Circuits and Systems
Vol.07 No.09(2016), Article ID:68545,10 pages
10.4236/cs.2016.79192
Optimization of Disjoints Using WDM-PON in an Optical Network
K. Sasi Kala Rani1, A. Renuga Devi2, J. Suganthi1
1Hindusthan Institute of Technology, Coimbatore, India
2Hindusthan College of Engineering and Technology, Coimbatore, India

Copyright © 2016 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 28 April 2016; accepted 15 May 2016; published 18 July 2016
ABSTRACT
An optical network is a type of data communication network built with optical fibre technology. It utilizes optical fibre cables as the primary communication medium for converting data and passing data as light pulses between sender and receiver nodes. The major issue in optical networking is disjoints that occur in the network. A polynomial time algorithm Wavelength Division Multiplexing-Passive Optical Networking (WDM-PON) computes disjoints of an optical network and reduces the count of disjoints that occur in the network by separating Optical Network Units (ONU) into several virtual point-to-point connections. The Arrayed Waveguide Grating (AWG) filter is included in WDM-PON to avoid the traffic in the network thereby increasing the bandwidth capacity. In case of a failure or disjoint Ant Colony Optimization (ACO) algorithm is used to find the optimized shortest path for re-routing. For enhanced security, modified Rivert Shamir Adleman (RSA) algorithm encrypts the message during communication between the nodes. The efficiency is found to be improved in terms of delay in packet delivery, longer optical reach, optimized shortest path, packet error rate.
Keywords:
Optical Network, Disjoints, Wavelength Division Multiplexing, Passive Optical Networking, Optical Network Units, Arrayed Waveguide Grating, Ant Colony Optimization

1. Introduction
An optical networking is a means of communication that uses signals encoded onto light to transmit information among various nodes of a telecommunications network. Using optical fibre cable by passing lights the nodes get communicated [1] . Considering an optical network, the Wavelength Division Multiplexing (WDM) collects input from many source channel and sends it to the same destination. In a WDM optical networks, the data packets are transmitted along light paths. A light path between nodes does not have wavelength converters, must maintain the same wavelength throughout the entire path; it leads to wavelength continuity constraint. The major issue is cuts appeared in that network due to optical links carry a very high volume of data, the link get disjoint or dislink. Hence, survivability is the most important in communication in the network. These dislinks have to be computed within the polynomial time algorithm.
2. Related Works
In the last few years an intense research activity has been addressed to the problem of optical network disjoints [2] . The networks are more and more frequently challenged by disjoint or dislink problems and to update the existing ones by the continuous re-routed back-up path. Due to the growth of the demand of bandwidth for new applications such as video and multimedia streams and advanced digital services, the network can carry high bandwidth of data causes disjoint in the network. These disjoints have to be computed by using various algorithm from past to present with shortest path. The recent attitude is towards the secured transmission and optimized shortest path.
Arunabha Sen [3] focused on tolerating a single link failure in a network. The active and back-up path must maintain the constant wavelength throughout the entire path. The link and node disjoint problems are intractable under wavelength continuity constraint. Using Integer Linear Programming (ILP) the disjoint problem is easier to solve. The suurballe’s algorithm, Active Path First (APF) helps to find the best path and active link path when dislink happens [4] . By removing the active dislink path or reserved path for the node and creating the back-up path. The Enhanced Active Path First (APFE) is same as the APF but additionally it determines the cost for every link, bandwidth and life time of the path also noted. It doesn’t listen to the multiple link failures occurred in the network because of disjoint.
Jian Quang Hu [5] shared to compute the multiple dislinks occurred in an optical network. The network failure was due to fibre cuts, hardware and software failures or power outages occurred in the networks. The heuristic algorithm, exhaustive search algorithm helps to finding the diversely routed path and Integer Linear Programming (ILP) algorithm guaranteed on minimum cost SRLG diverse routing problem [6] . The Mixed Integer Linear Programming (MILP) had an integer optimal solution which implemented on shared risks and reduced running time. But it is effective only for small number of nodes and cost is not mentioned.
Wenbo He [7] concentrated on generalized loop recovery in an optical mesh network. The term loop-back to provide pre-planned recovery of link or node failure. To achieve the characteristics such as speed, transparency and flexibility, the heuristic algorithm is used. It selects the direction for recovery from link or node failures in the network. The Operation Management Protocol Algorithm (OMPA) which enables the distributed application for generalized loop-backs [8] . It provides great flexibility in planning the configuration of a network and bandwidth utilization. But it is less efficient and works only on pre-planned information.
