Int'l J. of Communications, Network and System Sciences
Vol.6 No.1(2013), Article ID:27448,11 pages DOI:10.4236/ijcns.2013.61003
Performance Analysis of Hybrid MAC Protocol for Cognitive Radio Networks
1Department of Telecommunication Science, University of Ilorin, Ilorin, Nigeria
2Bayero University, Kano, Nigeria
3Departement of Electronics, University of York, York, UK
Email: faruk.n@unilorin.edu.ng, mohgumel@yahoo.com, aao500@york.ac.uk, seko1053@gmail.com
Received October 10, 2012; revised November 20, 2012; accepted December 14, 2012
Keywords: Dynamic Spectrum Access (DSA); Optimized Network Engineering Tool (OPNET); TV White Space; Cognitive Radio Networks; Signal-to-Interference Ratio (SIR); Hybrid MAC
ABSTRACT
The rapid growth in demand for broadband wireless services coupled with the recent developmental work on wireless communications technology and the static allocation of the spectrum have led to the artificial scarcity of the radio spectrum. The traditional command and control model (Static allocation) of spectrum allocation policy allows for severe spectrum underutilization. Spectrum allocated to TV operators can potentially be shared by wireless data services, either when the primary service is switched off or by exploiting spatial reuse opportunities. This paper describes a hybrid access scheme based on CSMA/CA and TDMA MAC protocols for use in the TV bands. The approach allows secondary users (SU) to operate in the presence of the primary users (PU) and the OPNET simulation and modelling software has been used to model the performance of the scheme. An analysis of the results shows that, the proposed schemes protect the primary user from harmful Interference from the secondary user. In terms of delay, it was found that packet arrival rates, data rates and the number of secondary users have significant effects on delay.
1. Introduction
The rapid growth in demand for broadband wireless services and the development of wireless communications technologies have lead to radio spectrum scarcity. The traditional command and control policies have become inefficient in utilization of the spectrum. Therefore, the need to adopt a better and smarter method of spectrum exploitation with properties of enhanced utilization efficiency and capable of accommodate the growing of the demand of the spectrum. The IEEE 802.22 standard for Wireless Regional Area Network (WRAN) that specifies how to and use unused spectrum (white space) in the TV broadcast band. The aim is to bring broadband access to hard-to-reach, low population density, areas. IEEE 802.22 specifies that the networks should operate in a point-to-multipoint configuration. A base station will manage its own cell and support a number of consumer premise equipments (CPE). Hence, there will be another infrastructure put in place to help the unlicensed users also termed as secondary users to make use of the TV unused portion of the spectrum band. To support all entities described, the networks must have cognitive capabilities i.e. it is a cognitive radio networks. Dynamic spectrum access (DSA) is a thrilling new concept that promises to provide flexibility to spectrum management, thereby, overcoming the limitations of traditional command and control model which gives a licensed user an exclusive right to a fixed and static amount of spectrum without taking account the time varying in the demand of the spectrum. The traditional spectrum allocation schemes primarily, focused on avoiding interference between the licensed (primary user) and unlicensed users (secondary users) without giving emphasis on the efficient utilization of the spectrum and the maximization of economic benefits in terms of revenue generation. Due to these, most of the spectrum is underutilized most of the time with low average occupancy values of less than 10 percent as reported in [1]. Regulatory bodies have shown great interest in achieving enhanced spectrum utilization, for instance in the United States; the FCC approved the use of TV white space as unlicensed wireless spectrum in November, 2004, Check et al., [2]. In the United Kingdom [3], OFCOM published a proposal in July 2009 for opening up the TV white space to new applications. In Nigeria, the Nigerian Communications Commission, NCC [4], published a report on national radio frequency spectrum emphasizing on the development of comprehensive and clear-cut policies that will ensure that spectrum resource is optimally utilised for the overall benefit of the nation and therefore, to continue to adopt policies that will ensure that this scarce resource is well managed. The TV white space which is the unused spectrum allocated for television services until recently belongs to the lower frequency range and meet the demand of the recently published rules as published by FCC [5]. The rule is aimed at regulating unlicensed secondary operation in the TV white space where the devices are divided into two categories: fixed and personal/portable as shown by Ghosh et al., [6]. The fixed devices can transmit up to 4 W Equivalent Isotropically Radiated Power (EIRP) with a Power Spectral Density (PSD) of 16.7 mW/100 kHz. The fixed devices are restricted in operating on adjacent channels of active TV broadcasting channels. While the personal/portable devices are allowed to transmit with a maximum EIRP of 100 mW (with PSD of 1.67 mW/100 kHz) on channels non-adjacent to TV broadcast services and 40 mW (with PSD of 0.7 mW/100 kHz) on channels adjacent to an active TV broadcasting channel.
This paper, describes hybrid MAC protocol which is based on partial IEEE 802.11 CSMA/CA and TDMA MAC protocols, specifically designed to enable dynamic spectrum access (DSA) in cognitive radio networks. Primary user is allocated slot for transmission and the secondary users are allowed to transmit on the white space, each SU therefore uses CSMA strategies to contend for the white spaces. The performance of the CSMA-TDMA protocol is evaluated and analyzed in terms of delay experienced by the secondary users as a function of the amount of white space and number of secondary users. The results are presented. The paper is organized as follows. Section 2, provide an overview of related MAC protocols for DSA. In Section 3, a model for the system is developed, Sections 4 and 5 provide details simulation and performance analysis and finally, Section 6 concludes the paper.
2. Over View of MAC Protocols for Cognitive Radio Systems
MAC protocol helps to determine whether the secondary user can access the spectrum or not. The primary user has the priority access and the secondary users access the spectrum opportunistically. The existing MAC approaches can be classified into 1) random access protocols, 2) time slotted protocols, and 3) hybrid protocols [7,8]. Random access or contention based protocol is based on carrier sense multiple access with collision avoidance (CSMA/CA) mechanisms which is similar to the IEEE 802.11 DCF standards. In the slotted MAC protocol, secondary user accesses the spectrum using Time-Division Multiple Access (TDMA) technique and this avoids unacceptable interference to primary receivers. The hybrid MAC protocol is usually based on ON/OFF Model [9].
