Paper Menu >>
Journal Menu >>
 Wireless Sensor Network, 2011, 3, 61-72 doi:10.4236/wsn.2011.32007 Published Online February 2011 (http://www.SciRP.org/journal/wsn) Copyright © 2011 SciRes. WSN A New MAC Protocol for Moving Target in Distributed Wireless Sensor Networks Jijun Zhao, Xiang Sun, Zhongcheng Wei, Zhihua Li School of Information & Electronic Engineering, Hebei University of Engineering, Handan, China E-mail: sx198574@sohu.com Received November 29, 2010; revised December 16, 2010; accepted February 21, 2011 Abstract A wireless sensor network (WSN) is composed of many nodes with limited power supply; most nodes are stationary in the network which could probably involve a few mobile nodes. Various medium access control (MAC) protocols specially aimed at a target locating application for WSNs have been proposed. However, most of these protocols based on the problem of energy-limited does not consider the mobility of nodes. Therefore, in order to solve such problem, this paper proposes a MAC protocol—Distribute Moving-MAC (DM-MAC). Under the condition of keeping high network coverage, the protocol utilizes the redundancy of nodes to strengthen the robustness and energy efficiency of network, and decreases the packet loss rate of the mobile node’s communication links for realizing reliable communication of two nodes. Simulation indicates that the new protocol has higher energy efficiency, lower packet loss rate and higher network coverage which suit for wireless sensor network with mobile nodes well. Keywords: Wireless Sensor Network (WSN), Distribute Moving-MAC (DM-MAC), LDAS, EAR, Mobility 1. Introduction A wireless sensor network (WSN) has characteristics of self-organization, multi-hop, large scale of monitoring and energy constraints. Recently, many research institu- tions have studied on this area and have a great break- through on it. Because WSN has a strong ability of pro- cessing ability within network, it has been applied to various situations, such as battlefield monitoring, ma- chine fault monitoring, biological monitoring, intelligent furniture and so on. MAC protocol in WSN is mainly to realize the reliable communication of point-to-point (node to node), sleeping mechanism, synchronization mechanism and so on. Therefore, MAC protocol has a decisive function to whole network due to a great influ- ence on energy efficiency, scalable to node density, frame synchronization, fairness, bandwidth utilization, flow control, and error control for data communication. The most key feature in WSN is the limitation of node energy, therefore, most MAC protocols have focused on the energy saving in WSN without considering the mo- bility of nodes. Nevertheless, there have been introduced a certain amount of mobile node in many position sys- tems and environmental monitoring systems. Thus, in- creasing the reliability of the mobile nodes communica- tion under the condition of ensuring network connection and coverage becomes a mayor research trend of MAC protocol study. In recent researches, Traffic-Adaptive Medium Access protocol (TRAMA) [1] and WiseMAC protocol [2] solve node sleeping mechanism well and limit energy consumption of the node in a certain low value, but bring about a large packet loss rate after sev- eral mobile nodes being added into network. The Lightweight Deployment-Aware Scheduling (LDAS) algorithm proposed in [3] solves the problem of low coverage (including sensor coverage and communication coverage) which caused by nodes’ sleeping mechanism; however, it doesn’t have a mechanism to realize the re- liable communication, so it doesn’t accomplish dynamic communication between the different nodes. The Eave- sdrop-And- Register (EAR) algorithm proposed in [4] which based on the Self-organizing Medium Access Control for Sensor networks (SMACS) algorithm can realize the reliable communication between mobile node and fixed node by depending on increasing the control head packets, but when adding the number of mobile nodes, it results in the packets collision with a high probability rate that leads to the node energy consump- tion much faster and it also doesn’t guarantee high rate of coverage in the monitoring area. The mobility-aware  J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 62 MAC protocol for sensor networks (MS-MAC) proposed in [5] can adjust the scheduling mechanism dynamically acco·rding to velocity of the node, but this protocol is based on the Senor-MAC (SMAC) protocol in [6,7], which doesn’t consider the problem of reliable commu- nication of mobile node and the network coverage. Here the network refers to this paper is the areas that are col- lectively covered by the set of all sensors. Based on the above researches, we find that the exist- ing MAC protocols are almost