Paper Menu >>
Journal Menu >>
 J. Software Engi neeri n g & Applications, 2010, 3, 939-943 doi:10.4236/jsea.2010.310111 Published Online October 2010 (http://www.SciRP.org/journal/jsea) Copyright © 2010 SciRes. JSEA 939 Digital Image Watermarking Algorithm Based on Fast Curvelet Transform Jindong Xu, Huimin Pang, Jianping Zhao College of Physical Engineering, Qufu Normal University, Shandong, China. Email: xujindong1980@yahoo.com.cn Received July 15th, 2010; revised August 18th, 2010; accepted August 21st, 2010. ABSTRACT A digital image watermarking algorithm based on fast curvelet transform is proposed. Firstly, the carrier image is de- composed by fast curvelet transform, and, the watermarking image is scrambled by Arnold transform. Secondly, the binary watermarking image is embedded into the medium frequency coefficients according to the human visual charac- teristics and curvelet coefficients. Experiment results show that the proposed algorithm has good performance in both invisibility and security and also has good robustness against the noise, cropping, filtering, JPEG compression and other attacks. Keywords: Digital Image Watermarking, Fast Curvelet Transform, Human Visual Characters, Robustness, Invisibility 1. Introduction In the past two decades, more and more researchers have devoted to the transform domain which shows good per- formance and robustness. Recently, Candès and Donoho [1,2] have developed a new multiscale transform which is called the Curvelet transform. It is anisotropic with strong direction, and provides optimally sparse represen- tations of objects along a general curve with bounded curvature. Hence, it has been widely used in image proc- essing field. At the same time, many research papers proposed to embed watermark based on the first curvelet transform [3-8]. Shi et al. [3] proposed a semi-fragile watermarking algorithm by embedding the wartermark in the maximum module of curvelet coefficient. This algorithm keeps good tolerance against JPEG compression. The method of Thai et al. [4] embedded a watermark in curvelet coef- ficients which are selected by a threshold. This method has good invisibility and robustness. Thai et al. [5] em- bedded the watermark in the curvelet transform which contain as much edge information as possible. It has good invisibility but poor robustness. The implementa- tion of the first curvelet transform includes subband de- composition, smooth partitioning, renormalize and ridgelet analysis. So these algorithms have many problems such as implementation complexity and large amount of redun- dancy. This paper proposes a digital image watermarking al- gorithm based on fast curvelet transform. Firstly, we take a binary-valued image which contains copyright infor- mation as watermark, and adapt Arnold transform to it to improve its security. Secondly, according to the human visual characteristics, we embed the watermark in curvelet coefficients of the original image. This algo- rithm is simple and easy to implement. Experiment re- sults show that our algorithm has good invisibility and security, and is robustness to the noise, cropping, filter- ing, JPEG compression and other attacks. 