Circuits and Systems
Vol.07 No.09(2016), Article ID:69128,12 pages
10.4236/cs.2016.79219
A Novel Approach to Reduce Handover Latency in Proxy Mobile IPv6 Based on Multi-Homing
Indumathi Lakshmi Krishnan1*, Shalini Punithavathani Davidson2
1Department of Computer Science and Engineering, National College of Engineering, Maruthakulam, India
2Department of Computer Science and Engineering, Government College of Engineering, Tirunelvelli, India

Copyright © 2016 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 22 April 2016; accepted 10 May 2016; published 27 July 2016
ABSTRACT
Proxy Mobile IPv6 (PMIPv6) is a network based mobility management protocol. It is proposed by the Internet Engineering Task Force. In PMIPv6 the Mobile Node (MN) need not participate in signalling of mobility. PMIPv6 is a layer 3 protocol. In this paper the issue of layer 3 mobility is resolved by the Enhanced Open Flow Technique (EOFT). Generally, the open flow protocol makes functions on network devices, routers, switches. Open flow controller act as server for network devices to make communication between them. In the proposed EOFT-PMIPv6, the control signalling and mobility is managed by EOFT controller. In PMIPv6, the Mobility Access gateway (MAG) has the responsibility of the control signalling. But in the EOFT-PMIPv6, the responsibility of MAG is done by the EOFT-Controller. In the proposed technique, the mobility management function is isolated from PMIPv6 mechanisms. These isolated mechanisms are combined in the EOFT-Con- troller. This EOFT-Controller satisfies the responsibility of the mechanisms which are separated from PMIPv6. The eminent mobile environment must provide the efficient multi-homing protocols. The proposed technique overcomes the problem of multihoming in PMIPv6. The EOFT-Controller takeover the responsibility of Layer 3 functions. Also, the proposed technique combines with Modified Mobility Access Gateway (M_MAG) and it handles the handover session dynamically. This paper provides the extended architecture of EOFT-PMIPv6 and provide unbeaten handover scheme for multi-homing. The result is provided by systematic analysis based on comparison with PMIPv6 and EOFT-PMIPv6 is obtained.
Keywords:
Binding Catch Entry (BCE), Logical Link Identifier (LL-ID), Mobility Access Gateway (MAG), PMIPv6, Open Flow, Multi-Homing

1. Introduction
Nowadays the technology of mobile communication has rapid growth. Particularly the internet and mobile phones and its various types has played vital role in the day-to-day communication. This makes force to improve the internet technology. The swift developments of mobile phones are supported by the internet and its protocols.
In the internet the transition of data is represented by packets. IPv4 is the first version of the internet protocol [1] . This is also represented as Internet Protocol next Generation (IPng). This IPv4 provides unique IP address for each computer system. But, the IPv4 address exhausted [2] . IPv6 is conventional expansion of IPv4. It is introduced by Request for Comments (RFC) [3] and it is an IPv6 is a host based mobility management protocol. PMIPV6 is a network based mobility management protocol standardized by IETF [4] .
PMIPv6 is a network based mobility management protocol standardized by IETEF [4] . It does not require MN participating in signalling of mobility i.e. the MN need not 1) modify the protocol stack 2) additional require of software to support mobility. According to PMIPv6 protocol an LMA updates a Binding Cache Entry (BCE) and switches the forwarding tunnel after receiving a Proxy Binding Update (PBU) message from the MN. Figure 1 explains the LMA in PMIPv6.
1.1. Analysis of PMIPv6 Based on Signalling Flow
In the network mobility protocols, the localized routing signals have messages and it increase the signalling cost and overhead. Table 1 provides Comparison summary between the different IP mobility protocols including PMIPv6 [8] - [10] .
1.2. PMIPv6-Open Flow
Open Flow is an innovative method managed by the network using software [5] . The main feature of the open flow method is to separate the work of network devices. The network devices forward packets using control and data functions [7] .
PMIPv6 Route Optimization focuses the problem of overhead [11] . To solve this problem, the bi-directional tunnel is used. In the Route Optimization of PMIPv6, CN must present in the concern PMIPv6 domain. To
Figure 1. Local mobility anchor in PMIPv6.
Table 1. Comparison between the different Ip mobility protocols [8] - [10] .
overcome this problem, the open flow method is introduced.
Technology of PMIPv6 with Open Flow
In the Open Flow PMIPV6, the signalling path did not pass through the LMA. It was passing through the tunnel. Thus the work load of the LMA is reduced. Figure 2 shows the signalling flow of Open Flow PMIPv6 [7] .