proposed based on the problems of energy consumption, network coverage and network connection. In the recent researches, very few MAC protocols could be used in a mobile network. Al- though a few protocols could support a number of the mobile nodes, they also exist the problem of high energy consumption, limit number of mobile nodes and low network coverage, etc [8-14]. DM-MAC proposed in the paper is based on the network environment which exist many stationary nodes and several mobile nodes. The protocol decreases occurrence probability of blind hole and solves unreliable point-to-point communications which are caused by LDAS algorithm, and improves the communication mode in EAR algorithm and intelligent scheduling mechanism in MS-MAC protocol to realize the communication between mobile nodes and stationary nodes. Meanwhile, the protocol could ensure the network having a good performance in network coverage and network connection which also enhance robustness of the network. In the network, the function of stationary node is to collect and monitor sensor data of surrounding environ- ment, locate the geographical position of the mobile nodes and send collecting data to sink node. As the target node need to be located, mobile node is to broadcast signals for the purpose of location by stationary node; meanwhile, mobile nodes also collect environmental data and send them to sink node by the stationary. Generally, mobile node is always composed of stationary node which fixed on the movable objects. We consider that the limitation of energy and hardware is not a key problem of the mobility, so some management tasks could be given to mobile nodes for achievement. The paper is organized as follows. In Section 2, we analysis the existing protocols which adapt to the distri- bute network for moving target; while Section 3 propos- es a new protocol whose performance is superior to the other existing protocols. Simulation results are presented in Section 4 and Section 5 concludes our work. 2. Related Protocols Analysis According to the aspects of sleeping mechanism, net- work coverage and building communication link, etc, we mainly analyze the following three protocols, with com- paring their advantages and disadvantages for the future research. 2.1. EAR Algorithm The basic idea of EAR is to build reliable communica- tion link though adding handshaking times and using SNR value of receiving signals. In the EAR algorithm, links are build up between mobile nodes and stationary nodes considering four kinds of frames: Broadcast Invite (BI), Mobile Invite (MI), Mobile Response (MR) and Mobile Disconnect (MD). The detail realization process of the algorithm is shown in Figure 1. BI sent by stationary node is used to invite mobile node to join in the communication. More- over, stationary node would last this action until its reg- istration form is full. When registration form is full, compare SNR value of the stationary node to the value of other nodes which have already connected with mobile nodes, write the higher value into the form. If BI frame has existed in the registration form, update registration form according to the time field in BI frame. MI frame sent by mobile nodes is to response to BI frame and re- quest to build up a connection. MR frame is to decide whether stationary node accepts the MI frame. When communication link can be established, the stationary node will send MR frame to mobile node in acknowled- gement of accepting the connection request. MD frame is to disconnect the link. After connecting with the statio- nary node, mobile node continues to listen to this statio- nary node. When the SNR value of signal which mobile node receives is lower than the threshold we set before or there are more appropriate stationary nodes communi- cating to the mobility, the mobile node sends MD frame to inform stationary node to interrupt linkage. After sta- tionary node receives this frame, it deletes information of mobile node in the registration form. The disadvantage of EAR algorithm: at first, it could only be used in the WSN based on TDMA technology; meanwhile, the network topology could only be cluster so that the algorithm could ensure the low time delay in network. Second, energy efficiency of stationary node is low, because stationary node needs to send extra BI Figure 1. The communication process of EAR algorithm.  J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 63 frame periodically to find out mobile node. Third, the algorithm doesn’t propose a suitable sleeping mechanism based on high redundant network, so it leads to large number of collision in the high density sensor network which could result in decreasing the energy efficiency of node, shorting the life of network and prolonging the communication latency. 