Journal of Computer and Communications
Vol.03 No.06(2015), Article ID:57603,12 pages
10.4236/jcc.2015.36012
Energy Consumption and Fault Tolerance in the MAC Protocols for WSN
Ridha Azizi
Computer Technology Department, High Institute of Technological Studies of Sousse (ISET), Sousse, Tunisia
Email: azizi_ridha@yahoo.fr
Copyright © 2015 by author and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 17 April 2015; accepted 27 June 2015; published 30 June 2015
ABSTRACT
Wireless sensor networks are currently experiencing widespread enthusiasm in the field of research, mainly because of the great benefits they promise in terms of flexibility, cost, range and robustness. In addition, such networks find use in a wide variety of applications, for example in collecting remote data, type of climate monitoring, seismic activity, or in other areas such as home automation and medical. Unfortunately, their disadvantages are up to their promises. Indeed, the sensor nodes are subjected to high energy consumption constraints due to their compact size as well as the deployment environment. Frequent replacement of batteries is excluded in a field that can be difficult to access. Therefore, the main challenge remains as a result of miniaturization and reduces power consumption to maximize network lifetime. The objective of this work is to make a thorough study of the energy consumption in wireless sensor networks. The study points are addressed at the media access protocol or MAC protocol.
Keywords:
Wireless Sensor Networks, Fault Tolerance, MAC Protocol Suitable for WSN

1. Introduction
WSN consist of a number of interconnected sensors that are able to survey the environment in which they are located and pass the information to certain nodes (Sink) deployed in a position to relay the large-scale information as illustrated in the following diagram. WSN form a new generation of networks with specific properties that do not fit in conventional architectures [1] - [4] . They have a very broad scope, covering several areas of scientific, logistical, military or health.
1.1. The Characteristics of a Suitable MAC Protocol for WSN
In order to design the best suited MAC protocol to the specific characteristics of WSN, we must consider the following properties [5] :
・ The energy optimization: this property is the most important of all in the case of WSN. Indeed, the fact that it is difficult to change or recharge the batteries of the nodes, is a real handicap that limits their lifespan. As the MAC layer controls the activities of the radio layer, which in turn consumes the most energy, then we can deduce that the MAC layer can manage this consumption trying to prevent the loss of this energy. Collision avoidance: This feature is the most important mission of all the MAC protocols, whether they are wired networks or wireless networks.
・ Adapting to change: WSN networks are dynamic in their size, density or their topology; so in this case, an efficient MAC protocol must carefully manage these changes without a network malfunction.
・ The “throughput”: this is the amount of successfully transmitted data between a transmitter and a receiver, in a definite time. It is a fairly important feature in the case of applications that require a good “throughput”.
・ Equity (fairness): It reflects the ability of the sensor nodes to share the channel fairly. In the case of WSN, this property is not taken into consideration since all nodes work together, regardless of the amount of information transmitted by the various nodes to perform a common task.
・ This property remains very important in conventional [6] wireless networks in the fact that each node wants to have the same chance as the other nodes for transmitting or receiving data.
・ The waiting or lag time: This is the time between the transmission time of a message and the time of receiving it successfully. The importance of this feature is dependent on the type of application.
While conventional MAC protocols are designed so that they maximize the “throughput”, they minimize latency and ensure equal opportunities for transmission (fairness). The MAC protocol design for WSN mainly focuses on minimizing energy consumption [7] .
1.2. Energy Consumption at the MAC Layer in WSN
We will try in what follows to analyze the reasons energy of energy loss at the MAC layer in WSN [8] :
・ Collisions: in the case of a collision between two or more packets, the latter will be rejected and therefore transmitted by their issuers. The webcast will increase the energy consumption of sensor nodes issuers.
・ The phenomenon of “idle-listening” or passive listening: It appears when the node is still listening to the medium to receive data possible. It is very costly in energy especially in the case of applications that do not require virtually a large data exchange. The cost of the energy consumption in radio communications type depends on both the transmit hardware/receipt and distance. Indeed, whichever is greater, (Case of WLAN, WWAN) the consumption cost due to listening and reception is negligible compared to that due to the transmission.
