Communications and Network
Vol.07 No.02(2015), Article ID:55448,16 pages
10.4236/cn.2015.72009
FMAC: Fair Mac Protocol for Achieving Proportional Fairness in Multi-Rate WSNs
Nusaibah M. Al-Ratta, Mznah Al-Rodhaan, Abdullah Al-Dhelaan
Computer Science Department, College of Computer and Information Sciences, King Saud University, Saudi Arabia
Email: nsoobyal-ratta@hotmail.com, rodhaan@ksu.edu.sa, rodhaan@ksu.edu.sa
Copyright © 2015 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 20 February 2015; accepted 3 April 2015; published 9 April 2015
ABSTRACT
In a multi-rate wireless environment, slow nodes occupy the channel for longer time than fast nodes and thus the total throughput of the network will be reduced. In this research, we study the problem of fairness in multi-rate wireless sensor networks. To improve the fairness, we propose a new protocol, FMAC (Fair MAC protocol) that is based on IEEE 802.11 MAC protocol to achieve proportional fairness between all nodes. FMAC protocol includes medium delay periods within Backoff algorithm to utilize the idle slots of time and reduce the number of collisions and then number of retransmissions, and thus reducing the energy consumption, which is very critical in wireless sensor networks. The experimental results show that transmissions become faster with less collisions and power consumption when applying FMAC, while the aggregated throughput and proportional fairness are increased. The detailed performance evaluation and comparisons are provided using the simulation.
Keywords:
Backoff, DCF, IEEE 802.11, Proportional Fairness, Wireless Sensor Networks

1. Introduction
Wireless Sensor Network (WSN) nowadays is regarded as one of the most recent technologies. It is an emerging and fast progressing field in the 21st Century. It has appeared as a result of increasing requirements of mobility in the world, while the traditional networks have proven that they cannot face the challenges of our new lifestyles.
Wireless sensor networks were developed initially to be used in the military field like enemy monitoring and battlefield reconnaissance [1] . Today, these networks have a variety of applications especially for tracking outdoor environments, which requires long-range operation for long times with high accuracy and with less maintenance [2] . They are, in essence, a type of Ad-Hoc network in which sensor nodes (SNs) are connected together with wireless links and can join or disconnect from the network with minimal cost and effort.
Wireless sensor networks (WSNs) comprise many of wireless sensor nodes that may be organized in multi- hop or one-hop network with varying quality of wireless link, especially in the case of network with a high traffic, as well as various distances from the sink node. In order to get accurate information from the sensing application, we have to insure the successful fair rate for data transferring from the sensors to the sink [3] [4] . Providing the maximum throughput with minimum power consumption is one of the greatest goals in WSNs. MAC layer is an important place to make the significance improvements towards achieving such goals, due to its responsibility for distribution of the shared resources and controlling the access of the contending nodes to the wireless channel. An efficient MAC protocol can play a big role in power saving, especially regarding the reduction of collisions and thus retransmissions which results in high power consumption [5] -[7] .
Collision is not only one of the most energy consumption sources; it also increases latency. So, reducing the collisions can improve the throughput. An efficient MAC protocol can contribute in prolonging the sensor lifetime [5] [8] .
The use of IEEE 802.11 protocol in WSNs is considered a new orientation to some extent. The efficiency of the IEEE 802.11 MAC protocol in WSNs has been proven in terms of many important issues like the throughput, delay and power consumption. Because of this and since we know that the channel access mechanism has a large effect on the performance of any network, we decided to design a light and efficient solution which is based on IEEE 802.11 MAC protocol to achieve the proportional fairness in multi-rate WSNs.
Our main objective is to achieve the proportional fairness between all nodes in multi-rate WSNs via designing a new MAC protocol. This new protocol will be able to investigate the trade-off among throughput and fairness.
We also aim to make an in-depth analysis and validation of the performance of the proposed protocol which can help in advancing research about the fairness problem using the distributed coordination function (DCF) for the IEEE 802.11 wireless sensor networks.
Many research papers related to the fairness issue were suggested solutions that include modifications of the size of contention window or even the size of the packets in order to restrict the transmission of some specific nodes, or adding some control information which may result in additional overhead or energy wastage. Also some solutions need a supplementary alteration for the upper layers characteristics such as routing issues.
Our proposed solution is lightweight in terms of not requiring any additional information or lot of computations. It includes a small modification in the standard backoff process to give different opportunities to the nodes that have different data rates. This work will hopefully promote the scientific and technological research in wireless sensor networks. However, the proposed protocol is also applicable in WLANs because it does not mainly depend on the nature of WSNs.
The rest of this paper is organized as follows: Section 2 defines the problem statement. Section 3 provides necessary background information. Section 4 gives a rich review of the related work. Then we present the methodology in Section 5. Next, the simulation and performance evaluation metrics as well as the experimental results are provided in detail in Section 6 and 7 respectively. Finally Section 8 concludes the paper and provides some future directions.
2. Problem Statement
The IEEE 802.11 uses the Distributed Coordination Function (DCF) to regulate transmissions at media access control (MAC) layer [9] . DCF provides long-term equal transmission opportunities to all competing nodes regardless of their data rates, which results in throughput-based fairness and therefore significantly degrades the aggregated throughput in a multi-rate wireless sensor network (WSN). This is because of the nodes with low-rates that need longer occupancy time of the channel for transmission, which will result in shortening the time that the fast nodes can find the channel as idle.