2.2. MS-MAC Algorithm MS-MAC algorithm adjusts node sleeping time dynami- cally according to the velocity of mobile node. Its main idea is based on SMAC protocol. The advantage of the algorithm is that it proposes a kind of sleeping mechan- ism which suits for the mobile networks. Similar with SMAC, MS-MAC algorithm sends SYNC frame to build up virtual clusters in the period of networking. In every virtual cluster, all the nodes keep synchronous and the nodes on the edge of two virtual clusters should follow synchronous periods of the two virtual clusters. There- fore, at the beginning of every scheduling mechanism, nodes send SYNC to build up virtual cluster to keep time synchronous. When the mobile nodes join in the network, it must follow time synchronous mechanism of the vir- tual cluster. So when the mobile node moves from one virtual cluster to another, it must wait until the next scheduling mechanism begins, therefore it could know the time synchronous mechanism of another virtual clus- ter. Generally, this mechanism increases time delay in communication. For example, suppose that one schedul- ing cycle is 2 minutes and nodes stay at wake-up status in 10 seconds in every 2 minutes, so mobile node at most needs to wait 1 minute 50 seconds to know synchronous mechanism of the virtual cluster. MS-MAC algorithm decreases the time delay by adjusting scheduling me- chanism dynamically for adapting the velocity of the mobility. At first, set a value v0 if velocity of mobile node is higher than 1/4 v0, make scheduling cycle as 1 minute if the velocity of mobile node is higher than 1/2 v0, then make scheduling cycle as 30 seconds, etc. Though MS-MAC algorithm could use the velocity to adjust scheduling cycle dynamically, it can’t ensure the reliable communication between stationary nodes and mobile nodes; meanwhile, this kind of sleeping mechan- ism also doesn’t ensure the high rate of coverage and connection of the whole network. 2.3. LDAS Algorithm When the node doesn’t know its own coordinate position information and the angle information of its neighbors, the sleeping mechanism can use the number of node’s neighbors to decide whether go to sleep, (the node’s neighbors defined in the paper are all the nodes in the circular area whose radius is the node sensing range r), so that it can cover the most sensing area on the base of high energy efficiency. The probability formula that the sleeping node is fully covered by its neighbors is as fol- lows [3]: 11 1 0.609Pr1 0.609 nn nAn ξ (1) ξ = 0.5*n*(n-1)*(0.276)n-1. n is the number of the awa- ken node’s neighbors (n could be selected according to QoS requirement). In the paper, we suppose that com- munication radius is equal to sensing radius. So when n = 3, the probability that node can be fully covered is: 0 ≤ Pr(A) ≤ 0.113, when n = 5, then the probability that node can be fully covered is: 0.312 ≤ Pr(A) ≤ 0.370. Suppose that n = 3 could satisfy the QoS requirement, meanwhile, the node finds three more neighbors which are not in sleeping status, the node considers its sensing rang being covered by its neighbors and the node could go to sleep- ing status. In this case, it could happen in following situ- ations, as Figure (a) shows, the node O1 could be aware of its three neighbors O2, O3, O4, so it goes to sleeping status. But when mobile node goes though the shadow region, any nodes in the network could not be aware of location of mobile node until the node O1 ends up its sleeping status. Now we consider the situation that the smallest sensing area which could be covered by its neighbors, as Figure (b) shows, suppose that the sensing radius and communication radius are R. Because central angle is 120˚, the whole area of shadow region is as fol- lows: 22 23 34 SR R (2) (a) (b)  J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 64 Because when n = 3, the probability which the node’s sensing area/communication area fully covered by its neighbor is among [0, 0.113]. Suppose that R = 10 m, so we can calculate the area S ≈ 166.032 m2; when n = 5, S ≈ 130.833 m2. Therefore, from the above data, it is known that if only using LDAS sleeping algorithm, there will be a large number of blind holes in the network, which could make mobile node disappear. Although a bigger blind hole occurs in network with a certain probability, LDAS has its own advantages: 1) the algorithm is simple that adapts to a large scale network, the nodes in the network can be random distributed; 2) the algorithm needn’t know geographical position infor- mation of neighbor nodes; 3) the algorithm can adjust dynamically to achieve the requirement of QoS; 4) the algorithm has a strong resistant ability for channel error and collision; 5), the blind hole appears randomly and has a small influence on event monitoring relatively; 6) the algorithm needn’t keep time synchronous mechanism. However, LDSA isn’t the mechanism which could real- ize a reliable point-to-point communication, so it makes the communication between mobile node and stationary node unrealized. 