Paper Menu >>
Journal Menu >>
 Wireless Sensor Network, 2010, 2, 373-380 doi:10.4236/wsn.2010.24049 Published Online May 2010 (http://www.SciRP.org/journal/wsn) Copyright © 2010 SciRes. WSN Research on Beta Trust Model of Wireless Sensor Networks Based on Energy Load Balancing Danwei Chen1, Xizhou Yu1, Xi ang hui Dong2 1College of Computer, Nanjing University of Posts and Telecommunications, Nanjing, China 2ZTE Corporation, Shenzhen, China E-mail: chendw@njupt.edu.cn, iyu xizhou@yahoo.com.cn Received February 27, 2010; revised March 18, 2010; accepted March 19, 2010 Abstract This paper proposed beta trust model based on energy load balancing combines the recent achievements of the trust models in distributed networks, together with the characteristics of wireless sensor networks. The inter-node trust relation is established after an overall evaluation of node trust value based on the monitor results of the node packets forwarding behavior conducted by inter-node collaboration. Due to the node en- ergy limitation in wireless sensor networks, energy load balancing mechanism is applied to prolong the node survival time. And the redundant routing protocol involves the presented trust model to develop the novel trust routing protocol of beta trust model based on energy load balancing. Simulation performance demonstrates that the beta trust model based on energy load balancing outperforms current schemes in energy consumption. Keywords: Wireless Sensor Networks, Beta Trust Model, Trust Routing Protocol, Network Security, Trust Evaluation 1. Introduction There are various attacking threats in Wireless Sensor Networks (WSNs) [1], which can be classified into rout- ing protocol loopholes related attack, such as Sybil attack, false routing information attack, selective forwarding attack, Sinkhole attack, Wormhole attacks and fraudulent confirmation attack; and broadcast authentication loop- holes related attack, such as HELLO flood attack, DOS attack and DDOS attack. Donggan Liu et al. proposed μTESLA [2] and solved the broadcast authentication loopholes related attack in most application scenario. The former type of attack, however, remains an open question for developing a generalized model for common applications. Center-less topology in WSNs determines that the nodes can not be authenticated uniformly by a third party. And the trust management system can be utilized in distributed network, aiming at establishing a trust network participated with trust nodes. Therefore, it is significant to develop a trust management system suitable for WSNs. 2. Basic Requirements for Trust System in WSNs Trust nodes in WSNs shall constitute a trust network which can resist attack from hostile nodes effectively, and save node energy and network bandwidth to ensure network existence time and effectiveness. The designed trust model shall meet the following requirements: 1) Moderate protocol algorithm complexity. The time and space complexity of the protocol algorithm shall meet the process speed and storage space requirements. And digital signature and public key pair system are not suitable for WSNs. 2) Moderate protocol communication. The energy consumption from inter-node communication outgrows that from calculation within the node. 3) Trust evaluation effectiveness. The trust model shall evaluate the node trust value effectively and reflect the dynamic node trust value in time by monitoring the node behavior. Therefore, it is a challenge to reach a moderate balance between 2) and 3) so as to design an applicable trust system in WSNs. 4) Security in WSNs. The designed system shall be able to resist malicious attack, identify attack behavior from hostile node and take effective resisting actions. 