Paper Menu >>
Journal Menu >>
 Wireless Sensor Network, 2011, 3, 83-91 doi:10.4236/wsn.2011.33009 Published Online March 2011 (http://www.SciRP.org/journal/wsn) Copyright © 2011 SciRes. WSN A Fault-Tolerant Cooperative Spectrum Sensing Algorithm over Cognitive Radio Network Based on Wireless Sensor Network Mohammad Akbari, Abolfazl Falahati Department of Electrical Engineering (School of Secure Communication), Iran University of Science and Technology, Narmak, Tehran E-mail: m_akbari@elec.iust.ac.ir, afalahati@iust.ac.ir Received January 25, 2011; revised February 15, 2011; accepted March 8, 2011 Abstract A serious threat to cognitive radio networks that sense the spectrum in a cooperative manner is the transmis- sion of false spectrum sensing data by malicious sensor nodes. SNR fluctuations due to wireless channel ef- fects complicate handling such attackers even further. This enforces the system to acquire authentication. Actually, the decision maker needs to determine the reliability or trustworthiness of the shared data. In this paper, the evaluation process is considered as an estimation dilemma on a set of evidences obtained through sensor nodes that are coordinated in an underlying wireless sensor network. Then, a likelihood-based com- putational trust evaluation algorithm is proposed to determine the trustworthiness of each sensor node's data. The proposed procedure just uses the information which is obtained from the sensor nodes without any pre- sumptions about node’s reliability. Numerical results confirm the effectiveness of the algorithm in eliminat- ing malicious nodes or faulty nodes which are not necessarily conscious attackers. Keywords: Cognitive Radio Network (CRN), Cooperative Spectrum Sensing, Wireless Sensor Network (WSN), Trust Evaluation, Maximum Likelihood Estimation (MLE) 1. Introduction One of the main limitations in developing next genera- tion networks and new services for the existing networks is bandwidth scarcity. Cognitive radio network is a novel idea that will overcome the spectrum scarcity problem with providing the capability of sharing the wireless channel between unlicensed users (secondary users (SU)) and licensed users (primary users (PU)) in an oppor tun is- tic manner. The PUs take precedence of the SUs in spec- trum access; a cognitive radio should not communicate on a channel that is being used by a licensed user [1-2]. This point makes the spectrum sensing process an essen- tial, a process for discovering the spectrum holes or dis- covering the presence of an active PU in the desired band. The spectrum sensing procedure can be accomplished individually or in a cooperative manner. Cooperative spectrum sensing itself might be accomplished via either decision fusion or data fusion [3]. In a data fusion scheme, SUs share their primary collected data from RF stimuli in a Fusion Center (FC) which decides the pres- ence or the absence of the PUs in the desired band using the shared information. However, in a decision fusion approach the CR nodes send their decision (that are made individually) to FC for final decision. Match filtering; cyclo-stationary feature detection and energy detection are three well-known methods which are used to sense the CR spectrum [4]. The proposed method in this paper is based on energy detection A. Taherpour et al. [5] proposed an energy-detection based data fusion method and show that in fading chan- nels Equal Gain Combining (EGC) data fusion has near-optimal performance without the requirement of channel gains estimation. According to their method if the measured energies average that is reported by coor- dinated nodes becomes larger than a specific threshold value the presence of the PU can be assumed to be true, otherwise the absence of the PU becomes true. They have shown that when the SNRs of the SUs are large enough the detector approaches the optimum detector. However, Signal to Noise Ratio (SNR) fluctuations due 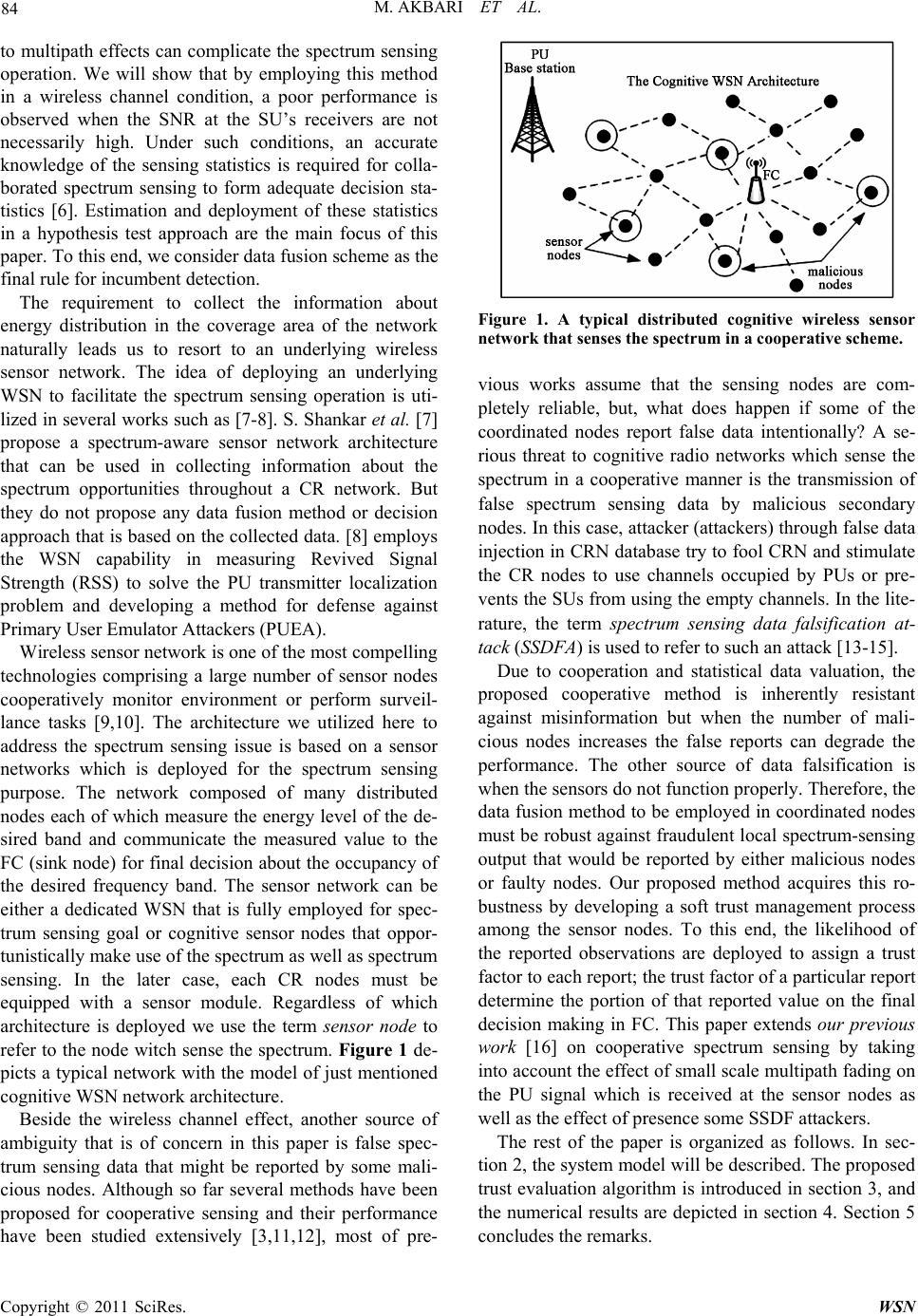 M. AKBARI ET AL. Copyright © 2011 SciRes. WSN 84 to multipath effects can complicate the spectrum sensing operation. We will show that by employing this method in a wireless channel condition, a poor performance is observed when the SNR at the SU’s receivers are not necessarily high. Under such conditions, an accurate knowledge of the sensing statistics is required for colla- borated