3. Design of the DM-MAC Protocol Combining with the above three kinds of algorithms, we design a MAC protocol based on distributed network– DM-MAC. On the premise of ensuring the network cov- erage, this protocol could realize the reliable communi- cation between stationary node and mobile node. Mean- while, the protocol uses the intelligent scheduling me- chanism proposed in MS-MAC algorithm to decrease the delay in the communication and to decrease the disap- pearance probability of mobile node which caused by the sleeping mechanism. 3.1. Main Design of the Protocol 3.1.1. Netw ork Initialization Suppose that nodes in the network are distributed ran- domly and sensing radius of every node r is equal to its communication radius R. Because the energy of mobile node can be considered infinitely, so we can increase the communication radius of the mobile node to 2R by using power control technology. The initial stage of establish- ing network, LDSA algorithm will be used to initialize the sleeping mechanism of every node. The concrete process is as follows: At first, the stationary node checks the number of its working neighbors (the number of working nodes in the sensing range of the node) in every CT (Checking Time) time. Second, the stationary node broadcasts its beacon message to show it existing in the network. The beacon message packet includes two parts: the nodes’ ID and the number of working neighbors. When other nodes receive this beacon message, update related node’s information in the receivers. If the node doesn’t receive the beacon message send by its neighbors in a long period, it will make its neighbors turn into sleeping status. So every node has a neighborhood table. According to requirement of QoS, we can estimate the required number of working nodes. If the number of ex- isting working neighbors is more than required, the node sends ticket packets to its working neighbors. In working stage, if the node has enough tickets to turn into sleeping status, it should also check the number of the working neighbors again to eliminate the nodes that sleep at the same time. So if the number of tickets node received is more than TT (Ticket Threshold), the node turns into ready-to-off status, and then the node goes to backoff stage (the backoff time is: random(0, Wmax)). Next, the node checks for the second time that whether it has enough working neighbors to make itself turn into sleep- ing status, if condition is satisfied, the node turns into sleeping status(off-duty) until passing by a time segment of ST (Sleep Time). After sleeping a period of ST, the node goes into on-duty status and clears the values of tickets. 3.1.2. Communication with St ati ona ry Node and Mobile Node When mobile node goes into the network, it broadcasts BI signal periodically at first (In EAR algorithm, BI is sent by stationary node which is used to invite the mobile node to join the communication. In order to decrease the energy consumption of stationary node and the probabil- ity of collision, we make mobile nodes to send BI signal). BI frame includes the velocity of mobile node, the ID of mobile node and several sensing parameters collected by mobile node. After the velocity of mobile node (the ve- locity value can be gained by RF Doppler Shifts [15]) is received by stationary node, it would be compared with VT (Velocity Threshold) which is set before the stage of establishing network, if the two values are different; changing the ST value defined in the sleeping mechanism to adjust the node’s sleeping time. In order to make the stationary node adjust its scheduling mechanism in ad- vance, we apply power control technology to increase the mobile node’s transmit power for enlarging its commu- nication radius. After setting proper scheduling mechan- ism, mobile node sends BI frame continuously and pe- riodically, when stationary node receives BI frame, it sends MI frame to the mobility to ensure that it has re- ceived the BI frame successfully (in EAR algorithm, MI frame is sent by mobile node). In the MI frame, it in- cludes the ID of stationary node and the SNR value of  J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 65 the BI that is received by stationary node. After the mo- bile node receives MI frame, it accords to SNR value in the connected communication links to decide whether to establish the connection, if the SNR value is bigger than the existing SNR value in the communication links, then the mobile node interrupts the