Modern Economy
Vol.5 No.4(2014), Article ID:44995,13 pages DOI:10.4236/me.2014.54039
Integrated Enterprise Risk Management: From Process to Best Practice
Kathryn Cormican
College of Engineering & Informatics, National University of Ireland, Galway, Ireland
Email: Kathryn.cormican@nuigalway.ie
Copyright © 2014 by author and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/


Received 28 February 2014; revised 30 March 2014; accepted 8 April 2014
ABSTRACT
There are strong motivating factors for increased awareness and action with regard to Enterprise Risk Management (ERM). Effective ERM policies and practices are lauded to increase stakeholder confidence, competitive advantage and ultimately an organization’s long-term viability. However previous studies suggest that the concept is poorly understood in practice and organizations are failing to implement the intended benefits. Furthermore, insufficient research has been conducted in this area and there are few comprehensive or practical guides available to managers in his domain. This paper attempts to address this deficit and expand the discussion on integrated enterprise risk management practices. The study presents findings from a qualitative study where critical success factors for effective enterprise risk management are identified and categorized. From this analysis an audit tool to assess ERM best practices is presented. The tool acts as an independent validation resource to ensure that an organization’s efforts are proactive and effective against current and emerging threats. The contributions of this research are many. First it enhances knowledge and skills in a neglected but essential multi-disciplinary area. Second the research is grounded in best practice and so adds to academic debate by validating and contradicting previous studies. Third the development of new and innovative tools in enterprise risk management adds bridges the gap from theory to practice.
Keywords:Enterprise Risk Management, Process, Tools, Best Practice Factors, Audit

1. Introduction
Enterprise Risk Management is an approach to identify, analyze and proactively plan responses to a wide range of risks in an organization [1] [2] . It is the continuous process of measuring and monitoring risk and developing appropriate strategies or corrective actions to manage the risk. According to Thompson [3] it adds value to the organization by ensuring that any exposure to risk is suitably understood and managed. Risk management is an evolving discipline. In the past an organization’s risks were examined one at a time in an isolated and compartmentalized basis. In those environments, risks were managed by functional or business-unit leaders with minimal oversight of how particular decisions or actions might affect other aspects of the organization [4] . Today, the emerging trend is towards a coordinated, interactive, enterprise-wide approach that assesses and manages all risks together [5] [6] . This holistic approach overcomes the limitations of silo-based traditional risk management. For that reason enterprise risk management is also referred to as “integrated risk management” and “holistic risk management” [7] . It is an important interdisciplinary research area [8] and it depends on many interrelated organizational dynamics [9] .
Many researchers define enterprise risk management in terms of its ability to support decision making. According to Önder and Ergin, [10] , enterprise risk management is a useful approach to identify and evaluate an organization’s decisions and strategies. Frigo and Anderson [4] note that enterprise risk management must be embedded in and connected directly to the enterprise’s strategy in order to add value. Bromiley et al. [5] also argue that enterprise risk management requires the alignment of risk management with corporate governance and strategy.
There has been much debate in the literature about the benefits of enterprise risk management (ERM) initiatives. According to recent studies organizations engage in ERM for two key reasons specifically compliance (e.g. adherence to directives, regulations and legislation) or performance (e.g. optimization of effectiveness and efficiency) [9] [11] . Other researchers assert that an effective enterprise risk management approach helps to mitigate risks and exploit opportunities [7] [12] [13] . Some researchers have found that enterprise risk management has a positive impact on a firm’s performance [7] [14] . However, other studies have suggested that implementations often fail to bring intended benefits [2] [15] . For example McShane et al. [6] posit that the relationship between ERM and firm performance is inconclusive. Despite this, Barton et al. [16] assert that the opportunity costs for neglecting enterprise rick management are large. They found that the mismanagement of risks has resulted in significant financial loss, decreased shareholder value as well as damaged company reputations.
It is clear that academic research on ERM is still in its infancy. Bromiley et al. [5] argue that to date most work has being conducted in accounting and finance disciplines and insufficient work has been conducted in the management discipline. Studies have suggested that organizations do not adequately understand the concept [2] [5] [17] . In addition, the number of firms that apply a systematic approach to risk management is limited [1] [15] . Önder and Ergin [10] note that most of the previous academic studies concerning enterprise risk management are theoretical. Furthermore, there is evidence to suggest that there is a bias towards larger firms in the literature. It seems that it is more probable for large and institutionalized organizations to adopt enterprise risk management and small firms do not actively engage in enterprise risk management.
Consequently it seems that these gaps must be addressed. There is a need for a systematic and integrated approach to ERM that provides clear directions to mangers and decision makers. The goal of this research is to identify, categorize and present best practice in the area of enterprise risk management. The findings of our work are based on qualitative research. 31 interviews were conducted with leaders of high tech manufacturing organizations in Ireland. The goal of the interviews was to gain a deep insight into the challenges, requirements and critical success factors for enterprise risk management. Based on these findings we present a best practice framework and supporting audit tool for enterprise risk management that is useful, practical and operations oriented. In other words it aims to bridge the gap between the theory and the practice. The framework is suitable for managers working in small firms to absorb and digest. Other characteristics of the contribution include:
• It provides the manager with a tool to detect gaps in best practice;
• It is user friendly, intuitive and easy to use;
• It is flexible and adaptable in all types of systems and processes;
• It provides sufficient information to enhance operational and strategic decision making;
• It is holistic in nature and integrates key organizational processes;
• It facilitates communication of individual events that may affect the overall system.
