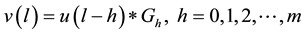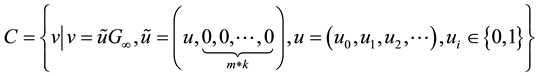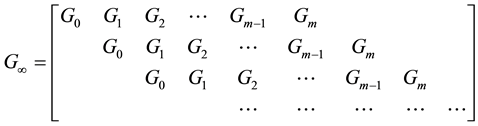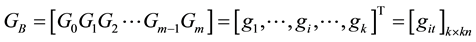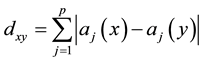International Journal of Intelligence Science
Vol.05 No.01(2015), Article ID:52453,6 pages
10.4236/ijis.2015.51002
Target Image Classification through Encryption Algorithm Based on the Biological Features
Zhiwu Chen1, Qing E. Wu1,2*, Weidong Yang2
1College of Electric and Information Engineering, Zhengzhou University of Light Industry, Zhengzhou, China
2School of Computer Science, Fudan University, Shanghai, China
Email: *wqe969699@163.com
Copyright © 2015 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 8 October 2014; revised 16 November 2014; accepted 1 December 2014
ABSTRACT
In order to effectively make biological image classification and identification, this paper studies the biological owned characteristics, gives an encryption algorithm, and presents a biological classification algorithm based on the encryption process. Through studying the composition characteristics of palm, this paper uses the biological classification algorithm to carry out the classification or recognition of palm, improves the accuracy and efficiency of the existing biological classification and recognition approaches, and compares it with existing main approaches of palm classification by experiments. Experimental results show that this classification approach has the better classification effect, the faster computing speed and the higher classification rate which is improved averagely by 1.46% than those of the main classification approaches.
Keywords:
Encryption, Palm Recognition, Classification, Feature Extraction

1. Introduction
The occurrence of computer has prompted the development of network and society informationization. On the other hand, the networked and informationized society demands a higher security for the information and systems [1] . The body biometric recognition technology is to use the biological characteristics owned by the human body to carry out an automatic identification, biology recognition technique for short, which is one of fundamental methods which are used for enhancing the security of information and systems. The palmprint recognition technology is an important part of the biology recognition ones [2] . Currently, the palmprint recognition technique has been widely used in police department, military branch and so on.
In 1998, the idea of automatic identification by using palm recognition was described systematically and comprehensively by Hong Kong Polytechnic University and Tsinghua University [3] , which summarized comprehensively the characteristic of palm and the palmprint and opened up the research areas of palmprint recognition technology. Based on high resolution palmprint images, You et al. used the point of interest in the palmprint to carry out identification [4] . Among algorithms of image segmentation [5] - [7] , the Fuzzy C-Means clustering [6] is one of algorithms that has some better features which can meet the human cognition pattern, be described concisely and clearly, and be easy to implement and so on. However, this algorithm has some disadvantages such as its performance depending on the initial clustering center, poor antinoise capability, and slow convergence and so on. From the research of traditional Markov Random Field (MRF) [7] , the segmentation effect of MRF to micro texture is better, but the segmentation result of macro texture has many isolated islands or small areas.
Through studying the biological characteristics of palm, this paper analyses the features of texture principal lines, papilla ridges and bifurcation points of palm. At the same time, this paper gives an encryption algorithm and presents a biological classification algorithm based on the encryption process. Moreover, this paper calculates the distance between the characteristic vector of identified palm and that of known palm, and estimates the similarity degree between the two vectors by the distance. According to the minimum distance, the classification result can be obtained. Finally, the comparison of the proposed and existing classification approaches of palm is given.
2. Biological Feature Analysis
An appropriate encryption algorithm is more suitable for the features extraction of biological information, because the encryption to features of biological target is only include the characteristics of biological target, but not involve in some noises and background. Therefore, the analysis to biological feature needs to be discussed firstly in this section. Here, the features of palmprint as a biological feature example are analyzed.
