Int'l J. of Communications, Network and System Sciences
Vol. 5 No. 2 (2012) , Article ID: 17611 , 7 pages DOI:10.4236/ijcns.2012.52013
Spray and Dynamic: Advanced Routing in Delay Tolerant Networks
Department of Computer Science, Faculty of Science and Technology, University Cadi Ayyad, Marrakech, Morocco
Email: sammou.elmastapha@yahoo.fr
Received December 11, 2011; revised January 5, 2012; accepted January 26, 2012
Keywords: Routing; Delay Tolerant Networks; DTN; Spray and Dynamic; Spray and Wait; MaxProp; Custody Transfer; Simulator
ABSTRACT
This paper addresses the problem of routing in delay tolerant networks (DTNs). Delay tolerant networks are wireless networks where disconnections occur frequently due to mobility of nodes, failures of energy, the low density of nodes, or when the network extends over long distances. In these cases, traditional routing protocols that have been developed for mobile ad hoc networks prove to be ineffective to the extent of transmitting messages between nodes. To resolve this problem and improve the performance of routing in delay tolerant networks we propose a new routing protocol called Spray and Dynamic; this approach represents an improvement of the spray and wait protocol by combining it with the two protocols: MaxProp and the model of “transfer by delegation” (Custody Transfer). To implement our approach Spray and Dynamic, we have developed a DTN simulator according to DTN network architecture.
1. Introduction
The domain of delays-tolerant networks (DTN) has really emerged in recent years to provide mechanisms to resolve communication problems and the problems of routing in delays-tolerant networks and necessary in an environment, there where it is almost impossible to find a connection from end to end communication path.
To resolve this problem researchers have proposed the use of routing protocols based on the mechanism StoreCarry-and-Forward [1]. According to this mechanism, a DTN node which is found disconnected from the rest of the network must keep long a given message in its storage unit and more specifically until a transmission opportunity it presents itself. An opportunity for transmission is to make contact with another node in the network that in turn agrees to act as a relay for the message.
Sometimes, a DTN node may be forced to choose among several opportunities for possible transmission for a given message. This choice can be random or may be based on statistical information describing the status of each relay available. In general, the right choice comes down to the relay which has the highest probability of encountering the destination of the message. To find such a relay, a DTN node needs information about the state of the various possible relays.
With the aim of improving the performance of DTN routing in networks we propose a new routing approach called Spray and Dynamic, this approach is to improve the routing protocol spray and wait by combining it with the two routing protocols MaxProp and the model of “transfer by delegation” (custody transfer).
2. Routing Protocols Used by Spray and Dynamic
The Spray and Wait routing protocol [2]: This is a simple routing protocol based on the messages replication. It consists of two phases:
· Spray phase: for every message originating at a source node, L message copies are initially spread— forwarded by the source and possibly other nodes receiving a copy—to L distinct “relays”.
· Wait phase: if the destination is not found in the spraying phase, each of the L nodes carrying a message copy performs direct transmission (i.e. will forward the message only to its destination).
Spray and Wait combines the speed of epidemic routing with the simplicity and thriftiness of direct transmission. It initially “jump-starts” spreading message copies in a manner similar to epidemic routing. When enough copies have been spread to guarantee that at least one of them will find the destination quickly, it stops and lets each node carrying a copy perform direct transmission.
The MaxProp routing protocol [3] uses several mechanisms to create a ranked list that determines which packets are transmitted first during a transfer opportunity. The primary factor that determines the ranked list is a delivery cost estimate assigned to each destination. The cost is based on the probability that the next transfer opportunity with a particular peer, estimated from observed history. These probabilities are added to form a path score; the minimum score of all possible paths via the current peer to a destination is chosen as the cost estimate.
· MaxProp considers the probability, 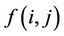 is the probability that j is the next node to establish contact with the node i.
is the probability that j is the next node to establish contact with the node i.
· For all nodes i, 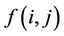 is initialized to
is initialized to
 .
.
· The cost of a path including nodes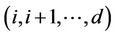 , will be the sum of probabilities that each connection along the path is not established.
, will be the sum of probabilities that each connection along the path is not established.
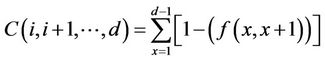 .
.
· The cost that will be associated with each destination, is the smallest among those associated with different paths to d.
The model of transfer by delegation (custody transfer) defined in [1,4,5] based on this general principle: a node that has agreed to store a message must forward this message to another node before itself abandon any responsibility opposite of that message. In this model by assigning responsibility for a message to a single node at any time. This model has the advantage of being economical in terms of resources, since a message is the responsibility of a node at any time during its delivery. However it now risk losing the message if the wearer goes down or destroyed. The application of the model of transfer by delegation is actually possible in networks where there are some mobile nodes moves in a planned and controlled. Communications may well be carried over long distances, for example using buses as carriers of messages [6].
3. Proposed Approach: Spray and Dynamic
In our approach we propose a new routing protocol called Spray and Dynamic that combines between the advantages of the three routing protocols: Spray and Wait [2], MaxProp [3] and the model of “transfer by delegation” [1,4,5].
This combination is to replace the wait phase of the protocol Spray and wait by another phase called Dynamic over which packet transmission is done according to the manner used by the routing protocol MAXPROP and the model of “transfer by delegation” proposed in the article [7] as shown in Figure 1.
The combination of these three approaches (Spray and
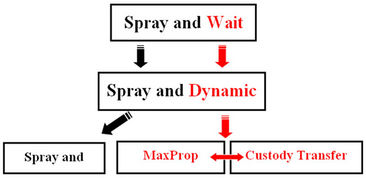
Figure 1. Illustrates the improvement of the Spray and Wait protocol by MaxProp and Custody Transfer.
Wait, MaxProp and Custody Transfer) combines three kinds of routing techniques depending on the degree of knowledge that a node has about its future contacts with other nodes in the network [8]:
· Controlled routing technique: This technique is based on controlled contacts between nodes, these nodes are usually controlled movements, their journey may follow a path fixed and predetermined to allow a maximum number of contacts with other nodes.
· Routing technique predicted: This technique tries to exploit some useful knowledge concerning the mobility of nodes or the history of their old transfers or of their old contacts.
· Opportunists routing technique: This technique is characterized by random contacts between nodes, and therefore the packet exchange, could not be scheduled in advance.
4. Transmission Strategy of Spray and Dynamic
It is a routing protocol simple and efficient, it is summed up in the following phases [2,7]:
Spray phase: a random routing phase, for each new message that has been generated by a source, this phase ensures that L copies of the latter will spread the same way used in the Epidemic routing in DTN network, and the message will present in L different relays.
Dynamic phase: a probabilistic routing phase, the probability of delivery is calculated using the history of contacts between nodes. The transmission of messages between nodes is based on the general principle set out in [7]:
1) When the source and destination in the same area.
· When a node encounters another node with the highest probability of delivery, it sends the message to that node and still keeps the message for transmission to other nodes in the future.
· When a node encounters another node that has a planned movement and a low probability of delivery, it sends this message to the node even if the probability of delivery is low, then it deletes the copy of the message he keeps, then, it frees up space in its storage unit.
· When a node encounters another node that has a planned movement and the probability of delivery is high, it sends the message to that node, then it deletes the copy of the message, then it releases the space at a storage unit.
2) When the source and destination in two different areas.
Nodes that can act as carriers of the message are nodes that have a high probability of delivery, the planned movements between zones and a sufficient transmission energy.
· In the case of a network where there are only the nodes that have random movements, the best carriers are the nodes that have a high probability of delivery and a sufficient transmission energy.
· In the case of a network where there are nodes that have random movements and nodes which have planned movements, the best carriers are the nodes that have a planned and controlled movement between zones and a sufficient transmission energy.
3) Cases where the nodes are not allowed to transmit messages.
· When a node encounters another node that has a high probability of delivery and has not enough energy.
· When a node encounters another node that has a planned movement and controlled and not enough energy.
· When a node encounters another node that has a planned and controlled movement and a high probability of delivery and has not enough energy.
4) Mechanisms of acquittals
· The acknowledgment mechanism between nodes is done according to the acknowledgment mechanism used by the model of “transfer by delegation” (Custody Transfer) and MaxProp [1,3-5].
5. Simulation and Test
The simulator is written in Java. JAVA is an object-oriented programming language, allows one hand to develop real applications and the other hand the objectoriented approach considers a program as consisting of a set of objects which adapts our approach (Spray and Dynamic). Figure 2 shows the main interface of the application.
5.1. Assumptions and Data Analysis
1) Value of L: L is the number of copies of a message that can circulate in the network. The authors of [2] propose an analytical model to calculate the number of copies to be created according to the size of the network and the delivery time, but this calculation requires knowledge of certain characteristics of the network. In our case L depends on the total number of nodes in the network, the probability of delivery and the mobility of nodes. To initialize the parameter L, we used the following formula:

N: Total number of nodes in the network E: Integer part
2) Assumptions: We assume that Packet routing is done from the “store-carry-and-forward”. The volume of the queue is considered infinite. The nodes move according to the two models of random mobility: Restricted random waypoint and Radom Waypoint [9-11]. The speed of nodes varies between Vmin = 200 ms and Vmax = 50 ms. The space of traveled nodes varies between 50 and 500 units of surface. The number of nodes varies between 8 and 300 nodes. The number of packets from the source is 1000 packets. The energy level of each node is 1000 units of energy. The probability of delivery is calculated locally according to formulas presented by the routing protocol MaxProp [3] and the model of “transfer by delegation” [1,4,5].
· MaxProp considers the probability,  is the probability that j is the next node to establish contact with the node i.
is the probability that j is the next node to establish contact with the node i.
· For all nodes i,  is initialized to
is initialized to
 .
.
· The cost of a path including nodes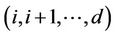 , will be the sum of probabilities that each connection along the path is not established.
, will be the sum of probabilities that each connection along the path is not established.
· 
· The cost that will be associated with each destination, is the smallest among those associated with different paths to d.
3) Data analysis: In this simulator we have analyzed the following data: The number of packets transmitted in the network; the number of packets not sent; the number of packets received by the destination; the energy consumed in the network; the amount of memory consumed in the network. This analysis is done according to the approach of the “Spray and Wait” and in our approach “Spray and Dynamic” to compare the two approaches.
5.2. Tests and Results
1) Scénario 1: Both areas are dense and connected. The internal connectivity of each zone is guaranteed. However, there is no permanent connection between the two areas. As is shown in Figure 3 and Table 1.
· Simulation results according to the approach of Spray and Wait.
· Simulation results according to the approach of Spray and Dynamic.

