Paper Menu >>
Journal Menu >>
 Wireless Sensor Network, 2010, 2, 7-17 doi:10.4236/wsn.2010.21002 anuary 2010 (http://www.SciRP.org/journal/wsn/). Copyright © 2010 SciRes. WSN Published Online J Simulation Study of the Influence of the Hidden and Exposed Stations for the Efficiency of IEEE 802.15.4 LR-WPAN Networks Dariusz KOŚCIELNIK AGH University of Science and Technology, Department of Electronics, Kraków, Poland Email: koscieln@agh.edu.pl Received August 14, 2009; revised Septemb er 20, 2009; accepted September 22, 2009 Abstract This article presents an analysis of wireless personal area networks with low transmission rate, utilized more and more often in industrial or alarm systems, as well as in sensor networks. The structure of these systems and available ways of transmission are defined by the IEEE 802.15.4 standard. The main characteristics of this standard are given in the first part of this article. The second part contains the description of simulation tests that have been realized. Their results make available an evaluation of the effective transmission rate of a transmission channel, the resistance to the phenomenon of hidden station as well as sensibility to the problem of the exposed station. Keywords: Wireless Network, Sensor Network, Lr-Wpan, Csma/Ca, Slotted-Csma/Ca, Transmission Proto- col, Hidden Station, Exposed Station 1. Introduction In the past few years, the interest concerning the Wire- less Personal Area Networks – WPAN, has been growing in a very important way. These systems make possible a free utilization of portable communication devices, a fast creation of improvised networks as well as an automa- tion of many repetitive everyday activities (updating of prepared data, address books, notebooks and calendars). All the WPAN networks must fulfill high expectations concerning low energy consumption and limited trans- mission range. However, in the recent period we can clearly observe a clear distinction between solutions that are currently created, resulting in a subdivision of the IEEE802.15 standard defining WPAN networks into four specialized thematic groups. The first of these groups (IEEE802.15.1) concerns the development of the Blue- tooth network, considered as a system of medium trans- mission rate. The axis of the studies concerning the sec- ond group (IEEE802.15.2) concerns the compatibility of the WPAN and WLAN systems (mainly of the IEEE802.11 standard). These works have been temporar- ily suspended, because the recent studies indicate that— at the current state of technology and standardization— the required compatibility is impossible to achieve. The third group (IEEE802.15.3) concerns WPAN networks with high transmission rate—HR-WPAN (High Rate Wireless Personal Area Network). The transmission in these systems is realized with a rate achieving 54Mb/s – there can be represented by the multimedia Wimedia network with medium transmission rate of 20Mb/s. The object of the IEEE802.15.4 standard concerns networks with low transmission rate—LR-WPAN (Low Rate Wireless Personal Area Network). The results of the studies presented in the further part of this article apply to the last one of the abovementioned systems. 2. LR-WPAN Networks The IEEE802.15.4 standard has been created in 2003, and its current form results of the modifications intro- duced three years later. The specification defines the physical layer—PHY (Physical Layer), the sublayer of access to the transmission link—MAC (Medium Access Control Sublayer), as well as the principle of their inter- action with the higher layers. The LR-WPAN networks are characterized by very low energy consumption, simplicity of their structure making possible to implement the transmission protocol on 8-bit microcontrollers, as well as low costs of receiv- ing and transmitting equipment. LR-WPAN networks are designed to be used in different industrial, agricultural 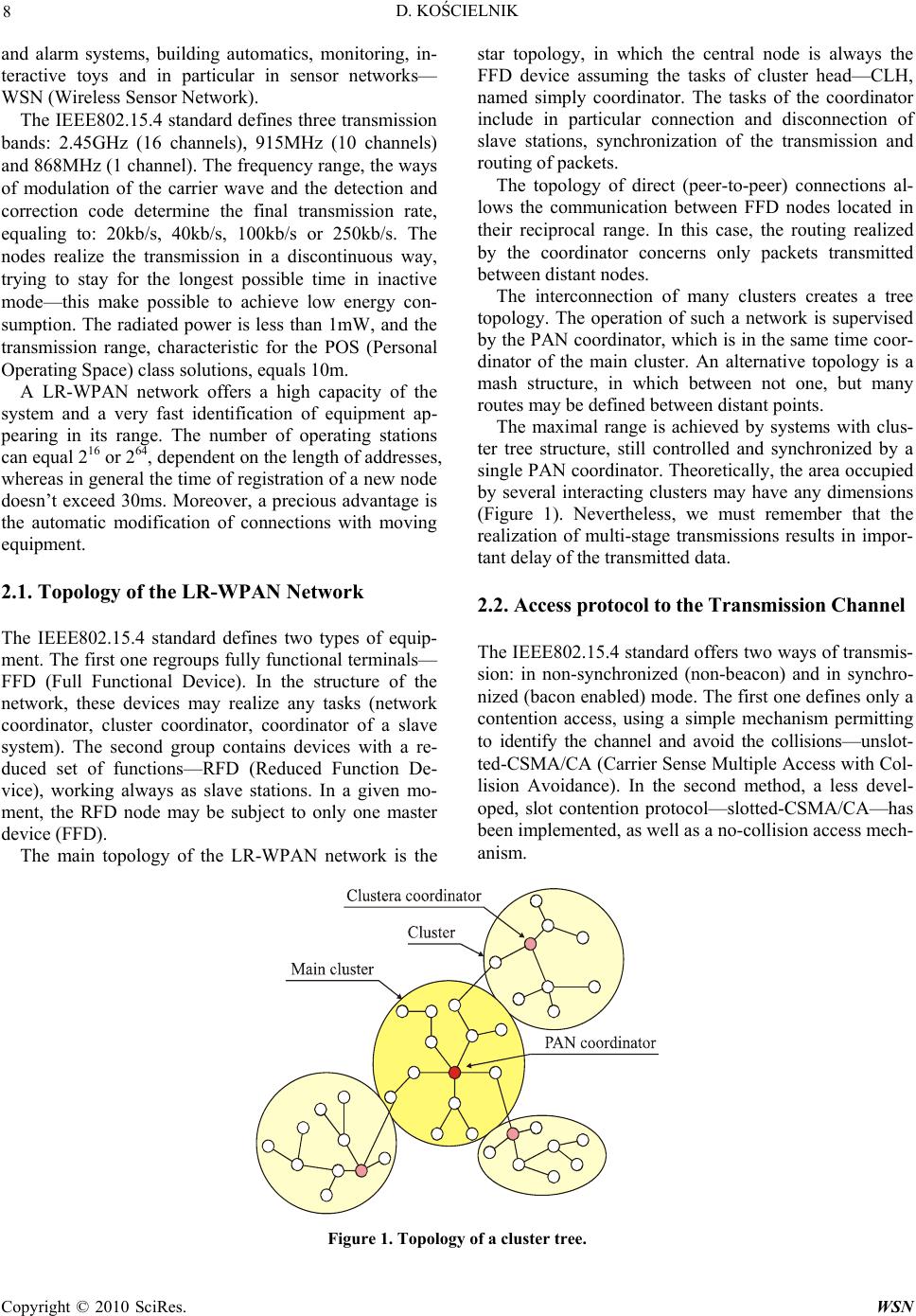 