The remainder of this paper is organized as follows. Section 2 introduces the concept of risk and theoretical models in this domain. Section 3 presented a methodology with supporting tools for enterprise risk management based on a synthesis of the literature. Section 4 outlines the research approach taken in this study. Section 5 presents a best practice model and audit tool.
2. The Concept of Risk
Risk is a concept used to express uncertainty about events and their outcomes that could have a negative effect on the performance of the organization and its goals. Mitchell [18] defines risk in terms of the probability of loss and the significance of that loss to the enterprise. Generally speaking, risk comprises the probability of a negative event occurring multiplied by how harmful that event would be [19] . Risk can therefore be defined as a function of these components as in (1).
Risk = ƒ(event, probability, impact) (1)
Previous work on the area of risk is varied. Sadgrove [20] reported on the categories of risk and noted that there are four main categories of risk in an enterprise namely financial, operational, strategic, and compliance risks. Harland et al. [21] take a broader perspective. They synthesized previous work in the area and present eleven types of risk. Smith and Merrit [22] examine the probability of events occurring as well as potential impacts in order to assess total loss and prioritization of different risks. Other models adopt a causation approach and consider the relationships between the factors [22] [23] . These models feature a bidirectional relationship between causes and effects (see Figure 1). In this view, some effects may in fact be the cause for other subsequent effects. Here the effect comprises the event and the impact of the event (e.g. the level of severity) whereas the consequence describes the outcome or loss incurred. There are many types of loss. Some include financial, performance, physical, psychological, social, time.
Many other models of risk management focus on the selection of strategies to manage the risk. Typically the strategies employed include transferring the risk to another party, avoiding the risk, reducing the negative effect of the risk, and accepting some or all of the consequences of a particular risk.
• Accept Risk: understand the risk, probability of occurrence and consequences. The organization must be equipped to react if it happens.
• Avoid Risk: Organizations can change the scope or activity to avoid the risk. They also can insert preventative measures to ensure that the risk does not occur.
• Monitor Risk: Here the organization will have specific contingency plans ready in the event of a known risk occurring.
• Transfer Risk: This option allows organizations to outsource or transfer the risk and associated responsibility to other entities such as contract organizations and or insurance companies.
• Mitigate Risk: In this option organizations must work hard to ensure that preventative measures are in place to reduce risk.
3. Enterprise Risk Management Process and Tools
Raghavan contends that an organization’s survival depends on its ability to anticipate and prepare for change rather than reacting to it when it inevitably occurs. Therefore it is important to implement an effective risk management process to understand, monitor and control risk in order to improve the organizations objectives, comply with regulations, improve the financial status and define goals more appropriately. The risk management process is continuous and iterative. It identifies the risks, analyzes its impacts and probabilities, tracks and mitigates the risks, and assures the information and reports are communicated. There are several approaches that have been suggested for the management of the risk as a process. Each process contains a series of interrelated
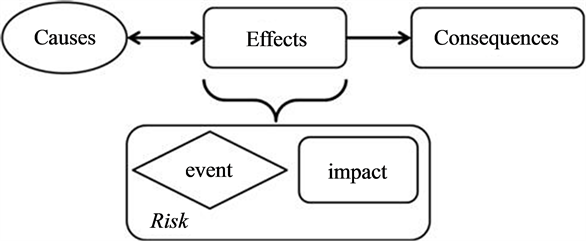
Figure 1. Causation model . steps that must be managed - . These are: (a) establish the context, (b) identify risk, (c) analyze risk, (d) monitor and control risk. Each of these is discussed in more detail below. It is also important to identify appropriate tools to help the organization and people responsible for risk management to better understand, anticipate and managed risk. These tools are synthesized in Table 1.
3.1. Establish the Context
It is essential to define the basic parameters within which risks must be managed. The overall context of risk includes the external (e.g. industry, regulators, and markets) and internal environment (e.g. people, processes, culture) . It is also critical to identify all the parties that might be affected by the results of decisions that the management takes. Macdonald states that stakeholders are people and organizations who affect, or affected by a decision or activity. Knowing all the parties and stakeholders is important for requirement identification and having the stakeholder’s support.
Process and functional modeling tools are often used to help an organization understand its context. Modeling tools such as IDEF0 and IDEF1 are can be used to describe what the process or function does, what controls it, what means is used to perform its functions, and what it produces. These structured analysis and design techniques are based on combining graphics and text that are then presented in an organized and systematic pro forma format . Network Diagrams comprise the critical path method (CPM) and programme evaluation and review technique (PERT). A Network Diagram is a graphical way to view tasks, dependencies, and the critical path of a project. Boxes or nodes are used to represent tasks, and dependencies and lines are used to connect the boxes. Generalized activity networks (GAN) are used to model the development process of a product or service which helps to establish the overall context of the work . The GAN method is particularly useful for small projects that require testing and validation .
