 Journal of Computer and Communications, 2014, 2, 38-45 Published Online July 2014 in SciRes. http://www.scirp.org/journal/jcc http://dx.doi.org/10.4236/jcc.2014.29006 How to cite this paper: Xia, X.N., Yu, J.G. and Cao, B.X. (2014) SCP-Trust Reasoning Strategy Based on Preference and Its Service Composition Process of Context-Aware Process. Journal of Computer and Communications, 2, 38-45. http://dx.doi.org/10.4236/jcc.2014.29006 SCP-Trust Reasoning Strategy Based on Preference and Its Service Composition Process of Context-Aware Process Xiaona Xia, Jiguo Yu, Baoxiang Cao School of Computer Science, Qufu Normal University, Rizhao, China Email: xiaxn@sina.com Received May 2014 Abstract Before providing services to the user, user preference considerations are the key conditions to achieve the self-adaptive decision-making about service selection and composition process, wh ich is the flexible concerned aspect provided by massive cloud computing environment data. Mean- while, during the whole services’ providing process, achieving the capturing and forming of ser- vice aggregation units’ topology logic, building the context environment’s process-aware of service composition, ensuring the trust and adaptation among service aggregation units, which are the important reasons to express timely requirement preference. This paper designs SCP-Trust Rea- soning strategy about the integration of user preference and trust, with process algebra, it is to achieve the context process-aware logic for service composition process, in order to improve the autonomous optimization and evolution of service implementation system. Keywords Preferences, Trust Reasoning, Context-Aware Process, Service Composition, Service Aggregation Unit 1. Introduction 1.1. Service and Cloud Technology With the rapid development of service and cloud computing, the business organization and topology building based Web services have gotten attention extensi vel y [1]-[4]. The integration of the two technologies make cloud services more rich, there are a large number of service resources in cloud, while it is difficult to select ser- vices for timely user requirements according to preferences, how to adaptively make out the countermeasures and topology implementation sequences by effectively analyzing preferences is the achievement goal of auto- nomous service selection and composition. However, the information interaction between users and service re- source pool, some information will often be missed or ignored as noise, which might cause imperfect require- ment conditions about service selection and composition, and does not fully reflect the trust and preferences, and even deviate from the real requirement substance, leading to the topological implementation results are not re-  X. N. Xia et al. quired by users, seriously, it causes the lack of information and destruction. 