connected link, establishes the link to the existing stationary node and then sends MR frame to establish the connection. If the SNR value is smaller than the existing SNR value in the communi- cation links, the mobile node neglects the MI frame and maintains the existing communication link. In order to decrease the times of comparison, we set E0 as threshold of SNR in advance, when SNR value in MI frame is smaller than E0, the mobile node neglects MI frame di- rectly. When SNR value in the connected communica- tion link is smaller than E0 or smaller than any SNR val- ues in the established communication links, mobile node must send MD to the stationary nodes to interrupt the communication link. Notice that, after stationary nodes have established the communication with the mobile nodes, even if stationary nodes maybe satisfy the condi- tion of turning into sleeping status, they can’t go to sleep until disconnecting the communication with the mobile nodes. 3.2. The Analysis of DM-MAC Protocol in Process and Time Sequence The content of DM-MAC protocol realized in the statio- nary node and mobile node are not the same, stationary node mainly implements sleeping mechanism, intelligent scheduling mechanism and reliable point-to-point com- munication mechanism, meanwhile, the function of mo- bile nodes is relative simple, it mainly completes reliable point-to-point communication mechanism and maintains SNR table in dynamic neighbor nodes. Here we focus on the protocol process of stationary nodes in detail. The basic flow chart is as Figure 2 shows. We suppose that when nodes send packets, the channel is free. The com- munication of stationary node includes the communica- tion between stationary node and mobile node, and the communication between stationary nodes. Figure 2 shows the communication basic flow on stationary node and Figure 3 shows the communication basic flow on mobile node, we apply CSMA/CA mechanism and S-MAC to realize the communication between the sta- tionary nodes so that the data which stationary nodes collect from the surrounding environment and the mobil- ity information which stationary nodes collect can be successfully multi-hop to the sink node. Some nodes are selected to analyze their time sequence. The topology distribution map is shown in Figure 4. A, B, C and D are stationary nodes, M is a mobile node, the sensing area of node B is fully covered by node A, C and D. Meanwhile, suppose that node B is also fully covered by its neighbors (In order to describe conveniently, we don’t consider the case of neighbors of node A, C and D temporarily). We suppose that when n = 3 can satisfy the QoS requirement, so if the number of working neighbors is 3, then node B could go to sleep. When the mobile node moves into the network, suppose that its communi- cation radius is r1 = 2R (which is two times bigger than stationary node’s communication radius), therefore, if node M moves as Figure 4 shown, node A will listen to BI frame at first which is sent by M periodically, mean- while, A adjusts the ST value dynamically by receiving the velocity in BI frame. According to the SNR in MI frame, when M continues moving, it will receive more MI signal, the node will choose the best nodes to estab- lish communication link (We can set how many number of stationary nodes should be linked with the mobile nodes beforehand). The detail time-slot chart of estab- lishing the link between stationary nodes and mobile nodes is as Figure 5 shows. We suppose that every mo- bile node can build communication link with only one stationary node. 3.3. The Implementation of DM-MAC Protocol In the design of the whole DM-MAC protocol, we main- ly implement the reliable point-to-point communication mechanism between stationary nodes and mobile nodes with intelligent sleeping mechanism. The sleeping me- chanism proposed in LDAS algorithm will appear a large area of blind holes because communication area of node having been on off-duty status is not fully covered by its neighbors. The sleeping mechanism proposed in LDAS algorithm will appear a large area of blind holes because communication area of node having been on off-duty status is not fully covered by its neighbors. Thus in DM-MAC protocol, we enlarge the mobile nodes’ com- munication radius to make sleeping node foresee the situation of the mobile nodes in early time, so the nodes can adjust its own scheduling mechanism after obtaining the velocity of mobility. The parameters of protocol we need to set beforehand are shown in Table 1. The fames involve in the DM-MAC protocol are as follows: neighborhood table packet, beacon message frame, ticket frame, BI frame, MI frame, MR frame and MD frame, their concrete frame structures are shows from Figure 5 to Figure 11. Since the new protocol is aimed to the MAC layer, when designing the frame, we don’t add packaging of physical layer and higher layer in the frame, such as packaged frame length in physical layer. In order to realize the sleeping mechanism which could 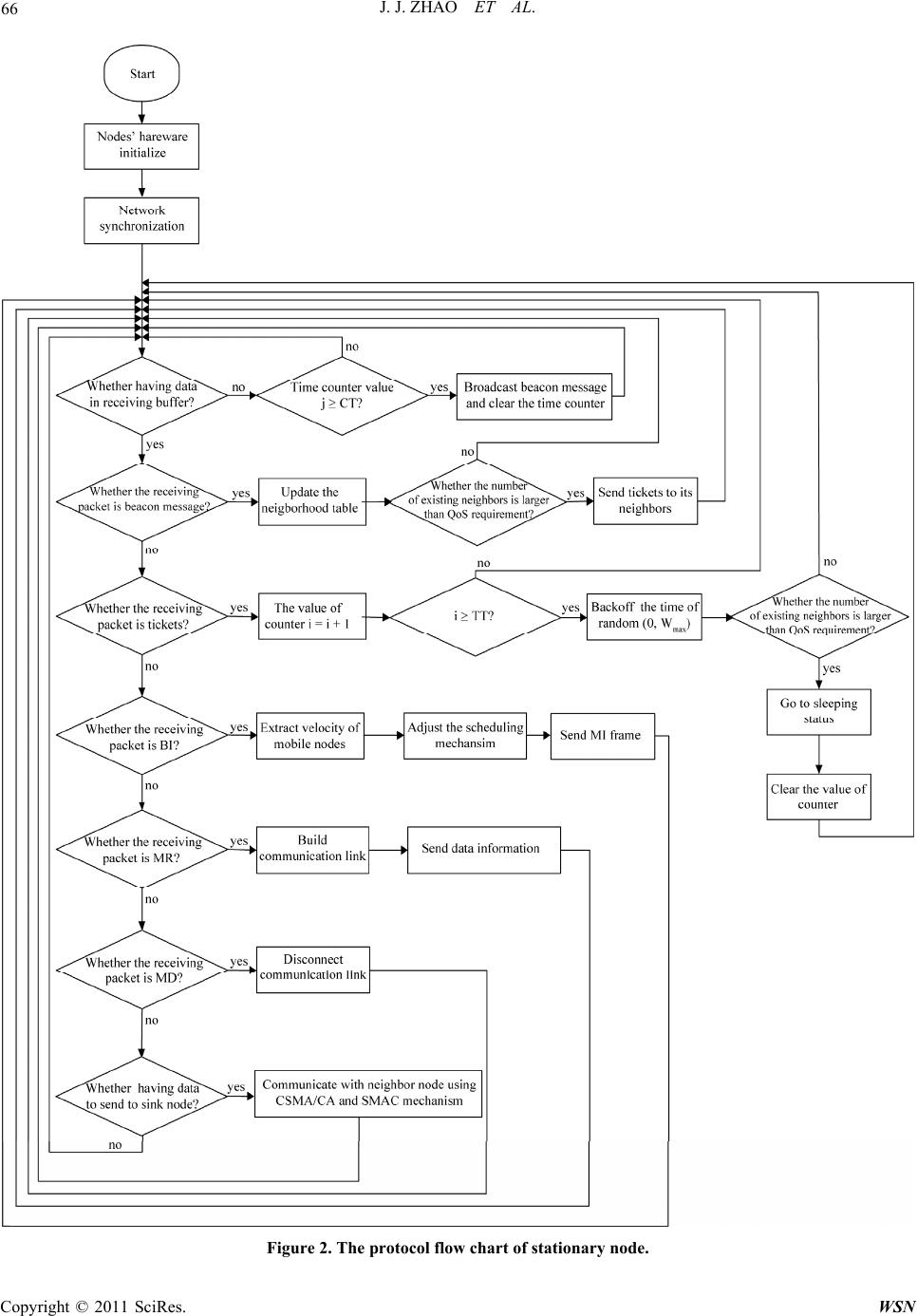 J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 66 Figure 2. The protocol flow chart of stationary node. 