Wireless Engineering and Technology
Vol.1 No.1(2010), Article ID:2337,6 pages DOI:10.4236/wet.2010.11003
A Perspective on Traffic Measurement Tools in Wireless Networks
![]()
1Department of Information Science and Engineering, Acharya Institute of Technology, Bangalore, Karnataka, India; 2 Department of Computer Science and Engineering, B.M.S. College of Engineering, Bangalore, Karnataka, India; 3Department of Electronics and Communication Engineering, B.M.S. College of Engineering, Bangalore, Karnataka, India.
Email: rameshbabu@acharya.ac.in, {gowrishankar.cse, pssvittala.ece}@bmsce.ac.in
Received April 13th, 2010; revised May 12th, 2010; accepted June 10th, 2010.
Keywords: SNMP, wireless sniffing, Syslog, network sniffing, wireless networks
ABSTRACT
To understand the characteristics of the wireless networks, the network usage data from wireless measurement tools are essential. The data collection is a process of collecting the network time-varying information in standardized format and from standard interfaces. The characteristics include signal propagation, received signal quality, network traffic, active applications and mobility of the mobile terminal (MT). The purpose of the measurement is to collect vital data of the wireless network. There are several tools available for this purpose. The most widely used network measurement tools are client side measurement tool, Syslog, Simple Network Management protocol (SNMP), network sniffing, wireless sniffing. This paper discusses the different wireless measurement tools and their benefits and limitation these tools.
1. Introduction
The data collection is a process of collecting the network time-varying information in a standardized formats and from a standard interfaces. This needs a Portable tool for data collection. The collected data need to be processed effectively without losing the “tail” of the data and identifying holes and cleaning data. In the pre-processing mechanism, the time-varying network parameters are arranged in an order. These time series may have few missing entries, due to the minor flaws in the measurement tools, which are estimated and filled using time series techniques.
There are many implicit differences in wired and wireless medium. Wired medium will have clear points of connection but wireless medium is physically dispersed. The mobility in wireless networks and novel devices used inspires new usage patterns. In this prevailing scenario, the measurement of wireless network information is essential. This strengthens our understanding of user and network behaviours. The better understanding leads to better network models. The improved network models are momentous to improvement in terms of network protocols, distributed algorithms, applications and improved deployment strategy.
The NGWN provides users with a wide range of services across HWNs coexisting with diverse throughput and coverage with a single MT. The existing cellular networks will provide communication services over a wide geographical area but has limited bandwidth to support emerging data services. But the future 3G cellular and 4G systems, such as UMTS, Wi-MAX (802.16), have lesser coverage and higher bandwidth when compared to cellular networks. The WLAN (IEEE 802.11 a/b/g/n) is able to provide higher data rate but with lesser coverage compared to cellular and 4G systems. Therefore an integration of cellular networks, Wireless Local Area networks (WLAN) and Wi-MAX would result in higher bandwidth, more network coverage and will also help in enhanced user mobility and with choice of new services and enhanced QoS [1]. Figure 1 illustrates the Speed v/s Mobility comparison of wireless networks. The characteristics of the different wireless networks are depicted in table 1.
