Wireless Sensor Network
Vol.6 No.2(2014), Article ID:43034,8 pages DOI:10.4236/wsn.2014.62004
A Joint Mobility Management Approach and Data Rate Adaptation Algorithm for IEEE 802.15.4/ZigBee Nodes
1Laboratoire d’Electronique Antennes et Télécommunications (LEAT), University of Nice Sophia Antipolis, Nice, France
2RedCAD, University of Sfax, Sfax, Tunisia
Email: Chiraz.CHAABANE@unice.fr
Copyright (c) 2014 Chiraz Chaabane et al. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. In accor-dance of the Creative Commons Attribution License all Copyrights (c) 2014 are reserved for SCIRP and the owner of the intellectual property Chiraz Chaabane et al. All Copyright (c) 2014 are guarded by law and by SCIRP as a guardian.
Received December 24, 2013; revised January 24, 2014; accepted January 31, 2014
Keywords:IEEE 802.15.4; Mobility; Rate Adaptation; Energy Consumption
ABSTRACT
This paper presents an original approach to reduce energy consumption in an IEEE 802.15.4/ZigBee cluster tree network related to a backbone network. Our approach uses an enhanced mobility management of end devices combined with a rate adaptation algorithm. The mobility management approach anticipates link disruption and relies on a speculative algorithm that does not require scanning neighbor cells. The joint mobility management and rate adaptation methods are based on the link quality indicator (LQI). It is demonstrated that even in a noisy en- vironment, the energy consumption as well as the latency of mobile devices can be significantly reduced.
1. Introduction
IEEE 802.15.4/ZigBee [1,2] nodes usually have low energy and low computation capacities. Therefore, reducing energy consumption is crucial in IEEE 802.15.4 networks. It is demonstrated in [3,4] that mobility management in IEEE 802.15.4 standard protocol is not efficiently handled and has to be optimized. Moreover, most of previous researches based on simulations did not consider the noise which is an important issue in real applications. In fact, since the transmitting signal strength range is very low, the effect of noise on the packet reception is important.
In [5], we presented an efficient mobility management approach that significantly reduces the energy consumption and the cell change delay of end devices. The proposed approach anticipates the link disruption and does not require scanning the neighbor cells. It is based on a speculative algorithm that manages cell reselection in an IEEE 802.15.4 cluster tree network connected to a backbone network. The anticipation of the link disruption between a mobile end device and its coordinator is based on an LQI threshold (LQIthreshold). This approach was first evaluated for several mobility scenarios without considering the noise effect. Then, in [6], the LQIthreshold formula has been evaluated in a noisy environment. We also compared the performance of two different speculative algorithms: the same-road algorithm and the probabilistic speculative algorithm. Simulations demonstrated that even in a noisy environment the gain in energy and delay can rise respectively up to 42% and 58%.
Managing mobility and the transmission of a large amount of data has become a big challenge given the limited node energy budget. Optimizing the throughput through adjusting the transmission bit rate of mobile sensor nodes according to the channel conditions can increase considerably the network QoS since it optimizes the use of the superframe. In WLAN networks (e.g. IEEE 802.11), several rate adaptation methods were proposed [7]. Some of WPAN sensor protocols offered multiple rates such as the cc2500 transceiver [8] protocol. However, they did not propose a mechanism for rate adaptation. Moreover, these protocols are proprietary. So far, this feature has not been thoroughly investigated in IEEE 802.15.4/ZigBee sensor networks mainly because sensor protocols do not offer multiple rates. In IEEE 802.15.42.4 GHz frequency band, the bit rate is 250 Kbps. However, previous studies [9,10] demonstrated the feasibility of having three other rates (500 Kbps, 1 Mbps and 2 Mbps) by modifying the chip mapping of symbols in the DSSS modulation.
In this paper, we propose a hybrid approach that reduces the energy consumption of IEEE 802.15.4 mobile end devices through mobility management and rate adaptation. We evaluate the efficiency of this approach in an IEEE 802.15.4 cluster tree network connected to a backbone network.
The paper is organized as follows: Section 2 presents the enhanced mobility management approach. In Section 3, an overview of available rate adaptation algorithms for IEEE 802.15.4/ZigBee networks as well as our mobilityaware rate adaptation algorithm is given. In Section 4, the network performance is evaluated in a noisy environment. Conclusion is given in Section 5.
2. Enhanced Mobility Management Approach
The mobility management aims at reducing the time and energy consumed during synchronization loss periods of mobile sensor nodes. It is a very important feature since resynchronization is energy consuming and has an impact on data transmission. In fact, in the case of communicating nodes, loosing synchronization affects the performance of the routing protocol and results in sending extra control packets. In addition to that, in IEEE 802.15.4 beacon-enabled mode, if an associated node misses a beacon message, it is not able to send packets during the ongoing superframe since it does not know the parameters of the superframe (e.g. length) that may have been changed since the last received beacon.
In this section, we present our mobility management approach for mobile end devices in IEEE 802.15.4 cluster tree network connected to a backbone network. The studied use case consists of static coordinators that form a grid. As it is illustrated in Figure 1, each vertical or horizontal segment can be assimilated to a road. Coordinators are placed in each intersection of a horizontal and a vertical line of the grid.
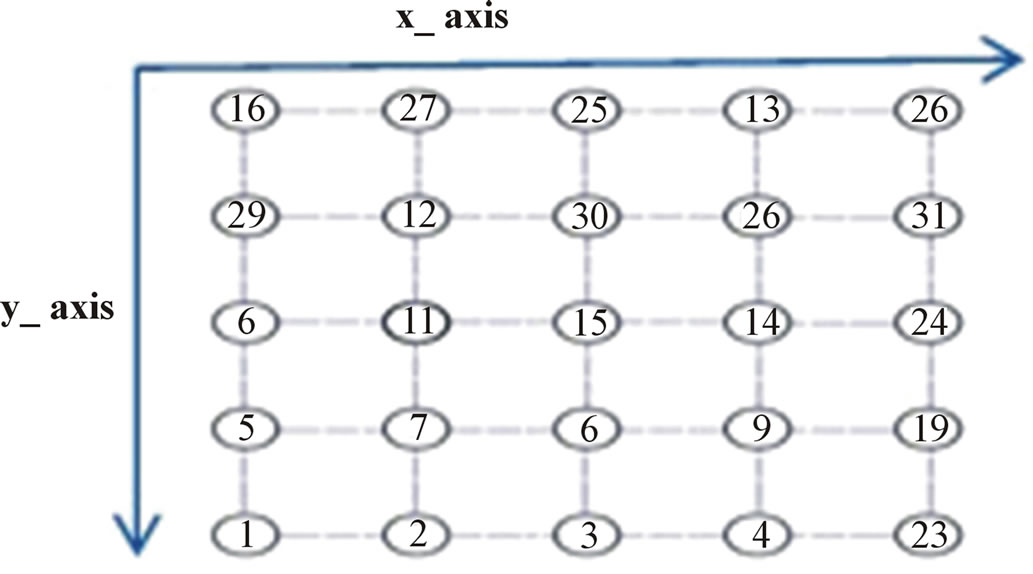
Figure 1. Grid architecture.
