Journal of Information Security
Vol.4 No.4(2013), Article ID:36799,12 pages DOI:10.4236/jis.2013.44024
Analysis of Malware Families on Android Mobiles: Detection Characteristics Recognizable by Ordinary Phone Users and How to Fix It
1School of Computer Science and Technology, Huazhong University of Science and Technology, Wuhan, China
2Hue University’s College of Education, Hue, Vietnam
Email: Hieudhsphue2002@yahoo.com
Copyright © 2013 Hieu Le Thanh. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Received April 9, 2013; revised May 11, 2013; accepted May 19, 2013
Keywords: Mobile Security; Android Malware Families
ABSTRACT
The sale of products using the android Operation System (OS) phone is increasing in rate: the fact is that its price is cheaper but its configured hardware is higher, users easily buy it and the approach to this product increases the risk of the spread of mobile malware. The understanding of majority of the users of this mobile malware is still limited. While they are growing at a faster speed in the number and level of sophistication, especially their variations have created confusion for users; therefore worrying about the safety of its users is required. In this paper, the author discussed the identification and analysis of malware families on Android Mobiles. The author selected the recognizable characteristics from ordinary users with their families collected from 58 malware families and 1485 malware samples and proposed solutions as recommendations to users before installing it with the ultimate desire to mitigate the damage in the community that is on the android phone, especially the ordinary users with limited understanding about potential hazards. It would be helpful for the ordinary users to identify the mobile malware in order to mitigate the information security risk.
1. Introduction
In recent years, Sales of products using Android phones have continued to accelerate. Specifically in 2012, phones which use the android operating system rose from 52.5% to 72.4% compared to 2011, while the IOS operating system fells from 15% to 13.9% compared to 2011, according to Gartner [1]. Some applications of the android operating system from Android Market are growing to compete with the largest application. Now Apps store is developed by third—party market, not to mention the thousands of everyday applications. According to Xyologic: “Android to overtake Apple soon”, Apple’s App store has now reached 25 billion downloads, Android’s App store has now reached 10 billion downloads, but both tracked at 1 billion downloads a month [2].
This increases the amount of malicious software on the Android operating system. According to security Kaspersky Labs, in the second quarter of 2012 the mobile malware increased in three folds. In 2012, 99% of all the mobile malware they detected every month was designed for Android. The most widespread malicious objects detected on Android smartphones can be divided into three main groups: SMS Trojans, advertising modules and exploits to gain root access to smartphones [3]. Specifically, 40% of modern smartphone owners do not use antivirus software [4].
Whilst malware is growing rapidly, a number of ordinary users that have easy access to the smartphone device do not have basic understanding of the potential danger. So we need to have the classification of samples according to similar characteristics, as well as collect more new malware to create malware families. Then, we can analyze it fully to make recognizable signs from ordinary users and guard solutions to mitigate the threats of the impact and risk of malwares before installing it from official android market or third-party market.
In this paper, the author first discussed the feature to select a sample of malware families and method to analysis them. Next, in Section 2, the author presented methods and tools to analyse malware samples. In section 3, the author presented some selected results of the features that ordinary users can easily recognize. From the analysis on the samples, the author collected the list from the project, blog and threat reports of antivirus companies [5,6] (including existing malware families and add them every day) and the threats that malicious applications can do. Section 4 shows the detection results with ten representatives of mobile phone antivirus software. In Section 5, the author discussed six (6) steps to security android phones. Finally, Section six (6) is the summary.
2. Methods and Tools to Analyze Malware Samples
In this section, the author first discussed the feature to select a sample of malware families and methods to analyses them.
2.1. Malware Family
Malware family feature that comes to notice is that of closeness which certain traits are preserved, including: similar activation, facial features, hereditary diseases and a host of other commonalities.
One of the variations which is most harmful is KungFu malware family. There are variations with different names KungFuA (KungFu1), KungFuB (KungFu2), KungFuC (KungFu3), KungFuD (KungFu4), KungFuE (KungFu Sapp) or KungFu Lena (Legacy Native ) with properties which are analysed as follows:
All KungFu malwares are packaged and downloaded from third markets and fora. It adds into applications a new service and a new receiver. With privilege root exploits, it automatically launches the service so that it doesn’t interact with the user. KungFu can collect information on the infected mobile phone, including IMEI number, phone model, version of Android OS. The first variant, KungFuA exploits Dalvik codes based on Java and a single C&C server and payload is encrypted with AES. Differently, KungFuB exploits native code and three C&C servers. KungFuC inherits from KungFuB, it exploits vulnerability to allow local users to gain privilege by sending a NETLINK message (CVE-2009-1185) [7]. KungFuD inherits from KungFuA and encrypted its native binaries. KungFuE inherits from KungFuD and encrypting a few strings to obfuscate its code and use a custom certificate in official market [8-10]. “DroidKungFu” variants structure mentioned in Figure 1.
Its purpose is to evade the detection of mobile antivirus software. So the virus software is difficult to effectively detect variants with a rate of 100%.
2.2. Methods and Tools to Analyze Android Mobile Malware Sample
Common method for analysing malware in android OS is reverse engineering. Reverse engineering is the process of discovering the technological principles of a device, object, or system through analysis of its structure, function, and operation [10]. Android OS was developed by Google and is based upon the Linux kernel and GNU software in which the malware application package files use the apk extension. They include all of the application’s code (.dex files), resources, assets, and manifest file. Dex file (Dalvik Executable) is compiled Android application code file. Tools that focus three groups on examining inner-workings of Android mobile applications:
1) Command line:
• Tool to unpack the .apk file: Winzip, Rar
• Tool to get the bytecode from the .dex file: for example, smali to compile and baksmali to decompile (or dex2jar and jd-gui), dexdump…
The author analysed a sample (RU .apk) below:
Step 1: The malware is an apk package extract of its content, show example Figure 2.
Step 2: Use smali .rar to compile smali file: extracted the byte code from classes .dex file, show example Figure 3.
Step 3: Open code contained in the MoviePlayer.smali file. You can discover the purpose of it, show example Figure 4.
2) Software to compile and decompile:
• Compile: Java code, smalicode and .dex: for example APKtoJava.
We analysed a sample (RU .apk) below:
Step 1: open APKtoJava (show Figure 5).
Step 2: open class java to read program file (show example Figure 6).
3) Using website: for example http://anubis.iseclab.org He analysed a sample (RU .apk) below:
Choose file apk website to analyse, show example Figure 7.
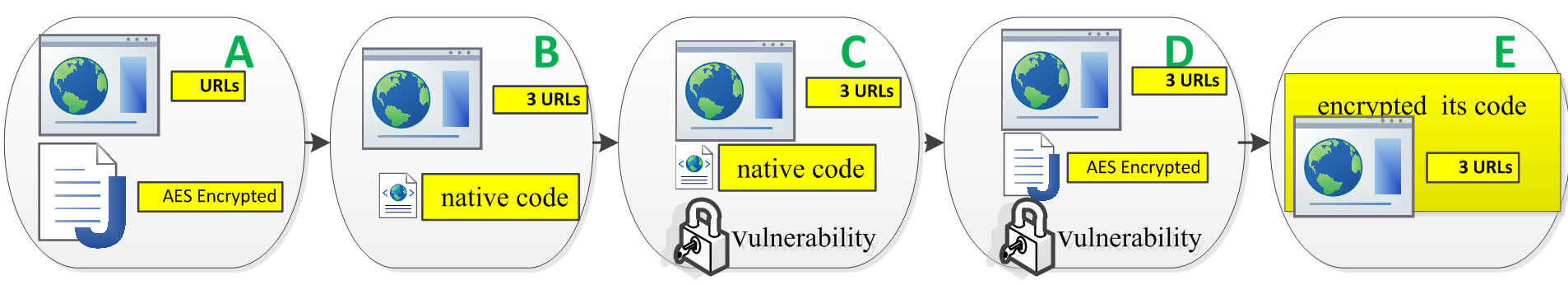
Figure 1. “DroidKungFu” variants structure.
Figure 2. Classes is dex file to analyze.
Figure 3. Movie player. Smali is main code of malware.