The main research object to palm is the palmprint and fingerprint. The palmprint is the whole human palm excluding fingers, i.e., the part between the finger roots and the wrist. There is a plenty of texture information in this area including several obvious principal lines, irregular wrinkles, trivial papillary ridges and a number of bifurcation points [3] , which can be used as the features of palm and extracted by different methods to carry out an identification. In recent years, some researches on palmprint recognition had been attracted special attention, and some progress had been obtained, but further researches are to be made.
The fingerprint refers to the grain generated by the jagged lines on the skin of the finger ends [8] [9] . These lines of the skin in the pattern, break point and intersection are varied, and the morphology of the grain varies with everyone. i.e., the grain line of everyone is different each other, which is called a “feature” in information processing. By comparing a man’s fingerprint with previously saved fingerprints, his real identity can be verified. There is a plenty of texture information in fingerprint segment [8] [10] including several obvious grain lines, rotation direction, area coverage, trivial papillary ridges, a number of bifurcation points, break point and intersection, which can be used as the features of fingerprint and extracted by different methods to carry out an identification.
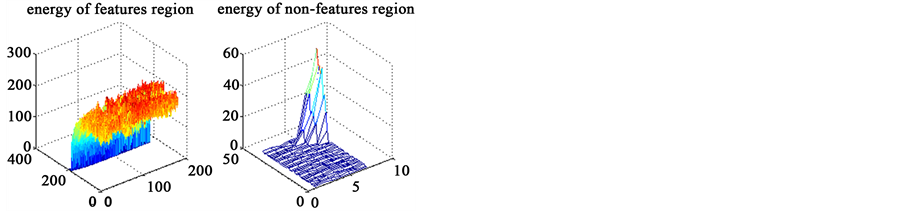
In palm image, the gray level of pixels in the features region and ones in the non-features region are different, as shown in the energy diagrams of Figure 1. From the Figure found clearly, the texture feature in the features region is very prominent, which shows a fine feature of energy mutation, but the energy feature diagram of non- features region almost levels off and the mutation is not obvious.
There are a plenty of papillary ridges in a palm, which are analogous to the fingerprints. However, compared with fingerprints, the geometric regularity of papillary ridges is not so evident. Through a large number of observations, these papillary ridges show some certain regularity in specific region of palm exclude fingers. As shown in Figure 2, in the lower part of index finger root, middle finger root, ring finger root and little finger root, there are four convergent points called as triangular points, which are formed by the corresponding papillary ridges. Since these triangular points are innate and not susceptible to being damaged, and their positions are very fixed, a palmprint image can be divided up by the positions of these triangular points.
In comparison with most recognition approaches, the fingerprint and palmprint recognition suffers fewer disturbances because of the shape of palm and the acquirement of fingerprint or palmprint image is stable. Thus, a relatively fixed fingerprint or palmprint image can be obtained no matter in when and where, and what state. In a
Figure 1. Energy feature of palm image.
Figure 2. Triangular point in a palm.
concrete extraction, either the one of those features of fingerprint or palmprint may be extracted such as the one of principal lines and bifurcation points, or all features are extracted by high resolution acquisition equipment and fuse them together to construct a high precision palm recognition system.
3. Image Encryption Algorithm Proposed to Target Feature
For carrying out encryption, an encryption algorithm is given as follows:
Assume the current inputted feature is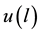 , and also inputted
, and also inputted 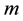 features are
features are 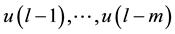 before. By the encryption algorithm, the current output information
before. By the encryption algorithm, the current output information 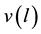 can be obtained. Their relationship can be denoted by the following formula.
can be obtained. Their relationship can be denoted by the following formula.
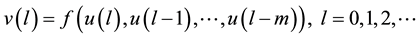
where 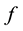 is a binary linear convolution code algorithm, i.e., is a Boolean function composed by modular binary addition operation. Assume the length of
is a binary linear convolution code algorithm, i.e., is a Boolean function composed by modular binary addition operation. Assume the length of 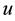 is a constant
is a constant 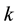 bits, and the length of
bits, and the length of 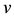 is a constant
is a constant 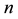 bits, which they are all called one section.
bits, which they are all called one section.