However, in the WSN where the distance is small, the energy consumption cost due to passive listening is almost the same order of magnitude as that due to the receipt and issue.
・ The phenomenon of “overhearing” or “on-listening”: this means that the node receives packets that are normally intended for other nodes. This can be a major cause of energy loss in the case of a high density area with the traffic voluminous enough.
・ The phenomenon of “over emitting” or “on-emission” is caused by the transmission of a message to a node that is not yet ready to receive data.
The synthesis of this part leads us to conclude that for WSN which are generally characterized by their high density and not much traffic, the phenomenon of “idle listening” or passive listening is the main cause of the loss of energy in the sensor nodes [1] .
2. Mac Protocols for WSN
2.1. Sensor-MAC Protocol
Sensor-MAC is a MAC protocol specifically designed for WSN [9] . It has been proposed by Ye et al. at the University of California at Los Angeles. The main objective of this protocol is to reduce energy losses due to causes that have been previously identified.
It supports the following four mechanisms:
・ Periodic states “active” and “asleep”
・ The collision avoidance.
・ Avoidance of the phenomenon of “over-listening”.
・ The “Message passing.”
2.1.1. The Periodic State Sequences “Active” and “Asleep”
During our analysis of the energy consumption at the MAC layer in WSN, we found that passive listening is the main cause of energy loss. The idea made by Sensor-MAC to minimize the passive listening is to train the nodes in a periodic sleep state [10] based on a “duty-cycle” fixed (equal to the ratio of the length of time “listen” on the sum of the periods “listen” and “sleep”).
Indeed, each node sleeps for a time and then wakes up and starts listening to see if there is another node wishing to initiate communication with him or wants itself initiates communication. During the sleep state, the node turns off its “radio” and starts a timer for waking later (see Figure 1).
The duration of the “listen” states and “sleep” ones varies from one application to another. Each node is free to choose its own status sequence “active/sleep.” However, to reduce the waiting time, each node must synchronize its state sequence “active/sleep” with the nodes, close to him [11] . Before each node starts a sequence of periodic reports, it must first choose their own sequence and exchange with its neighbors; He must maintain a sequence table that records the sequences of neighboring nodes. In order to choose its own sequence and set the table of sequences, each node must follow these steps:
・ The node starts listening to the media; if it intercepts any sequence of a neighboring node then it will immediately choose its own sequence and will be issued in the SYNC packet to all neighboring nodes.
・ If a node A receives a sequence of a neighbor node B before it chooses and announces its own sequence, then A must adopt the sequence of B. Once the sequence has been selected, node A must issue this sequence to neighboring nodes [11] . If a node A receives a sequence, a neighbor node B, different from his own. Two cases can occur:
・ If A admits that while neighbor B as A is to destroy his own sequence and follow the sequence of B.
・ If A has one or more neighbors with which it has already exchanged a sequence, then A must adopt both its own sequence and the sequence B. Thus, node A will be awake during the intervals “active” of the two sequences [10] .
2.1.2. The Collision Avoidance
If several neighboring nodes want to communicate with the same node at the same time, they will try to transmit their data when the node enters its “listen” period. This will lead to a collision of their requests. The principle of collision avoidance in Sensor-MAC is the same as used in DCF (Distributed Coordinated Function) for the case of IEEE 802.11, which uses the exchange of the RTS/CTS and the virtual/physical listening carrier. Indeed, in each transmitted packet, there is a field that indicates the transmission time remaining. In this case, if a node receives a packet destined for others, it will know through this field, the time it will remain silent. It will record this value in its NAV and will trigger a timer. The NAV will be decremented until it reaches zero. If this value is not zero then the node concludes that the medium is busy. This operation is called virtual listening carrier [10] .
2.1.3 Avoiding the Phenomenon of Overhearing
Since WSN are characterized by their high density, then it is obvious that a node receives packets from neighboring nodes that are not destined for it. The phenomenon of “Overhearing” can result in a significant loss of energy, especially when the traffic is busy. Sensor-MAC is trying to overcome this disadvantage by driving the neighboring nodes in a “sleep” phase, just after they “over-hear” an RTS or CTS packet. In Figure 2, nodes
Figure 1. The principle of periodic states “active” and “asleep” [10] .