This performance anomaly can be mitigated by adjusting the size of contention window, increasing contention window size for a specific node will reduce its competition opportunity for example, or adopting a more appropriate backoff algorithm [9] . On the other hand, proportional fairness intends to maximize the sum of logarithm of the throughput for all nodes while providing fairness in terms of throughput. Based on these observations, we propose a new MAC protocol for multi-rate WSN with a single sink node to achieve proportional fairness.
3. Background Information
In this Section, we will provide some necessary background information about the MAC layer protocols for WSN.
3.1. MAC Protocols for WSNs
In the traditional IEEE 802 local area networks (LANs), Data Link Layer is split into two sub layers: Logical Link Control (LLC) and Media Access Control (MAC). A new MAC sub layer for 802.11 was then developed. The main functions of MAC layer involve frame delineation, addressing, error checking, and organize access of all nodes to the shared-medium [10] .
The protocols for MAC layer in WSNs should be energy efficient in order to prolong lifespan of the nodes. The main objectives of such protocols include maximizing channel capacity usage while minimizing the delay time. Other goals involve fairness and stability [11] .
MAC is a fundamental method to control the successful transfer processes in the network. We can group existing MAC protocols for WSN in two main categories as follows: contention-based category and contention- free category [12] .
Contention-free protocols have a fixed assignment such as CDMA, TDMA and FDMA. Lack of flexibility in resource allocation is the main drawback of these protocols. So, they faced difficulties with changes in the configuration, and thus they are inappropriate in the dynamic wireless networks.
On the other hand, contention-based protocols have random assignment like CSMA and ALOHA. Such protocols have a high flexibility and they are widely applied in the wireless LANs. Systems can be developed by the use of more than one of these categories [11] .
Most of the suggested protocols in the category of contention-based are used the techniques of carrier sense multiple access (CSMA). In CSMA, the node has special carrier sensing capabilities. Before starting transmitting, the node must sense the channel. If it found that the channel is busy, then the access will be postponed to the next retrying [12] .
CSMA has two extensions, collision detection (CSMA/CD) and collision avoidance (CSMA/CA) [11] . In collision detection, the sender will be able to detect the collision after it happens and thus stop transmitting data. In collision avoidance, the node applies technique that avoids the collision before it happens, but with no guarantees.
Usually it is difficult to detect collisions in a wireless node. Many methods were proposed to address this problem, but even these approaches unable to grants enough ability for nodes to detect all collisions types. Therefore, IEEE 802.11 MAC protocol with CSMA/CA was suggested to be the standard protocol used in wireless local area networks (LANs) [11] [13] .
Two access methods are provided by IEEE 802.11 access scheme: Distributed Coordination Function (DCF) and Point Coordination Function (PCF). The former is for contention-based access scheme with asynchronous transferring, while the latter is for the contention-free and centralized access scheme [14] . The DCF method is involved in the CSMA/CA category for MAC protocols.
3.2. Binary Exponential Backoff
Wastage of channel utilization is mainly caused by collisions as well as the idle times resulted by the access distribution [14] . Binary exponential backoff (BEB) is regarded as an adaptive behavior provided by the IEEE 802.11 DCF mechanism in order to address such wastage.
Each node wants to send a frame, sets a random time for accessing the channel, this amount of time is varying based on the number of collisions which occurred earlier for that frame. If an ACK frame was not received, a node will assume that the corresponding packet was dropped by the collision, and thus it will retransmit this packet after invoking BEB. Backoff time is increased using BEB technique at each time the collision occurs, because this may indicate that the network is congested.
The BEB [9] [12] -[14] works as follows: Slot_Time is a unit of a constant length used to measure the time, also can be just called slot. In order to implement Binary Exponential Backoff scheme, each node has the Backoff Counter (BC), which is the counter used to compute the required empty slots of time for waiting before attempting to transmit. Before scheduling of a new transmission, the node should wait for random interval which is within a range that is uniformly distributed between 0 and the size of the current contention window (CW). Backoff value is defined as the following:
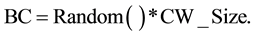 (1)
(1)
where the function Random ( ) returns a number selected randomly between 0 and 1.
If the node senses that the channel is busy, it will pause its backoff counter and postpone the transmission. After the end of the ongoing transmission, if it senses that the channel is idle then it will resume the counter again. At each time slot, the value of backoff counter is reduced by one. If its value becomes zero, and if the channel is found not busy for the time interval Distributed Inter Frame Space (DIFS), the node will (re)start trying to access it again.
If the node accessed the channel and successfully sent the packet, it will wait for the acknowledgment (ACK) frame from the receiver within SIFS interval (Short Inter Frame Space), which is less than DIFS. On the other hand, if the node needs to access but the channel is busy, it will stop the decreasing of the counter and preserve its value to be resumed in the next attempt of transmission.
If two nodes chose the same random backoff value, both of them will start transmission simultaneously, and thus the collision will occur. In this case, the sender nodes will detect the collision because of the absence of an ACK for their frames. So, every node will apply the exponential backoff algorithm. Firstly, the size of the contention window (CW) will be doubled. Next, it will choose a random number and assign it to the value of its backoff counter. Then, it will start decreasing the counter until it equals zero. Finally, the node will attempt to retransmit again. If it is successful, it will reset the value of CW to the minimum CWmin.
The initial value of contention window size is CWmin. At each unsuccessful (re)transmission, the size of contention window will be doubled, to reduce the contention. If this size reaches the maximum value CWmax, the protocol will stop the retransmission, discard all not transmitted packets, and reset the size to CWmin. Figure 1 shows the DCF protocol [15] .
3.3. DCF and RTS/CTS Access Mechanism
RTS/CTS exchanging can optionally extend the Binary exponential Backoff access mechanism of IEEE 802.11 DCF. When the node gets to access the channel, it will send the announcement for its incoming transmission rather than sending the actual data packets. This can be applied by sending a request to send (RTS) control packet to the receiver.
