Journal of Service Science and Management
Vol.6 No.1(2013), Article ID:29196,16 pages DOI:10.4236/jssm.2013.61013
From Theory to Practice—When and How to Implement Service Value Agreement
![]()
1Department of Computer and System Sciences, Stockholm University, Stockholm, Sweden; 2Department of Consulting and System Integration—Application Management, Tieto, Stockholm, Sweden.
Email: merat.ziyarazavi@tieto.com, seye-ziy@fc.dsv.su.se, cmagnus@dsv.su.se
Received November 19th, 2012; revised December 21st, 2012; accepted January 5th, 2013
Keywords: IT Outsourcing; Application Management; Service Value Agreement; Service Level Agreement; Value Co-Creation; Outsourcing Lifecycle
ABSTRACT
Traditionally, a Service Level Agreement (SLA) is used as an appendix in IT Service Management agreements to set expectations and delineate the service delivery description as well as the terms and conditions of delivery. However, SLAs are unable to imply and guarantee the added values expected by the customer. Service Value Agreement (SVA) is a newly developed framework that identifies the deliverable added values along with metrics to measure the quality and quantity of achievements in terms of business added values. The objective of this study is to expand the concept of SVA for Application Management (AM) services and suggest guidelines for its implementation in real business cases. This goal is fulfilled through the case study approach and outsourcing industry contributions. Authors suggest discussing the concept of SVA from early stages of the sales lifecycle and implementing it gradually during the steady state phase. Combination of Service Value Mapping approach and Piloting method is suggested for SVA proposition as an option with successful practical history.
1. Introduction
Information Technology Outsourcing (ITO) has many significant practitioners as well as much academia attention [1]. By expanding Global Delivery Model (GDM) strategy, organizations enthusiastically outsource the whole or parts of IT-based business processes to service provider firms [2]. Nowadays, GDM is motivated by a combination of internal and external factors. Environmental demands lead by cost cutting [3-5], focusing on core business processes by outsourcing non-core IT services and getting access to “best of breed” capabilities [3-6], and delivering higher quality services with better reaction to the end/user demands [7] are some examples of internal and external factors. These are considered as internal issues since they improve operational efficiencies by leveraging best practices by specialized service providers. On the other hand, they are assumed as external factors as they make the firm more competitive in the marketplace.
Traditionally, service providers leverage Service Level Agreement (SLA), at the heart of service management [8], in order to ensure service delivery as it is planned and according to the defined internal and external factors. An adequate SLA, as a formal written agreement between service provider and customer, is assumed a success factor in IT outsourcing assignments and service provider-customer relationship [9,10]. SLA, which mostly includes technical metrics, defines service delivery description, delineates boundaries, and lays down the parties’ expectations [11]. However, SLA does not evaluate business added values. Moreover, achieving the above mentioned external and internal factors cannot be appropriately addressed and assessed by means of SLA. Service Value Agreement (SVA), for the first time, is introduced by [12] to fill this gap. SVA is a framework for IT service offerings based on added values. As [12] defined, SVA reinforces traditional SLAs and fulfills those SLAs’ shortages by identifying IT service delivering added values along with their measurable metrics. It is very critical to understand that SVA differs from SLA in that the former keeps track of business values where the latter indicates service level target.
We have found no documented examples of SVA implementation either in academic literature or in other sources such as industry analysis. The main objective of this study, which is follow up research on our previous paper [12], is to explore SVA in practice by means of a case study and provide guidelines to put the first steps towards implementation of newly developed SVA by [12]. At the end of this study, recommendation remarks regarding “When” and “How” SVA should be offered are suggested. Besides, to make previously introduced SVA more comprehensive, seven new added values along with their measurement metrics with a specific focus on Application Management (AM) Operate services are introduced.
1.1. Research Environment
The empirical nature of this study required a practical environment in which the study could be conducted and the possibility for implementation and validation of results would exist. For this purpose Tieto as an IT outsourcing and consulting environment compatible with the nature of this research was chosen. Tieto is one of the largest IT service companies in Northern Europe providing IT outsourcing, consulting and product engineering services. Tieto aims to become a leading service integrator creating the best service experience in IT. The company’s customers are from different sectors such as automotive, financial services, telecom & media, healthcare & welfare, forest, energy, manufacturing, retail & logistics, and the public sector. Tieto is considered a serious competitor to global service providers such as IBM, Infosys, and Accenture.
1.2. Research Plan
Being in such an aggressive market makes Tieto put extra effort into research and development projects to gain competitive advantages. Gaining customer satisfaction can be the most powerful competitive advantage and this would not be achievable unless customers conceive high levels of value and business efficiency out of their relationship with the IT service provider. Absorbing more satisfaction and, consequently, more customers would be enough to motivate Tieto to go forward to better understand their customers’ values, a way to quantify them and accordingly implementing SVA in a live customer case. Therefore, the following questions are investigated: 1) how is it possible to expand SVA with specific focus on AM Operate services; 2) “When” and “How” SVA can be proposed and implemented?
The remainder of the paper starts with presenting a review of previous studies related to the areas covered in this paper (Chapter 2). After that, we describe the research methodology, data collection as well as validation methods used in this study (Chapter 3). This is followed by the results of the findings including the suggestions for expanding SVA as well as its implementation in the live environment (Chapters 4 and 5).
2. Previous Research
As mentioned, the objective of this research is to test SVA in practice and suggest a set of guidelines for further implementation of SVA. This includes understanding the evolved market demands from IT service provider firms and IT outsourcing lifecycle. Besides, value co-creation approach has been investigated since it is used as a method for implementing SVA by the authors. Obviously, a background on “what SVA is” and “why SVA is developed” should be in place.
2.1. Evolving Market Demands
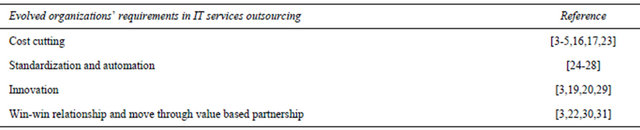
Outsourcing services as well as human resources had been a trend especially among companies with “poor financial performance” during 90s [4,13,14]. This made outsourcing as one of the top ten survival solutions in that particular period of time [15]. Since 1990, where offshoring in today’s context was a newborn concept, till this instant, delivering cheaper services to the customers by relying on low-priced labor has been the main inspiration for sending IT business processes abroad [4,5,16,17]. Increasing productivity, in second place, has been also emphasized as a primarily driver of outsourcing [7].
As time has gone on, other factors have come into account for keeping a company competitive in the Global Delivery (GD) market. Along with cost cutting, quality is another major global sourcing driver making a provider prominent among competitors [7-18]. From 2002 afterwards, customers have been looking for business models and organizational solutions rather than technical competences [19]. Nowadays, providing fast IT system with huge capacity is not a big deal anymore; instead, reengineering business processes and roles are at the center of attention [19]. Innovation as an effective factor on service quality increases the productivity and even creates competitive advantages for the provider [19]. Innovation is assumed as a revolution in computing area and plays a vital role in delivering better services so that, as [20] stated, computer technology and IT industry have gone through huge changes by means of innovation and standardization.
Along with evolution trend of global sourcing practices companies are following evolutionary track in strategies [18-21]. The studies conducted by [3-22] are two out of several researches that investigate this track with a focus on the same stream. As [22] describes, this trend begun from pure cost reduction strategy to value based partnership strategy. Reference [3] believes during the time, sourcing strategies moved away from win-lose relationship to long-standing relationship based on mutual trust and “win-win” partnership.