Due to the random nature of the contentions based access schemes, users using such protocols are prune to packets collision which might subsequently affects the spectrum utilization and the overall network performance in terms of throughput and delay. The contentious scheme has been successfully used in many wireless applications including the Local Area Network (LAN) and Wireless Local Area Networks (WLAN). However, slotted based mechanisms require tight synchronization mechanism and slot allocation strategy which makes the design of the protocol complex. Hybrid protocols try to achieve the tradeoff between the contention-based and slotted protocols.
Several MAC protocols have been proposed to enable dynamic spectrum access. Geirhofer et al., [10], propose a cognitive resource management protocol that, based on sensing, the infrastructure system allocates transmit power and transmission time to reduce interference. This leads to an interference-aware resource allocation. An electromagnetic interference (EMI) aware RTS/CTS protocol [11], for an infrastructure-based cognitive system was proposed. The system is designed to avoid harmful EMI caused to medical devices, which are considered to be primary users by allocating appropriate transmit power to the secondary user that satisfies the EMI constraint of the medical devices. The EMI immunity level is defined in terms of the electric field (measured in Volt per meter) in which the medical devices can operate normally and the channel access mechanism was similar to IEEE 802.11 CSMA/CA MAC protocol. Auer et al., [12] propose an interference aware medium access for dynamic spectrum sharing; a receiver transmits a busy signal in an adjacent time multiplexed mini slot upon data reception. Through exploitation of channel reciprocity, other potential transmitters are prevented from interfering by first listening to the busy signal. [13], proposed a novel slotted DSA protocol named T-MAC protocol. In the work, the super frame structure of T-MAC consists of one reservation frame, K information frames and one acknowledgment frame. Each of the reservation frames contains one sensing slot and N reservation slots. In order to decide which channel is available in current slot, all users must sense data channels in sensing slots. Several hybrid protocols have also been proposed for cognitive radio networks. [14], proposed an efficient multichannel MAC protocol and channel allocation schemes for TDMA based cognitive radio networks which integrate spectrum sensing, packet scheduling, and channel allocation. [15], proposed an interference mitigation MAC protocol for cognitive radio networks, the work describe a DSA scheme for use in the TV bands which uses cognitive radio techniques to determine the spectrum availability.
3. System Model
In this work we propose a system similar to IEEE 802.11 with a primary user who can be an owner of a TV station and an opportunist secondary user in a scheme which can be a user requiring access to the wireless network. The primary user does not access the wireless spectrum all the time and is given priority over the secondary users to transmit and also protected from interference from the secondary users. We propose the use of a modified concept similar to the concept of CSMA/CA MAC protocol where transmitting nodes sense the channel for any other nodes transmitting before attempting to transmit. We modify this to provide cognitive capabilities to the system. We consider a system consisting of a primary transmitter (PTx) transmitting to primary receivers (PRx) who re located with a 40 km radius as shown in Figure 1 below. The primary users are assumed not to be transmiting all the time making creating a form of spectrum holes which can be filled by the secondary users. The Secondary users would have to determine when the spectrum is vacant and an optimal position relative to the primary transmitter before transmitting. This distance forms one of the basics of our work.
As seen from Figure 1 the primary receiver (PRx,) is located at a distance D1 from the primary transmitter (PTx) and D2 from the secondary user transmitter (SUTx). The Signal to interference Ratio (SIR) at the receivers would determine if the primary user and the secondary users can transmit at the same time. The distances of separation also determine the SIR as transmit power diminishes with distance. The interference range is denoted by D2. We assuming the radius rp as the service area after the secondary user protection region (rp) as proposed in [16], where the primary receiver is able to detect the signal from the transmitter of the primary user.
3.1. Interference and Channel Modelling
Hidden node can lead to collusion or interference on the primary user by the secondary users or secondary user by
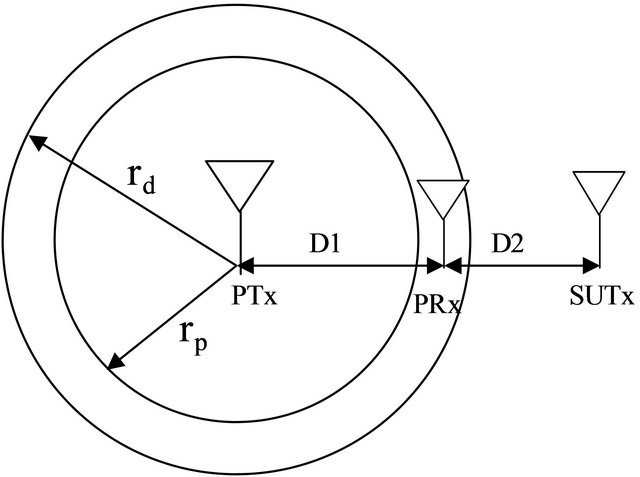
Figure 1. Showing detection (rd) and protection (rp) radius for primary receiver (PRx) in the presence of transmissions from the secondary transmitter (SUTx).
primary user especially when the transmitting channels are limited. [6] went further to explain that to state that interference can also occur amongst secondary users and among primary users when there is more than one primary or secondary user in the system. Increasing the power of nodes transmitting can help solve problems of hidden node and knowing the location and channel gain between the primary user and secondary users. There are other factors that can affect the performance of a cognitive radio network such as the overlapping between the time end period of transmission of the primary users and the beginning of transmission of the secondary users. The degree of this overlap might not only lead to interference but might affect the overall traffic load level.
In other to allow the coexistence of the primary and secondary users the above mention problems needs to be solved without causing unacceptable interference between the two user groups. Figure 2 shows the interfering signal at the primary receiver. The signal-to-interference ratio depends on the power in which the secondary user is transmitting and the distance from the primary receiver. AP is the access point (cognitive radio network base station). The signal strength at both the PRx (primary user receiver) and the SURx (secondary user receiver since the secondary user is a transceiver) is determined by the path loss equation. The free space path loss is used in this work but there are many published path loss models for a cognitive radio [17].