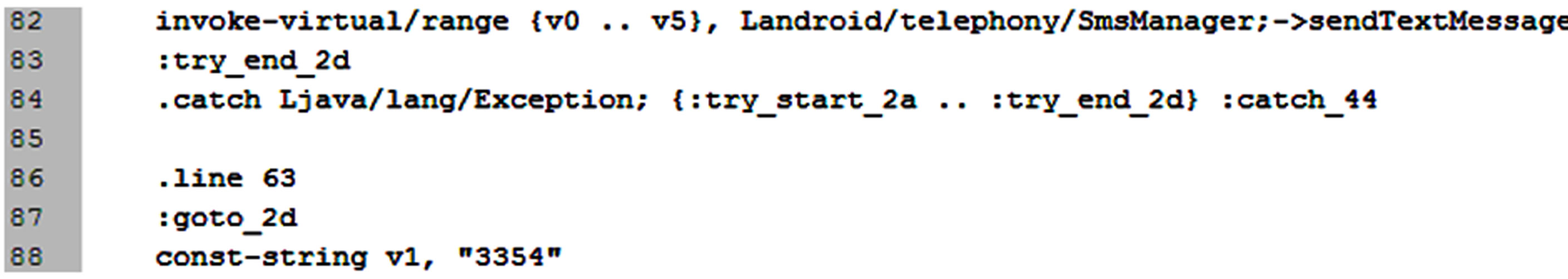
Figure 4. Malware send a message to phone number 3354.
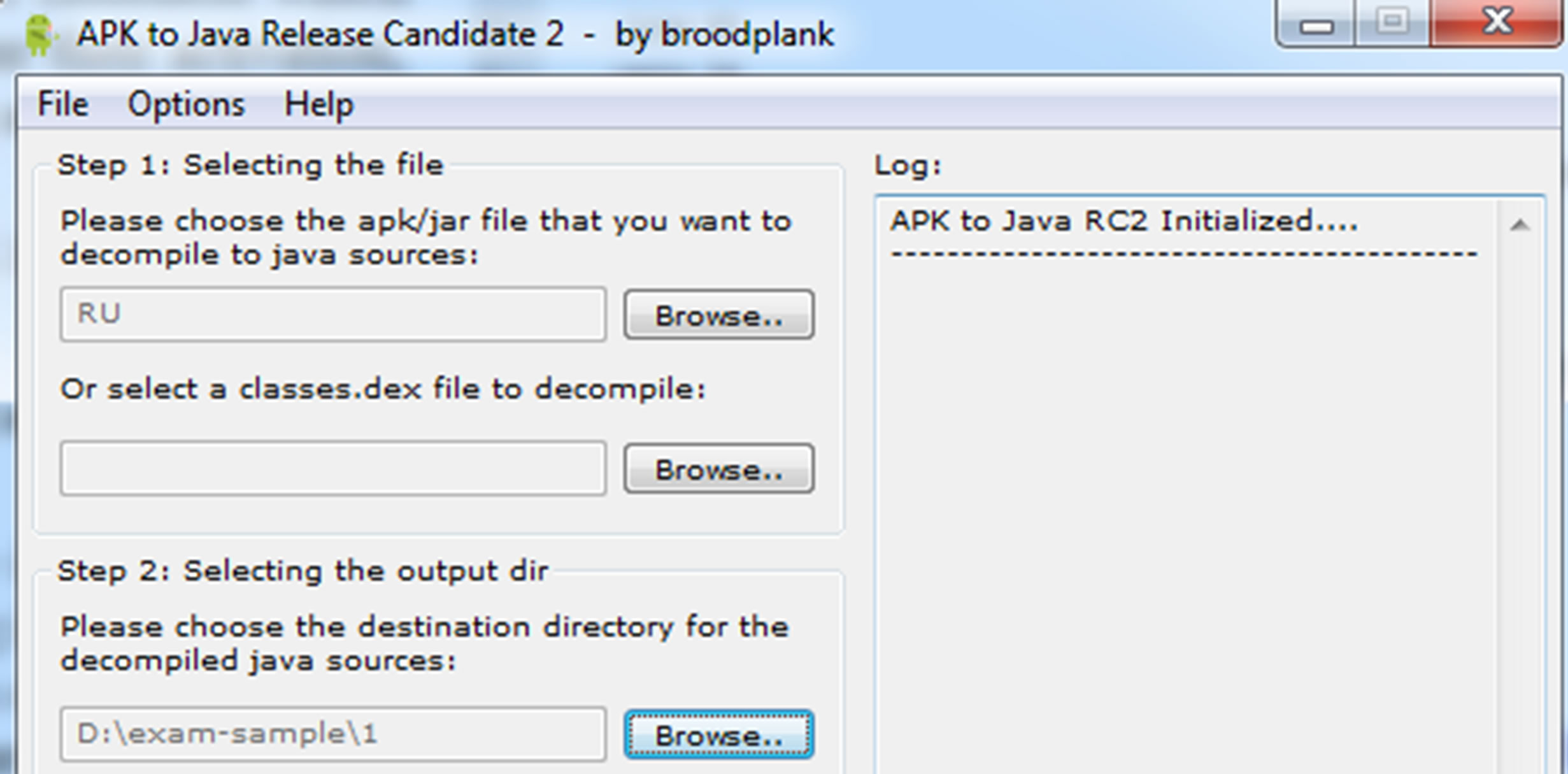
Figure 5. Screen of APK tool to decompile to java sources.
Figure 6. A Class java sources after decompile by APK tool.
Figure 7. An analysis result for file RU .apk from website.
3. Results of the Features That Ordinary Users Easily Recognize
In the process of analysing the samples the author collected, the author had encountered difficulties with different names of the first authors found it. So his statistics record all the different names for easy sorting into their malware families. In addition to describing the visible symptoms, the author used illustrations or icons in Table 1.
Besides, Symptoms of malware which exploits the device to gain root privilege are not easily visible. So we propose to use mobile Security software solutions in the next chapter, with some assessment test results with our samples set.
Statistical results below with reference from the first detection of the authors in manufacturer’s anti—virus software: Symantec, NQMobile, F-secure, Lookout, Kaspersky, AVG, … and projects related links, Blog: http://www.csc.ncsu.edu/faculty/jiang, http://www.fortiguard.com,http://androguard.blogspot.com, http://blog.fortinet.com/... [10-52].
