Engineering
Vol.6 No.4(2014), Article ID:43806,8 pages DOI:10.4236/eng.2014.64022
A Cooperation-Aware Scheme for Overcoming the Traffic Congestion in the Deployment of WSNs
Yu-Hsing Chien1, Joy Iong-Zong Chen1*, Bo-Hui Lee1, Wen Bin Wu2, Chieh Wen Liou2
1Department of Electrical Engineering, Dayeh University, Changhua, Taiwan
2Department of Electrical Engineering, Asia-Pacific Institute of Creativity, Miaoli, Taiwan
Email: *jchen@mail.dyu.edu.tw
Copyright © 2014 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/


Received 1 January 2014; revised 1 February 2014; accepted 8 February 2014
ABSTRACT
An algorithm for enhancing the throughput of CAS (Cooperation-Aware Scheme) over a WSN (wireless sensor network) is presented in this article. The WSNs are classified as a task-oriented framework due to the fact that the power supply, memory and computing power of wireless sensor nodes are greatly hampered in WSNs. This study focused on exploring problems caused by traffic congestion on the WSNs with a large amount of flow, such as packet loss, bandwidth reduction, and waste of energy on the sensor nodes. On the other hand, the proposed CAS is a cooperative strong node mechanism in which a threshold is preset in order to determine whether the node traffic is over or not. The privilege of corresponding sensor nodes is upgraded when the load exceeds the threshold. Therefore, the sensor node can command its child nodes to change the transmission path for distributing the traffic effectively. Moreover, once the traffic is over the overall network flow threshold, it is necessary to add the other new sensor nodes into the network for relieving the traffic.
Keywords:CAS; Cooperative Strong Node; Packet Loss; WSN

1. Introduction
A deployment of WSN (wireless sensor network) composed by many sensor nodes becomes a major field for studying in wireless communications due to the fact that it can provide a huge of applications. Traditionally, the sensor node is consisting of four units including sensing unit, processing unit, transceiver unit, and power unit. The WSNs are classified as a task-oriented application network type, since wireless sensor nodes are equipped with limited power, memory and computing capability. In addition, the main protocols of WSN is IEEE 802.15.4 for LR-WPANs (Low Rate-Wireless Personal Area Networks), TG4 (Task Group 4) within the IEEE 802.15 specifications. It is known that the characteristics of LR-WPAN WSNs are low rate, low energy consumption, low cost, and they can also support a large number of sensor nodes. The addressed issues in this article are focusing on avoiding the congestion problems and on increasing the packet arrival rate in a large network environment.
In WSNs, the energy management and packet loss are two interesting issues for discussion. Many routing protocols have been designed for researching and solving these problems, for example, the algorithms of LEACH (Low-Energy Adaptive Clustering Hierarchy), TEEN (Threshold Sensitive Energy Efficient Sensor Network) Protocol, HEED (Hybrid Energy-Efficient Distributed Clustering), GAF (Geographic Adaptive Fidelity), GEAR (Geographic and Energy Aware Routing), and Simple Least-Time Energy Routing Protocol with One-LEO (One-Level Data Aggregation) and so on. Most of the routing protocols reminded previously can be applied to reduce energy consumption and distribute traffic [1] . However, the more incremental in number of nodes, the significantly more promote packets processed by each sensor nodes. There is no guarantee that all nodes with large flow do not exhaust the energy, or have traffic congestion due to overloading. Even it is going to lead the packet loss or node failure. The existing routing protocol solution is to change the transmission path when packet traffic over the loading limits. It trades off the transmission efficiency for the benefit of traffic dispersion. Although it works in some cases when the traffic of all other paths exceeds loading limits in the same time, the WSNs will collapse. For avoiding the power waste, less storage space and low computation ability, ID-based signcryption scheme using bilinear pairing are proposed in [2] . In [3] , the authors applied the division of a single queue in each node to multiple weighted sub-queues logically and then forwarding packets in each sub-queue based on its weight. Such a proposed multi-queue-LIFO (Last-In, First-OUT) approach is used to remove the phenomena of delay and unfairness in congested WSNs. By means of migration, the data traffic in non-congestion region, a so-called on-demand node placement algorithm, is provided by the authors in [4] . An algorithm presented in [5] where the buffer in each node is adjusted according to the transmitting downstream nodes in order to minimize packet drop caused by the congestion.
In the priority-based scheme [6] in which mainly emphasized the importance of priority. Most the recent researches discussed about the congestion control problems for WSNs are only guarantee the simple fairness, which concluded that the sink obtains the same throughput performance from all sensors. In fact, the sensors might be deployed in different places and have the difference of hardware or capacity, thus, the sensing events are different totally. Thereafter, the priorities of sensors in passing message would be different. The most important sensors have the higher priority, which means that the important sensors can gain higher throughput performance. In [7] , a priority-based congestion control protocol is proposed. Such scheme uses packet inter-arrival time along with packet service time to measure a parameter defined as congestion degree and furthermore imposes hop-by-hop control based on the measured congestion degree as well as the node priority index. Each sensor node to be forwarded mainly depends on the congestion degree in the header of data packets. The notification is triggered when the node overhears a congestion notification from its parent node during a fixed time period. Finally, each node allocates data rate to its upstream nodes according to their priorities.