For each 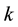 bits input, produce a
bits input, produce a 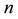 bits output. The relation of any input section
bits output. The relation of any input section 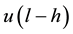 and any output section
and any output section 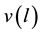 is a special relation of linear block encoding
is a special relation of linear block encoding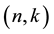
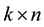
Therefore, for each message queue, 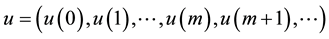
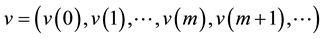
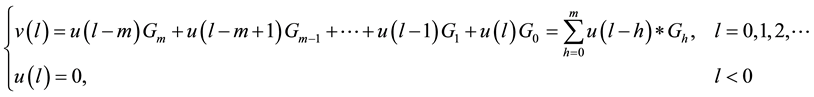
Formula (1) is a convolution code model. The binary linear convolution code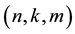
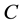
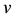
where 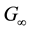
The 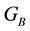
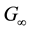
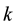
The 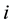
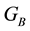
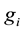
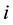
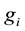
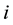
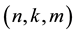
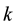
Through doing some experiments, the feature extraction based on the proposed encryption algorithm can provide translation, rotation, or scale invariant properties, because the algorithm is only involve in the characteristics of biological target, but not include the position of target.
4. Give Image Classification or Recognition Algorithm
4.1. Propose Algorithm of Classification or Recognition
According to the principal lines, triangular points, irregular wrinkles, trivial papillary ridges and a number of bifurcation points of palmprint feature, some palmprints can be classified. Or if the search fingerprints are classified according to such attributes of fingerprint as grain lines, rotation direction, area coverage, trivial papillary ridges, a number of bifurcation points, break point and intersection, with the 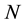
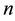
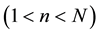
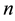
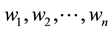
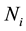
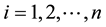
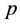
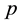
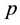
racteristic space. Moreover, for any sample to be identified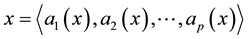
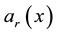
the 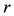
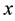
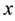
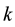
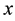
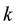
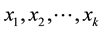

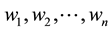
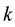
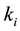
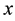
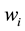
Distance definition: Assume the sample 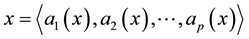
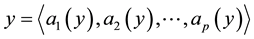
Assume 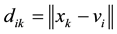
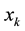
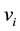
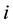
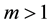
The center 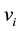
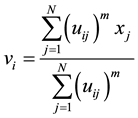
where 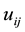
(1) The defined 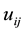
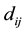
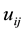
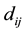
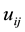
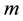
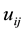
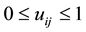
but the sample may not belong to the same category, so 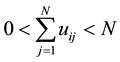
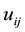
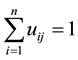
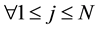
For a sample 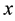
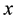
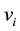
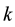
that is closest to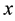
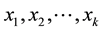
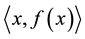
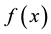
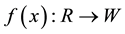
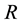
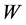
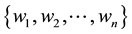