The process of network switching will involve the following three phases – network discovery, switching decision and execution [2]. The decision phase will play an important role in balancing network utilization, fulfilling the user requirements and QoS requirements of network
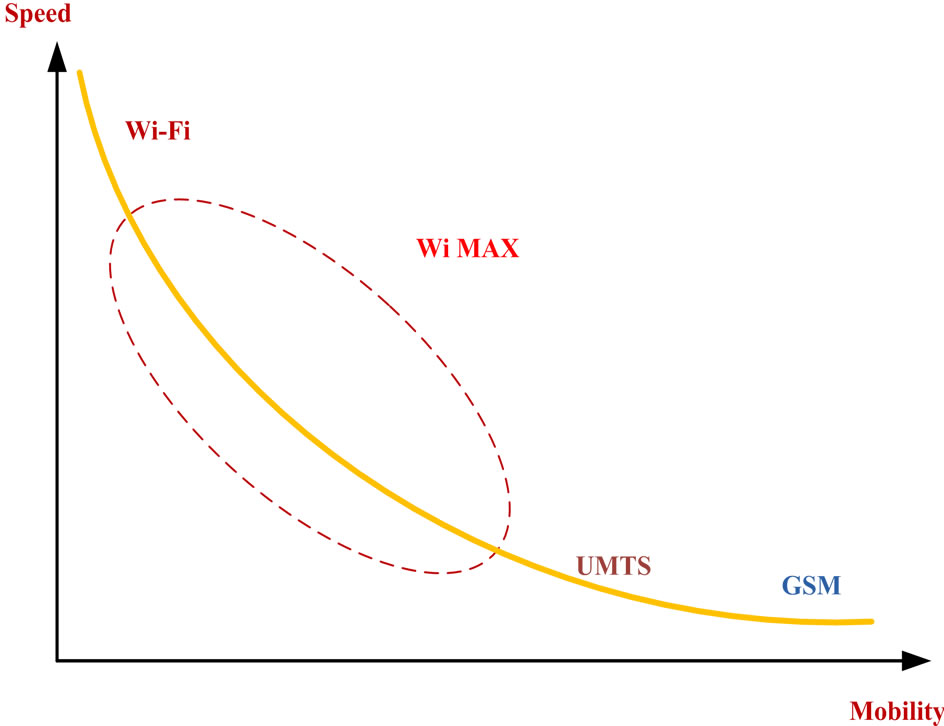
Figure 1. Speed vs. mobility comparisons of different wireless networks
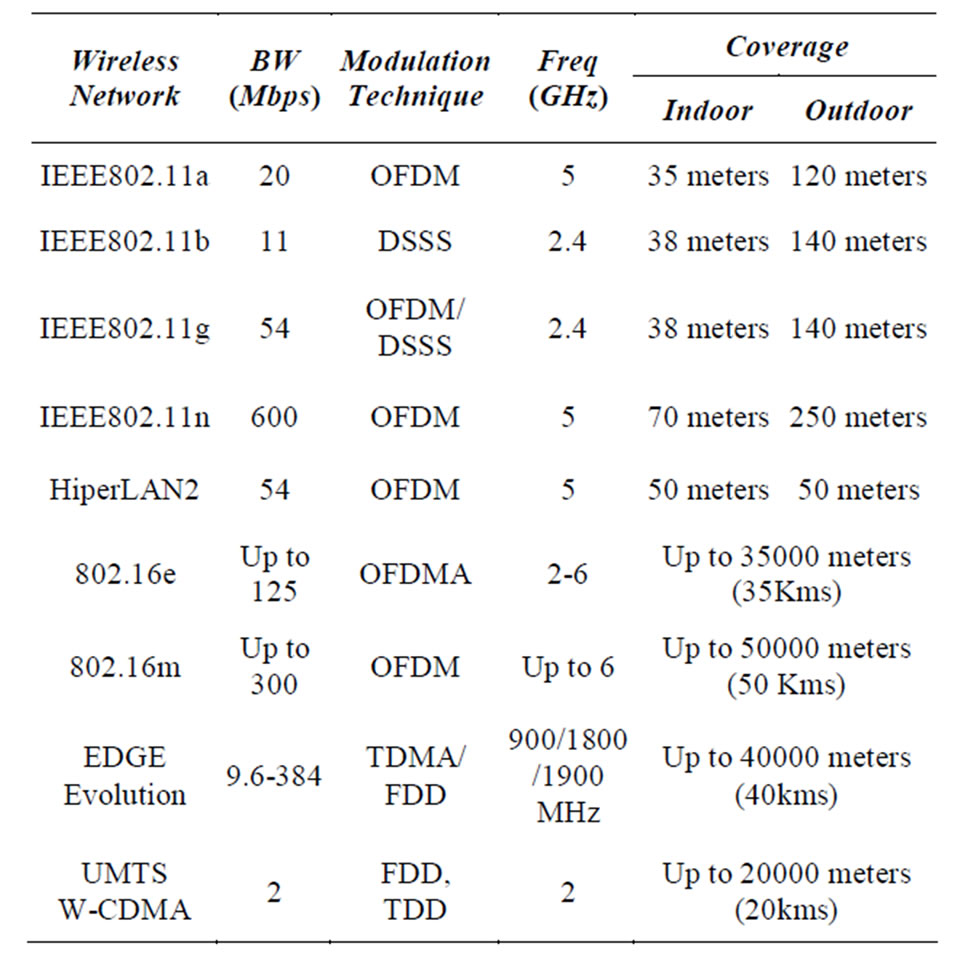
Table 1. Attribute comparisons of different wireless networks
applications. Thus, the need of effective decision mechanism is crucial. The decision mechanism is driven by a set of QoS parameters [3-6]. The QoS parameters are bandwidth, BER and cost. The criteria that affect these QoS parameters are wireless link quality and the current network load. The factors that influence link quality are noise and signal fading [7]. The Signal to Noise Ratio (SNR) value of the wireless channel can be considered as the measure of the channel quality in a wireless network. The network load is measured based on the number of active users and their network sessions and is also called as network traffic [8].
The signal fading in a wireless system is common phenomena of the radio channel. They are classified into two types, Flat fading and Frequency selective fading. In a narrowband wireless channel, the consistency bandwidth of the channel is larger than the bandwidth of the signal. In such channels all frequency components of the signal will experience the same amount of fading. Such a fading is called as ‘Flat fading’. On the other hand, in a wideband wireless channel the coherence bandwidth of the channel is smaller than the bandwidth of the signal. This result in Different frequency components of the signal, experiencing the different amount of fading called as ‘frequency selective fading’. Apart from these two types of fading, when the MT is moving at a high speed, the signal strength varies severely and undergoes deep fading within the small time frame. This type of fading is named as ‘Fast fading’ [9].