The basic idea of the second one rate-based scheme can be described at the time the congestion happens, that is, for a forwarding node to estimate the number of flows transmitted from each upstream neighbor and to assign transmission rate in accordance with the fairness. In [8] , a complex theory is applied to describe the statistical characteristic of WSNs firstly, and the ideal topology formation is studied according to these statistical characteristics. Finally, fitness model is used to generate the topology for reducing the congestion detected by sink. Each sensor node monitors its local buffer level and sets a congestion notification bit in the packet forwarded to the sink when the buffers generate overflow. The sink is going to infer congestion and broadcast a control signal to notify all source nodes for reducing the report frequency, when receives a packet set of congestion notification bit. A protocol called as distributed CODA (Congestion Detection and Avoidance) is proposed in [9] . The CODA teaches that the receiver of sensor node will broadcast a suppressive message to its upstream neighbors and make local adjustment to prevent propagating the congestion downstream when congestion is detected. At the same time, based on its own local network conditions, the receiver of sensor node needs to determine that whether to further propagate the backpressure signal or not as an upstream node receives a backpressure message. This scheme does not consider the fairness issue. Furthermore, the authors in [10] propose a mitigating congestion protocol which combines three congestion mitigating mechanisms, hop-by-hop flow control, rate limiting and prioritized MAC layer. This scheme described in [10] requires a tree routing structure to work correctly. A localized algorithm for aggregate fairness protocol is proposed in [11] . Generally, in WSN, a sensor will calculate and allocate the data rates of upstream neighbors by a weighted fairness function, when a sensor receives the number of packets that are more than it can forward. However, the fairness function of the congestion control protocol was not considered carefully with the remaining buffer size and transmission rate at the same time. On the other hand, the congestion control protocol only considers that the sum of data rate from upstream neighbors must be less than the sum of data rate when the congestion is detected.
In [12] , a congestion avoidance protocol is proposed on the basis of lightweight buffer management in sensor networks. Although it can realize and guarantee the packet without loss in the forwarding way, the buffer utilization is low. Most of congestion control protocols do not consider buffer state and data rate at the same time [13] -[15] . The rate-based scheme is just for a forwarding node to estimate the number of flows passing from each upstream neighbor, and assign rate in accordance with the fairness when the congestion is detected. Both the two schemes consider either in data rate or buffer state to allocate the data rate for its upstream neighbors [16] . Hence, in [17] a APTEEN (hybrid routing protocol) which allows the nodes in each network not only react to time-critical situation, but also give an overall energy efficient for comprehensive information retrieval. Moreover, an algorithm referred as DECHP (Distributed Energy-efficient Clustering Hierarchy Protocol), which distributes the energy dissipation evenly among all sensor nodes to improve network lifetime and average energy savings, was suggested in [18] .
On the basis of reviewing the aforementioned researches, in this article, a CAS (Cooperation-Aware Scheme) based on the change of the transmission path method is proposed. Compared with the previous protocols, it not only makes accurate selection of alternate paths, but also quickly adapts to the original network when a new node is required to be involved. Both in the Hierarchical protocols and Location-based protocols, when node traffic soon exceeds the load limit, the privilege level of nodes will be elevated and it can command its child nodes to change the transmission path. Compared to other distributed traffic agreements, we focus on the part of selection of alternative paths. The proposed method will be described in detail in Section II. Generally, there are three categories of congestion control schemes in WSNs, priority-based, rate-based, and buffer-based schemes.
The rest of the paper is organized as follows. The proposed models of CAS are established in Section 2. In Section 3, the experimental and comparisons results are illustrated. There is a brief conclusion drawn in Section 4.
2. Cooperation-Aware Scheme (CAS)
2.1. Questions and Preliminary
In this subsection, the questions claimed in [19] first briefly described before the CAS is presented. It is known that the AODV is based on the flooding broadcast scheme to search the path and a routing protocol for dynamic wireless networks. In the search path, each node in establishing a single minimum path for the destination node records path length and the information in the routing table by passing messages. AODV defines three types of messages to notify the different status of the event happened in WSN, including the routing request, the routing reply and the routing error. These three messages are based on the format of the packet to pass forward and backward. AODV defines path search method with two phases. First of all, the phase is to broadcast the routing request message and to establish a return path. The second phase is to return the routing reply message and to construct the transmission path. AODV defines routing request message contains the following important information, Originator IP Address, Originator Sequence Number, Destination IP Address, Destination Sequence Number, and Hop Count.
Accordingly, a WSN system is composed of many sensor node and the hardware conditions, such as energy and memory of these sensors are limited. Usually, there are two types of congestion in WSNs. One of them is channel collision and the other is buffer congestion. The first type of channel collision can be solved in MAC layer by the algorithms of CSMA, FDMA, TDMA, and CDMA illustrated in [11] . A growing number of sensor networks use CSMA for medium access. For example, the widely used Berkeley motes use a simple CSMA MAC as part of the Tiny-OS platform. The CSMA can improve channel collision but cannot solve the congestion problem. It may cause the buffer of a sensor overflow if several neighbors of the sensor have packets with high data rate to the sensor. Thereafter, a new mechanism we proposed in this report that can effectively solve the buffer congestion. The presented CAS which responses to ACK_Packet with a warning message when the node excess load already. The warning message is used to notify the particular child nodes of the need to change the path. Child node broadcasts query_Packet in order to obtain the weight value of the neighbor, and then selects an alternate node to solve the congestion problem. The detail description of the method will be given in the next section.