3. Trust Evaluation Model Blaze M. [3] firstly introduced the trust management for  D. W. CHEN ET AL. 374 the security in distributed system to solve the restriction using traditional encryption system. The early trust management engines are KeyNote [4] and RT framework [5]. Then trust management-based trust systems are ap- plied in e-commerce, ad hoc network and peer network. The network nodes in the WSNs are task-oriented, and functions as 1) transmitting nodes to collect the desig- nated relevant information and report to the base station, or 2) forwarding nodes to forward data packet from other nodes to the base station. Considering encryption and digests are applied to guarantee the system confidential- ity and integrity, the node trust values are based on the inter-node exchange behavior. Unlike the current trust systems, such as KeyNote, RT framework, eBay [6], CONFIDANT [7] and peer network, our model com- bines the direct and the indirect trust value to give an overall evaluation. We established the trust model based on the node data forwarding statistics and the energy conservation. And the trust value of the routing node is evaluated by 1) the direct trust value from the lower-lever nodes and 2) the indirect trust value from the neighbor nodes. Node trust value is computed through all the evalua- tions from other nodes, which avoids computing the ex- act local trust value and solves the dynamic trust value problem. It enhances the veracity of the trust mechanism and reflects the relativity of trust value and time. And chances are that some reliable nodes with high trust val- ue would take on more forwarding tasks from neighbor nodes, which renders them more vulnerable to be trapped in energy exhaust. Our construction, however, takes this situation into consideration and achieves energy load balancing to prolong the network existence and enhance the effectiveness. 4. Beta Trust Model Based on Energy Load Balancing 4.1. Basic Description The goal of the trust model is to choose credible node for routing information in order to ensure the data to reach the base station safely without losing packets maliciously. The evaluation of overall credibility of nodes in trust model would be involved in direct credibility and rec- ommended credibility comprehensively (namely indirect credibility), where the previous is concluded from direct interaction with evaluated node, while the latter is in- ferred from others nodes to the evaluated node. While selecting next hop node in the consideration of energy load balancing of sensor network, we will take surplus energy ratio as a standard. The trust model is based on the following assumptions: 1) WSNs is safe after ini- tialization and 2) after routing discovery, each node stores multiple routing paths to base station. In the process of research, it needs two important terms derived from trust evaluation areas, namely credi- bility and reputation, where credibility means subjective expectations (usually a real number within 0-1) derived from A to B, and reputation based on the observation of an individual history behavior is an expectation for fu- ture behavior. This paper will also introduce a new term, the node energy surplus ratio, which means a ratio be- tween the node surplus energy and initial total energy. For the sake of discussion, we define the expectation derived from future behaviors of B based on an observa- tion of B history behaviors as direct credibility from A to B. The expectation is based on an observation of history behaviors and evaluation information derived from A to B, so we define such expectation of future behaviors of B deduced from the observation information from C to B achieved by A from C as indirect credibility of A to B, which is based on an observation of history behaviors and evaluation information from C to B. In the stage of data transmission, nodes need to select routing paths, that is to say next hop node. Trust value obtained from the evaluation of trust system will be a basis of selecting routing, and the arbitrary node will try to choose neighbor nodes with high trust value and high energy surplus ratio as routing node. As for neighbor nodes whose trust value is lower than threshold value, the node will submit mistrust reports to base station. If base station receives the same mistrust report from dif- ferent nodes to some node many times, it will exclude the node from routing table, so as to achieve the goal that the network consists of trusted nodes. In the process of routing in WSNs, each node will generate a