If the receiver is ready to receive the data, it will reply by sending a clear to send (CTS) control packet. Using this technique, all other nodes within the range will be informed about this transmission. So, they will not disturb it. Both the control packets include the expected transmission length, thus the channel will be reserved efficiently for this transmission [16] .
3.4. Performance Anomaly
In wireless channels, there are many reasons that affect the quality of signals, such as the noise, attenuation and interference. This may cause unsuccessful reception of the frames. The implications of these errors are more
Figure 1. DCF protocol.
critical with 802.11 DCF, because it is not possible to distinguish between fail transmissions and collisions. When the frame is lost, the node will implement the exponential backoff process.
If the node uses a lower bit rate, this may result in a lower frame error rate and thus a better throughput. Unfortunately, diversity of bit rates, either by changing the bit rate for the same node or by the existence of nodes with different bit rates originally, causes a performance anomaly. Slower rate nodes consume longer time for transmission than faster rate nodes. As a result, there will be less time for fast nodes with an idle channel, and thus the throughput will be reduced [9] .
4. Related Work
Congestion control has a significant importance in wireless sensor networks. Scaling up wireless sensor networks by adding more sensors in a larger area implies increasing the traffic volume while the capacity of the channel around the bottlenecks cannot be increased easily, specifically with low-cost and low-energy constraints.
Resolving congestion does not guarantee fairness [17] , because in reality they are two different problems, although they are related in terms of their effects on the throughput of the network.
Fairness is one of the most important goals in wireless sensor networks. This issue becomes even more serious for networks with multi data rates. Usually, nodes with the low data rates have a longer occupancy time of the channel than other nodes, and thus will degrade the whole throughput of the network. Nodes may use different data rates because of the conditions of the channel, different generations of technologies, or simply based on their distance from the sink node [18] .
As wireless sensor networks are usually used in surveillance fields, the fair access to the network between all nodes must be ensured in order to enable the sink nodes to get a complete view of the monitored area. Cooperative MAC Protocol suggested in [19] to tackle this problem. Low data rate node assisted by a high rate node (called helper node) in its transmission. In order to reduce the occupancy time of the channel, it used two transmissions with high data rates, rather than only one transmission with a low data rate.
Fairness has different definitions based on different criteria. Regarding time scales, there are two types of fairness: the first type is called long-term fairness while the second is called short-term fairness [9] .
Long-term fairness gives equal probabilities of accessing the channel successfully among all competing nodes on a long-term scale. Short-term fairness gives the same thing, but within shorter time intervals. With short-term fairness, each node can access the channel after a short period of time that results in brief delays. Actually, short term fairness fulfils the long-term fairness, but not vice versa.
IEEE 802.11 MAC protocol provides good short-term fairness for the networks with a limited number of nodes [9] . But with large number of nodes, it does not provide short term fairness due to the use of exponential backoff by nodes that have collided packets, and thus results in more opportunities of transmission for other nodes.
All nodes choose their random backoff intervals from the similar contention range most of the time. So, they will have the same likelihood of channel access and thus IEEE 802.11 DCF MAC protocol achieves time-based fairness among nodes with similar bit rates [9] . If all nodes use the same frame size, 802.11 MAC protocol also provides throughput-based fairness (i.e. equal throughput shares). However, throughput fairness maybe caused bandwidth underutilization in multi-rate wireless networks. Also there are two other types of fairness: max-min fairness and proportional fairness. It was proved that if all nodes have the same weight, then the proportional fairness will be equivalent to the time-based fairness in the networks with multi data rates. Moreover, it was proved that the max-min fairness and throughput-based fairness are equivalent under the same condition. It is also argued that the proportional fairness achieves trade-off between throughput and fairness in the network [20] .
The standard 802.11 MAC protocol achieves max-min fairness in the utilization of the bandwidth. In multi data rate networks, the nodes with low data rate will consume more air-time and this differs from max-min fairness in the use of the bandwidth. Proportional fairness with respect to the use of the bandwidth is nearly equal to the max-min fairness with respect to the use of air-time [20] .
Proportional fair scheduling at each access point (AP) was proposed in order to get the balance between the aggregate throughput and the fairness in serving all nodes [21] . Proportional fair scheduling also achieves the trade-off between fairness and efficiency if there is a single AP that supports multi-rates.
Proportional fairness at the access point is for the distribution of the bandwidth on nodes in proportion to their data rates, or assigning the time equally among them if there is a single AP and all nodes with similar priority. In the case of multiple AP, proportional fairness will work by maximizing the sum of logarithms of bandwidth allocated for each node [21] .
Fair allocation was proposed [22] for coverage overlapping cells, in order to achieve the proportional fairness. Each new arrival mobile station (MS) will be linked to only one base station (BS). Under this constraint, Bin et al. [22] try to maximize the logarithm of total data rate for all mobile stations. Hence, every single BS must work on maximizing the logarithm of total data rate over its assigned MSs by allocating radio resources in a proportionally fair manner. They formulate general model of proportional fairness for overlapping coverage in multiple wireless cells.
The fair rate allocation problem was considered [23] to monitor the entire coverage area and maximize the total proportionally fairness in WSNs with regular topologies where the aforementioned problem was studied for WSNs with regular topologies that used slotted Aloha MAC layer. Narayanan et al. [23] conclude that, the best topology for the proportionally fair throughput is triangular, square and then hexagonal with respect to the growth size of the network, going from small, medium, to large respectively.