To make a long story short, we summarized the top four evolved customers’ requirements in Table 1. The information illustrated in Table 1 is resulted from reviewing vast amount of literatures in IT outsourcing and offshoring era.
Table 1. Top four organizations’ demands from IT services outsourcing.
2.2. SLA Shortcomings
From a business point of view, “What to measure” and “How to measure” are well-known dilemmas in IT outsourcing assignments. Regarding this, Aubert et al. (2003) cited in [25] state “less measurability in the outsourced activities leads to less complete contracts and, as a consequence, to less successful outsourcing”. Poppo and Zenger (2002) cited in [25] illustrate that managers show lower levels of satisfaction with the effects of IT services outsourcing on cost performance when the performance is not easily measurable. As mentioned earlier, an SLA includes service metrics that measure different criteria based on performance levels so that “good” service can be differentiated from typical “bad” service [11]. The importance and critical role of an SLA is inevitable, however several researchers have highlighted some practical defects of SLAs (e.g. [8,9]; Kern et al. 2002 cited in [9]) that hereafter are briefly described.
Firstly, most SLAs focus on specifying the amount of efforts that are to be spent on a certain task or process rather than specifying the results that are admirable for customers in terms of effectiveness of the service and business objectives [8]. For instance, usually it is stated that “in case of any fault in system X, the service provider is supposed to solve it in a certain amount of time”. However, it does not consider the customer’s business objectives thoroughly.
Secondly, service specifications are usually stated in terms of metrics that are unclear or impossible to be measured [8]. Effective metrics focus on two main domains namely: “point in time” and “trending analysis” [32]. In order to clarify this factor, service availability is taken as an example. Availability of services is always evaluated by a metric called availability percentage and it is difficult to determine its exact meaning in the context of business values. For instance, what does the following statement, which is a very common service level, exactly mean: “The availability percentage of the network should be 98%”? This service level brings up several questions: what is the difference between 98% of availability and 99%; what if the service is available on a weekend when nobody uses it and unavailable at a peak time such as a Monday morning; does 98% of availability bring business value to the customer?
Thirdly, since it is difficult to measure and describe the business consequences of failures in delivering specific services, some service specifications in SLAs are incomplete [8]. For instance, how it is possible to make a complete agreement on security control or disaster control services when there is no clue about quantifying the business consequences of for example fraud or loss of availability?
Fourthly, an SLA is a very technical document with deep focus on terminologies that are understandable for the specialists but not for senior managers, line managers, and end-users that also need to have a clear understanding of them. This problem makes SLA specification as “just an unsatisfying tradition” [8].
Last but not least, as Kern et al. (2002) cited in [9], apart from metric-oriented and technical issues that are not fully supported by SLA, there are some intangible benefits that can be delivered but have been ignored by SLAs. Effective provider-customer relationship and governance-oriented concerns like communication mechanisms, joint decision-making processes, partnership, mutual trust, and the “feeling” that a provider gives to a customer are examples of such intangible benefits. Respectively, the numeric metrics seem essential in agreements though the real problems and dissatisfactions mostly depend on intangible values.
2.3. Reinforce Traditional SLA with SVA
“You can’t manage what you don’t measure”, “you can’t improve what you don’t measure”, and “you probably don’t care to what you don’t measure”; these are three old axioms and key messages among senior managers and business analysts [33]. However, from IT services added value point of view, as [12] stated, in order to measure the added value delivered by IT services the concept of “value” should be clarified beforehand and a unanimous understanding on “what constitutes value?” is needed.
As [12] defines, Service Value Agreements is a reinforcement of traditional SLA and the main idea is to improve service delivery and help customers to conceive the business effects of delivered IT services. It is very critical to understand that SVA differs from SLA so that the former keeps track of business values where the latter indicates service level targets. SLA neither implies nor guarantees the added values which are expected by customers. SVA including predefined added values along with their correspondent measurable metrics answer the questions “What are the added values desired by customers that should be delivered by provider firm”; and “how and to what extend should added values be delivered?”
By means of SVA the focus from details of SLAs is reduced; rather value delivery at business level is to be considered. It is important to know that SVA is “collectively exhaustive” and “mutually exclusive” meaning that, on one hand, it includes the values and measurement indexes which are under the control of management and, on the other hand, no two indexes overlap one another [12].
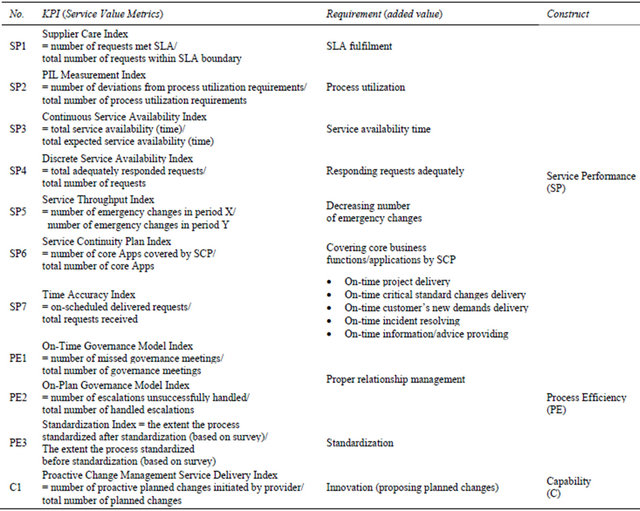
As it is introduced by [12] and is shown in Table 2, SVA includes eleven added values coming together with their correspondent metrics. The added values are categorized in three cornerstones based on their nature and purpose of development; service performance, process efficiency, and capability.
2.4. Value Co-Creation Approach—Customer Role as a Co-Creator
Nowadays, due to the nature of contracts, the dynamics of the IT service delivery have moved away from individually value creation mode to value “co-creation” and “co-production” mode [34]. Traditionally each party focused on its own contractual obligations while this trend has changed to co-creation of value; meaning that the service provider do not produce value individually rather the added value is created as the result of collaboration. From systematic point of view, service systems always involve two parties working together in order to co-create value through complicated value chains namely: client and provider. The former orders information goods or material goods which are their own properties and the latter grant capabilities for the benefit of client (Hill 1977 and Gadrey 2002 presented by [19-23]). More precisely,
Table 2. Service value agreement—added values and metrics (Adopted from [12]).
each value chain within a service system includes technology, people, shared information such as language and even other internal or external service systems that are configured dynamically. But the key point is close interaction of client and service provider which leads to value co-creation [23]. Moreover, value co-creation is the main aim of each service systems and it assures the health of service system.
Correspondingly, [35] argue that the market is being shifted from “goods-dominant” oriented to “service-dominant” oriented and, consequently, the role of customers is being changed from an isolated and passive one to being active and connected to the service provider. As such, customers demonstrate the value on the basis of “value-in-use” (S-D logic) and co-creation of value while service providers measure values on the basis of “exchange-value” and goods-dominant logic (G-D logic).