3.2. Identify the Risk
Risk identification is essential to effective risk management. By identifying a risk, a decision-maker or management team becomes conscious about specific events that may cause uncertainty and are likely to affect the organization . The central tenet of risk identification is to recognize future uncertainties to be able to manage
Table 1. Tools to support enterprise risk management.
these scenarios proactively. Systematic process analysis is a useful approach to risk identification. Here each phase and activity of a process is broken down and analyzed according to the inputs, outputs, and operations that take place during each phase. This facilitates the identification of potential risks. The benefit if this approach is that processes are thoroughly analyzed and risks are aligned to specific activities and process.
Influence diagrams offer a simple, visual and intuitive way to identify and display decisions, uncertainties, and objectives, and how they influence each other. This process helps to uncover risks. Cause and effect diagrams are causal diagrams that express the causes of a specific event. According to Rooney, et al. cause and effect diagrams are used to identify dominant factors that than can contribute to risk. Causes are usually grouped into major categories to identify sources of risk. The categories typically include man; machine; methods; materials; measurements (or data) and the meta-environment. Failure Mode and Effect Analysis (FMEA) is a systematic method for analyzing a process to identify where and how it might fail. Simply put it enables a decision maker to answer the following questions (a) what could go wrong? (b) Why would the risk or failure happen? and (c) what would be the consequences of each risk or failure? Pillay and Wang present the FMEA in terms of a ten step process. Fault Tree Analysis is another easy to use visual model that helps users to represent complex systems in an understandable manner. From this risks can be identified.
3.3. Analyze the Risk
The risk analysis process is the center point of risk management; it is a systematic use of information to investigate, estimate and evaluate risk. Essentially risk analysis is about the estimation of unseen and probabilistic events. The probabilities are unknown and the risk analysis is used to estimate the probability of occurrence . The tools used here can also vary from organization to organization depending on their strategies, objectives and goals.
In order to analyze the risk the characteristics of risks must be adequately documented. Risk analysis involves the systematic use of information to identify sources, estimate consequences and the likelihood of occurrence of these risks risk. Risk identification aims to determine the possible causes and probable consequence of the risk therefore it is imperative to measure the magnitude of the potential loss, and the probability that the loss will occur. Here the acceptability of the risk is determined and the actions that can be taken to make the risk more acceptable are evaluated . According to Sun et al. the purpose of risk evaluation is to prioritize risks in terms of severity and level of influence.
Strengths, weaknesses, opportunities and threats (SWOT) analyses are used in many companies as part of the risk analysis phase. Risk Analysis Tables are simple but effective tools to enable this process (see Table 2). Probabilistic Risk Assessment has emerged as an increasingly popular analysis tool in recent years. It is a comprehensive methodology used to evaluate risks associated with large complex operations or products. It adopts a life cycle approach to analysis. Here phases or aspects such from concept definition, through design and manufacture to end of life stages in development are analyzed. It is used to estimate risk by computing real numbers to determine what can go wrong, how likely is it to happen, and what are its consequences. Multiple Criteria Decision Making Analysis techniques use predefined criteria and associated weighting for each criteria to help decision makers systematically assess a risk.
3.4. Monitor and Control the Risk
Risk monitoring is the process of keeping track of identified risks, ensuring that action plans are implemented and evaluating the effectiveness of risk responses. It is a continuous process and appropriate systems and operations should be well defined and structured in order to use tools for risk monitoring and control . Simons’ framework identifies five controls should be used to manage risk:
• Diagnostic controls—these problem solving controls enables employees to ascertain whether specific actions were successfully completed;
• Boundary controls—these controls constrains employee activities by making it clear what actions are unacceptable;
• Belief controls—these controls presents the organizations cultures and principles that should guide action;
• Internal controls—these controls ensure that policies, procedures and rules are employed;
• Levers to control and manage risk—these controls ensures that the organization is implementing risk management strategies.
Table 2. Risk analysis table.
Barton et al. warns that decisions regarding control are dynamic and so they must be continually reevaluated. Control charts are specific templates used for controlling and monitoring the tasks or project tools. Risk audits can be used to evaluate the effectiveness of actions as well as the effectiveness of the processes being used. Variance and trend analysis can also be used to monitor the performance of processes.
4. Research Methodology
The goal of this study is to uncover deep insights into the specific challenges and critical success factors for enterprise risk management. Accordingly an inductive qualitative approach was deemed to be the most suitable research method to employ. The reasons for this are as follows:
• The research undertaken in this study is considered exploratory in nature, as relevant variables have yet to be defined;
• The exact subject under investigation is not very well documented in the literature; therefore the research could not be conducted experimentally;
• The study investigates complex issues and processes and hence the researcher anticipated that as the research proceeded the issues were likely to unfold to reveal new dimensions;
• A substantial amount of research was concerned with collecting and assessing the views and opinions of participants and subsequently it was felt that an inductive approach was the most suitable method.
In total 134 high-tech manufacturing companies employing no more than 100 people based in Ireland were contacted from the outset. The rationale for this selection was that organizations of this size were deemed to have standard operating procedures without being overly structured and controlled. Purposive sampling techniques were initially employed followed by snowball methods to facilitate literal replication in accordance with best practice [62] -[64] . Leaders and decision makers with responsibility for strategic direction and accountability for enterprise risk management were targeted as they were best placed to provide a full and detailed account of the relevant problems, activities and outcomes. To ensure that there was no participant or observer bias [65] , the individuals contacted were unknown to the researcher. The research protocol was approved by the company prior to data collection. Pre-test and pilot studies were conducted to ensure that the wording of the questions and logical flow was correct. From this, minor changes were made to the questions prior to the company interviews.
