Journal of Computer and Communications
Vol.04 No.11(2016), Article ID:70940,10 pages
10.4236/jcc.2016.411004
History-Based Backoff Algorithms for Mobile Ad Hoc Networks
Saher Manaseer, Fatima Badwan
Department of Computer Science, King Abdullah II School for Information Technology, The University of Jordan, Amman, Jordan

Copyright © 2016 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY 4.0).
http://creativecommons.org/licenses/by/4.0/



Received: March 3, 2016; Accepted: September 25, 201; Published: September28, 2016
ABSTRACT
Mobile Ad hoc Network (MANET) is a wireless network consisting of mobile devices (laptops, smart phones, etc.) that move and communicate with each other without the use of any existing network infrastructure or centralized server to avoid collisions which have negative effects on the performance of the network. Access to the shared media is controlled by a Backoff algorithm that is a part of the Media Access Protocol. In this paper, we improve the History Based Probabilistic Backoff (HPPB) algorithm by modifying the increment/decrement behavior of the Contention Window to introduce History Based Increment Backoff (HBIB) algorithm which outperforms HBPB in terms of throughput and end-to-end delay with various numbers of nodes and different traffic loads.
Keywords:
Media Access Protocol, Backoff, Mobile Ad Hoc Networks

1. Introduction
A Mobile Ad hoc Network (MANET) is a wireless network in which nodes communicate without a central base station [1] . Nodes in MANET can be routers, senders and receivers. Moreover, these nodes have different abilities and uses, they also have to find other nodes inside the transmission range to form a network because there are no control dedicated units to manage this connection, and this pattern decreases the cost and the complexity of the MANET [1] . The absence of infrastructure design plays a major role in the wide use of MANET networks in our life [2] . There is no need for a complex base station installation or a wiring design for MANETs which are self-building and self-managing [3] , and depend on Backoff algorithm to control the collisions on the shared media. In this work, we introduce a modification on a HBPB algorithm by using absolute value of (β) in the CW computation; β here represents order of collision and successful transmission in the network. MANET can be used in many useful applications that vary from military communication and commercial environments, to education and home networking [2] .
2. Related Work
Many improved backoff algorithms have been proposed in the literature. Mainly these improvements can be classified into two groups. The first, called BEB-like algorithms and the second group modify the CW size according to some computations made by the station depending on some information collected from its neighborhood [4] .
2.1. BEB-Like Algorithms
This category includes backoff algorithms that have the same basic functionality as BEB, which means that directly after a successful transmission, the CW is decreased, and after a collision, the CW is increased. [5] has proposed the Sensing Backoff Algorithm (SBA), in which nodes overhearing a successful transmission reduce its backoff window by a factor, not only the successful nodes. In MILD algorithm [6] a collided node increases its backoff interval by multiplying it by 1.5. A successful node decreases its backoff interval by one step, and migrate the backoff interval to the nodes overhearing a successful transmission through the nodes in the network which reduce the overall throughput of the network.
In [7] the authors proposed Exponential Increase Exponential Decrease (EIED) backoff algorithm in which the CW changed as follows: CW = min[RI*CW, CWmax] on a collision, CW = max[CW/RD, CWmin] on a success, where RI and RD > 0, here RI, RD calculated using the collision experience of the station, A linear increase/linear decrease (LILD) CW algorithm is proposed in [8] In this algorithm, upon a collision, the current CW is increased by a constant value ω. Upon receiving an ACK, it is decreased by ω with probability 1 − δ and unchanged with probability δ. The parameters ω and δ are set experimentally to constant values, LILD perform better than EIED in large network size, but EIED algorithm is more fit than LILD in fast variation of network load.
In [9] , the authors suggested the Pessimistic Linear Exponential Backoff (PLEB) Algorithm which is a mixture between linear and exponential increment behaviors is recommended, initially the CW increased exponentially so a long waiting time will be before trying the next transmission, after (N) retransmission failure the CW increased linearly, the experiments show that PLEB minimize the average of Packet Delay in dense networks.
Recently in 2014 new Contention Window based Multiplicative Increase Decrease Backoff (CWMIDB) algorithm for the DCF presented in [10] , the main objective of CWMIDB is reducing the number of collisions, since most of the previous algorithms improve the performance of MANETs but actually cause high packet collision rate, the algorithm modify CW size upon a collision depending on (I) which represent retransmission count of a packet as follows, Wi = 2i/2W for even values of i and Wi = 4 × 2 (I − 1)/2W for odd values of I, where W = CWmin.