Figure 2. Avoiding the phenomenon of overhearing [10] .
A, B, C, D, E and F form a multi-hop network in which each node can hear the nodes that are immediate neighbors.
We assume that A is about to issue a DATA packet to B, then what are that the nodes which must sleep during this transmission? As collisions happen at the receiver, then the D node must sleep since a transmission emanating from him may interfere with the packet received by B from A. The nodes E and F do not produce interference so they do not need to sleep. Concerning the node C which has two hops from B, it can transmit to E and A without worrying about an interference with the transmission received by B. However, C does not receive any request from E because such a request will collide with the (DATA packet) from A to C. In addition, when A finishes its show to B, it will wait the acknowledgment (ACK) of B. At this time, a transmission from C to A can collide with the ACK B. C should fall asleep because its transmissions have no effect [10] . To summarize, the immediately nodes next to the transmitter and the receiver must be asleep when they hear an RTS or CTS packet, respectively from the transmitter or the receiver. They can send data only the next time when they “listen” state with a NAV counter to 0.
2.1.4. The “Message Passing”
The transmission of a long message in one package can cost a lot of energy to the issuer because, if errors occur during the transmission, the transmitter shall retransmit the entire package. However, if it passes this long message into smaller packets, it will have a significant transmission delay because the RTS and CTS packets are required for each small packet sent. The approach used in Sensor-MAC is to fragment the long message into small fragments that will be transmitted together, using a single RTS and a single CTS to which the support will be booked throughout the transmission of these fragments. Each small fragment sent by the transmitter must be paid by the receiver. If applicable, the issuer must reissue this small fragment unacknowledged, and increase the transmission time. RTS and CTS packets each contain a field that indicates the time required to transmit the small fragments of data and ACK packets. Thus, if a neighboring node hears an RTS or CTS packet, it will automatically know the period during which it will remain asleep. This period is simply the time required to transmit the small fragments of data and ACK packets. This mechanism of “Message Passing” is therefore a source of energy saving level [10] nodes sensors.
2.2. TimeOut-MAC Protocol
The description of this protocol is based on an article published by Tijs Van DAM et al. [7] . TimeOut-MAC protocol is a protocol that was designed to address the Sensor-MAC protocol weaknesses in variable traffic load. The idea that the TimeOut-MAC protocol has made is to reduce the passive listening phenomenon by making the “duty-cycle” variable and dependent on the traffic volume, unlike the Sensor-MAC protocol which adopts a fixed duty-cycle.
2.2.1. Timeout-MAC Operation
Each node periodically wakes up to communicate with its neighbors and then returns to its sleepy state until the beginning of the next sequence. Meanwhile, the messages to their receivers will be stored in the “buffer”. During the “active” period, a node remains attentive to the support and could potentially transmit packets during this period. The period “active” ends when there is no longer any reception of message event for a period TA (Activity Timeout) which determines the playing time per active asleep/sequence. Therefore, the active period is adapted to the traffic load. The nodes communicate with each other using the RTS packets, CTS, DATA and ACK. Figure 3 illustrates the functioning of TimeOut-MAC we have described previously:
2.2.2. Synchronization between Nodes
The synchronization sequences were inspired from the method described in the Sensor-MAC protocol.
Figure 3. Operation of TimeOut-MAC protocol [7] .
The timing diagram described with Sensor-MAC and adapted by TimeOut-MAC pushes the nodes to form clusters so that each cluster is described by a sequence of states.
This allows efficient communication between the nodes and prevents maintenance of information for each node [12] .
2.2.3. Determination of TA (Timeout-Activity)
A node must not fall asleep while its neighbors communicate as it can be at any time the receiver of a message. Since a node C cannot hear, because of the limited scope of the issue, an RTS packet sent by a node A, TA interval should be large enough that C can receive at least the date of issue of the CTS packet (between receiving a packet and the date of issue, there is a difference in that the receiver is tuned to the carrier).
