Paper Menu >>
Journal Menu >>
 Journal of Information Security, 2010, 1, 29-40 doi:10.4236/jis.2010.11004 Published Online July 2010 (http://www.SciRP.org/journal/jis) Copyright © 2010 SciRes. JIS Design and Implementation of Multilevel Access Control in Synchronized Audio to Audio Steganography Using Symmetric Polynomial Scheme Jeddy Nafeesa Begum1, Krishnan Kumar1, Vembu Sumathy2 1Department of Computer Science and Engineering, Government College of Engineering, Bargur, India 2Department of Electronics and Communications Engineering, Government College of Technology, Coimbatore, India E-mail: {nafeesa_jeddy, pkk_kumar}@yahoo.com , sumi_gct2001@yahoo.co.in Received March 5, 2010; revised July 15, 2010; accepted July 19, 2010 Abstract Steganography techniques are used in Multimedia data transfer to prevent adversaries from eaves dropping. Synchronized audio to audio steganography deals with recording the secret audio, hiding it in another audio file and subsequently sending to multiple receivers. This paper proposes a Multilevel Access control in Syn- chronized audio steganography, so that Audio files which are meant for the users of low level class can be listened by higher level users, whereas the vice-versa is not allowed. To provide multilevel access control, symmetric polynomial based scheme is used. The steganography scheme makes it possible to hide the audio in different bit locations of host media without inviting suspicion. The Secret file is embedded in a cover media with a key. At the receiving end the key can be derived by all the classes which are higher in the hier- archy using symmetric polynomial and the audio file is played. The system is implemented and found to be secure, fast and scalable. Simulation results show that the system is dynamic in nature and allows any type of hierarchy. The proposed approach is better even during frequent member joins and leaves. The computation cost is reduced as the same algorithm is used for key computation and descendant key derivation. Steg- anography technique used in this paper does not use the conventional LSB’s and uses two bit positions and the hidden data occurs only from a frame which is dictated by the key that is used. Hence the quality of stego data is improved. Keywords: Steganography, Multilevel Access Control, Synchronized Audio, Symmetric Polynomial, Dynamic, Scalable 1. Introduction Transmission of audio files is very important for many applications and it is found that this transmission takes place through an insecure medium. For a live session where on the go audio transmission takes place, efficient techniques should be used. One way of preventing the dissemination of secret audio is through digital audio stenography. This protects valuable information from unauthorized persons. For real time audio transmissions the secret data is recorded and send subsequently to the receivers. For hiding the message there is a need for a secret key that is available with all receivers. This key has to be changed to preserve forward and backward secrecy. There is an additional very important require- ment called the multilevel access control. There are many scenarios in which situation arises, that only some users should be able to hear the data or all higher level users should also be able to hear the message that are relayed to the descendant users. To implement such a multilevel access control in steganography symmetric polynomial approach is used. In most existing schemes, key derivation is different from key computation. Key derivation needs iterative computation of keys for nodes along the path from a node to its descendant, which is inefficient if the path is long. In this scheme, both opera- tions are same by substituting (different) parameters in the same polynomial function assigned to node v. Thus, the key derivation efficiency can be improved. Our scheme also supports full dynamics at both node and user levels and permits any random access hierarchies. More importantly, removing nodes and/or users is an operation  J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 30 as simple as adding nodes and/or users in the hierarchy. A trusted Central Authority (CA) can assign secrets (i.e., polynomials) to corresponding nodes so that nodes can compute their keys. Also, nodes can derive their descen- dants’ keys without involvement of the CA once poly- nomial functions were distributed to them. In addition, the storage requirement and computation complexity at the CA are almost same as that at individual nodes, thus, the CA would not be a performance bottleneck and can deal with dynamic operations efficiently. The rest of the paper is as follows, Section 2 deals with related work Section 3 gives an insight into multi- level access control problem. Section 4 gives the system Overview, Section 5 describes the audio steganography method Section 6 deals about the symmetric polynomial approach Section 7 shows the simulation results and Sec- tion 8 gives the performance analysis and Section 8 con- cludes the paper. 