Circuits and Systems
Vol.07 No.08(2016), Article ID:67119,8 pages
10.4236/cs.2016.78103
Neural Network Based Normalized Fusion Approaches for Optimized Multimodal Biometric Authentication Algorithm
E. Sujatha1, A. Chilambuchelvan2
1Department of Information Technology, Kings Engineering College, Chennai, India
2Department of Computer Science and Engineering, R.M.D. Engineering College, Chennai, India

Copyright © 2016 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 23 March 2016; accepted 30 April 2016; published 6 June 2016
ABSTRACT
A multimodal biometric system is applied to recognize individuals for authentication using neural networks. In this paper multimodal biometric algorithm is designed by integrating iris, finger vein, palm print and face biometric traits. Normalized score level fusion approach is applied and optimized, encoded for matching decision. It is a multilevel wavelet, phase based fusion algorithm. This robust multimodal biometric algorithm increases the security level, accuracy, reduces memory size and equal error rate and eliminates unimodal biometric algorithm vulnerabilities.
Keywords:
Multimodal Biometrics, Score Level Fusion Approach, Neural Network, Optimization

1. Introduction
Multimodal Biometrics Algorithm is adapted to the application where high level security is required and applied for authentication mode. Multimodal Biometrics is an integration of more than one biometric trait to enhance security. This paper presents a matching algorithm for the person who claims the identity for authentication. Multimodal Biometrics algorithm is more robust and the integration of many unimodal biometrics makes the system high secured. Identifying and Verifying a human being can be done using their physiological and behavioral characteristics. Every individual is identified by: something you possess such as ID card, Smart Card etc., something you know such as PIN, passwords etc., and something unique about you such as biometric traits [1] [2] . Most of the existing security system based on something you possess can be easily lost, stolen, forged, duplicated and something you know security systems are compromised by forgotten, shared, stolen, guessed, hacked and something unique about systems are not easily compromised. Moreover the multimodal biometrics provides more security against vulnerability, spoof of attacks, intra-class variations, inter-class variations, non-universal- ity [1] [2] .
Every year the amount spent for the recovery of passwords is increased. After the twin tower incident on Sep 11, 2011, all realized the need for security [3] . With respect to the characteristics of unimodal biometrics as universality, uniqueness, permanence, measurability, performance, acceptability, circumvention, noise in sensed data, intra-class variations, and distinctiveness. The integration of 4 unimodal biometric makes the system more efficient, robust and secured. Multimodal Biometrics integrates more than one unimodal biometric traits for acquiring high level of security, accuracy and performance efficiency.
2. Proposed Multimodal Biometric Authentication Algorithm
This paper integrates four multimodal biometrics: Iris, Finger Vein, Palm Print and Face [4] . Multimodal biometrics enhance accuracy, security, robust, reliable over unimodal biometric traits. Each biometric recognition algorithm provides score after score level fusion which yields score to be matching module, which is normalized using normalization technique to bring compatibility between different multimodal biometrics and Neural Network technique [5] is adapted for compared with threshold and optimized before with computationally efficient Particle Swarm Optimization [6] [7] and finally authentication of genuine or imposter is identified. Figure 1 shows the proposed multimodal Biometric Authentic algorithm.
2.1. Iris Recognition
Iris recognition is unique and has strong unimodal characteristics in identifying a human being in spite of all security threats. Iris is a Physiological Biometrics. It is done by measuring the distance between pupil the boundary
Figure 1. Architecture diagram of proposed system.
of Iris. It is done by measuring the distance between pupil the boundary of Iris. It is done by measuring the distance between pupil the boundary of Iris. Both inner and outer boundaries are not concentric circles. Preprocessing is done for localization of iris image and is shown in Figure 2. Iris image Edge is detected by Canny Operator, Hough transform [7] [8] . For experimental analysis CASIA (Institute of Automation of the Chinese Academy of Sciences) Database v 2.0 is utilized. The method used to recognize Iris is based on phase, feature, Discrete Cosine Transform (DCT), Hamming Distance (HD) for matching. Gaussian filter is used to smoothen the Iris image [9] - [11] . To eliminate noise in the iris image, mask codes are used. Iris recognition is done based on wavelet packet decomposition of iris images.