In the first column of Table 4, the author collected the different names of the same malware families [5,52] by different anti-virus companies, based on installation methods, activation mechanisms or the name of the mali-
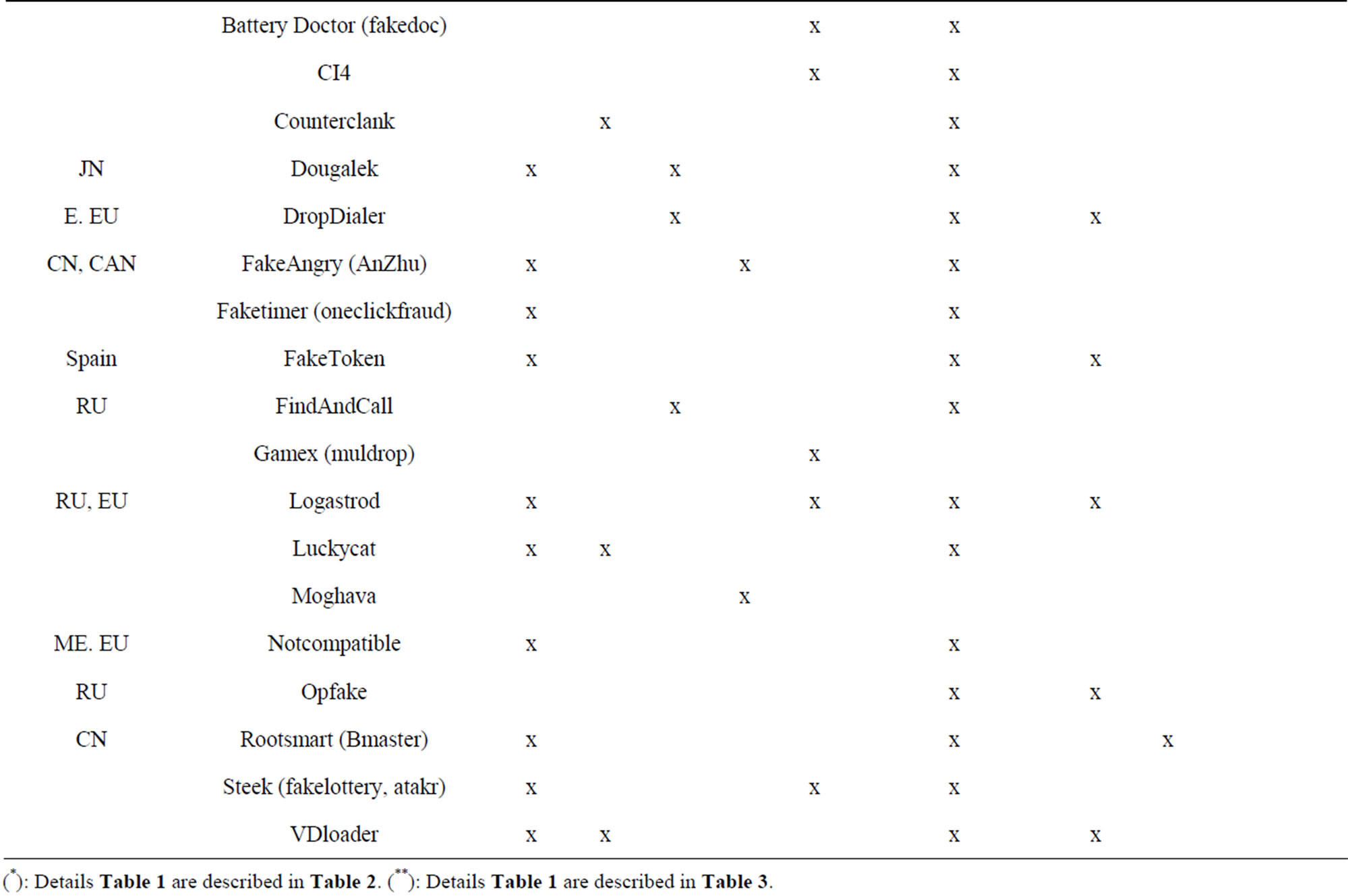
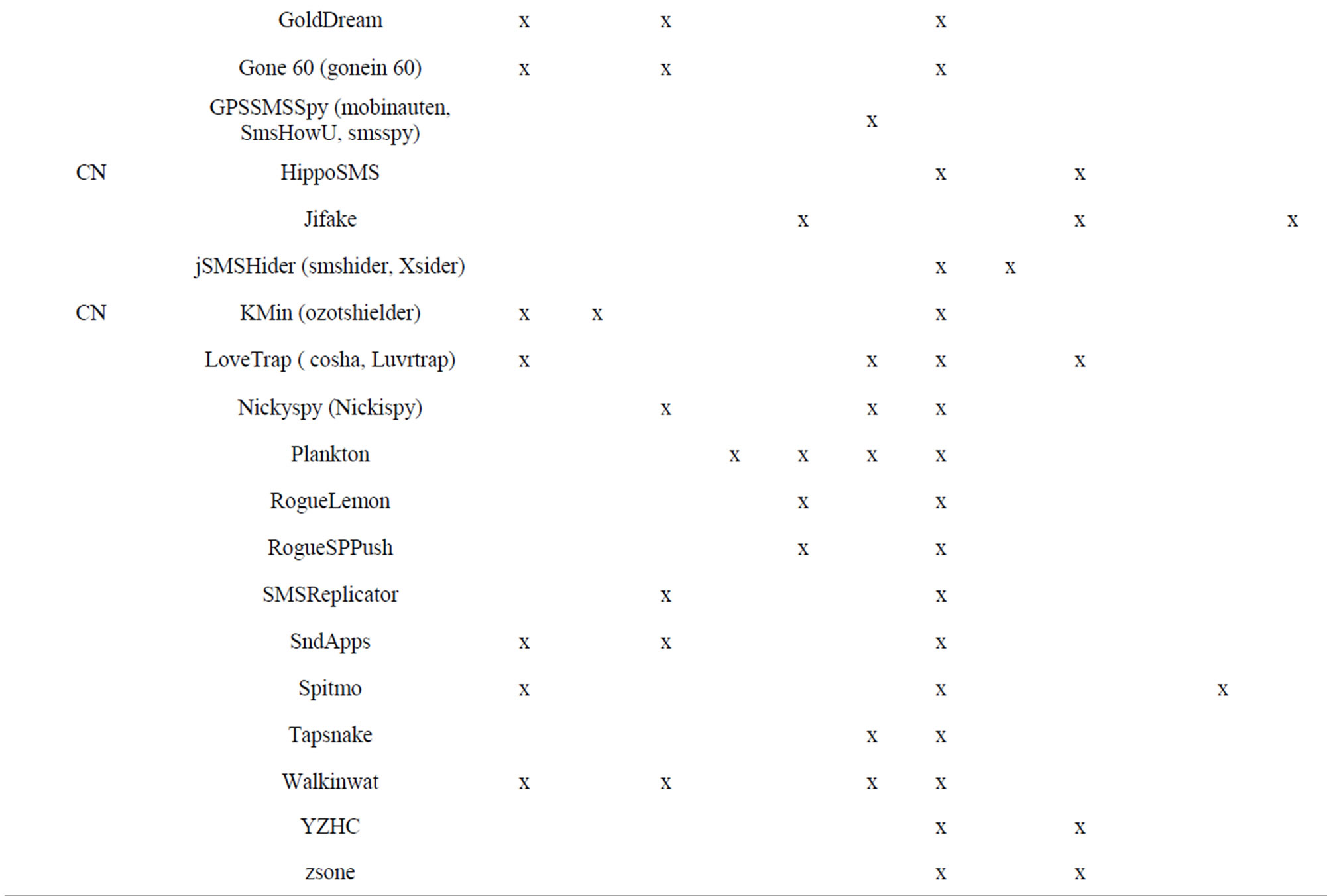
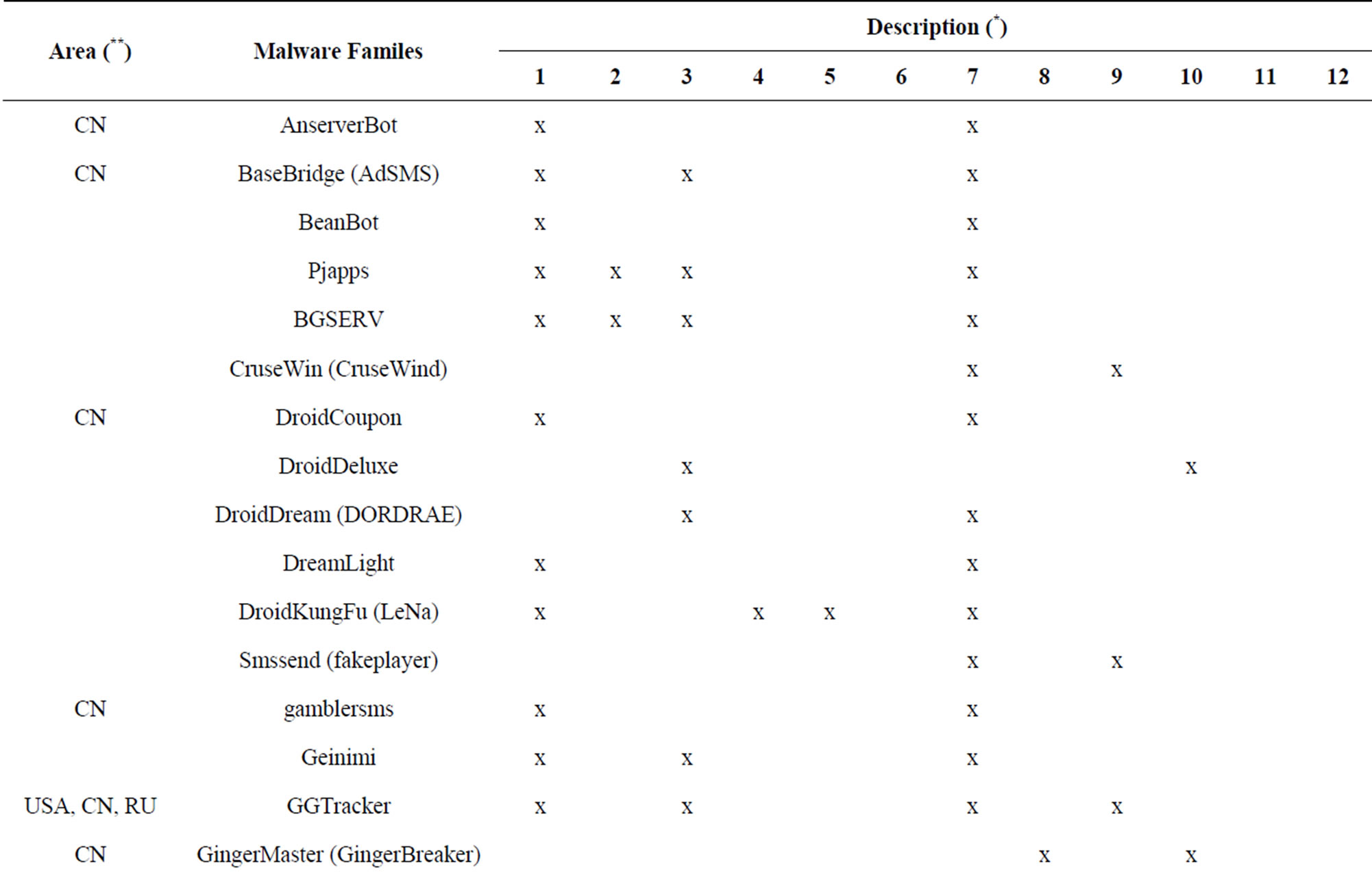
Table 1. Describes characterization and area of the effects of malware families.