Initially exploratory interviews were conducted (n = 8). Each interview lasted between 30 and 50 minutes. Unstructured open-ended questions were used without imposing any strict agenda. This allowed the interviewees to identify challenges and success factors in their own way. Care was taken to limit direct questioning and to avoid leading the interviewee. Afterwards, semi-structured interviews were conducted to ensure all aspects of the research was covered and data collection continues until the point of saturation (n = 23). Here, key questions were posed giving some room for explanation and elaboration. Interviews were recorded using a smartphone with the respondents’ permission. This enabled the researcher to concentrate on the content during the interview and also to document the discussion in an exact manner at a later stage. A chain of evidence was drawn up and a sample of respondents (n = 6) were asked to review a draft copy of the interview script. Data was coded and analyzed using NVivo. Initial themes were developed and propositions were compared to the extant literature. This helped to strengthen internal validity. Additional internal reliability was achieved by analysis of the data through pattern matching [62] [64] . External validity was achieved by ensuring replicated logic through the execution of 31 interviews [62] . This also helped to reduce the effect of observer bias [63] .
5. Critical Success Factors
While it is apparent that there are many factors that can facilitate and thus impede enterprise risk management within organizations, some key issues and themes emerged from the research. These are synthesized, categorized and discussed in more detail.
5.1. Awareness
The overriding majority of participants asserted that effective risk management is important for the overall success of their companies. Many noted that it was “imperative for reliable decision making”. Despite this, the findings of this analysis revealed that enterprise risk management practices are not widely implemented in reality. Many leaders and decision makers felt that they “do not have adequate information about risk management initiatives”. Respondents felt that in order for enterprise risk management to be successful all employees should be aware of the indicators or symptoms of potential risks. One respondent stated that it is essential for enterprises to “have the ability to recognize changes in the environment and system.” Employees should analyze processes to proactively search for risks. However this study found that oftentimes employees “do not ask the right questions”. Nor do they consider the consequence of the risks. It seems that promoting risk awareness should be a starting point for any risk management process. Barton et al. [16] also talk about the importance of creating a culture of risk awareness. Indeed, Lam [66] states that much of the battle is already won if people can be encouraged to understand the potential risks in their activities.
5.2. Policies
Hopkin [67] highlights the importance of a defined strategy for enterprise risk management. Barton et al. [16] assert that organizations must articulate policies and tolerances. However enterprise risk management is not a formal strategic objective in the organizations analyzed in this study. The majority of respondents stated that although they believed enterprise risk management was important it is not part of the strategic goals of the organization. For example, respondents stated: “we do not have a formal policy in place” and “we know it is important but it is not written down or communicated to all workers”. These findings are broadly in line with those of Kleffner et al. [17] who also found that organizations do not adopt an enterprise risk management strategy. This study also revealed that the organizations investigated do not have adequate resources dedicated to achieve risk management goals. Furthermore, risk initiatives are not aligned to the organizations overall strategy and risk performance indicators are not analyzed at the strategic level. These findings imply that whilst the participants studied recognize the importance and value of enterprise risk management, they do not adopt a systematic approach to prioritizing, aligning and integrating employee effort in this regard.
5.3. Processes
There was considerable discussion about the importance of processes in our study. Much of the discussion centered around two key elements namely risk identification and risk analysis. Participants stated that it was imperative to make a committed effort to identify risk. It was also highlighted that this activity was not the sole responsibility of management but rather “risk identification should occur at all hierarchical levels in the organization”. This finding supports the work of Moeller [68] . Many respondents stated that the inability to effectively analyze risk is a key barrier to enterprise risk management. Frigo et al. [4] highlight the importance of dedicated processes. They argue maintain that “developing strategic risk management processes and capabilities can become a strong foundation for improving risk management and governance”. However it seems that the vast majority of responding companies do not have a formal structured process in place for identifying and analyzing risk. Organizations in the study confirmed that they not have “an agreed process for reporting, managing and analysing risk.” Moreover, they do not focus on critical activities and they do not employ an integrated approach to ERM. However many respondents acknowledge that it is important to “move away from restrictive functional perspective to a more open process-oriented viewpoint.” Kleffner et al. [17] also call for a shift away from this functional or “silo” perspective.
5.4. Management
Central to effective risk management is senior management support and commitment. Many researchers [16] [21] [56] argue than ERM cannot succeed without strong support from senior management. One of the most prominent themes that emerged from this study includes “management buy-in”, “top management support” and “senior management support”. Respondents noted that management must demonstrate their commitment to enterprise risk management by actively engaging in the process. The study also highlighted the importance of clear roles and responsibility. One respondent noted that enterprise risk management can easily become “everybody’s problem and no one’s problem”. It seems that management must also ensure that appropriate ERM tools and techniques are disseminated and used throughout the organization. In particular, they must have a corrective action system in place. They must also align authority and allocate responsibilities to ensure effective implementation. Human resource policies and practices such as orientation, compensation and promotion initiatives should be used to encourage implementation. Management must also ensure the effective integration of risk management initiatives. Many respondents asserted that initiatives “cannot be considered in isolation” rather they must be “coordinated across the entire organization”. In other words, a holistic management perspective must be adopted to ensure success. These processes and systems must also be continually monitored adjusted to specific needs and improved.
