Journal of Information Security
Vol.06 No.01(2015), Article ID:52952,6 pages
10.4236/jis.2015.61003
Externalities and the Magnitude of Cyber security Underinvestment by Private Sector Firms: A Modification of the Gordon-Loeb Model
Lawrence A. Gordon1, Martin P. Loeb1, William Lucyshyn2, Lei Zhou1
1Robert H. Smith School of Business, University of Maryland, College Park, USA
2School of Public Policy, University of Maryland, University of Maryland, College Park, USA
Email: lgordon@rhsmith.umd.edu, mloeb@rhsmith.umd.edu, lucyshyn@umd.edu, lzhou@rhsmith.umd.edu
Copyright © 2015 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 23 September 2014; revised 20 October 2014; accepted 14 November 2014
ABSTRACT
Cyber security breaches inflict costs to consumers and businesses. The possibility also exists that a cyber security breach may shut down an entire critical infrastructure industry, putting a nation’s whole economy and national defense at risk. Hence, the issue of cyber security investment has risen to the top of the agenda of business and government executives. This paper examines how the existence of well-recognized externalities changes the maximum a firm should, from a social welfare perspective, invest in cyber security activities. By extending the cyber security investment model of Gordon and Loeb [1] to incorporate externalities, we show that the firm’s social optimal investment in cyber security increases by no more than 37% of the expected externality loss.
Keywords:
Economics of Information Security, Cyber security Investment

1. Introduction
With economic activity and national defense heavily and increasingly dependent on networked computer systems, cyber security issues continue to draw increasing attention by the media, as well as by executives at the highest levels of government, industry, and nonprofit organizations.1 A key reason for this increasing attention on cyber security issues by governments around the world is the eminent threat posed by cyber security breaches to a nation’s national defense and the nation’s economic strength [2] .
Firms in the private sector of many countries own a large share of critical infrastructure assets.2 Hence, cyber security breaches in private sector firms could cause a major disruption of a critical infrastructure industry (e.g., delivery of electricity), resulting in massive losses throughout the economy, putting the defense of the nation at risk. Moreover, the cyber security activities of a given firm affect not only the probability of that firm suffering a cyber security breach, but also the probability that other firms (and individuals) suffer cyber security breaches. As one example, consider a firm that is not adequately protected against malware that infects the firm’s computer system and, although undetected, use that firm’s computer as part of a botnet to attack other firms. Since there is no practical way for a firm to be made liable for the entirety of losses from breaches to other firms caused by the vulnerabilities to its own computer systems, complete reliance on market mechanisms to overcome the externalities problem breaks down (i.e., using the terminology of economics, there are market failures). In fact, it is well known that in the absence of government incentives and/or regulations (hereafter incentives/regulations) firms will under invest in cyber security activities relative to the quantity that maximizes social welfare (e.g., [5] -[8] ). Thus, governments have an interest in providing incentives/regulations to firms to invest in cyber security activities at a level that takes into account not only the private losses incurred by firms from breaches of cyber security, but also the costs of externalities resulting from such beaches.3,4
A prelude to developing incentives/regulations that take into consideration the costs of externalities, as well as the private costs, is an understanding of the relationship between the magnitude of externalities and the magnitude of cyber security underinvestment. Thus, the objective of this paper is to investigate the magnitude of under- investment in cyber security activities by a private sector firm that considers only its private costs and benefits without regard to externalities. This investigation will take place in the context of the influential Gordon-Loeb Model presented in [1] , hereafter referred to as GL Model, for deriving the appropriate level of cyber security investment.5 Earlier work, while recognizing that externalities results in underinvestment, has not sought to characterize the specific degree of underinvestment.
The primary contribution of this paper is to show how the existence of externalities changes the GL rule for the maximum a firm should, from a social welfare perspective, invest in cyber security activities. By analyzing the degree to which ignoring externalities causes underinvestment by firms in the absence of government regulations and incentives, the paper provides a basis for future examinations of potential actions designed to counteract cyber security underinvestment by private sector firms.
The remainder of this paper will proceed as follows. In the next, second, section of the paper we review the influential GL Model for making information security (cyber security) investments, and the subsequent literature dealing with the model. In the third section, we examine the effect of externalities on the optimal level of cyber security investment among private sector firms. We start by analyzing a specific example and then provide a general result characterizing the effect of externalities on the upper bound of a firm’s optimal level of cyber security investment. The fourth, and final, section of this paper will present some concluding comments.
2. GL Model Literature
In order to investigate the magnitude of a firm’s underinvestment (from a social welfare perspective), we analyze and extend the GL Model. Considering only the firm’s private cost and benefits, GL characterized a firm’s optimal amount to invest in cyber security activities. In doing so, they defined a security breach function that captured the relationship between the level of cyber security activity expenditures and the probability of a cyber security breach. As such, GL were able to address the fundamental question of particular interest to organizations concerning how much to spend on cyber security activities.6 GL present a single period economic model to examine the problem of a risk-neutral firm selecting the optimal level of expenditures on cyber security activities. The GL Model examines how the firm’s optimal level of cyber security expenditures, denoted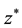 , varies with two parameters: 1)
, varies with two parameters: 1)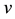 , the probability that a cyber security attack will be successful in the absence of any cyber security expenditures, and 2)
, the probability that a cyber security attack will be successful in the absence of any cyber security expenditures, and 2)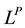 , the expected loss to the firm if the attack is successful. The model is briefly summarized below.
, the expected loss to the firm if the attack is successful. The model is briefly summarized below.
Denote
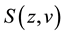 as the firm’s security breach function, defined as the probability that an information security breach occurs and where
as the firm’s security breach function, defined as the probability that an information security breach occurs and where
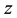 is the firm’s monetary investments in cyber security and
is the firm’s monetary investments in cyber security and
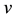
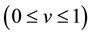 represents firm’s the underlying vulnerability to security breaches. GL postulate that the security breach function is twice continuously differentiable and meets the following five regularity conditions: 1) for all
represents firm’s the underlying vulnerability to security breaches. GL postulate that the security breach function is twice continuously differentiable and meets the following five regularity conditions: 1) for all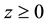 ,
,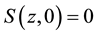 ; 2) for all
; 2) for all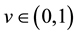 ,
,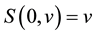 ; 3) for all
; 3) for all
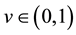 and for all
and for all
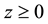 and
and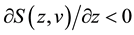 ; 4) for all
; 4) for all
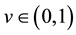 and for all
and for all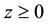 ,
,