In order to clarify the demarcation line between S-D logic and G-D logic referring to value-in-use and value-in-exchange respectively, we can consider a computer as an example. A manufacturing firm assembles a computer out of series of raw material including metal, plastic, etc. These substances cannot execute a sequence of logical and arithmetic operations in their raw form while, based on G-D logic, the production process of manufacturing firm creates value by delivering a computer. In other words, the manufacturing firm creates value in form of a good by transforming the raw material into computer which is in demand. On the other hand, the alternative perspective, S-D logic, describes the roles of producer and customer in value creation jointly so that the computer acts as an intermediary element [35] and gives input into the value creation chain. The computer does not provide any value if no one knows how to use it as a computational and arithmetical tool. It is the customer (end user) who co-creates the value by using the computer. As a result, inherently value is co-created by more than one service system and “reciprocal and mutually beneficial relationship” should be always under consideration [36]. Table 3 compares roles of customer and provider from G-D as well as S-D logics in brief.
By reminding the example of computer that is explained above, from organizational perspective, the IT value-in-use is co-created in cooperation with service provider firm. Based on primary organizational objectives the co-created value can be varied. However, the main target will be always measuring the conceived business values which are followed by financial features.
2.5. IT Outsourcing Lifecycle
Evolving market demands together with environmental pressures including external and internal factors are named as motivations for outsourcing IT services. Regardless the organizational strategy, during the outsourcing assignments, organizations have to enter to a new world, experience new types of engagements and try to catch a win-win situation in which both parties gain benefit [12]. In other words, the organization enters IT outsourcing lifecycle [1]. As it is conceived from practical experiments, the IT outsourcing lifecycle is divided into two main segments, pre-sales lifecycle and delivery lifecycle, each of which includes several milestones.
In this section these two main steps in IT outsourcing assignments are briefly described and the milestones are elucidated. It is worth mentioning that, as [37] also highlighted, much prior research in IT outsourcing field, has focused on sourcing strategies and just few academic works have addressed post-contract as well as pre-contract phases in detail. Therefore, the authors get use of practitioners’ experiences, ITIL books, and white papers to a wide extent in order to tackle the necessary detailed information.
2.5.1. Pre-Sales Lifecycle
As soon as an organization, as a potential future customer, sends out Request for Information (RFI) followed by Request for Proposal (RFP) to selected number of provider firms, the pre-sales teams are constructed within service providers and they officially come into action. The cycle is started by value proposition and ended by signing the contract. In between, based on customers and providers condition, there might be several other phases in between than is explained here. However, “due diligence and negotiation” is an inventible phase that parties need to go through.
a) Value Proposition
Value proposition is a proper analysis of value exchange in the service system and configuration of resources, i.e. people, technology and information, connected to other systems [35-36]. Nowadays, “customer value proposition” is one of the most in use terms in
Table 3. G-D logic vs S-D logic on value creation (Adopted from [36]).

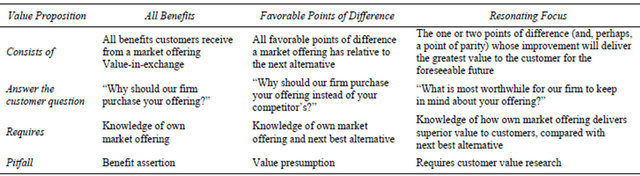
business markets especially in IT outsourcing sector [38]. As these authors have mentioned, a service may offer a superior value but if the service provider does not demonstrate it in a proper way, the customer will probably misunderstood it as a faint marketing slogan. In order to avoid these situations and stress the points that deliver relatively great value to the customer, the service provider needs to have in deep understanding about the customer’s business, weak areas, objectives, and requirements. However, despite the wide use of this term in the growing IT outsourcing trend, both service providers and customers try to find out whether the delivered benefits outweigh the costs and risks [39]. As Anderson and his colleagues have classified, term “value proposition” is used in three different ways namely:
• All benefits;
• Favorable points of difference;
• Resonating focus.
Most managers usually indicate all benefits that customer can receive out of a specific service, when asked for value proposition. They even may demonstrate the simple features of the service which deliver no value to the customer. In the second category, favorable point of difference, the service provider is aware of the alternative option that the customer has and tries to phrase its main competitive advantages. Though it needs a detailed knowledge of the customer’s business, their preferences, and as well as the competitor capabilities. In the third type of value proposition the provider has to choose one or two upmost point(s) of differences (and, perhaps, a point of parity) by which the most value is delivered to the customer. Table 4 briefly explains the value proposition alternatives and their pitfalls.
b) Due Diligence and Negotiation
It is in the due diligence and negotiation phase that customers make the last attempts to provide selected provider firms with a clear view of their real needs. Similarly, providers try to design the best solution by eliminating the assumptions and getting a better understanding on customer’s business values. Usually due diligence and negotiation are considered as two separate phases in pre-sales lifecycle [40,41]. However, the activities that need to be taken care are intertwined and overlapping enough to keep them under the same umbrella and to consider them as a single phase in IT outsourcing [37- 42].
Accenture, a globally leading IT service provider firm, calls due diligence a key activity; “the benefits of a focused, yet thorough due diligence effort is vital in helping companies understand what they are buying—and in creating the right strategies to obtain the desired value from a merger or acquisition” [40, p. 6]. Deloitte, one of the four big professional service firms providing consulting services, confirms the citation from Accenture and highlights due diligence as a mandatory step in IT outsourcing which enable organizations to achieve synergy, cost saving along with strategy enablement. Without due diligence, definite risks—such as noncompliant contract and out of time and budget service delivery—are not probably identified [43]. In other words, due diligence activity is a fundamental step in executing effective risk management including operational, people, financial, business, and delivery eras [40-43]. In another place, Deloitte introduces due diligence as the process of ensuring the information is accurate in all material respects and the documents do not contain an untrue or unrealistic statement of a material fact or omit to state a material fact required to be stated in the documents [41, p. 28]. Academic, in aligning with practical references and business reports, praise the importance of due diligence in IT outsourcing lifecycle and indicate clarifying “RFP baseline claim” at the heart and main stream of due diligence process [37].
On other hand, negotiation phase, which is occasionally interpreted as “war, battle, and blood bath” [37], is conducted after or simultaneous with due diligence and aimed at contract signing. As it is noticed practically and Lacity and Willcocks [37] also listed, there are several concerns in negotiation agenda such as negotiating SLA, responsibility matrix, sourcing strategy, price, benchmarking methods, and employee transfer. However, these concerns can be followed up at different detail levels
Table 4. Value proposition alternatives [38].
according to the customers’ requirements and complexity of the assignment.
c) Contract Signing
As it is conceived from the name, in this phase parties sign the contract by which the customer-provider relationship is turned into a legal agreement including pages “terms and conditions”. Obviously, the prior phases, value proposition as well as due diligence and negotiation, provide the main inputs for this phase. In other words, details of contract are negotiated and settled during the previous phases. Provider’s solutions along with parties’ expectations from the several-years partnership, which have been negotiated and agreed in previous phases, are manipulated by legal statements and construct the details of contract [37]. So prior to contract signing both parties need to gain same understanding regarding two questions: are data and information with measurable metrics are available; are the parties able to set metrics that are clear enough to help managing the outsourcing relationship?
To put all these in ITIL-based terms, ITIL Service Operation [44] introduce Contract Management as the commercial and legal aspect of IT outsourcing and underline security services, telecommunication facilities, leased properties management, and environmental equipment maintenance as its components.
2.5.2. Delivery Lifecycle
As the customer and chosen provider sign the contract, the mutual collaboration for delivering added values to the customer’s business by IT services will start. Based on project scope and the extent of complexity, different steps might be considered by parties in order to complete the delivery lifecycle. However, transition and steady state phases should always be in place to be able to deliver any service [37]. In practice, sometimes the importance and criticality of transition phase motivates providers to go one step further and divide it into two separate phases, transition and transformation [45].
