Open Journal of Discrete Mathematics
Vol.06 No.04(2016), Article ID:70340,10 pages
10.4236/ojdm.2016.64020
Near-Optimal Placement of Secrets in Graphs
Werner Poguntke
Fachbereich Technische Betriebwirtschaft, Fachhochschule Südwestfalen, Hagen, Germany

Copyright © 2016 by author and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY 4.0).
http://creativecommons.org/licenses/by/4.0/



Received: January 5, 2016; Accepted: August 30, 2016; Published: September 2, 2016
ABSTRACT
We consider the reconstruction of shared secrets in communication networks, which are modelled by graphs whose components are subject to possible failure. The reconstruction probability can be approximated using minimal cuts, if the failure probabilities of vertices and edges are close to zero. As the main contribution of this paper, node separators are used to design a heuristic for the near-optimal placement of secrets sets on the vertices of the graph.
Keywords:
Graph Algorithm, Cut, Secret Sharing, Approximation, Network Design

1. Introduction
We consider a scenario where a set of secrets is shared among individuals connected by a communication network, in such a way that no individual holds all the secrets. In other words, several individuals have to cooperate in order to reconstruct the whole secret set.
Secret sharing schemes were first introduced and investigated in [1] and [2] . In an (m, k)-threshold scheme, a secret is divided into k shares in such a way that the secret can be reconstructed whenever at least m of the shares have been collected. Survey papers on secret sharing schemes and threshold schemes are [3] and [4] .
In this paper, we always assume m = k, i.e. it is necessary to collect all of the shares in order to reconstruct the secret. Subsets of the set of all secrets (called shares) are stored in the nodes of a communication network whose nodes and links are subject to failure with certain probability. One vertex is assumed to be the user node.
We consider two main problems:
- to calculate the reconstruction probability of the secrets, given an assignment of shares to vertices, and
- to assign shares to vertices such that the reconstruction probability of secrets gets as large as possible.
Papers closely related are [5] - [7] .
As the main contribution of this paper, we present an approximation algorithm for the determination of the reconstruction probability, as well as a heuristic for the near optimal placement of shares.
2. Shared Secret Schemes in Networks with Failures
2.1. The Model
In this paper, a communication network is modelled by a finite undirected graph G = (V,E), where V consists of n vertices, and E is the set of edges. Let a finite set 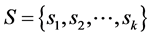 of secrets be given, and let
of secrets be given, and let 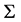 be a set of nonempty subsets (shares) of S. One node
be a set of nonempty subsets (shares) of S. One node 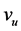 in V is supposed to be the user node. A shared secret scheme or secret sharing scheme on G is a 1-1 mapping
in V is supposed to be the user node. A shared secret scheme or secret sharing scheme on G is a 1-1 mapping
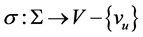 ,
,
i.e. each of the selected shares is placed on some node of the graph other than the user node.
It is further assumed that the vertices as well as the edges of G may possibly fail, i.e. they work with a certain probability only, and that the states of all single vertices and edges are independent from each other. In this paper, this probability is assumed to equal a fixed p (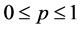 ) for all vertices and all edges. The only exception is the user node
) for all vertices and all edges. The only exception is the user node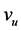 ; for technical reasons which will become clear later, it is assumed that
; for technical reasons which will become clear later, it is assumed that 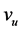 always works.
always works.
The reconstruction probability of 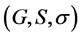 is the probability that the complete secret set S can be reconstructed by the user node, i.e. the probability that along paths using vertices and edges not having failed and starting from node
is the probability that the complete secret set S can be reconstructed by the user node, i.e. the probability that along paths using vertices and edges not having failed and starting from node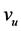 , it is possible to collect all the secrets
, it is possible to collect all the secrets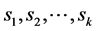 . It is obvious that as a function of p, the reconstruction probability is a polynomial. We denote this polynomial by r(p).
. It is obvious that as a function of p, the reconstruction probability is a polynomial. We denote this polynomial by r(p).
More formally, we call any subset 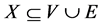 a state. A state X is operational if the secrets can be reconstructed provided each element of X works. In these terms, the reconstruction probability is the probability that the vertices and edges not having failed constitute an operational state.
a state. A state X is operational if the secrets can be reconstructed provided each element of X works. In these terms, the reconstruction probability is the probability that the vertices and edges not having failed constitute an operational state.
One problem is to determine the polynomial r(p). It can also be of interest to merely find the value 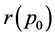 for a given
for a given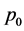 . Given the graph G, set
. Given the graph G, set 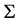 of shares and probability value
of shares and probability value 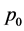 for all vertices and edges, another problem is to design a shared secret scheme (i.e. placement of shares on the vertices) such that
for all vertices and edges, another problem is to design a shared secret scheme (i.e. placement of shares on the vertices) such that 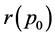 becomes maximum.
becomes maximum.
2.2. Introductory Examples and Previous Results
The diagram in Figure 1 shows a graph 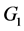 consisting of eight vertices and twelve edges. As in all the examples of this paper, the node labelled “1” is the user node
consisting of eight vertices and twelve edges. As in all the examples of this paper, the node labelled “1” is the user node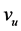 . Four secrets
. Four secrets 