Proportional Fairness Backoff (PFB) scheme was proposed to overcome the funneling effects of the converge-cast patterns in WSNs [24] [25] . Sensors that are in the area around the sink will have larger number of packets than far away sensors. Because of this disproportionate number of accumulated packets, it is very important to decrease the collisions number as well as increasing the throughput to mitigate this funneling effect in the Intensity Region, the region of the funnel.
Yuanfang et al. [24] [25] proposed a new scheme, PFB which provides additional opportunities of channel access to the nodes that are closer to the sink in order to address the funneling effect problem.
This problem has many effects in WSNs such as reducing the amount of the data gathered by the sink, shortening the lifetime of the sensors, breaking the stability as well as decreasing the whole throughput of WSN.
The probabilistic approach [26] provides the proportional fairness without having to solve an optimization problem. Load estimation strategy is used in this approach to estimate the total traffic load for each node, and thus adjusting the contention window according to the difference between the current share of the channel and the required one. So, each node will get a share of the channel that is appropriate to its traffic load. Hence, proportional fairness will be achieved among nodes.
In the next Section, we provide the details of our proposed protocol: Fair MAC protocol (FMAC).
5. Methodology
Wireless sensor networks are usually used in the monitoring applications. When a certain event happens in the monitored area, a large number of sensors will need to transmit their data simultaneously. But because of the WSNs nature, it is possible to find heterogeneous nodes with different data rates. Nodes with lower data rate will occupy channel for longer duration; this will result into higher delays and degrades the whole throughput of the network.
Another issue is that because of this many-to-one data transfer model, all nodes send to the sink, it is important to increase the throughput and reduce the number of collisions in order to mitigate funneling effects in the intensity region, the region of the funnel around the sink. We intend to find a new scheme which will reduce the collisions and utilize the idle slots of time, as well as providing more opportunities to the nodes that have higher data rates. Ultimately, we should achieve the proportional fairness among all nodes in the network.
Fair MAC Protocol (FMAC)
We propose the Fair MAC protocol (FMAC) which is based on the idea of using the medium delay periods within the backoff relative to the data rates of the nodes. This will give more opportunities to access the channel for the fast nodes and thus addresses the performance anomaly problem. The use of the medium periods within the backoff reduces the collisions and utilizes the idle time slots.
In FMAC, when the nodes want to calculate the backoff exponential value (BE), they also retrieve the data rate in order to calculate the medium delay (MD) value. Based on the data rate value, it will choose the value of the medium period (MP). MP is the value that determines how the percentage of MD should be from the actual backoff delay (B_Time). After computing the value of MP, which will be between 10 and 25 for fast nodes and between 26 and 40 for low nodes, this value will be used directly to get the percentage of MD from the current backoff delay value. MD value ranges between 10% and 40% of the current backoff delay. Calculations are done as follows:
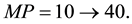 (2)
(2)
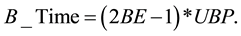 (3)
(3)
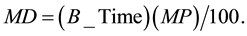 (4)
(4)
where B_Time is the actual backoff delay selected randomly by the node using the values: BE = 1, 2,3,4,5 and the unit backoff period (UBP).
The main stages of the proposed protocol are shown below in Figure 2 where we only concentrate on the case when the node needs to apply the modified backoff algorithm.
Firstly, the node calculates the actual backoff delay (B_Time). Secondly, it retrieves its data rate internally. Considering the data rate to be high or low can vary depending on the type of application used which highlights the important of selecting the right threshold.
If the node has a high data rate, then MP value will be selected randomly from 10 to 25. Else, if the node has a slow data rate, then MP value will be chosen randomly between 26 and 40. Next, the value of MP will be used to get the value of the percentage MD. After the period MD has elapsed, the channel will be assessed. If the channel is found idle, then the node will start the sending process. While if the channel is not idle, the node will
Figure 2. Flow chart of the main stages of FMAC.
continue the backoff process using the remaining time (R_Time), after subtracting the value of the elapsed MD, from the actual backoff delay (B_Time).
Assigning different values of MP for the nodes that have different data rates gives different opportunities for these nodes. In other words, the nodes that have a high data rate will be able to assess the channel after a relatively small delay (MD) from the actual backoff delay (B_Time). This means that if the collision occurs, the fast nodes will get more opportunity to access the channel after starting to apply the backoff process.
On the other hand, slow nodes will have a bigger value of MP and thus they will wait more time (MD) in order to be able to assess the channel. Of course, this will reduce their chances to access the channel, because it may be captured by the fast nodes.
FMAC is expected to contribute significantly in reducing the collisions because of the low probability of choosing the same random number for the backoff delay by any two nodes, and also choosing the same random number for the medium delay by these two nodes.
A very important point that must be taken into account here is that although FMAC gives more opportunity to access the channel for the fast nodes, it does not cause starvation for the slow nodes. This is because all these medium delay periods are actually applied within the main frame of the standard backoff process. FMAC enables both of the fast and slow nodes to assess the channel before the end of the actual backoff delay in order to utilize the idle slots of time and reduce the delay.
Another important point is that medium delay periods used in FMAC is similar to those periods defined in Improved Binary Exponential Backoff (IBEB) [27] , but not the same. Since IBEB does not focus mainly on achieving proportional fairness. Also, the computation of interim periods in IBEB is done more than once and without considering the data rate of the nodes.
6. Simulation and Performance Analysis
We implement Fair MAC protocol (FMAC) discussed in Section 4 using Network Simulator NS-2 version 2.35 under Linux (Fedora 19).