Onsite as well as offshore organizational structure along with knowledge retention and knowledge transfer methodologies are planned jointly by the service provider and customer during the transition and steady state phases [37]. In other words, the questions “who knows what” and “who does what” are answered throughout these two phases [37].
a) Transition and Transformation (T&T)
Perhaps service transition, where responsibility of phased out services [24, p. 77] is transferred from internal customer’s IT department or a 3rd party to the newly chosen service provider firm, is the most critical phase in outsourcing lifecycle. To be clearer, Service transition together with Service Design and Service Operation are progressive phases of service lifecycle by which change and transformation is represented [24]. Existence of a complete book in ITIL version 3 just for describing service transition, its processes, and involved roles and responsibilities, shows the gravity of the issue. It is in this phase that the knowledge is transferred to the onsite team in provider firm and will be expanded to the offshore team at the later stages [37]. As [24] states, “service transition processes ensure design improvements are directed into Service Operation while minimizing costs and risks.” In this phase the service portfolio of customer gradually moves from “as is” mode to “to be” mode.
Transition projects usually last between six to eighteen months based on the size and complexity of the outsourcing assignment. During this period, several activities are on the agenda to develop and improve the required capabilities in order to be able to transition the services into operation [26, p. 9] and establish operational performance [37]. For this purpose [37] highlight five activities:
• Popularize the contract (Interpret the contract and distribute it to the IT users)
• Launch post-contract management process including centralized team establishment and contract monitoring
• Consolidation and standardization along with rationalization
• Managing new requirements beyond baseline includeing new services
• Set realistic expectations based on provider performance Accordingly, practical resources such as white papers and [46] highlights other activities (e.g. staff transfer) and make this agenda longer with more detailed steps and activities. However, the main stream is compatible with what is listed above.
b) Steady State
Once the operational performance is established in transition and transformation phase, service provider and customer will focus on expanding their relationship on more value-added areas [37]. “Vendor Development” as one out of nine IT capabilities that are listed for IT service providers by [47], specifically focuses on delivering value-added to the customer’s business. As customers conceive the operational objectives of IT contract during the transition phase, they gradually expect more innovations and opportunities for revenue generation [37]. For this purpose, in the Steady State phase, both offshore and onsite teams provide supportive actions for customer’s systems, services, and application development requirements [37].
Practically, the real service delivery and maintenance support is gradually provided during steady state as the responsibility is transitioned from the current supplier to the new supplier. Therefore, transformation and steady state would be parallel at some points of time [48]. In other words, as service organization is prepared during the transition phase, the implementation of steady state processes is started [45].
3. Research Methodology
The objective of this article, which is extracted from a project conducted in cooperation with Tieto, is to provide guidelines for the first steps towards implementation of SVA. Due to the importance of AM services in supporting organizations’ businesses as well as ever increasing demand for these services, authors have been convinced to concentrate on expanding SVA aligned with AM services.
This study is a collaborative practice in which “emphasis is put on relating research activities to practice and on establishing fruitful collaboration between group of researchers and practitioners” [48]. Throughout this research, the authors obtain the best-of-breed by utilizing the combination of “reflective practitioners” [49], literature review, and experiences.
Accordingly, case study research method, based on definition proposed by [50], is chosen as the research methodology in order to conduct reliable research with validated results for further practical usage. As [50] defined, case study scrutinizes “a phenomenon in its natural setting, employing multiple methods of data collection to gather information from one or few entities (People, Groups or Organization).” This definition is completely compatible with the research environment and the resources that the authors have get access for data collection and analyzing purposes. The research is conducted in Tieto, a multinational IT consulting and outsourcing firm. The interaction with the firm involves senior managers, their reports, internal documentations and, of utmost important, one of Tieto’s customers. Organization X which is currently one of the Tieto’s customers and recently, summer 2012, has sent out a Request for Proposal (RFP) for complete IT service outsourcing is chosen as the case study. This specific customer is selected because new generation of requirements in IT services outsourcing assignments are demanded which have not been required previously by other customers. These requirements inspire the concept of SVA and, as a resultthe customer is considered as the most appropriate case to propose SVA and evaluate its implementation consequences in practice through service delivery lifecycle. The research process from general perspective is elucidated in Table 5.
Based on recommendations from case study methodology scholars (e.g. [51-53]), the subsequent case study research procedure, including six steps, has been followed. Table 6 summarized the case study research process and how they have been addressed.
4. Service Value Agreement Expansion
4.1. Background on the Case Study
Customer X is one of the market leaders in the Retail and Logistics sector in Europe. This company is working in a business environment that is rapidly changing and the competition is increasingly tough. Costumer X’s offering is based on the needs and core business processes of its customers. They help their customers to sell and market their products and services as well as manage customer contacts, deliver the products and manage supply chain, and invoice and run their financial transactions. All these processes are very ICT intensive and hence Customer X needs to continuously sharpen the focus on how to use IT as an enabler to serve its customers better.
This organization is working both in Business-toBusiness and Business-to-Customer business. In both areas the digitalization of the service chain is one key element to get satisfied customers. The mission of Customer X lies in smart use of IT enabling them to create digital multichannel customer services, create digital infrastructure platform for digital services, and reduce the fixed costs of the commodity IT.
The main challenges and problems of Customer X, as understood by the pre-sales team from what has been explained in the RFP, are: fragmented IT sourcing; fragmented IT operating model and IT governance; high IT spend; large number of small sub-contractors; inability to control the fixed costs; and large number of applications with lots of redundancy and overlaps.
Based on this short background which is extracted and interpreted from Customer X’s requirements defined in the proposed RFP, the main objectives of Customer X
Table 5. Research process.

Table 6. Case study research process.

are divided into four main value groups as follows:
• Primary business value which is significant cost reduction in IT expenses;
• Business process values including faster time-tomarket, higher business performance and process efficiency, and gaining competitive edge;
• IT values including consolidated IT, quality and reliability of IT services, business-IT integration, concrete governance model, centralized IT management, and digitalization;
• Customer values including be flexible and agile in new requirements identification, and continuous service improvement.
4.2. SVA Extension
As it is developed by [12], added values defined in SVA are divided into two main categories namely: generic added values and customized added values. The former are a group of high level added values that can be utilized in any AM service in aligning with organizations’ business objectives where the latter includes identified added values for Change Management service which is one of widely used AM Operate services.
In order to fulfill evolved customers’ requirements and also enrich the previously developed SVA [12] with more customized added values, two services have been considered by the authors (Availability Management, and Configuration Management services). These two services support customers’ businesses continuity by maintaining customers’ operations on daily basis. Therefore, they are assumed among utmost important AM Operate services demanded by large number of organizations.
It should be notified that ITIL Service Design mainly defines the practical guidelines for AM Operate services and there have been very little academic research conducted on ITIL and its ingredients [54,55]. Therefore, these services along with their added values and measurement metrics are described and indentified mostly based on ITIL Service Design definitions. The authors conceive the ITIL collection as a reliable source of information since they, as a framework including best practices, intended to guide practitioners to deliver high quality IT services. Besides, ITIL proposes vast amount of managerial as well as operational procedures to facilitate qualityand monetary-based values from IT services [56].