2. Related Work 2.1. Related Work in Steganography Information hiding using steganography [1] relates to protection of text, image, audio and digital content on a cover medium [2-5]. The cover media in many cases has been an image [1]. Aoki presented a method in which information that is useful for widening the base band is hidden into the speech data [6]. Sub band Phase shifting was also proposed for acoustic data hiding [3]. All these schemes focus on data that is stored in a hard disk or any other hardware whereas there are many applications like military warfare where the audio data is to be given in real time as in live broadcast system. Techniques for hiding the audio in real time came into existence [7] and systems for synchronized audio steganography has been developed and evaluated [8]. In our scheme secret speech data is recorded and at the same time it is sent to the re- ceiver and a trusted receiver extracts the speech from the stego data using the key which is shared between the server and the receiver. 2.2. Related Work in Multilevel Access Control The first multi level access solution was proposed by Akl et al. [9,10] in 1983 and followed by many others [11- 21]. These schemes basically rely on a one-way function so that a node v can easily compute v’s descendants’ keys whereas v’s key is computationally difficult to compute by v’s descendant nodes. In this paper, we pro- pose a new scheme based on symmetric polynomials for synchronized audio data. Unlike many existing schemes based on one-way functions, our scheme is based on a secret sharing method which makes the scheme uncondi- tionally secure [21,22]. Also, this multilevel access con- trol requires two types of key operations: (1) key com- putation. A node v computes its own key and (2) key derivation. A node v computes its descendants’ keys. 3. Multi Level Access Control Problem In practice, many group applications contain multiple related data streams and have the members with various access privileges. These applications prevail in various scenarios. 1) Multimedia applications distributing data in multi- layer coding format. For example, in a video broadcast, users with a normal TV receiver can receive the normal format, while others with HDTV receivers can receive both the normal format and the extra information needed to achieve HDTV resolution. 2) Communications in hierarchically managed organi- zations, such as military group communications where participants have different access authorizations. 3) Multilevel access control can be effectively used in Audio library and patient monitoring system. 4) E-newspaper subscription service may have multi- ple data streams. The service provider classifies the users into membership groups and provides data streams ac- cording to the subscription. 5) Video multicasting service in which users can sub- scribe to services with different video quality. Defense messaging systems where the server sends mes- sages and one or more can see the message according to the access rights. In these applications, group members subscribe to dif- ferent data streams, or possibly multiple of them. Thus, it is necessary to develop group access control mechanism that supports the multi-level access privilege, which is referred to as the Multilevel Access Control. 4. System Overview Multilevel Access Control applied to real time audio to audio steganography is useful for organizations which have a hierarchical structure. e.g., in the Indian Military system the following hierarchy exists in “Figure 1”. CHIEF OF ARMY BRIGADIER MAJOR CAPTAIN LIEUTANANT Figure 1. Military hierarchy. 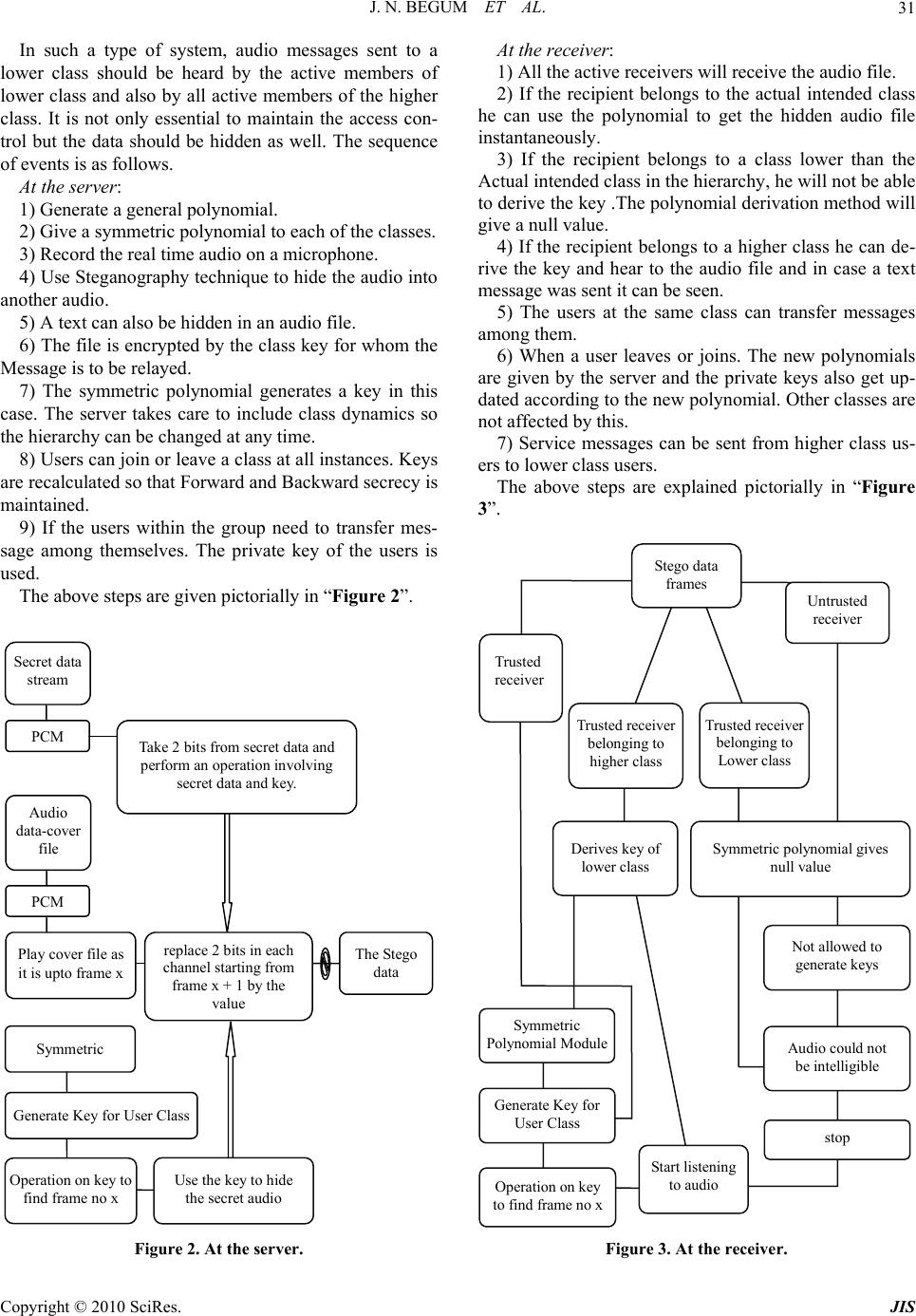 J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 31 In such a type of system, audio messages sent to a lower class should be heard by the active members of lower class and also by all active members of the higher class. It is not only essential to maintain the access con- trol but the data should be hidden as well. The sequence of events is as follows. At the server: 1) Generate a general polynomial. 2) Give a symmetric polynomial to each of the classes. 3) Record the real time audio on a microphone. 4) Use Steganography technique to hide the audio into another audio. 5) A text can also be hidden in an audio file. 6) The file is encrypted by the class key for whom the Message is to be relayed. 