In this paper, the free space path loss (FSPL) model is used. This is because it gives the worst case interference scenario and it is easy to analyse. The FSPL at a given distance (d) between any two users or access point is given by Equation (1):
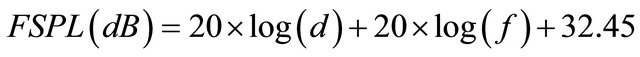 (1)
(1)
where d is the distance in km and f is the frequency in MHz. The SIR (Signal-to-interference) is defined as the ratio of the wanted signal from the primary user transmitter (PTx) and the unwanted signal from the secondary user transmitter (SUTx) when considering a single primary receiver and secondary transmitter in Figure 2.
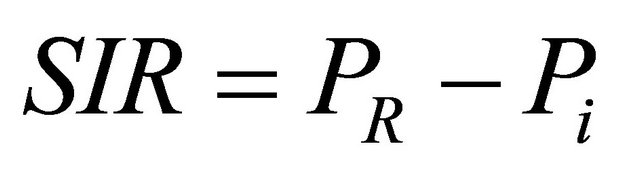 (2)
(2)
where Pi is the interference power in dBm from the SUTx, PR is the received power in dBm and SIR is the signal-to-interference ratio in dB at the primary user receiver. The simulation was carried out using wireless nodes with an operating transmission frequency of 2.4
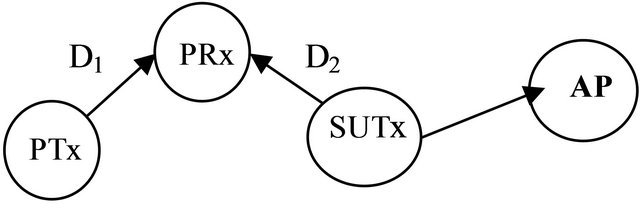
Figure 2. Network diagram.
GHz, receiver sensitivity of −95 dBm and speed of propagation 3 × 108 m/s at a distance of 0 - 3 km between the SUTx and the PRx. The result is shown in the Figures 3 and 4. In our model the primary transmitter transmits to the primary receiver. The transmitting signals from the primary transmitter vary with distance using the FSPL model. The secondary transmitter also attempts to transmit creating some unwanted signals which interferes with that primary transmission which is located at some certain distance as shown in Figure 1. We measure the quality of the received signal compared to the interference from the secondary users using the signal-to-interference ratio (SIR) which is the ratio of the power of the wanted signal and the aggregated power of the unwanted signals. Figure 3 shows the variability of interference power at the primary user (PRx) receiver with distance from the secondary transmitter (SUTx). The measured interference power at the primary receiver is −85.1 dBm when the secondary transmitter is transmitting at 5 mW and is 500 m from the PRx. Determination of the optimal transmitting power and the optimal distance of the secondary user transmitter that will not degrade the SIR at the primary receiver below the threshold level is the main focus of the work. A transmission between the transmitters of the primary users to the secondary users is assumed to fail if the SIR ratio at the receiver is below the SIR threshold and it is assumed to be successful is above the SIR threshold. Different cellular systems require different level SIR thresholds usually determined the system data rate requirement, examples of which are 18 dB, 14 dB, and 9 dB are required as the minimum acceptable SIR protection levels in Advanced Mobile Phone System (AMPS), Digital Time Division Multiple Access (TDMA) respectively. Systems such as IS-136, and Global System
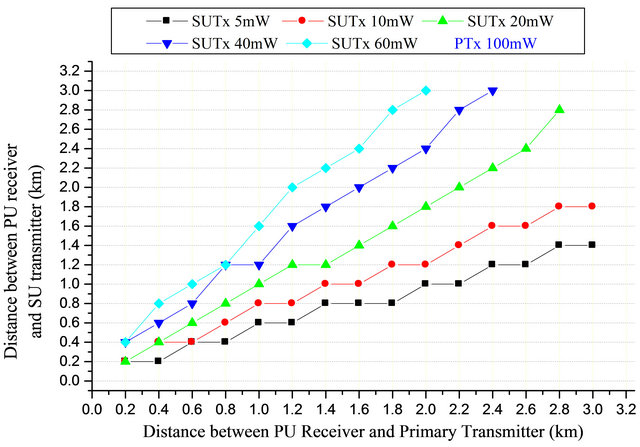
Figure 3. Interference power at the primary receiver.
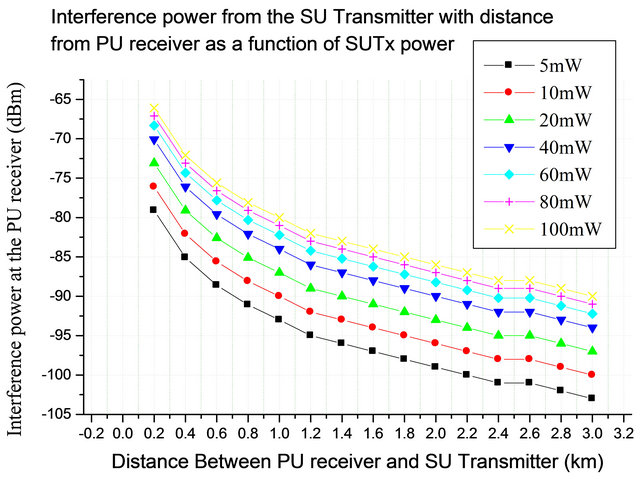
Figure 4. Maximum permissable transmission distance (km) between the SUTx and the PRx.
for Mobile Communication (GSM), respectively [18]. In our model 6 dB threshold level is used. The maximum allowable transmission distance for secondary transmission is computed and the result is shown in Figure 4.
In Figure 4, when the PRx is 3 km from the PTx transmitting at 100 mW, and SUTx power is 5 mW, at a target SIR of 6 dB, the maximum allowable transmission distance is 1.4 km. In Figure 5, the secondary transmitter can be up to 1.4 km to the primary receiver without degrading the SIR below the target. All the zones 0.2 km to 1.4 km are no-talk regions (protection zones) for secondary transmission; i.e. secondary user is not allowed to transmit within that range. This implies that the protection region for primary receiver is 1.4 km radius. Other zones 1.4 km to 3 km representing 1.6 km radius are allowable talk regions for secondary transmission; any transmission on this region will not cause severe interference to the primary receiver and therefore, its allowable region for secondary user transmission. However, the thickness (in km) of these zones (Talk and no-talk) depends solely on the transmit power of PTx and SUTx.