Simulated area is 350 m × 350 m. It contains 11 static nodes deployed randomly without assuming densely deployment but with ensuring the connectivity of the network. One of the nodes is the sink node which is every time located at the middle of the area and it assumed that it has stronger capabilities than other nodes. The remaining nodes are sensor nodes which are sending their data only to the sink in a one hop manner.
We assume the applications that involve sink-oriented transmissions [28] . We consider the uplink direction of the transmissions in a saturated network; each node always has data to be sent.
Nowadays, there are many applications need higher data rates than those that were used in old WSNs. these new applications include: media streaming (audio and video data), target tracking, exploration of disaster and critical controlling [29] -[32] . So, we assume high data rates which are similar to those that provided by 802.11 protocol.
Figure 3 shows an example of the assumed simulation area. In this Figure, the random topology with 20 sensor nodes is shown. There are 14 fast nodes and 6 slow nodes. The number of slow and fast nodes was selected randomly.
FMAC protocol is employed as the protocol for MAC layer. The performance of FMAC protocol is compared every time with that of the standard 802.11 MAC protocol. The mechanism of sending of RTS/CTS is used to safely access the channel for both protocols.
We use different data rates to represent the fast nodes and the slow nodes selecting 2 Mbps and 1 Mbps for this purpose respectively; according to the rates which are provided by the standard MAC 802.11, because of comparison issues.
Constant Bit Rate (CBR), based on the UDP protocol, used as traffic source generator. The number of sent packets was varied by tuning the interval of CBR. However, all nodes have the same interval along the single experiment.
We increase the number of sensor nodes gradually from 10 to 50 nodes in order to test the scalability of our protocol. Although that the numbers of slow and fast nodes are chosen randomly, we ensure that at least 30% of all nodes are slow nodes. We choose this percentage in order to see the impact of slow nodes clearly. Also the number of sent packets was increased gradually from 200 to 1000 packets to ensure the performance of our protocol under different traffic loads.
Figure 3. The virtual simulation area.
The time of simulation is 200 seconds and each experiment was done 30 times, then the average was calculated to produce the graphs for the results provided later. Table 1 shows a summary of the important parameters of the simulation. The values of other parameters unchanged as defined in the files of NS-2.
The major matrices used in this research to evaluate the performance of our proposed protocol are as follows: number of collisions, energy consumption, end-to-end delay, throughput aggregation for the network as a whole and Jain’s fairness index. We also make a comparison of the throughput for all the fast nodes with the throughput for all the slow nodes. The simulation results are provided in the next Section with Illustrative graphs.
7. Results and Discussion of Implications
All networks that are based on contention between nodes mainly experience the problem of collisions. As long as the number of collisions is increasing, the retransmission number is also increased, and thus more energy is consumed. Of course, this will affect the overall performance of the network, especially because of the limited resources in WSN.
On the other hand, as mentioned before, the performance anomaly, which is caused by slow nodes, will degrade the overall throughput of the network. So, we focus in this research on studying and analyzing these main related metrics.
7.1. Collisions
Although using of RTS/CTS mechanism solves the collision problem that is caused by the hidden terminal problem to some extent, there is still another reason for the collision. This reason is the probability of choosing the same number of the backoff interval time by two nodes that are in the range of each other. Figure 4 shows the comparison of collisions number for FMAC protocol and the standard 802.11 protocol under different sizes of the network.
The average number of collisions was reduced clearly when FMAC protocol is used instead of the standard MAC 802.11 protocol with different number of sent packets. Figure 4 shows that when the number of sent packets is increasing, the difference between FMAC and standard MAC 802.11 becomes bigger.
Collisions also tested under different loads; different numbers of sent packets, the results are shown in Figure 5. Although both protocols have a similar number of collisions with small number of nodes as in Figure 5, when increasing the number of nodes there is a noticeable difference for FMAC favor. There is about 4.33% reduction of the collisions number with FMAC protocol.
7.2. End to End Delay
End to end delay also has an effect on the performance of the network as a whole. Figure 6 and Figure 7 show
Figure 4. Comparison of collisions number for FMAC and standard MAC 802.11 (30 nodes).
Figure 5. Comparison of collisions number for FMAC and standard MAC 802.11 (600 packets).
Figure 6. Comparison of end-to-end delay for FMAC and standard MAC 802.11 (40 nodes).
Table 1. Important parameters of the simulation.
the comparison of end-to-end delay for both FMAC protocol and the standard MAC 802.11 protocol under different loads.
We can see from Figure 6 that end-to-end delay with FMAC protocol is slightly bigger than that with the standard MAC 802.11 protocol. However, the delay for both protocols is increased with the increase of the number of sent packets.
In Figure 7, we increase the number of nodes in the network and compare end-to-end delay for both two mentioned protocols.
We can see clearly that the delay with FMAC protocol is very similar to that with the standard MAC 802.11 protocol in all cases. However, the delay becomes a slightly bigger with the largest network size. FMAC increases the average end-to-end delay with only around 0.27%. As a result, such delay is insignificant in WSNs.
7.3. Energy Consumption
The secret of success for any protocol proposed to be applied in WSNs is the power saving.
In Figure 8 we provide the comparison of the average consumed power per node for FMAC and the standard MAC 802.11 protocol under different number of sent packets. When increasing number of sent packets, nodes in FMAC protocol consume a slightly less power than the standard MAC 802.11 protocol. However, both protocols consume more energy with heavy load.
Figure 8 shows the increase in energy consumption becomes slower with high loads, while Figure 9 shows the average consumed power per node for our proposed protocol and the standard MAC 802.11 protocol under different sizes of the network.
In Figure 9 we see that the consumed energy by both protocols is also increased as long as the size of the
Figure 7. Comparison of end-to-end delay for FMAC and standard MAC 802.11 (200 packets).