Jason P. Jue [9] investigated the subject of reliability via two link-disjoint paths in a mesh networks. It mainly considers on how reliable the two-path protection can be and how to achieve maximum reliability in the network. The heuristic algorithms, Two step Reliability Algorithm (TRA) and Maximum Reliability Algorithm (MRA) used to find the two link disjoint path with maximum reliability [10] . It gives maximum reliability against a single link failure. The time and performance efficiency is also high. But, it is based on theoretical one not by practical proof.
Mei Yang [11] presented a unified algorithm to computing the minimum cost multiple paths in the networks. The Min-Max search algorithm and Min-Max compute algorithm is used to solve the disjoint problem with minimum link or node sharing may be considered with minimum cost. The Minimum Cost Network Flow (MCNF) algorithm is used to finding the k-best paths with a defined collection of path problems with prioritized minimization of objectives [12] . It is more efficient at the time of path existing in a network. But there will be confusion occurs while using more number of nodes.
Hyeong-Ah Choi [13] investigated on double link failure recovery in wavelength division multiplexing optical networks. The three loop recovery methods are used for recovering double link failures to pre-computes the back-up for links presented. The heuristic algorithm, Maximum Arbitrary Double-link Protection Algorithm (MADPA) computes the dislinks by three phases such as pre-processing, concentration and expansion [14] . The optimized performance in recovering the double-link failures. But, it works only when the graph is planar.
2.1. Computing Disjoints in a Network Using Link Disjoint Light Path (LDLP)
To compute the disjoint or dislinks occurred in the network during communication between the nodes, the Link Disjoint Light Path (LDLP) algorithm is used. The active disjoint path is substituted with the back-up path using reduced 2-tree algorithm. It is used for isolating the failures one by one i.e. separating the whole network into an individual networks which has degree not more than two except source and destination in the network and it doesn’t form a triangle [15] . It is linear time algorithm which follows the contraction operations to compute the dislinks happened in the network. It also supports the different range of wavelengths for communication i.e. wavelength continuity constraint get avoided. It works even the network topology is a partial 2-tree. Finally, the running time of the algorithm is O(nW2), where n is the number of nodes and W is the number of wavelengths per link.
2.2. Reduced 2-Tree Algorithm
Input: A graph g, source s and destination t with their intermediate links
Output: Reduced 2-Tree
Steps:
1) Get the intermediate links and store the nodes in queue
2) Isolate the nodes-degree more than 2
3) Update the degrees of two nodes-doesn’t form a triangle
4) Insert it into the queue if degree is 1
End
2.3. LDLP Algorithm
Input: A graph G, source S, destination T with wavelengths
Output: A back-up path for link disjoint
Steps
1) Compute the reduced 2-tree
a) Find the dislinks occurred in the network
b) Isolate the network which has degree more than two
c) Update the nodes which doesn’t form a triangle
2) Convert reduced 2-tree into a triangle
d) Update all the link attributes
e) Reforming the reduced 2-tree into a complete network
3) Compute the shortest path for link disjoints
4) Stop when path does not found
5) Extract the solutions
End.
The drawbacks of LDLP algorithm are:
・ Limited to efficient performance by reducing the number of disjoints occurred in the network.
・ Disjoint size may not be optimal because of the unknown duration of isolation of nodes.
・ Takes more time consumption for re-routing back-up paths.
・ Does not concentrate on secured transmission with high bandwidth range.
3. Proposed WDM-PON Method
To completely address these challenges over LDLP algorithm in an optical networking, Wavelength Division Multiplexing-Passive Optical Networking (WDM-PON) algorithm is proposed. WDM-PON is a passive optical networking approach where currently being developed by several companies that can be used to more adequately address these challenges over fibre-based networks [16] . A WDM-PON design can be used to separate Optical-Network Units (ONUs) into several virtual point-to-point connections over the same physical infrastructure, a feature that enables efficient use of fibre compared to point-to-point Ethernet and offers lower latency than Time Division Multiplexing (TDM) based approaches. A notable advantage of this approach is the combination of high capacity per user, high security, and longer optical reach. WDM-PON therefore is highly suitable for applications such as mobile backhaul or business Ethernet service provision.