Each sub image of iris is represented by wavelet coefficients to generate iris binary code for recognition. Iris recognition module contains segmentation, feature code generation. In segmentation iris localization and normalization is done. In feature code generation phase 64 wavelet packets are generated. The mean energy distribution allows evaluating which packets are used to compute normalized adapted threshold for iris code generation. The energy measure Ei for a wavelet packet sub image Wi can be computed as
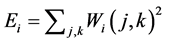 (1)
(1)
In Amsterdam Schiphol Airport (UK) Iris Recognition is used for immigration [12] . “After 200 over billion comparisons, iris recognition is accurate and reliable” by John Daugman. In CASIAV 2.0, 1200 eye images with 60 unique eyes & 20 different images of each unique eye.
2.2. Finger Vein Recognition
Finger Vein recognition is invisible to naked eye, difficult to forge, steal. It is reliable, accurate and unique in identical twins, triplets, quadruplets, quintuplets. Burn, abrasions, cuts do not affect the ridge structure and vein. It can be taken only from live body, so the subject is ensured alive. Preprocessing of Finger vein takes segmentation, enhancement, filtering, thinning. Figure 3 shows the finger Vein Recognition. The median filter is used
Figure 2. Iris recognition.
Figure 3. Finger vein recognition.
for image denoising [13] - [15] . Thinning removes selected foreground pixels from binary code. This evolutionary algorithm calculates local maximum curvatures in cross sectional profiles of a finger vein without affecting the variations in width and brightness of the vein. Phase based Correlation technique is implemented by Fast Fourier Transform, Laplacian of Gaussian. Finger Vein is one of the robust biometric recognition algorithm, and it is more secured.
2.3. Palm Print Recognition
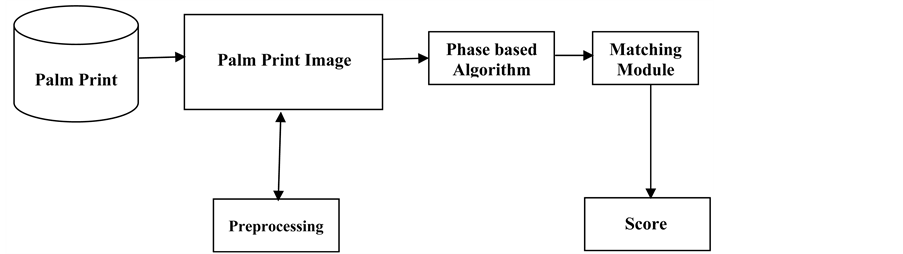
It is Physiological biometric trait. This algorithm uses 2D Discrete Fourier transform in phase based recognition system. The Principal Component Analysis, Local Binary Pattern Histogram hybrid algorithm [5] [16] is used. It is implemented on CASIA (Institute of Automation of the Chinese Academy of Sciences) Database v 2.0. It has high modality user acceptance. It is easy and convenient to integrate with other biometric recognition system. It consumes low resolution of digital camera. PSO is used for optimizing the normalized score. Low pass filter and boundary tracking algorithm is used in preprocessing phase. Palm print Recognition shown in Figure 4 includes the Phase based algorithm, module matching, score and preprocessing. Normalized hamming Distance is applied for matching module. It reduces error rates and improves the speed. It can be employed for high resolution or low resolution images. Low resolution images for civil and commercial applications. The preprocessing is used to set up coordinate’s alignment and segments the images for feature extraction. Preprocessing includes binarizing the palm images, extracting the contour of finger, detecting the key points, establishing a coordination system, extracting the central parts. Matching algorithm is based line approaches. Canny edge operator is used to detect palm lines. Palm print recognition algorithm finally provides score.
2.4. Face Recognition
The methods to recognize face are Principal Component Analysis (PCA), Local Feature Analysis (LFA), Eigen Face Values, Template based recognition, Euclidean distance, Bunch graph matching [17] - [19] . Face Recognition is implemented in Sydney Airport, Hongkong Vehicle Clearance. This algorithm is designed using neural network based recognition algorithm such as Gabor filters. Image preprocessing is done to eliminate the background and foreground image. Image segmentation shown in Figure 5 is done for binary code generation. It is
Figure 4. Palm print recognition.
Figure 5. Face recognition.
one of the commercialized biometric recognition algorithm. When is integrated with other biometric traits, it performs well. It is very fast in recognition. It is implemented on CASIA (Institute of Automation of the Chinese Academy of Sciences) Database v 2.0.