spectrum sensing to form adequate decision sta- tistics [6]. Estimation and deployment of these statistics in a hypothesis test approach are the main focus of this paper. To this end, we consider data fusion scheme as the final rule for incumbent detection. The requirement to collect the information about energy distribution in the coverage area of the network naturally leads us to resort to an underlying wireless sensor network. The idea of deploying an underlying WSN to facilitate the spectrum sensing operation is uti- lized in several wo rks such as [7-8]. S. Sh ankar et al. [7] propose a spectrum-aware sensor network architecture that can be used in collecting information about the spectrum opportunities throughout a CR network. But they do not propose any data fusion method or decision approach that is based on the collected data. [8] employs the WSN capability in measuring Revived Signal Strength (RSS) to solve the PU transmitter localization problem and developing a method for defense against Primary User Emulator Attackers (PUEA). Wireless sensor network is one of the most compelling technologies comprising a large number of sensor nodes cooperatively monitor environment or perform surveil- lance tasks [9,10]. The architecture we utilized here to address the spectrum sensing issue is based on a sensor networks which is deployed for the spectrum sensing purpose. The network composed of many distributed nodes each of which measure the energy level of the de- sired band and communicate the measured value to the FC (sink node) for final decision about the occupancy of the desired frequency band. The sensor network can be either a dedicated WSN that is fully employed for spec- trum sensing goal or cognitive sensor nodes that oppor- tunistically make use of the spectrum as well as spectrum sensing. In the later case, each CR nodes must be equipped with a sensor module. Regardless of which architecture is deployed we use the term sensor node to refer to the node witch sense the spectrum. Figure 1 de- picts a typical network with the model of just mentioned cognitive WSN network architecture. Beside the wireless channel effect, another source of ambiguity that is of concern in this paper is false spec- trum sensing data that might be reported by some mali- cious nodes. Although so far several methods have been proposed for cooperative sensing and their performance have been studied extensively [3,11,12], most of pre- Figure 1. A typical distributed cognitive wireless sensor network that senses the spectrum in a cooperative scheme. vious works assume that the sensing nodes are com- pletely reliable, but, what does happen if some of the coordinated nodes report false data intentionally? A se- rious threat to cognitive radio networks which sense the spectrum in a cooperative manner is the transmission of false spectrum sensing data by malicious secondary nodes. In this case, attacker (attackers) through false data injection in CRN database try to fool CRN and stimulate the CR nodes to use channels occupied by PUs or pre- vents the SUs from using th e empty channels. In the lite- rature, the term spectrum sensing data falsification at- tack (SSDFA) is used to refer to such an attack [13-15]. Due to cooperation and statistical data valuation, the proposed cooperative method is inherently resistant against misinformation but when the number of mali- cious nodes increases the false reports can degrade the performance. The other source of data falsification is when the sensors do not function properly. Therefore, the data fusion method to be employed in coordinated nodes must be robust against fraudulent local spectrum-sensing output that would be reported by either malicious nodes or faulty nodes. Our proposed method acquires this ro- bustness by developing a soft trust management process among the sensor nodes. To this end, the likelihood of the reported observations are deployed to assign a trust factor to each report; the trust factor of a particular report determine the portion of that reported value on the final decision making in FC. This paper extends our previous work [16] on cooperative spectrum sensing by taking into account the effect of small scale multipath fading on the PU signal which is received at the sensor nodes as well as the effect of presence some SSDF attackers. The rest of the paper is organized as follows. In sec- tion 2, the system model will be described. The proposed trust evaluation algorithm is introduced in section 3, and the numerical results are depicted in section 4. Section 5 concludes the remarks.  