Figure 4 shows that the length of the interval TA should check the following inequality:
TA > C + R + T
C with: length of the contention interval.
A: transmission time of the RTS packet.
T: time interval (very small) between the end of receipt of the packet RTS B and the start of transmission of CTS packet B.
Choosing a very wide interval TA can have negative consequences since the increase in TA implies an increase in the passive listening phase, therefore an increase in energy consumption.
2.2.4. Avoidance of the Phenomenon of Overhearing
TimeOut-MAC protocol, considers the avoidance of “over-listening” as an option which it can not ignore since it can disrupt the communication between nodes in the case of applications that require maximum “throughput”. Indeed, during the period when node A will go into “sleep” phase, it may lack the receipt of RTS or CTS packets destined to him and will therefore disrupt communications with others in his wake. Therefore, the “throughput” will decrease.
2.3. The Wise-MAC Protocol
Wise-MAC uses the technique of “Preamble Sampling” to minimize the energy loss due to passive listening. The technique of “Preamble Sampling” is to listen to the channel periodically during relatively short periods to see if there is an activity on the channel. If the channel is busy, the receiver continues its periodic listening awating a packet intended for it or until the channel returns to its free state [13] .
At the transmitter level, a preamble “Wake up” is transmitted before each message to ensure that the receiver will be in a state of “active” when the message is going to happen to him.
This preamble “Wake up” will consume energy either at the transmitter level or the receiver one when the data transfer has not yet started [13] .
To remedy this energy loss, Wise-MAC provides a method to dynamically determine the length of the preamble so that it is as small as possible. This method consists in knowing the sequences “asleep” direct neighbors of the issuer. Thus, experiencing the “asleep” sequence of the recipient, the issuer will issue its preamble “Wake up” for a minimum period Tp just before the receiver starts his new listening period. Figure 5 shows and explains the basic operation of the Wise-MAC protocol:
Each node maintains a table containing the sequences “asleep” direct neighbors, which will be read and updated by the node itself and this thanks to the ACK packet which is returned to him and which does not only fulfill its sending but also contains the term remaining at the receiver to start his next listening [14] . To avoid collisions, Wise-MAC uses a non-persistent CSMA technique with a random choice of the preamble “Wake up”.
Figure 4. Choice of the parameter in the Timeout TA-MAC protocol [7] .
Figure 5. The basic operation of the Wise-MAC protocol [14] .
2.4. The TRAMA Protocol (Traffic-Adaptive Medium Access Protocol)
TRAMA has been designed to reduce energy consumption in WSN. It is based on a TDMA approach of sharing time in several slots that will be allocated only to the nodes that have information to be transmitted, which reduces the waiting time of other nodes.
2.4.1. Operation TRAMA Protocol
TRAMA uses a distributed election algorithm based on traffic conditions at each node. This algorithm which will be processed subsequently allows to select potential receptors as “schedules” announced by issuers. The nodes using the TRAMA protocol exchange the “schedules” of transmission (specifying potential receptors messages to be issued, in chronological order, as well as traffic information to send) as well as the information about their neighborhood with their counterparts, located two jumps for from them. Thanks to its exchanged information, the TRAMA protocol will determine the nodes that may transmit or receive data during each time slot. Figure 6 shows the organization of time slots in the TRAMA protocol:
According to this figure, we notice that there are two types of media access based on time slots:
・ A random access (in collision) during the time slots for signaling.
・ A deterministic access (no collision) at the time slots for transmission.
・ The TRAMA protocol is composed of three components:
・ The neighbor protocol or Neighbor Protocol (NP).
・ The exchange protocol “schedule” or Schedule Exchange Protocol (SEP).
・ Adapted election algorithm or Adaptive Election Algorithm (AEA).
The first two NP and SIP protocols allow a node to exchange the information about the neighborhood and its “schedule” with its neighbors located two jumps of him. As for the AEA algorithm, it uses the information exchanged (Schedule and information on the neighborhood) to select the transmitters and receivers for the current time slot, and allows other nodes thus to enter into “low-power mode “.