2.5. Normalization
Normalization brings compatibility between multimodal biometric traits. Individual traits are not homogeneous. Gray scale matrix are used as training data for neural networks. Cartesian polar coordinates are used in normalization. After normalization the scores becomes convenient transformation for fusion.
2.6. Fusion Rules
Score level fusion rules are constructed in order to achieve more accuracy and complexity for other vulnerabilities. It consumes lower communication bandwidth. It is easy to process and provides optimal performance. Bayesian Classifier based fusion rules are constructed. There are two types of rules exists: AND and OR. It can be easily combined with other multimodal biometrics and also accessible. Table 1 illustrates the threshold values and the corresponding FAR and FRR
2.7. Optimization
At all levels this optimization is adapted to gain best solution. Particle Swarm Optimization is applied for reducing the search space. It is proven that more efficient compared with Genetic Algorithm. PSO is the combination of deterministic and probabilistic rules. Computational cost is affordable when compared to Genetic algorithm. Neural Network is adapted for the nature of adaptive learning, self-organization, and fault tolerance. Finger vain Recognition, threshold values and the respective FAR and FRR is shown in Table 2.
2.8. Research Issues
・ Integration of multimodal biometric is challenging. So it leads to complexity in memory and computations.
・ It is very hard to implement in real time since different sensor devices compatibility and instances of the devices must match in parallel processing time.
・ Selecting the multimodal biometric trait for considering the scenario is also challenging.
2.9. Performance Metrics
2.9.1. FAR-False Acceptance Rate
It measures the ratio of imposters are false accepted. If the threshold is high, low FAR is achieved. It is clear from Table 3 that if the threshold is high, low FAR is achieved and if the threshold is low, high FAR is achieved
Table 1. Iris recognition.
Table 2. Finger vein recognition.
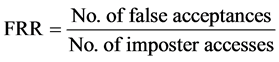 (2)
(2)

2.9.2. FRR-False Rejection Rate
It is determined by the number of Genuines are falsely rejected. If the threshold falls low, FRR rate is high. Table 4 illustrates the False Rejection Rate in terms of the threshold values.
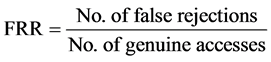 (3)
(3)
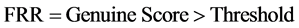
2.9.3. ERR-Equal Error Rate
It is calculated by the formulae when FAR is equal to FRR. If the devices are accurate when ERR is low. Lower ERR indicates better performance. The proposed fusion algorithm is illustrated in Table 5. It compares the individual Iris, Finger Vein, Palm print and Face with the Integrated model.
2.9.4. TER-Total Error Rate
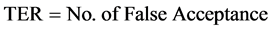 (4)
(4)
3. Experimental Results
Both inner and outer boundaries are not concentric circles. Iris is a Physiological Biometrics. It is done by measuring the distance between pupil the boundary of Iris. Normalized hamming Distance is applied for matching module. It reduces error rates and improves the speed. It can be employed for high resolution or low resolution
Table 3. Palmprint recognition.
Table 4. Face recognition.
Table 5. Proposed fusion algorithm.
images. Low resolution images for civil and commercial applications. The preprocessing is used to set up coordinate’s alignment and segments the images for feature extraction. Preprocessing of Finger vein takes segmentation, enhancement, filtering and thinning. The median filter is used for image denoising. Thinning removes selected foreground pixels from binary code. Fusion image which is the combination of Iris, Finger Vein, Palm print and the Face. Integrated model produces a better FRR when compared with the traditional Iris, Finger Vein, Palm print and Face.
4. Conclusion and Future Work
This paper presents a robust algorithm and secured at multiple levels, efficient by means of optimization technique to meet the performance needs of a multimodal biometric authentication system. Neural Network, Phase based techniques enhances performance and efficiency. Multimodal biometric eliminates demerits of unimodal biometric algorithms. The solution provided is best for authentication algorithm.
The future enhancement of this paper is that the other biometric traits can be considered as Brain and Heart Patterns, DNA, Aging Facial problems.
Acknowledgements
I would like to express my gratitude to the almighty god and visible god Parents who supports morally and my Husband Mr. D. Mohankumar for his motivation and my dear son M. S. Sanjay for his encouragement to pursue my Ph.D. degree.