neighbors list, which stores other nodes iden- tification (ID) within its communication region, mean- while every ID corresponds to credibility. Therefore, every node has a credibility list, which saves the credi- bility of other nodes from this node. The credibility of node can be divided into two parts- direct credibility and indirect part, in which direct credibility is calculated from downstream nodes of routing announcement nodes according to the state of forwarding packets by routing announcement nodes; indirect credibility is deduced from neighbor nodes via monitoring the state of for- warding packets by routing announcement nodes. Com- bining direct credibility with indirect credibility, the total credibility of routing announcement nodes can be calcu- lated so as to judge whether the node is trusted. 4.2. Establ ishme nt an d Calc ulat io n of Node Tr ust Trust value uses to judge whether monitored nodes are malicious; it is also an expectation for future behaviors of monitored nodes and has close relationship with past behaviors of monitored nodes. As an evaluation of past behaviors, reputation can use to calculate current trust Copyright © 2010 SciRes. WSN  D. W. CHEN ET AL.375 value. This paper will adapt reputation model to detect whether to exist malicious nodes. Bayesian can calculate posterior probability via prior probability as shown in Equation (1) j PB means the prior probability, and means the posterior probability. The priori probability is probability accord- ing to random events calculated from past experience. The posterior probability, after random experience, means an amendment for priori probability | j PB A j P B un- der conditions of A resulted from random experience. Therefore, via combination the prior probability with the posterior probability, it can calculate probability of fu- ture possible completed tasks according to situation of past data forwarding completed by node. 1 | |, 1,2,..., | jj jn ii i PB PAB PB Ajn PB PAB (1) where presents a combination of events, which means that a particular detecting node gets a special reputation value and . 1, 2,..., j Bj n 0 j PB A means a specific observed event. In order to reflect dynamic changes of node trust val- ues as time goes by, we need to improve accuracy of node trust evaluation. This paper will adopt a method of sending detected packets regularly to update reputation value. The event that packets forwarded by from i is expressed as j ij t at the time . The behavior that observes the behaviors of from to is expressed as . So it comes to the following for- mula: t ij1tt ij t D 11 1 0 | | ijij ij tt ij t t ijij ij lt l PPD P PPD t l (2) ij t P not only is the probability of an event that completes tasks derived from , but also is the prior probability of reputation derived from to , where this reputation is denoted as j ii j t ij R. We can see that, is not only the posterior probability of node repu- tation at the time , but also the priori probability at the time . ij t R t1t On the assumption that has assigned tasks to for times, has completed tasks for times with the probability i j mnjm x , so the past reputation derived from to is belonged to binomial distribution ij ,Bm xn. The priori probability of next task com- pleted is belonged to homogeneous distribution 0,1U on (0, 1) under no previous knowledge. As for individual monitored node, the monitored node has only two types of behavior: forwarding data or not forwarding data. Therefore, the binomial distribution can be used to model for the monitored nodes. The probability of completing next task by obeys that j 1 0 (0,1)(, ) () [()][()| ()] t ij lij tij l l UBmnx PPD P (3) So the posterior probability of completing next event by will be as follows j 1! 