2. Curvelet Transform Similar to the wavelet transform and the ridgelet trans- form, the curvelet transform theory is based on sparsity theory [8]. The idea of curvelet is to calculate the inner relationship between the signal and the curvelet function to realize the sparse representation of the signal. 2.1. Continuous—Time Curvelet Transform The curvelet transform can be expressed as ,, ,, :, j lk cjlk f (1) here, j = 0, 1, 2, …, is a scale parameter; l = 0, 1, 2, …, is an orientation parameter; and k = (k1, k2) ∈ Z2 is a translation parameter. The mother curvelet is φj (x), its Fourier transform is φj (ω) = Uj (ω), where Uj is fre-  Digital Image Watermarking Algorithm Based on Fast Curvelet Transform 940 quency window defined in the polar coordinate system such as: 3/4 2/2 ,2 22 jj j j UrW rV l (2) W and V are radial and angular windows respectively and will always obey certain admissibility conditions. Curvelet at scale 2-j, orientation θand position ,1 12 2, 2 l jl j j k xRk k can be expressed as: , ,, l jl jlk jk xRxx (3) So, for f ∈ L2 (R2), curvelet transform is expressed as: ,, 2 2 1ˆˆ ,,:( )d 2 1ˆexp i,d 2l jlk j,l jθk cilkf fURωx (4) 2.2. Digital Curvelet Transform Digital curvelet transform is linear and takes as input Cartesian arrays of the form f [t1, t2], 0 ≤ t1, t2 < n, which allows the output as a collection of coefficients: 12 12,.12 0, ,, :,, D jlk tt n cjlkftt tt D (5) In order to improve the curvelet transform—in the sense that they are conceptually simpler, faster and far less redundant. Paper [2] proposed the Fast Discrete Curvelet Transform (FDCT). There are two digital im- plementation of FDCT. The first is based on un- equally-spaced fast Fourier transform (USFFT) while the second is based on the wrapping of specially selected Fourier samples. The FDCT-Wrapping uses simpler choice of spatial grid to translate curvelets at each scale and angle. It needs less two-dimensional FFTs than FDCT-USFFT, so it is quickly. The architecture of FDCT via Wrapping is then roughly as follows: 1) Apply the 2D FFT and obtain Fourier sample 12 , f nn , -n/2 ≤ n1, n2 ≤ n/2 (n is the size of the picture). 2) For each scale/angle pair (j, l), form the product ,12 12 ˆ ,, jl Unnfnn . 3) Wrap this product around the origin and obtain ,12, 12 ˆ , jl jl , f nnWU f nn n n0 , where the range for 1and 2 is now 11, j nL and 22, 0 j nL (for in the range (/4,/4 ). 4) Apply the inverse 2D FFT to each, j l f , hence col- lecting the discrete coefficients . lk,, D cj 3. Watermarking Algorithm Based on FDCT 3.1. Watermark In this algorithm, the watermark is a binary-valued image with 32 × 32 pixels (Figure 1). Arnold transform is used to increase the data security, and its function is defined as (6). ' ' 11 mod 1 xx N kky y (6) Adapt n (here, n = 8) times Arnold transform to the original watermark W, then we obtain scrambling wa- termark (Figure 2). 3.2. Watermark Embedding According to the Human Visual Characteristic, we choose to embed the watermark into medium-frequency. In selected scale, the coefficients of each orientation are sorted and find criterion Ti by amplitude factor λ (λ ≥ 0). Then choose the minimum Ti as embedding parameter T. Finally, the watermark is embedded to coefficients which are chosen by T . The embedding procedure (Figure 3) is described as follows. 