Cite this paper
E. Sujatha,A. Chilambuchelvan, (2016) Neural Network Based Normalized Fusion Approaches for Optimized Multimodal Biometric Authentication Algorithm. Circuits and Systems,07,1199-1206. doi: 10.4236/cs.2016.78103
References
- 1. Veeramachaneni, K., Osadciw, L.A. and Varshney, P.K. (2005) An Adaptive Multimodal Biometric Management Algorithm. IEEE Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews), 35, 344-356.
- 2. Ross, A. and Jain, A.K. (2003) Information Fusion in Biometrics. Pattern Recognition Letters, 24, 2115-2125.
http://dx.doi.org/10.1016/S0167-8655(03)00079-5 - 3. Woodward Jr., J.D. (2000) Biometrics: Facing up to Terrorism. The Biometrics Consortium Conference, Arlington, February 2000, 362-369.
- 4. Daughman, J. (1988) Complete Discrete 2-D Gabor Transforms by Neural Networks for Image Analysis and Compression. IEEE Transactions on Acoustics, Speech and signal Processing, 36, 1169-1179.
- 5. Daughman, J. (1993) High Confidence Visual Recognition of Persons by a Test of Statistical Independence. IEEE Transactions on Pattern Analysis, 15, 1148-1161.
- 6. Daughman, J. (2004) How Iris Recognition Works. IEEE Transactions on Circuits and Systems for Video Technology, 14, No. 1.
- 7. Liam, L.W., Chekima, A., Fan, L.C. and Dargham, J.A. (2002) Iris Recognition Using Self-Organizing Neural Network. Student Conference on Research and Development, 169-172.
- 8. Bonney, B., Ives, R., Etter, D. and Du, Y.Z. (2004) Iris Pattern Extraction Using Bit Planes and Standard Deviations. Conference Record of the Thirty-Eighth Asilomar Conference on Signals, Systems and Computers, 7-10 November 2004, 582-586.
http://dx.doi.org/10.1109/acssc.2004.1399200 - 9. Lu, C.H. and Lu, Z.Y. (2005) Efficient Iris Recognition by Computing Discriminable Textons. International Conference on Neural Networks and Brain, Beijing, 13-15 October 2005, 1164-1167.
- 10. Wang, J. and Xie, M. (2006) Iris Feature Extraction Based on Wavelet Packet Analysis. International Conference on Communications, Circuits and Systems, Guilin, June 2006, 31-34.
http://dx.doi.org/10.1109/icccas.2006.284579 - 11. Grabowski, K., Sankowski, W., et al. (2006) Iris Recognition Algorithm Optimized for Hardware Implementation. IEEE Symposium on Computational Intelligence and Bioinformatics and Computational Biology, Toronto, 28-29 September 2006, 1-5.
- 12. Kumar, A. and Shen, H.C. (2004) Palm Print Identification Using Palm Codes. Proceedings of the Third International Conference on Image and Graphics, Hong Kong, 18-20 December 2004, 258-261.
http://dx.doi.org/10.1109/ICIG.2004.110 - 13. Li, F., Leung, M.K.H. and Yu, X.Z. (2004) Palmprint Identification Using Hausdorff Distance. IEEE International Workshop on Biomedical Circuits & Systems, 1-3 December 2004, S3/3-S5-8.
- 14. Hong, L., Jain, A.K. and Panikanti, S. (1999) Can Multibiometrics Improve Performance? Proc. AutoID, Summit, NJ, October 1999, 59-64.
- 15. Carlisle, A. and Dozier, G. (2000) Adapting Particle Swarm Optimization to Dynamic Environments. Proceedings of the International conference on Artificial Intelligence, Las Vegas, NV, June 2000, 429-434.
- 16. Kennedym, J., Eberhart, R.C. and Shi, Y.H. (2001) Swarm Intelligence V. Morgan Kaufmann, San Mateo.
- 17. Eberhart, R. and Kennedy, J. (1995) A New Optimizer Using Particles Swarm Theory. Proceedings of the 6th International Symposium on Micro Machine and Human Science, Nayoga, 4-6 October 1995, 39-43.
http://dx.doi.org/10.1109/MHS.1995.494215 - 18. Wang, D.S., Li, J.P. and Memik, G. (2010) User Identification Based on Finger-Vein Patterns for Consumer Electronics Devices. IEEE Transactions on Consumer Electronics, 56, 799-804.
http://dx.doi.org/10.1109/TCE.2010.5506004 - 19. Pandey, R., Mehta, A. and Garia, L.S. (2013) Hand Vien Recognotion Using Matlab. IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE), 5, 32-34.