3.2. Channel Access Mechanism
There are two basic types of a wireless system transmission network, the Ad-hoc network and the infrastructure based network. The Ad-hoc wireless system in which no access point is required as the wireless devices communicate directly to each other and the infrastructure-based system, where users transmit via an access point. In our work every secondary user transmits its data via the access point. The access point uses the information about the primary receiver to determine whether to allow the secondary transmission or not. Both the access point (AP) and secondary users perform periodic channel sensing. The sensing results from the SU users are sent back to the AP to construct a spectrum occupancy/availability map for each geographical location. A connection is initiated with the AP when the SU performs spectrum sensing. The sensing is based on primary transmitter energy detection as shown in [19]. This identifies the available free channel if the primary transmitter is not transmitting (white space).
Based on this white space, the SU then scans for a synchronization channel (SCH) transmitted from the AP. This is done via a beacon which is broadcast from the AP to all secondary users within the cell for time synchronisation and resource allocation information. The SU then initiates a connection by sending the request-to-send (RTS) packet after the SCH is received at the receiver, and based on the sensing results if the primary transmitter is ON/OFF. If it is ON the PTx at the AP performs admission control tests.
The AP determines if the SUTx is within the interference range of the PRx by computing the distance of the SUTx to the PRx using the signal transmitted by the SUTx, this is done in the presence of a PRx, If otherwise, the AP computes the appropriate transmission parameters which are the maximum allowable transmit power form the secondary user in order to avoid unacceptable interference at the PRx. This is then sent back with a “clear to send” (CTS) signal to the secondary user as shown in Figure 6. In the event that the secondary user is within the range of interference of the primary receiver, the request for data transmission from the user would be rejected and no CTS signal would be sent. The AP knows if a primary receivers is present or not and also knows their locations since the interference occurs at the primary receiver and the secondary user has to pass through admission control tests as described above. The primary receiver usually emits some local oscillator (LO) leakage power from its antenna terminal when it receives signals from the primary transmitter [20]. This is done in order to reliably determine the location of the primary receiver. A primary receiver detection method would also be used to exploits the LO leakage power instead of relying only
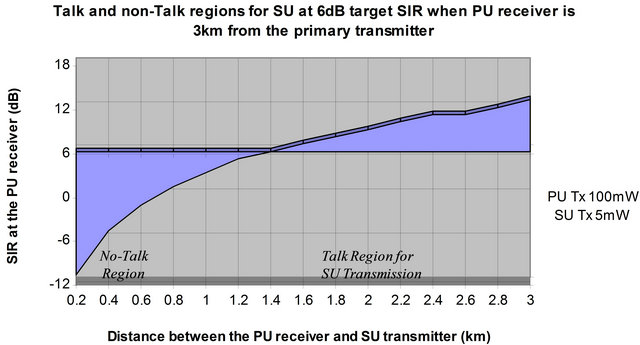
Figure 5. Talk and non-talk regions for the secondary user at 6 dB target SIR when the primary receiver is 3 km away from the primary transmitter.
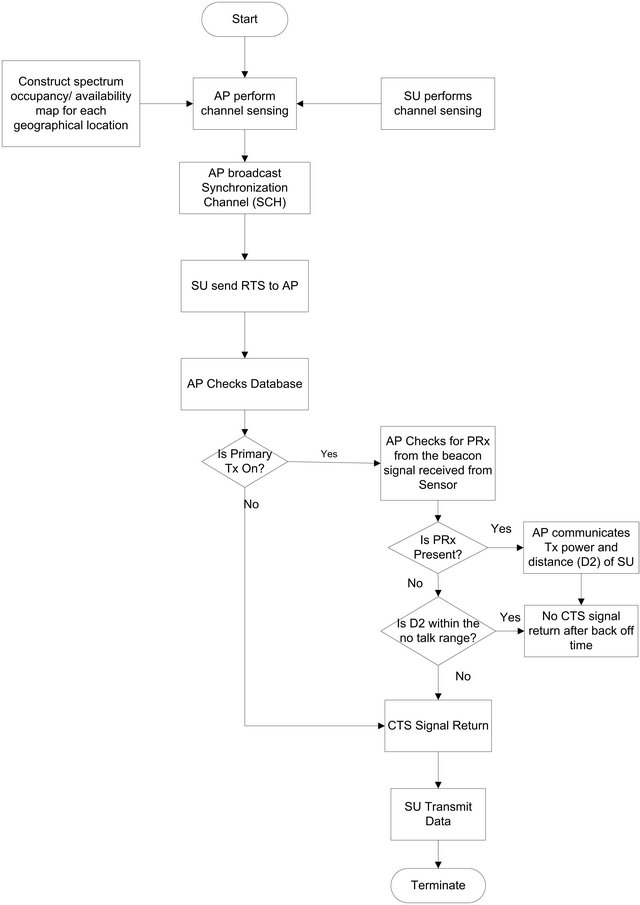
Figure 6. Flow chart channel access mechanism.
on the signal from the primary transmitter and detects the presence of the primary receiver directly.
The leakage primary receiver power may be up to −90 dBm [21]. Memory sensors could be attached to the primary receivers in order to improve sensing performance. The sensing can be carried out by allowing the sensor will send a beacon signal, and this needs to be detected at the AP. This would help to indicating when of the receiver is ON/OFF. The beacon signal is very useful and the AP could compute the sensing of the locations of the primary users and using this information to determine when the secondary users would transmit, this would grantee that cognitive network would not cause severe interference that would degrade the signal-to-interference ratio at the primary receivers. However, for distributed access, the secondary user makes decisions on spectrum access independently and autonomously without any central controller but the cognitive radio transceivers of the secondary user in a distributed access require greater computational resources than that of centralized access.
