Paper Menu >>
Journal Menu >>
 Open Journal of Applied Sciences, 2013, 3, 53-57 Published Online March 2013 (http://www.scirp.org/journal/ojapps) Copyright © 2013 SciRes. OJAppS Multi-Faces Image Recognition Jung-soo Han, Jeong-heon Lee, Gui-Jung Kim Division of Communication & Information, Baekseok University, Cheonan, Korea National Information Society Agency, Seoul, Korea Department of Biomedical Engineering, Konyang University, Nonsan, Korea Email: jshan@bu.ac.kr, opendori@gmail.com, gjkim@konyang.ac.kr Received 2012 ABSTRACT The paper suggests a great improvement in the recognition rate and speed by overcoming the disadvantage of 3D image processing taking a long time as well as that of 2D images weak in postures through correcting shooting angles with 3D data taken by multi cameras followed by application of the developed hybrid face recognition technology. Keywords: Hybrid; Face Recognition; 3D; 2D; Image Recognition 1. Introdu ction As of 2009, the ISO's two groups, SC29/WG11 (MPEG) and SC37, have been standardized in terms of face detection and recognition. Although technology of face detection and recognition has achieved substantial results, research on face detection and recognition technology related to an environment integrated into CCTV has just started. In Korea, as CCTV-based face detection and recognition technology serves a crucial role in preventing terror and crime and arresting criminals, its necessity is consi dered at national level. Currently, when it comes to arresting criminals, not only CCTVs installed in the nation cannot identify personal characteristics, but also a read rate is low, caused by light effects such as slow face recognition speed, lighting, and diverse facial pose and expression, although the face is detected or recognized[1]. As such, to overcome limited technology on CCTV-based face detection and recognition technology, research is conducted on detection and recognition tech- nology on various faces such as a recent IR-based face recognition technology strong in lighting. Particularly, developing outstanding face detection technology is a prerequisite for development of high-performance facial recognition system. However, the existing face detection method is to find a face location in an image, which has many problems to solve including face judgment, differ- ent-sized face search, exact-domain face search, face de- tection speed, result combination, along with problems in detecting face. A CCTV stands for Closed Circuit Televi- sion, communication equipment that enables a specific person to receive images collected by shooting equipment installed in a place after transmission through closed wired/wireless channels. Currently, although security thr ea t s occurs to CCTVs, regarding CCTV installment and operation, the law of it is not properly established, and the system of it is not properly conducted [2-5]. In this paper, we explained unmanned security control system and simulated faces recognition process . 2. Unmanned security Robots Unmanned security surveillance robots can recognize authori zed/una uthor ized by real-time processing images input by HD-level camera, save a relevant image to transmit via control server, store transmitted image ac- cording to a policy, which enables a controller to provide a preview function after searching saved images through a search function. Unmanned security surveillance robot's image recognition system has the following composition elements. Such as Figure 1, it serves as a function to detect a face in a HD-level image; extract and record face characteristic data to compare with authorizer. With regular hour (day- time) fixed mode, it serves as an alert surveillance (HD-level CCTV function), and automatically changes into move mode in set time (e.g. night time, after school, holidays, etc.), alert surveillance is performed by moving in a set place and a