Int'l J. of Communications, Network and System Sciences
Vol. 5 No. 11 (2012) , Article ID: 24665 , 4 pages DOI:10.4236/ijcns.2012.511075
The Research on QoS Model Design in Mobile Ad Hoc Networks
International School of Software, Wuhan University, Wuhan, China
Email: yunzhang@whu.edu.cn
Received September 12, 2012; revised October 27, 2012; accepted November 5, 2012
Keywords: Mobile Ad Hoc Networks; QoS; Model; MAC
ABSTRACT
Wireless Ad Hoc Networks is a special kind of wireless communication network. With the great development of multimedia applications, how to provide QoS guarantee in the MAC layer is the hot topic in wireless ad hoc network (MANET). This paper designed a QoS model in MANET. The feasibility and reliability of this model is analyzed and verified. Compared with the traditional model, the proposed approach is improved in MAC layer in order to achieve high control rate of low-priority transactions.
1. Introduction
Wireless Ad Hoc Networks is a special kind of wireless communication network, which is a multi-hop autonomous system composed by a plurality of nodes with a wireless transceiver device. The node in the network has the function as both host and router [1]. Over the past decade, MANET is increasingly becoming a hot research field in computer networking and wireless communications [2]. Since MANET doesn’t require fixed infrastructure and has a strong invulnerability, it has a high application value. The main characteristics of MANET include sharing radio channel, high bit error rate, multi-hop communications and dynamic topology. In this context, it is a great challenge to provide QoS support [3]. On the other hand, although the MANET protocol stack has the similarity with the Internet protocol stack, the related protocols cannot be directly copied from Internet protocol stack due to the particular features of MANET [4].
QoS support in MAC layer is a crucial and challenging topic in the research of wireless ad hoc networks [5]. MAC protocol has the inherent advantage for QoS. The wireless network requires strict synchronization and is complex in the case of multi-hop mobile allocation and scheduling between nodes. If the network has a larger number of nodes, the complexity will increase sharply, which limits the application of mobility protocols in wireless ad hoc networks. Xiao, Y. et al. presented a two-level protection and guarantee mechanism for voice and video traffic in the EDCA-based distributed wireless LANs, which can support multimedia applications such as voice and video over the wireless medium, a contention based channel access function [6]. Ahn, G. S. et al. proposed a stateless network model, called SWAN, which uses distributed control algorithms to deliver service differentiation in mobile wireless ad hoc networks [7].
2. A QoS Model Design in MAC Layer
The 802.11e MAC layer protocol mechanism can be well differentiated services with strong ability to control the business of low priority. However, this method has abandoned the original AIMD algorithm rate control and shaping mechanism. If the best-effort service requirements of the application layer initiates too large, there will be a large number of low priority packets at the MAC layer queuing. These low-priority data transmission rate will be low with the heavier routing load. The low-priority queue is lined after entering the packet is discarded in the MAC layer. Application layer mechanisms can guarantee the retransmission of these packets discarded, but it can also result in additional network overhead. Therefore, the need to control the applicationlayer contracting the queue is full in the MAC layer. Therefore, a feedback mechanism is design. When low priority data queue is full in the MAC layer, the admission control module will detect this situation. The accepted admission control module can control the realtime data services and is responsible for the control of the business. When the MAC queue is detected, the system immediately stops sending best effort to lower business data. To avoid too frequent start and stop transmitting data to the lower layer, the MAC layer queue keep half empty when the admission control module to control data re-starts sending.
Figure 1 shows the model of the signaling frame structure, including probe frames, and initial re-negotiation frames. The frame structure is basically the same, and different frames can be distinguished from type domain. The type domain 0 means it replies detection frame to the destination. All copy detection frame is corresponding domain in addition to the type domain. The type domain 1 denotes the frame sender sends detection frame. It records the bottleneck bandwidth of the domain. The type domain 2/3 means this frame respectively for source-based or network-based re-negotiation message frame. The probe frames of bottleneck bandwidth with 16 bits are not used domain for recording.
Figure 2 shows the process of probe frame path from source to the intermediate nodes. Different from data frame, the probe frame must be at the intermediate node through the layers below to achieve the SWAN module. The probe frame here is to be processed with the bottleneck bandwidth. Data frame needs to reach the IP layer that can be forwarded to the next hop, and it does not need to be forwarded to a higher level. Under ordinary ad hoc routing mechanism, detecting frames and data frames cannot be forwarded to a higher level. In this case, it is necessary to modify the IP layer mechanism to add a package format typing in the IP domain of the probe frame. IP layer receives a packet marked this format, and parses out the probe frame and forwarded to the SWAN module. Storage by SWAN module can be written, and the next hop bandwidth data are re-sent to the destination node. Since the path from origin to destination node is still part of the entire route, the route establishment process will not be re-initiated. This approach will not make the original establishment of the routing change.