1.2. Related Work Zeng et al. [4] proposed a global optimization method based on integer rules, with the help of context require- ment, one optimal implementation path was selected; Ardagna and Pernic [5] concerned the global and local is- sues about services selection; Yu and Lin [6] used the requirement optimization and result of knapsack problem to achieve composition services selection; Korkmaz and Krunz [7] put forward a kind of heuristic composition services selection options; Driven by architecture implementation goal, Canfora et al. [8] used genetic algo- rithms to solve services selection process; Fan Xiaoqin et al. [9] designed a kind of discrete particle swarm algo- rithm to improve services’ response capacity about timely requirement. 2. Preferences Requirement Principle Based on the preference right re-determine method of rough sets [10] [11], capturing preference process is built in the platform, and does the grasping and learning timely during the interaction between users and services, that is the pre-conditions about preferences and services. Definition 1 (Preference Knowledge Supporting System). Four-tuple stands for this sys- tem. U is the non-empty finite object set; A is the non-empty finite attribute set, , . C is the condition attribute set, D is decision-making supporting attribute set; , is range of ; is a information function, it might give the information domain for every preference attribute. Definition 2 (Weight Re-measure of Preference attribute): Supposing is one subset of attribute, is a specific description, after adding specific value xi in X, the weight of service selection is improved, the greater of improving degree, xi is more important for X preferences, the important degree of attribute of xi for X is defined as: ( ) ( ) ( ) 1 i i Xx xi X pos U pSig xpos U = If P and Q is the equivalence relationship in U, the positive domain of P for Q is denoted as , , P means that all classified results might be collected in the preference object sets of rela- tionship Q according to . Objective preference weight is described as: ( ) ( ) 1 i i in xi i pSig x pG pSig x = = ∑ Objective weight is basic value, the comprehensive weight will be gotten: ( )( )()( ) 1pI QpG ωαωα ω = +− , is experience factor of preference, expresses the preference degree for subjective and objective weight in selecting services, the greater , the more important is the ensured requirement branch; the smaller , the implementation of requirement cares for objective weight more. When , the selection process only thinks about current requirement goals, does not do the cognitive exhibition; if , it is needed to consider objective weight and be aware of the learning and evolution analysis about requirement goals. 