Open Flow is an innovative method managed by the network using software [5] . There are many technologies available in Open Flow [6] . In PMIPv6, the open flow technique is applied without the participation of MN. The main feature of the open flow method is to separate the functions of work of network devices. These network devices forward packets using control and data function [7] .
1.3. Analysis of PMIPv6 Based on Multihoming
In PMIPv6 protocol, when one interface detached from Mobile Nodethe other interface is still attached to the router. This situation is raised in PMIPv6 because the MAG have direct communication with M_MAG and it may have coverzge problem. There are many other proticolls supporting the multihoming of PMIPv6. There are many schemes to support PMIPv6 with multi-homing. Multiple registrations were explained in [12] . In this scheme all mobile network prefixes were registered with the home network to realize the benefit of multihoming. Also, L2-tunnels and information sharing among mobile routers in NEMO allowed mobile routers to achieve fault tolerance and path selection. The shim protocol [13] supported multihoming technique. Here, the Shim protocol was locally used between a multi-homed Mobile Node (MN) and the Local Mobility Anchor (LMA) in the PMIPv6 domain. A flow distribution scheme with the Shim locator preferences was proposed to provide flexible multihoming. The multihoming was supported by host identity protocol [14] . It merges the new identifier/locator split architecture proposed by HIP, especially designed for providing security and multihoming to MNs, with the micro-mobility management scheme of PMIPv6, which has been proposed for unmodified MNs with future Global Mobility Management (GMM) protocols. The existing bicasting technique [15] supported multi-homing of PMIPv6. Here, the Local Mobility Anchor (LMA) extended its Binding Cache Entry (BCE) for support of multiple bindings, and a mobile node (MN) performs the binding update to LMA. To support the handover, the LMA begins the bicasting of data packets to the New-Mobile Access Gateway (N-MAG) as well as Previous-Mobile Access Gateway (P-MAG). The same multihoming of PMIPv6 is supported by [16] . This was an enhanced multihoming support scheme based on a per-interface address configuration method. This scheme can provide a more flexible multihoming support and also maintain application session continuity during a handoff between two interfaces by using IPv6 extension headers.
The proposed EOFT technique reduces the difficulty of Local Mobility anchor (LMA) and Mobility Access Gateway (MAG) is reduced. It reduces the handover latency and packet loss and increase the performance than the existing PMIPv6 protocols. In existing multihoming techniques [12] - [14] focused only path selection, shim protocol, and mobility management respectively. But those techniques don’t focus on handover and multiple interfaces. The technique [15] focuses only to handover and not to various interfaces. The technique [16] focuses only session continuity in multihoming in various interfaces. But it did not provide strong support to the handover mechanism. But In the proposed technique the EOFT-Controller has the direct communication with M_MAG, so the Home Network Prefix (HNP) is dynamically assigned to MN and the immediately detach the
Figure 2. Signalling flow of open flow PMIPv6.
previous HNP. This dynamic approach of the proposed technique reduces the handover latency in multi-homing.
2. Proposed Method
The proposed Enhanced Open Flow (EOFT) is executing PMIPv6 apparently by open flow technique.
2.1. EOFT-PMIPv6 Architecture
In the open flow, signal and data did not communicate through the LMA and MAG [6] . In the EOFT-PMIPv6 is doing the work of open flow by the Virtual Flow Controller (VFC). VFC separate control signal path and communication path. The proposed system the virtually multiplies the MAG and the concern MAG is modified. This is represented as Modified-MAG (M_MAG). The modification i.e. the link between the MAG and M_MAG is done by the Open Flow Controller. This virtual distinction is shown in Figure 3.
2.2. Signalling Flow of the EOFT-PMIPv6
The proposed system architecture the signalling flow is handled by the tunnelling mechanism. The IP tunnel is generated in-between the LMA and M-MAG and M-MAG to LMA. Figure 4 shows the signalling flow of the proposed system.
The sender node i.e. the correspondent Node (CN) started to send the packets. When the mobile node visits the current network domain (PMIPv6), the MAG handover the signal to the EOFT-controller and the same controller send the message to the M_MAG. The M-MAG receives Router Solicitation (RS) from the Mobile Node. After receiving the RS the MN sends virtual RS to the EOFT-Controller. After receiving acknowledgement from the EOFT-controller, the MAG updates its Proxy Binding and the concern acknowledgment is send to the EOFT-controller. The EOFT-controller creates virtual tunnel between the controller and M_MAG and creates router advertisement. Then the physical tunnel is created between the LMA and M-MAG and the Data packet is transmitted.