D. KOŚCIELNIK 8 and alarm systems, building automatics, monitoring, in- teractive toys and in particular in sensor networks— WSN (Wireless Sensor Network). The IEEE802.15.4 standard defines three transmission bands: 2.45GHz (16 channels), 915MHz (10 channels) and 868MHz (1 channel). The frequency range, the ways of modulation of the carrier wave and the detection and correction code determine the final transmission rate, equaling to: 20kb/s, 40kb/s, 100kb/s or 250kb/s. The nodes realize the transmission in a discontinuous way, trying to stay for the longest possible time in inactive mode—this make possible to achieve low energy con- sumption. The radiated power is less than 1mW, and the transmission range, characteristic for the POS (Personal Operating Space) class solutions, equals 10m. A LR-WPAN network offers a high capacity of the system and a very fast identification of equipment ap- pearing in its range. The number of operating stations can equal 216 or 264, dependent on the length of addresses, whereas in general the time of registration of a new node doesn’t exceed 30ms. Moreover, a precious advantage is the automatic modification of connections with moving equipment. 2.1. Topology of the LR-WPAN Network The IEEE802.15.4 standard defines two types of equip- ment. The first one regroups fully functional terminals— FFD (Full Functional Device). In the structure of the network, these devices may realize any tasks (network coordinator, cluster coordinator, coordinator of a slave system). The second group contains devices with a re- duced set of functions—RFD (Reduced Function De- vice), working always as slave stations. In a given mo- ment, the RFD node may be subject to only one master device (FFD). The main topology of the LR-WPAN network is the star topology, in which the central node is always the FFD device assuming the tasks of cluster head—CLH, named simply coordinator. The tasks of the coordinator include in particular connection and disconnection of slave stations, synchronization of the transmission and routing of packets. The topology of direct (peer-to-peer) connections al- lows the communication between FFD nodes located in their reciprocal range. In this case, the routing realized by the coordinator concerns only packets transmitted between distant nodes. The interconnection of many clusters creates a tree topology. The operation of such a network is supervised by the PAN coordinator, which is in the same time coor- dinator of the main cluster. An alternative topology is a mash structure, in which between not one, but many routes may be defined between distant points. The maximal range is achieved by systems with clus- ter tree structure, still controlled and synchronized by a single PAN coordinator. Theoretically, the area occupied by several interacting clusters may have any dimensions (Figure 1). Nevertheless, we must remember that the realization of multi-stage transmissions results in impor- tant delay of the transmitted data. 2.2. Access protocol to the Transmission Channel The IEEE802.15.4 standard offers two ways of transmis- sion: in non-synchronized (non-beacon) and in synchro- nized (bacon enabled) mode. The first one defines only a contention access, using a simple mechanism permitting to identify the channel and avoid the collisions—unslot- ted-CSMA/CA (Carrier Sense Multiple Access with Col- lision Avoidance). In the second method, a less devel- oped, slot contention protocol—slotted-CSMA/CA—has been implemented, as well as a no-collision access mech- anism. Figure 1. Topology of a cluster tree. Copyright © 2010 SciRes. WSN 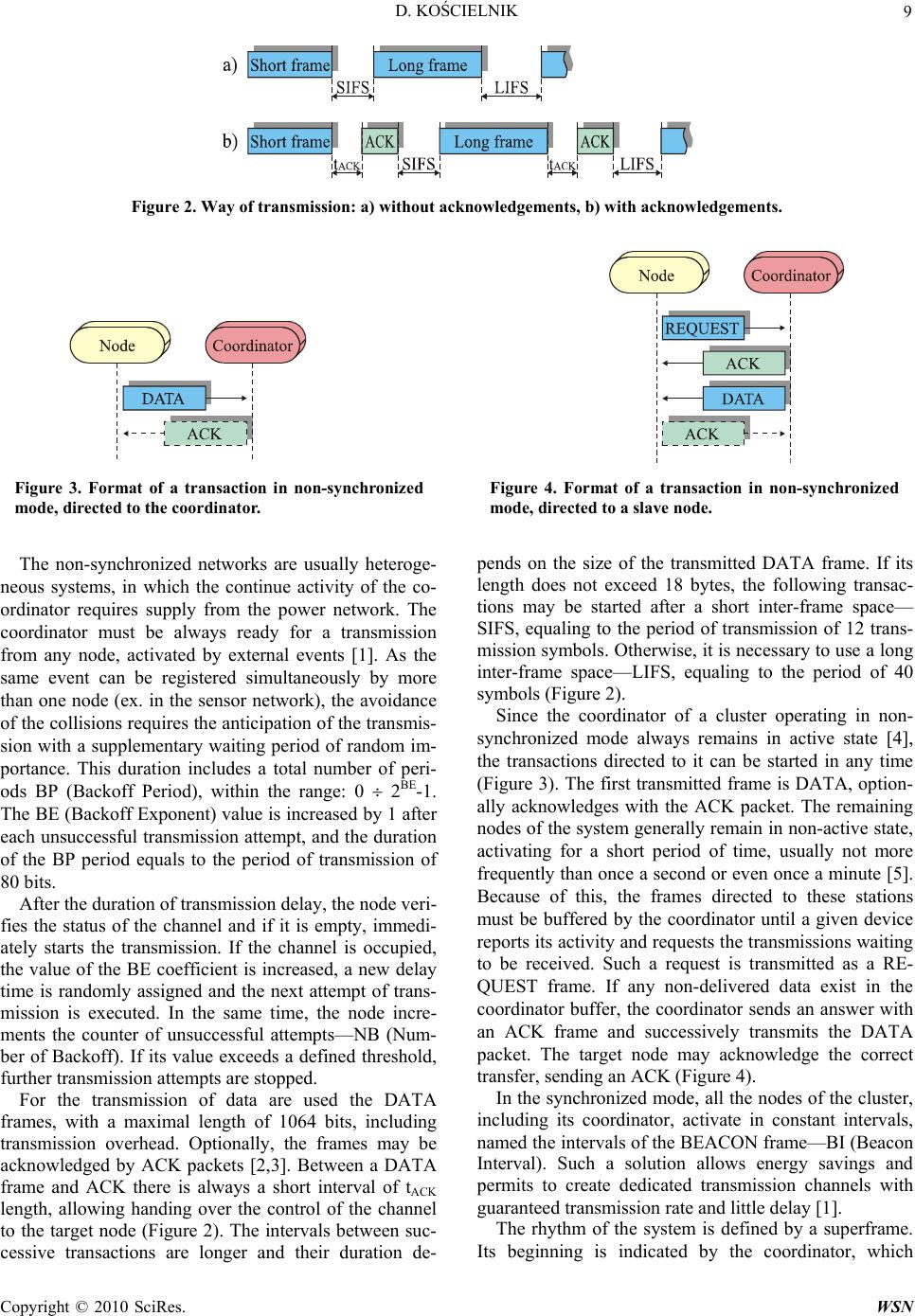 D. KOŚCIELNIK 9 Figure 2. Way of transmission: a) without acknowledgements, b) with acknowledgements. Figure 3. Format of a transaction in non-synchronized mode, directed to the coordinator. Figure 4. Format of a transaction in non-synchronized mode, directed to a slave node. The non-synchronized