Journal of Information Security
Vol.06 No.03(2015), Article ID:57630,8 pages
10.4236/jis.2015.63020
Palm Vein Authentication Based on the Coset Decomposition Method
Mohamed Sayed*
Faculty of Computer Studies, Arab Open University, Kuwait City, Kuwait
Email: msayed@aou.edu.kw
Copyright © 2015 by author and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 21 May 2015; accepted 27 June 2015; published 30 June 2015
ABSTRACT
The palm vein authentication technology is extremely safe, accurate and reliable as it uses the vascular patterns contained within the body to confirm personal identification. The pattern of veins in the palm is complex and unique to each individual. Its non-contact function gives it a healthful advantage over other biometric technologies. This paper presents an algebraic method for personal authentication and identification using internal contactless palm vein images. We use MATLAB image processing toolbox to enhance the palm vein images and employ coset decomposition concept to store and identify the encoded palm vein feature vectors. Experimental evidence shows the validation and influence of the proposed approach.
Keywords:
Biometrics, Coset Decomposition Method, Hand Veins, Personal Authentication

1. Introduction
Biometrics can be defined as an automated measurement of physiological or behavioral characteristics that are used to authenticate, determine or confirm identity of individuals [1] . The behavioral characteristics of human being are the way to sign their names, walk, speak or keystroke dynamics; while the physiological characteristics are the physical human traits such as hand shape, face, fingerprints, eyes, ears shape, and hand veins [2] . Biometric methods of identification show several particularities over classical methods such as identification cards (tokens) and personal identification numbers (passwords) for many reasons. For example, users to be sympathized have to present physically, often mandatory, at the place of identification. Also biometrics based identification techniques avoid carrying tokens or remembering passwords and prevent misuse of stolen identification cards, credit cards and passports [3] [4] .
Several important issues have to be taken into consideration to design an effective biometric system [5] . For instance, a user must be first enrolled in the system as a biometric template (or reference). Therefore, this template is securely stored in a central database or on a smart card issued to the user. This template can be used for matching when the user needs to be identified or authorized to login to a secured system. It is worth noting that any biometric system can operate in either verification (authentication) or identification modes; see for instance [6] .
One of the upcoming highly secure, accurate and precisebiometric technologies is the personal identification using palm veins [7] . It is the world’s first contactless authentication technology that uses the vein patterns in human palms to confirm a person’s identity [8] . The contactless feature that identifies people by their unique biological information gives it a hygienic advantage over other biometric systems. Advanced sensing and matching technologies are used in this biometric technology. The individual places his/her palm near to a sensor so that it takes the palm vein image by means of infrared rays and compares it with pre-registered palm vein images. As near-infrared light pushes through, blood deoxygenated hemoglobin streaming through the veins imbibes near-infrared rays, turning it out to be visible as black regions to the scanner. This system is not dangerous as a near-infrared ray is a component of sunlight, whose effect is much less than walking in sunlight. After the image acquisition the system initiates image enhancement and vein pattern segmentation. Thus the system translates the black lines of the infrared ray image as the blood vessel pattern of the palm and then matches it with the previously registered blood vessel pattern of the individual. If there is a match then access is allowed; if not the access is denied.
Similar to the problem of obtaining and reviewing a message through a noisy channel, when a user wants to access a system, the access device should permit access when palm vein information does not vary by more than a definite number of binary digits. Also, for security reason, it is eligible that palm vein information is saved in a database (on a token or on a smart card) in encrypted arrangement, rather than in normal digital image. Therefore, the techniques which employ coding theory can be proposed to solve the secure palm vein storage problem. In the literature there are several schemes which use ideas from coding theory for the biometrics storage problem; see for instance [9] . In this paper we apply an enhanced version of the coset decomposition algorithm [10] that uses syndrome bits as safe storage and decoding to palm vein templates. The syndrome bits should have enough attributes such that the templates are securely stored and then matched in a following stage. The implemented algorithm is used to overcome the disadvantage that a person who has access to the system may not match any of enrolled palm veins. Therefore, the algorithm should compute a bit string which will furnish access to the system even though the bit string is not shut to any of the stored palm vein templates.
2. Why Palm Vein Authentication?
At the present time many types of biometric systems are in use; the most widespread ones are fingerprints, face recognition, iris recognition, hand and finger geometry, voice print, signature identification, gait, DNA and dorsal hand vein. In the rest this section we will present some of the most commonly used biometric technologies.