M. AKBARI ET AL. Copyright © 2011 SciRes. WSN 85 2. Basic Assumptions and System Model A cooperative spectrum sensing scheme employing energy detection under fading channel condition is con- sidered as illustrated in Figure 1. It is assumed that a total number of N sensor node in an underlying WSN are coordinated to detect the spectrum holes of a frequency band which is licensed for primary users of a primary network. The sensor nodes send their collected data to the fusion center for final decision for the absence or the presence of primary users in the desired frequency band [13,14,16]. The channel model between primary base station and sensor nodes is assumed to be Nakagami multipath fad- ing [17-21]. The observation time interval T is small enough to presume that all received signal at energy de- tectors (CR nodes) experience the same fading condition during the observation. Besides uncertainty of reported energy that is measured by sensor devices due to multi- path fading phenomena and/or their malfunctioning be- haviour, it must be considered that a group of malicious nodes may try to misinform the FC. This issue is shown in Figure 1 where the attacker nodes with a circle drawn around them are determined. Figure 2 depicts the fusion center block diagram with the following variables: E 1: A 1N vector, represents reported energy of desired channel measured by N sensor nodes. E : Prefiltering output, a M 1 vector. i TF : Trust factor assigned to ith sensor node The actual model performance is obtained by per- forming three procedures namely pre-filtering, trust evaluation and data fusion. The sensor nodes use an energy detector for sensing the spectrum. if rt represents the PU signal at the energy detector input of the sensor nodes under two hypotheses 0 H or 1 H , i.e. absence or presence of a legitimate signal respectively, then: 0 1 nt H rt s tnt H (1) where, nt is an Additive White Gaussian Noise (AWGN) with zero mean and variance of 02N; s t represents the primary user signal which is influenced by the wireless channel. It is assumed that the sensor nodes sense the spectrum synchronously; thanks to the under- lying WSN, the FC will be able to obtain a snapshot of the current state of signal energy distribution in its cov- erage area through the WSN network. This Synchroniza- tion can be obtained easily by a beacon transmission Figure 2. Fusion center block diagram repres entation. through central node or other well-known methods such as GPS [22]. 3. Cooperative Spectrum Sensi n g A l g or i th m Based on Statistical Data Assessment In the following, each one of the three components of the proposed method will b e described in detail. 3.1. Prefiltering In order to determine the trustworthiness of the sensor node’s reports, a trust management process is developed throughout the sensor network. The trust evaluation al- gorithm is formulated as an estimation problem on a set of evidences ,1 i kek iNE obtained from distributed sensor nodes in kth sensing time. Very large or very small malicious node’s reported values, depending upon the channel state, can extremely affect the esti- mated parameters and the trust evaluation. After receiv- ing the reported i eks, pre-filter rejects these outliers that do not match the other reports. The chosen method for the outlier detection is a simple but efficient algo- rithm that is suitable to identify outliers with extreme different values in comparison with the others in a set [23]. Based on this algorithm, any particular value of the set of reported energy i eks should be tested to be in , lu ee interval, otherwise, that value will be known as outlier. The upper bound u e, and lower bound l e, for values i ek s can be determined as [23]: 3 3 u l e e (2) where, and are mean and standard deviation of the set of i eks respectively. 3.2. Statistical Assessment and Trust Assignment to the Observations 1) Trust Inference (Statistical Assessment) of The Ob- servation over AWGN Channel: It is well-known that under the AWGN channel condition assumption, in the absence of any deterministic signal, the reported random 1Hereinafter, we indicate the vectors with bold-face capital letters, random processes with capital letters indexed by time variable (e.g. X(t)), random variables with capital letters and others with minuscule letters.  