Figure 8. Comparison of energy consumption for FMAC and standard MAC 802.11 (20 nodes).
network increased. But, with significantly difference in favor of FMAC protocol. FMAC consumed less power than the standard MAC 802.11 protocol.
FMAC utilizes the idle time and reduces the number of retransmissions since the collisions were reduced. The average energy consumption is reduced by about 0.011% when applying FMAC. Although this is a small value, it considered sufficient to ensure that our protocol does not cause more energy consumption.
7.4. Aggregation Throughput
One of the main objectives of the proposed protocol is enhancing the aggregate throughput of the network as a whole. Figure 10 presents the comparison of aggregate throughput for FMAC and the standard MAC 802.11 protocols with different number of sent packets. As Figure 10 indicates when increasing the number of packets sent, FMAC protocol achieves greater throughput than the standard MAC 802.11 protocol. This means that the aggregate throughput of the network becomes larger when using FMAC protocol in a network of high load.
Aggregate throughput for FMAC and the standard MAC 802.11 protocols with different sizes of the network is shown in Figure 11. It shows that FMAC protocol still gives better throughput than the standard MAC 802.11 protocol. Of course, this significant difference in favor of FMAC is due to its ability to decrease the collisions.
Generally, FMAC protocol achieved an increase in the average aggregate throughput in all cases of about 1.9% higher than the standard MAC 802.11 protocol.
7.5. Proportional Fairness
WSN is usually used for monitoring purposes, which require gathering information from a large number of nodes in a fair manner as possible, while caring about throughput and aggregation throughput per node.
Figure 9. Comparison of energy consumption for FMAC and standard MAC 802.11 (1000 packets).
Figure 10. Comparison of aggregate throughput for FMAC and standard MAC 802.11 (50 nodes).
We are focusing on achieving proportional fairness between slow nodes and fast nodes. So, we calculate the average throughput for all fast nodes and then we compare this average with the average throughput for all slow nodes. Every time there is about 30% of nodes that have slow data rate.
Figure 12 shows this comparison for the standard 802.11 MAC protocol with different number of nodes, while Figure 13 shows the same thing but for FMAC protocol. The average of the throughput for all slow nodes is still larger than the average of the throughput for all fast nodes while the size of the network is increasing with the standard MAC 802.11 protocol as shown in Figure 12. Despite this, the slow nodes constitute only about 30%
Figure 11. Comparison of aggregate throughput for FMAC and standard MAC 802.11 (400 packets).
Figure 12. Comparison throughput of fast and slow nodes in standard MAC 802.11 (200 packets).
Figure 13. Comparison throughput of fast and slow nodes in FMAC (200 packets).
of the total number of nodes in the network. On the other hand, we can see in Figure 13 that the average of throughput for all slow nodes clearly becomes less than the average of the throughput for all fast nodes when applying FMAC protocol while the size of the network is increasing.
The same comparison between these two protocols is shown in Figure 14 and Figure 15 respectively, but this time with a different number of sent packets. In Figure 14, we can see that the difference in the average throughput for all slow nodes and the average throughput for all fast nodes becomes more significance when the number of sent packets is increased with the standard MAC 802.11 protocol. Again, the slow nodes that comprise about only 30% of the total number of nodes in the network have a higher average of throughput.
We can see exactly the opposite in Figure 15; the average of the throughput for all slow nodes significantly becomes less than the average of the throughput for all fast nodes when the number of sent packets is increased with FMAC 802.11 protocol. FMAC protocol achieves proportional fairness, between slow and fast nodes, more than the standard MAC 802.11 in all cases. But the difference is noticed more clearly with increasing of number of sent packets. This is due the fact that FMAC protocol gives more chance for the fast nodes to access the channel.
7.6. Fairness Index
Fairness index measures how the channel is shared equally by all nodes. It is concerned with the minimum number of transmitted packets by any individual node in the network relative to the maximum number of transmitted packets by any of the nodes in the network [33] . Jain’s index gives the fairness criterion taking into account all the nodes in the network [34] . Hence, the higher value of this index, the better fairness between all nodes. Jain’s fairness index is given by [35] :
Figure 14. Comparison throughput of fast and slow nodes in standard MAC 802.11 (10 nodes).
Figure 15. Comparison throughput of fast and slow nodes in FMAC (10 nodes).

where n is the number of all contending nodes and xi is share of the allocation which given for the ith node.
We compute Jain’s fairness index twice. The first time is for FMAC protocol with different sizes of the network and for the average number of sent packets. Figure 16 shows the comparison of this index for FMAC and the standard MAC 802.11 protocol.
The second time is shown in Figure 17, which is also for FMAC protocol but with different loads in the network and for the average number of nodes with the comparison of the standard MAC 802.11 protocol.
From both Figure 16 and Figure 17, it is clear that the value of Jain’s fairness index for FMAC protocol is higher than the standard MAC 802.11 protocol in all cases. As the load in the network increases, the difference between the values of the index for both two protocols becomes bigger. Also we can see in Figure 16 that with the largest network size, the value of the index for FMAC protocol becomes very close to 1, which is the maximum value of Jain’s fairness index and it indicates a higher achieved fairness.
8. Conclusion and Future Work
The main objective of the proposed algorithm is to design a new MAC protocol that achieves proportional fairness between nodes with different data rates in WSNs. Fair MAC protocol (FMAC) aims to enhancing the aggregate throughput as well as achieving the proportional fairness between all nodes in the network by reducing the collisions number and utilizing the idle slots of time.