Each coordinator defines and initializes a cluster which is a star network having a unique channel frequency on which all cluster nodes communicate. All end devices can only communicate through their coordinator. Coordinators are connected to a backbone network through a device named Super Coordinator (SC). Adjacent cells operate on different frequency channels and the hierarchical addressing mode is used to assign addresses to coordinators and end devices.
The SC has a list of all coordinator addresses, their spatial positions and the channel on which they communicate.
2.1. Procedure of Cell Changing
Our mobility management strategy is intended to keep mobile nodes connected to the network when they move from one cluster to another. This is ensured thanks to cell change anticipation. The handover procedure is triggered by a mobile node when the LQI of a received packet is lower than a given threshold value (LQIthreshold).
Figure 2 summarizes our optimized procedure of cell change and shows exchanged control packets. As detailed in [5], the new coordinator of association is determined by the Super Coordinator based on a speculative algorithm. This approach uses two new MAC control frames: the LQI notification packet (lqiNot) and the LQI response frame (lqiRsp). The lqiNot is sent by a mobile node to its coordinator when it receives a packet with an LQI lower than LQIthreshold. The lqiRsp frame is sent by the current coordinator to the mobile node and contains the next coordinator of association identifier as well as its channel number. The LQIthreshold formula has been defined in [5] and is as follows:
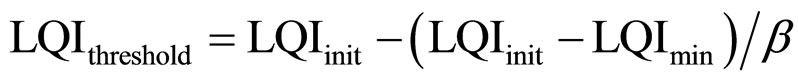 . (1)
. (1)
Where LQImin is a constant and β ≥ 1. LQIinit denotes the LQI corresponding to the first beacon frame received after a successful association procedure. The LQImin corresponds to the minimum value of the LQI parameter and it depends on the RF transceiver sensitivity and the LQI computation. We determine the appropriate time to trigger a new association procedure thanks to the β factor. In
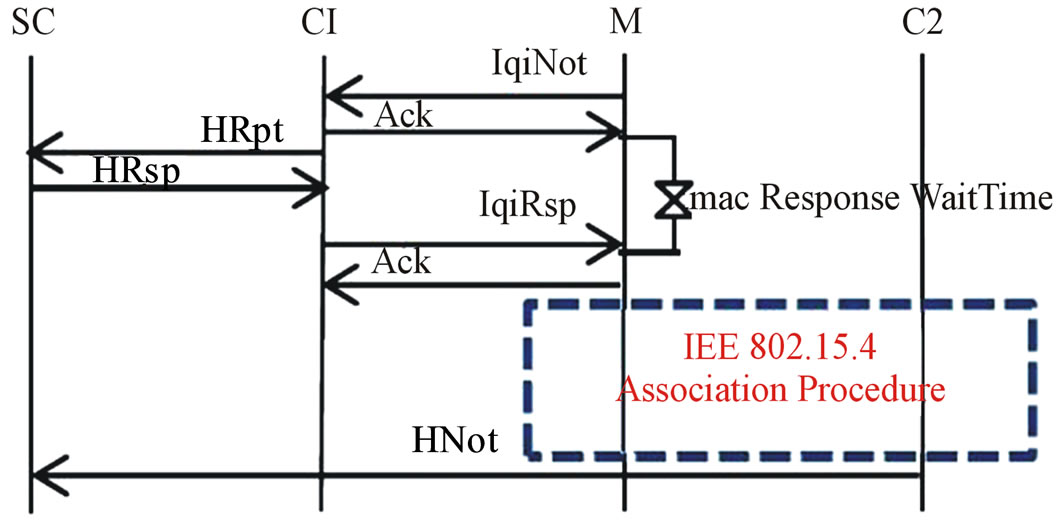
Figure 2. Timing in the cell reselection procedure.
fact, the higher β, the earlier the handover procedure is started (and vice-versa). In [5], we showed that a good tradeoff between the average energy and the cell reselection success rate can be obtained when β is set to 2. We use the same value in this study.
2.2. Speculative Algorithm
The speculative algorithm is handled by the SC in order to determine the next coordinator of association of a mobile node.
SC uses a network matrix in order to describe the geographical positions of coordinators. Columns describe vertical roads and rows describe horizontal roads of the grid. The current coordinator is determined based on two attributes which are its position in the matrix and the current road of the mobile.
In [6], we evaluated our enhanced mobility management approach in a noisy environment for three different mobility models using two different speculative algorithms. It was demonstrated that for the Manhattan mobility model with low turn probability, results are better using the same-road algorithm.
The same-road algorithm favors the movement of nodes on the same road. The choice of the next coordinator of association for a mobile node is based on the previous coordinator of association and on its current road. If the previous coordinator is situated on the left of the current coordinator, then the next coordinator is the coordinator which is on the right of the current one (and vice-versa). Obviously, sometimes, nodes can turn left or right leading to wrong selections of the next coordinator. A default direction is defined and corresponds to the x axis (Figure 1).
3. Rate Adaptation Algorithm
The 2.4 GHz physical layer standard data rate is 250 kbps. This layer uses the DSSS modulation technique. Each 4 bits are encoded into one symbol which is sent over 32 chips.
IEEE 802.15.4 radios can also provide three additional non-standard rates for IEEE 802.15.4 [9]: 500 kbps, 1 Mbps and 2 Mbps. Lanzisera et al. suggested a variable number of chips per symbol (16, 8 or 4). Thus, for each rate, a chip mapping is defined. If the channel conditions are good, using fewer chips per symbol increases the rate without decreasing the signal quality or making major changes in the hardware design.