M. AKBARI ET AL. Copyright © 2011 SciRes. WSN 86 variable i ek (which is normalized by two sided noise power spectral density 02N) will have a central Chi- square distribution. However, if a deterministic signal with energy s E is present at the energy detector input, the reported value of i ek will have a noncentral Chi-square distribution [24] as: 2 20 2 201 2 TW i TW s H EEN H (3) T, W and s E are the observation time, channel band width and signal energy average 2 0d T s Estt respectively. After prefiltering, we will have a vector of M values 1, , i ek iM which are samples of M random processes i E with known distribution (central Chi-square or noncentral Chi-square) but unknown pa- rameters value. The principle of maximum likelihood (ML) assumes that the sample data set E represents the 1,,; M fe e E population and it chooses those values for that most likely cause the observed data to occur [25]. So, given 1,, ii EekiM, the ML estimate for can be determined from the likelihood equation as [25]: 1 ˆmax, ,; i iMi E fe e (4) hence, 1 log, ,;ˆ0 ii M E i i fee (5) It is supposed that the sensor nodes are distributed in a large geographical area, so it can be said that the re- ceived signal at each sensor experiences identical inde- pendent channel condition (i.i.d.) [5], thus: 11i i M ii MEi E i= fe,,e;θ=fe,θ (6) Now, using ML estimator (MLE), we will be able to estimate the probability distribution ii Ei fe,θ. But- what is the pdf type of the observation? Central Chi- square or noncentral Chi-square? In order to give a pre- cise estimation on the parameters, we should know the pdf type of the process which is sampled by sensor nodes. This means, we should know the presence or absence of the PU in the under investigation band. To break the tie, we use an approximation model known as Torrieri model [26] that approximates a chi-squa re (ce ntral or no ncentral) as a Gaussian distribution: 2 00 0 2 11 1 , , i NH E NH (7) where 0 and 2 0 σ are the mean and variance of the energy detector output when 0 H is correct (i.e. no sig- nal present), and 1 and 2 1 are the mean and vari- ance of the energy detector output when 1 H is correct. If 1TW is satisfied the given model provide an ade- quate accuracy [26]. Substitution of (7) into (6) and em- ployment of (5), the i e s distribution parameters can be estimated in a straight forward manner. For a normal distribution, as indicated in (8), it can be shown easily that MLE gives a simple closed form equation to estimate 2 , ii parameters that will be suitable for a frequent- ly used evaluation algorithm: 0 2 2 0 10, 1 10,1 M ri i M rir i er M er M (8) Utilizing (8), we will be able to estimate the unknown parameters introduced in (7). In fact, (7) determines the probability distribution function for received power over the channel and also provides valuable information for FC to determine the expectancy of reported data. This expectancy helps FC to obtain the reliability of the node’s reports that can be used to eliminate the malicious users influence on the primary user detection. The pro- posed algorithm steps for trust factor evaluation are summarized as follows: 1) Given detected energies 1, , i ek iM, first estimate the mean and variance of ][kei probability distribution function through (8), 2) Assign unnormalized trust factor ' i TF , to ith de- tected energy, ' i iEii TFfEe k (9) 3) Normalized trust factor ' i TF for ith CR user in kth iteration will be as: M i ' i ' i iTF TF TF 1 (10) It is worth noting that the normalized-computed trust factor in (10) just determines the portion of correspond- ing nodes in final spectrum decision. One should con- sider that the trust factor of a node in comparison with trust factor of the other nodes would be a meaningful value. To include the pre-determined i TF s values, the calculation of i TF in previous subsection is modified as: 0 1 H ipi i p TF kTF kpTF (11) This means, the trust factor i TFk in kth iteration is  M. AKBARI ET AL. Copyright © 2011 SciRes. WSN 87 the weighting average of the current evaluated trust fac- tor i TF which is assigned to i ek and H-1 previously determined trust factors (1,,1) i TF kppH . 