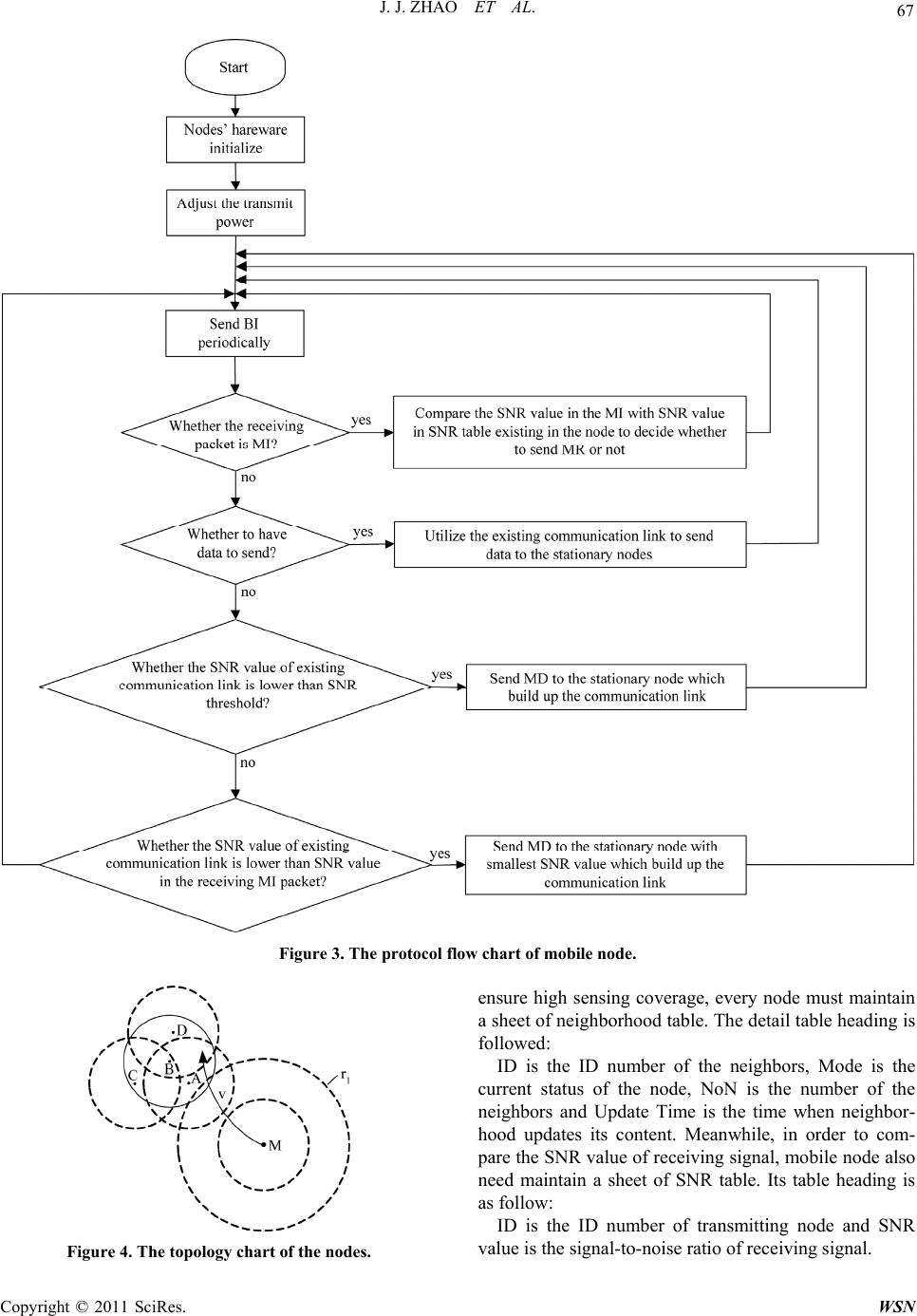 J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 67 Figure 3. The protocol flow chart of mobile node. Figure 4. The topology chart of the nodes. ensure high sensing coverage, every node must maintain a sheet of neighborhood table. The detail table heading is followed: ID is the ID number of the neighbors, Mode is the current status of the node, NoN is the number of the neighbors and Update Time is the time when neighbor- hood updates its content. Meanwhile, in order to com- pare the SNR value of receiving signal, mobile node also need maintain a sheet of SNR table. Its table heading is as follow: ID is the ID number of transmitting node and SNR value is the signal-to-noise ratio of receiving signal. 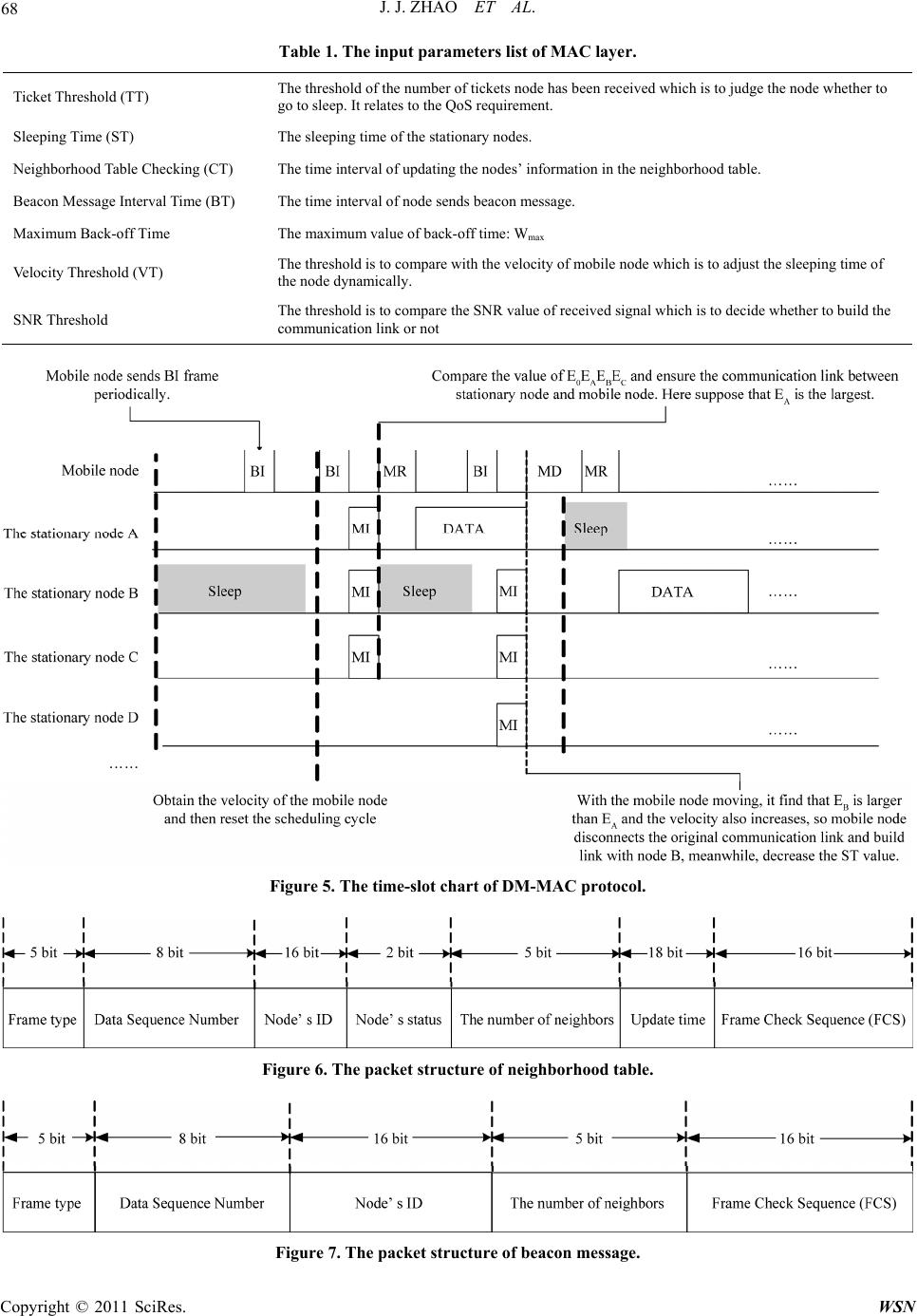 J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 68 Table 1. The input parameters list of MAC layer. Ticket Threshold (TT) The threshold of the number of tickets node has been received which is to judge the node whether to go to sleep. It relates to the QoS requirement. Sleeping Time (ST) The sleeping time of the stationary nodes. Neighborhood Table Checking (CT) The time interval of updating the nodes’ information in the neighborhood table. Beacon Message Interval Time (BT) The time interval of node sends beacon message. Maximum Back-off Time The maximum value of back-off time: Wma x Velocity Threshold (VT) The threshold is to compare with the velocity of mobile node which is to adjust the sleeping time of the node dynamically. SNR Threshold The threshold is to compare the SNR value of received signal which is to decide whether to build the communication link or not Figure 5. The time-slot chart of DM-MAC protocol. Figure 6. The packet structure of neighborhood table. Figure 7. The packet structure of beacon message.  J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 69 Figure 8. The packet structure of ticket. Figure 9. The packet structure of BI. Figure 10. The packet structure of MI. Figure 11. The packet structure of MR and MD. Table 2. The table heading of neighborhood table. ID Mode NoN Update Time (hour:minute:second) Table 3. The heading of SNR table. ID SNR value 4. Simulation Results In order to analyze the performance of DM-MAC proto- col, we simulate the protocol in PC. Suppose that energy consumption ratio of transmitting, receiving (idling) and sleeping is 10:4:0.01. There are 200 stationary nodes randomly distributed in an area of 150 × 150 m2, sensing radius and communication radius of the stationary nodes are 20 m, communication radius of mobile node is 20 m. Figures 12 and 13 show the case of node distribute and node sensing/communication coverage. We set ST = 1 min, CT = 10 sec, BT = 15 sec, VT = 3 m/s, TT = 8, the communication channel is 2405 MHz, when n = 3, QoS requirement could be satisfied. 4.1. Connection Rate of Mobile Nodes Under the above condition, comparing with DM-MAC and LDAS + EAR, we simulate the connection rate of mobile nodes in the network (the connection rate of mo- bile nodes = the number of mobile nodes which have already connected with stationary node/the number of whole mobile nodes). Suppose that there are 200 statio- nary nodes randomly distributed in the area, the simulate results are shows in Figure 14. In the figure, we know that when the number of mobile node is few, LDAS + EAR protocol has higher reliability of communication, but when the number of mobile node increases, packet loss rate relatively increases and the connection rate of mobile nodes decreases obviously. When mobile nodes are added up to 100, nearly 40% mobile nodes disappear. This is because LDAS + EAR protocol may bring in big blind holes. Of course collision also brings in disappear- ing which is the main factor either when the mobile 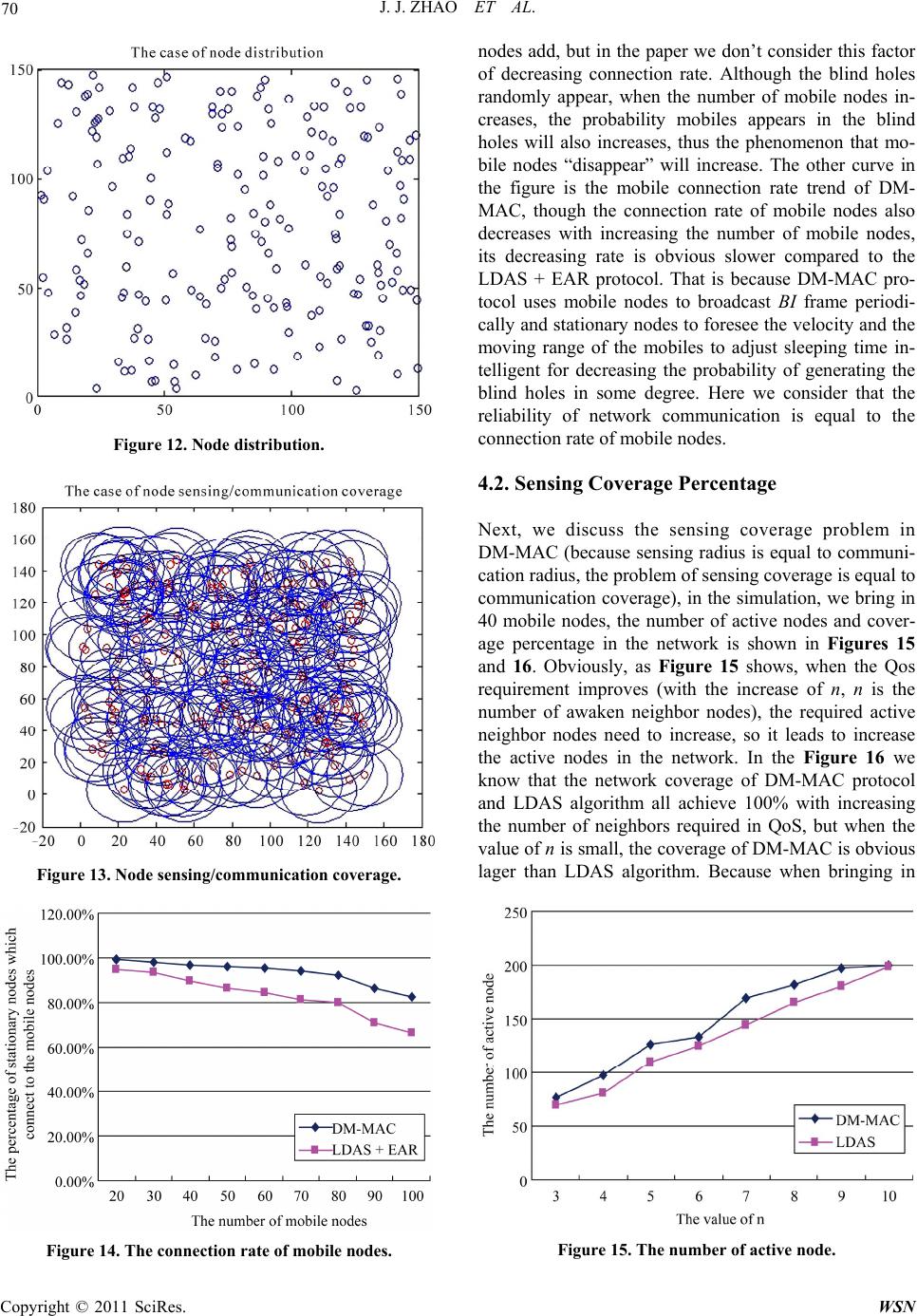 J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 70 Figure 12. Node distribution. Figure 13. Node sensing/communication coverage. Figure 14. The connection rate of mobile nodes. nodes add, but in the paper we don’t consider this factor of decreasing connection rate. Although the blind holes randomly appear, when the number of mobile nodes in- creases, the probability mobiles appears in the blind holes will also increases, thus the phenomenon that mo- bile nodes “disappear” will increase. The other curve in the figure is the mobile connection rate trend of DM- MAC, though the connection rate of mobile nodes also decreases with increasing the number of mobile nodes, its decreasing rate is obvious slower compared to the LDAS + EAR protocol. That is because DM-MAC pro- tocol uses mobile nodes to broadcast BI frame periodi- cally and stationary nodes to foresee the velocity and the moving range of the mobiles to adjust sleeping time in- telligent for decreasing the probability of generating the blind holes in some degree. Here we consider that the reliability of network communication is equal to the connection rate of mobile nodes. 