WDM-PON also will enable operators to build converged networks and consolidate existing access networks, including potentially eliminating central offices to reduce cost while boosting performance [17] . The Arrayed Waveguide Grating (AWG) filter used in WDM-PON is used to avoid traffic in the network that separates the wavelength for individual delivery and increases the bandwidth capacity for communication. It provides flexible access to the networks.
For optimal shortest path Ant Colony Optimization (ACO) algorithm is used for solving computational problems which can be reduced to finding good paths through graphs. The algorithm was aiming to search for an optimal path in a graph, based on the behaviour of ants seeking a path between their colony and a source of food. Ant colony optimization algorithms have been applied to many combinatorial optimization problems [18] . It is used to produce near-optimal solutions to the travelling salesman problem. They have an advantage over simulated annealing and genetic algorithm approaches of similar problems when the graph may change dynamically; the ant colony algorithm can be run continuously and adapt to changes in real time. Here, ACO helps to find the optimized shortest path for an active dislink path in the network.
The Rivert Shamir Adleman (RSA) algorithm is used to providing security in the network to avoid the unwanted hacking or misusing of data. A user of RSA creates and then publishes a public key based on the two large prime numbers, along with an auxiliary value. The prime numbers must be kept secret [19] . Anyone can use the public key to encrypt a message, but with currently published methods, if the public key is large enough, only someone with knowledge of the prime numbers can feasibly decode the message. It decrypts the original message received at destination.
Hence, the survival routing in the network is done by reducing the count of disjoints occurred in the network and improved security with optimized shortest path using ant colony optimization algorithm.
4. Disjoint Reduction
An increased growth in requirements for network leads to new approaches that make the improved performance in bandwidth scalability, quality of service, support of the energy traffic patterns and broadcast standards. The advanced method Wavelength Division Multiplexing-Passive Optical Networking (WDM-PON) is used to compute the disjoint or dislinks that occurred in the network which improves the efficiency with high bandwidth and less time for communication between the nodes in the network [20] . The Passive Optical Networking (PON) is a tele-communication network that uses a point-to-multipoint fibre to serve multiple premises. It reduces the amount of fibre and central office equipment and provides secure passive optical networking. Easy for upgrading the network using WDM-PON and provide flexible access to the network.
4.1. Wavelength Division Multiplexing-Passive Optical Networking (WDM-PON)
The networks may be insufficient for many high-bandwidth services in the future and the economics of new fibre deployments are often challenging; nevertheless, fibre will undoubtedly push deeper into access networks to support business services, mobile backhaul, multitenant buildings or fibre to the cabinet, and in some cases Fibre To The Home (FTTH) too. Meeting today’s fibre-based approaches, including TDM-PON and active point-to- point Ethernet, probably won't meet the likely requirements of the next generation of bandwidth-intensive traffic, either [21] .
The WDM-PON is a passive optical networking approach currently being developed by several companies shown in Figure 1 that can be used to more adequately address these challenges over fibre-based networks [22] . A WDM-PON design can be used to separate Optical-Network Units (ONUs) into several virtual point-to-point connections over the same physical infrastructure, a feature that enables efficient use of fibre compared to point-to-point Ethernet and offers lower latency than TDM-based approaches shown in Figure 1. A notable advantage of this approach is the combination of high capacity per user, high security, and longer optical reach. WDM-PON therefore is highly suitable for applications such as mobile backhaul or business Ethernet service provision [23] . WDM-PON also will enable operators to build converged networks and consolidate existing access networks, including potentially eliminating central offices to reduce cost while boosting performance.
If the WDM-PON system is properly designed, then it's possible to mix different transmission technologies. By following certain design rules during the installation of the WDM-PON system, it’s possible to allow step- wise channel upgrades to higher bit rates when the demand arises [24] . These design rules ensure that channel
Figure 1. WDM-PON structure.
OSNR requirements will be met in the presence of reflections and that inter-channel crosstalk is avoided. The result is an open and flexible access network that can support many applications and services over the same infrastructure. WDM-PON thus becomes an optical option for the access network as and where it makes sense.