01 p determines the portion of th kp assigned trust factor in the th k iteration and is defined as: 1 0 1 1 pH p pH pH (12) 1 and H are the actual design parameters. 1 corresponds to a linear decrease in participation of older judgments. Whatever a larger value to be selected for , the older judgment participation decreases much faster. 2) Trust Inference (Statistical Assessment) of The Ob- servation over Nakagami fading channel: When the re- ceived signal experiences the multipath fading condition, (3) is true for 0 H hypothesis only. Because, in the ab- sence of the legitimate signal the energy detector just measures the noise energy level of the channel thus its distribution depends on the noise model only. To solve this problem, we rewrite 1i P ekH as 00 11 0 ii ii Pe kPekHPH PekH PHPekH follows a central chi-square distr ibution but 1i Pe k H is generally unknown. In th e following, we determine the conditional probability of 1i Pe k H if the PU’s signal experiences a Nakagami multipath fading channel with parameter m. In this case, probability density func- tion of instant received power p at energy detector is [17]: 1 1 |e () r mmp m P p r mp fpH Pm (13) From (13), the probability density function of 1, ii P EekHp is a noncentral Chi-square distri- bution 2 20 2 TW pTN with two parameters 2TW and 0 2pT N which determine the degree of freedom and the noncentrality respectively [24]. Therefore: 111 0,d iiii p P EekH PEekHpfpHp (14) where r P is the average received power. Furthermore, 1i P ekH can be rewritten as: 0 1 211 2 0 2 /2 10 , 1 22 2 i ii pT ek TW N i ki PEe kHp ekN epT IekpTN (15) where x I is a modified Bessel function of the first kind. Substitution of (15) and (13) in (14) produce a complex expression for 1ii PEe k H which can be solved numerically. Thus, in order to obtain an ana- lytical closed form expression, an approximate solution is desired. To achieve this goal, we use an approximation model known as Torrieri model [26] that approximates a noncentral chi-square 2 20 2 TW pT N as a Gaussian distribution with mean and variance of 0 NTW pT and 2 00 NTWNpT respectively. If 1TW is satis- fied, the given model provides an adequate accuracy [26,27]. Utilizing (13) and applying the normal approxi- mation, (14) can be rewritten as: 2 02 0 2 0 2 0 1 02 00 1 2 012 00 2 1 1 2( ) eed 2 ed i r i r ii ekNTW pTmp m Pk NTW r m r m ekNTW pTmp TP k NTW m PEe k H NTWNpT mp p Pk m m P mTNTW NpT pp (16) In low power detection schemes, i.e. when the SNR at energy detector is small, the signal of )(ts has a little effect on the variance of the test statistics [26]. So, we can ignore pTN0 and assume that the variance of the PU signal is 2 0 NTW in either decision cases. Consi- dering these assumptions and performing some mathe- matical manipulation, (16) will be simplified as: 2 2 2 0 12 11 02 0 d 2 pC m NTW ii p PEe k HCep NTW (17) where, 1 C and 2 C are given by: 12 2242 000 2 0 2 2 1 12 200 e ri r m mNWPkekNTWmNPkW rNTW m ir m P CmT CekNTWmPkNW (18) Finally, using the well-known properties of the Gaus- sian function can be easily shown that: 2 2 2 0 1 12 102 0 d 2 ii pC m NTW PEe k H p Cep NTW  M. AKBARI ET AL. Copyright © 2011 SciRes. WSN 88 2 2 2 0 22 0 2 2 2 102 00 2 120 2 112 00 2 1 limee d 2 lim e 1 ()e d 2 pC m NTW sp m s sNTW msC m s x x Cp sNTW CsNTW CQ sNTW Qx x (19) where, is the Gaussian Q-function. Equation (19) pro- vides a closed-form relationship for computing 1ii PEe k H. Finally, our proposed relationship for determining the conditional probabilities 1ii PEe k H and 0ii PEe k H will be as follows: For a channel model with specific value of the para- meter m, (20) should be calculated as a function of i ek only once and to be used repeatedly. In order to determine (20) for channel models with different values of parameter m, higher order derivatives of the Q func- tion is necessary. It can be easily shown that: 22 11 2,1 nnx nnn ax Qx e axaxxaxax (21) Now, substituting (20) into 00 11ii i PekPek|HPHPek HPH we will be able to determine the likelihood of each pre- filtered report i ek and determine the trust factor fol- lowing the steps of trust evaluation algorithm that is pre- sented in part 1. 