When making the security investment decision, the firm would choose an investment level


and needs to satisfy the following condition:

For security breach functions meeting the aforementioned five regularity conditions, GL provide some general results concerning the relation between the optimal level of cyber security investment,




and

The optimal investment in information security is always less than or equal to



Willemson [19] provided a method for constructing a security breach function meeting all the assumptions of GL for which the optimal level of investment could be made to be arbitrarily close to 50% of the expected loss. Furthermore, by relaxing the GL assumption that the security breach function is continuously twice differentiable, [19] demonstrated that security breach functions could be constructed such that the optimal cyber security investment is arbitrarily close to the expected loss.
While the result of [19] appeared to severely limit the generality of the




3. Modifying the GL Model to Incorporate Externalities
In modeling a firm’s selection of the optimal amount to invest in information security, GL only considered the private costs to be borne by a firm that result from an information (cyber) security breach. The private costs of a breach, denoted by

There are good reasons, however, to believe that expected legal judgments and settlements would not fully internalize the externalities associated with an information security breach. For example, suppose a security breach results in malware that allows an attacker to gain complete control over the affected computer. That firm’s computer can then be controlled remotely to connect back to a central server, and become part of a network of compromised computers or “botnet” (often just called a “bot”). This network can be used for a variety of malicious purposes, such as conducting a distributed denial of service (DDOS) attack. The DDOS attack may well cause substantial losses to other organizations, yet the contribution of one computer (or one firm’s computers) towards the overall loss would be so small that the threat of legal repercussions to the firm owning the compromised computer(s) would be insignificant. Similarly, in addition to the cost of lost sales faced by the firm victimized by a DDOS attack, customers may face non-pecuniary costs in lost time and frustration in attempting to access the attacked firm’s website. While the costs to an individual customer may be small and difficult to detect and measure, the aggregate costs to all customers could be substantial. Still, because the individual losses are small, legal action spurred by these losses would not likely be taken on behalf of these customers. In addition, even if legal actions were to occur, where the final responsibility for covering these costs rests is unclear. The extension of the GL Model that follows is an attempt to show the impact of considering these, as well as other, externalities, on the adequacy of cyber security investments.
Let



vate loss plus the externality costs (i.e.,
The GL Model can then be easily extended to incorporate the externalities. The social optimal level of investment for the firm, denoted

so that


By comparing (6) and (2), and assuming




In order to examine the possible magnitude of a firm’s under investment in information security relative to the amount that maximizes social welfare, we first examine security breach function of the class I type specified by (3). Then, the firm’s (private) optimal investment in information security is given by (GL equation (6)):