networks are usually heteroge- neous systems, in which the continue activity of the co- ordinator requires supply from the power network. The coordinator must be always ready for a transmission from any node, activated by external events [1]. As the same event can be registered simultaneously by more than one node (ex. in the sensor network), the avoidance of the collisions requires the anticipation of the transmis- sion with a supplementary waiting period of random im- portance. This duration includes a total number of peri- ods BP (Backoff Period), within the range: 0 2 BE-1. The BE (Backoff Exponent) value is increased by 1 after each unsuccessful transmission attempt, and the duration of the BP period equals to the period of transmission of 80 bits. After the duration of transmission delay, the node veri- fies the status of the channel and if it is empty, immedi- ately starts the transmission. If the channel is occupied, the value of the BE coefficient is increased, a new delay time is randomly assigned and the next attempt of trans- mission is executed. In the same time, the node incre- ments the counter of unsuccessful attempts—NB (Num- ber of Backoff). If its value exceeds a defined threshold, further transmission attempts are stopped. For the transmission of data are used the DATA frames, with a maximal length of 1064 bits, including transmission overhead. Optionally, the frames may be acknowledged by ACK packets [2,3]. Between a DATA frame and ACK there is always a short interval of tACK length, allowing handing over the control of the channel to the target node (Figure 2). The intervals between suc- cessive transactions are longer and their duration de- pends on the size of the transmitted DATA frame. If its length does not exceed 18 bytes, the following transac- tions may be started after a short inter-frame space— SIFS, equaling to the period of transmission of 12 trans- mission symbols. Otherwise, it is necessary to use a long inter-frame space—LIFS, equaling to the period of 40 symbols (Figure 2). Since the coordinator of a cluster operating in non- synchronized mode always remains in active state [4], the transactions directed to it can be started in any time (Figure 3). The first transmitted frame is DATA, option- ally acknowledges with the ACK packet. The remaining nodes of the system generally remain in non-active state, activating for a short period of time, usually not more frequently than once a second or even once a minute [5]. Because of this, the frames directed to these stations must be buffered by the coordinator until a given device reports its activity and requests the transmissions waiting to be received. Such a request is transmitted as a RE- QUEST frame. If any non-delivered data exist in the coordinator buffer, the coordinator sends an answer with an ACK frame and successively transmits the DATA packet. The target node may acknowledge the correct transfer, sending an ACK (Figure 4). In the synchronized mode, all the nodes of the cluster, including its coordinator, activate in constant intervals, named the intervals of the BEACON frame—BI (Beacon Interval). Such a solution allows energy savings and permits to create dedicated transmission channels with guaranteed transmission rate and little delay [1]. The rhythm of the system is defined by a superframe. Its beginning is indicated by the coordinator, which C opyright © 2010 SciRes. WSN  D. KOŚCIELNIK 10 sends a BEACON packet. The superframe is divided into active and non-active parts (Figure 5). Any transmissions and related activities of single nodes take place only in the first part of the superframe, containing 16 slots and divided between contention access period—CAP and contention free period—CFP. The duration of the transmission of the BEACON frame is defined by BO (Beacon Order) parameter in the following way: BI = BSD*2BO, where the BSD (Base Superframe Duration) constant defined the period of the