1) Apply FDCT to the original image, get curvelet co- efficient C. 2) Select the curvelet coefficient to embed a bit wa- termark according to the following conditions. For 00,,2or,,32 For 12,, CjlkTT CjlkT TCjlkT (7) Then record the positions of these coefficients and the positions of 0 and 1 in the watermark. 3) The embedded coefficients are modified by the fol- lowing equations. ' ' Embed 0,,,, mod, ,,4 Embed 1,,,, mod, ,,34 CjlkC jlk CjlkTT CjlkC jlk CjlkTT (8) 4) Do inverse FDCT to C’, obtain the watermarked image. 3.3. Watermark Extraction The extraction procedure is composed of 4 steps and each step is described as follows. Figure 1. Watermark. Figure 2. Scrambled watermark. Copyright © 2010 SciRes. JSEA  Digital Image Watermarking Algorithm Based on Fast Curvelet Transform Copyright © 2010 SciRes. JSEA 941 IFDCT 1j 2 j 3 j 4j 5 j 3 j 1 l 2 l 3 l n l 2/,,0 TkljC 2/3,, TkljCT 4/,,,mod,,,, ' TTkljCkljCkljC TkljCT,,2/ 4/3,,,mod,,,, ' TTkljCkljCkljC Figure 3. Embedding procedure . 4.1. Invisibility Tests 1) Apply curvelet transform to watermarked image, obtain curvelet coefficient C’. The watermarked image is shown in Figure 5(a), the detected watermark from watermarked image is shown in Figure 5(b). 2) Locate the watermark positions from the original image by using embedding procedure step 2. Then ex- tract the coefficients C’ from the watermarked image using those watermark position. 3) Extract the watermark W’ from C’ with the follow- ing rule ' ' 1mod,,, 0mod,,, i ifCljkTT ifCljkTT 2 2 (9) 4) Apply T’-n (T’ is Arnold transform period) times Arnold transform to W’, obtain the binary watermark image. Figure 4. Original image. 4. Experimental Results In this program, the image is transformed through FDCT via Wrapping. We use standard 512 × 512 pixel image ‘Lena’ (Figure 4) for evaluation of our proposed method, and conduct experiments binary-valued image water- marking with the noted above parameter scale = 3, λ = 0.75. We have investigated the invisibility and the robust- ness of our watermarking system, analyzed the algorithm performance by objective and subjective standards. (a) (b) Figure 5. Invisibility Tests. (a) Watermarked image [PSNR 60.8028dB]; (b) Detected watermark [NC = 1.00]. = 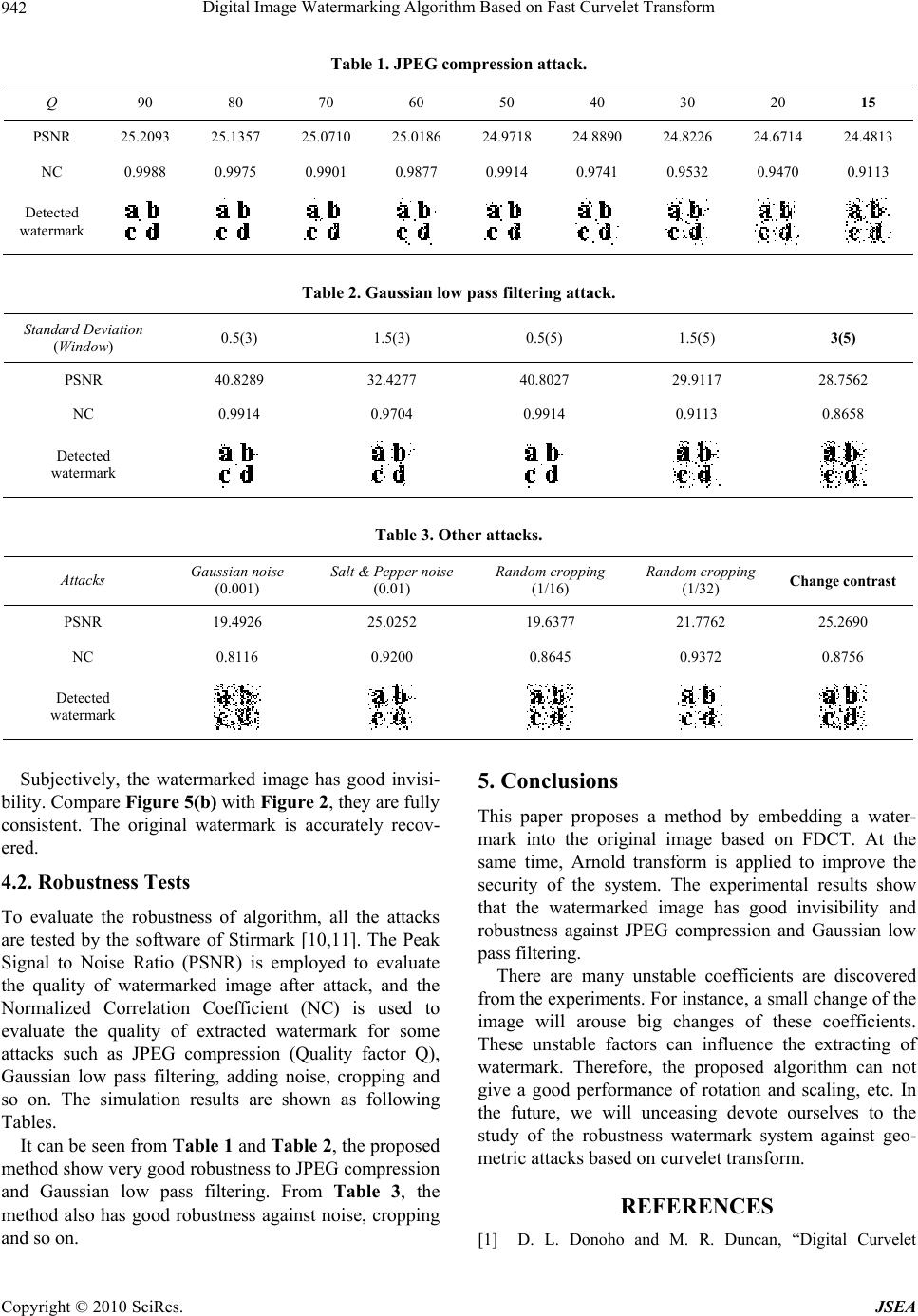 Digital Image Watermarking Algorithm Based on Fast Curvelet Transform 942 Table 1. JPEG compression attack. Q 90 80 70 60 50 40 30 20 15 PSNR 25.2093 25.1357 25.0710 25.0186 24.9718 24.8890 24.8226 24.6714 24.4813 NC 0.9988 0.9975 0.9901 0.9877 0.9914 0.9741 0.9532 0.9470 0.9113 Detected watermark Table 2. Gaussian low pass filtering attack. Standard Deviation (Window) 0.5(3) 1.5(3) 0.5(5) 1.5(5) 3(5) PSNR 40.8289 32.4277 40.8027 29.9117 28.7562 NC 0.9914 0.9704 0.9914 0.9113 0.8658 Detected watermark Table 3. Other attacks. Attacks Gaussian noise (0.001) Salt & Pepper noise (0.01) Random cropping (1/16) Random cropping (1/32) Change contrast PSNR 19.4926 25.0252 19.6377 21.7762 25.2690 NC 0.8116 0.9200 0.8645 0.9372 0.8756 Detected watermark Subjectively, the watermarked image has good invisi- bility. Compare Figure 5(b) with Figure 2, they are fully consistent. The original watermark is accurately recov- ered. 4.2. Robustness Tests To evaluate the robustness of algorithm, all the attacks are tested by the software of Stirmark [10,11]. The Peak Signal to Noise Ratio (PSNR) is employed to evaluate the quality of watermarked image after attack, and the Normalized