Paper Menu >>
Journal Menu >>
 J. Service Science & Management, 2010, 3, 181-185 doi:10.4236/jssm.2010.32022 Published Online June 2010 (http://www.SciRP.org/journal/jssm) Copyright © 2010 SciRes. JSSM 181 The Research of Risk Management in Two Non-Independent IT System Zhe Yin1,2, Yunfei Guo2, Maosheng Lai1* 1Department of Information Management, Peking University, Beijing, China; 2Mathematics Department, Yanbian University, Yanbian, China. Email: yinzhe@ybu.edu.cn Received March 30th, 2010; revised April 30th, 2010; accepted May 31st, 2010. ABSTRACT Enterprises use IT system in business sector/information management sector and production management sector on purpose of the operation, which, of course, is inseparable from risk management. Two non-independent risk estimates functions are hence founded in order to receive the information of risk easily, that is, the cash flow-based evaluation functions. Applying the logarithmic probability-distribution function in the estimates function as well as giving an ex- ample by simulating, this essay has explained the affection of the uncertain factors to the enterprise management such as the business treatment and so on. At last, it has commented the application of the estimates function in the risk man- agement. Keywords: IT System, Non-Independent, Risk Management, Logarithmic Probability-Distribution Function 1. Introduction The role of IT in business activities has been more and more important; besides, the amount of its investment is also increasing. The key of operating businesses more effectively is to base on the operating principles and to play the role of IT systems. The application of IT sys- tems can not only apply to business operations and main- tenance, but also to social services and business competi- tion [1]. Japanese companies consulting firms Shigeru Inoue [2] 2000, proposed that the key of risk management is enter- prise risk quantification, so the introduction of IT syst- ems need to use the reorganization of business structu- res [3], and through the systematic of business processes to achieve business strategy and IT systems integration and quantification of organic. UNISYS Corporation To- shiaki Otsuka [4] also proposed risk management should go through the entire IT system development, testing and operation cycle. When meeting a bad objective environ- ment, not only should we reconstruct the system, but also give the risk management throughout the system life cycle. In order to carry out the risk management of the chan- ges in the external environment [5], this article deals only with a risk quantification, to determine the percentage of operating losses, and to reduce risk through information sharing. First, the cash flow-based evaluation function which can reflect the values of IT systems is embodied; and considered the effects of IT investments and risk prediction of two non-independent IT systems such as knowledge management systems