2.2. Backoff Algorithm Based on Network Status
This group includes algorithms that depend on some computation done by the stations in the network to modify the CW size. In Measurement-based Backoff Fair MBFAIR [11] , the algorithm used some information collected from the neighborhood to compute the fair share that is used to modify the CW size. The Load-based Dynamic Backoff algorithm (LDB) described in [12] change CW size dynamically depending on the expected collision rate as a long-term factor and slot utilization as a short-term factor.
Another mechanism is described in [13] , the authors propose Exponential Linear Backoff Algorithm (ELBA) in which the CW size is changed exponentially and linearly according to the network load, a threshold is set to determine the network load which is specified by the number of collisions. If the CW size is smaller than the threshold, the CW size is adjusted exponentially, and if it is larger than the threshold, the CW size is adjusted linearly, ELBA provides better throughput and collision rate compared with both EIED and LILD algorithm. The History Based Adaptive Backoff algorithm (HBAB) [14] depend on the history of the channel, it means the CW is modified depending on the last N states of the channel whether it is busy or free, (0) indicate a busy channel, (1) for a free channel, and use ß, α as factors to modify the size of CW, this algorithm is very simple and provide a good result in reducing the average of packet delay and enhance the packet delivery fraction compared to the standard BEB.
In [15] , Yang ad Song suggest to modify the backoff time for the node depending on the value of its Acknowledgment (ACK) counter, this counter increase by one each time the node receive an ACK that doesn’t belong to it, and reset to zero if the ACK belong to it, different nodes will have different value of ACK counter after some successful transmissions, the algorithm is called the ACK-based Adaptive Backoff (AAB),which is better than BEB and MILD in the throughput, successful rate and energy efficiency. In [16] the authors proposed an enhancement on Probability Based Backoff algorithm (PBB) [17] by adding ß as a parameter in History Based Probabilistic Backoff algorithm (HBPB) which implements the order of collisions or successful transmissions, while PBB depend on α that indicate the collision rate and the success rate to determine the CW value. HBPB algorithm achieves better result than PBB algorithm in terms of throughput and delay. The next section presents the Backoff algorithm used in this paper
3. History Based Increment Backoff (HBIB) Algorithm
The main target of the proposed algorithm is to improve the throughput and end-to- end delay of the MANET which as a result reflects on its performance, that could be achieved by adjusting the increment/decrement procedure of the CW in the backoff algorithm, let us first describe the basic Binary Exponential Backoff algorithm idea, in BEB the CW is doubled upon a collision until the frame successfully transmitted or reach maximum number of retransmissions, and reset to CWmin which is equal to 31 after successful transmission [16] , the transmission terminated after 16 attempts of transmissions and the maximum CW reached is 1023, BEB results in decreased throughput due to resetting of CW to minimum value at every new transmission. BEB works as described in Figure 1.
The CW in case of collision can be mathematically represented as:
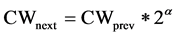 [16] (1)
[16] (1)
where α is static and equal to 1.
Figure 1. Binary exponential backoff algorithm.
In general, when trying to modify BEB the best decision always ignoring too short or too long backoff values, as many researches show that has bad effect on the performance of MANET. In HBPB Algorithm the value of α is diverse dynamically between −1 and 1, and set by the equation,
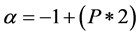 [16] (2)
[16] (2)
P here represent traffic load or collision rate,
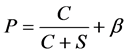 [16] (3)
[16] (3)
where C stand for number of collisions and S number of successful transmission, the variable β represent order of collision or successful transmission and calculated by
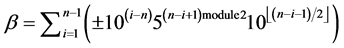 [16] (4)
[16] (4)
The ± sign used to specify the transmission whether it is a collision or successful one, variable n represents total number of transmissions, as can be shown in the algorithm the contention window size is not reset for every new transmission; it is hold from the preceding transmission. This can be seen in Figure 2.
Figure 2. History based probabilistic backoff algorithm.
In the following we explain in details the main modification that we have did on the HBPB to produce the suggested algorithm, followed by the pseudo code.