5.5. Culture
Leaders and senior managers can play a pivotal role, acting as role models to more junior staff by detecting and preventing risks and hazards themselves thereby promoting risk management issues in the organization. One of the merits of risk management as an organizational tool is that it can be tailored to the needs of every organization. It is also important to note that different policies will suit different organizations depending on the culture, demographics and needs of the organization and its employees. Many respondents in this study stated that “employees often don’t know what to do when they notice a potential risk”. Another revealed that is “not right to leave it to someone else” when a hazard or threat is identified. Upon analysis it sees that the concept of mutual accountability and empowerment is important to effective implementation. However in order to be accountable employees must be equipped with the requisite methods, tools and skills. Therefore effective training is imperative to effective risk management. The study also highlighted the importance of a risk champion. This is where dedicated individuals visibility identifies risks and act as mentors to others. To make this happen, specific resources such as time, money and training must be provided. This demonstrates commitment and support. Furthermore motivation theory suggests that individuals respond positively to incentives that reward achievement and performance. Consequently in order to create a culture conducive to action, ERM systems should be aligned to rewards. This will help to encourage appropriate behavior from all staff.
5.6. Benefits
We also found that the benefits arising from the implementation of ERM initiatives should be measured. Many of the respondents in this study agreed that effective enterprise risk management ultimately saves money for the organization. For example one respondent stated “makes financial sense”, while another “very good investment”. A common benefit that emerged was that good risk management practices “help us to meet legislative requirements”. They also acknowledge that it “consumes resources” which are often in short supply. A significant number of participants believed that ERM not an easy task and that it is “hard to implement risk policies in a small company”. In light of these findings it seems that it is important to determine whether these benefits or outputs have been achieved.
6. Enterprise Risk Management Audit Tool
This study has shown that there are many factors that have an impact on the success or failure of enterprise risk management initiatives. In light of this organizations must consciously develop best practice policies and systems to facilitate effective ERM. Many of these best practices are interrelated, dependent on each other and accordingly they must be considered in a holistic and integrated sense. The theoretical concepts identified in this study can be translated into concrete statements to create an enterprise risk management audit. Audits can provide value to the enterprise’s operations on many levels (e.g. strategic, operational, and tactical). First they create a common understanding about what integrated ERM means for organization at an operations level. They also provide a structure so that managers can analyze, and measure processes and systems that are essential forERM best practice so that areas for improvement can be identified and prioritized. This enables managers to ascertain whether the organization has adequate resources, systems, and processes for operating an efficient and effective ERM system. Customized solutions can be implemented that meet the specific requirements of the organization. Table 3 exhibits an ERM audit based on the key issues that have emerged from this study.
To be successful, key decision makers need to understand the rationale behind the introduction of risk management programs and buy into it as their reaction will influence the budget and implementation of risk management initiatives in the organization. Consequently it is important to assess managers’ awareness and understanding of risk initiatives as well as employees’ attitude towards their obligations to the company. Agreed policies
Table 3. Enterprise risk management audit.
and procedures were found to be important as they can help to communicate ideas and ensure effective implementation of risk management policies. The development of a formal policy can also provide an opportunity for assessing what arrangements will suit the organization. Therefore, it is important to determine whether organizations have policies on risk management issues and whether these are used and effective. We learned that in order to assess the barriers towards effective risk management in SMEs it is important to identify whether non-conformance was systematically monitored and whether corrective and preventative action systems and continuous improvements initiatives were in place. The management of risk was also found be imperative for success. It was noted that all activities in the risk process should be followed. These include identification, prioritization and evaluation of risk as well as implementation of corrective actions. Leaders and senior managers can play a pivotal role, acting as role models to more junior staff by detecting and preventing risks and hazards themselves thereby promoting risk management issues in the organization. One of the merits of risk management as an organizational tool is that it can be tailored to the needs of every organization. It is also important to note that different policies will suit different organizations depending on the culture, demographics and needs of the organization and its employees. We also found that the benefits arising and results from the implementation of such initiatives should also be measured. Research into risk management has confirmed the link between reduced costs and increased profits. Therefore it is important to determine whether these benefits or outputs have been achieved.
7. Conclusions
In the past, organizations addressed risk issues in a reactive and ad-hoc manner. Today these approaches are proved to be inefficient and outdated. Now, in order to address the needs, demands and expectations of regulatory bodies and other key stakeholders, contemporary organizations must adopt a systematic approach to effective risk management. Such an approach helps organizations to better identify, manage and control their risk activities. It also helps them to minimize defects, reduce costs and improve their corporate image. An effective risk management system provides an organization with a defined structure. However in order to implement a system, organizations must adopt best practices.