4.2. AWG Filter
WDM-PON provides the dedicated bandwidth of a point-to-point network and the fibre sharing inherent in PONs. WDM-PON uses an Arrayed-Waveguide-Grating (AWG) filter that separates the wavelengths for individual delivery to the subscriber ONUs. ONUs can be used at the subscriber sites to simplify inventory and spare-part handling shown in Figure 2. The optics not only simplifies operations, but also reduces deployment costs, since they don’t need the expensive wavelength-stability components that traditional fixed and tunable optics require [25] . There are multiple approaches to the ONU technology.
Given its ability to help service providers cope with current bandwidth demands as well as the next potential broadband access bottleneck, WDM-PON is becoming an important technology to consider in terms of its benefits and market timing [26] . As with any emerging technology, service providers need to consider the optimal strategy for initial deployment of WDM-PON. That includes how they could use WDM-PON for additional network applications as the technology matures and its costs come down.
5. Optimal Shortest Path
For optimal shortest path Ant Colony Optimization (ACO) algorithm is used. It is used to find the optimized shortest path for the data communication in the network. The ACO algorithm was called the Ant system and it was aimed to solve the travelling salesman problem, in which the goal is to find the shortest round-trip to link a series of nodes [27] . The general algorithm is relatively simple and based on a set of ants, each making one of the possible round-trips along the nodes in the network [28] . At each stage, the ant chooses to move from one node to another according to some rules:
ACO Algorithm
Input: A graph G, source S, destination T
Output: Optimized shortest path
Condition: It must visit each node exactly once
Initialization: Number of iterations, initial node, intensity of path
1) A distant node has less chance of being chosen
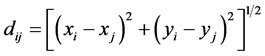 //dij-distance between two nodes x and y.
//dij-distance between two nodes x and y.
2) The more intense the update trail laid out on an edge between two nodes, the greater the probability that that edge will be chosen.
3) Having completed its journey, the ant deposits more on all edges it traversed, if the journey is short.
4) After each iteration, trails of nodes path are updated
where,∆τij-deposited path.
p-rate of path travelled decay per time interval.
Figure 2. AWG filter.
τij(t)-intensity of path.
t-time.
n-count.
End.
Hence, the ACO algorithm helps to find the best optimized for the active dislink path with reduced cost and it takes less time consumption for re-routing the back-up path [29] . The accuracy of the algorithm is high than the other shortest path methods.
6. Secured Transmission of Data
The secured data transmission is provided by one of the best cryptography method called Rivert Shamir Adleman (RSA) for encryption and decryption [30] . It encrypts the data using private and public key created by the user and send it to the destination. After performing specified number of rounds with the help of the key values the data get decrypted and used by receiver. For encryption, the equation follows as:
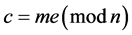 (1)
(1)
where m represents integer, public key (n,e). For decrypting the value send to receiver using the equation as:
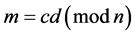 (2)
(2)
The term d represents the secret private key value which helps for deciphering the data while communication between the nodes.
Thus, the RSA algorithm provides security to the data during communication in the network.
7. Performance Evaluation
To validate WDM-PON with existing LDLP algorithm it considers following parameters such as reduction in disjoint, optimized shortest path, time consumption in delivering the packets, reducing packet error rate. The simulation result is based on 100 nodes. The WDM-PON improves the performance by
・ Delay in packet delivery
・ Longer optical reach
・ Optimized shortest path
・ Reducing packet error rate
The delay rate of packets delivered from source to destination is shown in Figure 3. WDM-PON reduces the delay rate of packets. WDM permits a fibre to carry many separate and independent channels. Multiple optical carriers at different wavelengths are modulated and transmitted over the same fibre. Hence delay rate will be less since more data can be transferred simultaneously. The shortest path can be estimated using ACO, which takes less time to estimate the shortest path.
The AWG filter avoids the traffic in the network and thus it increases the bandwidth capacity. Obviously, it leads to longer optical reach with reduced disjoint. From Figure 4, it is observed that there is a deviation in the
Figure 3. Delay in packet delivery.
Figure 4. Longer optical reach.
disjoint reduction when the network contains above 50 nodes. The data will be reached with less time consumption due to longer optical reach using WDM-PON than the LDLP algorithm and other previous existing methods.
It is observed that there is a drastic deviation in run time when applying ACO algorithm to find shortest path in WDM optical network. If the number of nodes in the network increases, the run time of ACO reduces because the nodes are randomly selected. While selecting the nodes, disjoint nodes are eliminated for traversal. But
Figure 5. Packet error rate.