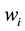
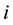
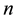
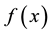
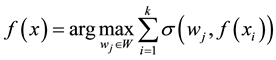
here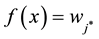
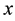
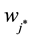
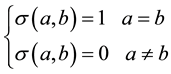
4.2. Experiment and Analysis
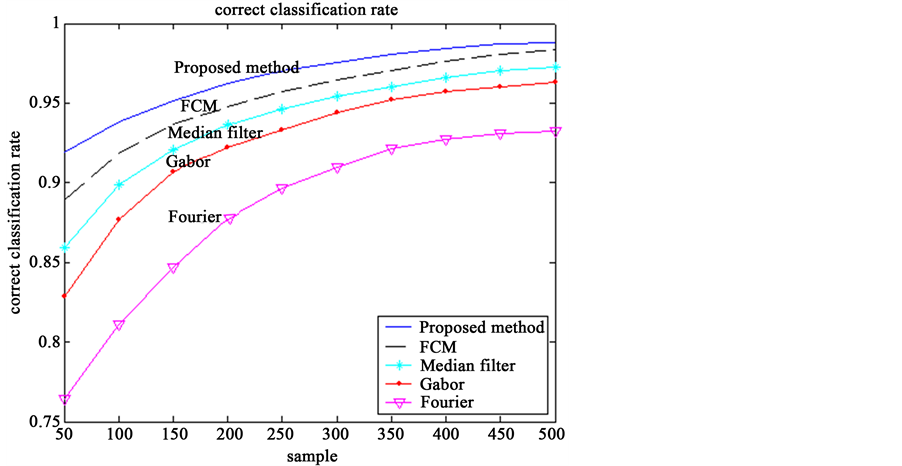
Here, the Hong Kong Polytechnic University (HKPU) palmprint database is used for evaluating the classification or recognition algorithm. For each palm image, 10 times repeating experiments are carried out by the above feature classification and recognition method in simulation. Moreover, some features of palm here are used for the classification and recognition algorithm, i.e., principal line, irregular wrinkle, trivial papillary ridge, bifurcation point, triangular point features. The number of samples is different in each experiment. The literature [11] provided an updated survey of palmprint recognition methods, and presented a comparative study to evaluate the performance of the state-of-the-art palmprint recognition methods. According to [11] , the proposed classification approach compares with those currently usually used approaches such as FCM [6] , Median filter [9] , Gabor [12] and Fourier transform [13] . The experimental results show that the average correct classification rates of these approaches are 95.57%, 94.11%, 93.24%, 92.45% and 88.17% in simulation of 500 times, respectively. The simulation results are shown in Figure 3.
Figure 3. Comparison of correct classification rate for the proposed and other classification approaches
From Figure 3 concluded, the average correct classification rate of the classification approach based on feature extraction of encryption is the highest among all referred approaches. In experiment, the average correct classification rate increases constantly with the increasing classification samples, and the curve of average correct classification rate gradually levels off as the samples increase when the number of samples reaches a certain value. Through 500 times simulation, the simulation results show that every average correct classification rate is a stable value respectively when the number of samples are enough much. Moreover, the average correct classification rate of the proposed approach based on feature encryption is the highest, and its classification effect is also the best, which is shown in Table 1.
To evaluate the comprehensive performance of these approaches, we adopt the combination of quantitative analysis and qualitative analysis method, and synthesize comparison based on some factors such as the computing speed, memory capacity, communications traffic and correct classification rate. We evaluate the merits and demerits of different classification approaches for palm. Table 1 gives the results of a comprehensive comparison.
In Table 1, the computing speed is the mean time obtained by the mean computing time of 10 times repeating test of these approaches at each step in simulation environment, which the computing time is only the computing time of algorithm itself. In simulation, the computer used is the Pentium 4 and 2G memory, and the programming language is Matlab. The memory capacity and the communications traffic are estimated approximately based on the computing course and complexity of every approach. From the results of Table 1 seen, the memory capacity and communications traffic are close related. The average correct classification rates are the average of two stages which are an average of 500 times simulations and then taking an average of 10 time-steps for every approach under the given simulation environment. In fact, they are the average of the correct classification rates in space and time, so they are an overall average of the correct classification rates.
On the basis of the simulation results, the classification approach based on feature extraction of encryption not only has the faster processing speed, the lower memory capacity and communications traffic, but also has better classification effect.
5. Conclusions
This paper firstly analyzes the features of a palm image such as wrinkles, principal ridges, papillary ridges, triangular points and so on. Then, this paper discusses the biological features of palm, presenting an encryption algorithm based on the features of palm. Moreover, this paper gives the feature extraction based on encryption algorithm, as well as the classification and recognition approach of palm image, at the same time, carrying out the simulation test. Finally, the simulation results prove the feasibility and effectiveness of all proposed algorithms or approaches in each stage.