Figure 2. Illustrates the main interface of the application.
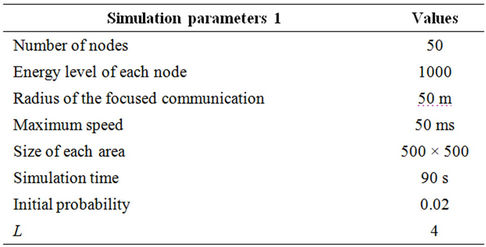
Table 1. Parameters of simulation 1.
2) Scénario 2: The node density is low in both areas. The internal connectivity of each zone is not guaranteed and there is no permanent connection between the two areas. As is shown in Figure 4 and Table 2.
· Simulation results according to the approach of Spray and Wait.
· Simulation results according to the approach of Spray

Table 2. Parameters of simulation 2.
and Dynamic.
According to simulations realized, Spray and Dynamic has good performance (Figures 5 and 6) compared to the approach of Spray and Wait (Figures 7 and 8).
Spray and Dynamic approach is a routing protocol simple and efficient permits both:
· Limit the number of carriers of a message by using


Figure 3. Illustrates a dense network and connected.


Figure 4. Illustrates a network is not dense and is not connected.
the MaxProp protocol and Custody Transfert.
· Limit the number of copies of a message circulating in the network by using the Spray and Wait protocol.
· Maximize the chances that a message reaches its destination.
· Minimize the resources consumed in the network such as bandwidth, capacity of storage devices and energy of the different nodes.
6. Conclusions
Delay tolerant networks are wireless networks where disconnections occur frequently due to mobility of nodes, failures of energy, the low density of nodes, or when the network extends over long distances.
In these cases, traditional routing protocols that have been developed for mobile ad hoc networks show inefficient since they require the existence of a dense and connected in order to route packets.
We have proposed a new approach to routing called Spray and Dynamic, this approach represents an improvement of the spray and wait protocol by combining it with the two protocols: MaxProp and the model of “transfer by delegation”. It is to broadcast the packets as soon as possible at first, then to forward packets according to routing metrics include: likelihood of delivery, spare battery and mobility of nodes to strictly limit the number of copies of each packet flowing through the network and optimize the use of network resources.
According to simulations, Spray and Dynamic has good performance compared to the approach of Spray and Wait, but its effectiveness can be improved.