The fingerprint recognition devices for laptop and cell phone access are now widely available from many different vendors at a low cost. With fingerprint technology [10] , users do not need to type passwords, instead a simple touch allows instant access. Now these systems are exceedingly used in identification modes. The patterns of friction ridges and valleys on an individual’s fingertips are unique to that individual. For decades, law enforcement has been classifying and determining identity by matching key points of ridge endings and bifurcations. However, some people may have damaged or eliminated fingerprints or may feel dissatisfied with placing their fingers on the same place where many other people have continuously touched. Also this type of biometrics is susceptible to distortion and noise imparted by dirt and twists.
The identification of a person by their facial image [4] can be done in a number of different ways, such as by capturing an image of the face in the visible spectrum using an inexpensive camera or by using the infrared patterns of facial heat emission. Facial recognition in visible light typically models key features from the central portion of a facial image. Using a wide assortment of cameras, the visible light systems extract features from the captured images that do not change over time, while avoiding superficial features such as facial expressions or hair. Some of the challenges of facial recognition in the visual spectrum include reducing the impact of variable lighting and detecting a mask or photograph. Some facial recognition systems may require a stationary or posed user in order to capture the image, though many systems use a real-time process to detect a person’s head and locate the face automatically. Major benefits of facial recognition are that it is nonintrusive, hands-free, continuous, and accepted by most users. However, this technology has many disadvantages such as it is affected by changes in lighting, the person’s hair, age, and if the user wears a glass. Facial images also depend on orientation/angle of user’s face with camera and requires extra camera equipment for user identification.
Iris (of the eye) recognition method [2] uses the colored area that surrounds the pupil. The iris patterns which can be obtained through a video based image acquisition system patterns are thought to be unique. Iris scanning devices have been used in personal authentication applications for several years. Systems based on iris recognition have substantially decreased in price, and this trend is expected to continue. The technology works well in both verification and identification modes. Current systems can be used even in the presence of eyeglasses and contact lenses. The technology is not intrusive and does not require physical contact with a scanner. Iris recognition has been demonstrated to work with individuals from different ethnic groups and nationalities. However, it is difficult to use because of positioning eye as well as it requires more time for matching with the enrolled data.
Hand and finger geometry of personal verification [3] are now well established. Hand recognition has been available for over 30 years. To achieve personal verification, a system may measure physical characteristics of either the fingers or the hands. These include length, width, thickness, and surface area of the hand. One interesting characteristic of this technology is that it requires a small biometric template (a few bytes). Hand and finger geometry has gained acceptance in a range of applications. It can frequently be found in physical access con- trol in commercial and residential applications, in time and attendance systems, and in general personal authentication applications. However there is no clear proof that it is unique.
Voice recognition [5] is the identification using the acoustic features of speech that have been found to differ between individuals. This technology is easy to use and it does not require any special training or equipment. Consumers prefer to use voiceprints over other biometric technology for identification according to a chase bank’s research study. However, physical conditions of the voice, such as those due to sickness, affect the voice verification process, also the environment noise reduces the overall accuracy and effectiveness of the recognition.
Signature identification is the analyses of the way a user signs his/her name [11] . The process used by such biometric system to verify a signature is called dynamic signature verification. It is worth noting that signature of a person may change after a long time, like if a user gone through an accident and he cannot use his hand and then he signs after a long time, his sign and pressure points may change.