2.4.2. The Appropriate Election Algorithm
During the time slots intended for the data transmission (deterministic access), AEA will select the transmitters and receivers. A node is selected to transmit if it has the highest priority in the series of all its neighboring nodes extending to the second jump. The priority of a node ID “u” during a time slot t is defined as the pseudo-rando hash function of the concatenation of “u” and t.
Figure 6. Organisation of time slots in the TRAMA protocol [15] .
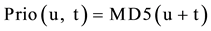
At any time during the time slot t deterministic access, identity node “u” can have three possible states: TX: transmission RX: reception, SL: asleep. For a given slot, a node “u” is in the state TX if it has the highest priority Prio (u, t) between the set of all its neighboring nodes of the second jump, or is in the process of transmitting. Each node runs AEA algorithm to determine its current state that is linked to its priority relative to others (second jump) but also to its neighbors’ “schedules”.
2.5. Lightweight the MAC Protocol
The Lightweight-MAC protocol is based on TDMA technique. The time is divided into time slots that can be used by the nodes to transmit data without having to listen to the channel [16] . At each time slot, Lightweight MAC assigns a node that will be the controller of that time slot.
2.5.1. The Node Synchronization
When the network is initialized (commissioning), all nodes are desynchronized. The gateway also called “Sink” begins with the control of its own time slot and will issue a control message by which the neighbor nodes of the bridge will be able to synchronize their sequences. Then these nodes will randomly choose their time slots they will control.
Once the time slots will be selected, these nodes will issue their control messages to continue the synchronization process.
2.5.2. Principle Transmit/Receive in-MAC Lightweight
- During a time slot, the slot of the controller node sends a message that contains two sections which are:
- The control message that carries the identifier (ID) of the time slot of the controller and the identifier (ID) of the time slot used. It contains the following information: the distance (in number of hops) between the node of the gateway, the recipient's address and length of the data unit.
- The data unit that contains the data to be transmitted.
- All the nodes receive control messages from their neighboring nodes. Two cases arise:
- If a node is not addressed in the transmitted control message, it will then take the “sleeping” state and not wake until the next time slot.
- If a node is addressed, then it will listen to the unit of transmitted data and then will return to its “asleep” state just after receiving the message.
2.5.3. The Collision Avoidance
To avoid collisions, the nodes maintain tables containing the identifiers of slots allocated to nodes located within a radius of three jumps. There is a possibility (low probability) of the same choice of the time slot between two or more nodes. In this case, the nodes inform their neighbors that a collision between the control messages occurred. Nodes that have issued these control messages are then used to halt their used control slots and reselect at random other slots (except those who have been chosen) after a back-off time depending on the identifier (ID) of the node.
2.6. The MAC Protocol of IEEE 802.15.4
Regarding the MAC protocol of this standard, it is responsible for the following [17] :
・ Synchronization by the generation of “network beacons”: the coordinator periodically sends “beacons” to synchronize the devices attached to it. This synchronization is important for the energy economy at the sensor nodes. In the “beacon enabled” mode, a structure of “superframe” is used. Which “superframe” is bounded by two “beacons” and is divided into its active part in a number of slots equal to 16 by default.
・ Auto-configuration: To support auto-configuration, the MAC protocol of IEEE 802.15.4 uses the association and dissociation functions used in WPAN networks.
・ Access to the channel: the mechanism used to access the channel CSMA/CA. However, the new standard does not include the RTS and CTS mechanisms because of the principle of low flow used in LR-WPAN.
・ Maintaining the GTS mechanism (Guaranteed Time Slot): When operating in “beacon-enabled” mode, a coordinator can allocate portions of the active part of the “superframe” to a device. These portions are called GTS.
・ The assurance of a reliable connection: To ensure reliable communication between the different entities, the MAC protocol of IEEE 802.15.4 employs mechanisms such as the acknowledgment, retransmission of the frame or verification data using the 16-bit CRC (used in CSMA/CA).
3. Comparative Study of Some Proposed Mac Protocols in WSN
3.1. The Comparison Criteria
To achieve this comparative study, we relied on the following four criteria:
- The allocation of the radio channel.