1 !! n m mn xx P mn (4) This paper draws on the experience of beta reputation system of e-commerce, and introduces establishment for node’s trust model, because beta distribution expresses node's reputation. The probability density function of beta distribution can be described as follows 1 1 1 ,Bp |,p1,0 1, q p xxxp q 0, 0qfx q 0 0,q (5) where q 1 ,1,01, q xx dxxp 1 0 1p Bp (6) The beta-family of probability density functions is a continuous family of functions indexed by the two pa- rameters and . The beta distribution p q |, f xpq can be expressed using the gamma function as 1 1 |, p1, 01 , 0, 0 q p pqx x pq xp q fx q (7) with the restriction that the probability variable 0x if 1p , and 1x if 1q . The probability expectation value of the beta distribution is given by p Ex pq (8) Considering the property of gamma function, 1!mm , Equation (4) can be changed into: 21 11 n m mn xx mn P (9) So P is subject to distribution 1, 1mn Copyright © 2010 SciRes. WSN 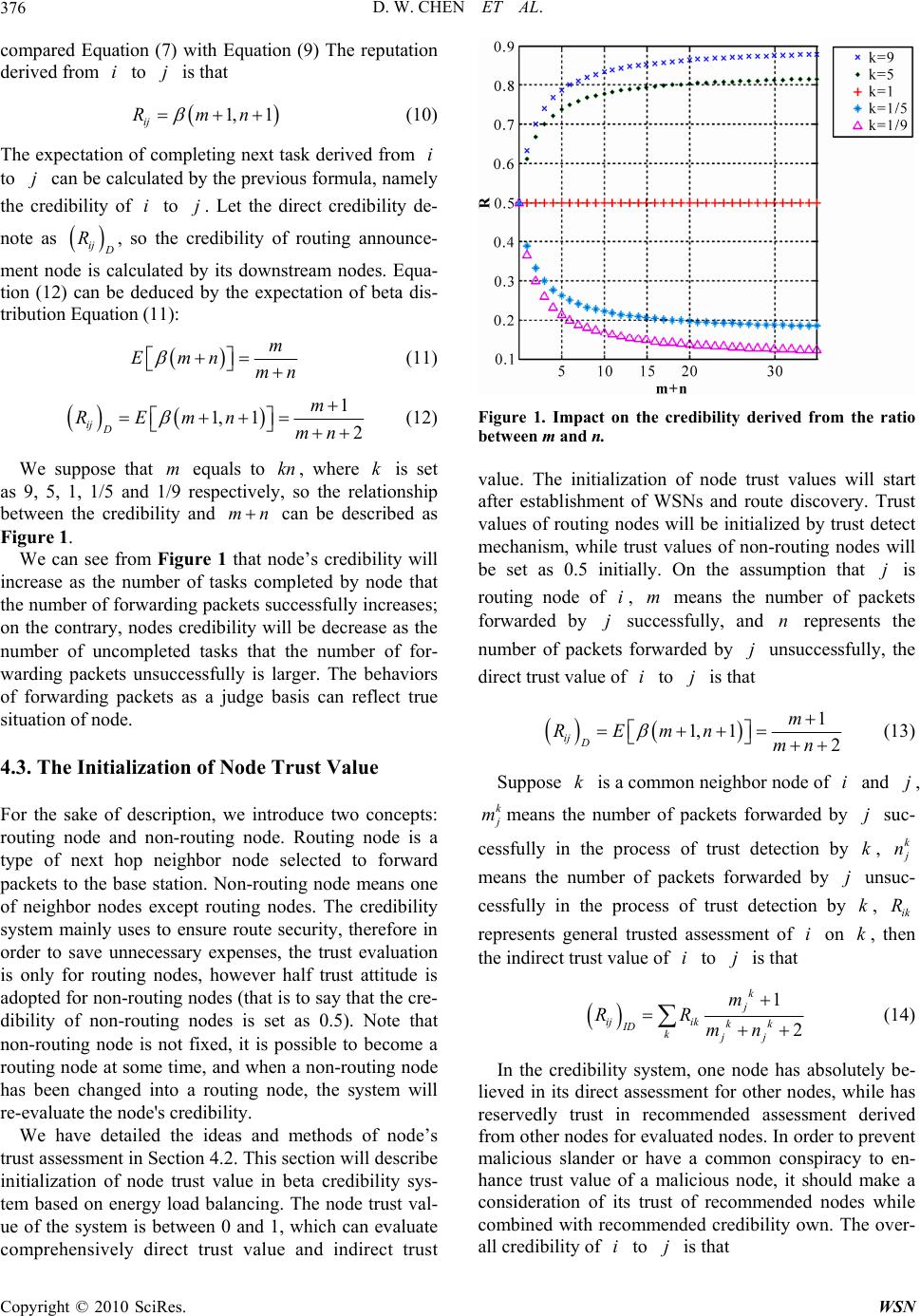 D. W. CHEN ET AL. 376 compared Equation (7) with Equation (9) The reputation derived from to is that i j 1, 1 ij Rmn (10) The expectation of completing next task derived from to can be calculated by the previous formula, namely the credibility of to . Let the direct credibility de- note as i j ij ij D R, so the credibility of routing announce- ment node is calculated by its downstream nodes. Equa- tion (12) can be deduced by the expectation of beta dis- tribution Equation (11): m Emnmn (11) 1 1, 12 ij D m REmn mn m (12) We suppose that equals to kn , where is set as 9, 5, 1, 1/5 and 1/9 respectively, so the relationship between the credibility and can be described as Figure 1. k mn We can see from Figure 1 that node’s credibility will increase as the number of tasks completed by node that the number of forwarding packets successfully increases; on the contrary, nodes credibility will be decrease as the number of uncompleted tasks that the number of for- warding packets unsuccessfully is larger. The behaviors of forwarding packets as a judge basis can reflect true situation of node. 4.3. The Initialization of Node Trust Value For the sake of description, we introduce two concepts: routing node and non-routing node. Routing node is a type of next hop neighbor node selected to forward packets to the base station. Non-routing node means one of neighbor nodes except routing nodes. The credibility system mainly uses to ensure route security, therefore in order to save unnecessary expenses, the trust evaluation is only for routing nodes, however half trust attitude is adopted for non-routing nodes (that is to say that the cre- dibility of non-routing nodes is set as 0.5). Note that non-routing node is not fixed, it is possible to become a routing node at some time, and when a non-routing node has been changed into a routing node, the system will re-evaluate the node's credibility. We have detailed the ideas and methods of node’s trust assessment in Section 4.2. This section will describe initialization of node trust value in beta credibility sys- tem based on energy load balancing. The node trust val- ue of the system is between 0 and 1, which can evaluate comprehensively direct trust value and indirect trust Figure 1. Impact on the credibility derived from the ratio between m and n. value. The initialization of node trust values will start after establishment of WSNs and route discovery. Trust values of routing nodes will be initialized by trust detect mechanism, while trust values of non-routing nodes will be set as 0.5 initially. On the assumption that is routing node of i, means the number of packets forwarded by successfully, and represents the number of packets forwarded by unsuccessfully, the direct trust value of to is that j m i jn j j 1 1, 12 ij D m REmn mn (13) Suppose is a common neighbor node of and , ki j k j mmeans the number of packets forwarded by suc- cessfully in the process of trust detection by , j kk j n ik R means the number of packets forwarded by unsuc- cessfully in the process of trust detection by k, represents general trusted assessment of on , then the indirect trust value of to is that j i k i j 1 2 k j ijik kk ID kjj m RR mn (14) In the credibility system, one node has absolutely be- lieved in its direct assessment for other nodes, while has reservedly trust in recommended assessment derived from other nodes for evaluated nodes. In order to prevent malicious slander or have a common conspiracy to en- hance trust value of a malicious node, it should make a