In HBIB algorithm we modify the increment behavior for the CW after a collision, by adding the absolute value of (β) to P equation as follow:
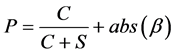 (5)
(5)
To increase the waiting time in case of collision which as a result reduces the contention on the channel and contribute in the increasing of the network throughput, also we modify the CW decrement by ignoring β from P calculation as follows:
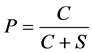 (6)
(6)
To minimize the CW decrement steps, to assist in avoiding the channel capture effect that gives the node with the minimum CW size the priority to access the channel which as a result increase the network delay
Then α is computed as mentioned earlier by Equation (2), the algorithm is summarized in Figure 3.
Figure 3. History based increment backoff algorithm.
4. Performance Evaluation and Results
In order to evaluate the performance of the suggested backoff algorithms the Network Simulator (NS) version 2.35 have been used with different MANET scenarios, created by Carnegie Mellon University (CMU)’s [18] traffic-pattern generator script cbrgen.tcl which is used to create a Constant Bit Rate (CBR) traffic connection between wireless mobile nodes to allow very tight control over the bandwidth in use at any moment, and CMU’s node-movement generator script “setdest”, which used Random Waypoint algorithm to create node movements pattern for mobile nodes. Our experiments have been run with the following simulation environment parameters (Table 1).
In this thesis we focus on the throughput and end-to-end delay as a performance metrics, since they have a key effect on the total performance of the network.
4.1. Throughput of the Network
Figure 4 and Figure 5 show how HBIB outperforms HBPB in terms of network throughput with different Packet rates 6, 10 Packets/s respectively and different num- ber of nodes due to the CW increment step which is larger in case of HBIB, and it is
Figure 4. Simulation result of network throughput versus number of nodes and traffic rate 6 Packets/s.
Figure 5. Simulation result of network throughput versus number of nodes and traffic rate 10 Packets/s.
known as the increment step increase, the backoff (waiting) time increase which as a result decrease the contention on the channel between the nodes, and increases the throughput of the network.
4.2. End-to-End Delay of the Network
Figure 6 and Figure 7 below illustrate how HBIB algorithm minimizes the network end-to-end delay compared with HBPB algorithm, as the CW decrement steps in HBIB algorithm are smaller than the steps in HPBP algorithm and it is known in backoff algorithms with large decrement steps the nodes will meet faster to the same range of backoff time which increase the contention as a result increase the delay of the network, by the time this could result to what is known as the channel capture effect which give the node with the minimum CW the priority to access the channel, leaving other nodes in the network waiting which as a result increase the network delay.
Figure 6. Simulation result of end-to-end delay versus number of nodes and a traffic rate of 4 Packets/s.
Figure 7. Simulation result of end-to-end delay versus number of nodes and a traffic rate of 8 Packets/s.
Table 1. The simulation environment parameters.
5. Conclusion
In this paper, we have enhanced an existing backoff algorithm called History Based Probabilistic Backoff (HBPB) algorithm which depends on (β) that implements the order of collisions and successful transmission for the backoff time computation. The proposed algorithm HBIB modifies the increment/decrement process by adding the absolute value of (β) to the increment formula and ignores it in decrement process, which attains an increment/decrement steps to improve the performance of the network in terms of throughput and end-to-end delay.
Cite this paper
Manaseer, S. and Badwan, F. (2016) History-Based Backoff Algorithms for Mobile Ad Hoc Networkse. Journal of Computer and Communications, 4, 37-46. http://dx.doi.org/10.4236/jcc.2016.411004
References
- 1. Zhalehpoor, S. and Shahhoseini, H.S (2009) SBA Backoff Algorithm to Enhance the Quality of Service in MANETs. International Conference on Signal Acquisition and Processing, ICSAP, Kuala Lumpur, 3-5 April 2009, 43-47.
http://dx.doi.org/10.1109/icsap.2009.47 - 2. Hoebeke, J., Moerman, I., Dhoedt, B. and Demeester, P. (2004) An Overview Mobile Ad Hoc Networks: Applications and Challenges. Journal of the Communications Network, 3, 60-66.
- 3. Bang, A.O. and Ramteke, P.L. (2013) MANET: History, Challenges and Applications. International Journal of Application or Innovation in Engineering & Management (IJAIEM), 2, 249-251.
- 4. Razafindralambo, T. and Lassous, I.G. (2009) SBA: A Simple Backoff Algorithm for Wireless Ad Hoc Networks. In: Fratta, L., Schulzrinne, H., Takahashi, Y. and Spaniol, O., Eds., NETWORKING 2009, Volume 5550, Springer-Verlag Berlin, Heidelberg, 416-428.