Table 1 gives the different numbers of chips per symbol, their corresponding bit rate, and the corresponding symbol period.
Rate adaptation algorithms are composed of two major steps that are the link quality estimation and the bit rate selection. Usually, the MAC sub layer uses one or more
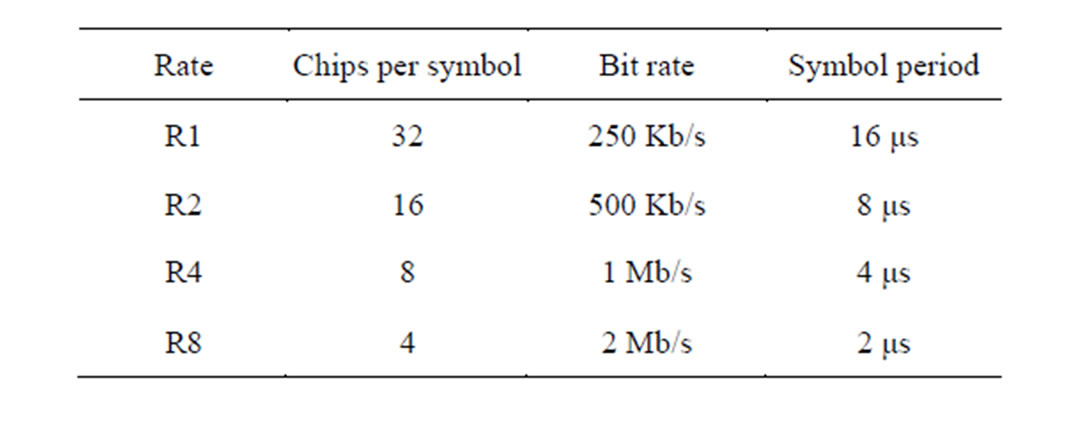
Table 1.Available rates.
parameters of the physical layer that describe the link quality in order to determine the most suitable bit rate for the outgoing frames. The contribution of our paper is a rate adaptation algorithm for IEEE 802.15.4 mobile nodes.
Our algorithm combines rate adaptation algorithm with a mobility management approach in order to optimize the energy efficiency and the synchronization time of mobile end devices.
3.1. Overview of Rate Adaptation Algorithms for IEEE 802.15.4
Rate adaptation techniques are either a function of packet delivery ratio (PDR) [11] or a function of signal strength [12] or a combination of both of them (hybrid algorithms) [9,10].
Both methods in [13] and [10] try to estimate the link quality by removing interferences that distort the estimation. The proposed SoftRate algorithm in [13] was based on the estimation of interference-free BER. The method proposed in [10] was based on the estimation of SNR and signal-to-interference ratio (SIR). In this study, if SNR is under a predefined threshold, the rate is decreased. Otherwise, if SIR is below a predefined threshold, the bit rate is incremented in order to reduce the packet transmission time and thus the probability of collision. Although it is based on the SNR of the last received packet, the SIR is evaluated over a window of 20 super frames, which may lead to inaccuracies if the network conditions change quickly.
On the other hand, the SoftRate algorithm uses a heuristic to predict channel BER at a few other bit rates using the BER estimate at one bit rate. The algorithm computes optimal thresholds for each rate R. Then, given interference-free BER estimate from the receiver and optimal thresholds at each bit rate, the SoftRate sender adjusts its bit rate.
Although the SoftRate can be applied to IEEE 802.15.4 network, it was evaluated using the IEEE 802.11 protocol. Moreover, SoftRate uses extra information added to the acknowledgment frame.
The DRACER rate adaptation algorithm [9] is based either on the LQI or the SNR predefined thresholds. In case of packet transmission failure (i.e. when the sender does not receive an acknowledgment), four different backoff schemes are evaluated:
• Backoff scheme A: The transmitter continues to send at a higher data rate until it is successful, with no reduction in rate.
• Backoff scheme B: Upon a packet failure, the transmitter drops down one data rate and transmits at that rate until receiving an ACK.
• Backoff scheme C: The transmitter drops to the legacy 802.15.4 coding (250 Kbps) upon a single packet failure.
• Backoff scheme D: The transmitter reduces the transmission rate by one step for each packet failure until it hits the legacy 802.15.4 rate.
Results showed that the DRACER rate adaptation algorithm reduces average network energy consumption. Moreover, results are better when the LQI metric is used to define the thresholds and when using the backoff scheme D. However, the DRACER does not consider the case of mobile nodes.
3.2. A Mobility-Aware Rate Adaptation Algorithm
In the previous studies on rate adaptation in IEEE 802.15.4 protocol, node mobility cost and impact on the link estimation was not a major concern. However, in mobile networks, wireless channel conditions are constantly changing. Thus, assessing the channel conditions usingthe channel history (i.e. statistics of packets delivery ratio (PDR)) may lead to irrelevant estimations. Therefore, we estimate the link quality using the LQI of the last received packet. The appropriate rate to be usedis then determinedaccording to the LQI value. Regardless of the current data rate, the next packet data rate is selected based on the most recent LQI at that frequency.
Our method defines LQI thresholds to be used by the rate adaptation algorithm. The range of possible LQI values is determined based on the maximum and the minimum LQI value of a packet. Given that our rate adaptation algorithm is used with our mobility management approach, the LQIthreshold is the minimum value that can be taken into account. Therefore, for each new successful handover the LQI range is computed again and thus the rate adaptation LQI thresholds. Obviously, if a node is static, the minimum possible LQI value is LQImin. Then, after determining the available range corresponding to the link between the mobile node and its new coordinator, four intervals are determined based on the rate adaptation LQI thresholds each one is assigned to a rate.
Let LQIMAX be the maximum value of LQI, ppdu LQI the LQI of the last received packet and setRate () the function used to update the rate of a given link. Our proposed algorithm is as follows:
LQIRA = ceiling ((LQIMAX – LQIthreshold)/4)
If (ppduLQI ≥ LQIMAX – LQIRA) Then setRate (R8);
Else If (ppduLQI ≥ LQIMAX – LQIRA * 2) Then setRate (R4);
Else If (ppduLQI ≥ LQIMAX – LQIRA * 3) Then setRate (R2);
Else setRate (R1);
Based on the LQIthreshold formula (Equation (1)), it can be noticed that LQIRA is a function of LQIinit, LQImin and LQIMAX. When LQIinit is high, LQIRA is low. In this case, the LQI values’ range for each rate is small. Therefore, rate selection algorithm is more sensitive to the channel condition changes: when the quality of channel worsens (i.e. LQI of the received packet decreases), it is more likely that the data rate drops. Actually, if a node is entering a new coordinator coverage area then the longer the handover procedure, the more likely the LQIinit is to be higher. In this case, the channel conditions have not been good enough to establish a new association for lower LQI values. However, when the channel conditions are good, the association is quickly successfully established and thus the corresponding LQIinit is low. The rate adaptation algorithm uses this information in order to dynamically adjust its rate adaptation LQI thresholds computation regarding the handover procedure conduct.