3.3. Data Fusion Algorithm Final decision for the presence or the absence of primary user in desired frequency band is devolved to data fusion block. This block deals with a group of reported energies with their known trust factors that are computed from (11). Generally speaking, every existing data fusion ap- proach which is modified to include the reliability of each component can be deployed. The simplest one is weighting average combination scheme: , 1 K ik i iek E (22) where ki, is weighting factor for particular i ek component and for our model is considered as its eva- luated trust factor ,ik i TF k . Final decision for hypothesis 0 H or 1 H is based on the calculated weighting average E, i.e. if T eE is correct the channel is occupied, otherwise, the channel is empty. Where, T e is a function of false alarm probabil- ity fa P, and should be evaluated numerically. f a P de- termines the probability that a free channel (spectrum hole) is imagined occupied wrongly. 4. Performance Evaluation Using computer simulation, the performance of the pro- posed spectrum sensing method is evaluated and is com- pared with the reference model (EGC) as bearing the following steps: 4.1. Simulation Setup Assume a group of N sensor nodes that are coordinated to sense the spectrum with the model as shown in Figure 1. The channel model between the CR nodes and the PU’s base station is assumed to be Nakagami with 1 m, i.e. a Rayleigh fading channel. Mean received SNR at the CR users considered to be –10 dBm. Obser- vation interval T and channel bandwidth W are chosen such that TW = 100. H and both are chosen to be 3. T e is determined numerically such that 0.01 fa P when no malicious node is present. The conditional probability of (20) for 1 m will be as: 12 22 00 12 0 1 22 00 2 2 0 e 2 1e i ri r TW ek i i TW ii iWPkekNTWNPkWf jr TW i r ek H H TW PEe k H ekNTWPkNW QH PkT NTW 1 H 22 0 2 12 0 2 120 2 1 1 12 00 e 2 | lim e i TW ek i i TW ii isNTW msC i m s ek H H TW PEe kHCsNTW CQ HH sNTW (20)  M. AKBARI ET AL. Copyright © 2011 SciRes. WSN 89 Although this relationship may at first seem compli- cated; in fact, considerable parts of this relationship are fixed values that need to be calculated only once. To evaluate 00 11ii i Pe kPek HPHPe k HPH and make the final decision for hypothesis 0 H or 1 H for the fading channel case, the priority probabilities of 0 PH and 1 PH must be determined. Several methods are proposed for estimating these parameters, one of which is the method that is proposed by H. Kim in [28]. Without loss of generality, for simplicity in the simulation we assumed that 01 0.5PH PH. To evaluate the performance of the given method, two prevalent parameters f a P (false alarm probability) and d P (detection probability) are considered. fa Pdeter- mines the ability strength of the applied method for de- tecting the spectrum holes and has impact on the spectral efficiency of the CRN; but, d Pdetermines the ability strength of the employed method in detecting and avoid- ing interference with the PUs. If i H shows the decision about channel occupancy at the FC, false alarm and de- tection probability are defined as: 10 11 fa i di PPHHH PPHHH (23) 4.2. Simulation Results To test the power of the proposed method in eliminating the effect of malicious sensor nodes or faulty nodes in the process of decision making about channel occupancy, worst condition is assumed; i.e., when the channel is occupied, malicious nodes report the smallest possible value which can be passed from the pre-filter block, but when the channel is free, malicious nodes report largest possible value which can be passed from the pre-filter. The false alarm probability of the proposed method for N = 50, N = 100, N = 200, N = 200 and N = 300 are depicted in Figure 3 and is compared with EGC method [5]. As can be seen from Figure 3, the proposed trust algorithm works quite well in the presence of noticeable percentage of malicious nodes. The effect of malicious nodes, up to 18% of total no des, is eli minated completely; Whereas, in similar conditions and for the same mali- cious nodes number, false alarm probability correspond- ing to EGC method is bigger than 0.97. Figure 4 shows the detection probability of the pro- posed method in comparison with EGC. When the mali- cious node percent increase to 22%, the performance of simple averaging and our trust algorithm becomes similar. However, the performance of simple averaging decreases Figure 3. False alarm probability Pfa of the proposed me- thod and EGC vs. malicious nodes percentage. Figure 4. Detection