surveillance poor site. It can be re- charged in a fixed mode, and saved images can be trans- mitted to the control center in a move mode when an alert surveillance. In a move mode, when an unauthor i zed is found, a warning message is transmitted to the unautho- rized by speaker warning and lamp alarm. Saved images during an alert surveillance are saved in the inside of the robot, and when it is recharged, they are transmitted to the control center to save. To compare information between authori zed/unaut horiz ed, a captured frame (or image) in a 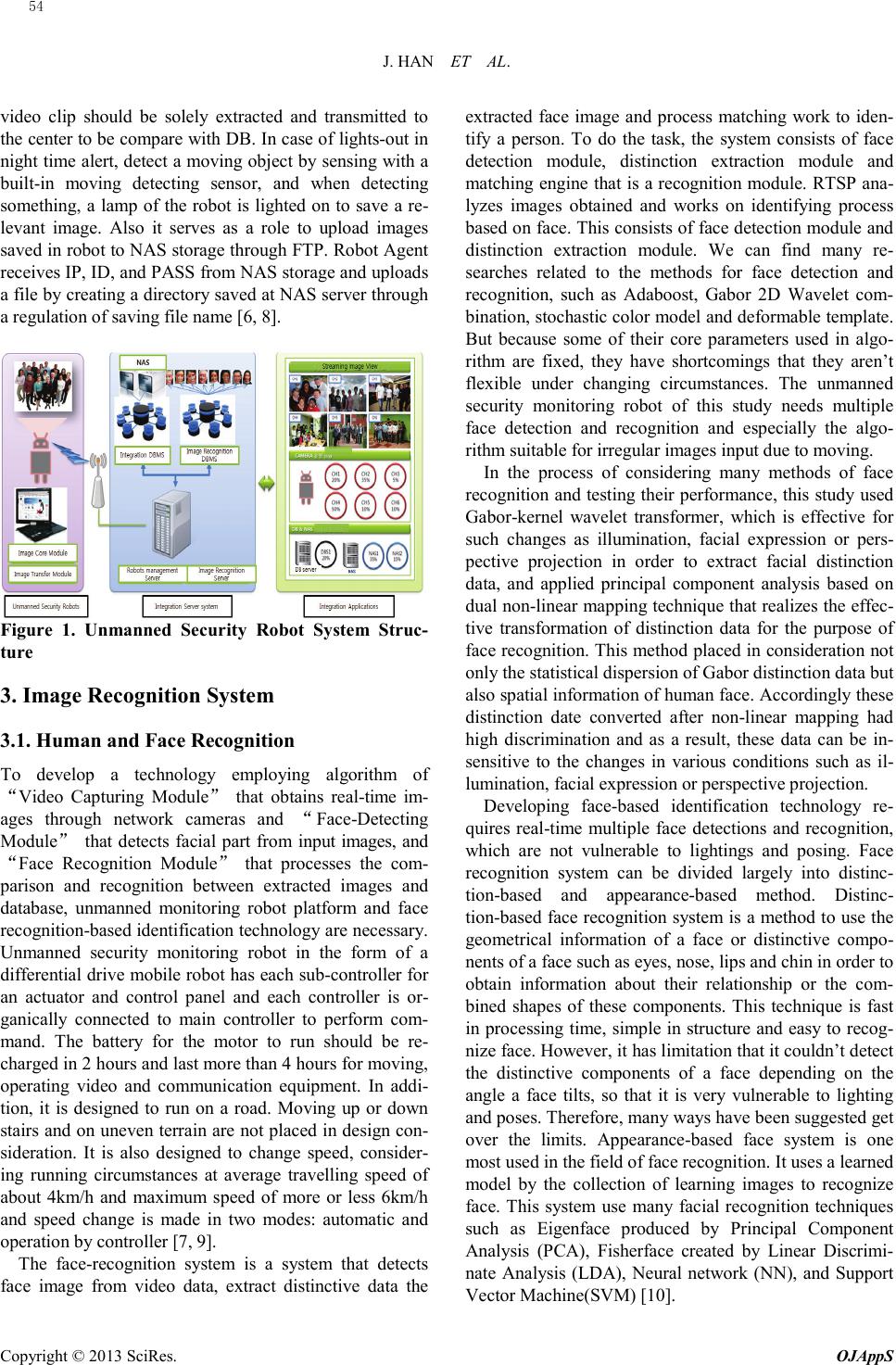 J. HAN ET AL. Copyright © 2013 SciRes. OJAppS video clip should be solely extracted and transmitted to the center to be compare with DB. In case of lights-out in night time alert, detect a moving object by sensing with a built-in moving detecting sensor, and when detecting something, a lamp of the robot is lighted on to save a re- levant image. Also it serves as a role to upload images saved in robot to NAS storage through FTP. Robot Agent receives IP, ID, and PASS from NAS storage and uploads a file by creating a directory saved at NAS server through a regulation of saving file name [6, 8]. Figure 1. Unmanned Security Robot System Struc- ture 3. Image Recognition System 3.1. Human and Face Recognition To develop a technology employing algorithm of “Video Capturing Module” that obtains real-time im- ages through network cameras and “Face-Detecting Modul e” that detects facial part from input images, and “Face Recognition Module” that processes the com- parison and recognition between extracted images and database, unmanned monitoring robot platform and face reco gnitio n-based identification technology are necessary. Un mann ed security monitoring robot in the form of a differential drive mobile robot has each sub-controller for an actuator and control panel and each controller is or- ganically connected to main controller to perform com- mand. The battery for the motor to run should be re- charged in 2 hours and last more than 4 hours for moving, operating video and communication equipment. In addi- tion, it is designed to run on a road. Moving up or down stairs and on uneven terrain are not placed in design con- sideration. It is also designed to change speed, consider- ing running circumstances at average travelling speed of about 4km/h and maximum speed of more or less 6km/h and speed change is made in two modes: automatic and operation by controller [7, 9]. The face-recognition system is a system that detects face image from video data, extract distinctive data the extracted face image and process matching work to iden- tify a person. To do the task, the system consists of face detection module, distinction extraction module and matching engine that is a recognition module. RTSP ana- lyzes images obtained and works on identifying process based on face. This consists of face detection module and distinction extraction module. We can find many re- searches related to the methods for face detection and recognition, such as Adaboost, Gabor 2D Wavelet com- bination, stochastic color model and deformable template. But because some of their core parameters used in algo- rithm are fixed, they have shortcomings that they aren’t flexible under changing circumstances. The unmanned security monitoring robot of this study needs multiple face detection and recognition and especially the algo- rithm suitable for irregular images input due to moving. In the process of considering many methods of face recognition and testing their performance, this study used Gabor-kernel wavelet transformer, which is effective for such changes as illumination, facial expression or pers- pective projection in order to extract facial distinction data, and applied principal component analysis based on dual non-linear mapping technique that realizes the effec- tive transformation of distinction