2.3. Hand over Mechanism of EOFT_PMIPv6
Based on the configuration of PMIPv6 domain, the EOFT_PMIPv6 handover employed as proactive or reactive mode.
2.3.1. EOFT_PMIPv6 Hand over on Reactive Mode
The MAG handover its signal to EOFT-controller and that controller creates virtual communication with M_MAG. The M_MAG send Router Solicitation message to the controller. If the EOFT controller sends positive authentication then the M_MAG make Proxy Binding Update (PBU) and send Proxy Binding acknowledgement (PBA) to the EOFT-controller. After receiving PBA the virtual tunnel is created by the EOFT-con- troller. Then the Bidirectional tunnel is created between the LMA and M_MAG. Here, the handover delay is represented by the time delay between the Router Solicitation (RS) and Bidirectional tunnel. Figure 5 shows the handover of EOFT_PMIPv6 in reactive mode.
2.3.2. EOFT_PMIPv6 Hand over on Proactive Mode
In the Proactive mode, after receiving request from the MN it starts the PBU and tunnel creation. Once the MN node detached from previous MAG the M-MAG receives the PBU and it send PBU to EOFT-Controller. Then the EOFT-controller creates Bi-directional tunnel. Through this tunnel the data packet is transferred. Figure 6 shows the handover of EOFT_PMIPv6 in proactive mode.
Figure 3. Proposed system architecture.
Figure 4. Signalling flow of the proposed system.
3. Analytical Assessment of Proposed System
3.1. Hand over Analysis of PMIPv6
In PMIPv6, the MN creates communication between MN and M_MAG through RS and RA. Here, the delay was based on the authentication request and authentication response. The time taken by RS message to reach M_MAG to MN is represented as TRA. The Handover delay was calculated as Equation (1)
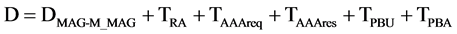 (1)
(1)
Here RS and TRA is calculated as
Figure 5. EOFT_PMIPv6 hand over on reactive mode.
3.2. Handover Analysis of EOFT_PMIPV6
Generally in the EOFT_PMIPv6 is based on the following Equation (2) According to the mode of handover it will be calculated
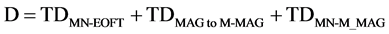 (2)
(2)
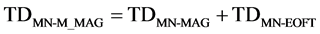 (3)
(3)
Table 2 shows the system notation and its descriptions.
Figure 6.EOFT_PMIPv6 hand over on proactive mode.
3.3. Handover Analysis of EOFT_PMIPv6 in Reactive Mode
Here, the initiation and end process is like as PMIPv6. However, in reactive mode, the MN does not require authentication. Here, the authentication is approved by EOFT-Controller.
The Equation (4) explains the handover delay.
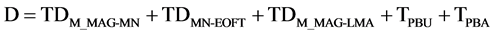 (4)
(4)
The above equation does not have initiation of tunnel time. So it does not affect handover latency.
Table 2. System notations and descriptions.
3.4. Handover Analysis of EOFT_PMIPv6 in Proactive Mode
The initiation of handover in proactive mode is activated when EOFT controller receives from MAG. In the Proactive mode, the MN does not send RS message, because it already sent RS message at the initiation of handover. So the authentication does not require in proactive mode. The following Equation (5) shows the handover delay of proactive mode.

3.5. Signaling Cost of the Proposed System
Hand over signaling consists of
1) MAG sending to EOFT controller
2) M_MAG sending Ack EOFT controller
3) M_MAG sending PBU to LMA
4) M_MAG receiving PBA from LMA
5) M_MAG sender Router solicitation with the prefix to MN
In this proposed system localized routing signalling is not have any messages. So the signalling cost and over head is reduced.
4. Result Analysis of the Proposed System
To analyze the proposed EOFT_PMIPv6 is compared with PMIPv6 in the basis of analytical model. The network simulator −3 (NS_3) [17] [18] tool is used to analysis the results.
4.1. Result Analysis Based on Handover
The proposed system is compared with PMIPv6 and EOFT_PMIPv6. Here, the handover latency is used as comparative parameter between PMIPv6 and EOFT-PMIPv6. Table 3 shows the parameters for the comparison [19] - [22] .