This paper reports on the findings of an exploratory qualitative study in Ireland. 31 interviews were conducted to identify and analyze challenges, issues and practices regarding enterprise risk management. The key themes that emerged centered on awareness, policies, processes, management, culture and benefits. The findings show that there is a need for an integrated approach to enterprise risk management. It seems that ERM practices are not widely employed in industry and many organizations do not consider the consequence of risk. ERM is not a strategic priority of the organizations studied. Strategies are not defined, documented or communicated and insufficient resources are dedicated to achieve risk management goals. The study found that risk identification should occur at all levels in the organization. However many responding organizations do not have a formal structured process in place to enable this. The support and commitment of senior management are essential to successful ERM implementation. They must actively engage in the process and delegate champions to create a culture to enable effective to ERM. Benefits and outcomes should also be measured.
An audit tool based on the specific findings of this research was developed and presented. This tool can help managers to diagnose gaps between their current and desired performance. It can enable decision makers to identify where successful strategies can be further exploited and pinpoint where problems, or potential, problems lie with regard to the implementation of best practice. By analyzing an organization’s activities and by quantifying the impacts of these activities the organization can respond in a planned and coordinated way and customized solutions that are grounded in best practice can be implemented.
References
- Bowling, D.M. and Rieger, L.A. (2005) Making Sense of COSO’s New Framework for Enterprise Risk Management. Bank Accounting & Finance, 18, 29-34.
- Chapman, C. (2003) Bringing ERM into Focus. The Internal Auditor, 60, 30-35.
- Thompson, R.M. (2013) A Conceptual Framework of Potential Conflicts with the Role of the Internal Auditor in Enterprise Risk Management. Accounting and Finance Research, 2, 65-77. http://dx.doi.org/10.5430/afr.v2n3p65
- Frigo, M.L. and Anderson, R.J. (2011) Strategic Risk Management: A Foundation for Improving Enterprise Risk Management and Governance. Journal of Corporate Accounting & Finance, 22, 81-88. http://dx.doi.org/10.1002/jcaf.20677
- Bromiley, P., McShane, M.K., Nair, A. and Rustambekov, E. (2014) Enterprise Risk Management: Review, Critique, and Research Directions. Forthcoming: Long Range Planning.
- McShane, M.K., Nair, A. and Rustambekov, E. (2011) Does Enterprise Risk Management Increase Firm Value? Journal of Accounting, Auditing & Finance, 26, 641-658. http://dx.doi.org/10.1177/0148558X11409160
- Hoyt, R.E. and Liebenberg, A.P. (2011) The Value of Enterprise Risk Management. Journal of Risk and Insurance, 78, 795-822. http://dx.doi.org/10.1111/j.1539-6975.2011.01413.x
- McNeil, A.J. (2013) Enterprise Risk Management. Annals of Actuarial Science, 7, 1-2. http://dx.doi.org/10.1017/S1748499512000334
- Arena, M., Arnaboldi, M. and Azzone, G. (2010) The Organizational Dynamics of Enterprise Risk Management. Accounting, Organizations and Society, 35, 659-675. http://dx.doi.org/10.1016/j.aos.2010.07.003
- Önder, Ş. and Ergin, H. (2012) Determiners of Enterprise Risk Management Applications in Turkey: An Empirical Study with Logistic Regression Model on the Companies Included in ISE (Istanbul Stock Exchange). Business and Economic Horizons, 7, 19-26.
- Mikes, A. (2011) From Counting Risks and Making Risks Count: Boundary-Work in Risk Management. Accounting, Organizations and Society, 36, 226-245. http://dx.doi.org/10.1016/j.aos.2011.03.002
- Nocco, B. and Stulz, R. (2006) Enterprise Risk Management: Theory and Practice. Journal of Applied Corporate Finance, 18, 8-20. http://dx.doi.org/10.1111/j.1745-6622.2006.00106.x
- Carona, F., Vanthienena, J. and Baesensa, B. (2013) A Comprehensive Investigation of the Applicability of Process Mining Techniques for Enterprise Risk Management. Computers in Industry, 64, 464-475. http://dx.doi.org/10.1016/j.compind.2013.02.001
- Smithson, C. and Simkins, B. (2005) Does Risk Management Add Value? A Survey of the Evidence. Journal of Applied Corporate Finance, 17, 8-17. http://dx.doi.org/10.1111/j.1745-6622.2005.00042.x
- Beasley, M., Branson, B. and Hancock, B. (2009) Report on the Current State of Enterprise Risk Oversight. ERM Initiative at North Carolina State University, Raleigh.
- Barton, T.L., Shenkir, W.G. and Walker, P.L. (2002) Making Enterprise Risk Management Pay Off. FT Press, Upper Saddle River.
- Kleffner, A.E., Lee, R.B. and McGannon, B. (2003) The Effect of Corporate Governance on the Use of Enterprise Risk Management: Evidence from Canada. Risk Management and Insurance Review, 6, 53-73. http://dx.doi.org/10.1111/1098-1616.00020
- Mitchell, V.W. (1995) Organizational Risk Perception and Reduction: A Literature Review. British Journal of Management, 6, 115-133. http://dx.doi.org/10.1111/j.1467-8551.1995.tb00089.x
- Macdonald, D. (2004) Practical Hazops, Trips and Alarms. Elsevier, Oxford.
- Sadgrove, K. (2005) The Complete Guide to Business Risk Management. Gower Publishing, Ltd., London.