7) The symmetric polynomial generates a key in this case. The server takes care to include class dynamics so the hierarchy can be changed at any time. 8) Users can join or leave a class at all instances. Keys are recalculated so that Forward and Backward secrecy is maintained. 9) If the users within the group need to transfer mes- sage among themselves. The private key of the users is used. The above steps are given pictorially in “Figure 2”. Secret data stream PCM Audio data-cover file PCM Symmetric Play cover file as it is upto frame x The Stego data Take 2 bits from secret data and perform an operation involving secret data and key. replace 2 bits in each channel starting from frame x + 1 by the value Generate Key for User Class Operation on key to find frame no x Use the key to hide the secret audio Figure 2. At the server. At the receiver: 1) All the active receivers will receive the audio file. 2) If the recipient belongs to the actual intended class he can use the polynomial to get the hidden audio file instantaneously. 3) If the recipient belongs to a class lower than the Actual intended class in the hierarchy, he will not be able to derive the key .The polynomial derivation method will give a null value. 4) If the recipient belongs to a higher class he can de- rive the key and hear to the audio file and in case a text message was sent it can be seen. 5) The users at the same class can transfer messages among them. 6) When a user leaves or joins. The new polynomials are given by the server and the private keys also get up- dated according to the new polynomial. Other classes are not affected by this. 7) Service messages can be sent from higher class us- ers to lower class users. The above steps are explained pictorially in “Figure 3”. Stego data frames Trusted receiver Trusted receiver belonging to higher class Derives key of lower class Trusted receiver belonging to Lower class Symmetric polynomial gives null value Not allowed to generate keys Audio could not be intelligible stop Start listening to audio Symmetric Polynomial Module Generate Key for User Class Operation on key to find frame no x Untrusted receiver Figure 3. At the receiver.  J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 32 4.1. Features of our Model Solutions of a synchronized steganography have been given in past [8]. In this once the stego data reaches the destination the audio can be listened by the trusted re- ceiver. Our contributions are 1) The key is used during the embedding process also. 2) The key is not a simple key it identifies a class of users. 3) If the key used belongs to a low level group in the hierarchy, the higher level class of user can derive the key using the symmetric polynomial approach and listen to it. 4) There can be normal message transfer among the Group elements and also service messages from higher classes. 5) Forward and backward secrecy is maintained. 6) It is a dynamic one where new hierarchies can be introduced, User level and class level dynamics are taken care. 5. Synchronized Audio to Audio Steganography The data to be sent is not available. It is recorded in real time before starting the steganography scheme. When the covering media is being played at the same time the au- dio file is recorded and put into the cover file. The stego bit stream is then transmitted to the receivers. Multilevel Access control using symmetric polynomial is used at this stage to generate the key to make secure transmis- sion of the audio file. According to the hierarchy the trusted users are able to retrieve the hidden audio file.In this system, both of cover data and secret data are di- vided into fix-sized frames according to pulse code modulation setting. To cover low size and high phonetic quality the sampling rate of the hidden audio is set to 8 kHz. Three main processes are involved in the synchro- nized audio to audio steganography. 1) Using data sampling, acoustic signals are embedded into another audio. 2) Bit Embedding: The key used helps in hiding the audio file in bit positions and once the bit positions are found data is hidden after performing an operation on secret data and the key. 3) Synchronized Process: Malicious and intentional attacks can be avoided as the secret data is real time. 5.1. Algorithm Step 1: Record the Secret Speech Data: The audio files are divided into fix-sized frames and set to be specific PCM format. PCM quantification is decided by sampling rate, sampling size, and sampling channel. The PCM property of cover audio wav is set to be 32kHz-16bit-2ch, while the secret wav data is 16kHz-8bit-1ch. Formula used for steganography: Steganography process: cover_medium + hidden_data + stego_key = stego_medium Part of The Wave File Format opened using Notepad: 52 49 46 46 24 40 01 00 57 41 56 45 66 6D 74 RIFF $ @. Wave Fmt10 00 00 00 01 00 02 00 11 2B 00 00 44 AC 00 00 ……. + …D…04 00 10 00 