In the reactive mode it does not require authentication also it does not include tunnel creation time so it does not affect handover latency. In the Proactive mode when the mobile node receives message from EOFT-Con- troller, it automatically receives M_MAG details through the EOFT-controller. So it does not require signal handover between MAG and M_MAG. By this transmission in Proactive mode the handover latency is reduced. According to Equation 4.3 and 4.4, the analytical assessment proves that the proposed system reduces the handover latency. Here, the transmission time for RS and RA messages are considered to be equal. The following graph Figure 7 shows the handover delay between PMIPv6, EOFT_PMIPv6_R (Reactive mode), EOFT_ PMIPv6-P (Proactive Mode). The handover delay of PMIPv6 is 2.4 seconds and the proposed EOFT_PMIPv6_ R is 1.3 seconds and EOFT_PMIPv6_P is 0.6 seconds.
4.2. Result Analysis Based on Multi-Homing Handover
In order to analyze the proposed technique EOFT-PMIPv6 is compared with PMIPv6 and F-PMIPv6. It is decided to simulate the three protocols and acquire the results in a similar fashion as the mathematical model. The protocols have been simulated used Network Simulator (NS_3). NS_3 is an event simulator targeting network research and has a support for many protocols over the different network layers. The simulation is done in the signaling cost vs. the handover of the nodes.
Figure 8 provides the simulation result of single interface with PMIPv6, FPMIPv6 and proposed EOFT- PMIPv6 which provides lower signaling cost and handover time than the existing two protocols (PMIPv6, FPMIPv6).
Figure 9 provides the simulation result of EOFT_PMIPv6 with single interface (FTP-FTP) and multiple
Table 3. Analytical parameters.
Figure 7. Comparative analysis graph.
Figure 8. Simulation of various protocols with single interface.
Figure 9. Simulation of single and multiple interfaces.
interfaces (FTP-WiFi). While compare with the single interface the multiple interface has near equal to single interface also have better performance than the PMIPv6 and FPMIPv6.
5. Conclusion and Future Work
According to the analytical assessment it proved that the proposed system effectively reduces the handover delay while compare with PMIPv6. In the future it should compare with other mobility protocols such as FPMIPv6 also be implemented in the test bed to prove the results. The proposed technique focused multiple interfaces in the multi-homing domain, i.e. more than various MAGs. In the future different LMA is also done by with the security considerations.
Cite this paper
Indumathi Lakshmi Krishnan,Shalini Punithavathani Davidson, (2016) A Novel Approach to Reduce Handover Latency in Proxy Mobile IPv6 Based on Multi-Homing. Circuits and Systems,07,2530-2541. doi: 10.4236/cs.2016.79219
References
- 1. Perkins, C. (2002) IP Mobility Support for IPv4. IETF RFC 3344, August
- 2. Li, Z.M., Peng, W. and Liu, Y.J. (2012) An innovative IPv4-IPv6 Transition Way for Internet Service Provider. IEEE symposium on Robotics and Application (ISRA), Kuala Lumpur, 3-5 June 2012, 672-675.
- 3. Johnson, D., Perkins, C. and Arkko, J. (2004) Mobility Support in IPv6. IETF RFC 3775, June.
- 4. Gundavelli, S., Leung, K., Devarapalli, V., Chowdhury, K. and Patil, B. (2008) Proxy Mobile IPv6. IETF RFC 5213, August 2008
- 5. McKeown, N., Anderson, T., Balakrishnan, H., Parulkar, G., Peterson, L., Rexford, J., Shenker, S. and Turner, J. (2008) OpenFlow: Enabling Innovation in Campus Networks. ACM SIGCOMM Computer Communication Review, 38, 69-74.
http://dx.doi.org/10.1145/1355734.1355746 - 6. Suzuki, K., Sonada, K., Tomizawa, N., et al. (2014) A Survey on OpenFlow Technologies. IEICE Transactions on Communications, E97-B, 375-386.
- 7. Yuta Watanabe, Yoshitaka Nakamura, Osamu Takahashi (2015) A Method to Improve Network Performance of Proxy Mobile IPv6. Graduate School of Systems Information Science Future University, Hakodate, 8th International Conference on Mobile Computing and Ubiquitous Networking (ICMU), Hakodate, 20-22 June 2015, 74-75.