main superframe (the shortest possible), containing 16 slots with a length of 60 transmission symbols. In a similar way is defined the size of the active part of the superframe—SD (Superframe Duration), equaling to: SD = BSD*2SO, where the values of: SO (Superframe Order) and BO are interdependent: SO ≤ BO and 0 ≤ BO ≤ 14. The contention access used in the CAP period uses a somewhat more developed, slotted CSMA/CA (slot- ted-CSMA/CA) mechanism. The node initiating a trans- action synchronizes its activities to the start of the closest BP period and begins the counting of the transmission delay, defined randomly in the way described above. Further away, the verification of the channel status be- gins, during this time by the contention window duration —CW. The contention window consists of several (by default two) BP periods. The node can start a transmis- sion only, if during the whole CW period the channel remained unoccupied. Otherwise, after increasing by 1 the BE and NB values, a following attempt of transmis- sion is started. However, before that the node must verify if the counter NB does not exceed the threshold value and the transaction does not exceed the contention period of the superframe. Before the transaction directed to the coordinator starts, the source node must correctly receive a BEACON frame and synchronize its activities within the limits of appropriate time periods. Only then the contention pro- cedure can be started. The procedure ends with the transmission of the DATA frame (Figure 6). The coor- dinator, being responsible for generating the BEACON frame, must pass to the active state from the frequency of redundancy of the superframe. In such a way, the trans- actions directed to this node are not subject to any further limitations. The other nodes of the network may activate much more rarely. The coordinator must still buffer data transmitted to it. The information concerning packets waiting for delivery is sent in a BEACON frame, to- gether with the network identification as well as its main operation parameters. When a device activate, it receives information indicating, if a transaction of reception should be initiated (Figure 7). Therefore, also in this case the source of transactions realized in both directions are nodes not being coordinators (see Figure 3, Figure 4, Figure 6 and Figure 7). A supplementary function of the coordinator is the al- location and maintenance of guaranteed time slots—GTS, designed for applications that require channels with con- stant transmission rate and little delay [2]. The coordina- tor may prepare up to seven such structures, containing Figure 5. Structure of a superframe. Figure 6. Format of a transaction in synchronized mode, directed to the coordinator. Figure 7. Format of a transaction in synchronized mode, directed to a slave node. Copyright © 2010 SciRes. WSN 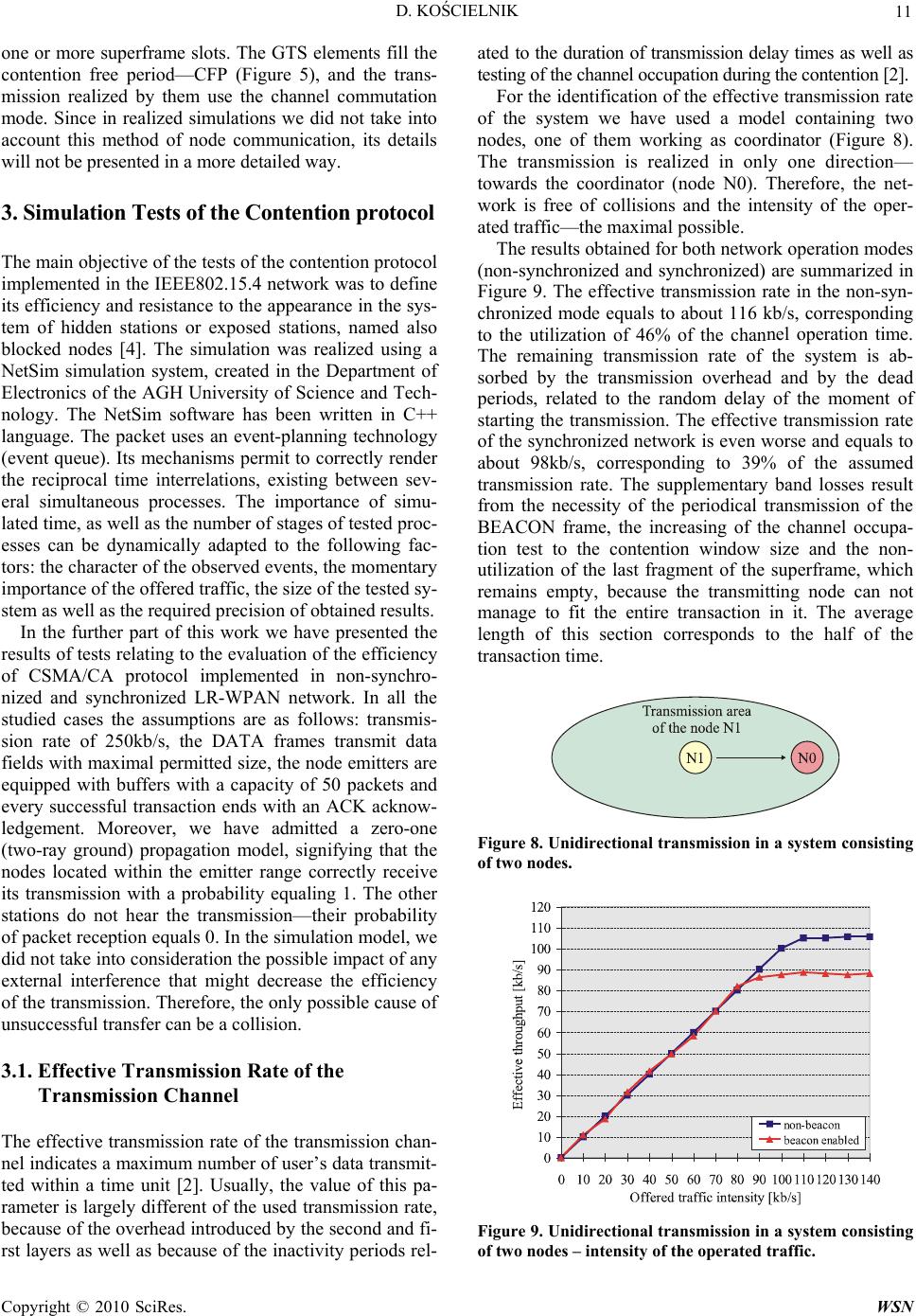 D. KOŚCIELNIK 11 one or more superframe slots. The GTS elements fill the ontention free period—CFP (Figure 5), and the t protocol plemented in the IEEE802.15.4 network was to define of the Transmission Channel The f the transmission chan- el indicates a maximum number of user’s data transmit- rst layers as well as because of the inactivity periods rel- ated to the duration of transmission delay times as well as the channel occupation during the contention [2]. w nel operation time. crans- testing of mission realized by them use the channel commutation mode. Since in realized simulations we did not take into account this method of node communication, its details will not be presented in a more detailed way. 3. Simulation Tests of the Contention The main objective of the tests of the contention protocol im its efficiency and resistance to the appearance in the sys- tem of hidden stations or exposed stations, named also blocked nodes [4]. The simulation was realized using a NetSim simulation system, created in the Department