data for the purpose of face recognition. This method placed in consideration not only the statistical dispersion of Gabor distinction data but also spatial information of human face. Accordingly these distinction date converted after non-linear mapping had high discrimination and as a result, these data can be in- sensitive to the changes in various conditions such as il- lumination, facial expression or perspective projection. Developing face-based identification technology re- quires real-time multiple face detections and recognition, which are not vulnerable to lightings and posing. Face recognition system can be divided largely into distinc- tion-based and appearance-based method. Distinc- tion-based face recognition system is a method to use the geometrical information of a face or distinctive compo- nents of a face such as eyes, nose, lips and chin in order to obtain information about their relationship or the com- bined shapes of these components. This technique is fast in processing time, simple in structure and easy to recog- nize face. However, it has limitation that it couldn’t detect the distinctive components of a face depending on the angle a face tilts, so that it is very vulnerable to lighting and poses. Therefore, many ways have been suggested get over the limits. Appearance-based face system is one most used in the field of face recognition. It uses a learned model by the collection of learning images to recognize face. This system use many facial recognition techniques such as Eigenface produced by Principal Component Analysis (PCA), Fisherface created by Linear Discrimi- nate Analysis (LDA), Neural network (NN), and Support Vector Machine(SVM) [10]. 54  J. HAN ET AL. Copyright © 2013 SciRes. OJAppS 3.2. Intellectual Image Monitoring System Intellectual Image Monitoring/Controlling System con- sists of robot-operation management server and im- age-recognition management server. This system receives image information in real time from network camera built in a security monitoring robot, displays concerned infor- mation on 9 screens, and monitors and remote control the status of a robot platform. Also the system includes inte- grated management DB that controls the storage and dis- posal of transmitted images and data necessary for robot operation and system controlling, image recognition DB that manages data of image recognition and licens- er/ non -licenser, and the function of control and manage the entire system in interlocking with other systems. HD Network Camera Control Module use a camera of HD quality to receive images in real time through robot and supports and control the camera remote to make it (robot) act actively against unexpected events [10, 11]. As DB operating system that receives, stores, deletes or search images RTSP recorder saves in accordance with related policy, Image Storage DB performs a role of managing integrated controlling server. Im- age-recognition management server saves facial informa- tion (facial distinction date and concerned facial thumb- nails) from a robot’s Image Analyzer to set up image tracking and face recognition DB in storage. After saving them, it compares the new information with the data al- ready registered in DB to discriminate and then send the results back to the robot. 3.3. Security Monitoring Service Escaping from the conventional mode of one-way securi- ty monitoring system and focusing on mobility and self-controlling, which are characteristics of a robot, this paper places its objective in the development and com- mercialization of intellectual security monitoring/ control- ling system that can run unmanned 24 hours through grafting with HD high quality image-based intellectual image technology of a network camera. To provide efficient security monitoring service in op- eration of 24-hour image security monitoring system, a monitoring robot is designed to perform video-securing work in a gate (at fixed position) during daytime and at night it moves automatically on specified routes (set on a map) to monitor any intruder and actively cope with un- expected situations. <Table 1> shows scenarios by situa- tion for the operation of unmanned security monitoring robot [1, 4]. 