2.2. CAS Algorithms
The functionality of the proposed mechanism could be divided into two modes when the node receiving a packet, one is general node mode and the other is strong node mode. In this sub-section presents each mode in detail. The general node mode is the basic mode for operating in CAS. In this mode, the node adopts the selected routing protocol, and when the buffer loading exceeds the threshold, the node will switch the mode to the strong node mode and then begin to perform traffic dispersing action.
In the general node mode, when the buffer loading is higher than HLTV_1, the node will switch to the strong node mode. The node does not become an alternate node for the other nodes when the node is in the strong mode. In strong node mode, the node will not respond to other nodes asking for the packet of node weight, and provides the permission to notify the child node to change the transmission path. In the strong node mode, when the buffer loading is lower than LL in the node, it switches back to the general node mode and provides an alternate node function.
Network congestion occurs while the assigned traffic load exceeds the available capacity at any point in the WSN environment [8] . Despite the fact that single path routing increases the probability of congestion occurrences, the congestion very likely runs out even for multipath routing schemes. Congestion avoidance is the process of detecting incipient congestion and preventing its occurrence. Buffer loading is one way frequently used to detect incipient congestion [20] -[22] . Multipath routing is inherently an avoidance scheme since the traffic is distributed among the available paths and hence the congestion is able to be avoided. The avoidance mechanism is designed to handle the instant increase in the amount of traffic. Although this kind of traffic is assumed to be transient and will stop when the event being monitored disappears, it is not always the case. The traffic may keep on flowing in high data rates if the sensors monitor a variety of physical phenomenon.
In CAS scheme, the buffer loading is applied to detect the outcome of congestion problems. When the buffer loading is higher than the preset threshold, there are impending congestion problems, thereby, the operating node mode is going to be switched into the strong node mode for reducing the network traffic. The transmission path and the node traffic of a child node is changing and observing, respectively, when in the strong node mode. If the traffic congestion is not reduced or just sustains in a saturated state, the node keeps stay in the strong node mode. In advance, once the node traffic keeps on increasing and reaching the buffer loading threshold in the strong node mode, all its child nodes of the transmission path are changed into the strong node mode case. As described above, the action to change the child nodes of the transmission path is divided into two stages. It is the reason to avoid changing modes of all child nodes of the path at the same time, which will not alleviate congestion but only transfer the congestion to other nodes. Unless in the strong node mode, a large number of sub-node path will be changed to effective relieve traffic. The node has been unable to handle the current flow, when the buffer loading is higher than a value preset in HLTV_2.