A palm has wide area and more complicated vascular pattern and contains some differentiating features which can be used for personal identification. This technology relies on comparing the palm vein patterns present in the ventral side and the dorsal side of both hands and fingers. The idea of using palm vein can be summarized as follows: Hemoglobin in the blood is oxygenated in the lungs and carries oxygen to the tissues of the body through the arteries. After it releases its oxygen to the tissues, the deoxidized hemoglobin returns to the heart through the veins. These two types of hemoglobin have different rates of absorbency. Deoxidized hemoglobin absorbs light at a wavelength of rang 750 nm to 940 nm in the near-infrared region. It has been recently attracted the attention of researchers. It is more preferable than the other types of biometrics as it is impossible to steal or counterfeit the patterns and the pattern of the vessels of the hand is fixed and unique with repeatable biometric features. The system consists of a small palm vein scanner (camera or sensor) that is easy and natural to use, fast and highly accurate. Also there is no need of sensor cleaning. The recent researches have been obtained a certain figure of palm vein recognition rates, see for example [12] and [13] . The drawbacks of such technology are the noises in the imaging patterns and impossibility of dimension reducing because of the non-complexity of the models. An obvious proof of correctness of palm vein identification is also required.
3. Palm Vein Authentication Model
Our palm vein authentication system is factually composed of five consolidated components. The first component is a near-infrared camera which is used to capture images and to convert them into digital formats. The second component is a signal processing procedure which develops the palm vein template and performs quality control activities. The third component is a data storage which is responsible for keeping information of registered palm vein templates as encoded feature vectors at which any new captured palm vein can be compared to during matching phase. The forth component is a matching algebraic procedure which compares the new palm vein data to one or more palm vein data kept in database storage. The latter component is a decision process which uses the results obtained from the matching component to produce a system-level decision.
3.1. Near-Infrared Camera
There are various civilian areas in which infrared camera can be exploited such as security systems and warning for a threats’ presence. There are two main types of infrared cameras, see [14] and [15] . The first type is called vision chips and can be used in the visible range. It allows the images preprocessing using smart sensing techniques due to the increase and growth of integrated micro circuits. The other technology is more oriented to specific military uses which fulfills its preprocessing purpose through its special structure and design. The infrared energy [16] is merely a portion of the electromagnetic spectrum which involves radiations from gamma rays, X-rays, ultra violet, a thin region of visible light, infrared, terahertz waves, microwaves, and radio waves. These are all related and differentiated in the wave length. In particular, a near-infrared camera is able to integrate smart sensors in order to accomplish the extraction of signal and perform processing and comprehension of palm vein images.
It is known that each object emits a certain amount of black bodyradiation as a function of its temperature. The higher an object’s temperature, the more infrared radiation is emitted as a black body radiation. A near-infrared camera can reveal this radiation in a way like to the way a customary camera detects the visible light. It can work even in complete darkness because the surrounding light level does not concern. This makes it valuable for rescue operations in undergrounds or smoke-filled buildings. Sensor emanates infrared ray to the persons’ palm which should be placed few centimeters from the sensor. The idea of image capturing is simple and can be summarized as follow: Oxygen reduced blood within the veins absorbs the near-infrared light and then the infrared camera takes a raw image of the palm vein pattern. Then we can precisely identify the structure of the pattern of veins on the palm of the human hand. By using signal processing, the system changes the raw images into palm vein patterns.
3.2. Signal Processing Algorithm
The image is captured, by using a specific near-infrared camera, as an input image and various mathematical operations are applied to this image in order to extract all efficient features. The objective of pre-processing is to improve the image information by suppressing unsought distortions and enhancing some image options. This is extremely important for further processing [17] . The first step in image pre-processing is image cropping. Some unimportant portions of the image can also be removed and, therefore, most interested image region is concentrated. Then the process of noise reduction, which is the method of removing noise from a signal, is initiated. Therefore, in order to enhance the quality of obtained palm vein patterns, different filters are applied on the segmented these patterns such as 2-D Gabor filter [18] which help in preserving high-frequency parts of images and suppresses the noises that exist in vein patterns. Median filter which could reduce salt and pepper noise, see [19] , is also used to eliminate blurs and make the borderline smooth. Moreover, the filtered vein images should also undergo morphological operations to remove the pixels on the boundaries of vein patterns without allowing them to break apart.
In general, there are different image segmentation methods such as region growing method, relaxation method, edge detection method, division and combination method, and threshold method. The dynamic threshold based segmentation process is carried out which subdivides each image into its constituent regions. The palm vein inner layer are extracted according to the specified (or selected) threshold and the segmented palm vein patterns are obtained.
3.3. Data Storage