4.2.1. Availability Management Service
The purpose of Availability Management is to provide a point of focus for all availability-related issues, regarding both services and resources, ensuring that availability targets in all areas are measured and conceived [39]. By understanding the relationships of the service delivery components and defining a system model [57], Availability Management service ensures the agreed level of availability is provided. For this purpose, the operational position of service components, their level of importance, as well as monitoring and measuring of IT availability are considered as key activities [39]. As ITIL defines, this service by its reactive and proactive activities, continually tries to ensure all operational services meet the availability objectives. Besides, the new or changed services are designed in a way to meet the targets without affecting the performance of running services. Therefore, it is needed to outline the business process requirements, identify the critical IT systems and services, and monitor and measure the availability of components [39-58].
a) Availability Based on Reliability and Maintainability
In simple words, availability is the time when a service or system is operational and availability management is monitoring and measuring the availability trend and keeping the factors with negative impacts under control. As [56] mentioned and availability management concept from ITIL Service Design approves, reliability and maintainability are two components of availability. Reference [59] also defined a formula for assessing availability with same modules. On the other hand, Availability is the foremost fundamental aspect of service, which assures value for customer while at the same time it is the most readily sensed aspect of service [30]. Therefore, measuring the added values delivered by Availability Management service is a mission.
Based on definitions proposed by [39, p. 101], maintainability measures the speed of provider firm to fix a failure occurred in a service or component while reliability measures how long a service or component can operate without interruption. Three formulas, as follows, are introduced by ITIL in order to calculate the reliability and maintainability.
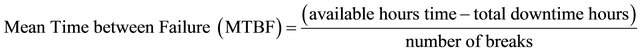 (1)
(1)
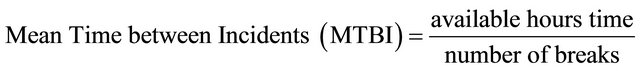 (2)
(2)
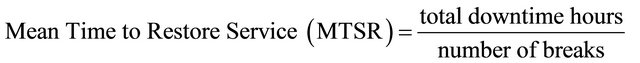 (3)
(3)
As ITIL states, Equations (1) and (2) define reliability and Equation (3) calculates the maintainability.
According to what ITIL defines and inspired by Zack’s formula on measuring the availability of IT services, the authors propose a metric to measure the first added value delivered by Availability Management service based on reliability and maintainability. Equations (4) and (5) trigger the index for this purpose
 (4)
(4)
where
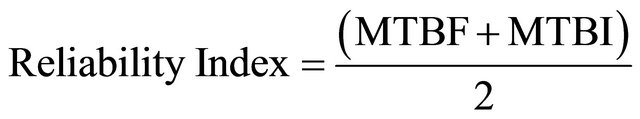 . (5)
. (5)
As the result, the final metric can be calculated by Equation (6):
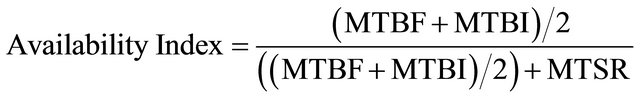 . (6)
. (6)
b) Proactive and Preventive Availability Management
As already mentioned above, availability management can be done reactively or proactively. The reactive activities consist of monitoring, measuring, and analyzing the services and components availability. On the other hand, proactive activities contain design and plan new components as well as proposing recommendations for more efficient and effective availability management [39]. As [12] highlighted and is also understood from the sale case discussed in this study, innovation and be proactive is always in demand. Being proactive in this service can not only fulfill part of customers’ demand on innovation but also facilitates continual improvement and risk reduction. Accordingly, the authors consider being proactive as another added value delivered by Availability Management service and propose the following metric (Equation (7)) for measuring the extent of service provider innovation in this regard.
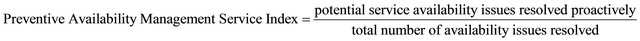 . (7)
. (7)
c) Efficient of Availability Management
The third added value identified for Availability Management service monitors the efficiency of the service. Obviously, when a service or a component is not available, one or more users are prevented from operating. In other words, unavailability leads to time lost and consequently decreases productivity. Therefore, from a business point of view, it is essential to measure the level of efficiency by means of a metric. For this purpose, the authors propose an index (Equation (8)) as follows:
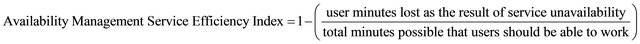 (8)
(8)
4.2.2. Configuration Management Service
Configuration Management service, as the backbone of all AM services, is one of the most important AM Operate services provided by service provider firms. ITIL puts specific focus on this service and provides a comprehensive glossary along with essential guidelines on the different configuration management concepts such as Configuration Management Service, Configuration Management Process, Configuration Item (CI), and Configuration Management Systems (CMS). Therefore, the providers’ service descriptions inspired from ITIL to a wide extent and have got a lot of input from its best practices.
Configuration Management service ensures CIs, which can be a service component or a system, are well-identified, maintained, and the changes are under full control [52, p. 65]. This service acts as a supportive service to all AM services since the CIs can come from any service, system, or product. As it is mentioned in the ITIL-based Tieot’s Configuration Management service description, the added value is delivered through three distinctive components of the service namely: prepare/enhance, operate, and audit. The main stream of all these three modules within the service, as a Delivery Mentor of Tieto highlighted, is to structure the configuration information in a “useful, reliable, and useable” manner. In order to achieve this, the maintained information should be demanded (useful), up-to-date and accurate (reliable), and easily accessible from user’s point of view (useable). As [39, p. 123] mention, Configuration Management service handles the information on the “relationships between the business, the services, the supporting services and the technology”. On the other hand, in order to define the scope of configuration management as well as the resource of information, a plan is needed [46]. Therefore, accurate configuration plan along with well-defined relationships promote usable, reliable, and useful Configuration Management service. In other words, the added values delivered to the customer’s business by means of this service are dependent on configuration plan by which the guidelines for storing accurate data with specified relationships are provided.
a) Accurate and in Detail Configuration Plan
According to what has been explained so far, the importance of a configuration plan, along with accuracy of configured data, is outstanding. Two indices (Equations (9) and (10)) are introduced by measuring which usefulness, reliability, and usability of configuration management service can be assessed.
Request can be reported in form of incident, problem, release, or change. These two indices evaluate the ability of the service provider in proposing a comprehensive configuration plan with precise configuration information. Consequently, the maturity of service provider in optimizing the performance of service assets and reducing “costs and risks caused by poorly managed assets” [52, p. 65] is evaluated.
3. Service Value Agreement Proposition
3.1. “When SVA”?
By term “When SVA” the authors intend to answer the question “in which stage of IT services outsourcing SVA should be discussed and utilized?” Time wise, SVA proposition can be discussed from two perspectives: pre-sales lifecycle and delivery lifecycle. As is extensively discussed in Section 3.5, service provider firms together with customers’ organizations have to go through IT outsourcing lifecycle during the outsourcing assignments. Therefore, SVA, as an indicator for value delivery [12], should be considered and pinpointed throughout the lifecycle.
a) Pre-Sales Lifecycle
Based on practitioners’ experiences which have been transferred during the project work, there are four major matters which customers consider when they release Request for Information (RFI) and Request for Proposal (RFP) namely: Need, Cost, Solution, and Risk. Customers ask for IT solutions from service providers according to their business needs. Accordingly, solutions are proposed by providers in which the risks of solutions implementation, as well as the costs of solutions, are evaluated and reported to the customer. However, these four core issues which construct the cornerstones of IT service delivery at the later stage, have diverse levels of importance for customers in different stages of sales process. As a Lead Product Manager and Senior Advisor of Tieto unanimously expressed according to the experiences, utmost importance in value proposition stage belongs to Needs while it has the least level of attention in contract signing stage. On the other hand, minimizing Risks of solutions implementation and setting off a relationship with provider is at the centre of attention in contracting phase while they are not discussed in early stages e.g. value proposition. These unwritten facts are shown graphically in Figure 1.