The algorithm of CAS mainly designed to avoid packets dropped by nodes due to high traffic loading. When a node is in danger of being overloading, part of the traffic is distributed to other nodes before the occurrence of the congestion problem. Figure 1 shows the operation of CAS. Figure 1(A) indicates that the network in a normal state. Figure 1(B) shows an event occurs in node 9, and it transmits a large number of packets to the node 5, which is therefore changed to the strong node mode and responds an ACK packet with a warning message to replace with its transmission path. In Figure 1(C), node 9 receives the ACK packet with a warning message and broadcasts query packets. In Figure 1(D), node 5 has entered a strong node mode, hence, it does not respond until node 6 and node 8 returning information to node 9. In Figure 1(A), initiate node changes the transmission path to next node, but since next node is transmitting to other node which enters state of change the path in CAS as shown in Figure 2. In Figure 1(A), next node received the ACK packet with a warning message.
2.3. Calculation of Node Weights
In the algorithm, three factors are used in the calculation of weight values, buffer loading, energy consumption, and hops the base station. To reduce the occurrence of congestion and to improve packets delivery ratio, reliabilities are the main issue for discussion of this mechanism. Weight values will affect selection of the alternate
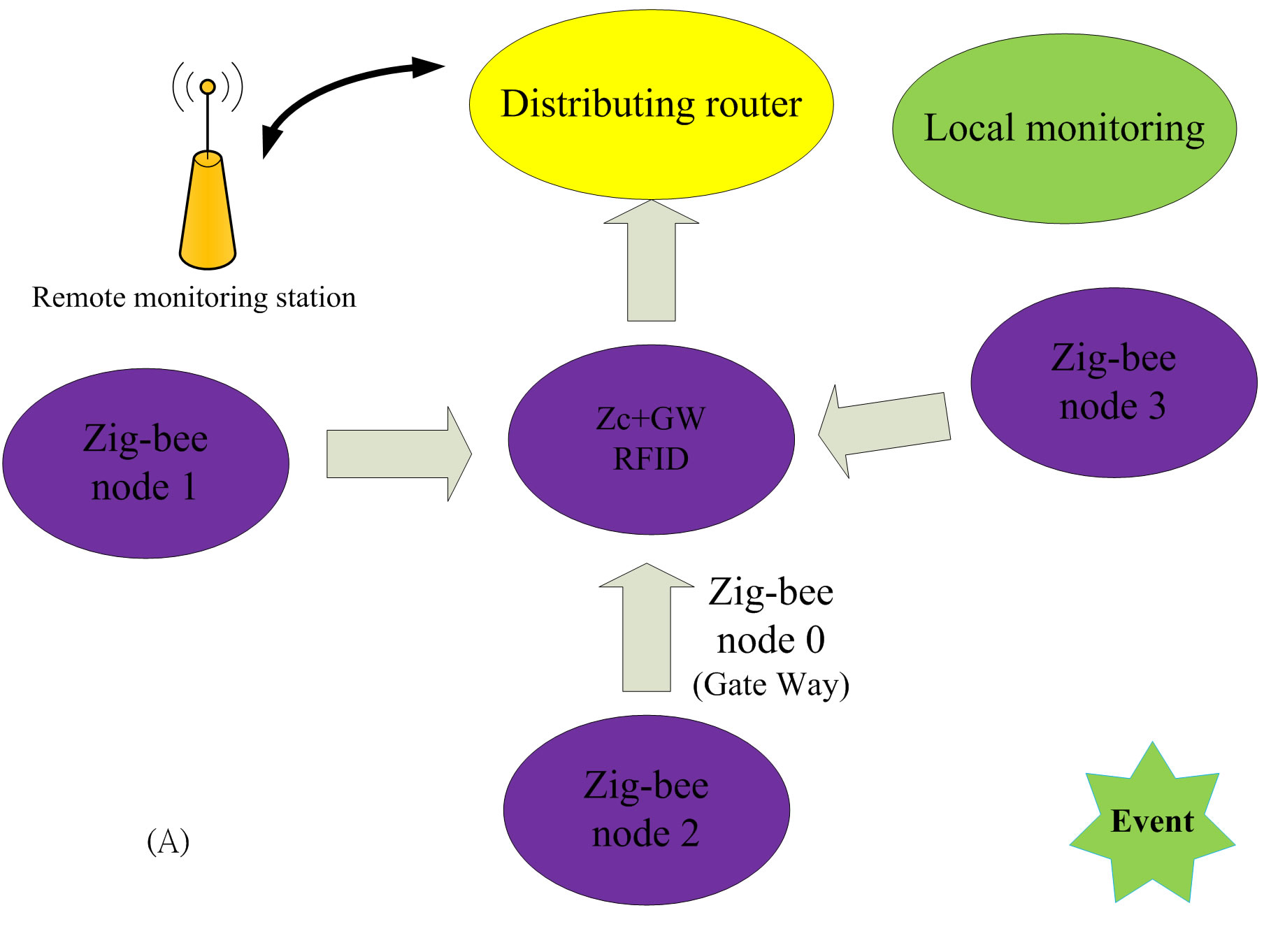
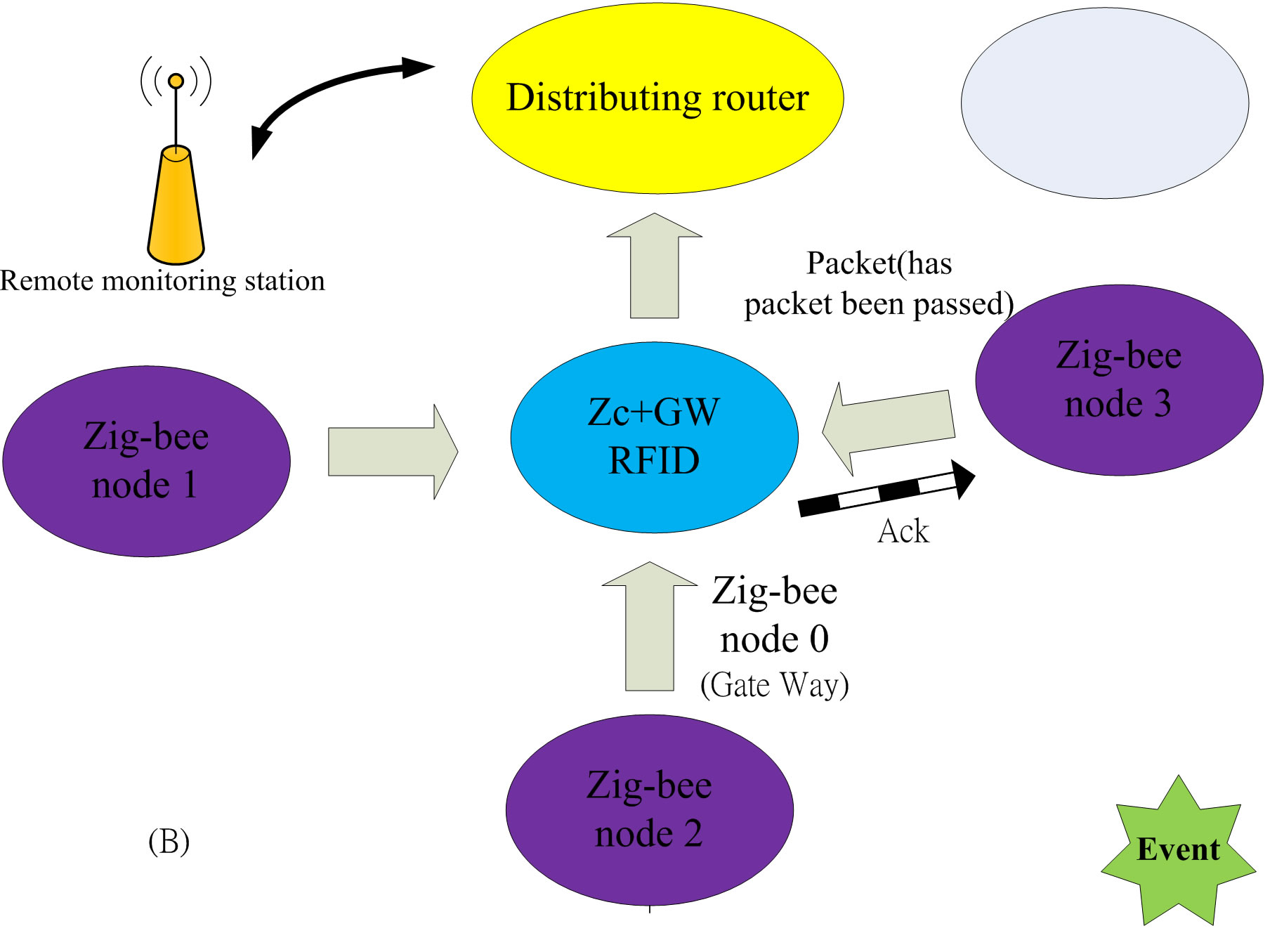
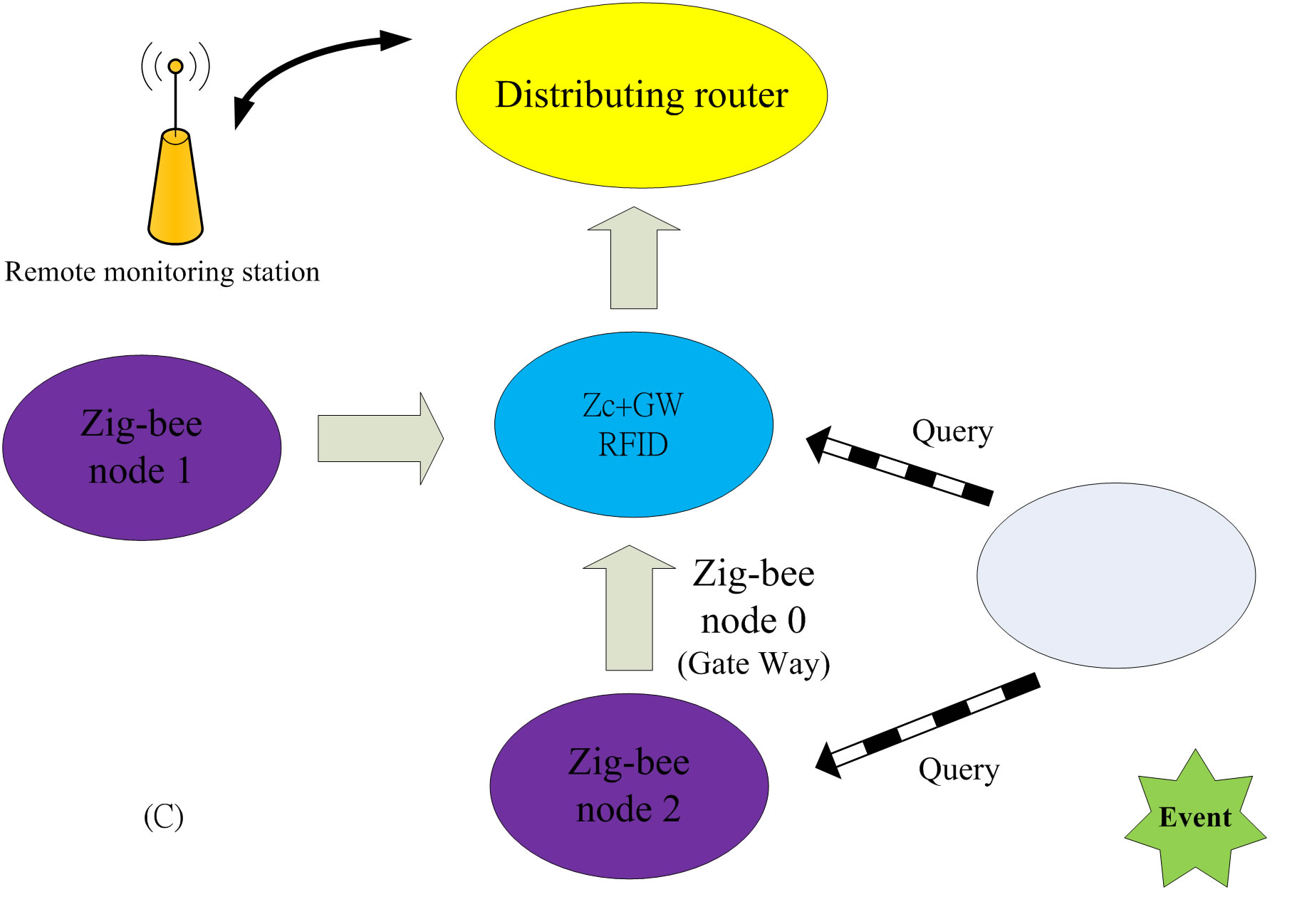

Figure 1. The work flow of CAS.