The next generation wireless systems typically have higher bandwidth and support optimal mobility, need to challenge with the frequency selective fading and fast fading. The next generation wireless systems make use of low complexity techniques such as Orthogonal Frequency Division Multiplexing (OFDM) in the physical layer and Orthogonal Frequency Division Multiple Access (OFDMA) mechanisms in the link layer to prevail over the effect of frequency selective fading [10].
2. Wireless Network Measurements
To understand the characteristics of the wireless networks, the network usage data from wireless measurement tools are essential. The characteristics include signal propagation, received signal quality, network traffic, active applications and mobility of the MT. The purpose of the measurement is to collect vital data of the wireless network. There are several tools available for this purpose. The most widely used network measurement tools are client side measurement tool, Syslog, Simple Network Management protocol(SNMP), network sniffing, wireless sniffing.
2.1 Client Side Network Management Tools
The wireless measurement tools mentioned above i.e. Syslog, SNMP, network sniffing and wireless sniffing tools are intended to monitor the network from the viewpoint of the network. In client side methods the measurement tools are installed in client to measure the activities at the client side. This client side measurement has many advantages.
A client side tool can accurately determine what exactly a client is doing. While Syslog will provide information about set of clients which are associated to the particular AP/BS, a client side tool can list all the APs/BSs that a client can handle, which are useful for mobility tracing. A client side tool can list all the applications that are running on it, rather than just those applications that generate network traffic. Client side tools are extensively used in WMAN and WWAN measurements [11,12].
Writing a generic client side program, such as tcpdump, Wireshark formerly called Ethereal and kismet will be a challenging task, because it has to run on variety of operating systems and different device drivers.