and intelligence proc- essing systems. Knowledge management systems are the IT systems of the operational management levels, while intelligent processing systems for of IT systems which are for the purpose of knowledge discovery, personaliza- tion-depth study of levels. This article gives the logarithmic probability distribu- tion function and proposes specific statistical methods of quantifying the risk. Ultimately, in order to adapt to so- cial changes in the external environment, the application of the evaluation function in the risk management is also discussed. 2. The Role of Information Sharing As a manager of IT systems, there is need to analyze business strategy and decision-making, and to determine the system operators who will invest in IT systems and operators who can increase efficiency of the systems through the application of IT systems. The system re- sponsible for CIO and the CEO positions of different operators are unlikely to adopt the same evaluation sys- tems. In order to fully share information, using the same assessment system and the introduction of discounted cash flow method [6] are the preferred methods of eva- luation function. As the evaluation function, not only can  The Research of Risk Management in Two Non-Independent IT System 182 it reflect their own business performance, but also accu- rately can it reflect the risks to the business environment. Therefore, in order to be prepared to risk, it is also nec- essary to venture into visual (through statistical tables and charts) besides quantifying, which can achieve a more intuitive result. 3. The Cash-Flow Considered Evaluation Function In order to show the effect of IT systems, we introduce the evaluation function (the cumulative efficiency), wh- ich is composed of the IT investment costs, income and value-added. 1 {()() ()}(,) T t FI CopetCRt CG tfr tOpbOpi (1) where I: construction costs of IT systems; Cope(t): maintenance costs of IT systems; CR(t): reduced costs within the enterprise; CG(t): increased turnovers according to IT systems con- struction; T: lifetime of IT system; Opb: added value of improving the business environ- ment; Opi: reduction effect of business management risk; (,) f rt : function of the current conversion efficiency (r = risk rate, t = time); The main idea of constructing evaluation function F is that the profit is equal to the difference between input and income. Besides, the risk rate will change with the change of the time .So F is a dynamic function. and 1 (,) (1 )t frt r (2) When the purpose of IT investments in the market is to improve the enterprise’s competitive edge, the system values is mainly in terms of increasing the value of the amount of CG(t) and its business environment the added value of Opb. And when for the management purposes, the system performance in terms of cost reduction is in the amount of the value of CR(t). When in order to im- prove the business environment or to lay a good founda- tion for business environment, importing IT systems to reduce costs or improve enterprise efficiency does not work at all. The role of IT systems can be changed as the business environment to reduce Opi (risk reduction) as its neces- sity. The value of Opb, Opi and t can be used as the ref- erence variable of the business environment, which can be quantified by using options and other methods. 