Figure 1. Six shares on graph
A shared secret scheme (i.e. placement of shares on vertices) is also shown in the diagram. The reconstruction probability polynomial turns out to be:
Hence, e.g., 
Different variants of the model and related problems have been considered by many authors. Nearly all of the problems turn out to be NP-hard. In particular, it is easy to see that determining what we have called 
In [6] , 

For the same graph 
with
As usual, a subset C of 


Mincuts play a central role in the rest of this paper. The dual approach based on inclusion-minimal operational sets (sometimes called minpaths) is used in [6] . For a survey on the roles of cuts and paths in network reliability, see [8] .
For s in S, call a subset C of 

In the following, to make a clear distinction, and following the terminology of [13] , we call a subset 



To illustrate the notion of cuts for secret sharing schemes, we look at another example which was also considered in [6] . Figure 3 shows a graph 







A shared secret scheme is also shown in the diagram, with reconstruction polynomial

and
In this example, there are no one-element mincuts. The mincuts consisting of two elements turn out to be the following:





Figure 4 presents a slightly better placement of the shares on the nodes of 

Figure 2. Another share assignment on graph
Figure 3. Six shares on graph
Figure 4. Another share assignment on graph
with
3. Using Mincuts for Approximations
The following obvious fact is the basis of our approximation to
Remark 1.
A state 

In other words, this means that 
Theorem 1.
Let 
Proof:
Let 

By inclusion-exclusion, this leads to:
Using independence of the states of single elements, one finally gets the formula of the theorem.
If we now set
for




At this point, it is certainly plausible that if 

As usual, we define
For the above examples, let 



where the following notation is used: 







Table 1 gives an overview on the secret sharing schemes considered in the examples. As can be seen, for these graphs of modest size, 

4. A Heuristic for Share Assignment Based on Node Separators
Once the relevance of mincuts for the reconstruction probability has become clear, we now turn to the question what makes a shared secret scheme have few mincuts. It turns out that, basically, there are two different effects that make a set X of vertices and edges a cut:
・ X is a node separator, and the complete secret set S cannot be reconstructed by 
・ X contains all vertices that carry one specific secret
To illustrate this, let us look at the example of Figure 3 again. 




It is now possible to identify the reason why the shared secret scheme of Figure 4 has fewer two-element mincuts than the scheme shown in Figure 3: In the scheme shown in Figure 4, 


Table 1. Reconstruction probabilities 

From these observations, we conclude that when designing a shared secret scheme, it is advantageous to place “secret mincuts” on node separators of the graph.
The heuristic presented also tries to avoid assigning a share to a node lying “behind” another node which carries a larger share. This point is illustrated via the small example presented in Figure 5: the assignment in diagram (a) is obviously more reliable than the one in diagram (b), since placing share 

We are now ready to present our heuristic for share assignment. The main idea is to place large shares on nodes close to 



We assume a graph 






is defined by iteration, according to the following algorithm.
We begin with precomputations consisting of three algorithms:
・ Algorithm BFS-tree
・ Algorithm separators
・ Algorithm list of shares
We next describe the algorithm for share assignment.
It is assumed that the algorithms BFS-tree, separators, and list of shares have been executed and have produced the numbering 