2.2 Syslog
Syslog records detail steps of association, and have been used effectively for studying user activity patterns [13, 14]. To all intents and purposes Syslog is a standard for sending and receiving of log messages [15]. The wireless APs and BSs can be configured to log appropriate events in the network. The Syslog messages are used to understand the sate of an MT in the wireless network. The AP or BS can generate a time stamped message whenever an MT authenticates, de-authenticates, associates, dis-associates or roams to that AP or BS. By collecting these messages it is possible to determine the state of the MTs on the network. The Syslog messages are stored and analyzed locally in the BS or transmitted across the network for storage and analysis by a dedicated computer.
There is no standard format for Syslog messages. The messages that APs or BSs send can vary in format and amount of information contained. In most of the cases APs and BSs manufactured from same manufacturer will have different Syslog message formats. In certain cases the message formats differ for each version of the same product. In a heterogeneous wireless environment, multiple type of APs and BSs with varieties of Syslog message formats. It is necessary to translate these messages in to an intermediate format prior to the data analysis. In some of the measurement studies [16,17], the multiple Syslog message formats are translated to general, intermediate parsed format for the purpose of analysis. Figure 2 indicates the parsed Syslog trace data format.
2.3 SNMP
The SNMP is a generic tool in measuring and managing a network device, called ‘network object’ in the network management terminology [18]. The SNMP provides information on both traffic volume and the number of active users. This makes the SNMP the most suitable tech nique used for both traffic studies [14,19,20] and user mobility studies [21].

Figure 2. Parsed syslog format
A network administrator runs a tool known as ‘manager’, which communicates with SNMP ‘agents’. Agents run on network objects and provide interface between the object and manager. A network object can contain several objects, such as statistics or configuration items, arranged in a database known as Management Information Base (MIB). The network statistics are stored in the MIB variables and these variables are represented in a standard format known as Abstract Syntax Notation (ASN) .The manager queries the agent for the purpose of measurement and agent replies by extracting information from the MIB variables. Both request and reply will be in the standard SNMP message format [22]. In the recent version of SNMP few MIB variables, like MAC address, IP address, Signal strength, Power saving mode, Network session length and Traffic of the MT associated with AP or BS, are specific to the wireless network [23]. The SNMP messages are shown in figure 3.
Some of the advantages of the SNMP are
● SNMP messages provide more detailed information about the status of the network than Syslog messages.
● SNMP provides information on both traffic volume and the number of active users. Hence it is suitable to be used for both traffic studies and user mobility studies.
● SNMP messages are generally device independent and are usually available in a standard format.
The drawbacks of SNMP are
● SNMP-based approaches is that they require an interval between SNMP polls (typically every 1-5 minutes), and it has been shown that long poll intervals may miss wireless clients that associate with APs for less than this poll interval [24].

Figure 3. Set of SNMP messages
● The SNMP-based approaches may be able to retrieve such detailed wireless MAC/PHY information through the use of a properly defined MIB, the most existing SNMP MIBs for APs (MIB-I (RFC 1066), MIB-II (RFC 1213), and 802.11 MIB (IEEE Std 802.11-1999)) provide very limited visibility into MAC-level behaviour.
2.4 Network Sniffing
The network or packet sniffing refers to the process of capturing of the network traffic at the network interface. For the purpose of sniffing, the network interface should be in a promiscuous mode. In this mode the interface will ignore its assigned address and captures all the frames/ packets present in the network. There are programs, such as tcpdump, Ethereal and kismet, which will capture and analyze the frame/packet [25-27].
Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Kismet will work with any wireless card which supports raw monitoring (rfmon) mode, and (with appropriate hardware) can sniff 802.11b, 802.11a, 802.11g, and 802.11n traffic. The Kismet is good for WLAN surveillance. It is capable to sense the details of all wireless access points (WAPs) and WLAN nodes, showing channels, use of encryption and signal strength.
Ethereal is a network packet analyzer. A network packet analyzer will try to capture network packets and tries to display that packet data as detailed as possible. You could think of a network packet analyzer as a measuring device used to examine what's going on inside a network cable. The Ethereal is not an intrusion detection system. It will not warn when someone does strange things on the network that the user isn’t allowed to do. However, if strange things happen, Ethereal might help you figure out what is really going on. Ethereal will not manipulate things on the network, it will only “measure” things from it. Ethereal doesn’t send packets on the network or do other active things (except for name resolutions, but even that can be disabled). The trace of an ethereal is shown in figure 4.