4. Simulation Parameters
We study the performance of a cognitive radio network by studying the interference that occurs during the interaction of primary and secondary transmitters. The interference affects the delay performance of the network. We study the impact the delay would have on the network throughput using OPNET version 14.5 to simulate the network performance. The network model assumes a network area of 4 km × 4 km with four wireless local area network (WLAN) nodes, the primary transmitter, primary receiver, access point and the secondary user as shown in Figure 2. We run all the simulations for maximum of 300 s depending on the scenario. We also considered both the centralised and distributed access scheme has been considered. The data rate for each user is 11 Mbps and the packet inter arrival rate follows the exponential distribution with a mean value of 1000 packets/sec. The packet size is also an exponential distribution with a mean value of 1024 bytes. Since the packet size is below the 2034 bytes limit, fragmentation is not needed. Direct sequence spread spectrum (DSSS) is used for both users. The channel access mechanism is based on the CSMA/CA MAC protocol and the IEEE 802.11 b and the TDMA. Detail simulation parameters are shown in Table 1.
Defining the White Space
In this paper, a spectrum hole (White Space) is the period of time that the primary user is not transmitting and the amount of white space is represented by time. There are
Table 1. Showing simulation parameters.
two (2) main classification of spectrum based on the occupancy [22,23] namely:
1) The Black space: The spectrum that is fully occupied by a primary user and 2) The white space: Unused space or not occupied by a primary users.
A traffic flow control mechanism based on an events based technique is deployed to model the primary user activity to generate an ON/OFF traffic over the period of 300 s, the ON periods are the busy time and the OFF periods are the idle times for secondary access [16]. Figure 7, illustrates the 0/1 (OFF/ON) states, 0 denoting the channel is free (OFF) and 1 denoting the channel is busy (ON) and occupied by the primary user, these 0/1 alternating stages is referred to as the channel usage pattern and the OFF periods represents the spectrum opportunists or spectrum hole commonly known as white space. The secondary user has the ability to detect the OFF times of the primary user and transmit packets over the white space if it is not within the no-talk zone of the primary receiver. The black spaces are not good candidates for dynamic spectrum access as the secondary user will cause severe interference to the primary user which would degrade the minimum SIR at the primary receiver. However, the white spaces can be use for dynamic spectrum access. In this work, we assume all the OFF periods from a primary user transmission are considered as white spaces and can be identified instantaneously. A secondary user can transmit packets within the white space if the period of the white space 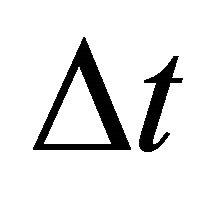 is greater than the sensing period.
is greater than the sensing period.
5. Simulation Results
5.1. Performance in Terms of White Space Utilization Efficiency
Efficiency of use of white space depends on the distribution and duration of white space. TDMA technique was employed to model the primary user activity to generate an ON/OFF traffic over the period of 60 s, the ON periods are the busy time and the OFF periods are the idle times
Figure 7. Traffic generation and channel usage pattern.
for secondary access. Consider a case where a primary user transmitting 10 packets at a data rate of 11 Mbps over the channel. Spectrum opportunities are generated. The spectrum is categorised in to two main phases, the black space when the channel is fully occupied by the primary user and the white space when the channel is free as shown in Figure 8. The bar chart in Figure 8, illustrates alternates ON and OFF periods for the primary transmitter. Observed white space exists at various time slots. There are 20 slots over the period of 60sec which contains the black and white spaces. The slots (9, 15, 21, 30, 36, 42, 48, 51, 57) denotes potential white space for secondary user transmission this shows that there are 9 white spaces. While the remaining slots denotes primary user activity which contains data and control traffic, though it doesn’t precisely signify complete black space but could also contains some white spaces where the spectrum is not fully utilized by the primary user. Within the white spaces, the secondary users are allowed to transmit 10 packets per second over the channel and CSMA/CA access scheme was used as the access scheme. The result is shown in Figure 8. In this scenario, the secondary user transmits during the white spaces except the white space at 57 sec. The secondary user efficiently utilizes the white space and the efficiency of white space utilization can be obtained as follows: 8 out of 9 white spaces that existed from the primary user transmission in Figure 8 are fully occupied by the secondary user in Figure 9. Therefore, this shows that 88.89% of the white spaces are utilized by the secondary user which is the white space utilization efficiency thus; this has proven the effectiveness of the model for exploiting white space.
5.2. Performance in Terms of Delay as Function of Amount of White Space
Delay and packet loss are two major factors that have tremendous impacts on communication networks. Some applications are sensitive to delay while some can tolerate the delay. Figure 10 shows the variation of delay as a
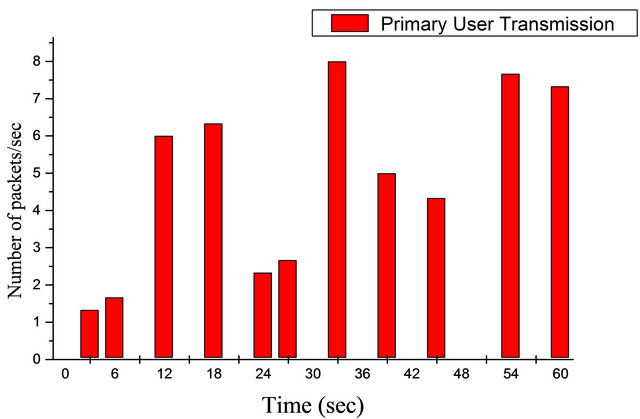
Figure 8. Primary user transmission.
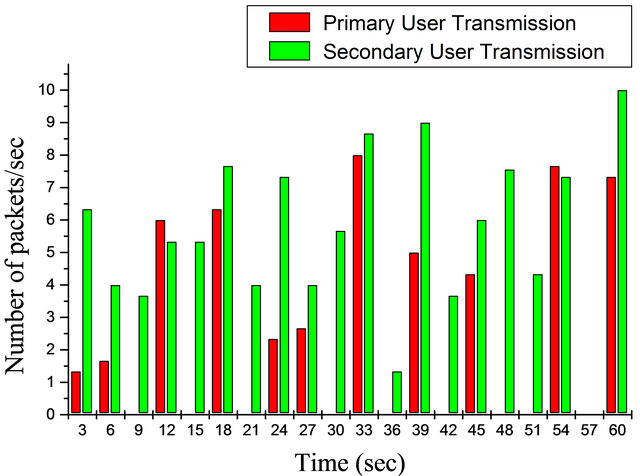
Figure 9. Primary and secondary user transmission.