probability Pd of the proposed method and EGC vs. malicious nodes percentage. Figure 5. The effect of H on Pd. drastically for higher percentages of malicious nodes. When 30% of cooperating nodes are malicious, the de- tection probability of simple averaging is decreased to 0.5, whereas, the detection probability of proposed trust algorithm is bigger than 0.97. However, the performance of simple averaging de- creases drastically for higher percentages of malicious nodes. When 30% of cooperating nodes are malicious, the detection probability of simple averaging is de- creased to 0.5, whereas, the detection probability of pro posed trust algorithm is bigger than 0.97. 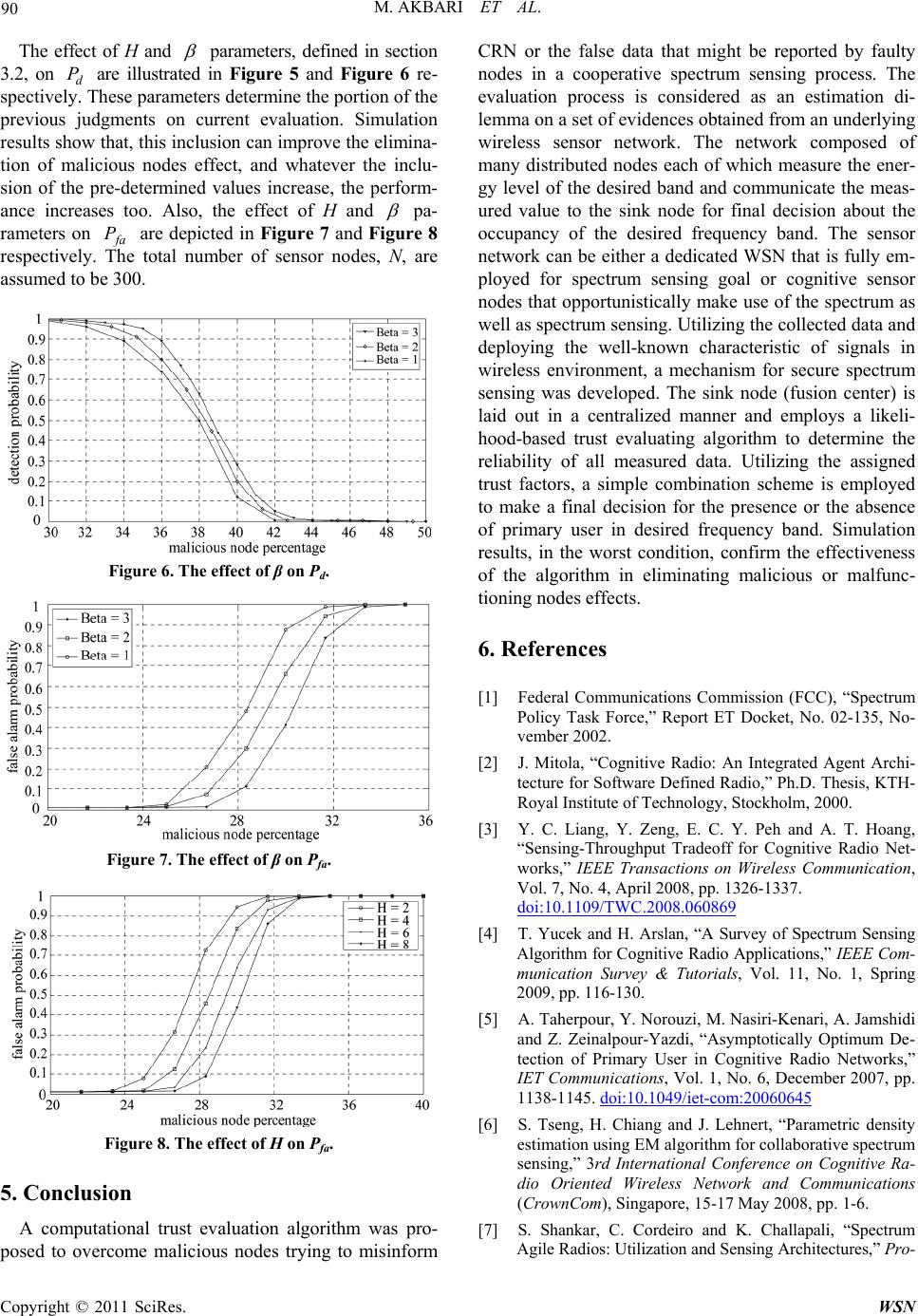 M. AKBARI ET AL. Copyright © 2011 SciRes. WSN 90 The effect of H and parameters, defined in section 3.2, on d P are illustrated in Figure 5 and Figure 6 re- spectively. These parameters determine the portion of the previous judgments on current evaluation. Simulation results show that, this inclusion can improve the elimina- tion of malicious nodes effect, and whatever the inclu- sion of the pre-determined values increase, the perform- ance increases too. Also, the effect of H and pa- rameters on fa P are depicted in Figure 7 and Figure 8 respectively. The total number of sensor nodes, N, are assumed to be 300. Figure 6. The effect of β on Pd. Figure 7. The effect of β on Pfa. Figure 8. The effect of H on Pfa. 5. Conclusion A computational trust evaluation algorithm was pro- posed to overcome malicious nodes trying to misinform CRN or the false data that might be reported by faulty nodes in a cooperative spectrum sensing process. The evaluation process is considered as an estimation di- lemma on a set of evidences obtained from an underlying wireless sensor network. The network composed of many distributed nodes each of which measure the ener- gy level of the desired band and communicate the meas- ured value to the sink node for final decision about the occupancy of the desired frequency band. The sensor network can be either a dedicated WSN that is fully em- ployed for spectrum sensing goal or cognitive sensor nodes that opportunistically make use of the spectrum as well as spectrum sensing. Utilizing the collected data and deploying the well-known characteristic of signals in wireless environment, a mechanism for secure spectrum sensing was developed. The sink node (fusion center) is laid out in a centralized manner and employs a likeli- hood-based trust evaluating algorithm to determine the reliability of all measured data. Utilizing the assigned trust factors, a simple combination scheme is employed to make a final decision for the presence or the absence of primary user in desired frequency band. Simulation results, in the worst condition, confirm the effectiveness of the algorithm in eliminating malicious or malfunc- tioning nodes effects. 6. References [1] Federal Communications Commission (FCC), “Spectrum Policy Task Force,” Report ET Docket, No. 02-135, No- vember 2002. [2] J. Mitola, “Cognitive Radio: An Integrated Agent Archi- tecture for Software Defined Radio,” Ph.D. Thesis, KTH- Royal Institute of Technology, Stockholm, 2000. [3] Y. C. Liang, Y. Zeng, E. C. Y. Peh and A. T. Hoang, “Sensing-Throughput Tradeoff for Cognitive Radio Net- works,” IEEE Transactions on Wireless Communication, Vol. 7, No. 4, April 2008, pp. 1326-1337. doi:10.1109/TWC.2008.060869 [4] T. Yucek and H. Arslan, “A Survey of Spectrum Sensing Algorithm for Cognitive Radio Applications,” IEEE Com- munication Survey & Tutorials, Vol. 11, No. 1, Spring 2009, pp. 116-130. [5] A. Taherpour, Y. Norouzi, M. Nasiri-Kenari, A. Jamshidi and Z. Zeinalpour-Yazdi, “Asymptotically Optimum De- tection of Primary User in Cognitive Radio Networks,” IET Communications, Vol. 1, No. 6, December 2007, pp. 1138-1145. doi:10.1049/iet-com:20060645 [6] S. Tseng, H. Chiang and J. Lehnert, “Parametric density estimation using EM algorithm for collaborative spectrum sensing,” 3rd International Conference on Cognitive Ra- dio Oriented Wireless Network and Communications (CrownCom), Singapore, 15-17 May 2008, pp. 1-6. [7] S. Shankar, C. Cordeiro and K. Challapali, “Spectrum Agile Radios: Utilization and Sensing Architectures,” Pro-  M. AKBARI ET AL. Copyright © 2011 SciRes. WSN 91 ceedings of IEEE DySPAN, 8-11 November 2005, pp. 160-169. [8] A. W. Min, K. G. Shin