Based on the best of practices shown in Figure 1, the authors are of the opinion that debating SVA should not be postponed to contract signing phase where parties are mainly focused on risks lessen. SVA would be more effective and easier to utilize if it brings up from very early stages of sales process and its content is planned according to the parties’ priorities. By following this proposition, the service provider gains better understanding regarding the requirements and customer’s considerations and, consequently, proposes more appropriate solutions with more realistic prices. On the other hand, the customer can focus on all four aspects of service delivery thoroughly during the sales process. Moreover, a wellgrounded relationship is drawn after SVA negotiation.
b) Delivery Lifecycle
As it is discussed in Section 3.5.2, knowledge transfer and responsibilities hand over are carried out during the transition phase followed by setting up delivery centers, consolidation, and standardization in transformation
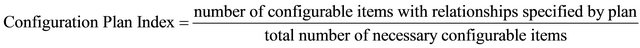 (9)
(9)
 (10)
(10)
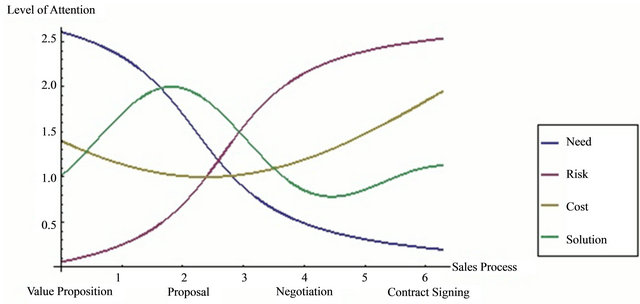
Figure 1. Sales process—customers considerations.
phase. In other words, the basic ground for the next step, which is steady state phase, is settled throughout the transition and transformation phases. During the steady state period continuous support is granted by provider firm and consequently the added values are delivered to the customer’s business. Therefore, steady state can be undoubtedly interpreted as the stage in which added values are conceived in live environment. However, as the Delivery Mentor of Tieto described, the value delivery does not happen at once overnight for all services, applications, and infrastructure but it will take place gradually as the responsibility is transferred, applications as well as infrastructure are populated, and service levels are stabilized.
Based on what is discussed above and what is experienced in the explained case study, it seems it is the best to implement SVA during the steady state gradually as applications and service levels are stabilized. As the Offering Developer of Tieto highlighted, this approach encompasses a “win-win” situation for both parties where the provider understanding regarding the customer’s requirements becomes even more realistic and a complete control over the services is gained.
3.2. “How SVA”?
It is much easier to speak about value delivery than really do it in practice. As it is depicted by [30], “Services are a means of delivering value to customers by facilitating outcomes customers need to achieve”. SVA identifies these values and desirable outcomes; however, we still need to understand how to offer SVA to customers. Should it be a catalogue full of added values which are proposed in a same way that service catalogue is offered; or should it be a standalone entity with no explicit co-relation with offering catalogue? Should it be in form of a legal bonded promise from the first day of implementation; or should it be initially implemented temporary for a short period of time? These questions have been raised by pre-sales team when it was decided to propose SVA, for the first time, to Customer X in order to offer something extra ordinary and fulfill parts of their requirements in more innovative manner.
Since this area is completely untouched and immature both in practice and academia, there exists no best of breed as well as right or wrong answer available to the above questions. As a result, practitioners’ personal ideas, which come from several-years experience of being in IT outsourcing market and in deep awareness of IT service management, build up reliable knowledge as the ground for building up the future best of practices.
The consequence of Tieto’s expertise brainstorming is two approaches: Service Value Mapping (SVM) and Piloting. These, as two short answers to the above questions, have been utilized in the customer sales case and have got a lot of attention both internally, in Tieto, and externally, from customer side. The idea lies in SVM approach is in aligning with Value Stream Mapping—the standard lean manufacturing technique—by which the flow of information and material required to provide a service for customer are monitored and analyzed [60]. Similarly, SVM approach identifies, traces, and analyzes the added values that are ideally delivered by each service and required by customer. The added values are selected and extracted from the list of added values presented in the updated SVA. In selection of added values both generic and customized categories of added values defined by [12] have been considered. Figure 2 shows example of utilizing this approach for Configuration Management and Availability Management services.
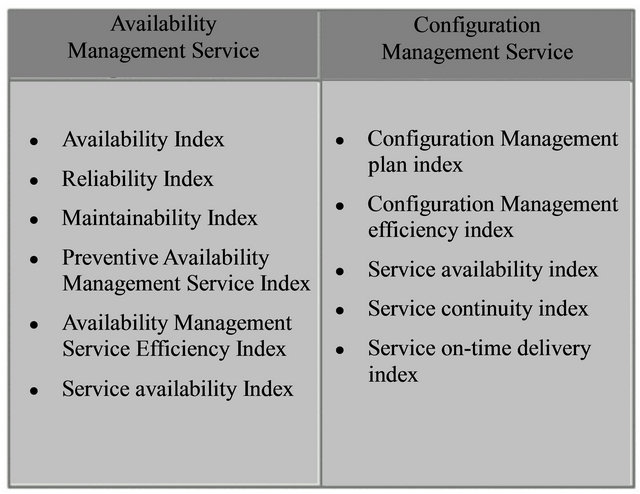
Figure 2. Example of service value mapping approach for two AM operate services.
Based on customers’ demands and maturity of service providers, as the added values are mapped to each service, more new added values might be identified. The new values can be developed and the appropriate correspondent measurement metrics are designed. The newly introduced indices in Section 4.2 are result of pursuing this process.
According to the market trend and what is expressed by one of the Sales Specialists of Tieto, the overall condition of service delivery in the first months fluctuates. During the transition phase the service provider can have a real idea of the nature of applications, services, and their functionalities. However, as the Delivery Mentor of Tieto said, “the Service Level Manager and the counterpart at the customer side should know the services to such a high degree that the service level negotiations can take place during the due diligence phase. The SLA shall be understood and signed before day first of the service delivery. Then, if the SLA turns out to be wrong, both parties should have the right to propose changes and re-negotiations”. Perhaps what makes parties to be able to decide on SLA even before starting the service delivery is experience and the routine nature of service levels and delivery content of services. However, this cannot be applicable for SVA. Immaturity in implementing and forecasting the outcomes of value targets allows neither service provider nor customer to accept any terms and conditions blindly. This uncertainty and unfamiliarity motivates the authors as well as practitioners involved with the sales case to suggest a temporary period for SVA experimenting. ITIL also highlights the importance of testing, pilot and deploy activities service delivery [52]. As a result, the authors believe Pilot period is essential for further negotiations and bridging “win morewin more” relationship and recommend implementing of SVA as Pilot for an agreed period of time during steady state. The advantages of implementation of Pilot are twofold: on one hand, it helps providers to become more familiar with the services and do self-assessment to meet the value targets and, perhaps, negotiate more realistic value target with customer. On the other hand, during this period customers can practice SVA in the live environment, understand how it really differs from traditional SLA, and put more effort on co-creating the added values with the service provider.