3.4. Face Recognition System Process Face Recognition System is a system that extracts face from input images, and recognizes who is whom through similarity assessment process and characteristic data reg- istered by extracting characteristic data for recognition in extracted face. To achieve this, it is composed of face detection module, characteristic extraction module and similarity assessment engine, a recognition module. An assessment module for face similarity is used as a PCA-specific extractor input based on Gabor-kernel for facial range image extracted through Adaboost learning algorithm. A face recognition system calculates an Eucli- dean distance between authorizer and unauthorized r e gis- tered and factors of characteristic data extracted, which maps face in the closest distance. It is a module that cal- culates similarity between registered faces, recognizing whom is out of authorizers through face recognition, and it serves as a function of grouping as unauthorized, oth- erwise[12, 13]. 4. Faces Recognition Process Face Recognition System is a system that extracts face from input images, and recognizes who is whom through similarity assessment process and characteristic data reg- istered by extracting characteristic data for recognition in extracted face. To achieve this, it is composed of face detection module, characteristic extraction module and similarity assessment engine, a recognition module. A process of face recognition system is as follows. Figure 2 shows face image registration process from structured system. After 1 or 2 people registered, and then if the face of CCTV images coming into the camera compare with the images on the server and it matches the data stored in the image a nd displayed the name recogni- tion. Figure 3 shows the register and at the same time, three CCTV images showed on the recognition process. How- ever, when you receive the generic self image is displayed on the tail-light rod, grow up. Depending on the distance of the camera or if the far is recognition, but the feature extraction is unable, just when I came close with a cam- era-aware image possible. Figure 2. Face Image Registration 55  J. HAN ET AL. Copyright © 2013 SciRes. OJAppS (a) 3 faces recognition (b) un-registration search Figure 3. Faces Recognition Simulation 5. Conclusion In conclusion, this paper was conducted for a method to protect personal privacy at maximum at a CCTV environment following the trend of international and domestic standardization, and a framework modeling method that analyzes face detection and recognition system security widely applicable, which finds an implementation method to develop a standard model that can be demonstrated on important service (client ID management, criminal arrest, terror prevention and access management, etc.) based on information protection and biometric reference standard development, and delineates standardized plans for personal information protection on requirements for related bio information and reference management server, mechanism, secured system of database, and management system, image surveillance system and CCTV-based image surveillance system. In this paper, methods are suggested for developing a basic algorithm and framework for 2D-based face recognition where face images for reference DB for face recognition are collected, converted to data as a reference for similarity using an engine for extracting characteristics, with the fabricated face image information mapped with DB as well as a module for image input/output interface, image pre-treatment, normalization and