After the pre-processing and obtaining enhanced and segmented palm vein patterns, we use the local line binary pattern (LLBP) method [20] to generate best bits representations of digitized palm vein templates and consequently extract feature vectors. Therewith, using coset decomposition algorithm, the palm vein feature vectors are encoded (or encrypted) and stored as registered templates (called encoded feature vectors) in the system database.
The palm vein images which have resolutions 480 × 640 pixels are acquired for various users. These images were used to extract palm vein templates as described in the previous section, then encoded using a suitable code (see below) and stored as code words in the system database.
In matching process if the population is considerable, it might take an extended time to explore through the system database. Thus, to improve the performance of matching system, a common strategy can be used. We may divide the database into various bins at which each bin contains only the palm veins of the same class. In each class we put a representative of the most characteristic information in the palm vein images set in order to reduce the matching time and the size of database. When a palm vein is asked to be identified, it is only compared with these in the bin of the same class. However, dividing the system database into many bins does not always improve the matching system performance. Many realistic systems make use of other features to further divide the database into more bins. Other systems attach palm veins with a number of attributes and classify them according to tags.
Then the system is ready to match palm vein images using the coset decomposition algorithm as a modified hamming distance measure.
3.4. Matching Algorithm
The consequence of the matching process between two palm vein feature vectors, having the appearance of being different, could be a decision of either match or no match. Since, the result of the matching is required to be distinctly decision, a reasonable threshold or an acceptable difference level is demanded. Therefore, an algorithmic method is needed to evaluate the overall dissimilarities between two palm veins feature vectors and check whether or not the degree of likeness between two palm vein feature vectors is higher than the threshold. In general, the threshold is usually calibrated according to the desired security level. In this regard, the higher of the threshold standard, the more intricate of the matching process and the easier for the two palm vein data to be accurately considered as match or no match. On the other hand, the lower of the threshold standard the easier of matching process but the harder for the palm vein data to be considered a match or no match.
In this work we use linear coding theory to solve the problems of securely storing and matching of palm vein feature vectors, since, as motioned above, these vectors are stored in binary forms. Solving this problem directs us to inspect low rate large minimum distance error-correcting codes which should accompany with an efficient decoding algorithm up to the required distance. The author syndrome decoding coset decomposition algorithm introduced in [10] will be revisited to present a reliable and secure storing as well as authentication of palm veins.
To introduce coset decomposition method, we initially need to take into account the basic decoding problem. Let  be the group of two elements and let n and k be positive integers with
be the group of two elements and let n and k be positive integers with . We wish to emphasize that the feature vector of a palm vein is given in form of a word of length n as an element of
. We wish to emphasize that the feature vector of a palm vein is given in form of a word of length n as an element of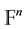 , the direct product of n copies of the group
, the direct product of n copies of the group . As a matter of fact
. As a matter of fact 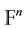 is a commutative group under the addition operation. Now, the weight of a word
is a commutative group under the addition operation. Now, the weight of a word 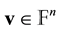 is defined to be the number of nonzero entries in
is defined to be the number of nonzero entries in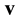 . Moreover, the hamming distance,
. Moreover, the hamming distance, 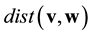 , of
, of 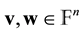 is defined to be the weight of the difference
is defined to be the weight of the difference . Here
. Here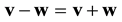 , as all the elements are product of copies of
, as all the elements are product of copies of  in which each element is its own additive inverse. A coding function f is defined by the mapping
in which each element is its own additive inverse. A coding function f is defined by the mapping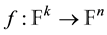 , and instead of retaining a word
, and instead of retaining a word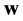 , we store the word
, we store the word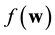 . In this respect, the coding function should be injective; otherwise there would be two distinct words of length k that would be considered as the same word of length n.
. In this respect, the coding function should be injective; otherwise there would be two distinct words of length k that would be considered as the same word of length n.
We say that 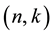 -code is a linear code of a length n and dimension k over
-code is a linear code of a length n and dimension k over 