(*): Details Table 1 are described in Table 2. (**): Details Table 1 are described in Table 3.
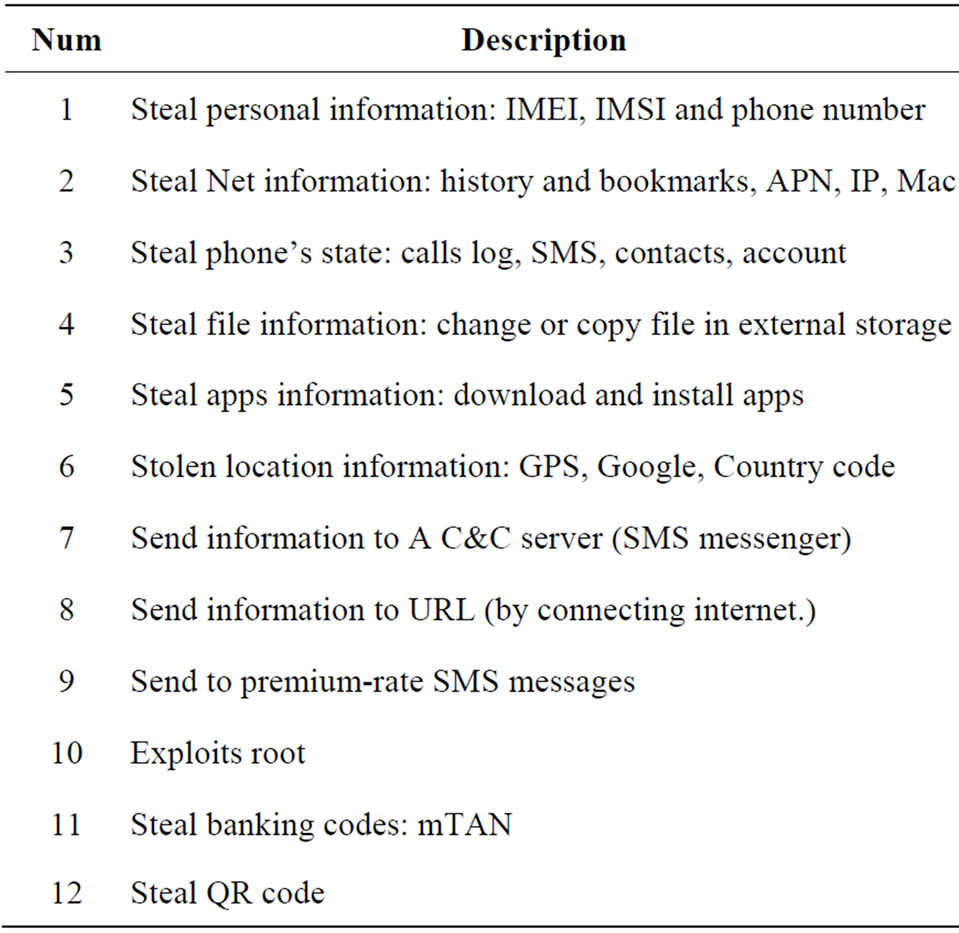
Table 2. Gives detailed explanation of stolen information activities of malware.
cious packaged applications added. This solved problem of naming schemes of malware families such as [5]: “Last but not least, during the process of collecting malware samples into our current dataset, we felt confusions
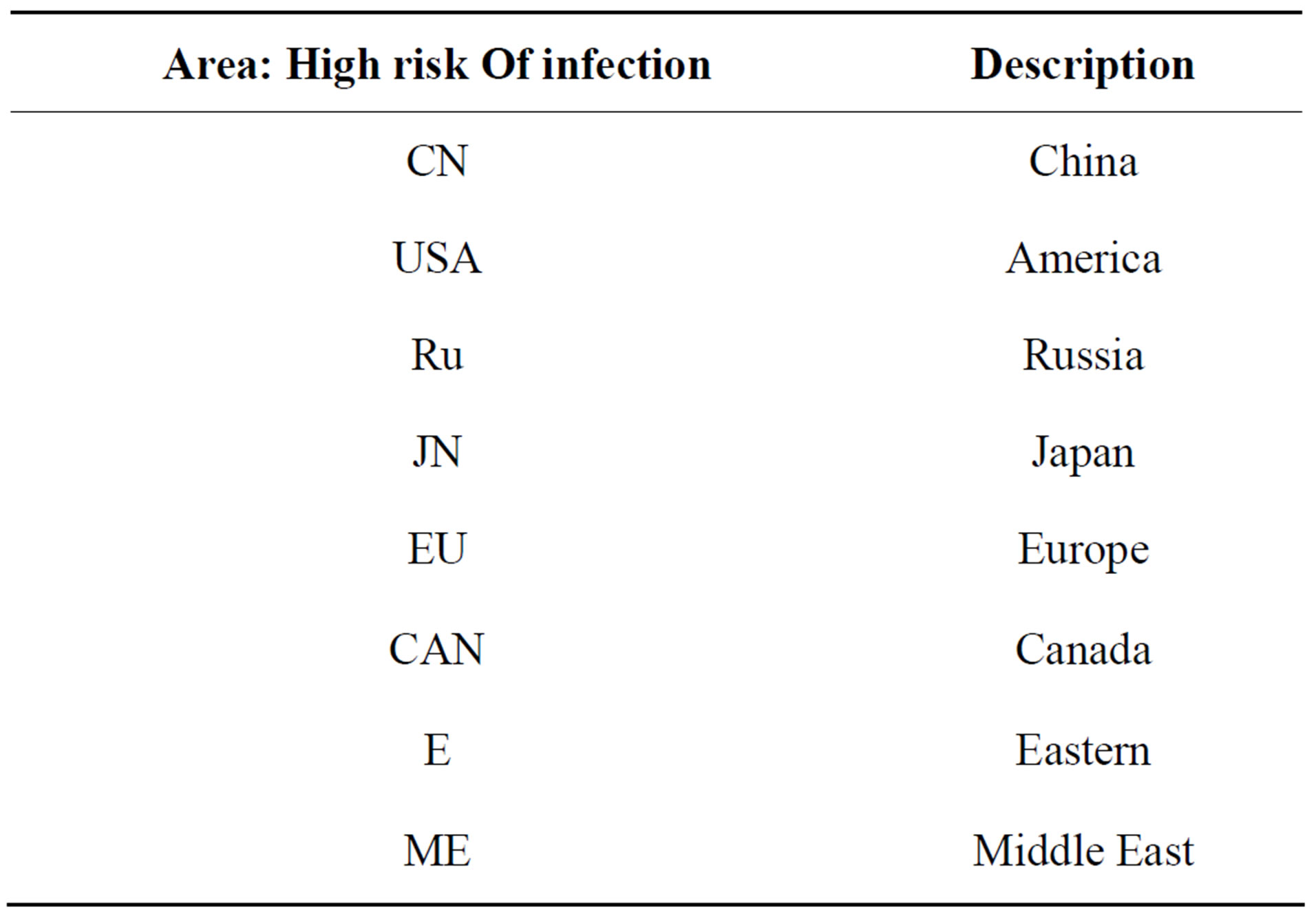
Table 3. Abbreviated name of areas.
from disorganized or confusing naming schemes”.