64 61 74 61 00 40 01 00 00 00 00 00 …. data. @.......... Wave_Format_PCM: 01 11 channel count: 02 00 Samples: 11 2B 00 00 bytes: 44 AC 00 00 Block align: 04 00 bits per sample: 10 00 Step 2: Use Symmetric Polynomial to calculate key of the class Step 3: Perform calculation and decide the frame from which the data is to be embedded. Step 4: Decide two bit locations in each frame and clear the bit in the locations. cmask1 = (2loc1−1) xor (keybit) cmask2 = (2loc2−1) xor (Keybit) cmask = cmask1 cmask2 hide the secret data bits into these bit locations by again performing an operation on the secret data along with the key. The cover media has two channels so data is written on both the channels. Other bits are not changed. Step 5: The next set of data will go to the next frame. Step 6: Do the repetitive process till the recoding is over. Step 8: Transmit using sockets. Step 9: At the receiving end, use the key and play the audio. Step 10: If the receiving user belongs to higher class, he can derive the key and listen to the audio. 6. Symmetric Polynomial Approach 6.1. Symmetric Polynomial A CA selects a large positive integer P as the system modulus, p need not be a prime and a threshold number t so that less than t + 1 users cannot collaborate together to disclose their ancestors’ keys. Then, the CA can ran- domly generate a symmetric polynomial in m variables with co-efficient from Zp in which the degree of any variables is at most t as: 12 12 12 12,,, 12 00 0 ,,, mod m m m tt ti ii miiim ii i Px xxaxxxP where 12 ,,, m ii i a are randomly generated coefficients by the CA. The polynomial function 12 ,,, m Pxx x is kept as a secret to the CA. Every class in the hierarchy 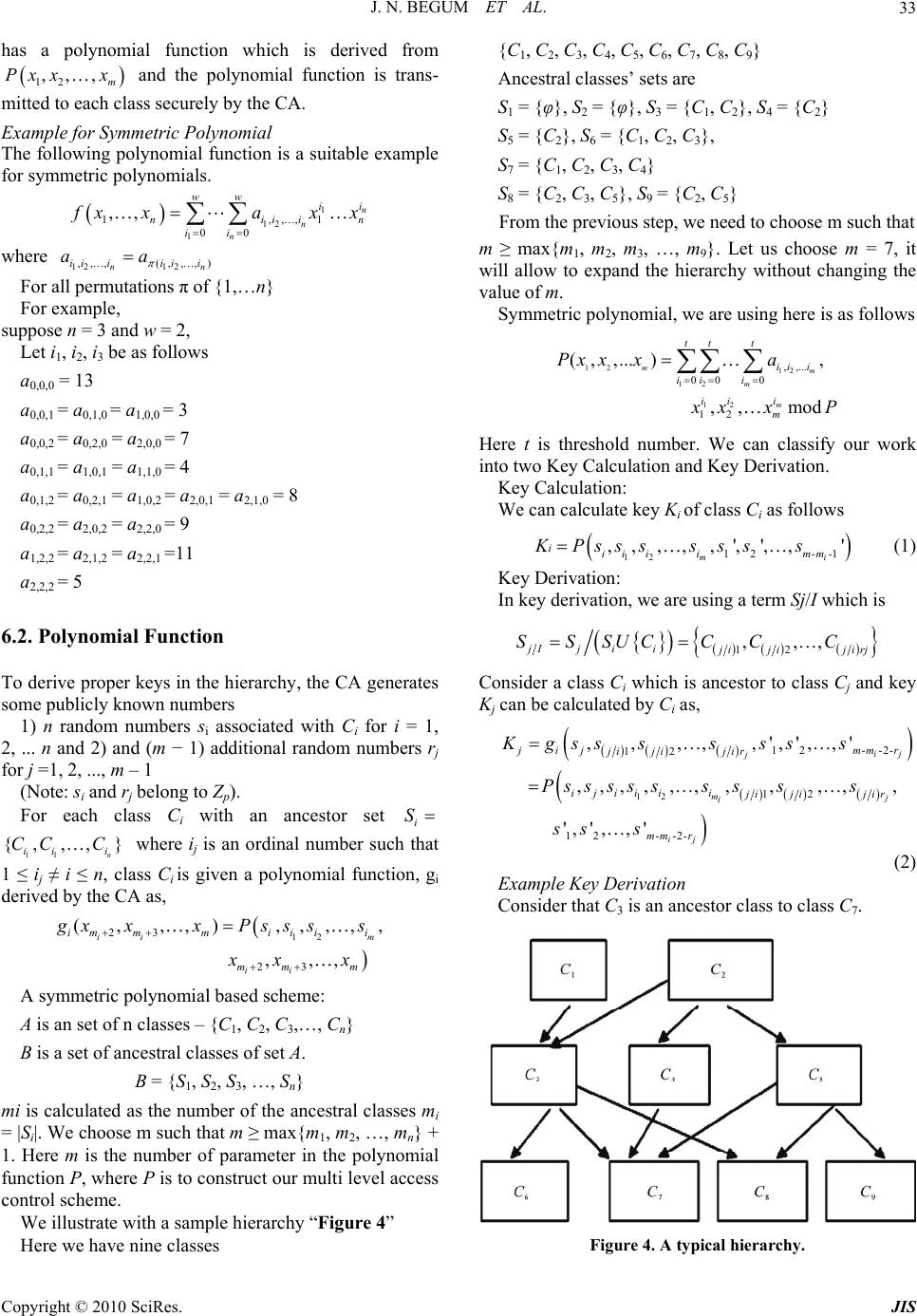 J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 33 has a polynomial function which is derived from 12 ,,, m Pxx x and the polynomial function is trans- mitted to each class securely by the CA. Example for Symmetric Polynomial The following polynomial function is a suitable example for symmetric polynomials. 1 12 1 1,,,1 00 ,, n n n ww i i niiin ii f xxa xx where 12 12 ,,, (,,,) nn ii iii i aa For all permutations π of {1,…n} For example, suppose n = 3 and w = 2, Let i1, i2, i3 be as follows a0,0,0 = 13 a0,0,1 = a0,1,0 = a1,0,0 = 3 a0,0,2 = a0,2,0 = a2,0,0 = 7 a0,1,1 = a1,0,1 = a1,1,0 = 4 a0,1,2 = a0,2,1 = a1,0,2 = a2,0,1 = a2,1,0 = 8 a0,2,2 = a2,0,2 = a2,2,0 = 9 a1,2,2 = a2,1,2 = a2,2,1 =11 a2,2,2 = 5 6.2. Polynomial Function To derive proper keys in the hierarchy, the CA generates some publicly known numbers 1) n random numbers si associated with Ci for i = 1, 2, ... n and 2) and (m − 1) additional random numbers rj for j =1, 2, ..., m – 1 (Note: si and rj belong to Zp). For each class Ci with an ancestor set i S 11 {, ,, } n ii i CC C where ij is an ordinal number such that 1 ≤ ij ≠ i ≤ n, class Ci is given a polynomial function, gi derived by the CA as, 12 23 23 (,,,) ,,,,, ,,, ii m ii immmii ii mm m g xxx Pssss xx x A symmetric polynomial based scheme: A is an set of n classes – {C1, C2, C3,…, Cn} B is a set of ancestral classes of set A. B = {S1, S2, S3, …, Sn} mi is calculated as the number of the ancestral classes mi = |Si|. We choose m such that m ≥ max{m1, m2, …, mn} + 1. Here m is the number of parameter in the polynomial function P, where P is to construct our multi level access control scheme. We illustrate with a sample hierarchy “Figure 4” Here we have nine classes {C1, C2, C3, C4, C5, C6, C7, C8, C9} Ancestral classes’ sets are S1 = {φ}, S2 = {φ}, S3 = {C1, C2}, S4 = {C2} S5 = {C2}, S6 = {C1, C2, C3}, S7 = {C1, C2, C3, C4} S8 = {C2, C3, C5}, S9 = {C2, C5} From the previous step, we need to choose m such that m ≥ max{m1, m2, m3, …, m9}. Let us choose m = 7, it will allow to expand the hierarchy without changing the value of m. Symmetric polynomial, we are using here is as follows 12 12 12 12 , ,... 00 0 12 (,,...), ,, mod mm m m tt t ii i ii i i ii m Px xxa x xx P Here t is threshold number. We can classify our work into two Key Calculation and Key Derivation. Key Calculation: We can calculate key Ki of class Ci as follows 12 12 --1 ,,,, ,',',,' mi iii iimm KPsss ssss (1) Key Derivation: In key derivation, we are using a term Sj/I which is 12 ,,, jIj ii j i jijirj SSSUC CCC Consider a class Ci which is ancestor to class Cj and key Kj can be calculated by Ci as, 12 12 --2- 12 12 12 --2- ,,, ,,',', ,' ,,,,,, ,,,,, ', ',, ' ij j mj i ij j ij mmr ji jijir ijiiii ji jijir mm r Kgsssssss Ps ssssssss ss s (2) Example Key Derivation Consider that C3 is an ancestor class to class C7. Figure 4. A typical hierarchy. 