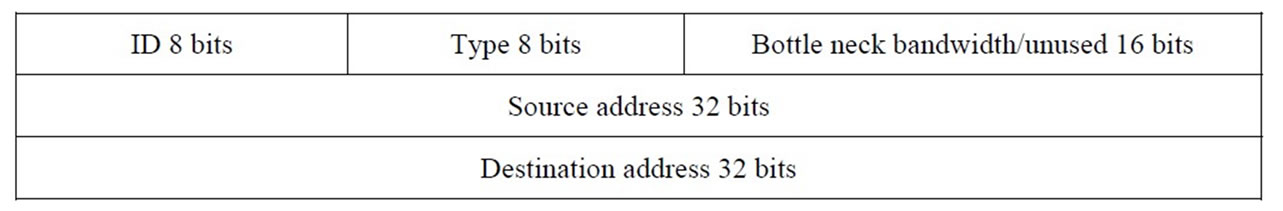
Figure 1. Frame structure of signaling in SWAN.
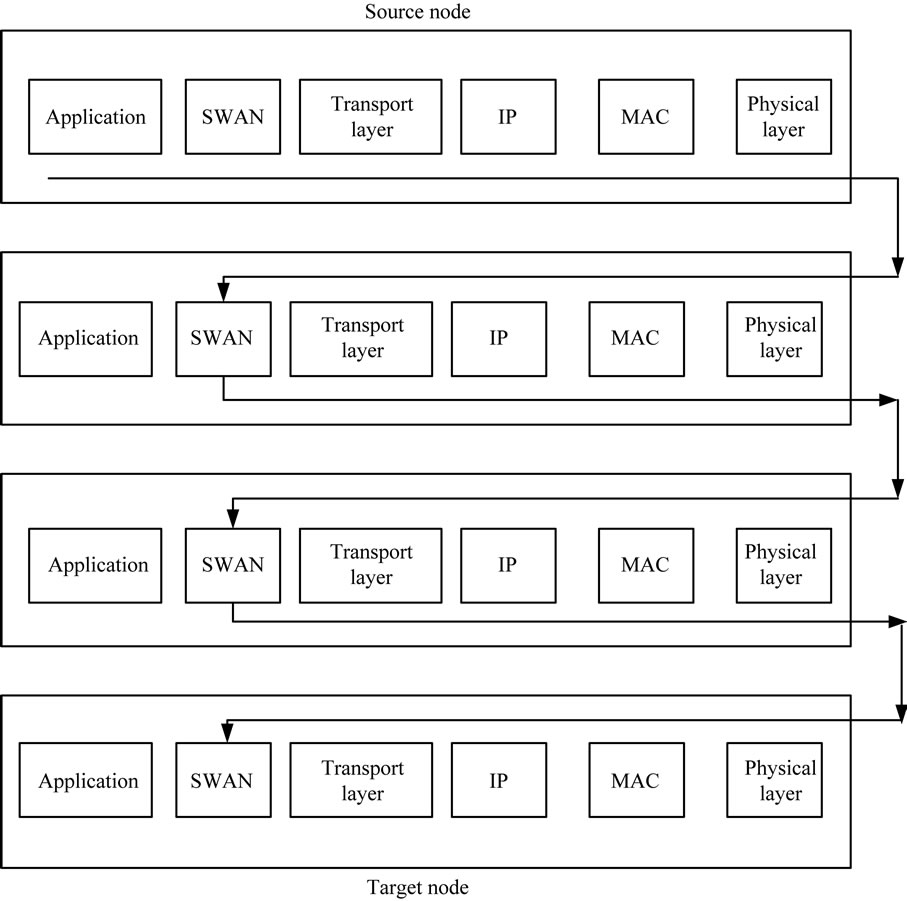
Figure 2. Process of original probe frame in all nodes.
3. Simulations and Result Analysis
The simulations are carried out with 500 m × 500 m rectangular range with node communication distance 150 m and sharing the same channel. The maximum allowable gap between the actual rate and shaping rate in SWAN model and AIMD algorithm is 10%. Change the TCP operations and the number of the load status in the network, and the transmission of best-effort service node is 10. Greedy strategy is adapted for TCP traffic and FTP service. Keep sending packages to lower queue, and try to seize all resources.