From visible symptoms malware families in Table 5, the author proposes some specific criterion for identifying the mobile malware:
Ordinary phone users can recognize several features such as: premium-rate services and phone bill abnormal increase, display of a black screen, automatically install a software in which its users has not requested, or without a launcher icon after installation in applications list, warning requirements application not licensed and crack




Table 4. Description about visible symptoms of malware.
them, …
However, malicious software is not a software bug so when installing or running the software, you should consider bug occurrence with above several features.
4. Detection Results of Malware Families
The author installed four mobile security software from Lenovo Store on a Lenovo phone P70 (version 2.3.5) to
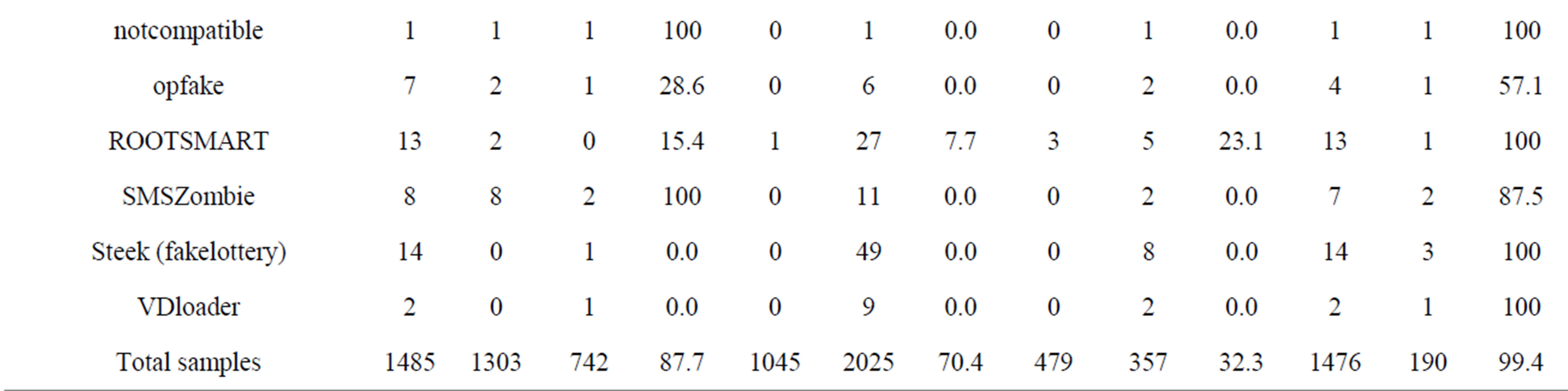
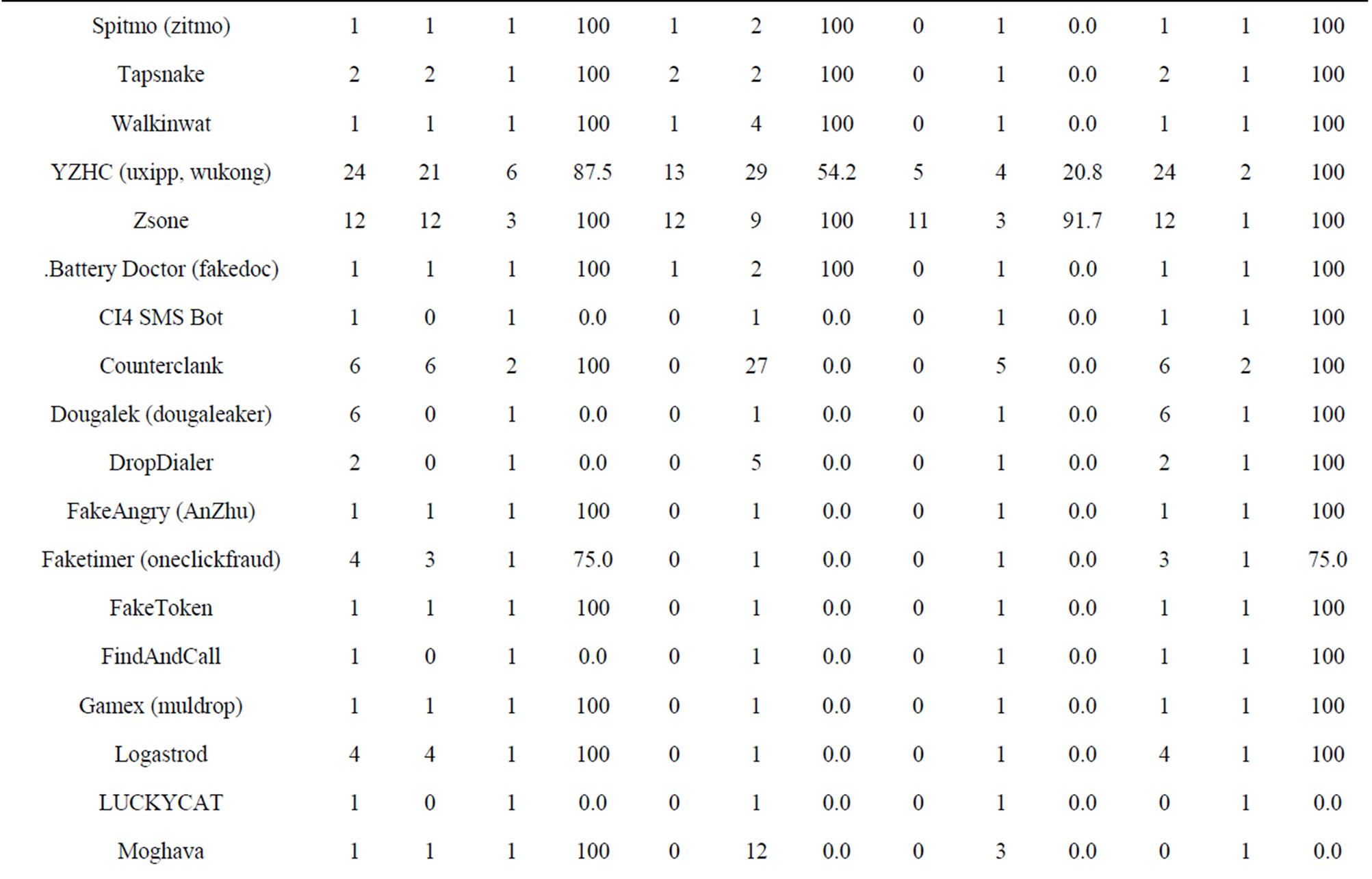