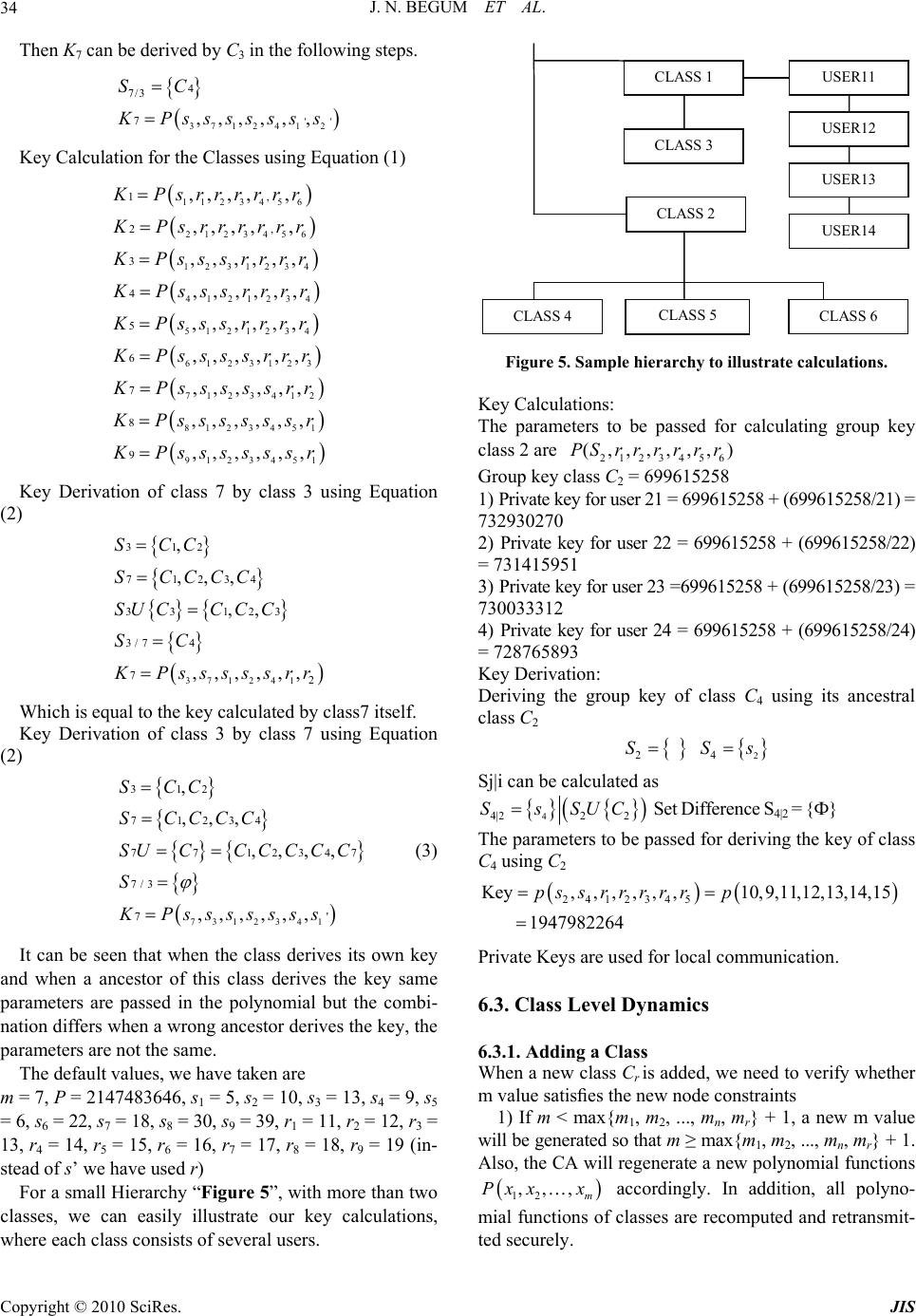 J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 34 Then K7 can be derived by C3 in the following steps. '' 371241 2 4 7/3 7,,,,,, SC K Psssssss Key Calculation for the Classes using Equation (1) 1123456 2123456 1 2 31234 4121234 5 1 21234 6123123 7123412 8123 451 9 1, 2, 3 4 5 6 7 8 9 ,,,,, ,,,,, ,,,,,, ,,,,,, ,,,,,, ,,,,,, ,,,,,, ,,,,,, , K Psrrrrrr K Ps rrrrrr K Psss rrrr K Psssrrrr K Ps ss rrrr K Pssss rrr K Ps ss s s rr K Ps ss s s s r KPss 123451 ,,,,, s sssr Key Derivation of class 7 by class 3 using Equation (2) 371241 312 71234 33 123 3/7 4 72 , ,,, ,, ,,,,,, SCC SCCCC SU CC CC SC K Psssssrr Which is equal to the key calculated by class7 itself. Key Derivation of class 3 by class 7 using Equation (2) 7312341 312 7 1234 7712347 7/3 7' , ,,, ,,,, ,,,,,, SCC SCCCC SUCC CCCC S KPsssssss (3) It can be seen that when the class derives its own key and when a ancestor of this class derives the key same parameters are passed in the polynomial but the combi- nation differs when a wrong ancestor derives the key, the parameters are not the same. The default values, we have taken are m = 7, P = 2147483646, s1 = 5, s2 = 10, s3 = 13, s4 = 9, s5 = 6, s6 = 22, s7 = 18, s8 = 30, s9 = 39, r1 = 11, r2 = 12, r3 = 13, r4 = 14, r5 = 15, r6 = 16, r7 = 17, r8 = 18, r9 = 19 (in- stead of s’ we have used r) For a small Hierarchy “Figure 5”, with more than two classes, we can easily illustrate our key calculations, where each class consists of several users. CLASS 3 CLASS 4 CLASS 6 CLASS 5 CLASS 2 USER11 USER12 USER13 USER14 CLASS 1 Figure 5. Sample hierarchy to illustrate calculations. Key Calculations: The parameters to be passed for calculating group key class 2 are 2123456 ( ,,,,,,)PSr rrrrr Group key class C2 = 699615258 1) Private key for user 21 = 699615258 + (699615258/21) = 732930270 2) Private key for user 22 = 699615258 + (699615258/22) = 731415951 3) Private key for user 23 =699615258 + (699615258/23) = 730033312 4) Private key for user 24 = 699615258 + (699615258/24) = 728765893 Key Derivation: Deriving the group key of class C4 using its ancestral class C2 2 24 SSs Sj|i can be calculated as 4 4|22 2 SsSUC Set Difference S4|2 = {Ф} The parameters to be passed for deriving the key of class C4 using C2 2412345 Key,,, ,, ,10,9,11,12,13,14,15 1947982264 pssrr rr rp Private Keys are used for local communication. 6.3. Class Level Dynamics 6.3.1. Adding a Class When a new class Cr is added, we need to verify whether m value satisfies the new node constraints 1) If m < max{m1, m2, ..., mn, mr} + 1, a new m value will be generated so that m ≥ max{m1, m2, ..., mn, mr} + 1. Also, the CA will regenerate a new polynomial functions 12 ,,, m Pxx x accordingly. In addition, all polyno- mial functions of classes are recomputed and retransmit- ted securely.  J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 35 2) If m ≥ max{m1, m2, ..., mn, mr} + 1, the CA selects a random number sr for the new class Cr so that a new polynomial function gr can be computed and transmitted to class Cr securely. However, if class Cr is added as a parent class of any existing classes, we need to modify keys of Cr’s descendant classes to prevent class Cr from obtaining old keys of its descendant. 6.3.2. Deleting a Class When a class Cr is removed from the hierarchy, we need to determine whether the class Cr is a leaf node or a par- ent node. Here, a leaf node is defined as a node without any descendant: 1) class Cr is a leaf node: The CA can simply discard the public parameter sr without changing any other keys. 2) class Cr is a parent node: Once class Cr is deleted from the hierarchy, we cannot allow it to compute keys of Cr’s descendant classes using polynomial function gr. We need to prevent class Cr from accessing its descen- dants’ resources. 6.3.3. Moving a Class A class Cr can be moved from one node to another node in the hierarchy. There are four cases: 1) leaf node to another leaf node: the CA simply re- computes new polynomial function gr according the new hierarchy and securely transmits gr to Cr. 2) leaf node to parent node: the CA recomputes poly- nomial functions of class Cr and Cr’s new descendant classes according to the new hierarchy. The CA securely transmits polynomial functions to the affected classes; 3) parent node to leaf node: the CA recomputes poly- nomial functions of previous descendant classes of Cr and class Cr according to the new hierarchy and then, securely transmits these polynomial functions to the af- fected classes 4) parent node to parent node: the CA recomputes polynomial functions of previous and present descendant classes of Cr and class Cr according to the new hierarchy and then, securely transmits these polynomial functions to the affected classes. 6.3.4. Merging a Class Two or more classes can merge together and become one class Cr. Similarly, the CA needs to find previous and present descendant classes of the merging classes. The CA randomly chooses a new number sr and then, gener- ates polynomial functions for all corresponding classes. 