The core idea of FMAC protocol is that each node computes a medium delay period in proportion to its data rate, directly after the computation of the actual backoff delay period. Then, when the medium period has
Figure 16. Comparison of Jain’s fairness index of FMAC and standard MAC 802.11 (average load).
Figure 17. Comparison of Jain’s fairness index of FMAC and standard MAC 802.11 (average number of nodes).
elapsed, it will check the channel to be idle. If the channel is busy, the node will continue the backoff process with remaining delay of the actual period. This will achieve proportional fairness and maximize the aggregate throughput by giving more probability to access the channel for the fast nodes. FMAC protocol is compatible with the standard IEEE 802.11, only small changes are required. However, the proposed protocol is also applicable in WLANs because it does not mainly depend on the nature of WSNs.
The experimental results show that when using FMAC the transmission becomes faster with less power consumption due to the better utilization of idle time slots. Also the average number of collisions is reduced by 4% and the average aggregation throughput increased by 1.9%. Using Jain’s fairness index, FMAC protocol obtains higher values. Thus, experimental results indicate that FMAC protocol achieves its main objectives.
The experiments also reveal some interesting future work such as achieving more aggregated throughput by adjusting the interim delay periods more specifically. Also we may compare our protocol against other protocols in existence today, analytically and/or using the simulation. Another possible future direction would be to perform the proposed protocol in different environments or using real world experiments.
Acknowledgements
This paper was supported by NSTIP strategic technologies program project number 10-INF1184-02 in the Kingdom of Saudi Arabia.
References
- Xu, N. (2002) A Survey of Sensor Network Applications. IEEE Communications Magazine, 40, 102-114.
- Corke, P., Wark, T., Jurdak, R., Wen, H., Valencia, P. and Moore, D. (2010) Environmental Wireless Sensor Networks. Proceedings of the IEEE, 98, 1903-1917. http://dx.doi.org/10.1109/JPROC.2010.2068530
- Wang, Z.Q., Yu, F.Q., Tao, L.Q. and Zhang, Z.S. (2011) A Fairness Spatial TDMA Scheduling Algorithm for Wireless Sensor Network. 12th International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT), Gwangju, 20-22 October 2011, 348-353.
- Sridharan, A. and Krishnamachari, B. (2007) Maximizing Network Utilization with Max-Min Fairness in Wireless Sensor Networks. 5th International Symposium on Modeling and Optimization in Mobile, Ad Hoc and Wireless Networks and Workshops, Limassol, 16-20 April 2007, 1-9. http://dx.doi.org/10.1109/WIOPT.2007.4480030
- Pei, H., Li, X., Soltani, S., Mutka, M.W. and Ning, X. (2013) The Evolution of MAC Protocols in Wireless Sensor Networks: A Survey. IEEE Communications Surveys & Tutorials, 15, 101-120. http://dx.doi.org/10.1109/SURV.2012.040412.00105
- Kumar, B., Yadav, R.K. and Challa, R.K. (2010) Comprehensive Performance Analysis of MAC Protocols for Wireless Sensor Networks. International Conference on Computer and Communication Technology (ICCCT), Allahabad, 17-19 September 2010, 342-347. http://dx.doi.org/10.1109/ICCCT.2010.5640504
- Patil, U.A., Modi, S.V. and Suma, B. (2013) Analysis and Implementation of IEEE 802.11 MAC Protocol for Wireless Sensor Networks. International Journal of Engineering Science and Innovative Technology (IJESIT), 2, 278-284.
- Singh, U.K., Phuleriya, K.C. and Laddhani, L. (2012) Study and Analysis of MAC Protocols Design Approach for Wireless Sensor Networks. International Journal of Advanced Research in Computer Science and Software Engineering, 2, 79-83.
- Duda, A. (2008) Understanding the Performance of 802.11 Networks. 19th International Symposium on Personal, Indoor and Mobile Radio Communications, Cannes, 15-18 September 2008, 1-6. http://dx.doi.org/10.1109/PIMRC.2008.4699942
- Kabara, J. and Calle, M. (2012) MAC Protocols Used by Wireless Sensor Networks and a General Method of Performance Evaluation. International Journal of Distributed Sensor Networks, 2012, Article ID: 834784. http://dx.doi.org/10.1155/2012/834784
- Jain, S. and Mahajan, R. (2000) Wireless LAN MAC Protocols.
- Nadeem, T. and Ashok, A. (2005) Performance of IEEE 802.11 Based Wireless Sensor Networks in Noisy Environments. 24th IEEE International Conference on Performance, Computing, and Communications, Phoenix, 7-9 April 2005, 471-476. http://dx.doi.org/10.1109/PCCC.2005.1460615
- Zhai, H.Q., Kwon, Y. and Fang, Y.G. (2004) Performance Analysis of IEEE 802.11 MAC Protocols in Wireless LANs. Wireless Communications and Mobile Computing, 4, 917-931. http://dx.doi.org/10.1002/wcm.263
- Bononi, L., Conti, M. and Gregori, E. (2000) Design and Performance Evaluation of an Asymptotically Optimal Backoff Algorithm for IEEE 802.11 Wireless LANs. Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, 4-7 January 2000, 10. http://dx.doi.org/10.1109/HICSS.2000.926987
- Khalaj, A., Yazdani, N. and Rahgozar, M. (2007) Effect of the Contention Window Size on Performance and Fairness of the IEEE 802.11 Standard. Wireless Personal Communications, 43, 1267-1278. http://dx.doi.org/10.1007/s11277-007-9300-5
- Weinmiller, J., Woesner, H. and Wolisz, A. (1996) Analyzing and Improving the IEEE 802.11-MAC Protocol for Wireless LANs. Proceedings of the 4th International Workshop on Modeling, Analysis, and Simulation of Computer and Telecommunication Systems, MASCOTS’96, San Jose, 1-3 February 1996, 200-206.