In our approach, the acknowledgments (ACKs) have to be enabled so that both sender and receiver are able to estimate the link quality of each packet sent. Acknowledgments are sent according to the last computed rate. The beacon frame is always broadcasted using the legacy rate in order to ensure its reception. The beacon request frames are also sent using the legacy rate given that nodes that are requesting beacons have not been associated yet and do not have a full knowledge of the channel conditions.
The IEEE 802.15.4 standard specifies a synchronization header for each packet consisting of a preamble followed by a two-symbol start frame delimiter (SFD). As it has already been done in [9], we have added three SFDs to denote the three additional data rates. When a packet is being received, the physical layer recognizes the current data rate of the incoming packet so that the appropriate detection scheme can be used.
4. Evaluation of the Approach
Simulations have been performed in order to evaluate the performance of the network in terms of energy and synchronization time when nodes are moving. As mentioned earlier, when a node does not receive a beacon, it does not send data packet and has to enable its receiver in order to find the beacon. Therefore, the higher the number of received beacon, the longer communications can be assured. Thus, the synchronization time is estimated by the number of received beacons.
First, we have compared the network performance when using the mobility-aware rate adaptation algorithm (RA + MM approach) to the mobility management approach (MM) and to the standard protocol procedure (STD). We have varied the number of mobile nodes from 6 to 30 by a step of 6. This first set of simulation scenarios are intended to evaluate the efficiency of the RA + MM for the whole network. Then, we have focused on its efficiency for a given communicating node that can be a sender or a receiver. The rate adaptation algorithm is strongly dependent on the channel conditions that vary over time.
Therefore, the performance of our algorithm has been evaluated when the packet interval changes.
4.1. Simulation Setup
In this paper, the noise model is an additive Gaussian white noise (AGWN) generated using the Box-Muller method [14] and the variance has been set to 0.3. Simulations have been carried out using the NS-2 simulator [15]. A two-ray ground propagation model has been used.
Using a noise model considerably changes simulation results since the LQI depends on a random phenomenon among other factors (e.g. distance between communicating nodes).
We have used the Manhattan mobility model without pause periods and with a turn probability (TurnProb) set to 0.2. Table 2 summarizes common setup parameters for all mobility scenarios.
4.2. Network Performance of the Mobility-Aware Rate Adaptation Algorithm
The average number of received beacon by end devices as well as the average remaining energy have been determined for each scenario and given in Figure 3 and in
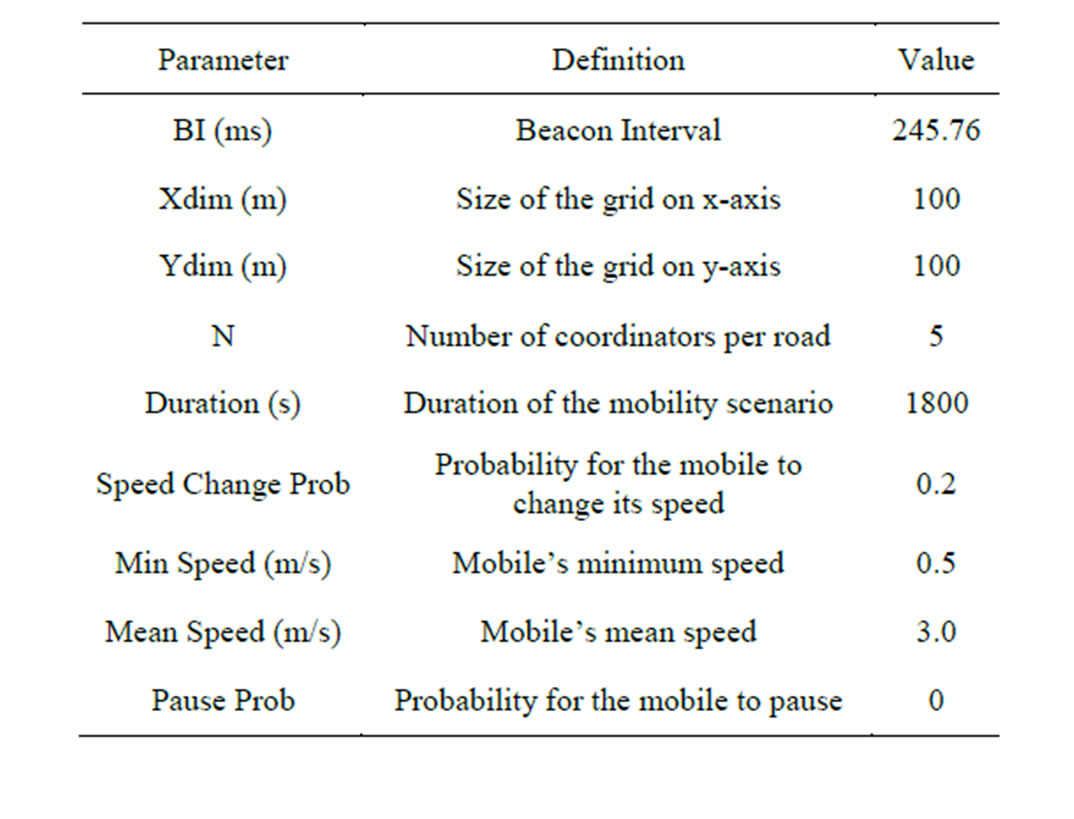
Table 2. Simulation setup.
Figure 4. As it can be seen, the average number of received beacon and the remaining energy are more important for both RA + MM and MM approaches compared to the standard IEEE 802.15.4 protocol. However, the difference between the average number of received beacon when using either the RA + MM or MM approach is not very important. Nevertheless, the remaining energy when using the RA + MM approach is more important. As a consequence, one can verify the energy efficiency of the RA + MM approach.