6.3.5. Splitting a Class A class Cr splits into two classes Cr1 and Cr2. Depending on whether Cr is a parent node or leaf node, the CA has to determine what previous and present descendant cla- sses are associated with these classes (Cr, Cr1 and Cr2). The CA then selects two new numbers sj1 and sj2 and generates polynomial functions for these affected classes. 6.3.6. Adding a Link If two classes Cr and Ck are linked together, we establish a new direct parent-child relationship between two classes, say class Cr is the parent of class Ck. There are two different cases: 1) class Cr was an ancestor of class Ck through other classes. The CA does not need to per- form anything; and 2) class Cr is the only parent for class Ck in the new hierarchy. The CA selects a new number Sk, and generates new polynomial functions for class Ck and its descendants classes. The CA securely transmits new polynomial functions to these affected classes. 6.3.7. Deleting a Link If two linked classes Cr and Ck are disconnected, we de- stroy a direct parent-child relationship between two classes, say class Cr will not be the parent of class Ck in the new hierarchy. Again, there are two different cases: 1) class Cr is still an ancestor of class Ck through other classes in the new hierarchy. The CA does not need to perform anything; and 2) class Cr is not an ancestor for class Ck in the new hierarchy. The CA selects a new number Sk, and generates new polynomial functions for class Ck and its descendants classes. The CA securely transmits new polynomial functions to these affected classes. 6.4. User Level Dynamics In this scheme, every class represents certain access privileges. Also, a group of users in a class can share a key if they belong to the same class. For example, all users in class Cj can compute the keys of class Cj and its descendant classes. Dynamic user operations deal with how a user can join in a class or leave from a class, and possible displacement from one class to a different class. They all require the class key to be changed after any user operation is completed so that the issue of backward secrecy and forward secrecy can be addressed. Specifi- cally, our scheme can revoke a user from a class Cj. It is as quick and efficient as to join a user in the class Cj. Both operations require that the CA randomly select a new public parameter sj for Cj and recompute a new polynomial function gj by using the new sj. Since the polynomial function gj is newly produced, other polyno- mial functions and keys are also recomputed for the de- scendant classes of Cj. This will guarantee both back- ward secrecy and forward secrecy. The efficiency can be improved if backward secrecy or forward secrecy is not required. Another common user operation is to allow a  J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 36 user to move from one class Cj to another class Ck. Here, the CA will randomly choose two new public parameters sj and sk for Cj and Ck so that new polynomial functions and keys are recomputed and transmitted to Cj, Ck and their descendants respectively. Thus, both backward se- crecy and forward secrecy are guaranteed. 6.4.1. User Join Every time if a single user wants to join a group the CA just allows the user to be added to the hierarchy and gen- erates a private for that user by providing the corre- sponding group key. When a new user joins the hierar- chy, it should be provided with a group key and there are no changes to be made on the user’s key. 6.4.2. User Leave When a user wants to leave from the hierarchy the CA change the group key by making changes on anyone of the following changing the polynomial or changing the value factor P. 7. Simulation Results The system is developed using .NET and found to be secure and fast. The system takes care of USER level and class level dynamics. The large number of numbers pre- vents a possible guessing. e.g., for a eight parameter polynomial, 16 (i.e., 10922789888000) combinations possible. Bursty leave and join operations also are possi- ble and the system can be used for any hierarchy. The outputs are shown in Figures 6-10. 8. Performance Analysis Performance and security: Each user ui will receive 2 2 2 2 22 ,... 