For QoS model, our main concern is the delay of the real-time traffic throughput and best effort services. Compared SWAN model with the improved model by these two parameters, we can see the improvement and the progress. The best effort service node is set to 10. Figures 3 and 4 show the comparison of delay parameter of the real-time services of the two models in the MAC layer.
It can be seen from the figure that the delay of improved model of the real-time service is set to be lower than the SWAN model, and the delay is always stable. The delay of SWAN model is more obvious changing up and down. Only when the delay increases to a threshold to reduce the sending rate of the business, the delay is changing up and down in the proposed model. Among the SWAN model, the delay of real-time service with the best effort service sending rate is increasing. Until the delay exceeds the threshold rate of decline, the delay of real-time business declines. The improved model is more stable.
4. Conclusion
Wireless ad hoc network can quickly build up a mobile communication network compared to conventional communication networks. The biggest difference with other networks is that MANET can be constructed at any time, any place to support of the network without hardware network facilities. Its establishment does not depend on the existing network communication facilities, with a certain degree of independence. To provide quality of service guarantee in the network is an important aspect for a network, which is also a research hotspot issue and difficult problem. The main aspect of the research about this problem is to provide different levels of service for different business. For different business, it should provide a different bandwidth, delay, reliability of the service to ensure the various types of services to obtain the required quality of service. To provide quality of service guarantees needs to understand the status and parameters of the network, control access and the rate of new business. This relates to the design of the various layers of the network nodes and cross-layer. It is a system design

Figure 3. Delay of the improved model.
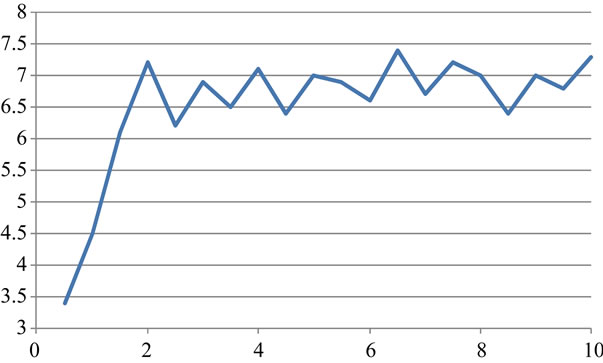
Figure 4. Delay of SWAN model.
work, and its research needs in-depth understanding of the architecture of the network and node. Because of the special nature of the wireless ad hoc network, it commonly uses the computer network to provide service quality assurance and the model does not apply to this network. Therefore, it needs a specialized network design model to accomplish this task.
REFERENCES
- C. Cormio and K. R. Chowdhury, “Common Control Channel Design for Cognitive Radio Wireless Ad Hoc Networks Using Adaptive Frequency Hopping,” Ad Hoc Networks, Vol. 8, No. 4, 2010, pp. 430-438. doi:10.1016/j.adhoc.2009.10.004
- I. F. Akyildiz, W. Y. Lee and K. R. Chowdhury, “CRAHNs: Cognitive Radio Ad Hoc Networks,” Ad Hoc Networks, Vol. 7, No. 5, 2009, pp. b810-b836. doi:10.1016/j.adhoc.2009.01.001
- A. Abdrabou and W. Zhuang, “Statistical QoS Routing for IEEE 802.11 Multihop Ad Hoc Networks,” IEEE Transactions on Wireless Communications, Vol. 8, No. 3, 2009, pp. 1542-1552. doi:10.1109/TWC.2008.080573
- J. Gomez, L. A. Mendez, V. Rangel and A. T. Campbell, “PCQoS: Power Controlled QoS Tuning for Wireless Ad Hoc Networks,” Telecommunication Systems, Vol. 47, No. 3, 2011, pp. 303-321. doi:10.1007/s11235-010-9320-4
- H. Su and X. Zhang, “Cross-Layer Based Opportunistic MAC Protocols for QoS Provisionings over Cognitive Radio Wireless Networks,” IEEE Journal on Selected Areas in Communications, Vol. 26, No. 1, 2008, pp. 118-129. doi:10.1109/JSAC.2008.080111
- Y. Xiao, F. H. Li and S. Choi, “Two-Level Protection and Guarantee for multimedia traffic in IEEE 802.11 e Distributed WLANs,” Wireless Networks, Vol. 15, No. 2, 2009, pp. 141-161. doi:10.1007/s11276-007-0018-9
- G. S. Ahn, A. T. Campbell, A. Veres and L. H. Sun, “Supporting Service Differentiation for Real-Time and Best-Effort Traffic in Stateless Wireless Ad Hoc Networks (SWAN),” IEEE Transactions on Mobile Computing, Vol. 1, No. 3, 2002, pp. 192-207. doi:10.1109/TMC.2002.1081755