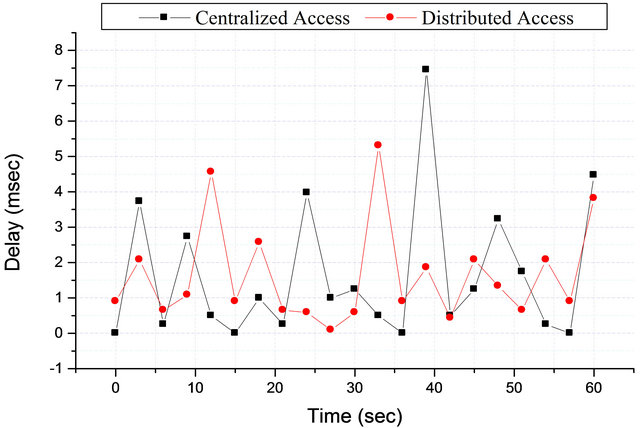
Figure 10. Delay as a function of amount of white space.
function of amount of the white space for a period of 1 min. A time slot RTS/CTS channel access mechanism was used for the secondary user. Once the AP successfully receives an RTS message, and the SU passed the admission control test as described in Section 3.2, the AP immediately transmits a CTS message to the user after a short inter frame space (SIFS) period during the CTS time slot. The rise in time between when the secondary user receives CTS message and when it starts transmitting on the channel accounts for the delay at that instant of time. The distribution of delay at different time slots (White Space) gives the delay as a function of the amount of white space. Figure 10 shows variation in delay for both centralise and distributed access schemes, the least been zero when no delay is experienced and the largest is 7.5 milliseconds which occurred at delay around 39 sec. This delay could be as the results of packets loss due to interference from the primary user transmission: the secondary user is transmitting and suddenly the primary user resumes transmission as such this could interfere with the secondary user transmission and causes some packets loss which would results in retransmission and add delay on to the user. At 57 sec no delay is experienced as the secondary user does not transmit any packets within the white space. The average delays experienced for centralized and distributed access are 1.9 ms and 1.2 ms respectively.
5.3. Effects of Arrival Rates on Delay
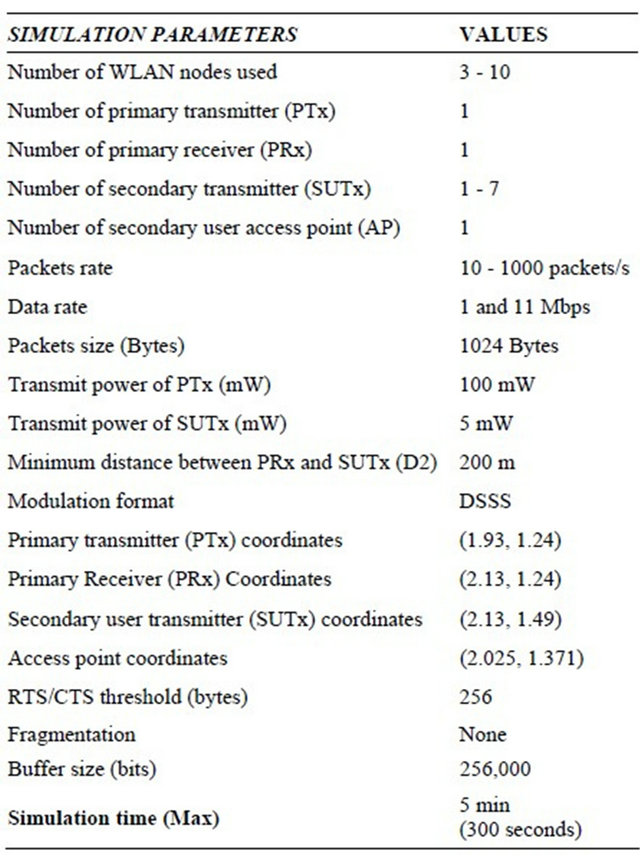
The effects of packets arrival rates on the delay have been investigated. In this scenario, infrastructure based cognitive radio is considered, the simulation was performed using packet inter arrival rates ![]() of 0.1, 0.01 and 0.001 which follow an exponential distribution with a mean value of
of 0.1, 0.01 and 0.001 which follow an exponential distribution with a mean value of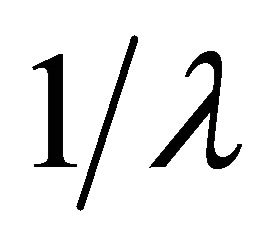 , corresponding to 10, 100 and 1000 packets/s respectively. Fixed packet size was used which also follows an exponential distribution with a mean value of 1024 Bytes at a data rate of 11 Mbps. Figure 11 shows the variation of delay as a function of amount of the white space for different packet arrival rates for the period of 1 min (60 sec).
, corresponding to 10, 100 and 1000 packets/s respectively. Fixed packet size was used which also follows an exponential distribution with a mean value of 1024 Bytes at a data rate of 11 Mbps. Figure 11 shows the variation of delay as a function of amount of the white space for different packet arrival rates for the period of 1 min (60 sec).
In Figure 11, when the SU is transmitting 10 packets/ sec, the variability of the delay follows the same trends as in Figure 10. The maximum peak delay is 43.19 ms when the secondary user is transmitting 100 packets in every second and rises to a maximum of 269 ms when the arrival rate is 1000 packets/s. The arrival rate accounts for the amounts of packets generated and injected into the channel every second within the white space. The sudden increase in delay from 43.19 ms to 269 ms was the results of some packets lost due to buffer overflow that could leads to retransmission and add delay on to the user. To investigate the performance of the effects of delay on delay sensitive applications such as VOIP, the average delay over the period of 5 min (300 sec) as a function of packets arrival rates was evaluated results shown in Figure 12.