of Electronics of the AGH University of Science and Tech- nology. The NetSim software has been written in C++ language. The packet uses an event-planning technology (event queue). Its mechanisms permit to correctly render the reciprocal time interrelations, existing between sev- eral simultaneous processes. The importance of simu- lated time, as well as the number of stages of tested proc- esses can be dynamically adapted to the following fac- tors: the character of the observed events, the momentary importance of the offered traffic, the size of the tested sy- stem as well as the required precision of obtained results. In the further part of this work we have presented the results of tests relating to the evaluation of the efficiency CSMA/CA protocol implemented in non-synchro- nized and synchronized LR-WPAN network. In all the studied cases the assumptions are as follows: transmis- sion rate of 250kb/s, the DATA frames transmit data fields with maximal permitted size, the node emitters are equipped with buffers with a capacity of 50 packets and every successful transaction ends with an ACK acknow- ledgement. Moreover, we have admitted a zero-one (two-ray ground) propagation model, signifying that the nodes located within the emitter range correctly receive its transmission with a probability equaling 1. The other stations do not hear the transmission—their probability of packet reception equals 0. In the simulation model, we did not take into consideration the possible impact of any external interference that might decrease the efficiency of the transmission. Therefore, the only possible cause of unsuccessful transfer can be a collision. 3.1. Effective Transmission Rate of effective transmission rate o n ted within a time unit [2]. Usually, the value of this pa- rameter is largely different of the used transmission rate, because of the overhead introduced by the second and fi- For the identification of the effective transmission rate of the system we have used a model containing two nodes, one of them working as coordinator (Figure 8). The transmission is realized in only one direction— towards the coordinator (node N0). Therefore, the net- ork is free of collisions and the intensity of the oper- ated traffic—the maximal possible. The results obtained for both network operation modes (non-synchronized and synchronized) are summarized in Figure 9. The effective transmission rate in the non-syn- chronized mode equals to about 116 kb/s, corresponding to the utilization of 46% of the chan The remaining transmission rate of the system is ab- sorbed by the transmission overhead and by the dead periods, related to the random delay of the moment of starting the transmission. The effective transmission rate of the synchronized network is even worse and equals to about 98kb/s, corresponding to 39% of the assumed transmission rate. The supplementary band losses result from the necessity of the periodical transmission of the BEACON frame, the increasing of the channel occupa- tion test to the contention window size and the non- utilization of the last fragment of the superframe, which remains empty, because the transmitting node can not manage to fit the entire transaction in it. The average length of this section corresponds to the half of the transaction time. Figure 8. Unidirectional transmission in a system consisting of two nodes. Figure 9. Unidirectional transmission in a system consisting of two nodes – intensity of the operated traffic. C opyright © 2010 SciRes. WSN 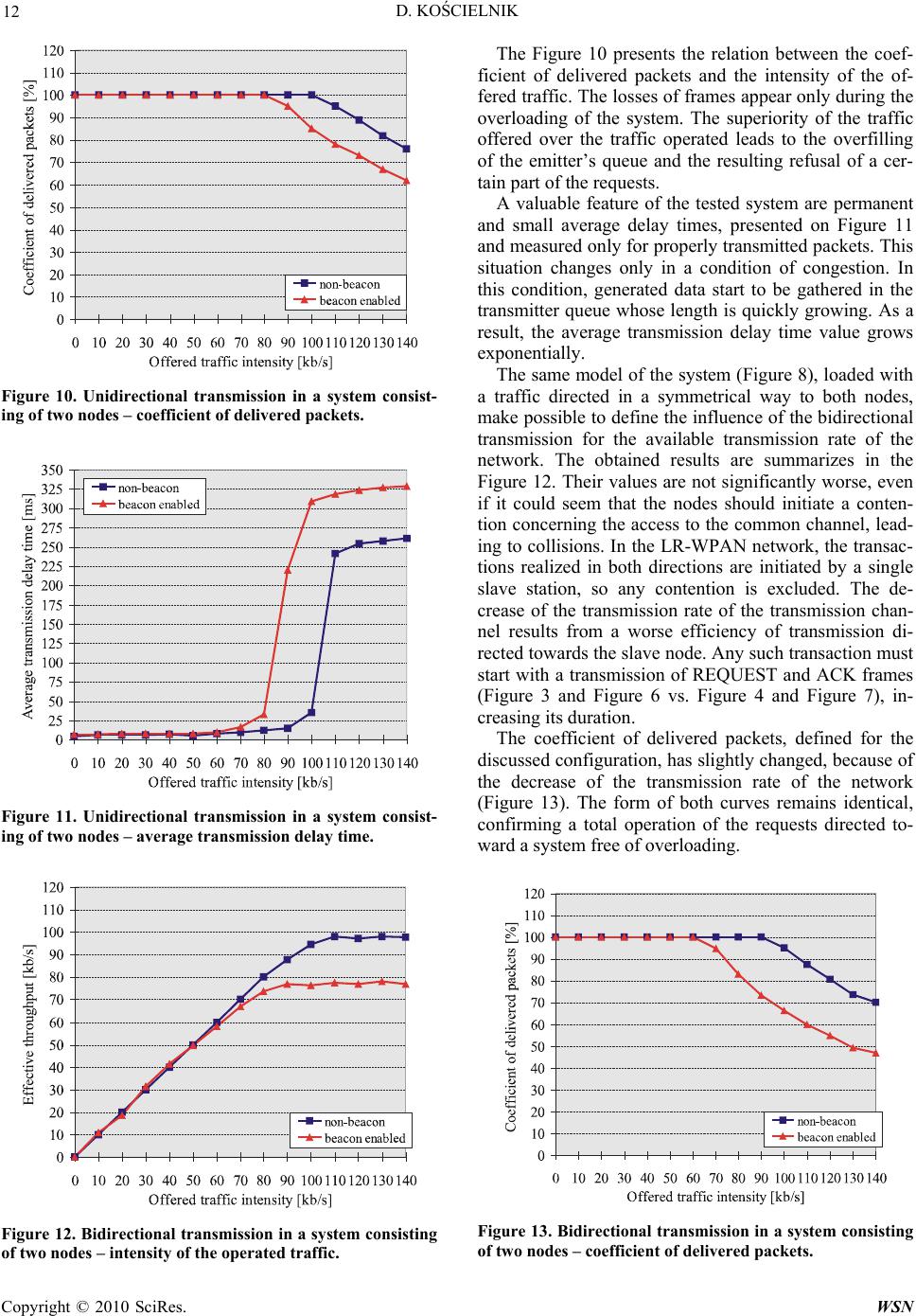 D. KOŚCIELNIK 12 Figure 10. Unidirectional transmission in a system consist- ing of two nodes – coefficient of delivered packets. Figure 11. Unidirectional transmission in a system consist- ing of two nodes – average transmission delay time. Figure 12. Bidirectional transmission in a system consisting of two nodes – intensity of the operated traffic. The Figure 10 presents the relation