consideration of its trust of recommended nodes while combined with recommended credibility own. The over- all credibility of to is that i j Copyright © 2010 SciRes. WSN  D. W. CHEN ET AL. Copyright © 2010 SciRes. WSN 377 value of to can be updated to Equation (19). ij 0.5, is a non-routing node, 1 2, is a routing node 1 k j ijik kk D ij kjj ik k j m RR Rmn j R (15) In the course of updating credibility system, we not only take reputation accumulated by history behaviors of nodes into account, but also need consider sensitivity of trust changes dynamically, so that it needs to reflect be- havior changes of nodes in order to minimize the impact on network after some nodes being captured. It can be seen from Equation (15) that directly depends on the ratio between and n. The more this ratio is, the higher the trust value of node will be gotten; vice versa. It is in accord with the design of evaluating trust value of node via forwarding packets, and has a finer defensive effect for malicious loss packets of nodes. ij R m4.5. Trust Decision The main objective of the credibility system is to select trust routing nodes and network topology excluding ma- licious nodes to ensure security of data transmission. At the same time, taken limitation of sensor node’s power into account, neighbor nodes will regard the node as a routing node for a long time, and then the node’s power may be run out quickly so that it may lead to partial fail- ure of sensor network. In order to prevent above situation, it need consider energy load balancing. Therefore, trust decision is very important. 4.4. The Update of Node Credibility Value The behavior of node may change as time goes by, so the credibility system must update the trust values of nodes dynamically. The credibility system adopts a method of opening detection mechanism regularly to monitor changes of routing node’s behaviors and update routing node trust value dynamically, so that reflect the changes of the sensor network in time and ensure the security of data transmission, as for non-routing node without updating. We suppose that j E is residual energy rate of , and j r , e mean trust weights and energy weights respectively. The trust decision value, , is defined as ij T ijr ijej TRE (20) Suppose that is a routing node of with and obtained in a new round of trust detection, we define the aging parameters ji m n age as the impact on current trust evaluation derived from past detected data, then We define as the trust threshold of system. When makes a decision to select next hop routing node , it obeys the following decision-making principles: t R i j 1) Select routing node with ; ij t RR newold age mm m (16) 2) If many trust values are all higher than , select one of nodes with the greatest ; t R ij T new old age nn n (17) Therefore the direct trust value of to can be updated that i j3) If many are same, choose one of routing nodes with the highest ; ij T ij R 1 2 new ij Dnew new new m Rmn (18) 4) If many are same, then choose one of routing nodes with the shortest routing path. ij R In the credibility system, when considers historical behaviors of nodes, it should also take sensitivity of up- dating trust values into account and needs reflect the be- havior changes of nodes in time. Therefore, we consider historical behaviors in direct trust while consider current behaviors in indirect trust. On the assumption that , kk After above decision-making, the routing node has higher credibility with more remaining energy. The en- ergy surplus ratio used in system also prevents the use of high-power devices from attacking via using energy de- fects of WSNs. As for one routing node with trust value lower than , it will send a warning report to base sta- tion. If base station recesives the same of warning report from many nodes to a certain node, base station will t R j new jnew mn is derived from monitoring of k on in a new round of trust detection, then the overall trust j 0.5, is a non-routing node, 1 () 2, is a routing node 1 k jnew ij Dnewiknewkk ijnew kjnew jnew iknew k j m RR Rmn j R (19)  D. W. CHEN ET AL. 378 exclude this node from network topology, so that the network consists of trust nodes. 