4. Conclusions
This study is conducted as a follow up on our previous research to suggest a set of guidelines for implementing the newly developed SVA. By this, the appropriate ground for developing best of practices in the field of SVA, which is still immature in practice and academia, is prepared. On one hand, from academic point of view, the knowledge domain around SVA goes one step further by implementing what has been built up previously by [12] in theory. On the other hand, from a practical point of view, a tangible feeling regarding SVA implementation in live environment is given to both service providers and customers.
This study provides senior managers with a conceptual clarity to discuss “When” and “How” SVA should be proposed and, consequently, enables them to set up a common foundation for partnership. It is essential to keep SVA under consideration from very early stages of outsourcing lifecycle (i.e. RFI or RFP phases) and implement it gradually after transformation and during the steady state phase. It is equally important to consider pilot execution for an agreed period of time in order to keep the rooms free for further negotiations regarding the value targets. The solid advantages of these two approaches can be listed as: 1) SVA content is planned according to the parties’ priorities throughout the pre-sales lifecycle; 2) service providers remain focused on right requirements and, therefore, desired solutions with more realistic prices are proposed; 3) service provider together with targeted customer standardize the service value targets during the pilot period; 4) value co-creation approach is utilized by the three prior advantages.
Service Value Mapping approach in aligning with one of the lean manufacturing techniques, Value Stream Mapping, is discussed as an appropriate proposal for SVA proposition. Based on customers’ priorities and requirements, Service Value Mapping identifies, traces, and analyzes the added values that are ideally delivered by each service and required by customers. This approach enables customers to conceive values easier by keep tracking of value flow in different services.
Finally, the previously developed SVA have been enriched by means of seven new designed added values and their correspondent measurement metrics. Now, the updated SVA is even more powerful to cover both customers’ high level added values and service-based added values.
Further Research
The idea of SVA, its functionality as well as its components have attracted the senior managers’ attention in Customer X quickly and an SVA is viewed a competitive advantage in the market. This has been highlighted in very early stages of pre-sales lifecycle (i.e. RFI phase) by the representatives of Customer X. Value mapping approach and its closeness to industry-based lean technique helped Customer X to instantly conceive the delivered added values to their business. However, currently, the identified added values are limited to few AM Operate services and the rest are untouched. Expanding SVA in other AM as well as data centre services can be seen a step forward.
As it is discussed, this study and its recommended principles are based on one case study. Obviously, this study provides both practitioners and researchers with the initial directives. However, it is essential to examine SVA with more and more customers, gain knowledge on the consequences of its implementation, and progressively construct a comprehensive best of practices on SVA.
5. Acknowledgements
The authors wish to hereby thank Pernilla Wikman, the Vice President of Application Management—Tieto Sweden, and Torbjörn Tergesten, Delivery Mentor—Tieto Sweden, for their continuous support.
REFERENCES
- S. Cullen, P. Seddon and L. Willcocks, “Managing Outsourcing: The Lifecycle Imperative,” MIS Quarterly Executive, Vol. 4, No. 1, 2005, pp. 229-246.
- M. Kotabe, “Global Sourcing Strategy and Sustainable Competitive Advantage,” Industrial Marketing Management, Vol. 33, No. 1, 2004, pp. 7-14. doi:10.1016/j.indmarman.2003.08.004
- K. Krishnamurthy, D. Jegen and B. Brownell, “Strategic Out-Tasking: Creating ‘Win-Win’ Outsourcing Partnerships,” Information and Management, Vol. 46, No. 1, 2009, pp. 42-51. doi:10.1016/j.im.2008.11.004
- M. C. Lacity, S. A. Khan and L. P. Willcocks, “A Review of the IT Outsourcing Literature: Insights for Practice,” Journal of Strategic Information Systems, Vol. 18, No. 3, 2009, pp. 130-146. doi:10.1016/j.jsis.2009.06.002
- W. L. Tate, L. M. Ellram, L. Bals and E. Hartmann, “Offshore Outsourcing of Services: An Evolutionary Perspective,” International Journal of Production Economics, Vol. 120, No. 2, 2009, pp. 512-524. doi:10.1016/j.ijpe.2009.04.005
- K. E. Pearlson, “Strategic Management of Information Systems,” John Wiley & Sons, Hoboken, 2009.
- E. Brynolfsson and S. Yang, “Information Technology and Productivity: A Review of the Literature,” Advances in Computers, Vol. 43, 1996, pp. 179-214. doi:10.1016/S0065-2458(08)60644-0
- J. J. M. Trienekens, J. J. Bouman and M. V. D. Zwan, “Specification of Service Level Agreements: Problems, Principles and Practices,” Software Quality Journal, Vol. 12, No. 1, 2004, pp. 43-57. doi:10.1023/B:SQJO.0000013358.61395.96
- J. Goo, R. Kishore, H. R. Rao and K. Nam, “The Role of Service Level Agreement in Relational Management of Information Technology Outsourcing: An Empirical Study,” MIS Quarterly, Vol. 33, No. 1, 2009, pp. 119-145.
- K. D. Larson, “The Role of Service Level Agreement in IT Service Delivery,” Proceeding of Information Management & Computer Security, MCB University Press, Bradford, 1998, pp. 128-132.
- I. S. Hayes, “Metrics for IT Outsourcing Service Level Agreement,” White Paper, Clarity Consulting Inc., Chicago, 2004.
- M. Ziyarazavi, C. Magnusson and T. Tergesten, “Qualifying and Quantifying IT Services Added Values in Outsourcing Assignments—Service Value Agreement,” Journal of Service Science and Management, Vol. 5, No. 4, 2012, pp. 318-330. doi:10.4236/jssm.2012.54038
- P. Strassman, “Outsourcing: A Game for Losers,” Computerworld, Vol. 29, No. 34, 1995, p. 75.
- P. Strassman, “Most Outsourcing Is Still a Game for Losers,” Computerworld, Vol. 38, No. 4, 2004, p. 19.
- J. N. Lee, M. Q. Huynh, K. R. Chi-Wai and S. Pi, “The Evolution of Outsourcing Research: What Is the Next Issue?” Proceeding of the 33rd Hawaii International Conference on System Sciences, Hawaii, 4-7 January 2000, 10p.
- J. Fisher, R. Hirschheim and R. Jacobs, “Understanding the Outsourcing Learning Curve: A Longitudinal Analysis of a Large Australian Company,” Information Systems Frontiers, Vol. 10, No. 2, 2008, pp. 165-178. doi:10.1007/s10796-008-9070-y
- L. M. Ellram, W. L. Tate and C. Billington, “Offshore Outsourcing of Professional Services: A Transaction Cost Economics Perspective,” Journal of Operations Management, Vol. 26, No. 2, 2008, pp. 148-163. doi:10.1016/j.jom.2007.02.008
- R. M. Monczka and R. J. Trent, “Worldwide Sourcing: Assessment and Execution,” Internal Journal of Purchasing and Materials Management, Vol. 28, No. 4, 1992, pp. 9-19.
- J. Spohrer and P. P. Maglio, “The Emergence of Service Science: Toward Systematic Service Innovations to Accelerate Co-Creation of Value,” Production and Operations Management, Vol. 17, No. 3, 2008, pp. 238-246. doi:10.3401/poms.1080.0027
- N. Bowen and J. Spohrer, “Viewpoint: The Future of Computing Practice and Education,” IEEE Computer Society, Vol. 43, No. 1, 2010, pp. 86-89. doi:10.1109/MC.2010.83
- R. M. Monczka and R. J. Trent, “Global Sourcing—A Development Approach,” Internal Journal of Purchasing and Materials Management, Vol. 27, No. 2, 1991, pp. 2-8.