Now suppose for the firm’s initial probability of an information security breach




The preceding discussion illustrates that in the presence of externalities, social costs diverge from private costs resulting in underinvestment by the firm. Table 1 provides additional data on how underinvestment percentage changes with externality costs for the specified example.
The following proposition, a generalization of the GL rule, shows how externalities affect the magnitude of a firm’s maximum socially optimal investment in cyber security.
Proposition 1: Suppose the security breach probability function satisfies regularity conditions (1), (2), (3), (4’) and (5). Denote



Proof: The maximum socially optimal amount is found by substituting




The desired result, inequality (8), follows since
Notice that for the special case where there are no externalities,

Table 1. Relationship between externalities and underinvestment in cybersecurity for security breach probability function
Table 2. Maximum social optimal investment as externalities vary.
Since most firms in the private sector look only at their private costs of security breaches, it is rational to expect them to under invest in cyber security activities relative to the social optimal. Accordingly, in order to move towards socially optimal levels of cyber security investments, there is a compelling argument for governments (or some other entity focusing on increasing social welfare) to explore a variety of regulations and/or incentives that are designed to get private sector firms to increase their cyber security investments.
4. Concluding Comments
The primary objective of this paper has been to extend the GL Model for deriving the optimal level of investment in cyber security activities. This extension focused on examining the impact of considering the costs associated with the externalities of cyber security breaches (i.e., spill-over effects, of cyber security breaches to other organizations and individuals), in addition to private costs (i.e., the costs to the individual organizations experiencing the cyber security breaches), on a private sector firm’s optimal level of cyber security investment level as viewed from a social welfare perspective. For a risk-neutral firm, under specified regularity conditions, we show that the firm’s social optimal investment in cyber security increases by no more than 37% of the expected externality loss. Unless private sector firms consider the costs of breaches associated with externalities, in addition to the private costs resulting from breaches, underinvestment in cyber security activities is essentially a given. Thus, cyber security underinvestment poses a serious threat to the national security and to the economic prosperity of a nation. Accordingly, governments around the world are justified in considering regulations and/or incentives designed to increase cyber security investments by private sector firms.
In the U.S. there is a general preference for developing market-based incentive mechanisms rather than new regulations to get private sector firms to increase their investment on cyber security activities. The efficacy of such an approach has, to date, been problematic. Indeed, the problems associated with successfully developing and implementing such incentives have led many in the U.S. to call for regulations requiring private sector firms to invest enough into cyber security activities to cover externalities as well as private sector costs.9 In other countries, which are more heavily government controlled, regulations requiring private sector firms to increase their investment in cyber security activities to cover externalities (as well as private costs) may well be the clearly preferred method for handling the cyber security underinvestment concern.
Acknowledgements
This research has been supported by the United States Department of Homeland Security (DHS) Science and Technology Directorate, the Netherlands National Cyber Security Centre (NCSC) and Sweden MSB (Myndighetenförsamhällsskyddochberedskap)―Swedish Civil Contingencies Agency.
References
- Gordon, L.A. and Loeb, M.P. (2002) The Economics of Information Security Investment. ACM Transactions on Information System Security, 5, 438-457. http://dx.doi.org/10.1145/581271.581274
- U.S. Department of Homeland Security (2013) Executive Order 1636: Improving Critical Infrastructure, Department of Homeland Security Integrated Task Force, Incentives Study. Washington DC.
- Presidential Executive Order 13636 (2013) Improving Critical Infrastructure Cybersecurity. Federal Registrar, 78, 11739-11743. https://www.federalregister.gov/articles/2013/02/19/2013-03915/improving-critical-infrastructure-cybersecurity
- Presidential Policy Directive/PPD-21 (2013) Critical Infrastructure Security and Resilience. http://www.whitehouse.gov/the-press-office/2013/02/12/presidential-policy-directive-critical-infrastructure-security-and-resil
- Varian, H. (2004) System Reliability and Free Riding. In Camp, L. and Lewis, S., Eds., Economics of Information Security, Springer US, 1-15. http://dx.doi.org/10.1007/1-4020-8090-5_1
- Gordon, L.A., Loeb, M.P. and Lucyshyn, W. (2003) Sharing Information on Computer Systems Security: An Economic Analysis. Journal of Accounting and Public Policy, 22, 461-485. http://dx.doi.org/10.1016/j.jaccpubpol.2003.09.001