- 5. Haas, Z.J. and Deng, J. (2003) On Optimizing the Backoff Interval for Random Access Schemes. IEEE Transactions on Communications, 51, 2081-2090.
http://dx.doi.org/10.1109/TCOMM.2003.820754 - 6. Bharghavan, V., Demers, A., Shenker, S. and Zhang, L.X. (1994) MACAW: A Media Access Protocol for Wireless LAN’s. ACM SIGCOMM Computer Communication Review, 24, 212-225.
http://dx.doi.org/10.1145/190314.190334 - 7. Song, N., Kwak, B., Song, J. and Miller, L.E. (2003) Enhancement of IEEE 802.11 Distributed Coordination Function with Exponential Increase Exponential Decrease Backoff Algorithm. The 57th IEEE Semiannual Spring Vehicular Technology Conference, VTC, Jeju, 22-25 April 2003, 2775-2778.
- 8. Galtier, J. (2004) Optimizing the IEEE 802.11b Performance Using Slow Congestion Window Decrease. Proceedings of 16th ITC Specialist Seminar on Performance Evaluation of Wireless and Mobile Systems, Anvers, 31August-2 September 2004, 165-176.
- 9. Yassein, M.B., Manaseer, S., Al-hassan, A.A., Taye, Z.A. and Al-Dubai, A.Y. (2010) A New Probabilistic Linear Exponential Backoff Scheme for MANETs. Proceedings of the 2010 IEEE International Symposium on Parallel and Distributed Processing, Workshops and PhD Forum, IPDPSW, Atlanta, 19-23 April 2010, 1-6.
- 10. Madhavi, T. and Rao, G.S.B. (2014) Development of Collision Alleviating DCF Protocol with Efficient Backoff Algorithm for Wireless Ad hoc Networks. Springer Science + Business Media, New York.
- 11. Fang, H.-Y., Xu, L. and Li, X.-H. (2010) Logarithmic Backoff Algorithm of MAC Protocol in Ad Hoc Networks. Proceedings of the International Conference on E-Business and E-Government, ICEE, Guangzhou, 7-9 May 2010, 1695-1698.
- 12. Seo, C.-K., Wang, W.D. and Yoo, S.-J. (2005) Load-Based Dynamic Backoff Algorithm for QoS Support in Wireless Ad Hoc Networks. In: Jia, X.H., Wu, J. and He, Y.X., Eds., Mobile Ad-Hoc and Sensor Networks, Volume 3794, Springer-Verlag Berlin, Heidelberg, 466-477.
http://dx.doi.org/10.1007/11599463_46 - 13. Lin, C.-H., Shieh, C.-K., Hwang, W.-S. and Ke, C.-H. (2008) An Exponential-Linear Backoff Algorithm for Contention-Based Wireless Networks. Proceedings of the International Conference on Mobile Technology, Applications & Systems (Mobility Conference), Yilan, 10-12 September 2008, 42.
http://dx.doi.org/10.1145/1506270.1506324 - 14. Nasir, Q. and Albalt, M. (2008) History Based Adaptive Backoff (HBAB) IEEE 802.11 MAC Protocol. 6th Annual IEEE Communication Networks and Services Research Conference, Halifax, 5-8 May 2008, 533-538.
http://dx.doi.org/10.1109/cnsr.2008.20 - 15. Yang, Y., Song, G.n., Wei, K., Zhang, W.X. and You, X.H. (2015) ACK-Based Adaptive Backoff for Random Access Protocols. Science China Information Sciences, 58, 1-14.
- 16. Rajagopalan, N. and Mala, C. (2002) An Efficient and Dynamic Backoff Algorithm for IEEE 802.11 Networks. International Journal of System Assurance Engineering and Management, 3, 77-83.
- 17. Rajagopalan, N. and Mala, C. (2010) Analysis and Comparative Study of Different Backoff Algorithms with Probability Based Backoff Algorithm. In: Meghanathan, N., Boumerdassi, S., Chaki, N. and Nagamalai, D., Eds., Recent Trends in Network Security and Applications, Springer-Verlag Berlin, Heidelberg 331-339.
http://dx.doi.org/10.1007/978-3-642-14478-3_34 - 18. Greis, M. (2000) Generating Node-Movement and Traffic Connection Files for Large Wireless Scenarios.
http://www.isi.edu/nsnam/ns/tutorial/nsscript7.html