Let C be an 











In this paper, the preserved palm vein feature vector 


where the first k entries of a codeword 



We define the syndrome of 




Given a feature vector 









Here 



The palm vein authentication problem often deals with large amount of bits; another difficulty is how to cope with the 10% to 20% of expected errors. Therefore, we require an 


Suppose that we have a coding function 



3.5. Decision Process
As discussed above, the feature vectors of palm vein images acquired from the same person are most probably dissimilar, and needs error detection and correction for matching. Therefore, the matching of the preserved (enrolled) palm vein and the inquest palm vein might be modeled as a noisy channel problem. Once an image of a user’s palm vein is scanned, filters act as a directed smoothing process which removes residual random noise. Then, the extracted feature vector is produced by giving out bits at certain specified positions. Next, the proposed matching algorithm measures similarities between the extracted codeword 


The accuracy of any biometric authentication algorithm is measured according to the rates of false acceptance and false rejection. The false acceptance rate (FAR) gives the rate at which someone, other than the actual person is falsely recognized. Thus an unauthorized user is accepted by the system due to erroneous in matching. The false rejection rate (FRR) is how frequently the system fails to match between a palm vein of a person and the same person’s palm vein which is enrolled in the database.
4. Experimental Results
To verify the effectiveness of the algorithm mentioned in section 3, we conducted several experiments using various palm vein images. The algorithm has been implemented in MATLAB and executed on PC with CORE i7 CPU@2.6 GHz, 8G RAM and Windows 8.1 version. Palm vein images (with corrected position and shape) were obtained by a non-contact palm vein sensor that includes an imaging source camera with wavelength of 940 nm. It is worth noting that the sensibility of most security IR cameras falls off between 850 nm and 940 nm. After palm vein image cropping, we transform the normalized image to an 8-bit gray image based on a proposed gray-scale. This is to reduce the complexity of coding problem. By utilizing segmentation process, the extracted feature vector of length m × n × 16, where m × n is the (reduced) size cropped image and 16 is the size of each sub-image, is obtained through extracting LLBP features from each sub-image. Whenever we capture many samples from the same individual, the values of each bit in same location of LLBP codes should be all identical. This is the ideal situation, however, some bits may have different values as a result of considering the interference factors such as displacement and rotation. There are also small gestural differences or changes in the palm vein over the time. As a result of all these negative effects in recognition and matching performance, we use the error detection and correction (coset decomposition) algorithm. Therefore, LDPC is used first to encode binary feature vector and second to measure the similarity between the extracted and enrolled (registered in database) binary codes.
The database from 50 users, with five images per user (with minimum interval of one week per each image), was acquired and used as a basis for the system database. A randomly selected image for each user is used to test the proposed approach. It has found to report higher verification accuracy of 99.8% for FAR and 99.6% for FRR.As expected the identification performance improves as the length of feature vectors increase. The performance of the palm vein authentication algorithm is shown in Figure 1. The carefully chosen partition size is a decisive in attaining higher performance. The selection of small partition size may give much noise and thus the correct prevailing features of palm veins are not represented in the particular region. Figure 2 shows that identification (or recognition) rate is increasing as the result of increasing the partition size.
Figure 1. Performance of the palm vein authentication algorithm.
Figure 2. Identification rates for different partition sizes.
5. Conclusions
Palm vein pattern recognition is an upcoming biometric technology which is easy to train, use, implement and operate. Furthermore, it is a convenient technology with high security and accuracy level. It can be used for personal computers log-in, building entrance and ATM machine. It can also be used as identification verification for medical record management. In spite of the fact that the palm vein authentication is gaining momentum, it is still untested as it has not yet been available for mass production. There are some factors that might affect the quality of the captured images such as user body temperature, ambient temperature, humidity, heat unevenly distribution, heat radiation, camera calibration and focus of camera. In addition, this technology is not applicable to people who lost their palms.