2 00 , ,...,... ,,... n n n n ii nn iw iw i i ii n ii g fsxxgx x axx The time complexity for computing the group key is O (w2n). An important measure for a secure group com mu- nication scheme is the number of rekeying messages. Suppose that t users will be joining the group. The TA will send k and gi to each of them respectively (2t mes- sages) and broadcast one message to tell which users are joining. The total number of rekeying messages is O (2t). Suppose that t users are leaving the group. The TA only broadcasts one message to tell which users are leaving, thus the number of rekeying messages is O (1). Suppose that t users are joining and another v users are leaving the group, the total number of rekeying messages is still O (2t). As for the security of the scheme, if w + 1 class col- lude, then they can Figure out the function f entirely. Therefore, the scheme is w-resilient. Moreover, if less than w + 1 classes collude, they cannot get any informa- tion about the key, i.e., any value in the key space looks like a valid and equiprobable key to these colluding users. It follows that the scheme is unconditionally secure. 8.1. Memory Each user will be able to calculate the key based on the Figure 6. Users and classes.  J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 37 Figure 7. Key calculation for all classes. Figure 8. Communication among same class. polynomial and hence very less memory is used. All pa- rameters are publicly available and using the same method keys of lower hierarchy can be derived by sub- stituting the corresponding parameters as given by the derivation module. The steganography module does not involve any storage for storing the already recorded data as always data is recorded and subsequently sent to the receivers. The size of the cover medium does not in- crease because only two bits are used in each channel. 8.2. Computation Cost When the user joins there is no need for recalculation because the recorded message has already been played. When a user leaves a group key is recalculated and given to the class. Private keys are generated from this. The  J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 38 Figure 9. Hiding the message. Figure 10. Recording the message. value of the new key involves not a change of parameters but a change of mod P value. Hence each class will be able to get a new polynomial value by passing the same parameters. Any left user will not be able to get the key. Only one key is used during creation of stego data. The higher class users need not remember the keys of all their descendant classes but rather using a simple scheme de- rive the exact parameters to generate the key. Hence the computation cost is reduced. 8.3. Communication Cost The P value is changed by the Trusted Authority and when the users try to calculate the key the new key will be generated. The computation cost is reduced because, the class users are not bothered about the key transmis-  J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 39 sion. Once the polynomial is given the users can calcu- late their own key. 8.4. Dynamics Class joining, Class leaving, Dynamic Hierarchy and New user joining a class are all done by the trusted authority in a phased manner thereby allowing the scheme to scale to greater hierarchy. Additionally local messaging and service messages are taken care in this system. 8.5. No of Rekeys To calculate the no of changes might be made on the user’s key based on user join/leave. Key must be chang- ed when a new user is being joined/left from the hierar- chy In the Hierarchy “Figure 11” for analyzing the no. of rekeys there are 50 classes and Let every classes con- sists of four users each, then we can calculate an unique key for every class based on this group key, we can gen- erate a private key for every single user. Classes: Totally fifty classes of eight levels Figure 11. Hierarchy analyzed for calculating the no. of rekeys. Users: Every class is consists of 4 users User joins: Every time if a single user wants to join a group the CA just allows the user to be added to the hierarchy and generates a private for that user by providing the corresponding group key. The secrecy is maintained as the audio is real time. User leave: When a user wants to leave from the hierarchy the CA change the group key by making changes on anyone of the following Changing the polynomial, or by Chang- ing the value factor P. The total no of key changes to be made = No. of Ancestor classes + 1 as shown in Table 1. 