4.3. Performance Analysis of a Communicating End Device
So far, we have not considered the case where end devices are communicating. In this section, we have conducted simulations where two nodes are communicating. In the beacon-enabled mode, packets sent from a source (Src) to a destination (Rcv) are routed by the corresponding coordinators of Src and Rcv even if they share the same PAN (same coordinator for both the sender and the receiver). In our approach, if the Src and Rcv are not in the same PAN, packets are routed from the coordinator of Src to the coordinator of Rcv by the Super Coordinator. This hybrid routing mechanism has been implemented and added to NS-2 simulator. When an end device receives a packet with an LQI lower than the LQIthresholds, it has to trigger the change of cell procedure by sending an LQINot message to its coordinator. When it
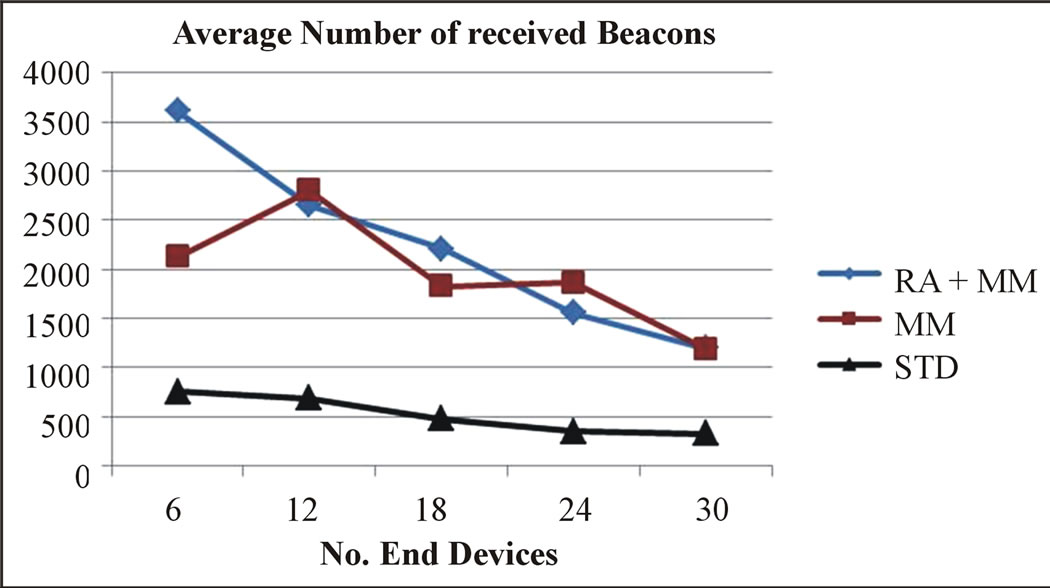
Figure 3. Average number of received beacons.
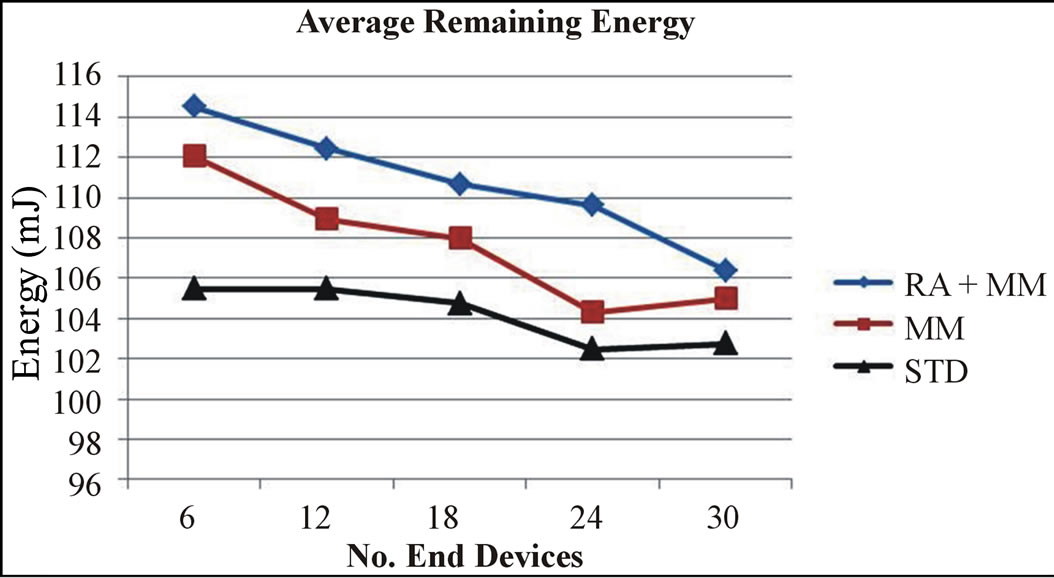
Figure 4. Average remaining energy.
receives the LQIRsp, it has to begin the association procedure with the new coordinator. At this stage, the node cancels the packet transmission and resumes it at the end of the association procedure. If nodes are receiving data packets, the probability that they trigger this procedure more often is higher. Moreover, when end devices are sending or receiving data packets, the amount of exchanged packets with their corresponding coordinators is more important. In consequence, end devices are able to update the data rate more quickly.
4.3.1. Energy, Synchronization and PDR Evaluation
Simulations have been conducted using both RA + MM and MM approaches as well as the IEEE 802.15.4 standard protocol (STD).
We study the impact of communication on the remaining energy and the synchronization time of both sender and receiver. In our simulations, packets’ length is 113 bytes (physical layer) and they are sent using a constant bit rate transmission every 10 seconds. The packet delivery ratio is determined in each simulation.