4. An Empirical Analysis of Aisk Quantitative 4.1 Examples and Statistical Methods to Quantify the Risk Take medium-scale IT systems as an example, cost of the project A has been shown in Table 1. Initial develop- ment costs are 1 million yuan, annual maintenance costs are 150,000 yuan, the annual loss of initial cost is 30%, an annual increase of turnover is 20%, and value-added based on customer satisfaction is 100,000 yuan. Assum- ing that IT system life are 7 years, the investment benefit evaluation function (expression (1)) = 1.1253 million yuan. Cost of the project B is shown in Table 2. There is no problem from quantity to consider, then how much will the risks be? The risk of cumulative incremental value of operating benefits (expression (1)) can be expressed through the probability distribution function, according to Pareto dis- tribution theory, cumulative incremental value of operat- ing benefits meets the log-normal distribution. Suppose the best reduced cost per year of project A is 300,000 yuan, the minimum is 50,000 yuan, the maximum is 320,000 yuan, operational efficiency expectations is 200,000 yuan, the standard deviation is 50,000 yuan; he best reduced cost per year of project B is 200,000 yuan, the minimum is 65,000 yuan, the maximum is 250,000 yuan, operational efficiency expectations is 150,000 yuan, the standard deviation is 30,000 yuan, and the correlation coefficient of the two projects r = −0.2, the cumulative incremental value of operating benefits meets the log- normal distribution . Table 1. Costing table of project A Initial investment I 1 million yuan maintenance costs s /year Cope 150,000 yuan reduced costs within the enterprise /year CR 300,000 yuan increased turnovers according to IT systems construction /year CG 200,000 yuan risk rate r (%) 5% added value of improving the business environment Opb 100,000 yuan Table 2. Costing table of project B Initial investment Ⅱ 600,000 yuan maintenance costs s /year Cope 100,000 yuan reduced costs within the enterprise /year CR 200,000 yuan increased turnovers according to IT systems construction /year CG 150,000 yuan risk rate r (%) 4% added value of improving the business environment Opb 60,000 yuan Copyright © 2010 SciRes. JSSM 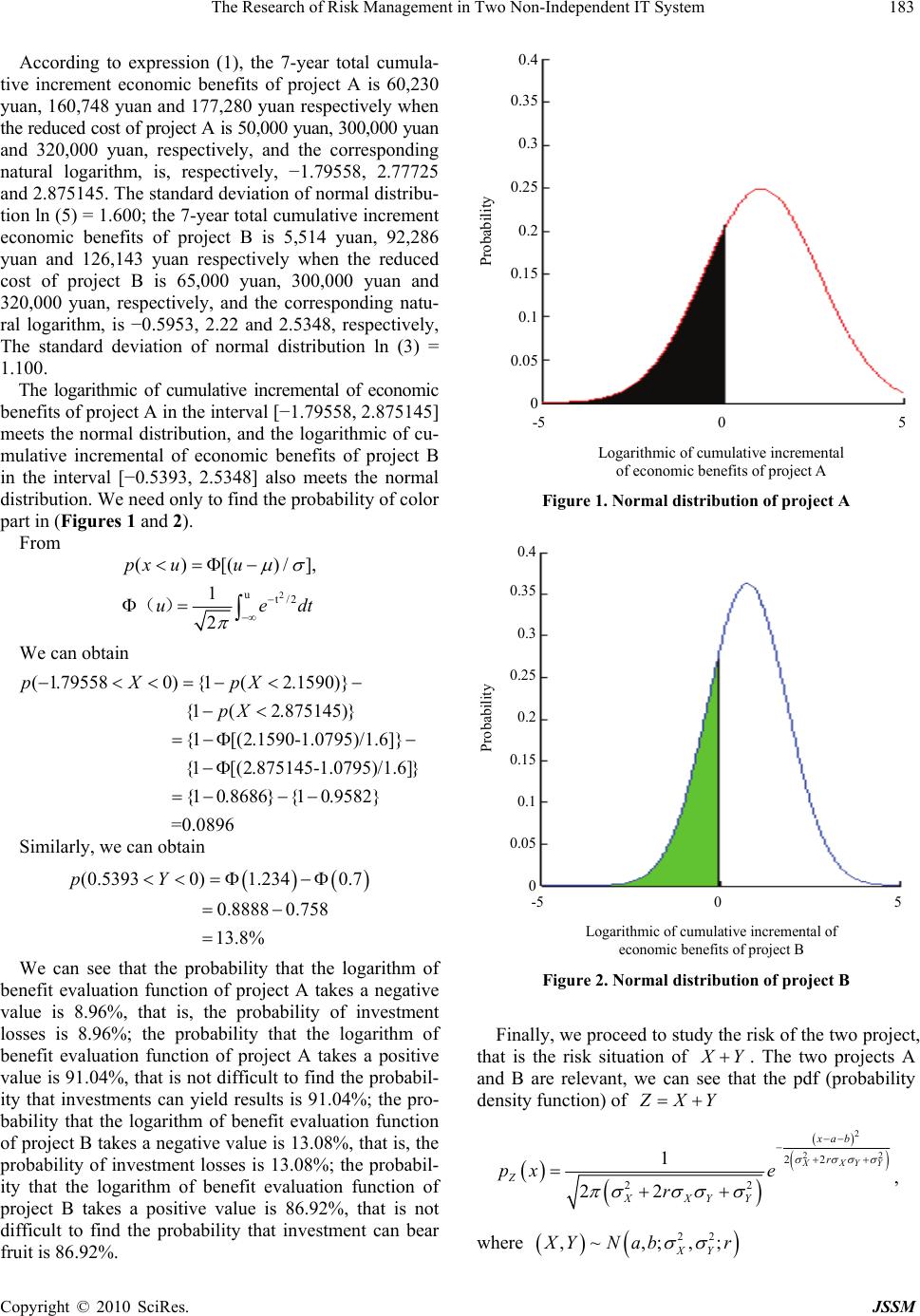 The Research of Risk Management in Two Non-Independent IT System183 According to expression (1), the 7-year total cumula- tive increment economic benefits of project A is 60,230 yuan, 160,748 yuan and 177,280 yuan respectively when the reduced cost of