3. Preference-Driven Trust Relationship and Evaluation In order to extend and deepen the cognitive range of service customer SC, thereby enhancing complex synergy and the accuracy of service scheduling in different platforms, and increasing cross-organizational the effective- ness of service selection and composition. Assume that service provider of SP about service customer A of SC is , if the number of service customers interacting with m SP is n, under the premise of not involving preferences, its interactive evaluation records might be expressed as follows matrix structure:  X. N. Xia et al. 1,1 1,21,31, 2,12,22,32, 1.. ,1.. ,1 ,2 ,3, ,1 ,2 ,3, ... ... ............... ... ............... ... rr rr m rr rr m n Am rr rr i iiim rr rr n nnnm SQ SQSQSQ SQ SQSQSQ SQ SQ SQSQSQ SQ SQSQSQ = (1) Every element in matrix is the evaluation vector of the different service times, which is equivalent to ( 1)(2)(3)() , ,,,, ,, ,, rttttx ABAB ABABAB SQSQ SQSQSQ = , the same time, every element of vector is also a multidimen- sional vector, when it is expressed as 1,()2,()3,(),() ,,, ,, ,, ,, tjtjtjtjv tj ABAB ABABAB SQSQ SQSQSQ = , represents that is one v-dimensional vector. In matrix , ,1 ,2 ,3, , , ,, rr rr j jjjm SQ SQSQSQ express QoS of m service provider entities for this set of values might be recognized as m SP service providers in line with the actual target values, it might verify whether other SC service customer reflect QoS of SP service providers, furthermore, it might reduce its trust values: ( 1)(2)(3)() , ,,,, ,, ,, rttttx ABAB ABABAB SQSQ SQSQSQ = This formula represents QoS of SC service entity A for SP service provider B. Take any one element from , ( 1)(2)(3)() , ,,,, ,, ,, rttttx CBCB CBCBCB SQSQ SQSQSQ = , this formula QoS of SC service customer C for SP service provider B, because SC service customer C really completes its own evaluation, so that, it mi ght justify the trust of SC service customer C according to the differences’ evaluation of SC service customer for SP service provid- er B. From and , the evaluation vector of SC service customer A and SC entity C for SP service provider B about moment: 1,()2,( )3,( ),( ) ,,, ,, ,, ,, tjtjtjtjv tj ABAB ABABAB SQSQSQSQSQ = (2) 1,()2,( )3,( ),( ) ,,, ,, ,, ,, tjtjtjtjv tj CBCB CBCBCB SQSQ SQSQSQ = (3) Combining with the preferences analysis of the second part, the evaluation difference based on preferences is der ive: ()( ) ,( ),, , ,, 1 ,,, v Btjktjk tj ACm ABCB k A CBtjpIQQ ωω = ∆=∆=⋅− ∑ (4) Further, the ratio of the difference in value of the trust mi ght be calculated as: ,( ),(), ,, , 1 v B tjB tjktj ACACm AB k Q ϕω = = ∆∑ (5) ,( ),( ) ,, 1 B tjB tj AC AC C ψ =+Λ−⋅∂ (6) In Formula (6), represents the component of gradient, “ ” expresses arithmetic modulo, is con- stant value. When difference is smaller that threshold constant , it means credible, the smaller the difference value, the higher the trust. When the difference value is greater than , it means incredible, its trust values is negative. Thus through SP entity B, about SP service provider SC entity C, the trust evaluation of SP service customer A has the information evaluation vector: ,( 1),(2),() , ,,, , ,, BBt BtBtx ACAC ACAC C CCC = (7) Through the trust level method, if the trust evaluation , trust density value is 1, and 0 otherwise. requirement preference is the premise, the trust evaluation of other n SC is equivalent to ( ) ( ) , ,, ,, B BB ACAC AC pI f ω αβγ ⋅ , it is refined as the following matrix structure: 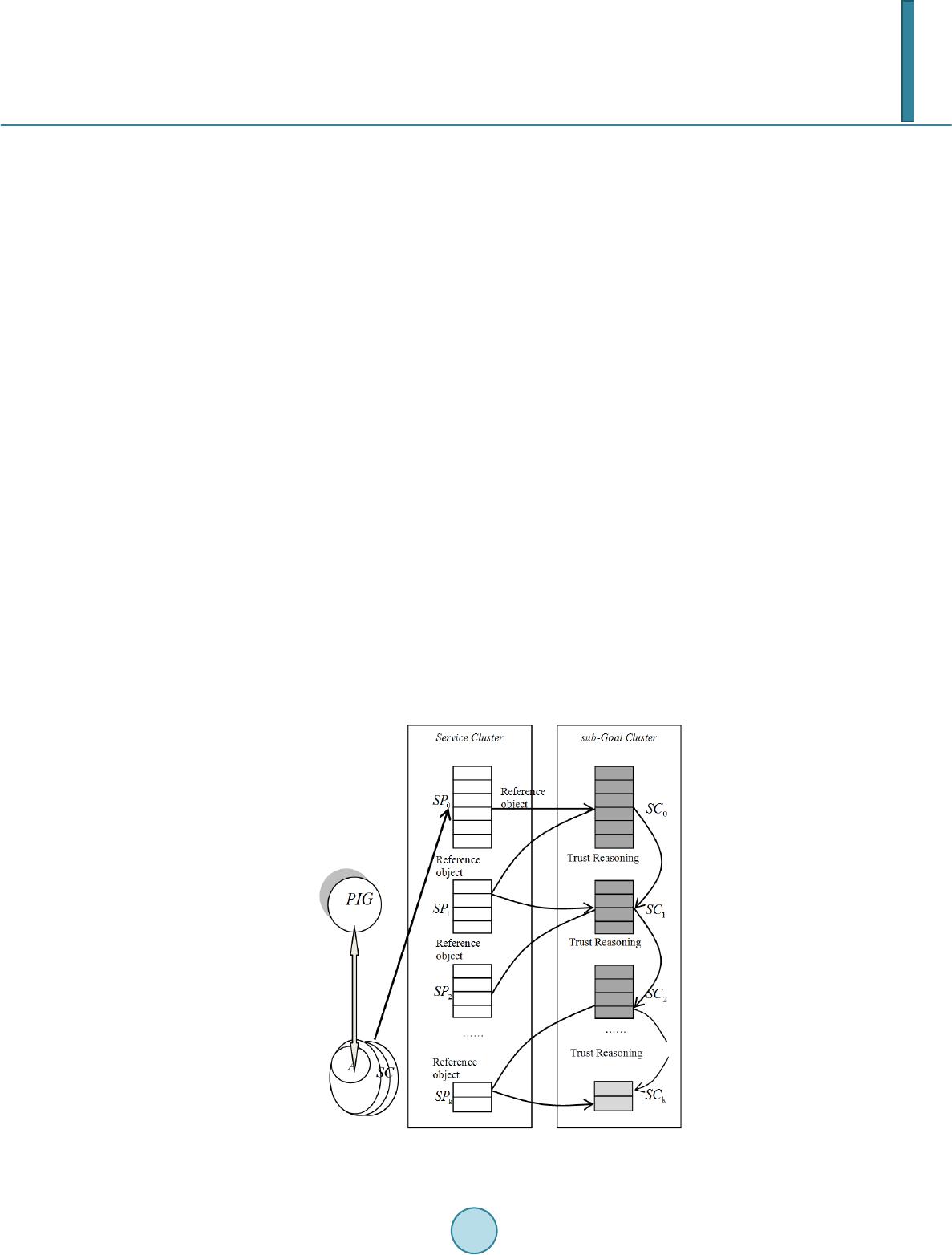 X. N. Xia et al. 123 ,1 ,1 ,1,1 123 ,2 ,2 ,2,2 1.. ,1.. 