LDLP algorithm consumed more time because it traverses all the nodes in the network to find shortest path.
By avoiding the dislinks occurred in the network using WDM-PON, it reduces the count of packets getting error due to disjoint in the network and secured transmission improves the performance using RSA algorithm as shown in Figure 5.
8. Conclusion
The polynomial time algorithm WDM-PON computes the link-disjoint light paths in an optical network and receives a lot of attention with high performance, longer optical reach. It avoids the disjoint occurred in the network upto 70% than the previous methods and LDLP algorithm. The arrayed waveguide grating filter is used to avoid the traffic in the network and increases the bandwidth capacity. The ACO algorithm solves the computational problem in finding the path and gives result with optimized shortest path. The modified RSA algorithm admits simple solutions to security problems during transmission of data between source and destination. In addition, the WDM-PON algorithm focuses on technology towards higher bit rates of transmission and longer reach.
Cite this paper
K. Sasi Kala Rani,A. Renuga Devi,J. Suganthi, (2016) Optimization of Disjoints Using WDM-PON in an Optical Network. Circuits and Systems,07,2207-2216. doi: 10.4236/cs.2016.79192
References
- 1. Xue, G., Gottapu, R., Fang, X., Yang, D.J. and Thulasiraman, K. (2014) A Polynomial-Time Algorithm for Computing Disjoint Lightpath Pairs in Minimum Isolated-Failure-Immune WDM Optical Networks. IEEE/ACM Transactions on Networking, 22, 470-483.
- 2. Li, C., McCormick, S.T. and Simchi-Levi, D. (1992) Finding Disjoint Paths with Different Path Costs: Complexity and Algorithms. Networks, 22, 653-667.
http://dx.doi.org/10.1002/net.3230220705 - 3. Medard, M., Barry, R.A., Finn, S.G., He, W. and Lumetta, S.S. (2002) Generalized Loop-Back Recovery in Optical Mesh Networks. IEEE/ACM Transactions on Networking, 10, 153-164.
http://dx.doi.org/10.1109/90.986592 - 4. She, Q., Huang, X. and Jue, J.P. (2010) How Reliable Can Two-Path Protection Be? IEEE/ACM Transactions on Networking, 18, 922-933.
http://dx.doi.org/10.1109/TNET.2009.2036911 - 5. Chlamtac, I., Ganz, A. and Karmi, G. (1992) Lightpath Communications: An Approach to High Bandwidth Optical WAN’s. IEEE Transactions on Communications, 40, 1171-1182.
http://dx.doi.org/10.1109/26.153361 - 6. Zheng, S.Q., Wang, J., Yang, B. and Yang, M. (2010) Minimum-Cost Multiple Paths Subject to Minimum Link and Node Sharing in a Network. IEEE/ACM Transactions on Networking, 18, 1436-1449.
http://dx.doi.org/10.1109/TNET.2010.2044514 - 7. Andersen, R., Chung, F., Sen, A. and Xue, G. (2004) On Disjoint Path Pairs with Wavelength Continuity Constraint in WDM Networks. Twenty-Third Annual Joint Conference of the IEEE Computer and Communications Societies, 1, 524-535.
http://dx.doi.org/10.1109/infcom.2004.1354524 - 8. Choi, H., Subramaniam, S. and Choi, H.A. (2002) On Double-Link Failure Recovery in WDM Optical Networks. Proc. IEEE INFOCOM, Washington DC, 23-27 June 2002, 808-816.
- 9. Makki, K., Broussard, J. and Pissinou, N. (2000) On Optical Communications Networks and Wideband Network Architecture. Computer Communications, 23, 901-911.
http://dx.doi.org/10.1016/S0140-3664(99)00219-4 - 10. Ramaswami, R. and Sivarajan, K.N. (1998) Optical Networks: A Practical Perspective. Morgan Kaufmann.
- 11. Mukherjee, B. (1997) Optical Communication Networks. McGraw Hill, New York.
- 12. Doshi, B., et al. (1999) Optical Network Design and Restoration. Bell Laboratories Technical and Journal, 4, 58-83.
http://dx.doi.org/10.1002/bltj.2147 - 13. Xu, D., Chen, Y., Xiong, Y., Qiao, C. and He, X. (2004) On Finding Disjoint Paths in Single and Dual Link Cost Networks. Proc. IEEE INFOCOM, Hong Kong, 9-11 March 2004, 705-715.