- Harland, C., Brenchley, R. and Walker, H. (2003) Risk in Supply Networks. Journal of Purchasing and Supply Management, 9, 51-62. http://dx.doi.org/10.1016/S1478-4092(03)00004-9
- Smith, P.G. and Merritt, G.M. (2002) Proactive Risk Management—Controlling Uncertainty in Product Development. Productivity Press, New York.
- Gericke, K. and Blessing, L. (2008) A Framework to Understand Project Robustness. Proceedings of 3rd International Conference on Design Computing and Cognition (DCC08), Atlanta, 21-22 June 2008, 919-926.
- Raghavan, R.S. (2005) Risk Management in SMEs. The Chartered Accountant, 6, 528-535.
- Pojasek, R.B. (2008) Quality Toolbox: Risk Management 101. Environmental Quality Management, 17, 95-101. http://dx.doi.org/10.1002/tqem.20180
- Ammar, A., Berman, K. and Sataporn, A. (2007) A Review of Techniques for Risk Management in Projects. Benchmarking: An International Journal, 14, 22-36.
- Leopoulos, V.N., Kirytopoulos, K.A. and Malandrakis, C. (2006) Risk Management for SMEs: Tools to Use and How. Production Planning & Control, 17, 322-332. http://dx.doi.org/10.1080/09537280500285136
- Kim, C.H., Yim, D.S. and Weston, R.H. (2001) An Integrated Use of IDEF0, IDEF3 and Petri Net Methods in Support of Business Process Modelling. Proceedings of the Institution of Mechanical Engineers, Part E: Journal of Process Mechanical Engineering, 215, 317-329.
- Kostiuk, P.F. and Ky, P. (2004) Use of Generalized Activity Network Models for Analysis of European ATM Development Projects. 1-9.
- Golenko-Ginzburg, D. and Blokh, D. (1997) A Generalized Activity Network Model. The Journal of the Operational Research Society, 48, 391-400.
- Hallikas, J., Kaarvonen, I., Pulkkinen, U., Virolainen, V.M. and Tuominen, M. (2004) Risk Management Processes in Supplier Networks. International Journal of Production Economics, 90, 47-58. http://dx.doi.org/10.1016/j.ijpe.2004.02.007
- Rooney, J.J., Vanden Heuvel, L.N. and Lorenzo, D.K. (2009) Cause and Effect. Quality Progress, 42, 38-44.
- Pillay, A. and Wang, J. (2003) Modified Failure Mode and Effects Analysis Using Approximate Reasoning. Reliability Engineering & System Safety, 79, 69-85. http://dx.doi.org/10.1016/S0951-8320(02)00179-5
- Aven, T. and Heide, B. (2009) Reliability and Validity of Risk Analysis. Reliability Engineering & System Safety, 94, 1862-1868. http://dx.doi.org/10.1016/j.ress.2009.06.003
- Mobey, A. and Parker, D. (2002) Risk Evaluation and Its Importance to Project Implementation. Work Study, 51, 202- 208. http://dx.doi.org/10.1108/00438020210430760
- Sun, Y., Huang, R., Chen, D. and Li, H. (2008) Fuzzy Set-Based Risk Evaluation Model for Real Estate Projects. Tsinghua Science & Technology, 13, 158-164. http://dx.doi.org/10.1016/S1007-0214(08)70143-3
- Simons, R. (2000) Performance Measurement & Control Systems for Implementing Strategy Text and Cases. Prentice Hall, Upper Saddle River.
- Jeong, K.Y., Cho, H.B. and Phillips, D.T. (2008) Integration of Queuing Network and IDEF3 for Business Process Analysis. Business Process Management Journal, 14, 471-482. http://dx.doi.org/10.1108/14637150810888028
- Dorador, J.M. and Young, R.I.M. (2000) Application of IDEF0, IDEF3 and UML Methodologies in the Creation of Information Models. International Journal of Computer Integrated Manufacturing, 13, 430-445. http://dx.doi.org/10.1080/09511920050117928
- Ang, C.L. (1999) Enactment of IDEF0 Models. International Journal of Production Research, 37, 3383-3397. http://dx.doi.org/10.1080/002075499190103
- Huang, X.G., Wong, Y.S., Liu, Z.J. and Qiu, Z.M. (2005) Critical-Path-Analysis-Based Dynamic Component Supplier Optimization. International Journal of Computer Integrated Manufacturing, 18, 702-709. http://dx.doi.org/10.1080/09511920500324290
- Cobb, B.R. (2009) Influence Diagrams for Capacity Planning and Pricing under Uncertainty. Journal of Management Accounting Research, 21, 75-97. http://dx.doi.org/10.2308/jmar.2009.21.1.75
- Cobb, B.R. and Shenoy, P.P. (2008) Decision Making with Hybrid Influence Diagrams Using Mixtures of Truncated Exponentials. European Journal of Operational Research, 186, 261-275. http://dx.doi.org/10.1016/j.ejor.2007.01.036
- Detwarasiti, A. and Shachter, R.D. (2005) Influence Diagrams for Team Decision Analysis. Decision Analysis, 2, 207- 228. http://dx.doi.org/10.1287/deca.1050.0047
- Howard, R.A. and Matheson, J.E. (2005) Influence Diagrams. Decision Analysis, 2, 127-143. http://dx.doi.org/10.1287/deca.1050.0020
- Hughes, B., Hall, M. and Rygaard, D. (2009) Using Root-Cause Analysis to Improve Risk Management. Professional Safety, 54, 54-55.