123 ,,, , 123 ,,, , ... ... ............... ... ............... ... m jjj j m jjj j n Am m jj jj jjjj n jm jm jmjn fff f fff f ffff f fff f = (8) 4. SCP-TP (Service Composition Preference-Trust Reasoning) SCP-TP is described as the follows: according to goal’s preferences, service entity SA might reduces its own trust relationship, which is showed as the interaction relationship between SA and SC0, the whole interaction ac- cepts the preference-driven effect of PIG (Platform Implementation Goal). SA is one set of SP entities interacted with SC entities A, SC0 is one set of SC entities interacted with SP entities in SA set. Because the preference im- plementation condition led by goal’s changing is the trust logic of SP of S Pk in Fig ure 1, which might gotten by the indirect trust relationship by PIG. Trust reasoning and process-aware in Figure 1 is described as follows: 1) Preferences of platform goal and real-time user requirement is mapped for PIG (related characterization described in the paper has been assigned), PIG realization is attributed to cluster logic set of SC service custom- er entity A. The serialization process of A is submitted by SP0, and does a series of reasoning that SC0 cluster set is the starting point, to get the trust value for S P1 cluster set. 2) Besides SC0 cluster set, SC interacted with SP1 cluster also introduces the reasoning and process-aware with SC1 cluster. Contrasting SC0 cluster and SC1 cluster about the difference of SP1 cluster, reduces the trust results of SC1. In this process, SP cluster entity is viewed as the reference of SC trust evaluation and reduces SC1 trust. In this way, tr ust reasoning and service goal might reduce SP1 cluster and SC1 cluster . 3) According to the second step of this process, further reasoning, it might get QoS weight of SPk cluster that its trust coincide s with preferences. SC0 driven by PIG has n entities, there are z entities in SC1, S P0 has m entities, SP1 is with y entities. Prefer- ence QoS evaluation matrix of SP1 se t related to PIG is described as: Figure 1. Trust reasoning and process-aware of SCP-TP.  X. N. Xia et al. 1,11,2 1,31, 2,12,22,32, 1.. 0,1.. ,1,2,3, ,1 ,2 ,3, ... ... ......... ...... ... ......... ...... ... rrr r y rrr r y ynrrr r j jjjy rrr r n n nny QQ fQ Qf ff QQf ff fff f = (9) Corresponding to QoS of SP entities adjusted by PIG, it might get the trust evaluation of n SC entities in SC0 set according to above reasoning and aware: () () ( ) () () ( ) () () ( ) ( ) 1,11,1 1,11,21,21,21,1,1, 2,12,1 2,12,22,22,22,2,2, 1.. 