It can be seen in Figure 5 that the number of received beacons for both the sender and the receiver is consistent with the general network evaluation results shown in Figure 3. It can also be seen that the received beacons’ number of both sender and receiver is higher than the average beacon number from Figure 3. Moreover, as it is illustrated in Figure 6, the remaining energy in the RA + MM approach is higher than in the MM approach. However, unlike the results obtained in the previous simulations (Figure 4), the remaining energy when using the standard protocol is the highest among the three approaches. Actually, when using the standard protocol, the time during which nodes are not synchronized is the longest. Therefore, the number of sent and received data packets is the lowest. As a result, the energy spent in data communication is lower than in the RA + MM and MM approaches. We can also deduce from Figures 4 and 6 that data transmission has a stronger impact on the remaining energy than the cell change procedures which is mainly due to the length of data packets. Figure 7 gives
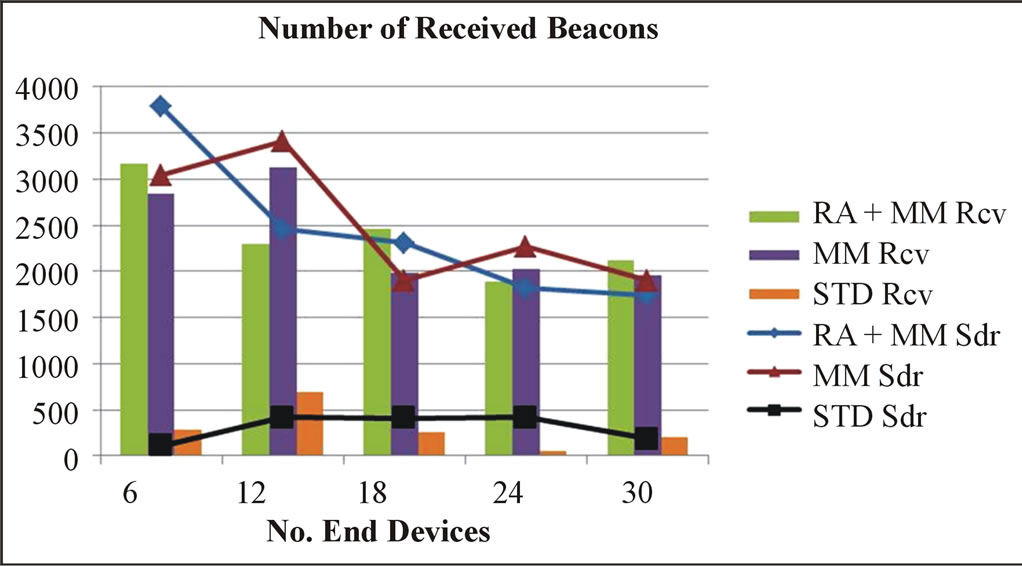
Figure 5. Number of received beacons for communicating nodes.
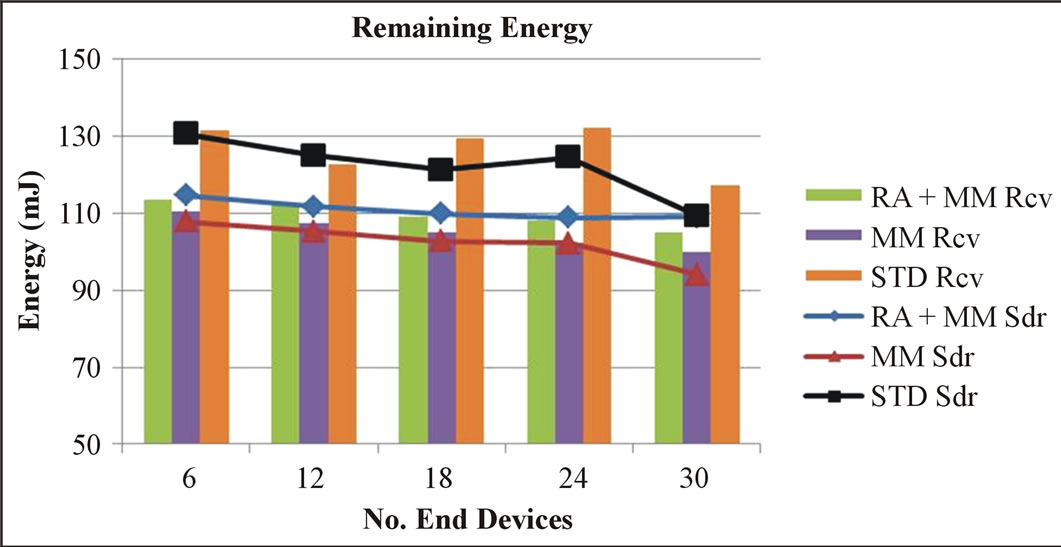
Figure 6. Remaining energy of communicating nodes.
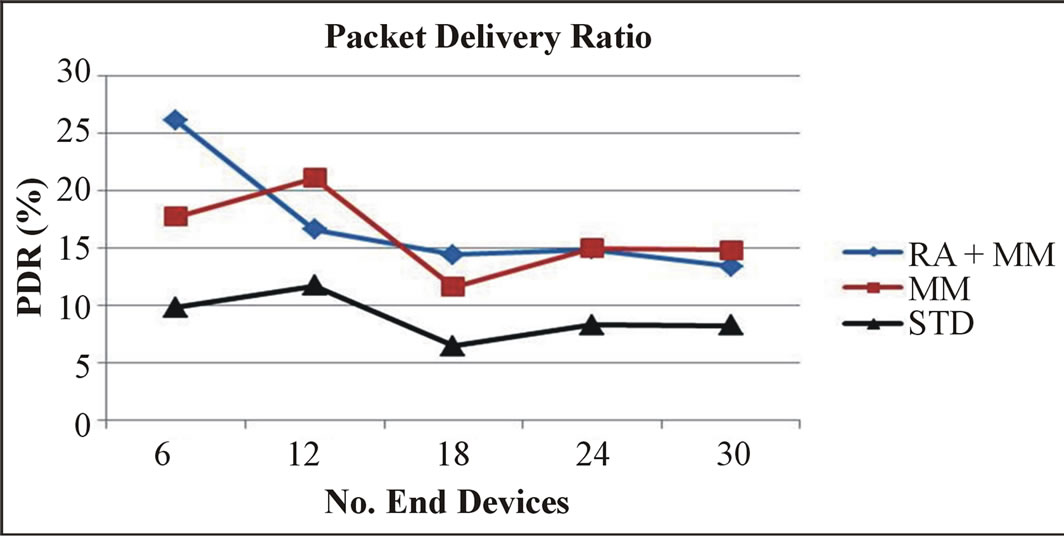
Figure 7. Packet delivery ratio.
the packet delivery ratio (PDR) for the different approaches. It can be seen that there is a slight variation between the RA + MM and the MM approaches. However, PDR is always better than in the STD case.