We have developed an algorithm which merges the biometrics and cryptography. Some of biometric matching algorithms analogous to the presented algorithm have been proposed in the literature. Our model which is fit for matching user palm veins is, to the best of my knowledge, entirely new. We can apply the same approach to different biometrics systems, for instance, the iris biometrics. In particular, the iris matching could be easier in terms of high true match rates because of the large amount of information that might be extracted from an iris. A possible extension to the described approach would be, to some outlines, to build a multi-biometrics authentication system.
References
- Sayed, M. and Jradi, F. (2014) Biometrics: Effectiveness and Applications within the Blended Learning Environment. Journal of Computer Engineering and Intelligent Systems (CEIS), 5, 1-8.
- Vacca, J.R. (2007) Biometric Technologies and Verification Systems. Elsevier Science & Technology.
- Teoh, A., Gho, A. and Ngo, D. (2006) Random Multispace Quantization as an Analytic Mechanism for Biohashing of Biometric and Random Identity Inputs. IEEE Transactions on Pattern Analysis and Machine Intelligence, 28, 1892- 1901. http://dx.doi.org/10.1109/TPAMI.2006.250
- Jain, A. and Aggarwal, S. (2012) Multimodal Biometric System: A Survey. International Journal of Applied Science and Advance Technology, 1, 58-63.
- Raina, V.K. and Pandey, U.S. (2011) Biometric and ID Based User Authentication Mechanism Using Smart Cards for Multi-Server Environment. 5th National Conference on Computing for Nation Development, 5BVICAM, New Delhi, 10-11 March 2011.
- Raina, V.K. (2011) Integration of Biometric Authentication Procedure in Customer Oriented Payment System in Trusted Mobile Devices. International Journal of Information Technology Convergence and Services, 1, 15-25. http://dx.doi.org/10.5121/ijitcs.2011.1602
- Tome, P., Vanoni, M. and Marcel, S. (2014) On the Vulnerability of Finger Vein Recognition to Spoofing. IEEE International Conference of the Biometrics Special Interest Group (BIOSIG), Darmstadt, 10-12 September 2014, 1-10.
- Zhou, Y. and Kumar, A. (2011) Human Identification Using Palm-Vein Images. IEEE Transactions on Information Forensics and Security, 6, 1259-1274. http://dx.doi.org/10.1109/TIFS.2011.2158423
- Sutcu, Y., Rane, S., Yedidia, J.S., Draper, S.C. and Vetro, A. (2008) Feature Transformation for a Slepian-Wolf Biometric System Based on Error Correcting Codes. Computer Vision and Pattern Recognition (CVPR) Biometrics Workshop, Anchorage, 1-6.
- Sayed, M. (2015) Coset Decomposition Method for Storing and Decoding Fingerprint Data. Journal of Advanced Computer Science & Technology, 4, 6-11. http://dx.doi.org/10.14419/jacst.v4i1.3958
- Yang, J. (2010) Biometric Verification Techniques Combing with Digital Signature for Multimodal Biometrics Payment Systems. IEEE International Conference on Management of e-Commerce and e-Government, Chengdu, 23-24 October 2010, 405-410. http://dx.doi.org/10.1109/icmecg.2010.88
- Kang, W. and Wu, Q. (2014) Contactless Palm Vein Recognition Using a Mutual Foreground-Based Local Binary Pattern. IEEE Transactions on Information Forensics and Security, 9, 1974-1985. http://dx.doi.org/10.1109/TIFS.2014.2361020
- Yang, G.P., Xi, X.M. and Yin, Y.L. (2012) Finger Vein Recognition Based on a Personalized Best Bit Map. Sensors, 12, 1738-1757. http://dx.doi.org/10.3390/s120201738
- Corsi, C. (2010) History Highlights and Future Trends of Infrared Sensors. Journal of Modern Optics, 57, 1663-1686. http://dx.doi.org/10.1080/09500341003693011
- Corsi, C. (2012) Infrared: A Key Technology for Security Systems. Advances in Optical Technologies, 2012, Article: ID: 838752.
- Rogalski, A. (2003) IR Detectors: Status Trends. Progress in Quantum Electronics, 27, 59-210. http://dx.doi.org/10.1016/S0079-6727(02)00024-1
- Xi, X., Yang, G., Yin, Y. and Meng, X. (2013) Finger Vein Recognition with Personalized Feature Selection. Sensors, 13, 11243-11259. http://dx.doi.org/10.3390/s130911243
- Yang, J.F. and Yang, J.L. (2009) Multi-Channel Gabor Filter Design for Finger-Vein Image Enhancement. Proceedings of the 5th International Conference on Image and Graphics, Xi’an, 20-23 September 2009, 87-91. http://dx.doi.org/10.1109/icig.2009.170
- Yang, J.F. and Yan, M.F. (2010) An Improved Method for Finger-Vein Image Enhancement. Proceedings of the 2010 IEEE 10th International Conference on Signal Processing, Beijing, 24-28 October 2010, 1706-1709. http://dx.doi.org/10.1109/icosp.2010.5656832
- Rosdi, B.A., Shing, C.W. and Suandi, S.A. (2011) Finger Vein Recognition Using Local Line Binary Pattern. Sensors, 11, 11357-11371. http://dx.doi.org/10.3390/s111211357
- Gallager, R. (1962) Low-Density Parity-Check Codes. IEEE Transactions on Information Theory, 8, 21-29.
- Sayed, M. (2011) Coset Decomposition Method for Decoding Linear Codes. International Journal of Algebra, 5, 1395- 1404.
NOTES
*On leave from Faculty of Engineering, Alexandria University, Egypt.