between the coef- ficient of delivered packets and the intensity of the of- fered traffic. The losses of frames appear only during the overloading of the system. The superiority of the traffic offered over the traffic operated leads to the overfilling of the emitter’s queue and the resulting refusal of a cer- tain part of the requests. A valuable feature of the tested system are permanent and small average delay times, presented on Figure 11 and measured only for properly transmitted packets. This situation changes only in a condition of congestion. In this condition, generated data start to be gathered in the transmitter queue whose length is quickly growing. As a result, the average transmission delay time value grows exponentially. The same model of the system (Figure 8), loaded with idirectional tra s are initiated by a single sla nt of delivered packets, defined for the di a traffic directed in a symmetrical way to both nodes, make possible to define the influence of the b nsmission for the available transmission rate of the network. The obtained results are summarizes in the Figure 12. Their values are not significantly worse, even if it could seem that the nodes should initiate a conten- tion concerning the access to the common channel, lead- ing to collisions. In the LR-WPAN network, the transac- tions realized in both direction ve station, so any contention is excluded. The de- crease of the transmission rate of the transmission chan- nel results from a worse efficiency of transmission di- rected towards the slave node. Any such transaction must start with a transmission of REQUEST and ACK frames (Figure 3 and Figure 6 vs. Figure 4 and Figure 7), in- creasing its duration. The coefficie scussed configuration, has slightly changed, because of the decrease of the transmission rate of the network (Figure 13). The form of both curves remains identical, confirming a total operation of the requests directed to- ward a system free of overloading. Figure 13. Bidirectional transmission in a system consisting of two nodes – coefficient of delivered packets. Copyright © 2010 SciRes. WSN  D. KOŚCIELNIK Copyright © 2010 SciRes. WSN 13 Figure 14. Bidirectional transmission in a system consisg tinFigure 16. Unidirectional transmission in a system contain- ing hidden stations – intensity of the operated traffic. of two nodes – average transmission delay time. Figure 15. Example of a system with a hidden station. Average delay time calculated for properly transmitted packets is about three times longer then the one discus- sed in example on Figure 14. Also this time, when reque- sts are suppressed, queues in transmitter buffers begin to grow quickly. As a result, the time when successful tran- .2. Influence of a Hidden Station for the Transmission Rate of the System Usually, a station of a large WPAN network embraces by its range only some closest nodes. More distant devices, not receiving its signal, may have an important negative impact for the transmission of data with the closest neighbors. The simplest example ted in Figure 15. alization of the receiver of this transmis- on, the range of the new transmission will include the of both fram of the trans- actions will result unsuccessful. The collisions caused by hidden stations are much more troublesome for the system that those resulting from the contention for the access to the radio channel. A long time of emission of a single frame significantly in- creases the probability of generating in this period a new request directed to the hidden station [3]. Its immediate realization will disturb the transaction being already in progress with the distant node. Studying the influence of the presence of a hidden sta- tion for the operation of the LR-WPAN network, we have used the model presented in Figure 15. A centrally places coordinator (node N0) works with two slave nodes (N1 and N2), located out of their reciprocal range. The entire offered traffic is evenly dividedween slave stations, rs exclusively to the coordinator. The results of simulation tests, summarized in Figure 16, indicate a radical decrease of the transmission rate of e system—for both transmission modes it equals to ervicing and to system overloading. Th smission of the subsequent packet may begin increases exponentially. 