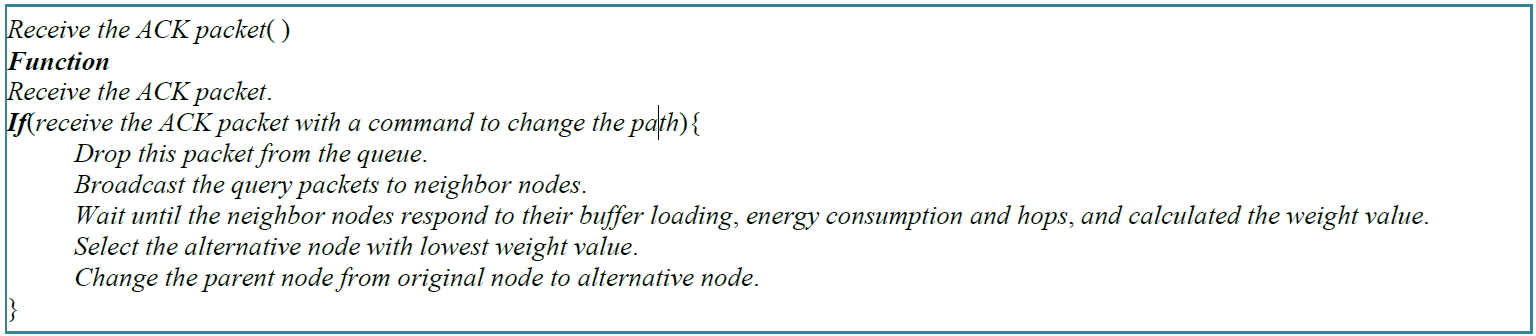
Figure 2. The pseudo code of the node receive the ACK packet.
path. The number of hops decides the distance of this node to the base station, and it is the most important factor for selection of alternate path. If the hop count of alternate node is higher than the original node, it has longer distance. To calculate the priority, we first determine the number of hops, then the amount of residual energy and the remaining buffer size finally. The nodes on the alternate path will soon become the strong node mode when the residual energy and the remaining buffer size weight are too high. Threshold value is set to alternately select nodes with the most important ability to assist the traffic. This method proposes a weight calculation by collecting three kinds of neighboring node information. It chooses the nodes with the lowest W (weight) value to form a new transmission path. The calculation of weight values can be obtained as
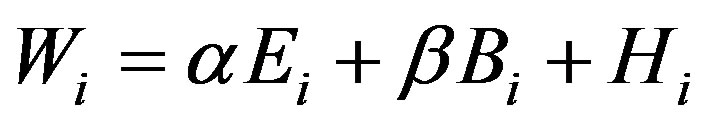 (1)
(1)
where Wi is the weight value of node i, Ei denotes the energy consumption of the i-th node, Bi indicates buffer loading of node i, and the number of hops to base station from node i is represented as Hi. Assume that several neighbors have the same minimum hops, the priority is calculated according to values of α and β. Thereafter, the lowest value of W is determined, where α and β are with the values between 0 to 1, and are controlled by the network administrator. Moreover, the two values have to satisfy that 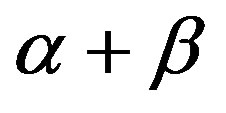 .
.
Figure 2 shows a pseudo code of child node received an ACK packet with the messages for a path change.
3. Simulating Results and Analysis
The simulation framework describes simulation environment, simulation parameters, and the simulation programs. The simulation results are shown and analyzed in Figures 2 and 3. Table 1 show the system parameters of the experiment which is performed by fussing CAS mechanism into the AODV protocol. The CAS scheme will lead to switch into the node mode when the node traffic exceeds the threshold. On the other hand, then the child nodes will change the path of the received command according to the CAS mechanism for avoiding drop of packets due to the fact that a full buffer occurs. Currently, the thresholds values of HLTV_1 and HLTV_2 are assigned as 70% and 80%, respectively, and LL is additionally set as 50%.
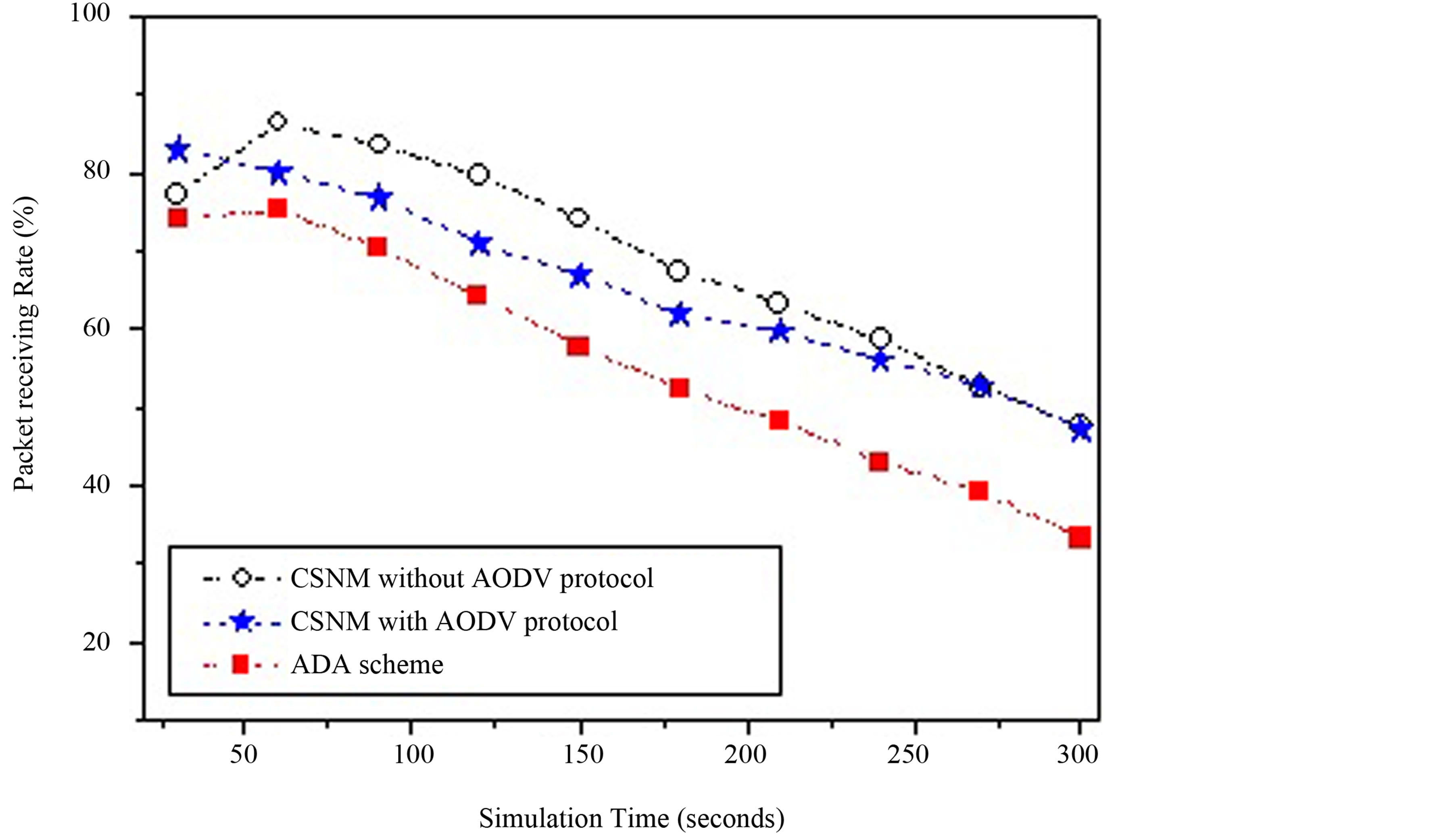
Figure 3. The packet receiving rate of AODV-CAS and AODV.
Table 1. The parameters of CAS experiments.
Figure 3 shows the comparison of packet receiving rate of AODV-CAS and other schemes. As shown in the figure, the packet receiving rate of CAS mechanism with the AODV protocol is better than other schemes. So, the proposed CAS mechanism is able to mitigate the congestion problem and to avoid the loss of packets. In the traffic environment, because of the buffer size of a single node being limited in the AFA scheme and BB scheme, the effect of congestion avoidance is restricted. The mechanism proposed in this article is cooperative, and able to use the resources of each node. In words, in the traffic environment, the performance will be better than other schemes.