Figure 5. Illustrates the result of analysis of the approach of the Spray and Dynamic depending on the parameters of simulation 1.


Figure 6. Illustrates the result of analysis of the approach of Spray and Dynamic depending on the parameters simulation 2.

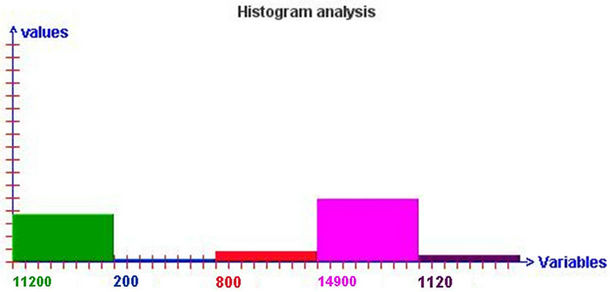
Figure 7. Illustrates the result of analysis of the approach of the Spray and Wait depending on the parameters of simulation 1.

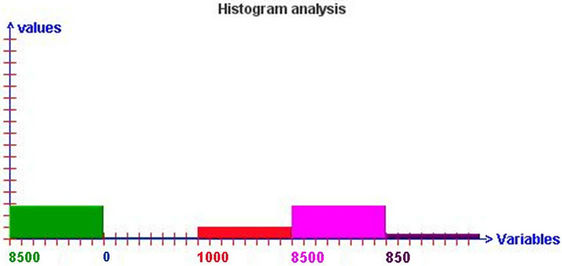
Figure 8. Illustrates the result of analysis of the approach of Spray and Wait depending on the parameters simulation 2.
REFERENCES
- F. Warthman, “Delay Tolerant Networks,” 2003. http://www.ipnsig.org/reports/DTN_Tutorial11.pdf
- T. Spyropoulos, K. Psounis and C. S. Raghavendra, “Spray and Wait: An Efficient Routing Scheme for Intermittently Connected Mobile Networks,” In: ACM SIGCOMM Workshop on Delay-Tolerant Networking, 2005, pp. 252-259.
- J. Burgess, B. Gallagher, D. Jensen and B. N. Levine, “MaxProp: Routing for Vehicle-Based Disruption-Tolerant Networks,” Proceedings of the 25th IEEE International Conference on Computer Communications, Barcelona, April 2006, pp. 1-11. doi:10.1109/INFOCOM.2006.228
- F. Guidec, “Deployment and Implementation Support Services Communicating in Pervasive Computing Environments,” HDR Thesis, Université de Bretagne Sud, Lorient, 2008.
- K. Fall, W. Hong and S. Madden, “Custody Transfer for Reliable Delivery in Delay Tolerant Networks,” Technical Report, Intel Research Berkeley, 2003.
- X.-L. Zhang, J. Kurose, B. N. Levine, D. Towsley and H.-G. Zhang, “Study of a Bus-Based Disruption Tolerant Network: Mobility Modeling and Impact on Routing,” Proceedings of the 13th Annual ACM International Conference on Mobile Computing and Networking MobiCom 07, September 2007, pp. 195-206.
- El M. Sammou, “Routing in ‘Delay Tolerant Networks’ (DTN): Improved Routing with MAXPROP and the Model of ‘Transfer by Delegation’ (Custody Transfer),” International Journal of Computer Science and Network Security, Vol. 4. No. 1, 2011.
- M. Ibrahim, “Routing and Performance Evaluation of Disruption Tolerant Networks,” l’Université de Nice-Sophia Antipolis, 2008.
- C. Bettstetter, H. Hartenstein and X. Pérez-Costa, “Stochastic Properties of the Random Waypoint Mobility Model,” Modeling and Analysis of Mobile Networks, Vol. 10, No. 5, 2004, pp. 555-567.
- C. Bettstetter, G. Rest, and P. Santi, “The Node Distribution of the Random Waypoint Mobility Model for Wireless Ad Hoc Networks,” IEEE Transactions on Mobile Computing, Vol. 2, No. 3, 2003, pp. 257-269. doi:10.1109/TMC.2003.1233531
- C. Bettstetter and C. Wagner, “The Spatial Node Distribution of the Random Waypoint Mobility Model,” Proceedings of German Workshop on Mobile Ad-Hoc Networks (WMAN), GI Lecture Notes in Informatics, Ulm, March 2002.