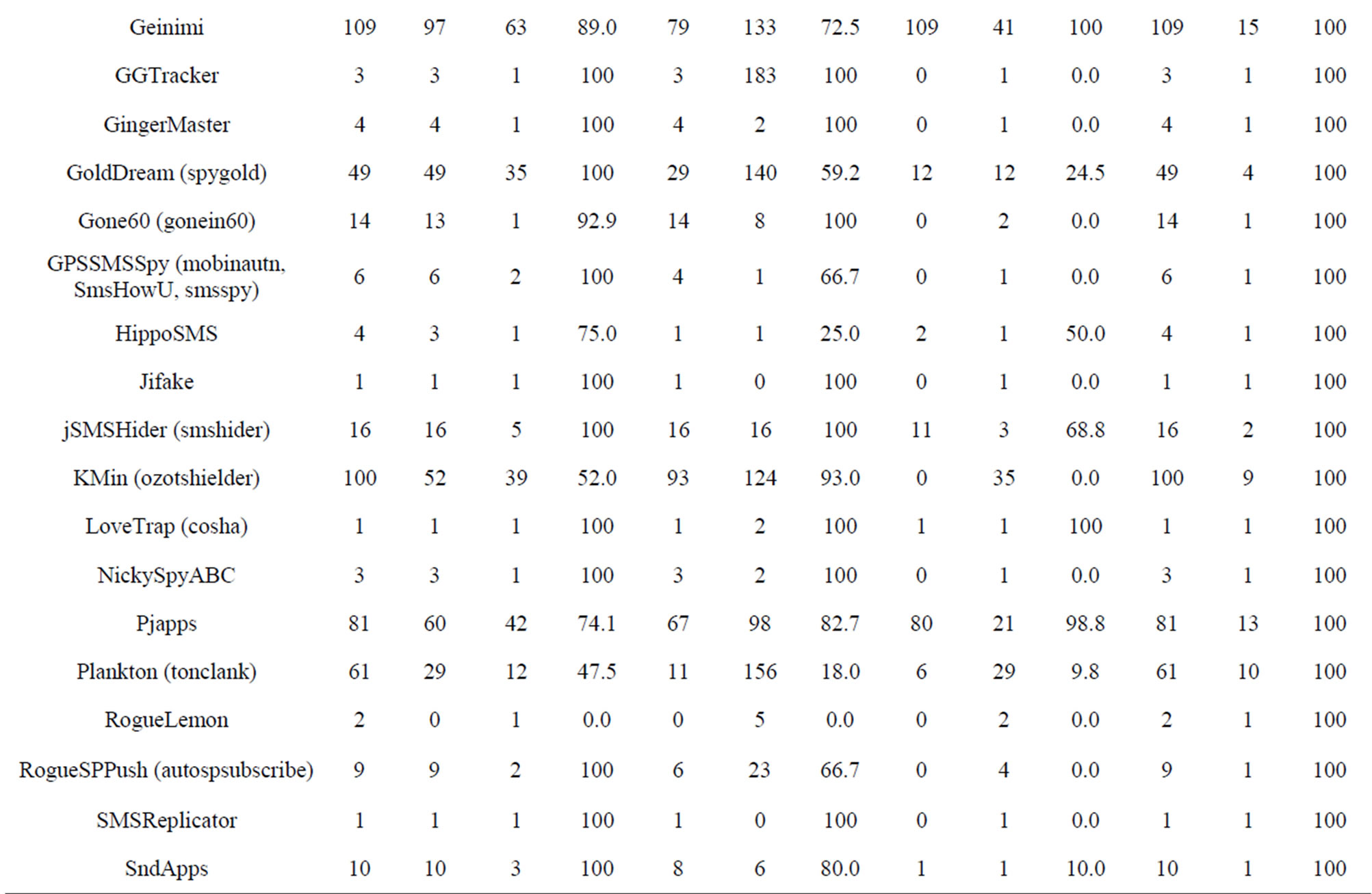
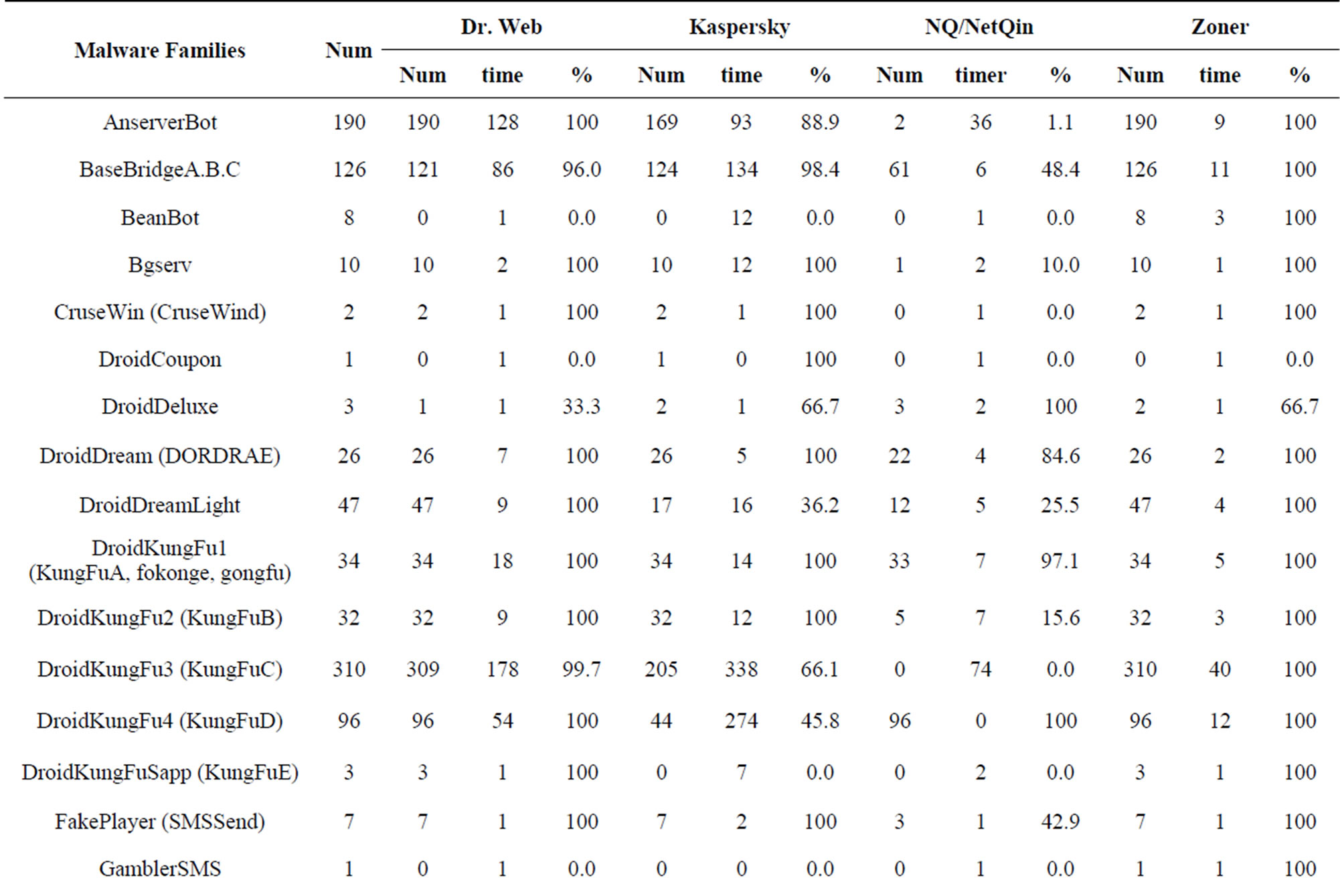
Table 5. Detection results from top anti-virus software 2012.
assess the effectiveness test on the same configuration and the same phone, the same samples set. (Dr. Web Anti-virus v7.00.3 (Dr. Web), Kaspersky Mobile Security. 9.10.139 (Kaspersky), NQmobile antivirus v5.2 (NQ or NetQin) and Zoner Mobile Security v1.0.0 (Zoner).
From the testing results, we are shown that some software like Zoner detection rate to 99.4% (Tables 5 and 6, Figure 8).
5. Discussion
From the analysis of malware families and samples, the author saw that the ability to detect malware from the users is usually limited. The rapid development of new applications and variations to immune with mobile security software requires overall solution from the analysis of new variants and detect new viruses to alert the com-
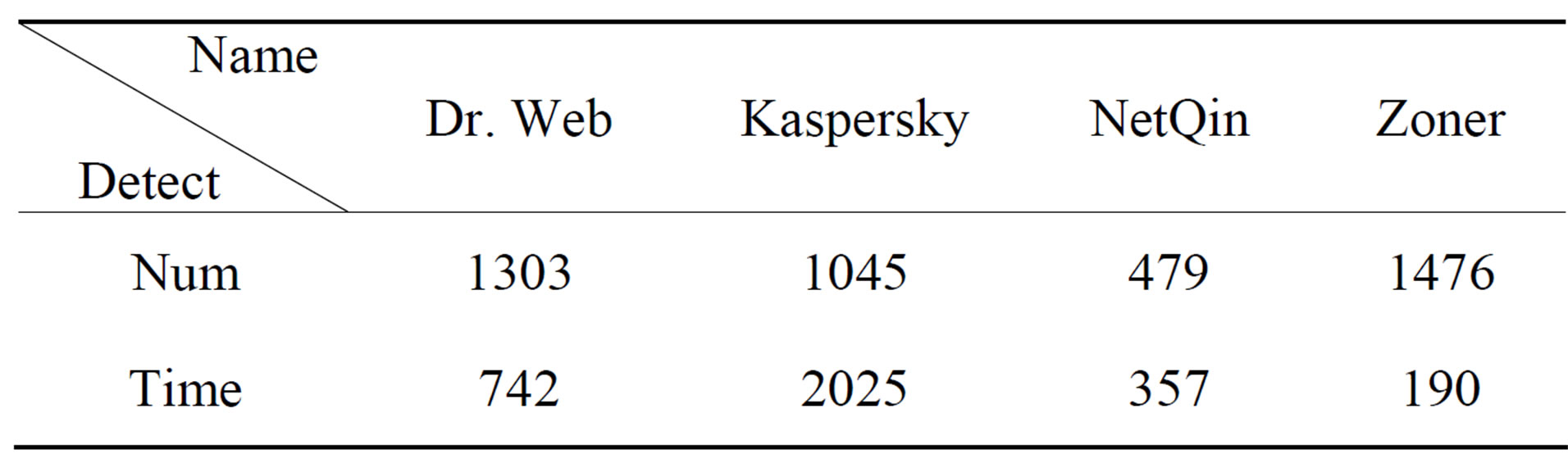
Table 6. Result detect malware families (total).