5. Performance Analysis and Simulations of Trust Routing Protocol 5.1. Performance Analysis of TRP and INSENS INSENS (INtrusion-tolerant routing protocol for wireless Sensor NetworkS) is a well-designed secure routing pro- tocol, which achieve data efficient transmission by mak- ing use of redundant routing [9]. In WSNs, it is essential to save energy for the protocol designation; however, INSENS cannot overcome more waste of energy from sending packets multiply. We will introduce beta trust model into INSENS to set up the trust detection mecha- nism, evaluate routing node credibility, and make deci- sion to choose some routing nodes to forward packets. We will analyze security of our protocol based on the beta trust model, called trust routing protocol (TRP) after introduction of trust management model and resist against current different typical attacks in WSNs. In order to ensure packets to be forwarded to base sta- tion safely, the way of sending packets of INSENS is shown in Figure 2 (redundant routing mode). A data packet is copied into a number of ectypes. The transmis- sion path takes on a tree structure in network. Suppose that a certain node with H hops to base station has () routing paths, and each intermediate forwarding node has all routing paths, and then including the number of packets sent by source nodes and intermediate forwarding nodes, the quantity of packets generated by sending a data packet is that N 1NN 1 21 H iH iH H i NN SNNNN (21) Whereas the quantity generated under TRP is that 1SH (22) Figure 2. INSENS: redundant routing protocol mode. As the expansion of network scale, INSENS will make network load increase exponentially, while the consump- tion of TRP for network resource will almost increase linearly. Thus, as long as proper control of communica- tion consumption in the process of trust detection, the communication consumption of TRP is much smaller than INSENS. It can reduce node's energy consumption and save network resources greatly, and be conducive to network expansion. But the computing expense derived from introduction of trust evaluation system relative to communication expense is almost negligible. 5.2. Emulation of TRP and INSENS The main goal of introducing beta trust model into IN- SENS is to give up the way of sending packets multiply via redundant routing path, and to adopt a way of trust routing paths to send packets, which reduces energy con- sumption of nodes and prolongs the survival time of network, meanwhile alleviates network load and saves communication resources. In order to verify TRP described in this paper with an introduction of energy load balancing beta trust model whether satisfy the goal of this paper, this subsection will make simulations for TRP and INSENS, and compare the performance of two protocols according to simula- tions. The weights used in the simulation are set as fol- lows: weight_old = 0.6, weight_trust = 0.8, weigth_en- ergy = 0.2, Rt = 0.6. The paper will adopt two following evaluation indexes to compare and analyze the performance of TRP and INSENS. 1) The number of transmitted packets Under the same conditions of sending the same pack- ets, compare the total quantity of packets sent by all nodes in the course of sending packets from source node to destination node, including packets sent by source node and forwarded by intermediate node. Because the energy consumption of network is mainly embodied in sending packets, this performance index can reflect not only the difference of energy consumption in the process of communication, but also the situation of network re- sources usage. 2) Packet loss It means a ratio of the number of packets not received by destination node to the number of packets sent by source node. This performance index can reflect the im- pact on the protocol to network communication and whether it is applicable to WSNs. The protocol with higher packet loss is not obviously suitable to network communications. This paper also includes simulation of dynamic changes of routing node trust value in order to verify two additional problems: first, the ability of TRP resisting malicious attacks; second, whether the node could dis- Copyright © 2010 SciRes. WSN  D. W. CHEN ET AL.379 cover malicious routing nodes on upstream then exclude them and select trust nodes. According to simulations, we design two following scenarios. Scenario 1: Suppose that there is a coordinate system with base station at (0, 0). 