Correlation Coefficient (NC) is used to evaluate the quality of extracted watermark for some attacks such as JPEG compression (Quality factor Q), Gaussian low pass filtering, adding noise, cropping and so on. The simulation results are shown as following Tables. It can be seen from Table 1 and Table 2, the proposed method show very good robustness to JPEG compression and Gaussian low pass filtering. From Table 3, the method also has good robustness against noise, cropping and so on. 5. Conclusions This paper proposes a method by embedding a water- mark into the original image based on FDCT. At the same time, Arnold transform is applied to improve the security of the system. The experimental results show that the watermarked image has good invisibility and robustness against JPEG compression and Gaussian low pass filtering. There are many unstable coefficients are discovered from the experiments. For instance, a small change of the image will arouse big changes of these coefficients. These unstable factors can influence the extracting of watermark. Therefore, the proposed algorithm can not give a good performance of rotation and scaling, etc. In the future, we will unceasing devote ourselves to the study of the robustness watermark system against geo- metric attacks based on curvelet transform. REFERENCES [1] D. L. Donoho and M. R. Duncan, “Digital Curvelet Copyright © 2010 SciRes. JSEA  Digital Image Watermarking Algorithm Based on Fast Curvelet Transform943 Transform: Strategy, Implementation and Experiments,” Proceeding of the SPIE on Wavelet Application VII, Or- lando, 2000, pp. 12-30. [2] E. J. Candes, L. Demanet and D. L. Donoho, “Fast Dis- crete Curvelet Transforms [R],” Applied and Computa- tional Mathematics, 2005, pp. 1-43. [3] J. P. Shi and Z. J. Zhai, “Curvelet Transform for Image Authentication,” Rough Set and Knowledge Technology, LNAI 4062, 2006, pp. 659-664. [4] T. D. Hien, I. Kei, H. Harak, et al., “Curvelet-Domain Image Watermarking Based on Edge-Embedding,” Lec- ture Notes in Computer Science, Vol. 4693, No. 2010, 2007, pp. 311-317. [5] T. D. Hien, K. Miyara, et al., “Curvelet Transform Based Logo Watermarking,” Innovative Algo-Rithms and Tech- niques in Automation, Industrial Electronics and Tele- communication, 2007, pp. 305-309. [6] H. Y. Leung, L. M. Cheng and L. L. Cheng, “Digital Watermarking Schemes Using Multi-Resolution Curvelet and HVS Model,” Lecture Notes in Computer Science, Vol. 5703, 2009, pp. 4-13. [7] H. Y. Leung, L. M. Cheng and L. L. Cheng. “A Robust Watermarking Scheme Using Selective Curvelet Coeffi- cients,” International Conference on Intelligient Informa- tion Hiding and Multimedia Signal Processing, Harbin, August 2008, pp. 465-468. [8] T. D. Hien, K. Miyara, I. Kei and F. F. Ali, “Digital Wa- termarking Based on Curvelet Transform,” 9th Interna- tional Symposium on Signal Processing and Its Applica- tions, Sharjah, Feburary 2007, pp. 1-4. [9] J. L. Cheng and T. Shan. “Development and Prospect of Image Multiscale Geometric Analysis,” Acta Electronic Sinica, Vol. 31, No. 12 A, pp. 1975-1981. [10] A. P. Fabien and Petitcolas. “Watermarking Schemes Eval uat ion, ” IEEE. Signal Processing, Vol. 17, No. 5, 2000, pp. 58-64. [11] Stirmark. http://www.petitcolas.net/fabien/watermarking /stirmark/ Copyright © 2010 SciRes. JSEA |