The important concern with network sniffing is that the volume of data generated from the sniffing process is much larger than Syslog and SNMP. A typical sniffing of 802.11b wireless network operating at 11 Mbps speed can generate several gigabits of data within few minutes. It is vital to ensure that sufficient disk space is available to store the captured frames/packets in the hard disk. Another major concern in the network sniffing is the privacy of captured information. The frame/packet that is captured through sniffing may contain sensitive data especially when the data within the frame/packet is not encrypted. The issue of privacy may be alleviated by only capturing the header data, which may be sufficient for a network measurement. Even with this, the privacy problem is not completely overcome as some vital information,
Figure 4. Network sniffing trace
such as packet size, MAC/IP address, higher layer protocol and inter-arrival time, stand exposed. The result of such a sniffing is referred to as a trace.
2.5 Wireless Sniffing
The wireless sniffing is a WLAN measurement tool [28]. Syslog, SNMP and network sniffing are the generic measurement tools which will be used in measuring all types of wireless as well as wired networks. The wireless snifffing is a measurement tool useful only for a wireless network. It will operate at AP/BS or at a switch that connects wireless network to the wired backbone. The disadvantage of wire side measurement is that not all wireless data observable from the wired network, such as management frames, beacons, retransmissions and collisions, send traffic via wired network. The wireless sniffer is widely used to collect the MAC level frame information in a wireless network. Even though wireless sniffer can be installed on a host under measurement, but in majority of cases, it is installed on an autonomous device. This independent device could be a laptop or any MT or a PDA system. This makes the wireless sniffer to monitor the wireless network in promiscuous mode without interfering with the stations under study/monitoring. Wireless sniffers capture both the data frames as well as management frames. The management frames captured by wireless sniffer includes beacon frames, request to send (RTS) frames, clear to send (CTS) frames and Acknowledgement (ACK) frames. Nevertheless, there is need of special hardware and software in form of drivers is essential for effective working of a wireless sniffer. Ethereal and Kismet are the most admired wireless sniffer and analyzer software. There are good amount of research works reported on wireless performance using Wireless sniffers .The measurement of streaming media over wireless link using independent sniffers [29,30], measurement of congestion in wireless LAN [31], in the network monitor research in [32], a complete wireless sniffer system is implemented and used to characterize a typical computer science department WLAN traffic.
Wireless measurement can be applied to the mobile host. This is accomplished by placing wireless network interface card in a monitor mode. In this mode, the wireless card captures all types of frames/packets. These frames/packets may be analyzed similar to those of network sniffing. Since this mode is not a promiscuous mode it limits the wireless sniffer in the mobile host as a simple network monitoring tool. Figure 5 shows an example of wireless sniffing trace.
The advantages and disadvantages of wireless sniffing are as listed below.
Advantages of wireless sniffing are:
● Wireless Sniffing done be an independent sniffer in a promiscuous mode will not cause any interference with the hosts under test in wireless experiment. Therefore, sniffing can be used to measure these devices, such as the wireless game consoles, which do not provide general accesses for measurement purpose.
● Wireless sniffing can provide frame level information and wireless network conditions, such as the RSSI and sending capacity.
● Wireless sniffers can be used as wireless network diagnostic tools as they are capable to capture wireless management frames, such as RTS, CTS, Authentication / De-authentication frames and Association / Disassociation frames.
Disadvantages of Wireless sniffers are:
● Wireless sniffers cannot record all the frames that are transmitted over the network [31,33] since the sniffer is only capturing the frames at its own location this results in non capturing of the packets lost due to a hidden terminal and packets lost due bit errors.
● The Received Signal Strength Indicator (RSSI) is measured relative to the wireless sniffer installation location. This measurement of received signal strength may not be same as the AP or the clients that are remote from the wireless sniffer installation location.