Figure 3 shows the comparison results of packet receiving rates without considering energy consumption. Under the outcome of the consideration, the scheme presented in this work shows much more advantages. The node is keeping on cooperation and maintains a high receiving rate when the node does not exhausted by energy consumption. The experimental results show the proposed mechanism is suitable for applying the issues focus on the receiving rate of WSNs.
The proposed scheme is compared with the AFA (Aggregate Fairness Algorithm) algorithm shown in [7] , and with BB (Buffer-Based) congestion avoidance scheme in [8] too. In the AFA scheme, a sensor node i have a packet to forward sensor node j, only if the buffer state of sensor node j is not full. Otherwise, the buffer of sensor node j, sensor node i will hold the packet until it overhears a packet piggybacking a non-full buffer state from sensor node j. Thus, such aforementioned statements can protect packet from losing at all. The AFA scheme is a rate-based scheme. The BB scheme has to confirm that a sensor node i send a packet to its downstream neighbor sensor node j only when sensor node j has buffer space to hold the packet. It also completely holds all the packets without missing.
4. Conclusion
The proposed scheme CAS is focused on improving the congestion problems that might occur in WSNs, when the extension of the network lifetime and the reduction of transmission delay are aware. A strong node mode is applied in the mechanism of CAS. Strong node mode means that the node with large traffic that provides permission to its child nodes to decide whether to change the transmission path or not. Some ways are proposed to solve the issue that is more than one child node transmission path changes at the same time. Furthermore, it is used to avoid propagation problems caused by high loading to the alternate node. There are three factors adopted in the deployment, e.g. remaining buffer size, residual energy and the number of hops. The alternate node is the shortest path in the surrounding neighbors of the original node and the most capable of handling traffic.
References
- Barontib, P., Pillaia, P., Chook, V., Chessa, S., Gotta, A. and Hu, Y.F. (2007) Wireless Sensor Networks: A Survey on the State of the Art and the 802.15.4 and ZigBee Standards. Computer Communications, 30, 1655-1695. http://dx.doi.org/10.1016/j.comcom.2006.12.020
- Al-Karaki, J.N. and Kamal, A.E. (2012) Lightweight Trusted ID-Based Signcryption Scheme for Wireless Sensor Networks. International Journal on Smart Sensing and Intelligent Systems, 5, 799-810.
- Xiong, J.J., Lyu, M.R. and Ng, K.-W. (2012) Congestion Performance Improvement in Wireless Sensor Networks. IEEE Aerospace Conference, Big Sky, 3-10 March 2012, 1-9. http://0rz.tw/h20zI
- Cha, H., Kim, K.-H. and Yoo, S.W. (2011) A Node Placement Algorithm for Avoid in Congestion Regions in Wireless Sensor Networks. 3rd International IEEE Conference on Ubiquitous and Future Networks (ICUFN), Dalian, 15-17 June 2011, 202-207. http://0rz.tw/IUtVJ
- Michopoulos, V., Guan, L. and Phillips, I. (2010) A New Congestion Control Mechanism for WSNs. IEEE 10th International Conference on Computer and Information Technology (CIT), Bradford, 29 June-1 July 2010, 709-714. http://0rz.tw/wfu8q
- Yaghmaee, M.H. and Adjeroh, D.A. (2009) Priority-Based Rate Control for Service Differentiation and Congestion Control in Wireless Multimedia Sensor Networks. Computer Networks: International Journal of Computer and Telecommunications Networking, 53, 1798-1811.