100 nodes are distributed ran- domly within the range of 1000*1000m2 in coordinate system, and node’s communication distance is 250m. INSENS and TRP will generate redundant routing paths. For the sake of simplicity, the simulation will generate two routing paths for each node as possible, however some nodes may have a routing path because of topo- logical structure. The system will select four nodes ran- domly to generate 4 cbr data streams, where each cbr data stream sends two packets per second, the length of one data packet is 512 bytes, and the simulation time is 30 seconds. In trust routing, it can be seen from Figure 1, when the number of packets detected by the system reaches 30, it is more accurate for evaluation of node trust value. Therefore, we select 30 packets sent by trust detection at a time in simulation. In this scenario, it will make a statistics about the number of transmitted packets as shown in Figure 3 and packet loss as shown in Figure 4 in INSENS and TRP respectively. Figure 3 shows that although the number of packets sent by TRP is much more than INSENS in the initial stage, after 12 seconds the later surpassed the former and the gap between the two protocols becomes larger and larger as time goes by. Because TRP starts trust routing detection at the beginning and consume a certain amount of network resources, once completes trust detection, packets are forwarded in accordance with trust routing. However INSENS always forwards packets according to redundant routing. On the assumption that there are h hops between the node and base station, and each node has two routing paths, then the total quantity of transmitted packets reaches about (3 * 2h-2) (2 + 22 + 23 + ... + 2 * 2h). Obviously, according to INSENS, middle nodes may discard duplicated packets, meanwhile be- cause of signal conflict, network congestion and so on, it also drops some packets, and in fact the quantity of a packet transmitted in network may not reach (3 * 2h-2). Figure 2 shows the network consumption of INSENS is much more than that of TRP when sending the same source packets, so the improvement derived from intro- duction of trust evaluation system indeed saves a lot of energy and network resources, extending survival time of WSNs and improving effectiveness of completing tasks. a N It can be seen from Figure 4, the average packet loss of TRP is about 2.5%, which is higher than INSENS, because of WSNs with higher packet loss. In TRP, source packets are forwarded to base station only along a routing path, while in INSENS, source packets are spread over the network via redundant routing paths. There are many copies of packets sent to base station through multiple paths. Thus, INSENS has a slightly 05 10 1520 2530 0 1000 2000 3000 4000 5000 6000 7000 Time (s) The number of transmmited packets TRP INSENS Figure 3. The number of transmitted packets. 05 10 15 20 25 30 0 0.5 1 1.5 2 2.5 3 3.5 4 Time (s) Packet loss (%) TRP INSENS Figure 4. Packet loss. lower packet loss. However, as expansion of network scale and frequency of sending packets raises, the con- sumption of INSENS for network resources will increase exponentially, also it will result in more serious network congestion and channel conflict, and its packet loss will increase greatly. Whereas the consumption of TRP for network resources under above mentioned situation will almost increase linearly, it is much better than INSENS in terms of network congestion and channel conflict. Scenario 2: Suppose that there is a coordinate system with base station at (0, 0). 