0,1.. ,1,1,1,2,2 ,2,2,2 , ,1,1 ,1,2 , ,,,...,, , ,,,...,, ...... ...... ,,, ,..., , ...... ...... ,, y yy y yy yn iiii iii iiy n nnn ff f ff f Tff f ff αβγαβγαβ γ αβγαβγαβγ αβγαβγαβγ αβγ α = ( ) ( ) ,2 ,2,2,2 , , ,...,, nnnnny f βγ αβγ (10) matrix represents QoS evaluation of SC0 about SP 1, matrix represents QoS evaluation of SC1 about SP1. Further might be obtained: 1,1 1,21,31, 2,1 2,22,32, 1.. 1,1.. ,1 ,2 ,3, ,1 ,2 ,3, ... ... ......... ...... ... ......... ...... ... rr rr y rr rr y yzrrrr i iiiy rr rr z zzzy QQQ Q QQQ Q QQQQ Q QQQ Q = (11) This process is described as: Step 1: Calculate the evaluation values of E and F for SP entity H, then reduce the trust of E about F, the evaluation difference value of H at moment is ( ) (), , , ,, 1 ,,, i ii u H tktkt EFim EHFH k EFHtQQ ηη ϖ = == − ∑ (12) Step 2: According to the above reasoning and PIG adjustment of SC and SP, it might reduce and get the trust about services’ participation: () , () ,,, 1 ii I u H tkt Ht EFEFmEH k PIG Q ϕ ηϖ = = ⋅ ∑ (13) () () ,, 1i IHt Ht EF EF T ϕσ =+ Λ−⋅ (14) The goal trust of service entity E and F during selecting and compositing of SP entity H scheduling by PIG is: 3 12 () () () () , ,,,, ,,,, v HtHt Ht Ht H EFEF EFEFEF T TTTT = (15) ( )( ) ()()( ) 123 , ,,,, ,,,,,,,,,,,,,, Hy EFEF EF EFEF f ffff αβγαβγ αβγαβγαβγ = (16) Further might get every S C1 service entity’s information evaluation of SC0 service entity E by SP1 set. Every participation entity’s trust evaluation of SC1 about SC service entity in SC0 is expressed in the left part of Fo r mu - la (17). j line of Formula (17) expresses the trust evaluation of j SC1 entity that service entity E has completed to refer different service provider SP1, then it might also get the trust evaluation process of E about every SC1 enti-  X. N. Xia et al. ty, it is showed as the right matrix structure in Formula (17). ( ) () ( ) ,1,1 ,1 12 ,1 ,2,1 12 ,2,2 ,2 ,2 ,2,2 12 ,1 ,1,1,1,1 ,1 12 ,, ,, ,, ,, ,, , idiridir idir jjj v jj jidiridir idir vjjj jj j vidiridir idir jj jjjjjjjj jj v jz jzjzidir jzj f ffff ff f fff f fff f αβγ αβγ αβγ αβ −− −−−− ⇒ ( ) ,, , idir idir z jz γ (17) Based on the above results, the trust calculation reasoning model driven by preferences between service pro- viders and service customers about PIG is Formula (18): ( )( )( ) ( )( )( ) ( ) 1,11,11,11,21,2 1,21,1,1, 2,12,12,12,22,22,22,2,2, ,1,1 ,1 ,, ,,, ,,,, ,, ,,, ,,,, ,, , idiridir idiridiridiridiridiridir idir zzz idiridir idiridiridiridiridiridir idir zzz idiridir idir nnn ff f ff f f αβγ αβγαβγ αβγ αβγαβγ α βγ ( )( ) ,2,2 ,2,,, ,, ,,,, idiridir idiridiridiridir nnnnznz nz αβγ αβγ (18) The first line of Formula (18) is corresponding to the first column of the right part in Formula (18), that ex- presses the corresponding trust evaluation of some service customer entity SC for every entity in SC1 set. Ac- cording to the above logical derivation