4.3.2. Impact of Packet Interval
The IEEE 802.15.4 slotted CSMA/CA protocol uses backoff periods to overcome packet transmission failures. In fact, if a packet transmission fails, the sender has to wait for a random backoff period before resuming the packet transmission. However, this period is computed independently from the channel coherence time. Therefore, if the channel conditions during retries are still the same or worse, successive failures occur and latency is increased. Network performance would improve if the packet interval depends on the time coherence of the channel. If the interval is too small compared to the coherence time, packet error rate will be high when channel conditions are bad and vice-versa. The packet interval management may also involve the application layer. However, since backoff parameter is a MAC-layer parameter, designing a PHY-aware mac layer would give extra information to handle packet interval more efficiently.
In this section we highlight the impact of modifying the packet interval. For that, we have varied the packet transmission interval (1, 5, 10, 20 and 60 seconds) of the CBR (Constant Bit Rate) application. The number of mobile nodes in the scenarios is set to six including a sender and a receiver. As it can be seen in Figure 8 and in Figure 9, the remaining energy in RA + MM approach is always higher with a slight difference in the number of received beacon. In Figure 10, one can see the impact of changing packet transmission interval on the packet delivery ratio.
5. Conclusion
This paper proposes a mobility-aware data rate adaptation algorithm. The joint mobility management and rate adaptation modules are based on the LQI parameter. The rate adaptation algorithm uses LQI thresholds and dynamically adjusts them according to the most recent handover procedure conduct. Although adding three ad-
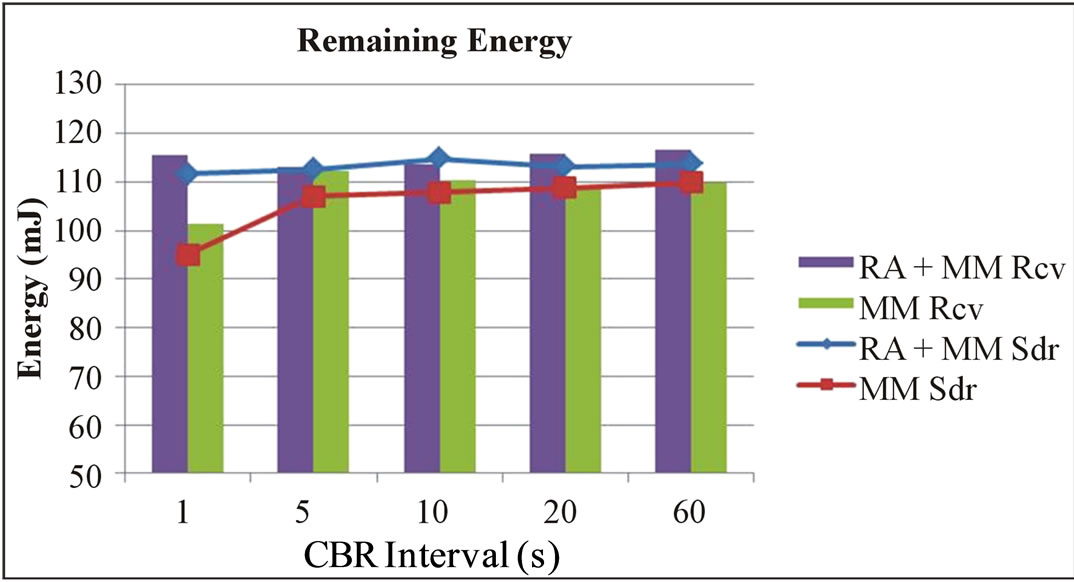
Figure 8. Remaining energy of communicating nodes vs. CBR interval.
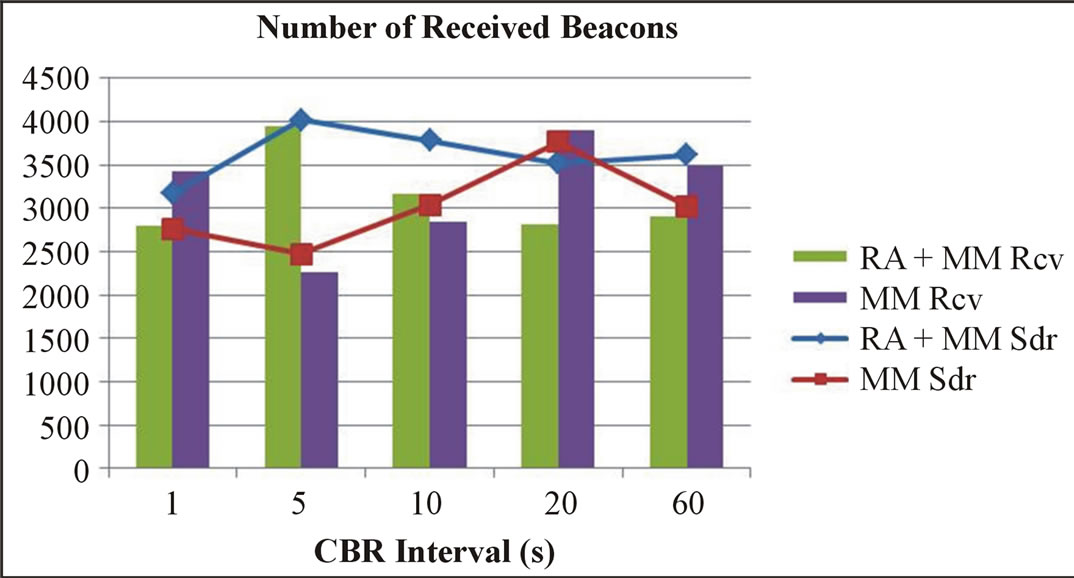
Figure 9. Number of received beacon of communicating nodes vs. CBR interval.