9. Conclusions and Future Work 9.1. Conclusions Thus in this Paper, Design And Implementation Of Mul- tilevel Access Control In Synchronized Audio To Audio Steganography Using Symmetric Polynomial Scheme is implemented successfully .The implementation results show that any type of hierarchy can be introduced and all dynamics can be done. For a 8 parameter polynomial that can have use 8 among the 16 values there are 16 com- binations. Also, nodes can derive their descendants’ keys without involvement of the CA once polynomial func- tions were distributed to them. In addition, the storage requirement and computation complexity at the CA are almost same as that at individual nodes, thus, the CA would not be a performance bottleneck and can deal with dynamic operations efficiently. Table 1. No of rekeys for user leaving from a corresponding class. Class 1: 1Class 11:4Class 21:5 Class 31:7 Class 41:8 Class 2:2Class 12:4Class 22:6 Class 32:7 Class 42:9 Class 3:2Class 13:4Class 23:6 Class 33:7 Class 43:9 Class 4:2Class 14:4Class 24:6 Class 34:7 Class 44:9 Class 5:3Class 15:4Class 25:6 Class 35:8 Class 45:9 Class 6:3Class 16:5Class 26:6 Class 36:8 Class 46:9 Class 7:3Class 17:5Class 27:6 Class 37:8 Class 47:9 Class 8:3Class 18:5Class 28:6 Class 38:8 Class 48:9 Class 9:3Class 19:5Class 29:7 Class 39:8 Class 49:9 Class 10:4Class 20:5Class 30:7 Class 40:8 Class 50:9  J. N. BEGUM ET AL. Copyright © 2010 SciRes. JIS 40 9.2. Future Work 1) The Trusted authority can still made secure by chang- ing the value of the parameters. 2) A symmetric polynomial can be changed by the trusted authority. 3) Bit selection for steganography can be made by us- ing some pseudo random generator. 10. References [1] W. Stallings, Ed., “Network and Internetworking Secu- rity,” Pearson Education Asia, Singapore, 2001. [2] N. F. Johnson, Z. Duric and S. Jajodia, “Information Hiding Steganography and Watermarking-Attacks and Countermeasures,” Kluwer Academic Publishers, Boston, 2001. [3] F. A. P. Petitcolas, R. J. Anderson and M. G. Kuhn, “In- formation Hiding - A Survey,” Proceedings of IEEE, Vol. 87, No. 7, 1999, pp. 1062-1078. [4] M. Hosei, “Acoustic Data Hiding Method Using Sub- Band Phase Shifting,” Technical Report of IEICE, EA, Vol. 106, No. 205, 2006, pp. 7-11. [5] M. Wu and B. D. Liu, “Multimedia Data Hiding,” Springer-Verlag, New York, 2003. [6] T. Aoki and N. Homma, “A Band Widening Technique for VoIP Speech Using Steganography Technology,” Report of IEICE, SP, Vol. 106, No. 333, 2006, pp. 31-36. [7] X. P. Huang, R. Kawashima, N. Segawa and Y. Abe, “The Real-Time Steganography Based on Audio-to-Au- dio Data Bit Stream,” Technical Report of IEICE, ISEC, Vol. 106, No. 235, September 2006, pp. 15-22. [8] X. P. Huang, R. Kawashima, N. Segawa and Y. Abe, “Design and Implementation of Synchronized Audio-to- Audio Steganography Scheme,” IEEE Explore, 2008, pp. 331-334. [9] S. G. Akl and P. D. Taylor, “Cryptographic Solution to a Problem of Access Control in a Hierarchy,” ACM Trans- actions on Computer Systems, Vol. 1, No. 3, March 1983, pp. 239-247. [10] S. J. MacKinnon, P. D. Taylor, H. Meijer and S. G. Akl, “An Optimal Algorithm for Assigning Cryptographic Keys to Control Access in a Hierarchy,” IEEE Transac- tions on Computers, Vol. 34, No. 9, September 1985, pp. 797-802. [11] S. Chen, Y.-F. Chung and C.-S. Tian, “A Novel Key Management Scheme for Dynamic Access Control in a User Hierarchy,” COMPSAC, September 2004, pp. 396-397. [12] I. Ray, I. Ray and N. Narasimhamurthi, “A Cryptographic Solution to Implement Access Control in a Hierarchy and More,” SACMAT’02: Proceedings of the 7th ACM Sym- posium on Access Control Models and Technologies, ACM Press, New York, 2002, pp. 65-73. [13] R. S. Sandhu, “Cryptographic Implementation of a Tree Hierarchy for Access Control,” Information Processing Letter, Vol. 27, Vol. 2, February 1988, pp. 95-98. [14] G. C. Chick and S. E. Tavares, “Flexible Access Control with Master Keys,” Proceedings on Advances in Cryp- tology: CRYPTO’89, LNCS, Vol. 435, 1989, pp. 316-322. [15] M. L. Das, A. Saxena, V. P. Gulati and D. B. Phatak, “Hierarchical Key Management Scheme Using Polyno- mial Interpolation,” SIGOPS Operating Systems Review, Vol. 39, No. 1, January 2005, pp. 40-47. [16] L. Harn and H. Y. Lin, “A Cryptographic Key Generation Scheme for Multilevel Data Security,” Computers and Security, Vol. 9, No. 6, October 1990, pp. 539-546. [17] V. R. L. Shen and T.-S. Chen, “A Novel Key Manage- ment Scheme Based on Discrete Logarithms and Poly- nomial Interpolations,” Computers and Security, Vol. 21, No. 2, March 2002, pp. 164-171. [18] M.-S. Hwang, C.-H. Liu and J.-W. Lo, “An Efficient Key Assignment for Access Control in Large Partially Or- dered Hierarchy,” Journal of Systems and Software, Feb- ruary 2004. [19] C. H. Lin, “Dynamic Key Management Scheme for Ac- cess Control in a Hierarchy,” Computer Communications, Vol. 20, No. 15, December 1997, pp. 1381-1385. [20] S. Zhong, “A Practical Key Management Scheme for Access Control in a User Hierarchy,” Computers and Se- curity, Vol. 21, No. 8, November 2002, pp. 750-759. [21] X. Zou, B. Ramamurthy and S. Magliveras, “Chinese Remainder Theorem Based Hierarchical Access Control for Secure Group Communications,” Lecture Notes in Computer Science (LNCS), Vol. 2229, November 2001, pp. 381-385. [22] X. Zou, B. Ramamurthy and S. S. Magliveras, Eds., “Se- cure Group Communications over Data Networks,” Springer, New York, October 2004. |