Figure 5. Two share assignments.
We next describe the algorithm for share assignment.
The algorithm share assignment assigns a share to the next node according to the following principles:
・ (1st priority) nodes inside node separators should carry common secrets
・ (2nd priority) nodes along paths in the BFS-tree should not carry common secrets
This algorithm (including the precomputations) is polynomial in n, the number of vertices of the graph.
It can be easily checked that for the examples considered above, the algorithm produces the share assignments with higher reconstruction probability.
5. Conclusion
The presented algorithm for share assignment in communication networks uses node separators of the underlying graphs. This algorithm produces better results than simply placing large shares close to the user node, as is suggested in previous publications. One interesting question for further research is that under which assumptions concerning the underlying graph and set of shares, the heuristic presented here results in an optimal placement of the shares on the nodes.
Acknowledgements
This research was supported by Fachhochschule Südwestfalen―University of Applied Sciences.
Cite this paper
Poguntke, W. (2016) Near-Optimal Placement of Secrets in Graphs. Open Journal of Discrete Mathematics, 6, 238-247. http://dx.doi.org/10.4236/ojdm.2016.64020
References
- 1. Blakley, R. (1979) Safeguarding Cryptographic Keys. Proceedings of the AFIPS 1979 National Computer Conference, 48, 313-317.
- 2. Shamir, A. (1979) How to Share a Secret. Communications of the ACM, 22, 612-613.
http://dx.doi.org/10.1145/359168.359176 - 3. Simmons, G.J. (1991) An Introduction to Shared Secret and/or Shared Control Schemes and Their Application. Contemporary Cryptology, IEEE Press, New York, 441-497.
- 4. Stinson, D.R. (1992) An Explication of Secret Sharing Schemes. Designs, Codes, and Cryptography, 2, 357-390.
http://dx.doi.org/10.1007/BF00125203 - 5. Blundo, C., de Santis, A., Stinson, D.R. and Vaccaro, U. (1995) Graph Decomposition and Secret Sharing Schemes. Journal of Cryptology, 8, 39-64.
http://dx.doi.org/10.1007/BF00204801 - 6. Lee, C.-Y., et al. (1999) A Probability Model for Reconstructing Secret Sharing under the Internet Environment. Information Sciences, 116, 109-127.
http://dx.doi.org/10.1016/S0020-0255(98)10104-4 - 7. PÖnitz, A. and Sans, O. (2001) Computing the Reconstruction Probability of Distributed Secret Sharing Schemes Using the Composition Method. (Unpublished Manuscript)
- 8. Colbourn, J. (1987) Combinatorics of Network Reliability. Oxford University Press, Oxford.
- 9. Shier, D.R. (1991) Network Reliability and Algebraic Structures. Clarendon Press, Oxford.
- 10. Bienstock, D. (1988) Some Lattice-Theoretic Tools for Network Reliability Analysis. Mathematics of Operations Research, 13, 467-478.
http://dx.doi.org/10.1287/moor.13.3.467 - 11. Tittmann, P. and Blechschmidt, A. (1991) Reliability Bounds Based on Network Splitting. Elektronische Informationsverarbeitung und Kybernetik, 27, 317-326.
- 12. Poguntke, W. and Simonet, G. (2004) Secrets and Separators. ALGCO—Algorithmes, Graphes et Combinatoire, LIRMM—Laboratoired’Informatique de Robotique et de Microélectronique de Montpellier, Report 04001.
- 13. Kloks, T. and Kratsch, D. (2006) Listing All Minimal Separators of a Graph. Proceedings of the 11th Annual Symposium on Theoretical Aspects of Computer Science, Springer, LNCS 775, 759-768.
http://dx.doi.org/10.1137/s009753979427087x - 14. Poguntke, W. (2003) Using Mincuts to Design Secret Sharing Schemes in Graphs. Extended Abstract. Electronic Notes in Discrete Mathematics, 13, 97-102.
http://dx.doi.org/10.1016/S1571-0653(04)00447-0
NOTES
1In this paper, all calculations were done using Matlab.



