- 8. P′erez-Costa, X., Torrent-Moreno, M. and Hartenstein, H. (2003) A Performance Comparison of Mobile IPv6, Hierarchical Mobile IPv6, Fast Handovers for Mobile IPv6 and Their Combination. ACM Mobile Computing and Communications Review, 7, 5-19.
http://dx.doi.org/10.1145/965732.965736 - 9. Gwon, Y., Kempf, J. and Yegin, A. (2004) Scalability and Robustness Analysis of Mobile IPv6, Fast Mobile IPv6, Hierarchical Mobile IPv6, and Hybrid IPv6 Mobility Protocols Using a Large-Scale Simulation. IEEE International Conference on Communications, 7, 4087-4091.
- 10. P′erez-Costa, X., Schmitz, R., Hartenstein, H. and Leibsch, M. (2002) A MIPv6, FMIPv6 and HMIPv6 Handover Latency Study: Analytical Approach. Proceedings of IST Mobile & Wireless Communications Summit, The Netherland, 14 June 2002, 100-105.
- 11. Abeille, J. and Liebsch, M. (2007) Route Optimization for Proxy Mobile IPv6. draft-abeille netlmm-proxymip6ro-01.txt, November.
- 12. Li, Y., Kum, D.-W. and Cho, Y.-Z. (2008) Multihoming Support Scheme for Network Mobility Based on Proxy Mobile IPv6. ISECS International Colloquium on Computing, Communication, Control, and Management, 3-4 August 2008, 635-639.
- 13. Li, Y., Kum, D.-W., Seo, W.-K. and Cho, Y.-Z. (2009) A Multihoming Support Scheme with Localized Shim Protocol in Proxy Mobile IPv6. IEEE Communications, IEEE ICC 2009 Proceedings, Dresden, 14-18 June 2009, 1-5.
- 14. Iapichino, G. and Bonnet, C. (2009) Host Identity Protocol and Proxy Mobile IPv6:Secure Global and Localized Mobility Management Scheme for Multihomed Mobile Nodes. IEEE Communications “GLOBECOM” Proceedings, USA, 30 November-4 December 2009, 1-6.
- 15. Kim, J.I. and Koh, S.J. (2011) Extension of Proxy Mobile IPv6 with Bicasting for Support of Multi-Homing and Mobility in Wireless Networks. IEEE Workshops of International Conference on Advanced Information Networking and Applications (WAINA), Singapore, 22-25 March 2011, 86-89.
- 16. Li, Y., Kum, D.-W., Kang, J.-E. and Cho, Y.-Z. (2008) An Enhanced Multihoming Support Scheme with Proxy Mobile IPv6 for Convergent Networks. IEICE Transactions on Communications, E91-B, 3095-3102.
- 17. Quereilhac, A., Saucez, D., Turletti, T. and Dabbous, W. (2015) Automating Ns-3 Experimentation in Multi-Host Scenarios. WNS3’15 Proceedings, Spain, 13-14 May 2015, 1-8.
http://dx.doi.org/10.1145/2756509.2756513 - 18. Choi, H.-Y., Min, S.-G., Han, Y.-H., Park, J. and Kim, H. (2010) Implementation and Evaluation of Proxy Mobile IPv6 in NS-3 Network Simulator. Proceedings of the 5th International Conference on Ubiquitous Information Technologies and Applications (CUTE), Sanya, 16-18 December 2010, 1-6.
- 19. Oh, S. and Choo, H. (2009) Low Latency Handover Scheme Based on Optical Buffering at LMA in Proxy MIPv6 Networks, Proceedings of the International Conference on Computational Science and Its Applications: Part II, Seoul, 29 June-2 July 2009, 479-490.
- 20. Makaya, C. and Pierre, S. (2008) An Analytical Framework for Performance Evaluation of IPv6-Based mobility Management Protocols. IEEE Transactions on Wireless Communications, 7, 972-983.
http://dx.doi.org/10.1109/TWC.2008.060725 - 21. Lee, J.-H. and Ernst, T. (2011) Lightweight Network Mobility within PMIPv6 for Transportation Systems. IEEE Systems Journal, 5, 352-361.
http://dx.doi.org/10.1109/JSYST.2011.2158681 - 22. Jeon, S., Kang, N. and Kim, Y. (2012) Resource-Efficient Network Mobility Support in Proxy Mobile IPv6 Domain. International Journal of Electronics and Communications, 66, 390-394.
http://dx.doi.org/10.1016/j.aeue.2011.09.006
NOTES
*Corresponding author.