3 bet of this situation is pre-which direct their transfe sen The node N1 transmits data to the node N0 located in its range. The transmission is not „heard” by the node N2, which is a hidden station for N1. However, the range of N2 includes the N0 node. The hidden station does not know about the transaction being realized. After receiv- ing a transmission order, the node shall verify the chan- nel occupation and start the transmission. Irrespective of the physical loc th only 23% of the effective channel transmission rate. Moreover, the network works with the efficiency close to maximal only in certain, relatively narrow interval of the intensity of the offered traffic. A further increase of the number of requests results in an important worsening of the quality of their s e shape of obtained characteristics corresponds to the panic curve, defining the operation of many systems with collision access. si N0 node. In the area occupied by N0 a collision es will occur and at least one (the first)  D. KOŚCIELNIK 14 Figure 17. Unidirectional transmission in a system contain- ing hidden stations – average collision probability. Figure 18. Unidirectional transmission in a system contain- ing hidden stations – coefficient of delivered packets. F h igure 19. Bidirectional transmission in a system containing idden stations – intensity of the operated traffic. The reason of the decrease of the network transmis- sion rate when the intensity of the offered traffic exceeds of a given threshold value is the increase of the channel occupation time, favorable to the appearance of colli- sions with the hidden stations. The retransmissions acti- vated by both nodes increase in an artificial way the in- tensity of requests directed towards the system, leading to its overloading. It is worth to mention that in a con- gestion conditions the transmission rate of a non-syn- chronized network decreases to zero, whereas a synchro- nized system always guarantees a certain minimal level of the servicing of transmission requests. Such an ad- vantage is a side effect of the algorithm realized by the node of the LR-WPAN network, verifying before the start of each transaction, if its duration shall not exceed ts the verage collision probability, obtained for both network operation modes (non-synchronized and synchronized). The defined characteristics of the coefficient of deliv- ered packets indicate that the loss of frames appears even with a very little intensity of the offered traffic (Figure 18). Their reason is the cancellation of further retrans- missions of these packets, not delivered with a pre-de- fined admissible number of attempts. As the intensity of the requests increases, this phenomenon appears more and more often. In an overloaded system, the queues of the single emitters become overfilled and a more signifi- cant part of the offered traffic is refused. The objective of the successive series of tests con- sisted in verifying the influence of the hidden station for the node located in the range of its signal. In a system presented in Figure 15 this function is assumed by te coordinator. We should remind that the transactions f the limits of the finishing superframe. Thanks to that, the hidden station rarely disturbs the last transmission that can be fit into the superframe. The Figure 17 presen a h o the coordinator are initialized by other nodes of the clus- ter, strongly influenced by the presence of the hidden station. Based on this we can presume that the hidden station shall also disturb the servicing of requests di- rected towards the coordinator. The