munity, and then users should also take preventive measures:
1) Users carefully read and understand permissions, an application and compare it with the real features of this app. In particular, users should not install or update software not necessary for the unknown effects of this app.
2) When an app is installed, users should check that the extraordinary can happen: no icon appears corresponding with this app (without, more one icon), Check
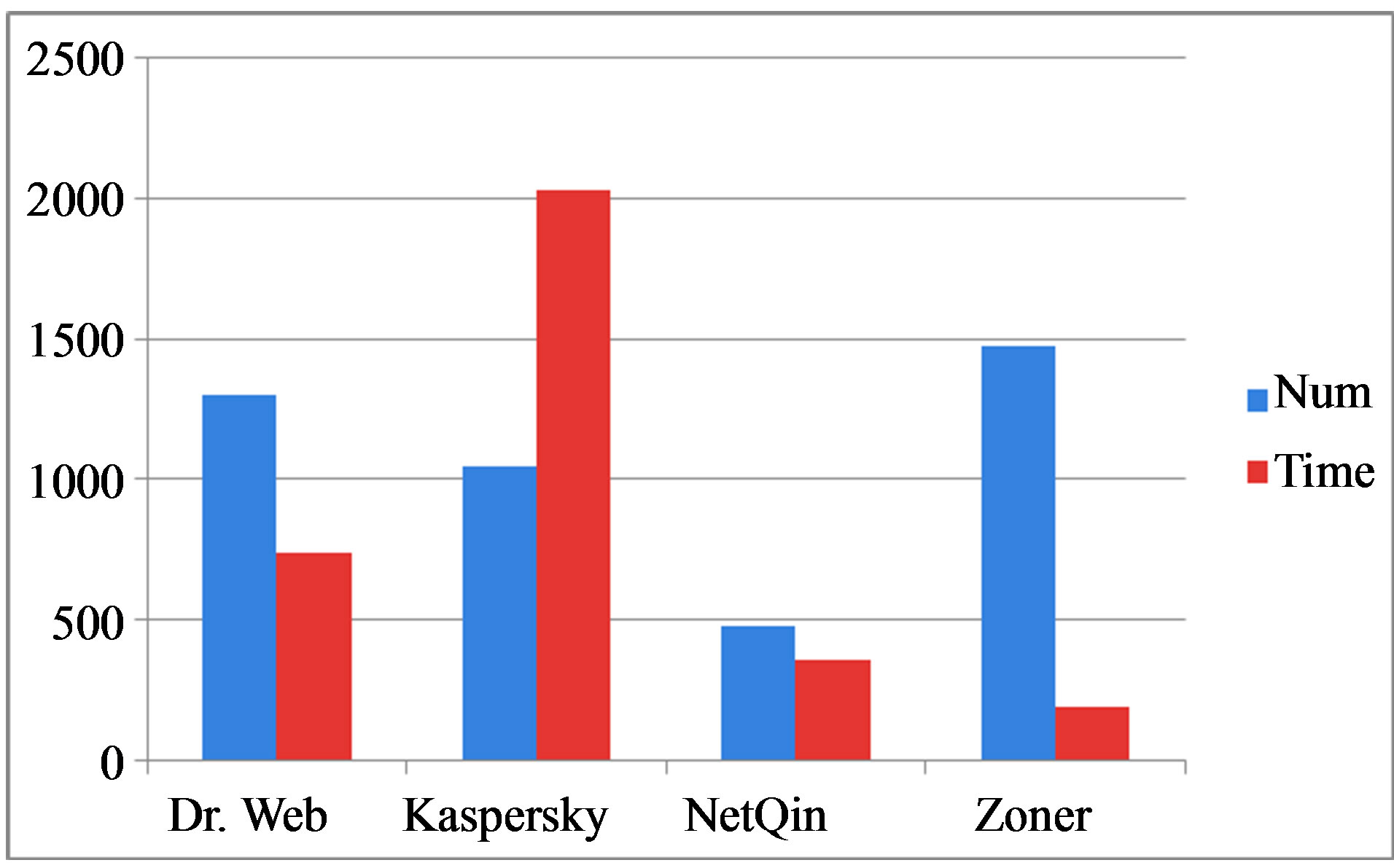
Figure 8. Result detect malware families (Chart).
regularly phone bill or account.
3) Users should invest a mobile security software copyright and install all apps from the official Android Market instead of third—party market.
4) Users should download an app with thousands of downloads and mostly positive comments.
5) Turn off unused features such as: GPS, GPRS, WIFI (Settings > Wireless & networks > Wi-Fi), extend memory (Settings -> Applications -> Development -> USB debugging), .… Especially, Android OS allows users to install file. APK in unknown sources directly and the malware easily penetrate the user’s phone. (Settings -> Applications -> unknown sources).
6) Keep your phone patched up to date.
6. Conclusions
From the analysis of the characteristics of the collected malware samples, the author classified them into their existing families or their addition of a new family for their collection with 58 malware families and 1485 malware samples. And the author introduced three different techniques to analyze the sample introduced in Section 1.
The author selected the recognizable characteristics from ordinary users with their families that had collected (Table 1), and proposed solutions as recommendations to users before installing it with the ultimate desire to mitigate the damage in the community that is on the android phone, especially the ordinary users with limited understanding about potential hazards. The visible Symptoms of malware which exploit the device to gain root privilege are difficult to see and detect because they silently execute malicious code in the platform OS. Mostly, they steal information and send to remote server or URL by SMS messages (premium rate number or not).
The author presented evaluation results of the test 04 mobile security software of top ten software from AVTEST in 2012 [51] with each family in order for the users to have the appropriate choice to proceed with fixing them and prevent them in the future, especially with malwares using root exploits when detecting the infection.
Beside, ordinary phone users recognize malwares by visible symptoms in order to fix it (Table 4) and they are careful when downloading and installing apps from official Android Market with security advisories (Section 5). If users are really concerned with the potential risks, they should consider investing in an effective mobile security app because it is still the best bet to stay protected anywhere, anytime. Also, when we are installing software of unknown source, the phones are also infected with malicious software before it can protect the phones.
REFERENCES
- UK, “Worldwide Mobile Device Sales to End Users by Operating System in third Quarter of 2012,”2012. http://www.gartner.com/it/page.jsp?id=2237315
- R. Thurner, “A Breakdown by Country of the Most Popular App Download Services to Help Make the Business Case,” 2012. http://www.smartinsights.com/mobile-marketing/app-marketing/app-download-statistics/
- Kaspersky Lab, “The overall statistics for 2012,” 2012. http://www.securelist.com/en/analysis/204792255/Kaspersky_Security_Bulletin_2012_The_overall_statistics_for_2012#1
- “Number of the Week: 40% of Modern Smartphones Owners Do Not Use Antivirus Software,” 2012. http://www.kaspersky.com/about/news/ press/2012/number-of-the-week-40-percent-of-modern-smartphones-owners-do-not-use-antivirus-software
- Y. J. Zhou and X. X. Jiang, “Dissecting Android Malware: Characterization and Evolution,” Proceedings of the 33rd IEEE Symposium on Security and Privacy (Oakland 2012), San Francisco, 20-23 May 2012, pp. 95-109.