Figure 5. Wireless sniffing trace in WLAN
● The location of the sniffer plays an important role in the wireless sniffing. For example, a location very close to an AP is helpful when studying the AP behaviour, but may miss some traffic sent from a distant client due to signal attenuation and on the other hand the similar effect is experienced when the sniffer is near to the client and away from the AP. This results in ‘Generic losses.
● The wireless sniffing suffers from ‘AP losses due to the firmware incompatibility between AP and monitoring device. These losses can be minimized by using redundant sniffers or sniffers with interface cards having different chipset and using antennas of different gains and positioning the sniffers at strategic places [34].
3. Conclusions
The wireless Measurement is an important phase of any study on wireless networks. The data collection phase acts as the building stone of the study of wireless measurements. The various wireless measurements tools used to measure the characteristics will have their own strength and weaknesses. The wireless sniffing is one of the measurement techniques that could be used for effective measurement of wireless network time varying characteristics. The data collection of wireless networks can be supported by standardization of interfaces and formats of information which is common to all network vendors. The archival of the network data will help in better understanding and methodical study of wireless networks. Our future work includes the building up the effective measurement framework and step ahead for predicting the missing values in measurements by applying intelligent hybrid technique like Fuzzy neural approach.
REFERENCES
- M. S. Kuran and T. Tugcu, “A Survey on Emerging Broadband Wireless Access Technologies,” Computer Networks, Vol. 51, No. 11, 2007, pp. 3013-3046.
- F. Siddiqui and S. Zeadally, “Mobility Management across Hybrid Wireless Networks: Trends and Challenges,” Computer Communications, Vol. 29, No. 9, 2006, pp. 1363-1385.
- W. Chen and Y. Shu, “Active Application Oriented Vertical Handoff in Next-generation Wireless Networks,” IEEE Wireless Communication and Networking Conference, Vol. 3, 2005, pp. 1383-1388.
- T. Al-Gizawi, K. peppas, D. Axiotis, et al., “Interoperability Criteria, Mechanisms and Evaluation of System Performance for Transparently Interoperating WLAN and UCLIENTS-HSDPA Networks,” IEEE Networks, Vol. 19, No. 1, 2005, pp. 66-72.
- Q. Song and A. Jamalipour, “Network Selection in an Integrated Wireless LAN and UCLIENTS Environment using Mathematical Modeling and Computing Techniques,” IEEE Wireless Communication Magazine, Vol. 12, No. 3, 2005, pp. 42-48.
- F. Zhu and J. McNair, “Optimization for Vertical Handoff Decision Algorithms,” IEEE Wireless Communication and Networking Conference, Vol. 2, 2004, pp. 867-872.
- J. Zhang, L. Cheng and I. Marsik, “Models for Non-intrusive Estimation of Wireless Channel Bandwidth,” 9th IFIP International Conference on Personal Wireless Communication Conference, 2003, pp. 334-348.
- M. Papadopouli, H. Shen, E. Raftopoulos, et al., “Shortterm Traffic Forecasting in Campus-wide Wireless Networks,” 16th IEEE International Symposium on Personal, Indoor and Mobile Wireless Communications, 2005, pp. 1446-1452.
- K. Pahlvan and P. Krishanamurthy, “Principles of Wireless Networks—A Unified Approach,” Prentice-Hall, Inc., 2002.
- R. Prasad, “OFDM for Wireless Communication Systems,” Artech House Inc., Norwood, 2004.
- D. Tang and M. Barker, “Analysis of a Metropolitan-Area Wireless Network,” Wireless Networks, Vol. 8, 2002, pp. 107-120.
- M. Claypool, R. Kinicki, W. Lee, M. Li and G. Ratner, “Characterization by Measurement of a CDMA 1xEVDO Network,” 2nd International Workshop on Wireless Internet, 2006, pp. 2-es
- F. Chinchilla, M. Lindsey and M. Papadopouli, “Analysis of Wireless Information Locality and Association Patterns in a Campus,” Proceedings of INFOCOM ’04, Hong Kong, March 2004, pp. 906-917.