- Chen, S. and Zhang, Z. (2006) Localized Algorithm for Aggregate Fairness in Wireless Sensor Networks. Proceedings of the 12th Annual International Conference on Mobile Computing and Networking, Los Angeles, 24-29 September 2006, 274-285. http://dx.doi.org/10.1145/1161089.1161121
- Wu, J.H. and Luo, J. (2012) Research on Multi-Rate in Wireless Sensor Network Based on Real Platform. 2nd International Conference on Consumer Electronics, Communications and Networks (CECNet), Yichang, 21-23 April 2012, 1240-1243.
- Yang, T., Kulla, E., Oda, T., Barolli, L., Younas, M. and Takizawa, M. (2012) Performance Evaluation of WSNs Considering MAC and Routing Protocols Using Goodput and Delay Metrics. 15th International Conference on Network- Based Information Systems (NBiS), Melbourne, 26-28 September 2012, 341-348.
- Jiang, L.B. and Liew, S.C. (2005) Proportional Fairness in Wireless LANs and Ad Hoc Networks. IEEE Wireless Communications and Network Conference (WCNC), 3, 1551-1556.
- Li, L., Pal, M. and Yang, Y.R. (2008) Proportional Fairness in Multi-Rate Wireless LANs. IEEE INFOCOM 2008, The 27th Conference on Computer Communications, Phoenix, 13-18 April 2008, 1004-1012.
- Chen, B.B. and Chan M.C. (2006) Proportional Fairness for Overlapping Cells in Wireless Networks. IEEE 64th Vehicular Technology Conference, Montreal, 25-28 September 2006, 1-5.
- Narayanan, S., Jun, J.H., Pandit, V. and Agrawal, D.P. (2011) Proportionally Fair Rate Allocation in Regular Wireless Sensor Networks. IEEE Conference on Computer Communications Workshops, Shanghai, 10-15 April 2011, 549-554. http://dx.doi.org/10.1109/INFCOMW.2011.5928874
- Chen, Y.F., Li, M.C., Wand, L., Yuan, Z.X., Sun, W.P., Zhu, C.S., Zhu, M. and Shu, L. (2009) A Proportional Fair Backoff Scheme for Wireless Sensor Networks. IEEE 6th International Conference on Mobile Adhoc and Sensor Systems, Macau, 12-15 October 2009, 971-976.
- Chen, Y.F., Li, M.C., Shu, L., Wang, L. and Hara, T. (2012) A Proportional Fairness Backoff Scheme for Funnelling Effect in Wireless Sensor Networks. Transactions on Emerging Telecommunications Technologies, 23, 585-597. http://dx.doi.org/10.1002/ett.2516
- Chakraborty, S., Swain, P. and Nandi, S. (2013) Proportional Fairness in MAC Layer Channel Access of IEEE 802.11s EDCA Based Wireless Mesh Networks. Ad Hoc Networks, 11, 570-584. http://dx.doi.org/10.1016/j.adhoc.2012.08.003
- Khan, B.M., Ali, F.H. and Stipidis, E. (2010) Improved Backoff Algorithm for IEEE 802.15.4 Wireless Sensor Networks. 2010 IFIP, Wireless Days (WD), Venice, 20-22 October 2010, 1-5.
- Akan, O.B. and Akyildiz, I.F. (2005) Event-to-Sink Reliable Transport in Wireless Sensor Networks. IEEE/ACM Transactions on Networking, 13, 1003-1016. http://dx.doi.org/10.1109/TNET.2005.857076
- Jagadeesha, R. and Alfandi, O. (2013) Implementation of WSN Protocol on a Heterogeneous Hardware. Journal of Engineering Science and Technology, 8, 521-539.
- Zhu, N.H., Du, W., Navarro, D., Mieyeville, F. and Connor, I.O. (2011) High Data Rate Wireless Sensor Networks Research. Proceedings of 14ème Journées Nationales du Réseau Doctoral de Micro et Nanoélectronique (JNRDM 2011), Paris, 23-25 May 2011.
- Zhu, N.H. and O’Connor, I. (2013) Performance Evaluations of Unslotted CSMA/CA Algorithm at High Data Rate WSNs Scenario. 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, 1-5 July 2013, 406-411.
- Kohvakka, M., Arpinen, T., Hännikäinen, M. and Hämäläinen, T.D. (2006) High-Performance Multi-Radio WSN Platform. Proceedings of the 2nd International Workshop on Multi-Hop Ad Hoc Networks: From Theory to Reality, Florence, 26 May 2006, 95-97.
- Nithya, B., Mala, C. and KumarB, V. (2012) Simulation and Performance Analysis of Various IEEE 802.11 Backoff Algorithms. Procedia Technology, 6, 840-847. http://dx.doi.org/10.1016/j.protcy.2012.10.102
- Bin Sediq, A., Gohary, R.H. and Yanikomeroglu, H. (2012) Optimal Tradeoff between Efficiency and Jain’s Fairness Index in Resource Allocation. IEEE 23rd International Symposium on Personal Indoor and Mobile Radio Communications (PIMRC), Sydney, 9-12 September 2012, 577-583.
- Jain, R., Chiu, D.-M. and Hawe, W.R. (1984) A Quantitative Measure of Fairness and Discrimination for Resource Allocation in Shared Computer System: Eastern Research Laboratory. Digital Equipment Corporation.



