4.2. Sensing Coverage Percentage Next, we discuss the sensing coverage problem in DM-MAC (because sensing radius is equal to communi- cation radius, the problem of sensing coverage is equal to communication coverage), in the simulation, we bring in 40 mobile nodes, the number of active nodes and cover- age percentage in the network is shown in Figures 15 and 16. Obviously, as Figure 15 shows, when the Qos requirement improves (with the increase of n, n is the number of awaken neighbor nodes), the required active neighbor nodes need to increase, so it leads to increase the active nodes in the network. In the Figure 16 we know that the network coverage of DM-MAC protocol and LDAS algorithm all achieve 100% with increasing the number of neighbors required in QoS, but when the value of n is small, the coverage of DM-MAC is obvious lager than LDAS algorithm. Because when bringing in Figure 15. The number of active node. 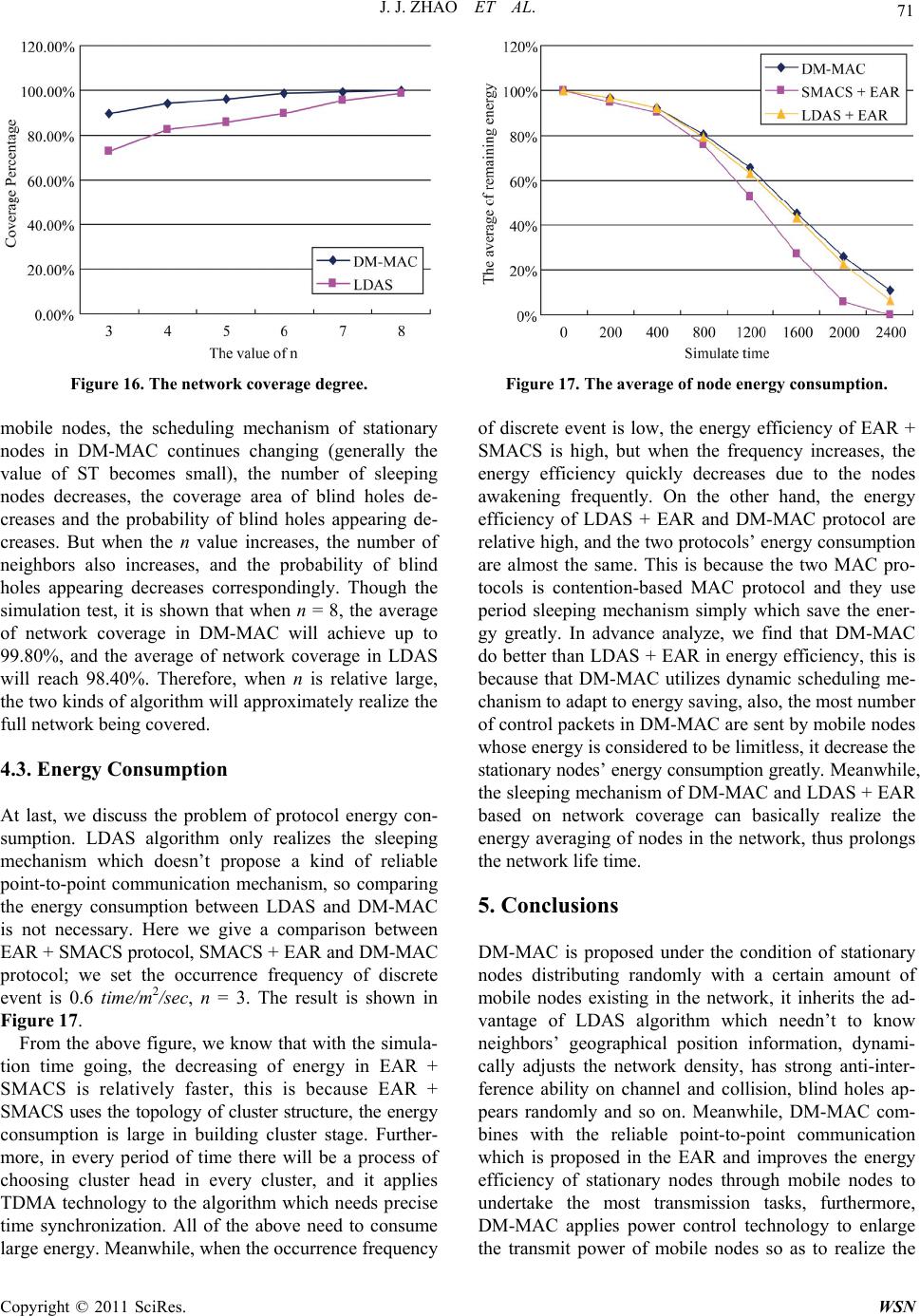 J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 71 Figure 16. The network coverage degree. mobile nodes, the scheduling mechanism of stationary nodes in DM-MAC continues changing (generally the value of ST becomes small), the number of sleeping nodes decreases, the coverage area of blind holes de- creases and the probability of blind holes appearing de- creases. But when the n value increases, the number of neighbors also increases, and the probability of blind holes appearing decreases correspondingly. Though the simulation test, it is shown that when n = 8, the average of network coverage in DM-MAC will achieve up to 99.80%, and the average of network coverage in LDAS will reach 98.40%. Therefore, when n is relative large, the two kinds of algorithm will approximately realize the full network being covered. 4.3. Energy Consumption At last, we discuss the problem of protocol energy con- sumption. LDAS algorithm only realizes the sleeping mechanism which doesn’t propose a kind of reliable point-to-point communication mechanism, so comparing the energy consumption between LDAS and DM-MAC is not necessary. Here we give a comparison between EAR + SMACS protocol, SMACS + EAR and DM-MAC protocol; we set the occurrence frequency of discrete event is 0.6 time/m2/sec, n = 3. The result is shown in Figure 17. From the above figure, we know that with the simula- tion time going, the decreasing of energy in EAR + SMACS is relatively faster, this is because EAR + SMACS uses the topology of cluster structure, the energy consumption is large in building cluster stage. Further- more, in every period of time there will be a process of choosing cluster head in every cluster, and it applies TDMA technology to the algorithm which needs precise time synchronization. All of the above need to consume large energy. Meanwhile, when the occurrence frequency Figure 17. The average of node energy consumption. of discrete event is low, the energy efficiency of EAR + SMACS is high, but when the frequency increases, the energy efficiency quickly decreases due to the nodes awakening frequently. On the other hand, the energy efficiency of LDAS + EAR and DM-MAC protocol are relative high, and the two protocols’ energy consumption are almost the same. This is because the two MAC pro- tocols is contention-based MAC protocol and they use period sleeping mechanism simply which save the ener- gy greatly. In advance analyze, we find that DM-MAC do better than LDAS + EAR in energy efficiency, this is because that DM-MAC utilizes dynamic scheduling me- chanism to adapt to energy saving, also, the most number of control packets in DM-MAC are sent by mobile nodes whose energy is considered to be limitless, it decrease the stationary nodes’ energy consumption greatly. Meanwhile, the sleeping mechanism of DM-MAC and LDAS + EAR based on network coverage can basically realize the energy averaging of nodes in the network, thus prolongs the network life time. 5. Conclusions DM-MAC is proposed under the condition of stationary nodes distributing randomly with a certain amount of mobile nodes existing in the network, it inherits the ad- vantage of LDAS algorithm which needn’t to know neighbors’ geographical