- D. Kotz and K. Essien, “Analysis of a Campus-wide Wireless Network,” Proceedings of MOBICOM’ 02, Atlanta, September 2002, pp. 107-118.
- C. Lonvik, “The BSD Syslog Protocol,” IETF RFC 3164, August 2001, pp. 1-27.
- T. Henderson, D. Kotz and I. Abyzov, “The Changing Usage of Mature Campus-Wide Wireless Network,” 10th ACM International Conference on Mobile Computing and Networking, 2004, pp. 187-201.
- D. Kotz and K. Essien, “Analysis of a Campus-wide Wireless Network,” Wireless Networks, Vol. 11, No. 1-2, 2005, pp. 115-133
- K. McCloghire, D. Perkins and J. Schoenwaelder, “Structure of Management Information Version 2 (SMIv2)”, IETF RFC 2578, April 1999.
- Balachandran, G. M. Voelker, P. Bahl and V. Rangan “Characterizing User Behavior and Network Performance in a Public Wireless LAN,” Proceedings of ACM SIGMETRICS ’02, Marina Del Rey, June 2002, pp. 195-205.
- D. Tang and M. Baker, “Analysis of a Local-Area Wireless Network,” Proceedings of MOBICOM’00, Boston, August 2000, pp. 1-10.
- M. Balazinska and P. Castro, “Characterizing Mobility and Network Usage in a Corporate Wireless Local-Area Network,” Proceedings of MOBISYS’03, San Francisco, May 2003, pp. 303-316.
- M. Subramanian, “Network Management: Principles and Practice,” Addison-Wesley, Reading, 2000
- J. Flick and J. Jhonson, “Definitions of Managed Objects for Ethernet-Like Interface Types,” IETF RFC 2665, Chipcom Corporation, August 1999.
- Mani Subramanian, “Network Management,” Pearson Education.
- “Ethereal Protocol Analyzer”. http://www.ethrereal.com
- “Kismet Wireless Sniffing Software”. http://www.Kismetwireless.net
- Tcpdump Packets Capture Software. http://www.tcpdump. org
- R. Shenoy, A. L. Ananda, M. C. Chan and W. T. Ooi, “Mobile, Wireless and Sensor Networks: Technology, Application and Future Directions,” John Wiley & Sons, Hoboken, 2006
- T. Kuang and C. Williamson, “Real Media Streaming Performance on an IEEE 802.11b Wireless LAN,” Proceedings of IASTED Wireless and Optical Communications (WOC), July 2002, pp. 306-311.
- G. W. Bai and C. Williamson, “The Effects of Mobility on Wireless Media Streaming Performance,” Proceedings of Wireless Networks and Emerging Technologies (WNET), July 2004, pp. 596-601.
- A. P. Jardosh, K. N. Ramachandran, K. C. Almeroth and E. M. Belding-Royer, “Understanding Congestion in IEEE 802.11b Wireless Networks,” Proceedings of the Internet Measurement Conference (IMC), Berkeley, October 2005, pp. 279-292.
- J. Yeo, M. Youssef and A. Agrawala, “A Framework for Wireless LAN Monitoring and its Applications,” ACM Workshop on Wireless Security (WiSe 2004) in Conjunction with ACM MobiCom 2004, Philadelphia, October 2004, pp. 70-79.
- M. Claypool, “On the 802.11 Turbulence of Nintendo Ds and Sony PSP Hand-Held Network Games,” Proceedings of the 4th ACM Network and System Support for Games (Net Games), Hawthorne, October 2005, pp. 1-9.
- J. Yeo, S. Banarjee and A. Agarwaala, “Measuring Traffic on the Wireless Medium: Experience and pitfalls,” Technical Reports, CS-TR-4421, Department of Computer Science, University of Maryland, December 2002.