- Contagio Mobile, “Download Malware Categories”. http://contagiominidump.blogspot.com/
- US-CERT/NIST, “Vulnerability Summary for CVE-2009- 1185,” 2009. http://web.nvd.nist.gov/view/vuln/detail? vulnId= CVE-2009-1185
- X. X. Jiang, “Security Alert: New Sophisticated Android Malware DroidKungFu Found in Alternative Chinese App Markets,” 2011. http://www.cs.ncsu.edu/faculty/jiang/DroidKungFu/
- X. X. Jiang, “Security Alert: New DroidKungFu Variants Found in Alternative Chinese Android Markets,” 2011. http://www.cs.ncsu.edu/faculty/jiang/DroidKungFu2/
- X. X. Jiang, “Security Alert: New DroidKungFu Variant AGAIN! Found in Alternative Android Markets,” 2011. http://www.csc.ncsu.edu/faculty/jiang/Droid KungFu3/
- Wikipedia, “Reverse_Engineering”. http://en.wikipedia.org/wiki/ Reverse_engineering
- X. X. Jiang, “Security Alert: AnserverBot, New Sophisticated Android Bot Found in Alternative Android Markets,” 2011. http://www.csc.ncsu.edu/faculty/jiang/AnserverBot/
- Symantec, “Android.Basebridge,” 2011. http://www.symantec.com/ security_response/writeup.jsp?docid=2011-060915-4938-99 &tabid=2
- X. X. Jiang, “Security Alert: New BeanBot SMS Trojan Discovered,” 2011. http://www.csc.ncsu.edu/faculty/ jiang/BeanBot/
- Trendmicro, “ANDROIDOS_BGSERV.A,” 2011. http://about-threats. trendmicro.com/us/malware/AndroidOS_BGSERV.A
- Symantec, “Android.Pjapps,” 2011. http://www.symantec.com/securit yresponse/writeup.jsp?docid=2011-022303-3344-99&tabid=2
- M. Balanza, “Android Malware Acts as an SMS Relay,” Trend Labs, 2011. http://blog.trendmicro.com/trendlabs-security-intellige nce /android-malware-acts-as-an-sms-relay/
- NQMobile, “DroidCoupon”. http://labs.netqin.com/us/?p=112
- Kindsight Lab, Malware Analysis Report, “AndroidOS/ DroidDeluxe,” 2011. https://www.kindsight.net/ sites/default/files/Kindsight_Malware_Analysis-Android-Trojan-DroidDeluxe-final.pdf
- Lookout, “Technical Analysis DroidDream Malware,” 2011. https:// blog.lookout.com/droiddream/
- Trendmicro, “ANDROIDOS_DORDRAE.N,” 2011. http://aboutthreats.trendmicro.com/us/malware/ANDROIDOS_DORDRAE.N
- AVGbobilation, “Malware Information: DroidDreamLight,” 2011. http://cms.avg-hrd.appspot.com/securitycenter/securitypost_20110601.html
- X. X. Jiang, “Security Alert: New Sophisticated Android Malware Droid KungFu Found in Alternative Chinese App Markets,” 2011. http://www.cs.ncsu.edu/faculty/jiang/DroidKung Fu/
- X. X. Jiang, “Security Alert: Be Cautious with Android Spyware—GamblerSMS,” 2011. http://www.cs.ncsu.edu/ faculty/jiang/GamblerSMS/
- Symantec, “Android.Ggtracker,” 2011. http://www.symantec.com/ security_response/writeup.jsp?docid=2011-062208-5013-99&tabid= 2
- Symantec, “Android.Geinimi,” 2011. http://www.symantec.com/ security_response/writeup.jsp?docid=2011-010111-5403-99&tabid=-9
- AVGbobilation, “Malware information: GingerMaster”. http://cms.avg-hrd.appspot.com/securitycenter/securitypost_20110825.html#tabs-2
- Symantec, “Android.Golddream,” 2011. http://www.symantec.com/ security_response/writeup.jsp?docid=2011-070608-4139-99& tabid=2
- AVGbobilation, “Malware Information: Gone60,” 2011. http://cms.avg-hrd.appspot.com/securitycenter/securitypost_20110927.html#tabs-2
- Y. Takash, “Beta Version of Spytool App for Android Steals SMS Messages,” i, TrenLabs, 2012. http://blog.trend micro.com/trendlabs-security-intelligence/beta-version-of-spytool-app-for-android-steals-sms-messages/
- A. Apvrille, “QR Code and Mobile Malware: It Happened!” FortiBlog, 2011. http://blog.fortinet.com/qr-code-and-mobilemalware-it-happened/
- Mcafee, “Virus Profile: Android/J.SMSHider.A,” 2011. http://home. mcafee.com/VirusInfo/VirusProfile.aspx?key=527859#none
- Symantec, “LoveTrap” 2011. http://www.symantec.com/security_res ponse/writeup.jsp?docid=2011-072806-2905-99&tabid=2
- Symantec, “Android.Ozotshielder,” 2011. http://www.symantec.com /security_response/writeup.jsp?docid=2011-091505-3230-99
- AVGbobilation, “Malware Information: NickiSpy”. http://cms.avg-hrd.appspot.com/securitycenter/securitypost_20110804.htm#tabs-2
- M. Ballano, “Android Threats Getting Steamy,” 2011. http://www.symantec.com/connect/blogs/android-threats-getting-steamy
- X. Jiang, “Security Alert: New Stealthy Android Spyware— Plankton—Found in Official Android Market,” 2011. http://www.csc.ncsu.edu/faculty/jiang/Plankton/
- X. Jiang, “Security Alert: New Rogue App RogueLemon Found in Alternative Chinese Android Markets,” 2011. http://www.csc.ncsu.edu/faculty/jiang/RogueLemon/
- X. Jiang, “New Rogue Android App—Ro-gueSPPush— Found in Alternative Android Markets,” 2011 http://www.cs.ncsu.edu/faculty/jiang/RogueSPPush/
- Zimry, Irene, Raulf and Leong-F-Secure, “On Android threats Spyware: Android/SndApps.A and Trojan: Android/SmsSpy.D,” 2011. http://www.f-secure.com/weblog/archives/00002202.html
- Forensic Blog, “Detailed Analysis of Android.Spitmo,” 2011, http://forensics.spreitzenbarth.de/2011/12/06/detailed-analysis-of-android-spitmo/
- Symantec, “Walkinwat,” 2011. http://www.symantec.com/security_response/writeup.jsp?docid=2011-033008-4831-99&tabid=2
- Symantec, “Tapsnake,” 2010. http://www.symantec.com/security_response/writeup.jsp?docid=2010-081214-2657-99
- T. Strazzere, “Security Alert: Zsone Trojan Found in Android Market,” 2011. https://blog.lookout.com/blog/2011/05/11/security-alert-zsone-trojan-found-in-android-market
- Symantec, “Android.Counterclank,” 2012. http://www.symantec.com/security_response/writeup.jsp?docid=2012-012709-4046-99&tabid=2
- Symantec, “Android.Dougalek,” 2012. http://www.symantec.com/security_response/writeup.jsp?docid=2012-041601-3400-99
- L. Arsene, “Android SMS Bot Uses Twitter to Hide C&C Server,” 2012. http://www.hotforsecurity.com/blog/android-sms-bot-uses-twitter-to-hide-cc-server-2602.html
- I. Asrar, “Android.Dropdialer Identified on Google Play,” 2012. http://www.symantec.com/connect/blogs/androiddrodialer-identified-google-play
- B. Botezatu, “From China with Love: New Android Backdoor Spreading through Hacked Apps,” 2012. http://www.hotforsecurity.com/blog/from-china-with-love-new-android-backdoor-spreading-through-hacked-apps-1317.html
- I. Asrar, “Scam Proves Privacy Concerns on Mobile Devices,” 2012. http://www.symantec.com/connect/blogs/scam-proves-privacy-concerns-mobile-devices-0
- AV-TEST, “Test Report: Anti-Malware solutions for Android,” 2012. http://www.av-test.org/en/tests/mobile-devices/android/
- Open Source Database of Android Malware (links + signatures), 2012 https://code.google.com/p/androguard/wiki/DatabaseAndroMawares#Open_Source_database_of_android_malwares