Figure 12 shows the average delay as a function of packets arrival rates, it shows that the delay increases as the amount of packets generated increases. An average delay of about 1.9 ms was measured when the secondary user is transmitting 10 packets/s and this increase drasticcally to 17 ms for packets arrival rate of 100. A maximum average delay of 95 ms was measured when the secondary user is transmitting 1000 packets/s this is still within an acceptable delay range of 1 - 150 ms for VOIP call [24].
5.4. Delay as Function of the Number of Secondary Users
Dynamic spectrum access network is aiming to bring broadband access to hard-to-reach low population density areas thereby utilizing unused spectrum allocated to the television broadcast service on a non interfering basis. A minimum of 90 subscribers are to be served and a total of 4500 subscribers per coverage area [25]. We have
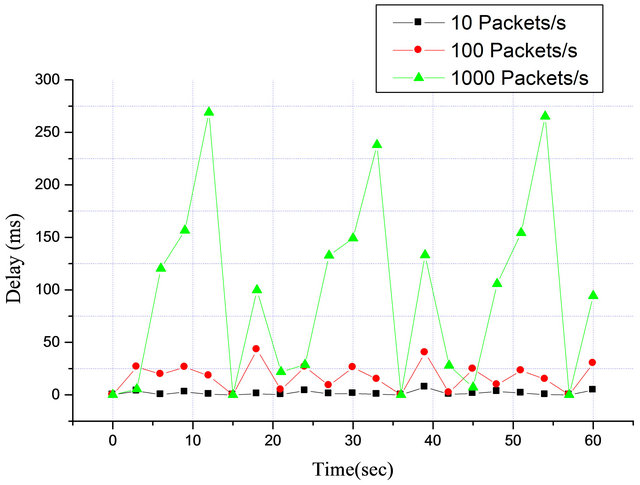
Figure 11. Variation of delay as a function of amount of the white space for different packet arrival rates for the period of 1 min (60 sec).
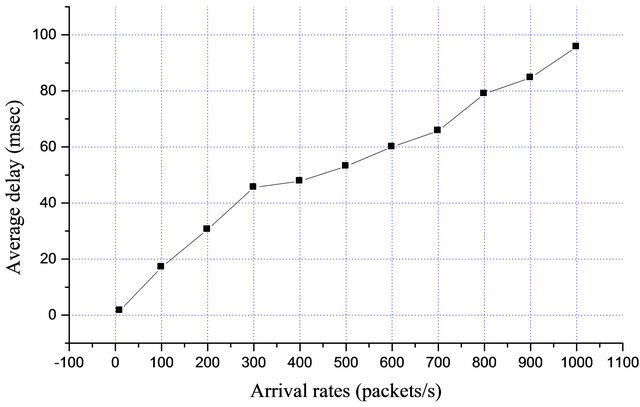
Figure 12. Average delay with packets arrival rates.
investigated delay as function of amount of the white spaces for one primary user and one secondary user, and an average delay of 1.9 ms was experienced by the secondary user for centralized dynamic spectrum access. The effect of the number of secondary users on delay has also been studied the result is shown in Figure 13.
In Figure 13, the average delay remain the same 1.9 ms when only one secondary user is accessing the white space, the delay increases to 2.33 ms and 4.24 ms when two and six secondary users are on the network respectively, its indicating that the secondary user experiences extra 2.34 ms delay when five more secondary users join the network. This shows that delay increases with increasing number of secondary users. In this case, the request from each secondary user is buffered at the AP before undergoing the admission control test, the processing rate decrease with increase in buffer size which would subsequently add delay onto the user.
6. Conclusion
The opening up of the TV white space should allow
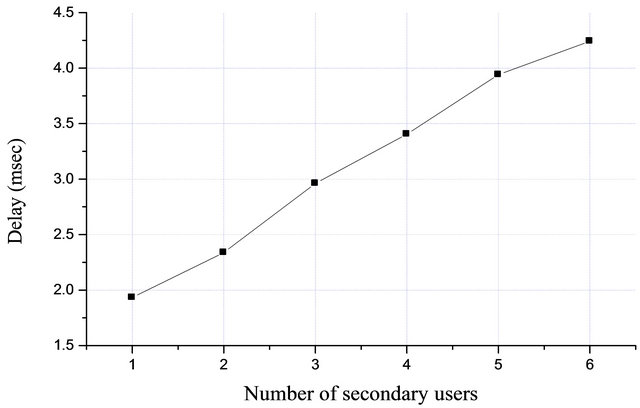
Figure 13. Average of delay experienced by the secondary user as a function of the number of secondary users.
secondary access to the spectrum. We proposed the implementation of a cognitive wireless system using an efficient MAC protocol for DSA. The proposed system examined the problem of the hidden node system and we proposed a solution. In this paper, a hybrid access scheme based on CSMA/CA and TDMA MAC protocols for use in the TV bands is described and the performance of the scheme in terms of delay and white space utilization is evaluated. Analysis of the results shows that, the scheme protects the primary user from harmful Interference from the secondary user. It was also found that, packets arrival rates, data rates and the number of secondary users have significant effects on delay.
REFERENCES
- M. A. McHenry, P. A. Tenhula, P. A. McCloskey, D. A. Roberson and C. S. Hood, “Chicago Spectrum Occupancy Measurements and Analysis and a Long Term Studies Proposal,” 2005. http://www.wtapas.org/final-papers/ChicagoSpectrum-McHenry-Session-I-1.pdf
- W. A. Check, A. Scott, S. L. Mace, D. L. Brenner and D. Nicol, “Unlicensed Operation in TV Broadcast Bands,” Report and Order Memorandum Opinion FCC 10-174, 2004. http://www.google.co.uk/url?sa=t&rct=j&q=unilicensed%20operation%20in%20the%20tv%20broadcast%20bands&source=web&cd=1&ved=0CCcQFjAA&url=http%3A%2F%2Fwww.ncta.com%2FDocumentBinary.aspx%3Fid%3D151&ei=4d8WT9urM-r44QSx98iTBA&usg=AFQjCNHyo2NO15jeifSLvITxboJ_7EAKVA&sig2=j6NFMVF-UpXK9DmoujBOIQ&cad=rja
- Office of Communications, “Digital Dividend: Cognitive Access, Statement Licence-Exempting Cognitive Devices Using Interleaved Spectrum,” 2009. http://stakeholders.ofcom.org.uk/binaries/consultations/cognitive/statement/statement.pdf
- Nigerian Communications Commission, “Commercial Frequency Management Policy, Administrative Procedures and Technical Guidelines,” 2007. http://www.google.co.uk/url?sa=t&rct=j&q=&esrc=s&source=web&cd=2&ved=0CDsQFjAB&url=http%3A%2F%2Fwww.ncc.gov.ng%2Findex.php%3Foption%3Dcom_docman%26task%3Ddoc_download%26gid%3D137%26Itemid%3D&ei=tPz6ULeQLunG0QXo5oHgDA&usg=AFQjCNFCo9gKnxGSoTmScqyL72v3kb9q7w&bvm=bv.41248874,d.d2k&cad=rja
- Federal Communications Commission, “FCC Officially Frees TV White Space Spectrum,” 2012. http://news.cnet.com/8301-30686_3-20017435-266.html
- C. Ghosh, S. Roy and D. Cavalcanti, “Coexistence Challenges for Heterogeneous Cognitive Wireless Networks in TV White Spaces,” IEEE Wireless Communications, Vol. 18, No. 4, 2011, pp. 22-31.