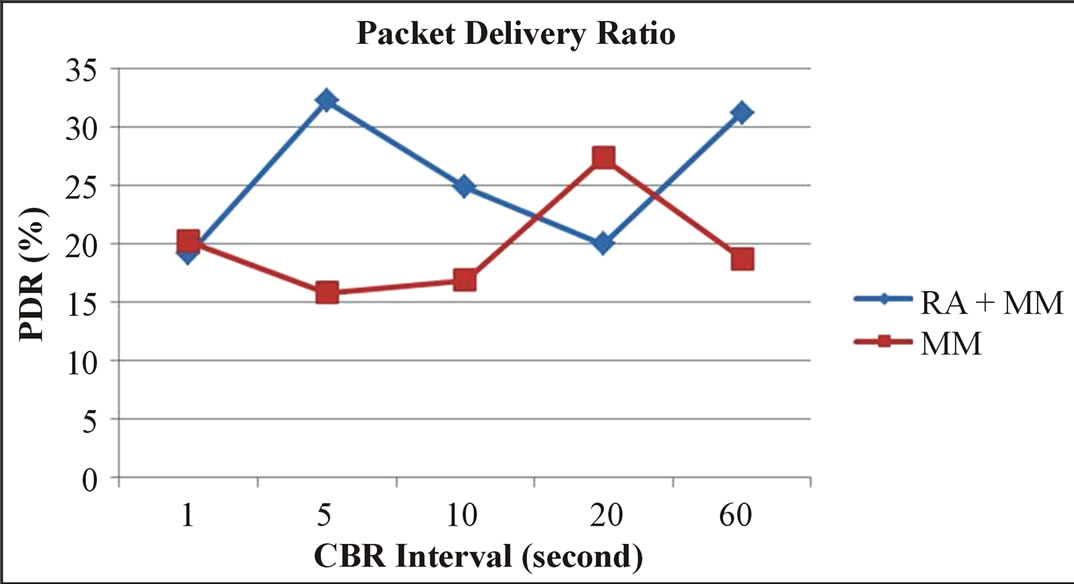
Figure 10. Packetdelivery ratio of communicating nodes vs. CBR interval.
ditional rates to the IEEE 802.15.4 standard protocol does not require heavy changes in the hardware design, we have shown that our approach (RA + MM approach) is more energy efficient compared to the standard protocol and to the case where only the mobility management approach is used (MM approach). In fact, simulations have demonstrated that besides the considerable improvement in the average time of synchronization for both MM and RA + MM approaches compared to STD approach, the average remaining energy in RA + MM is higher. We have also analyzed the performance of communicating nodes (a sender and a receiver) and have figured out that the high remaining energy when using the standard protocol (STD) is due to long periods of synchronization loss during which nodes do not communicate. We have also demonstrated the energy efficiency of our approach compared to the mobility management (MM) approach. Communicating node analysis has also shown the efficiency of our approach in terms of synchronization time. In fact, the number of received beacons for both sender and receiver is higher than the average beacon number. Finally, we have highlighted the impact of changing the packet interval on the network performance. This is useful for conceiving a new PHYaware MAC layer that can tune CSMA-CA backoff periods; accordingly, the packet transmission time can be tuned in order to optimize the packet delivery ratio.
REFERENCES
- IEEE 802.15 WPAN Task Group 4 (TG4), “IEEE 802.15.4- 2006 standard: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Low Rate Wireless Personal Area Networks (LR-WPANs),” 2006. http://www.ieee802.org/15/pub/TG4.html
- Zigbee Alliance Homepage. http://www.zigbee.org
- C. Chaabane, A. Pegatoquet, M. Auguin and M. B. Jemaa, “Energy Optimization for Mobile Nodes in a Cluster Tree IEEE 802.15.4/ZigBee,” Computing, Communications and Applications Conference, Hong Kong, 11-13 January 2012, pp. 328-333.
- L. Chen, T. Sun and N. Liang, “An Evaluation Study of Mobility Support in ZigBee Networks,” Journal of Signal Processing Systems, Vol. 59, No. 1, 2010, pp. 111-122. http://dx.doi.org/10.1007/s11265-008-0271-x
- C. Chaabane, A. Pegatoquet, M. Auguin and M. BenJemaa, “An Efficient Mobility Management Approach for IEEE 802.15.4/ZigBee Nodes,” High Performance Computing and Communication & 2012 IEEE 9th International Conference on Embedded Software and Systems (HPCC-ICESS), Liverpool, 25-27 June 2012, pp. 897- 902.
- C. Chaabane, A. Pegatoquet, M. Auguin and M. BenJemaa, “Mobility Management Approach for IEEE 802.15.4/ ZigBee Nodes in a Noisy Environment,” Proceedings of 26th International Conference on Architecture of Computing Systems (ARCS), Prague, 19-22 February 2013, pp. 1-5.
- S. Biaz and S. E. Wu, “Rate Adaptation Algorithms for IEEE 802.11 Networks: A Survey and Comparison,” IEEE Symposium on Computers and Communications, Marrakech, 6-9 July 2008, pp. 130-136.
- CC2500 Single Chip Low Cost Low Power RF Transceiver Datasheet (Rev. C), 19 May 2009, Texas Instruments. http://www.ti.com/product/cc2500
- S. Lanzisera, A. M. Mehta and K. S. J. Pister, “Reducing Average Power in Wireless Sensor Networks through Data Rate Adaptation,” Proceedings of the 2009 IEEE International Conference on Communications, Dresden, 14- 18 June 2009, IEEE Press, Piscataway, pp. 480-485.
- F. Martelli, R. Verdone and C. Buratti, “Link Adaptation in Wireless Body Area Networks,” Proceedings of IEEE VTC Spring, Budapest, 15-18 May 2011, pp. 1-5.
- M. Lacage, M. H. Manshaei and T. Turletti, “IEEE 802.11 Rate Adaptation: A Practical Approach,” Proceedings of the 7th ACM International Symposium on Modeling, Analysis and Simulation of Wireless and Mobile Systems (MSWiM ‘04), Venice, 4-6 October 2004, ACM, New York, pp. 126-134.
- G. Holland, N. Vaidya and P. Bahl, “A Rate Adaptive mac Protocol for Multi-Hop Wireless Networks,” Proceedings of the 7th Annual International Conference on Mobile Computing and Networking (MobiCom ‘01), Rome, 16-21 July 2001, ACM, New York, pp. 236-251.
- M. Vutukuru, H. Balakrishnan and K. Jamieson, “CrossLayer Wireless Bit Rate Adaptation,” Proceedings of the ACM SIGCOMM 2009 Conference on Data Communication (SIGCOMM ‘09), Barcelona, 17-21 August 2009, ACM, New York, pp. 3-14.
- G. Box, and M. Muller, “A Note on the Generation of Random Normal Deviates,” Annals of Mathematical Statistics, Vol. 29, No. 2, 1958, pp. 610-611. http://dx.doi.org/10.1214/aoms/1177706645
- “Ns-2Simulator,” Version ns-2.34, 2009. http://nsnam.isi.edu/nsnam/index.php/mainpage