100 nodes are distributed ran- domly within the range of 1000*1000m2 in coordinate system, and node’s communication distance is 250m. The interval time of trust update is 30 seconds, and si- mulation time is 60 seconds. In TRP, base station gener- ates three routing paths for , of which the next hop nodes are , V N A N B N and . In the initial stage, , C NA N B N and are all healthy nodes, while C N B N will be captured within 0 ~ 30 seconds, which will discard all packets without forwarding. In this simulation scenario, trust values of to , V NA N B N and can be shown in Figure 5. C N Copyright © 2010 SciRes. WSN 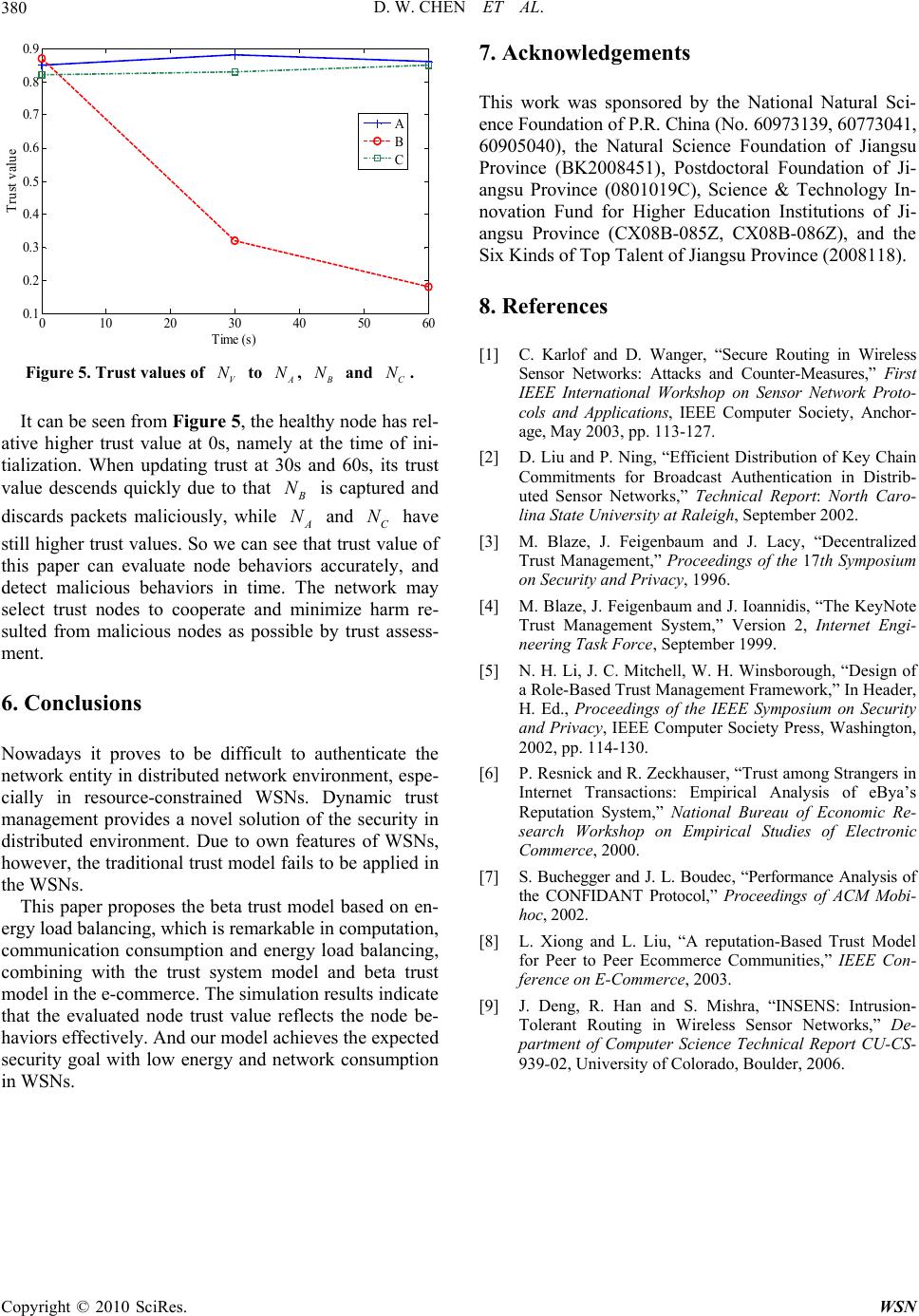 D. W. CHEN ET AL. Copyright © 2010 SciRes. WSN 380 7. Acknowledgements 010 20 30 40 50 60 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 Time (s) Trust value A B C This work was sponsored by the National Natural Sci- ence Foundation of P.R. China (No. 60973139, 60773041, 60905040), the Natural Science Foundation of Jiangsu Province (BK2008451), Postdoctoral Foundation of Ji- angsu Province (0801019C), Science & Technology In- novation Fund for Higher Education Institutions of Ji- angsu Province (CX08B-085Z, CX08B-086Z), and the Six Kinds of Top Talent of Jiangsu Province (2008118). 8. References [1] C. Karlof and D. Wanger, “Secure Routing in Wireless Sensor Networks: Attacks and Counter-Measures,” First IEEE International Workshop on Sensor Network Proto- cols and Applications, IEEE Computer Society, Anchor- age, May 2003, pp. 113-127. Figure 5. Trust values of V N to A N , B N and C N . It can be seen from Figure 5, the healthy node has rel- ative higher trust value at 0s, namely at the time of ini- tialization. When updating trust at 30s and 60s, its trust value descends quickly due to that B N A N is captured and discards packets maliciously, while and have still higher trust values. So we can see that trust value of this paper can evaluate node behaviors accurately, and detect malicious behaviors in time. The network may select trust nodes to cooperate and minimize harm re- sulted from malicious nodes as possible by trust assess- ment. C N [2] D. Liu and P. Ning, “Efficient Distribution of Key Chain Commitments for Broadcast Authentication in Distrib- uted Sensor Networks,” Technical Report: North Caro- lina State University at Raleigh, September 2002. [3] M. Blaze, J. Feigenbaum and J. Lacy, “Decentralized Trust Management,” Proceedings of the 17th Symposium on Security and Privacy, 1996. [4] M. Blaze, J. Feigenbaum and J. Ioannidis, “The KeyNote Trust Management System,” Version 2, Internet Engi- neering Task Force, September 1999. [5] N. H. Li, J. C. Mitchell, W. H. Winsborough, “Design of a Role-Based Trust Management Framework,” In Header, H. Ed., Proceedings of the IEEE Symposium on Security and Privacy, IEEE Computer Society Press, Washington, 2002, pp. 114-130. 6. Conclusions Nowadays it proves to be difficult to authenticate the network entity in distributed network environment, espe- cially in resource-constrained WSNs. Dynamic trust management provides a novel solution of the security in distributed environment. Due to own features of WSNs, however, the traditional trust model fails to be applied in the WSNs. [6] P. Resnick and R. Zeckhauser, “Trust among Strangers in Internet Transactions: Empirical Analysis of eBya’s Reputation System,” National Bureau of Economic Re- search Workshop on Empirical Studies of Electronic Commerce, 2000. [7] S. Buchegger and J. L. Boudec, “Performance Analysis of the CONFIDANT Protocol,” Proceedings of ACM Mobi- hoc, 2002. This paper proposes the beta trust model based on en- ergy load balancing, which is remarkable in computation, communication consumption and energy load balancing, combining with the trust system model and beta trust model in the e-commerce. The simulation results indicate that the evaluated node trust value reflects the node be- haviors effectively. And our model achieves the expected security goal with low energy and network consumption in WSNs. [8] L. Xiong and L. Liu, “A reputation-Based Trust Model for Peer to Peer Ecommerce Communities,” IEEE Con- ference on E-Commerce, 2003. [9] J. Deng, R. Han and S. Mishra, “INSENS: Intrusion- Tolerant Routing in Wireless Sensor Networks,” De- partment of Computer Science Technical Report CU-CS- 939-02, University of Colorado, Boulder, 2006. |