- Notification.
- Energy Management.
- Quality of service.
3.1.1. The Allocation of the Radio Channel
In radio frequency communications, if there is more than a node that wants to transmit data on the same channel and at the same time, then communication problems such as collisions or distortion can arise. To avoid such problems, some of the bandwidth is allocated to each node [18] . This allowance can be either static or dynamic:
・ Static Allocation: This allocation technique divides the bandwidth into N parts. Each party is allocated to a node. Multiplexing techniques used to divide the bandwidth have been described in the first part of this chapter and are: TDMA, FDMA and CDMA. In general, the MAC protocol in WSN, employing a static allocation of the channel, using the TDMA technique. This technique requires a synchronization between nodes to allow each node to identify its time slots. The synchronization in the case of WSN is distributed in which each node or group of nodes generates its own sequence of states that will be adjusted periodically. The centralized synchronization is not applicable in WSN because this kind of network suffers from high latency and a packet loss is fairly common. So in the event of a delay or loss of sync signal, the network will be disrupted.
・ Dynamic allocation: In this technique of allocation, there is no bandwidth allocated in a predefined manner for each node. Any node wishing to access the channel must win the restraint. With this type of allocation, there is a high probability of collision.
3.1.2. Notification
To succeed communication between transmitter and receiver, this later must be listening channel when the transmission starts. Thus, he will be notified of the existence of a transmission on the channel. This notification can be classified into two types:
・ By reservation: This type of notification is used by protocols based on a static channel allocation, where the nodes have predetermined slots for transmission or reception. Lightweight-MAC protocol is an example that uses this type of notification.
・ By listening to the channel: In protocols using a dynamic allocation of the channel, there is no predetermined slot to transmit or receive data. A node can always be a tuned channel waiting to receive a transmission intended for it. Although this listening method could increase the chances of receiving the message, this method is too costly in energy. To avoid such losses, nodes periodically change their “sleeping state” and “active state “. Listening to the channel can be synchronous or asynchronous. Synchronous: the sequence of states “active/sleep” is determined by an exchange of synchronization messages. Each node knows when these neighboring nodes will be active. Thus the sender node waits until the receiver enters the active state to transmit its message. Sensor-MAC and MAC-TimeOut are protocols which employ synchronous listening to the channel. Asynchronous: The nodes do not know when their neighbors are active. They shall periodically be tuned channel to check if a transmission will take place. This method is known under the name of “Preamble Sampling”. Wise-MAC uses this type of listening channel.
3.1.3. Power Management
This criterion will be treated with the advantages and disadvantages in terms of energy management, of each MAC protocol described above. They then listen to the channel to chek if a transmission will take place.
3.1.4. QoS
Unlike traditional networks, the basic components of the service quality are the bandwidth, fairness and latency. These components are, for the majority of MAC protocols proposed for WSN (except for the MAC protocol of IEEE 802.15.4), sacrificed at the expense of optimizing the energy consumption of sensor nodes. This does not mean that the quality of service need not be included in this type of network, except that it is essentially dependent on the type of application running at the WSN. Indeed, Sensor-MAC designers, Time-Out or MAC-MAC Wise had the first goal, the energy consumption reduction to maximize the network lifetime which was fine with the applications they use (military...). However, and for the case of the MAC protocol of IEEE 802.15.4 (standard used for purposes of applications for the general public), bandwidth and latency for example are service quality parameters strongly taken into account.
3.2. The Comparative Tables
Table 1 and Table 2 show the classification of MAC protocols proposed for WSN, according to the four criteria that has been described previously (The allocation of the radio channel, notification, energy management, quality of service).
4. Experimental Study, Sensor-MAC Protocol and Timeout-MAC
4.1. Setting the Network Used
The network that will be used to perform all simulations of different scenarios consists of 100 nodes arranged in a grid (GRID), with a duration of simulation equal to 60 seconds.