- Kunreuther, H. and Heal, G. (2003) Interdependent Security. Journal of Risk and Uncertainty, 26, 231-249.
- Lelarge, M. (2012) Coordination in Network Security Games: A Monotone Comparative Statics Approach. IEEE Journal on Selected Areas in Communications, 30, 2210-2219.
- Treasury Department Report to the President on Cybersecurity Incentives Pursuant to Executive Order 13636. (2013). http://www.treasury.gov/press-center/Documents/Supporting Analysis Treasury Report to the President on Cybersecurity Incentives_FINAL.pdf
- U.S. Department of Homeland Security (2013) Executive Order 13636: Improving Critical Infrastructure, Department of Homeland Security Integrated Task Force, Incentives Study Analytic Report. http://www.dhs.gov/sites/default/files/publications/dhs-eo13636-analytic-report-cybersecurity-incentives-study.pdf
- Böhme, R. (2010) Security Metrics and Security Investment Models. In: Echizen, I., Kunihiro, N. and Sasaki, R., Eds., Advances in Information and Computer Security, Springer-Verlag, Berlin, Heidelberg, 10-24. http://dx.doi.org/10.1007/978-3-642-16825-3_2
- Campbell, K., Gordon, L.A., Loeb, M.P. and Zhou, L. (2003) The Economic Cost of Publicly Announced Information Security Breaches: Empirical Evidence from the Stock Market. Journal of Computer Security, 11, 431-448.
- Cavusoglu, H., Mishra, B. and Raghunathan, S. (2004) The Effect of Internet Security Breach Announcements on Market Value: Capital Market Reactions for Breached Firms and Internet Security Developers. International Journal of Electronic Commerce, 9, 69-104.
- Gordon, L.A., Loeb, M.P. and Zhou, L. (2011) The Impact of Information Security Breaches: Has There Been a Downward Shift in Cost? Journal of Computer Security, 19, 33-56.
- Gal-Or, E. and Ghose, A. (2005) The Economic Incentives for Sharing Security Information. Information Systems Research, 16, 186-208. http://dx.doi.org/10.1287/isre.1050.0053
- Hausken, K. (2007) Information Sharing among Firms and Cyber Attacks. Journal of Accounting and Public Policy, 26, 639-688. http://dx.doi.org/10.1016/j.jaccpubpol.2007.10.001
- Gansler, J.S. and Lucyshyn, W. (2005) Improving the Security of Financial Management Systems: What Are We to Do? Journal of Accounting and Public Policy, 24, 1-9. http://dx.doi.org/10.1016/j.jaccpubpol.2004.12.001
- Gordon, L.A., Loeb, M.P. and Sohail, T. (2010) Market Value of Voluntary Disclosures Concerning Information Security. MIS Quarterly, 34, 567-594.
- Willemson, J. (2006) On the Gordon & Loeb Model for Information Security Investment. The Fifth Workshop on the Economics of Information Security (WEIS), University of Cambridge, 26-28 June. http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.60.9931&rep=rep1&type=pdf
- Baryshnikov, Y. (2012) IT Security Investment and Gordon-Loeb’s 1/e Rule. 2012 Workshop on Economics and Information Security, Berlin, 25-26 June. http://weis2012.econinfosec.org/papers/Baryshnikov_WEIS2012.pdf
NOTES
1For purposes of this paper, we use the term cyber security to mean the protection of information that is transmitted via any computer network, including the Internet. In addition, for the purpose of this paper, the terms cyber security and information security are considered to be synonymous.
2In the U.S., for example, a figure of 85% has been used in various government reports concerning the portion of U.S. critical infrastructure assets owned by firms in the private sector (e.g., see http://www.dhs.gov/critical-infrastructure-sector-partnerships). The importance of the critical infrastructure in the U.S. is highlighted by [3] and [4] .
3For example, see [9] and [10] .
4Although the focus in this paper is on the U.S., the issues addressed in the paper are equally applicable to other countries.
5The GL model is widely cited in the cyber security research literature, with more than 700 Google Scholar citations at the time of this writing and having been featured in both The Wall Street Journal (see http://www.wsj.com/news/articles/SB10001424053111904900904576554762089179984) and Financial Times see http://www.ft.com/cms/s/2/606e0e5a-b345-11e2-b5a5-00144feabdc0.html#axzz2iO8fsZhJ). Böhme [11] writes, “Undoubtedly the most famous security investment model has been proposed by Gordon and Loeb… (p. 11).”
6Some other key questions receiving attention in the literature include (1) what is the economic cost of a cyber security breach? (e.g., [12] , [13] , [14] ), (2) what is the effect of information sharing on cyber security? (e.g., [6] , [15] , [16] ), (3) what strategies should be employed to manage cyber security risks? (e.g., [17] ), and (4) what is the market value impact of disclosing information security activities on the 10-K Reports file with the Securities and Exchange Commission (e.g., [18] ).
7A function


8The combination of externality costs and private costs is what economists refer to as social costs.
9In recent conversations between two of the authors of this paper and several senior executives from large private sector firms, it was clearly noted that, without a formal regulation concerning the investment level of cyber security activities, externalities were unlikely to be adequately considered by U.S. firms.