- M. D. Aundhe and S. K. Mathew, “Risk Mitigation in Offshore IT Outsourcing Contracts: A Service Provider Perspective,” European Management Journal, Vol. 27, No. 6, 2009, pp. 418-428. doi:10.1016/j.emj.2009.01.004
- J. Spohrer, P. P. Maglio, J. Bailey and D. Gruhl, “Steps Toward a Science of Service Systems,” IEEE Computer, Vol. 40, No. 1, 2007, pp. 71-77. doi:10.1109/MC.2007.33
- “ITIL Service Strategy,” Office of Government Commerce, TSO, London, 2007.
- K. Wüllenweber, D. Beimborn, T. Weitzel and W. König, “The Impact of Process Industrialization on Business Process Outsourcing Success,” Information Systems Frontiers, Vol. 10, No. 2, 2008, pp. 211-224. doi:10.1007/s10796-008-9063-x
- C. Rosenkranz, S. Seidel, J. Mendling, M. Schaefermeyer and J. Recker, “Toward a Framework for Business Process Standardization.” 5th International Workshop in Business Process Design, Springer, Berlin, Heidelberg, 2010, pp. 43-53.
- M. Schäfermeyer and C. Rosenkranz, “To Standardize or Not to Standardize? Understanding the Effect of Business Process Complexity on Business Process Standardization,” 19th European Conference on Information Systems (ECIS2011), Helsinki, 9-11 June 2011.
- H. V. Leijen, “The Role of Contextuality in Process Standardization,” In: W. Baets, Ed., Knowledge Management and Management Learning: Extending the Horizons of Knowledge-Based Management (Integrated Series in Information Systems), Springer Science and Business Media, USA, 2005, pp. 251- 286.
- B. Martorelli, E. Rose and C. F. Ross, “Application Outsourcing Clients Are Satisfied, but Want More,” Forrester, Cambridge, 2010.
- P. Matthyssens and K. Vandenbempt, “Moving from Basic Offering to Value-Added Solutions: Strategies and Alignment,” Industrial Marketing Management, Vol. 37, No. 3, 2008, pp. 316-328. doi:10.1016/j.indmarman.2007.07.008
- I. Oshri, J. Kotlarsky and P. Willcocks, “Outsourcing Global Services,” Palgrave Macmillan, New York, 2008. doi:10.1057/9780230227415
- A. Dagenhardt, A. Godard and F. P. Rauch, “Top 10 Pitfalls of Application Management Services,” White Paper, Siemens IT Solutions and Services, Berlin, 2010.
- “ITIL Service Design,” Office of Government Commerce, TSO, London, 2007.
- I. C. Ng, R. Maull and N. Yip, “Outcome-Based Contracts as a Driver for Systems Thinking and ServiceDominant Logic in Service Science: Evidence from the Defense Industry,” European Management Journal, Vol. 27, No. 6, 2009, pp. 377-387. doi:10.1016/j.emj.2009.05.002
- S. L. Vargo and R. F. Lusch, “Evolving to a New Dominant Logic for Marketing,” Journal of Marketing, Vol. 68, No. 1, 2004, pp. 1-17. doi:10.1509/jmkg.68.1.1.24036
- S. L. Vargo, P. P. Maglio and M. A. Akaka, “On Value and Value Co-Creation: A Service Systems and Service Logic Perspective,” European Management Journal, Vol. 26, No. 3, 2008, pp. 145-152. doi:10.1016/j.emj.2008.04.003
- M. C. Lacity and L. P. Willcocks, “Information Systems and Outsourcing,” Palgrave Macmillan, New York, 2009.
- J. C. Anderson, J. A. Narus and W. V. Rossum, “Customer Value Proposition in Business Markets,” Harvard Business Review, Vol. 84, No. 3, 2006, pp. 91-99.
- N. Levina and J. W. Ross, “From the Vendor’s Perspective: Exploring the Value Proposition in Information Technology Outsourcing,” MIS Quarterly, Vol. 27, No. 3, 2003, pp. 331-364.
- M. Dier, “Accenture Merger, Acquisition, Divestiture and Alliance Services,” White Paper, Accenture, Dublin, Chicago, 2012.
- Deloitte, “Strategies for Going Public,” White Paper, Deloitte M&A Consultative Services, 2010.
- IBM Global Technology Services, “Transition and Transformation, Transitioning Services with Minimal Risk,” White Paper, IBM, 2007.
- M. Walsh, A. Ramchandran and S. Nolen, “Ignorance is not Bliss, IT Due Diligence is Fundamental for Effective Post-Merger Synergy Capture,” White Paper, Deloitte M&A Consultative Services, New York, 2008.
- “ITIL Service Operation,” Office of Government Commerce, TSO, London, 2007.
- M. Lacity and L. Willcocks, “An Empirical Investigation of Information Technology Sourcing Practices: Lessons from Experience,” MIS Quarterly, Vol. 22, No. 3, 1998, pp. 363-408. doi:10.2307/249670
- “ITIL Service Transition,” Office of Government Commerce, TSO, London, 2007.
- L. Willcocks, D. Feeny and G. Islei, “Managing IT as a Strategic Resource,” McGraw Hill, Maidenhead, 1997.
- L. Mathiassen, “Collaborative Practice Research,” Information Technology & People, Vol. 15, No. 4, 2002, pp. 321-345. doi:10.1108/09593840210453115
- E. Gummesson, “Relationship Marketing and A New Economy: It’s Time for De-Programming,” Journal of Services Marketing, Vol. 16, No. 7, 2002, pp. 585-590. doi:10.1108/08876040210447315
- M. Myers and D. Avison, “Qualitative Research in Information Systems,” SAGE, London, 2002.
- R. Stake, “The Art of Case Study Research,” SAGE, Thousand Oaks, 1995.
- H. Simons, “Towards a Science of the Singular: Essays about Case Study in Educational Research and Evaluation,” Centre for Applied Research in Education, University of East Anglia, Norwich, 1980.
- R. K. Yin, “Case Study Research: Design and Methods,” SAGE, Newbury Park, 2003.
- A. Hochstein. G. Tamm and W. Brenner, “Service Oriented IT Management: Benefits, Cost and Success Factors,” Proceedings of 15th European Conference on Information Systems, Regensburg, 26-28 May 2005.
- B. C. Potgieter, J. H. Botha and C. Lew, “Evidence that Use of the ITIL Framework is Effective,” Proceeding of the 18th Annual Conference of the National Advisory Committee on Computing Qualifications, Tauranga, 10- 13 July 2005.
- J. Van Bon, G. Kemmerling and D. Pondman, “IT Service Management, an Introduction,” Van Haren Publishing, San Antonio, 2002.
- J. Zeng, “A Case Study on Applying ITIL Availability Management Best Practice,” Contemporary Management Research, Vol. 4, No. 4, 2008, pp. 321-332.
- G. Ritchie, “Introducing ITIL Availability Management,” Serio Ltd., Edinburgh, 2008.
- S. Zacks, “Introduction to Reliability Analysis: Probability Models and Statistics Methods,” Springer-Verlag, New York, 1992. doi:10.1007/978-1-4612-2854-7
- [61] M. Rother and J. Shook, “Learning to See: Value Stream Mapping to Create Value and Eliminate Muda,” The Lean Enterprise Institute—One Cambridge Centre, Cambridge, 2008.