4.2. Setting the Sensor-MAC protocols and Timeout-MAC
Sensor-MAC has been configured with a frame length (the sum of the “active” period and the “sleeping” period) equal to 1 second and a length of the “active” period we set at 150 ms.
Timeout-MAC has been configured with a length of 615 ms frame equals and a length of period TA (Timeout Activity) equal to 15.
Table 1. Comparative study of some MAC protocols in WSN.
Table 2. Advantages and disadvantages of MAC protocols in WSN.
4.3. Setting Scenarios
In the simulation model that was used, the definition of a scenario is through a configuration file in which you must specify the type of communication used in the network: point to point or Sink-to-node. The message length and flow rate are used in number of messages per second (msg/s).
4.4. Simulation Results
Following the execution of the scenarios described above, we collected different energy consumption values as follows:
4.4.1. Case of Communication Model “Point to Point”
The energy consumption in the model “Point to Point” is presented in Figure 7.
According to Figure 7, we note that the Sensor-Mac protocol consumes more energy than TimeOut-Mac protocol. The energy consumption for Sensor-Mac protocol exceeded 0.6 while the energy consumption for TimeOut-Mac protocol has not exceeded 0.4 for 160 bytes/node/second. We present in Figure 8 the throughput in the communication in the model “Point to Point”.
In Figure 8, the Sensor-Mac protocol provides a throughput less than 0.6 per 160 bytes/node/second while the Time Out-Mac protocol provides a throughput higher than 0.7 for the same number of bytes/node/second. The throughput offered by the two protocols is almost equal and which is 0.9 for a number of bytes/node/secondless than 60.
Figure 7. Energy consumption in the model “Point to Point”.
Figure 8. Throughput in the communication model “Point to Point”.
4.4.2. Case of Communication Model “Node to Sink”
The energy consumption in the model “node to Sink” is presented in Figure 9.
According to Figure 9, we note that the TimeOut-Mac protocol consumes less energy than Sensor-Mac protocol.
The energy consumption for TimeOut-Mac protocol increases relative to number of bytes/node/second. It is equal to 0.2 for a number of bytes/node/second which is worth 0, and does not exceed 0.8 for a 6 bytes/node/ second in the model “node to Sink”. While the energy consumed by Sensor-Mac protocol for the same number of bytes/node/second is almost equal to 1.3.
We present in Figure 10 the throughput in the communication in the model “node to Sink”.
Figure 9. Energy consumption in the model “node to Sink”.
Figure 10. Throughput in the communication model “node to Sink”.
According to Figure 10, the Sensor-Mac protocol provides a throughput less than 0.65 per 6 bytes/node/ second in the model “node to Sink” while the TimeOut-Mac protocol provides a throughput higher than 0.4 for the same number of bytes/node/second. The throughput offered by the two protocols is almost equal and which is 0.9 for a number of bytes/node/second less than 2.
4.5. Interpretation of Results
In both models the point and point a node to Sink, we notice that TimeOut-Mac consumes significantly less energy than Sensor-MAC
Regarding the throughput since in the model point point Timeout-MAC proves itself better than Sensor-MAC since its value doesn’t begin to go down above 87% only from the traffic of 118 bytes/node/s while it is 77 bytes/node/s in the case of Sensor-MAC. In the model node to Sink, a low traffic (≤2 bytes/node/s), the nodes using the Sensor-MAC protocol has a throughput ≥ 87%. However, by increasing the traffic, we see that the throughput decreases in a sudden manner. This is due to the fact that the Sensor-MAC adopts a fixed duty-cycle either in transmission, inreception or in the passive listening state. This “duty-cycle” does not adapt to the load of traffic so there will be a data loss.
5. Conclusions
Wireless sensor networks are likely, in the future to change the way we live, and work. They constitute a major technological development to the various problems in several areas of health-related application, security, envi- ronment, etc.
In this paper, we make a study of wireless sensor networks and its various power-saving mechanisms fault tolerance. We also conduct a comparative study of some protocols of the MAC layer. We find that the protocols of the existing MAC layer are dedicated either to guarantee the reliability or to control congestion in a unidirectional sense. Current research, in this area, has focused on achieving a reliable transfer with minimal loss of data, taking into account the energy economy. It is necessary, therefore, to show that the MAC layer must perform a good transfer without energy dissipation, to prolong the life of the sensor, the maximum possible. Indeed, the MAC layer must be based on a new control efficient protocol and an economical transmission.