- Arabian-Hoseynabadi, H., Oraee, H. and Tavner, P.J. (2010) Failure Modes and Effects Analysis (FMEA) for Wind Turbines. International Journal of Electrical Power & Energy Systems, 32, 817-824. http://dx.doi.org/10.1016/j.ijepes.2010.01.019
- Tunchel, G. and Alpan, G. (2010) Risk Assessment and Management for Supply Chain Networks: A Case Study. Computers in Industry, 61, 250-259. http://dx.doi.org/10.1016/j.compind.2009.09.008
- Chin, K.S., Wang, Y.M., Poon, G.K.K. and Yang, J.B. (2009) Failure Mode and Effects Analysis Using a Group-based Evidential Reasoning Approach. Computers & Operations Research, 36, 1768-1779. http://dx.doi.org/10.1016/j.cor.2008.05.002
- Van Leeuwen, J.F., Nauta. J., De Kaste, D., Odekerken-Rombouts, Y.M.C., Oldenhof, M.T., Vredenbregt, M.J. and Barends, D.M. (2009) Risk Analysis by FMEA as an Element of Analytical Validation. Journal of Pharmaceutical and Biomedical Analysis, 50, 1085-1087. http://dx.doi.org/10.1016/j.jpba.2009.06.049
- Ferdous, R., Khan, F.I., Veitch, B. and Amyotte, P.R. (2007) Methodology for Computer-Aided Fault Tree Analysis. Process Safety and Environmental Protection, 85, 70-80. http://dx.doi.org/10.1205/psep06002
- Reay, K.A. and Andrews, J.D. (2002) A Fault Tree Analysis Strategy Using Binary Decision Diagrams. Reliability Engineering & System Safety, 78, 45-56. http://dx.doi.org/10.1016/S0951-8320(02)00107-2
- Bernroider, E. (2002) Factors in SWOT Analysis Applied to Micro, Small-to-Medium, and Large Software Enterprises: An Austrian Study. European Management Journal, 20, 562-573. http://dx.doi.org/10.1016/S0263-2373(02)00095-6
- Markovska, N., Taseska, V. and Pop-Jordanov, J. (2009) SWOT Analysis of the National Energy Sector for Sustainable Energy Development. Energy, 34, 752-756. http://dx.doi.org/10.1016/j.energy.2009.02.006
- Tixier, J., Dusserre, G., Salvi, O. and Gaston, D. (2002) Review of 62 Risk Analysis Methodologies of Industrial Plants. Journal of Loss Prevention in the Process Industries, 15, 291-303. http://dx.doi.org/10.1016/S0950-4230(02)00008-6
- Kaplan, S. (1997) The Words of Risk Analysis. Risk Analysis, 17, 407-417. http://dx.doi.org/10.1111/j.1539-6924.1997.tb00881.x
- Solomon, K., Giesy, J. and Jones, P. (2000) Probabilistic Risk Assessment of Agrochemicals in the Environment. Crop Protection, 19, 649-655. http://dx.doi.org/10.1016/S0261-2194(00)00086-7
- El-Gayar, O.F. and Leung, P.S. (2001) A Multiple Criteria Decision Making Framework for Regional Aquaculture Development. European Journal of Operational Research, 133, 462-482. http://dx.doi.org/10.1016/S0377-2217(00)00183-1
- Dey, P.K. (2012) Project Risk Management Using Multiple Criteria Decision-Making Technique and Decision Tree Analysis: A Case Study of Indian Oil Refinery. Production Planning & Control: The Management of Operations, 23, 903-921. http://dx.doi.org/10.1080/09537287.2011.586379
- Knechel, W.R. (2007) The Business Risk Audit: Origins, Obstacles and Opportunities. Accounting, Organizations and Society, 32, 383-408. http://dx.doi.org/10.1016/j.aos.2006.09.005
- Curtis, E. and Turley, S. (2007) The Business Risk Audit-A Longitudinal Case Study of an Audit Engagement. Accounting, Organizations and Society, 32, 439-461. http://dx.doi.org/10.1016/j.aos.2006.09.004
- Yin, R.K. (2002) Case Study Research, Design and Methods. 3rd Edition, Sage, Newbury Park.
- Creswell, J.W. (2003) Research Design Qualitative, Quantitative, and Mixed Methods Approaches. 2nd Edition, Sage Publications, Thousand Oaks.
- Voss, C., Tsikriktsis, N. and Frohlich, M. (2002) Case Research in Operations Management. International Journal of Operations and Production Management, 22, 195-219. http://dx.doi.org/10.1108/01443570210414329
- Robson, C. (2002) Real World Research. 2nd Edition, Blackwell Publishing, Hoboken.
- Lam, J. (2014) Enterprise Risk Management: From Incentives to Controls. John Wiley & Sons, Hoboken. http://dx.doi.org/10.1002/9781118836477
- Hopkin, P. (2012) Fundamentals of Risk Management: Understanding, Evaluating and Implementing Effective Risk Management. Kogan Page Publishers, London.
- Moeller, R.R. (2007) COSO Enterprise Risk Management: Understanding the New Integrated ERM Framework. John Wiley & Sons, Hoboken.