- C. Cormio and K. R. Chowdhury, “A Survey on MAC Protocols for Cognitive Radio Networks,” Ad Hoc Networks, Vol. 7, No. 7, 2009, pp. 1315-1329 doi:10.1016/j.adhoc.2009.01.002
- I. F. Akyildiz, W. Y. Lee and K. R. L. Chowdhury, “Cognitive Radio Ad Hoc Networks,” Ad Hoc Networks, Vol. 7, No. 5, 2009, pp. 810-836. doi:10.1016/j.adhoc.2009.01.001
- R. Pinyi, W. Yichen, D. Qinghe and X. Jing, “A Survey on Dynamic Spectrum Access Protocols for Distributed Cognitive Wireless Networks,” EURASIP Journal on Wireless Communications and Networking, Vol. 2012, 2012, p. 60. doi:10.1186/1687-1499-2012-60
- S. Geirhofer, T. Lang and B. M. Sadler, “Interference-Aware OFDMA Resource Allocation: A Predictive Approach,” IEEE Military Communications Conference, San Diego, 16-19 November 2008, pp. 1-7.
- P. Phunchongharn, E. Hossain, D. Niyato and S. Camorlinga, “A Cognitive Radio System for E-Health Applications in a Hospital Environment,” IEEE Wireless Communications, Vol. 17, No. 1, 2010, pp. 20-28.
- G. Auer, H. Haas and P. Omiyi, “Interference Aware Medium Access for Dynamic Spectrum Sharing,” 2nd IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Dublin, 17-20 April 2007, pp. 399-402.
- Y. Wang, P. Ren and G. Wu, “A Throughput-Aimed MAC Protocol with QoS Provision for Cognitive Ad Hoc Networks,” IEICE Transactions on Communications, Vol. E93- B, No. 6, pp. 1426-1429. doi:10.1587/transcom.E93.B.1426
- G. N. Iyer and Y. C. Lim, “Efficient Multi-Channel MAC Protocol and Channel Allocation Schemes for TDMA Based Cognitive Radio Networks,” International Conference on Communications and Signal Processing (ICCSP), Kerala, 10-12 February 2011, pp. 394-398.
- N. Faruk, M. Ali and M. I. Gumel, “Interference Mitigation MAC Protocol for Cognitive Radio Networks,” Wireless Engineering and Technology, Vol. 3, No. 2, 2012, pp 63-71.
- R. Tandra, A. Sahai and V. Veeravilla, “Unified SpaceTime Metrics to Evaluate Spectrum Sensing,” IEEE Wireless Communication Magazine, Vol. 49, No. 3, 2011, pp. 54-61.
- A. F. Molisch, L. J. Greenstein and M. Shafi, “Propagation Issues for Cognitive Radio,” Proceedings of the IEEE, Vol. 97, No. 5, 2009, pp. 787-804. doi:10.1109/JPROC.2009.2015704
- A. Mitra, “Lecture Notes on Mobile Communication,” 2012. http://www.iitg.ernet.in/scifac/qip/public_html/cd_cell/EC632.pdf
- P. Papadimitratos, S. Sankaranarayanan and A. Mishra, “A Bandwidth Sharing Approach to Improve Licensed Spectrum Utilization,” IEEE Communications Magazine, Vol. 43, No. 12, 2005, pp. S10-S14. doi:10.1109/MCOM.2005.1561918
- B. Wild and K. Ramchandran, “Detecting Primary Receivers for Cognitive Radio Applications,” 1st IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Baltimore, 8-11 November 2005, pp.124-130. http://www.eecs.berkeley.edu/~dtse/3r_ben_dyspan05.pdf
- S. M. Weiss, R. D. Weller and S. D. Driscol, “New Measurements and Predictions of UHF Television Receiver Local Oscillator Radiation Interference,” Merrill Weiss Group Metuchen, 2006. http://h-e.com/sites/default/files/sites/default/files/tech_docs/rw_bts03.pdf
- T. Rahul, S. M. Mishra and A. Sahai, “What Is a Spectrum Hole and What Does It Take to Recognize One?” http://www.eecs.berkeley.edu/~sahai/Papers/SpectrumHolesProcIEEE.pdf
- R. Tobias, C. Kloeck and F K. Jondral, “A Cognitive Approach to the Detection of Spectrum Holes in Wireless Networks,” 4th IEEE Proceedings of Consumer Communications and Networking Conference, Las Vegas, 11-13 January 2007, pp. 1118-1122.
- L. Chris and S. Pickavance, “QoS Requirements for Voice, Video, and Data,” Selecting MPLS VPN Services, Cisco Press, 2006. http://www.informit.com/articles/article.aspx?p=471096&seqNum=6
- I. F. Akyildiz, et al., “Next Generation/Dynamic Spectrum Access/Cognitive Radio Wireless Networks: A Survey,” Computer Networks, Vol. 50, No. 13, 2006, pp. 2127- 2159. doi:10.1016/j.comnet.2006.05.001