process, SC0 is the starting point, SP1 deduces trust value of SC0 for SC1, then, S C0 is as the starting point, S P2 deduces trust value for S C2, it might get the trust about SCk in Fig ure 1. Through the above derivation process, we might obtain the QoS acquisition approach of QoS that there SP in- teracted with SC indirectly, and QoS evaluation model that direct interaction trust is precondition and user pre- ferences are the important factors adjusted by PIG. The trust and process-aware in Figure 1, according the above analysis and argumentation, temporary indirect trust about service selection and composition migh t get the transformation and indirect transition in Fig ure 2. This process might be described as: first, SC entity S might get the trust relationship of SC0. Secondly, according to the forward reasoning, it might get SP 0 entity D adjusted by PIG. Based on service composition and PIG, transition relationship of trust in Figure 2 achieves other indirect transition routing of trust. 5. Service Composition Process Based on Process-Aware Process topology and implementation semantic logic of CAPT, this part gives CCML description. <CCML: Composition> <CCML: sequence> <!--read channel--> <!--get PIG implementation decision-maki n g--> <CCML: Capture the activities about PIG, which are managed in some way> <!--read service transition channel based on the goal of some activity--> <CCML: readChannel Channel=“PIG_channelName” Service=“PIG_serviceName” action=“PIG_actio nName” port=“portName”> <!--implement one service activity--> <!--process-aware logic of PIG reads the context requirement and implement from corresponding service reg- ister channel. --> <!--read service register channel--> <CCML: readReg reg=“PIG_registerName” Service=“PIG_ServcieName” action=“PIG_actionName” port= “portName”> <CCML: execute action=“PIG_actionName” Service=“PIG_serviceName”> <!--write channel--> <CCML: writeChannel Channel=“PIG_ cha nnel N ame” Service=“PIG_serviceName” action=“PIG_actionName” port=“portName”> 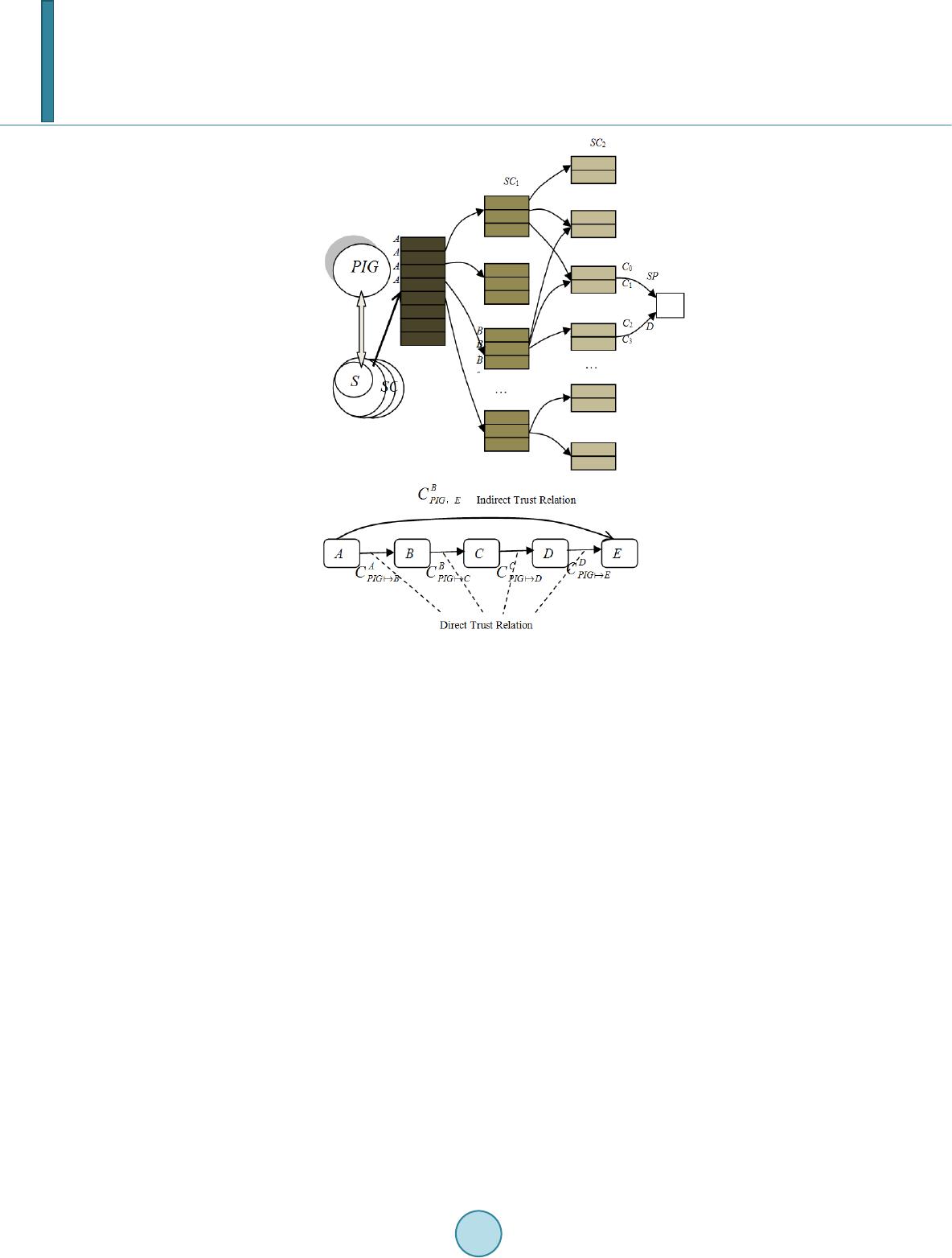 X. N. Xia et al. Figure 2. Transformation and transition of trust. <!--write service register channel--> <CCML: writeReg reg=“PIG_registerName” Service=“PIG_ServcieName” action=“PIG_actionName” port= “portName”> <CCML: execute action=“PIG_actionName” Service=“PIG_serviceName”> </CCML: sequence> </CCML: composition> 6. Conclusions Thinking about preferences of service selection and composition, this paper analyzes and argues the trust rea- soni ng strategies and implementation measures of service flow platform. For goal preferences and topology ef- fectiveness, this paper designs and achieves process-aware approach that PIG is the main adjustment mechanism, then gives the algorithm and adjustment platform logic for actual implementation case. In processing of problems, timely goal preferences of goal and trust reasoning of flow are the key problem in