position information, dynami- cally adjusts the network density, has strong anti-inter- ference ability on channel and collision, blind holes ap- pears randomly and so on. Meanwhile, DM-MAC com- bines with the reliable point-to-point communication which is proposed in the EAR and improves the energy efficiency of stationary nodes through mobile nodes to undertake the most transmission tasks, furthermore, DM-MAC applies power control technology to enlarge the transmit power of mobile nodes so as to realize the  J. J. ZHAO ET AL. Copyright © 2011 SciRes. WSN 72 reservation mechanism between mobile nodes and sta- tionary nodes. In order to decrease the communication loss rate of mobile nodes and time delay, DM-MAC combines with the scheduling mechanism in MS-MAC, which could adjust the sleeping time intelligently. Generally speaking, DM-MAC protocol is simple to realize. The energy consumption of every node is nearly the same. Moreover, the protocol can basically realize the reliable communication, so it could be applied to the real time positioning and tracking system. But DM-MAC protocol doesn’t consider the problem of network con- nectivity, so there is a problem that the stationary nodes near the sink node will consume the energy much faster, thus will make the network paralysis in advance. Our future work is to solve this problem and analyze the im- pacts on different values of TT, ST, BT, VT and Wmax for the performance of network. 6. Acknowledgment This work is supported by the Scientific Research Fund of Hebei Province Education Department (2008110) and Scientific & Technological Research and Development Projects of Handan in Hebei province (0821103041-2). 7. References [1] V. Rajendran, K. Obraczka and J. Garcia-Luna-Aceves, “Energy-Efficient, Collision-Free Medium Access Con- trol for Wireless Sensor Networks,” Proceedings of the ACM Sensor Systems 2003, Los Angeles, 2003, pp. 181- 192. [2] A. El-Hoiydi and J.-D. Decotignie, “WiseMAC: An Ultra Low Power MAC Protocol for Multi-hop Wireless Sensor Networks,” Algorithmic Aspects of Wireless Sensor Net- works First International Workshop, Vol. 3121, 2004, pp. 18-31. [3] K. Wu, Y. Gao, F. Li and Y. Xiao, “Lightweight Dep- loyment-Aware Scheduling for Wireless Sensor Net- works,” ACM/Kluwer Mobile Networks and Applications (MONET) Special Issue on Energy Constraints and Life- time Performance in Wireless Sensor Networks, Vol. 10, No. 6, 2005, pp. 837-852. [4] K. Sourabi, J. Gao, V. Ailawadni and G. J. Pottie, “Pro- tocols for Self-Organization of a Wireless Sensor Net- work,” IEEE Personal Communications, Vol. 7, No. 5, 2000, pp. 16-27. doi:10.1109/98.878532 [5] H. Pham, and S. Jha, “An adaptive Mobility-Aware MAC Protocol for Sensor Networks (MS-MAC),” IEEE Inter- national Conference on Mobile Ad-hoc and Sensor Sys- tems, 25-27 October 2004, pp. 558-560. [6] W. Ye, J. Heidemann and D. Estrin, “Medium Access Control with Coordinated Adaptive Sleeping for Wireless Sensor Networks,” IEEE/ACM Transactions on Net- working, Vol. 12, No. 3, 2004, pp. 493-506. doi:10.1109/ TNET.2004.828953 [7] W. Ye, J. Heidemann and D. Estrin, “An Energy-Effi- cient MAC Protocol for Wireless Sensor Networks,” INFOCOM 2002, pp. 1567-1576. [8] B. Kusy, A. Ledeczi and X. Koutsoukos, “Tracking Mo- bile Nodes Using RF Doppler Shifts,” ACM Sensor Sys- tems, 2007, pp. 29-42. [9] L. Wang and Y. Xiao, “A Survey of Energy-Efficient Scheduling Mechanisms in Sensor Networks,” Mobile Networks and Applications, Vol. 11, No. 5, 2006, pp. 723-740. doi:10.1007/s11036-006-7798-5 [10] P. Raviraj, H. Sharif, M. Hempel and S. Ci, “MOB- MAC—An Energy Efficient and Low Latency MAC for Mobile Wireless Sensor Networks,” 2005, pp. 370-375. [11] T. V. Dam and K. Langendo, “An Adaptive Energy- Ef- ficient MAC Protocol for Wireless Sensor Network,” The First ACM Conference on Embedded Networked Sensor Systems, 2003, pp. 171-180. [12] M. Ali, T. Suleman and Z. Uzmi, “MMAC: A Mobili- ty-Adaptive, Collision-Free MAC Protocol for Wireless Sensor Networks,” Proceedings of 24th IEEE Perfor- mance, Computing, and Communications Conference, 2005, pp. 401-407. [13] D. Tian, N. D. Georganas, “A Coverage-Preserving Node Scheduling Scheme for Large Wireless Sensor Net- works,” Proceedings of the 1st ACM International Workshop on Wireless Sensor Networks and Applications, 2002, pp. 32-41. doi:10.1145/570738.570744 [14] A. L. Henrique, F. Daniel, L. dos Aldri, S. J. Marcos, and A. A. Ferreira, “A Taxonomy for Medium Access Con- trol Protocols in Wireless Sensor Networks,” Annales des Télécommunications, Vol. 60, No.1, 2005, pp. 944-969. [15] H. Yousefi’zadeh, H. Jafarkhani and J. Kazemitabar, “A Study of Connectivity in MIMO Fading Ad-Hoc Net- works,” Journal of Communication and Networks, Vol. 11, 2009, pp. 47-56. |