characteristics extraction. With development of a technology to map the fabricated face image information with user DB and measure similarity, a technology that can overcome the limitations in multi processing ability of the existing fingerprint recognition system and save the maintenance cost of RFID card method has been suggested. To achieve this, by manufacturing an unmanned security surveillance robot, images input through HD-level camera are processed real-time to identify author i zed/u na ut ho r i ze d , save a relevant image to transmit to the control server, and keep transmitted recorded images according to a policy, which offers a person in charge to preview them after saved image search through search function. It is a module to upload images real-time to the integrated control system by saving transmitted module and image real-time that enables monitoring at the integrated control system application. The face recognition system is a system that detects face from input images, and recognizes who is whom through similarity assessment process between characteristic data registered by extracting characteristic data to recognize extracted face. 6. Acknowledgements “This work was supported by the Security Engineering Research Center, granted by the Korea Ministry of Knowledge Economy.” REFERENCES [1] Frederic Dufaux, “Scrambling for Privacy Protection in Video Surveillance Systems”, IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECH- NOLOGY, 2008, 18(8). [2] Kenichi YABUTA, “Privacy Protection by Masking Moving Objects for Security Cameras”, IIEICE Trans- actions on Fundamentals of Electronics, Communications and Computer Sciences, Volume E92.A, Issue 3, 2009 : 919-927. [3] Mitsuji Muneyasu, “An Implementation of Privacy Protection for a Surveillance Camera Using ROI Coding of JPEG2000 with Face Detection”, IIEICE Transac- tions on Fundamentals of Electronics, Communications and Computer Sciences, 2009, E92-A(11) : 2858-2861. [4] E. Yu and J. Aggarwal, "Human action recognition with extremities as semantic posture representation," Proc. Int. Conf. Computer Vision, Pattern Recognition, 2009: 1-8. [5] TI, “TMS320C64x+ DSP Image/Video Processing Li- brary Programmer's Guide,” Texas Instruments, Dallas, Texas, May, 2008. [6] TI, “Vision Library Application Programming Interface Reference Guide,” Texas Instruments, Dallas, Texas, Nov., 2009. [7] Chris Stauffer and W.E.L Grimson, “Adaptive Back- ground Mixture Models for Real-time Tracking,” Proc.IEEE Conference on Computer Vision & Pattern Recognition, 1999, 2 : 246- 252. [8] A Al-Habaibeh, F Shi, N Brown, D Kerr, M Jackson and R M Parkin, "A novel approach for quality control system using sensor fusion of infrared and visual image processing for laser sealing of food containers," MEA- SUREMENT SCIENCE AND TECHNOLOGY, 2004 : 1995~2000. [9] Philippe Simard, Norah K. Link, Ronald V. Kruk, "Eval- uation of Algorithms for Fusing Infrared and Synthetic Imagery," Enhanced and synthetic vision 2000. Confe- rence, Orlando FL, 2000, 4023 : 127-138. [10] C. Wren, A. Azerbayejani, T. Darrel, and A. Pentland, “Pfinder: real-time tracking of the human body.” IEEE Trans. Pattern Analysis and Machine Intelligence, 1997, 19(7): 780-785. [11] S. Kang, J. Paik, A. Koschan, B. Abidi, and A. Abidi, “Real-time video tracking using PTZ cameras.” Proc. 56  J. HAN ET AL. Copyright © 2013 SciRes. OJAppS SPIE 6th International Conference on Quality Control by Artificial Vision, 2003, 5132 : 103-111. [12] P. Azzari, L. Stefano, and A. Bevilacqua, “An effective real-time mosaicing algorithm apt to detect motion through background subtraction using a PTZ camera.” IEEE Conf. Advanced Video and Signal-Based Surveil- lance, 2005 : 511-516. [13] G. A. Ramirez and O. Fuentes, “Multi-pose face detec- tion with asymmetric HAAR features.” Applications of Computer Vision, 2008. WACV 2008. IEEE Workshop, 2008 : 1-6. 57 |