service computing and cloud computing, PIG fully considers goal preferences and topology trust, and reduces SCP-strategy logic, and achieves the context process-aware logic and implementation process. Through actual case’s R&D and optimal project of platform, it improves the autonomous optimization and evolution capacity of service flow. Acknowledgement s This paper is supported by National Natural Science Foundation of China (61373027, 11101243), Natural Science Foundation of Shandong Province of China (ZR2012FQ011, ZR2012FM023, ZR2009GM009), the Key Science-Technology Development Project of Shandong Province of China (No. 2009GG10001014, 2012GGX10123) and Promotional Foundation (2005BS01016) for Middle-aged or Young Scientists of Shan- dong Province, SRI of SPED (J12LN06, J07WH05), DRF and UF (3XJ200903, XJ0609) of QFNU.  X. N. Xia et al. References [1] Zhang, J.-L. and Fan, Y.-S. (2010) Service-Oriented Enterprise and Business Ecosystem. Computer Integrated Manu- facturing Systems, 16, 1751-17 59. [2] Xu, L.-D., Liu, H.-M., Wang, S., et al. (20 09 ) Modeling and Analysis Techniques for Cross-Organizational Workflow Systems. Systems Research and Behavioral Science, 26, 367-389. http://dx.doi.org/10.1002/sres.978 [3] Armbrust, M., Fox, A., Griffith, R., et al. (20 10 ) A View of Cloud Computing. Communications of the ACM, 53, 50- 58. http://dx.doi.org/10.1145/1721654.1721672 [4] Zeng, L.Z., Benatallah, B., Hgu, A.H.H., et al. (2004) QoS-Aware Middleware for Web Services Composition. IEEE Trans on Software Engineering, 30, 311-327. http://dx.doi.org/10.1109/TSE.2004.11 [5] Ardagna, D. and Pernici, B. (2005) Global and Local QoS Guarantee in Web Service Selection. Proceedings of Busi- ness Process Management Workshops, Springer, Berlin, 32-46. [6] Yu, T. and Lin, K. (20 05 ) Service Selection Algorithms for Composing Complex Services with Multiple Qos Con- straints. Proceedings of the 3rd International Conf erence on Service Oriented Computing, Springer, Berlin, 130-143. [7] Kor mza , T. and Krunz, M. (2001) Mul ti-Constrained Optimal Path Selection. Proceedings of the 20th Joint Conference of IEEE Computer and Communications, Piscataway, 834-843. [8] Canfora, G., Penta, M.D., Esposito, R., et al. (2005) An Approach for QoS-Ware Service Composition Based on Ge- netic Algorithms. Proceedings of the 2005 Con f erence on Genetic and Evolutionary Computation, ACM, New York, 1069-1075. [9] Fan, X.Q., Jiang, C.J., Fang, X.W., et al. (2010) Dynamic Web Service Selection Based on Discrete Particle Swarm Optimization. Journal of Computer Research and Development, 47, 147 -156. [10] Beynon, M. (2001) Reduces within the Variable Precision Rough Sets Model: A Further Investigation. European Journal of Operational Research, 134, 592 -605. http://dx.doi.org/10.1016/S0377-2217(00)00280-0 [11] Po mykala , J. (1988) The Stone Algebra of Rough Sets. Bulletin of the Polish Academy of Sciences, 36 , 495-50 7 .
|