic Convoy Tree-Based Collaboration for Target Tracking in Sensor Networks. IEEE Transactions on Wireless Communications, 3, 1689-1701.
http://dx.doi.org/10.1109/TWC.2004.833443 - 17. Tsai, H.W., Chu, C.P. and Chen, T.S. (2007) Mobile Object Tracking in Wireless Sensor Networks. Computer Communications, 30, 1811-1825.
http://dx.doi.org/10.1016/j.comcom.2007.02.018 - 18. Heinzelman, W., Chandrakasan, A. and Balakrishnan, H. (2000) Energy-Efficient Communication Protocol for Wireless Sensor Networks. Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Hawaii, 4-7 January 2000.
http://dx.doi.org/10.1109/HICSS.2000.926982 - 19. Fan, X. and Song, Y. (2007) Improvement on LEACH Protocol of Wireless Sensor Network. Proceedings of the International Conference on Sensor Technologies and Applications, (SensorComm 2007), Valencia, 14-20 October 2007, 260-264.
http://dx.doi.org/10.1109/sensorcomm.2007.4394931 - 20. Chang, W.R., Lin, H.T. and Cheng, Z.Z. (2008) CODA: A Continuous Object Detection and Tracking Algorithm for Wireless Ad Hoc Sensor Networks. Proceedings of 5th IEEE Consumer Communications and Networking Conference, Las Vegas, 10-12 January 2008, 168-174.
http://dx.doi.org/10.1109/ccnc08.2007.44 - 21. Zhao, F., Shin, J. and Reich, J. (2002) Information-Driven Dynamic Sensor Collaboration. IEEE Signal Processing Magazine, 19, 61-72.
http://dx.doi.org/10.1109/79.985685 - 22. Olule, E., Wang, G., Guo, M. and Dong, M. (2007) RARE: An Energy Efficient Target Tracking Protocol for Wireless Sensor Networks. Proceedings of the International Conference on Parallel Processing Workshops, Xi’an, 10-14 September 2007, 1298-1306.
http://dx.doi.org/10.1109/icppw.2007.71 - 23. Walchli, M., Skoczylas, P., Meer, M. and Braun, T. (2007) Distributed Event Localization and Tracking with Wireless Sensors. Proceedings of the 5th International Conference on Wired/Wireless internet Communications (WWIC’07), Coimbra, 23-25 May 2007, 247-258.
http://dx.doi.org/10.1007/978-3-540-72697-5_21 - 24. Xu, Y., Winter, J. and Lee, W.C. (2004) Prediction-Based Strategies for Energy Saving in Object Tracking Sensor Networks. Proceedings of 2004 IEEE International Conference on Mobile Data Management, Berkeley, 19-22 January 2004, 346-357.
- 25. Abdelkader, M., Hamdi, M. and Boudriga, N. (2008) Voronoi-Based Sensor Network Engineering for Target Tracking Using Wireless Sensor Networks. Proceedings of the New Technologies, Mobility and Security Conference (NTMS’08), Tangier, 5-7 November 2008, 1-5.
http://dx.doi.org/10.1109/ntms.2008.ecp.102





























