- Wang, C.G., Sohraby, K., Lawrence, V., Li, B. and Hu, Y.M. (2006) Priority-Based Congestion Control in Wireless Sensor Networks. Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC), Taiwan, 5 June-7 July 2006, 22-31. http://dx.doi.org/10.1109/SUTC.2006.1636155 http://0rz.tw/10d4u
- Liu, L.F., Wu, J.G., Xiao, F. and Wang, R.C. (2013) CFM: A Fitness-Model-Based Topology Control Algorithm for Wireless Sensor Networks. International Journal on Smart Sensing and Intelligent Systems, 6, 58-76.
- Wan, C.-Y., Eisenman, S.B. and Campbell, A.T. (2003) Congestion Detection and Avoidance in Sensor Networks. Proceedings of the ACM Conference on Embedded Networked Sensor Systems (SenSys), Los Angeles, 5-7 November 2003, 266-279. http://sensys.acm.org/2003/
- Hull, B., Jamieson, K. and Balakrishna, H. (2004) Mitigating Congestion in Wireless Sensor Networks. Proceedings of the ACM Conference on Embedded Networked Sensor Systems (SenSys), 3-5 November 2004, 134-147. http://sensys.acm.org/2004/
- Chen, S.G. and Zhang, Z. (2006) Localized Algorithm for Aggregate Fairness in Wireless Sensor Networks. Proceedings of the ACM International Conference on Mobile Computing and Networking (MobiCOM), Los Angeles, 24-29 September 2006, 274-285. http://www.sigmobile.org/mobicom/2006/
- Chen, S.G. and Yan, N. (2006) Congestion Avoidance Based on Lightweight Buffer Management in Sensor Networks. Proceedings of the IEEE International Conference on Parallel and Distributed Systems (ICPADS), 17, 934-946.
- Xiong, Z.Y., Fan, X.P., Liu, S.Q., Li, Y.Z. and Zhang, H. (2013) Performance Analysis for DCT-Based Coded Image Communication in Wireless Multimedia Sensor Networks. International Journal on Smart Sensing and Intelligent Systems, 6, 120-135.
- Intanagonwiwat, C., Govindan, R., Estrin, D., Heidemann, J. and Silva, F. (2003) Directed Diffusion for Wireless Sensor Networking. IEEE/ACM Transactions on Networking, 11, 2-16. http://dx.doi.org/10.1109/TNET.2002.808417
- Heinzelman, W.R., Chandrakasan, A. and Balakrishnan, H. (2000) Energy-Efficient Communication Protocol for Wireless Sensor Networks. Proceedings of the 33rd Hawaii International Conference on System Sciences, Maui County, 4-7 January 2000, 1-10. http://dx.doi.org/10.1109/HICSS.2000.926982 http://0rz.tw/UcVnG
- Manjeshwar, A. and Agrawal, D.P. (2001) TEEN: A Routing Protocol for Enhanced Efficiency in Wireless Sensor Networks. Proceedings of the 15th International Parallel and Distributed Processing Symposium, San Francisco, 23-27 April 2001, 2009-2015. http://dx.doi.org/10.1109/IPDPS.2001.925197 http://www.ipdps.org/ipdps2001/
- Manjeshwar, A. and Agrawal, D.P. (2002) APTEEN: A Hybrid Protocol for Efficient Routing and Comprehensive Information Retrieval in Wireless Sensor Networks. Proceedings of the International Parallel and Distributed Processing Symposium, Fort Lauderdale, 15-19 April 2002, 195-202. http://dx.doi.org/10.1109/IPDPS.2002.1016600 http://www.ipdps.org/ipdps2002/
- Moussaoui, O. and Naimi, M. (2005) A Distributed Energy Aware Routing Protocol for Wireless Sensor Networks. International Workshop on Modeling Analysis and Simulation of Wireless and Mobile Systems Archive, Hyatt Regency Montreal, 10-13 October 2005, 34-40. http://dl.acm.org/citation.cfm?id=1089444 http://www.ietf.org/mail-archive/web/mip4/current/msg01502.html
- Perkins, C.E., Belding-Royer, E.M. and Das, S. (2003) Ad Hoc on Demand Distance Vector (AODV) Routing. The Internet Engineering Task Force, Minneapolis. https://www.ietf.org/meeting/58/
- Yu, Y., Govindan, R. and Estrin, D. (2003) Geographical and Energy-Aware Routing: A Recursive Data Dissemination Protocol for Wireless Sensor Networks. UCLA Computer Science Department Technical Report, UCLA, Los Angeles. http://graphics.stanford.edu/courses/cs428-03-spring/readings.html
- Razzaque, Md.A. and Hong, C.S. (2009) Congestion Detection and Control Algorithms for Multipath Data Forwarding in Sensor Networks. International Conference on Advanced Communication Technology, 1, 651-653.
NOTES

*Corresponding author.