- 14. Bhandari, R. (1994) Optimal Diverse Routing in Telecommunication Fibre Networks. Proc. IEEE INFOCOM, Toronto, 12-16 Jun 1994, 1498-1508.
- 15. Mukherjee, B. (2006) Optical WDM Networks. Springer, New York.
- 16. Kodialm, M. and Lakshman, T.V. (2001) Dynamic Routing of locally Restorable Bandwidth Guaranteed Tunnels Using Aggregated Link Usage Information. Proceedings of 12th Annual Joint Conference of the IEEE Computer and Communications Societies, Vol. 1, Anchorage, 22-26 April 2001, 376-385.
http://dx.doi.org/10.1109/infcom.2001.916720 - 17. Dravida, S. anderson, J., Doshi, B.T. and Harshavardhana, P. (1994) Fast Restoration of ATM Networks. IEEE Journal on Selected Areas in Communications, 12, 128-136.
http://dx.doi.org/10.1109/49.265712 - 18. Li, G.Z., Doverspike, B. and Kalmanek, C. (2001) Fibre Span Failure Protection in Mesh Optical Networks. Proceedings of SPIE Optical Networking and Communications, Vol. SPIE 4599, Colorado, 19-24 August 2001, 130-142.
- 19. Wu, T.H. (1992) Fibre Network Service Survivability. Artech House, London.
- 20. Xue, G., Chen, L. and Thulasiraman, K. (2003) Quality-of-Service and Quality Protection Issues in Preplanned Recovery Schemes Using Redundant Trees. IEEE Journal on Selected Areas in Communications, 21, 1332-1345.
http://dx.doi.org/10.1109/JSAC.2003.816597 - 21. Medard, M., Finn, S.G., Barry, R.A. and Gulhger, R.G. (1999) Redundant Trees for Preplanned Recovery in Arbitrary Vertex-Redundant or Edge-Redundant Graphs. IEEE/ACM Transactions on Networking, 7, 641-652.
http://dx.doi.org/10.1109/90.803380 - 22. Modiano, E. and Narula-Tam, A. (2002) Survivable Lightpath Routing: A New Approach to the Design of WDM-Based Networks. IEEE Journal on Selected Areas in Communications, 20, 800-809.
http://dx.doi.org/10.1109/JSAC.2002.1003045 - 23. Kurant, M. and Thiran, P. (2007) Survivable Routing of Mesh Topologies in IP-over-WDM Networks by Recursive Graph Contraction. IEEE Journal on Selected Areas in Communications, 25, 922-933.
http://dx.doi.org/10.1109/JSAC.2007.070606 - 24. Medard, M., Finn, S.G. and Barry, R.A. (1997) A Novel Approach to Automatic Protection Switching Using Trees. ICC’97 Montreal, towards the Knowledge Millennium, Montreal, 8-12 Jun 1997, 272-276.
- 25. Suurballe, J.W. and Tarjan, R.E. (1984) A Quick Method for Finding Shortest Pairs of Disjoint Paths, Networks, 14, 325-336.
http://dx.doi.org/10.1002/net.3230140209 - 26. Lee, K. and Siu, K. (2001) An Algorithmic Framework for Protection Switching WDM Networks. National Fiber Optic Engineers Conference, Baltimore, 8-12 July 2001, 402-410.
- 27. Jukan, A. (2001) AoS-Based Wavelength Routing in Multi-Service WDM Networks. Springer-Verlag, Wien.
http://dx.doi.org/10.1007/978-3-7091-6247-7 - 28. Ghani, N., Dixit, S. and Wang, T.S. (1999) Channel Provisioning for Higher Layer Protocols in WDM Networks. Proceeding of SPIE All Optical Configuration: Architecture, Control and Management Issues, Boston, 25 August 1999.
- 29. Hu, J.Q. (2003) Diverse Routing in Optical Mesh Networks. IEEE Transactions on Communications, 51, 489-494.
http://dx.doi.org/10.1109/TCOMM.2003.809779 - 30. Yuan, S. and Jue, J.P. (2005) Dynamic Lightpath Protection in WDM Mesh Networks under Wavelength-Continuity and Risk-Disjoint Constraints. Computer Networks, 48, 91-112.
http://dx.doi.org/10.1016/j.comnet.2004.10.013