project A is 50,000 yuan, 300,000 yuan and 320,000 yuan, respectively, and the corresponding natural logarithm, is, respectively, −1.79558, 2.77725 and 2.875145. The standard deviation of normal distribu- tion ln (5) = 1.600; the 7-year total cumulative increment economic benefits of project B is 5,514 yuan, 92,286 yuan and 126,143 yuan respectively when the reduced cost of project B is 65,000 yuan, 300,000 yuan and 320,000 yuan, respectively, and the corresponding natu- ral logarithm, is −0.5953, 2.22 and 2.5348, respectively, The standard deviation of normal distribution ln (3) = 1.100. The logarithmic of cumulative incremental of economic benefits of project A in the interval [−1.79558, 2.875145] meets the normal distribution, and the logarithmic of cu- mulative incremental of economic benefits of project B in the interval [−0.5393, 2.5348] also meets the normal distribution. We need only to find the probability of color part in (Figures 1 and 2). From 2 ut/2 ()[() /], 1 2 px uu uedt () We can obtain ( 1.795580){1(2.1590)} {1(2.875145)} {1[(2.1590-1.0795)/1.6]} {1[(2.875145-1.0795) pXpX pX /1.6]} {10.8686}{10.9582} =0.0896 Similarly, we can obtain (0.53930) 1.2340.7 0.88880.758 13.8% pY We can see that the probability that the logarithm of benefit evaluation function of project A takes a negative value is 8.96%, that is, the probability of investment losses is 8.96%; the probability that the logarithm of benefit evaluation function of project A takes a positive value is 91.04%, that is not difficult to find the probabil- ity that investments can yield results is 91.04%; the pro- bability that the logarithm of benefit evaluation function of project B takes a negative value is 13.08%, that is, the probability of investment losses is 13.08%; the probabil- ity that the logarithm of benefit evaluation function of project B takes a positive value is 86.92%, that is not difficult to find the probability that investment can bear fruit is 86.92%. 0.4 0.35 0.3 0.25 0.2 0.15 0.1 0.05 0 Probability -5 0 5 Logarithmic of cumulative incremental of economic benefits of p ro j ect A Figure 1. Normal distribution of project A 0.4 0.35 0.3 0.25 0.2 0.15 0.1 0.05 0 Probability -5 0 5 Logarithmic of cumulative incremental of economic benefits of project B Figure 2. Normal distribution of project B Finally, we proceed to study the risk of the two project, that is the risk situation of X Y. The two projects A and B are relevant, we can see that the pdf (probability density function) of Z XY 2 22 22 22 1 22 XXYY xab r Z XXYY px e r , where 22 ,~ ,;,; XY X YNabr Copyright © 2010 SciRes. JSSM 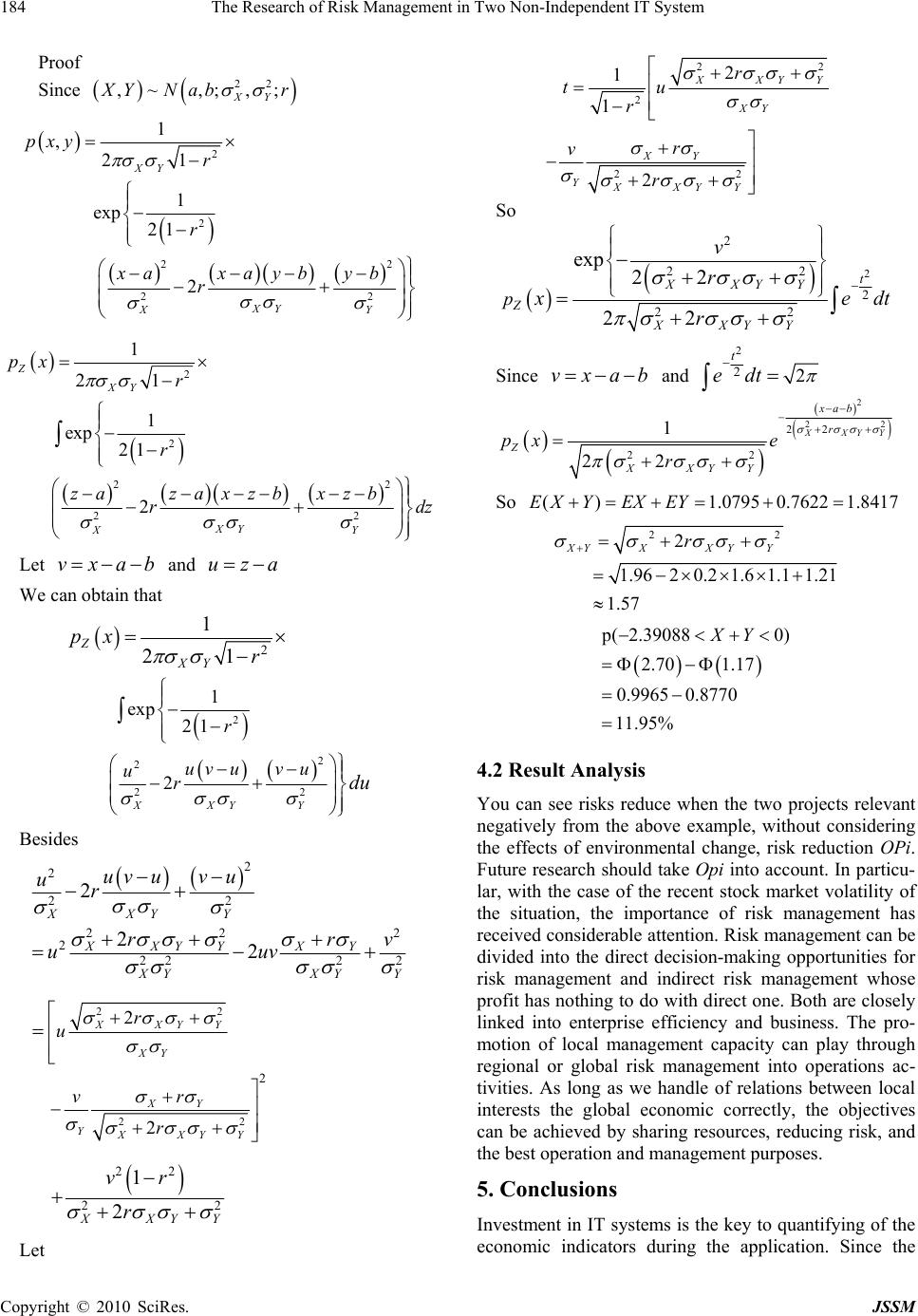 The Research of Risk Management in Two Non-Independent IT System 184 Proof Since 22 ,~ ,;,; XY X YNabr 2 2 22 22 1 , 21 1 exp21 2 XY XY XY pxy r r xaxayb yb r 2 2 22 22 1 21 1 exp21 2 Z XY XY XY px r r zazaxzb xzb rdz Let and vxab uza We can obtain that 2 2 2 22 2 1 exp21 2 1 21 XY XY Z XY r uv uv