and X. Hu, “Attack-Tolerant Dis- tributed Sensing for Dynamic Spectrum Access Net- works,” 17th IEEE International Conference on Network Protocols, Princeton, 13-16 October 2009, pp. 294-303. doi:10.1109/ICNP.2009.5339675 [9] H. Chen, H. Wu, X. Zhou and C. Gao, “Agent-Based Trust Model in Wireless Sensor Networks,” 8th IEEE In- ternational Conference on Software Engineering, Artifi- cial Intelligence, Networking, and Parallel/Distributed Computing, Qingdao, July-August 2007, pp. 119-124. doi:10.1109/SNPD.2007.122 [10] G. Vijay, E. Bdira and M. Ibnkahla, “Cognitive Ap- proaches in Wireless Sensor Networks: A Survey,” 25th Biennial Symposium on Communications, Kingston, 12- 14 May 2010, pp. 177-180. doi:10.1109/BSC.2010.5472978 [11] A. Ghasemi and E. S. Sousa, “Asymptotic Performance of Collaborative Spectrum Sensing under Correlated Log- Normal Shadowing,” IEEE Communication Letters, Vol. 11, No. 1, January 2007, pp. 34-36. [12] T. Shu and M. Krunz, “Throughput-Efficient Sequential Channel Sensing and Probing in Cognitive Radio Net- works under Sensing Errors,” Proceedings of ACM Mo- biCom’09, September 2009. [13] R. Chen, J. M. Park, Y. T. Hou and J. H. Reed, “Toward Secure Distributed Spectrum Sensing in Cognitive Radio Networks,” IEEE Communication Magazine, Vol. 46, No. 4, April 2008, pp. 50-55. [14] P. Kaligineedi, M. Khabbazian and V. K. Bhargava, “Secure Cooperative Sensing Techniques for Cognitive Radio Systems,” IEEE International Conference on Communications (ICC), Beijing, 19-23 May 2008, pp. 3406- 3410. [15] S. Xu, Y. Shang and H. Wang, “Double Thresholds based Cooperative Spectrum Sensing against Untrusted Sec- ondary Users in Cognitive Radio Networks,” 69th IEEE conference on Vehicular Technology, Barcelona, 26-29 April 2009, pp. 1-5. doi:10.1109/VETECS.2009.5073511 [16] M. Akbari and A. Falahati, “SSDF Protection in Cooper- ative Spectrum Sensing Employing a Computational Trust Evaluation Algorithm,” 5th International Sympo- sium on Telecommunication, December 2010. [17] A. GoldSmith, “Wireless Communication,” Cambridge University Press, Cambridge, 2005. [18] Q. Wang, D. W. Yue a nd Y. Wang, “Performa nce Analy - sis of Spectrum Sensing Using Diversity Technique,” 5th International Conference on Wireless Communication, Networking and Mobile Computing, Beijing, 24-26 Sep- tember 2009, pp. 1-5. doi:10.1109/WICOM.2009.5301177 [19] W. Zhang, J. Yang, Q. Yan and L. Xiao, “Performance Analysis of Cooperative Sensing with Equal Gain Com- bining over Nakagami Channels in Cognitive Radio Net- works,” 6th International Conference on Wireless Com- munication and Mobile Computing, September 2010. [20] H. G. Kang, I. Song, Y. H. Kim, T. An and D. Kim, “Spectrum Sensing Based on Nonlinear Combining for Cognitive Radio with Receive Diversity,” 44th Annual Conference on Information Sciences and Systems (CISS), Princeton, 17-19 March 2010, pp. 1-6. doi:10.1109/CISS.2010.5464977 [21] C. Yu and K. Chen, “Multiple Systems Sensing for Cog- nitive Radio Networks over Rayleigh Fading Channel,” Vehicular Technology Conference (VTC), Singapore, 11- 14 May 2008, pp. 1574-1578. [22] E. D. Kaplan and C. J. Hegarty, “Understanding GPS: Principles and Applications,” 2nd Edition, Artech House Inc., London, 2006. [23] R. K. Pearson, “Outliers in Process Modeling and Identi- fication,” IEEE Transactions on Control System Tech- nology, Vol. 10, No. 1, January 2002, pp. 55-63. doi:10.1109/PROC.1967.5573 [24] H. Urkowitz, “Energy Detection of Unknown Determi- nistic Signals,” Proceedings of IEEE, Vol. 55, No. 4, 1967, pp. 523-531. doi:10.1109/PROC.1967.5573 [25] A. Papoulis and S. U. Pillai, “Probability, Random Va- riables and Stochastic Processes,” 4th Edition, McGraw- Hill, New York, 2002. [26] R. F. Mills and G. E. Prescon, “A Comparison of Various Radiometer Detection models,” IEEE Transactions on Aerospace and Electronic Systems, Vol. 32, No. 1, Janu- ary 1996, pp. 467-473. doi:10.1109/7.481289 [27] C. Cordeiro, K. Challapali, D. Birru and S. Shankar, “IEEE 802.22: An Introduction to the First Wireless Standard based on Cognitive Radio,” Journal of Commu- nications, Vol. 1, No. 1, April 2006, pp. 38-47. [28] H. Kim and K. G. Shin, “Efficient Discovery of Spectrum Opportunities with MAC-Layer Sensing in Cognitive Ra- dio Networks,” IEEE Transactions on Mobile Computing, Vol. 7, No. 5, May 2008, pp. 533-545. |