The advantage of the presented encryption algorithm is that its calculation is small and it programming is simple. However, the combination between this algorithm and other feature extraction algorithms for image will need to be discussed in the future. Moreover, to compare with existing classification or recognition approaches, the classification approach based on feature extraction of encryption in this paper has some advantages, such as the faster processing speed, the lower memory capacity and communications traffic, as well as better recognition effect, etc., and its potential application could include fingerprint recognition, iris recognition, medical image classification, etc., lots of biological classification and recognition. However, more wide applications will be urgently studied in the further work.
Table 1. Comprehensive comparison of different classification approaches for palm.
Acknowledgements
This work is supported by Project of Henan Province Science and Technology (No. 142300410247); Key Project of Henan Province Education Department (No: 14A413002, 12A520049, 14A413010); Project funded by China postdoctoral science foundation (No. 2013M531120); Aerospace support fund (No. Chinare 2014-04-07); Project of Zhengzhou Science and Technology (No. 131PPTGG411-4), and fund of ZZULI (No. 2013XJJ013), respectively.
References
- Janarthanam, S., Ramalingam, M. and Narendran, P. (2010) Texture Analysis on Low Resolution Images Using Unsupervised Segmentation Algorithm with Multichannel Local Frequency Analysis. International Conference on Communication and Computational Intelligence (INCOCCI), 4-6 January 2010, 260-265.
- Yue, F., Zuo, W.M. and Zhang, D.P. (2010) Survey of Palmprint Recognition Algorithms. Acta Automatica Sinica, 36, 353-365.
- Shu, W. and Zhang, D. (1998) Automated Personal Identification by Palmprint. Optical Engineering, 37, 2359-2362. http://dx.doi.org/10.1117/1.601756
- You, J., Li, W.X., et al. (2002) Hierarchical Palmprint Identification via Multiple Feature Extraction. Pattern Recognition, 1, 847-859. http://dx.doi.org/10.1016/S0031-3203(01)00100-5
- Xie, X.Z., Wu, J.T. and Jing, M.G. (2013) Fast Two-Stage Segmentation via Non-Local Active Contours in Multiscale Texture Feature Space. Pattern Recognition Letters, 34, 1230-1239. http://dx.doi.org/10.1016/j.patrec.2013.04.016
- Yu, J. (2011) Texture Segmentation Based on FCM Algorithm Combined with GLCM and Space Information. International Conference on Electric Information and Control Engineering, Wuhan, 15-17 April 2011, 4569-4572. http://dx.doi.org/10.1109/ICEICE.2011.5778005
- Long, Z.L. and Younan, N.H. (2013) Multiscale Texture Segmentation via a Contourlet Contextual Hidden Markov Model. Digital Signal Processing, 23, 859-869. http://dx.doi.org/10.1016/j.dsp.2012.11.009
- Jiang, X.B., You, X.E., Yuan, Y. and Gong, M.M. (2012) A Method Using Long Digital Straight Segments for Fingerprint Recognition. Neurocomputing, 77, 28-35. http://dx.doi.org/10.1016/j.neucom.2011.07.018
- Kızrak, A.M. and Özen, F. (2011) A New Median Filter Based Fingerprint Recognition Algorithm. Procedia Computer Science, 3, 859-865. http://dx.doi.org/10.1016/j.procs.2010.12.141
- Caldwell, T. (2013) Tabletop Combines Image Display and Fingerprint Recognition. Biometric Technology Today, 2013, 1, 12-13. http://dx.doi.org/10.1016/S0969-4765(13)70180-2
- Zhang, D., Zuo, W.M. and Yue, F. (2012) A Comparative Study of Palmprint Recognition Algorithms. ACM Computing Surveys, 44, 1-37. http://dx.doi.org/10.1145/2071389.2071391
- Pan, X. and Ruan, Q.Q. (2009) Palmprint Recognition Using Gabor-Based Local Invariant Features. Neurocomputing, 72, 2040-2045. http://dx.doi.org/10.1016/j.neucom.2008.11.019
- Li, W., Zhang, D. and Xu, Z. (2002) Palmprint Identification Based on Fourier Transform. Journal of Software, 13, 95- 97.
NOTES
*Corresponding author.