u ur px r du Besides 2 2 22 22 2 2 222 2 2 22 XY XY XXYYXY XYXY Y uv uv u ur rv uuv r 22 22 2 2 2 XXYY XY XY YXXYY r u r v r 22 22 1 2 XXY vr rY Let 22 2 2 1 1 XXY XY r tu r Y 22 2 XY YXXYY r v r So 2 2 22 2 22 exp 22 22 t XXYY Z XXYY p v r x edt r Since vxab and 2 22 t edt 2 22 22 22 1 22 XXYY xab r Z XXYY px e r So ()1.0795 0.76221.8417EX YEXEY 22 2 1.9620.21.61.11.21 1.57 XYXX YY r p ( 2.390880) 2.70 1.17 0.9965 0.8770 11.95% XY 4.2 Result Analysis You can see risks reduce when the two projects relevant negatively from the above example, without considering the effects of environmental change, risk reduction OPi. Future research should take Opi into account. In particu- lar, with the case of the recent stock market volatility of the situation, the importance of risk management has received considerable attention. Risk management can be divided into the direct decision-making opportunities for risk management and indirect risk management whose profit has nothing to do with direct one. Both are closely linked into enterprise efficiency and business. The pro- motion of local management capacity can play through regional or global risk management into operations ac- tivities. As long as we handle of relations between local interests the global economic correctly, the objectives can be achieved by sharing resources, reducing risk, and the best operation and management purposes. 5. Conclusions Investment in IT systems is the key to quantifying of the economic indicators during the application. Since the Copyright © 2010 SciRes. JSSM  The Research of Risk Management in Two Non-Independent IT System Copyright © 2010 SciRes. JSSM 185 top-down management style, is very difficult to forecast the future assessment of corporate efficiency, this paper presents the loss probability calculation method of risk quantification and easily sharing of risk information me- thod. (Figure 1, Figure 2) can play a function of profit and loss evaluation of the effectiveness of visualization. Future research purpose is the establishment of IT inve- stsment and run-time system, real-time investment eva- luation system in order to reduce investment risks. REFERENCES [1] R. L. Nolan and F. W. Mcfarlan, “Information Technol- ogy and the Board of Directors,” Harvard Business Re- view, Vol. 83, No. 10, 2005, pp. 96-106. [2] S. Inoue, “Risk Management,” Unisys Technology Review, Vol. 67, No. 6, 2000, pp. 100-119. [3] J. F. Sowa and J. A. Zachman, “Extending and Formalizing the Framework for Information Systems Architecture,” IBM System Journal, Vol. 31, No. 3, 1992, pp. 590-616. [4] T. Otsuka, “Software Testing Technology,” Unisys Tech- nology Review, Vol. 93, No. 8, 2007, pp. 70-88. [5] J. Liu, “Introduction to Risk Management [M],” China Financial Press, Beijing, September 2005. [6] T. L. Patton, J. F. Wang translated, “Enterprise Risk Ma- nagement\CFO Management & AMP; Products [M],” China Renmin University Press, Beijing, 2007. |