References
- Fleury, E., Chelius, G. and Cute, T. (2003) Minimization of Energy in Sensor Networks. CITI Laboratory/INSA Lyon, Villeurbanne.
- Holger, K. and Willig, A. (2003) A Short Survey of Wireless Sensor Networks. Telecommunication Networks Group, Technical University Berlin, Berlin.
- Lwakabamba, B. (2004) Performance Analysis Experiments for the Wireless Sensor Networks Integrated into the C6 Virtual Reality Environment. Iowa State University, Ames.
- Pujolle, G. (2005) Networks Editions 2005. Eyrolles.
- Demirkol, I., Ersoy, C. and Alagöz, F. (2003) MAC Protocols for Wireless Sensor Networks: A Survey. Communications Magazine, 44, 44.
- Ryan Burchfield, T., Venkatesan, S. and Weiner, D. (2007) Maximizing Throughput in ZigBee Wireless Networks through Analysis, Simulations and Implementations. Proceedings of the International Workshop on Localized Algorithms and Protocols for Wireless Sensor Networks Santa Fe, New Mexico, 18-20 June 2007, Localgos 2007, CTI Press, Athens, 15-29.
- Van Dam, T. and Langendoen, K. (2003) An Adaptive Energy Efficient MAC Protocol for Wireless Sensor Networks. Faculty of Information Technology and Systems, Delft University of Technology, Delft.
- Akyildiz, I., Su, W., Sankarsubramaniam, Y. and Cayirci, E. (2002) A Survey on Sensor Networks. IEEE Communications Magazine, 40, 102-114. http://dx.doi.org/10.1109/MCOM.2002.1024422
- Van Dam, J.M. (2003) An Adaptive Energy-Efficient MAC Protocol for Wireless Sensor Networks. Master Thesis, Delft University of Technology, Delft.
- Heidemann, J., Ye, W. and Estrin, D. (2002) An Energy Efficient-MAC Protocol for Wireless Sensor Networks. Proceedings of 21st Annual Joint Conference of the IEEE Computer and Communications Societies, 3, 1567-1576.
- Ye, W. and Heidmann, J. (2003) Medium Access Control in Wireless Sensor Networks. USC/ISI Technical Report ISI-TR-580.
- Culler, D., Estrin, D. and Srivastava, M. (2004) Overview of Sensor Networks. IEEE Computer Society, Washington DC.
- Decotignie, J.D., El-Hoiydi, A., Enz, C. and Le Roux, E. (2003) WiseMAC, an Ultra Low WiseNET Protocol for the Wireless Sensor Network. ACM SenSys’03, Los Angeles.
- El-Hoiydi, A. and Decotignie, J.D. (2004) WiseMAC: An Ultra Low Power MAC Protocol for the Downlink of Infrastructure Wireless Sensor Networks. 9th International Symposium on Computers and Communications, 1, 244-251. http://dx.doi.org/10.1109/iscc.2004.1358412
- Rajendran, V., Obraczka, K. and Garcia, J.J. (2003) Energy-Efficient, Collision-Free Medium Access Control for Wireless Sensor Networks. ACM SenSys’03, Los Angele, 5-7 November 2003, 12 p.
- Van Hoesel, L.F.W. and Havinga, P.J.M. (2004) A Lightweight Medium Access Protocol (LMAC) for Wireless Sensor Networks: Reducing Preamble Transmissions and State Transceiver Switches. INSS, Japan.
- Zheng, J. and Myung L. (2004) Will Make Ubiquitous IEEE 802.15.4 Networking Is Reality? IEEE Communications Magazine, 42, 140-146.
- Azizi, R. (2015) Comparative Study of Transport Protocols in WSN. International Journal of Computer Applications, 113, 1-9. http://dx.doi.org/10.5120/19827-1674