diagrams presented in Figure 19 have been ob- tained using the model given in Figure 15, in which the offered traffic has been evenly divided between all the nodes. Contrary to the assumptions, the presence of the hidden station has only a limited influence for the trans- actions realized by the coordinator. Moreover, the inten- sity of traffic realized by this station is not suddenly de- creased when the threshold value is exceeded, such as it was the case for the other nodes. The differences existing in the way of servicing the transactions realized in each direction are connected with the length of initiating frames. A transaction directed to the coordinated starts with a long DATA packet, whereas the transfer in the other direction is initiated with a much shorter REQUEST frame (Figure 3 and Figure 6 vs. Fig- ure 4 and Figure 7). Therefore, in the second case the Copyright © 2010 SciRes. WSN  D. KOŚCIELNIK Copyright © 2010 SciRes. WSN 15 s m by hidden sta- tio in system with bidirec- tio ission rate of ea ed in these conditions probability of a collision caused by the hidden station imoment, only one of two independent channels can be used—it signifies, that a half of the transm uch lower. Moreover, if a collision appears, its duration shall also be shorter, reducing its influence for the chan- nel transmission rate. The frames ACK and DATA initi- ated by the coordinator are received by all the nodes of the cluster, so the hidden stations have not any influence for the further part of the transaction. The transmission directed to the slave node is similar to a transaction con- cerning reservation of channels with RTS and CTS frames, used in IEEE802.11 standard and protecting WLAN network against problems created ch channel is lost. Studying the effects of an exposed station we have used the model presented in Figure 22. The intensity of the offered traffic is evenly divided between nodes N1 and N3. The characteristics obtain ns. Irrespective of the status of the system, the transmis- sion realized by the coordinator make that when the threshold value of the intensity of offered traffic is ex- ceeded, the coefficient of delivered packets does not de- crease to zero, as it was the case previously (Figure 20). Its value gradually decreases, because the overfilling of the buffer in the coordinator’s emitter results in the re- fusal of an increasing number of requests. Average collision probability nal transmission (Figure 21) is very similar to the one presented on Figure 17. The values of obtained points are quit identical to results of simulation tests of the system with unidirectional transmission. 3.3. Effect of the Exposed Station The problem of the exposed station appears in a LR-WP- AN network containing many ne Figure 20. Bidirectional transmission in a system containing hidden stations – coefficient of delivered packets. ighboring clusters. In a certain sense, this phenomenon is contrary to the above- mentioned effect of a hidden station. In this case, nodes belonging to different clusters and located in the range of their respective signals disturb the reciprocal effective utilization of independent, because physically separated transmission channels. An exemplary fragment of a syst- em containing exposed stations is presented in Figure 22. When the N1 node starts a transaction directed to its coordinator N0, the signal arrives also to the N3 station. When N3 receives in the same time a transmission re- quest, after verifying the status of the own channel it will incorrectly conclude that the channel is occupied and the start of the transmission will be unnecessary delayed. An identical problem concerns the N1 node in the case if the first transmission is started by the N3 device. In a given Figure 21. Bidirectional transmission in a system containing hidden stations – average collision probability. Figure 22. Example of a system containing exposed stations.  D. KOŚCIELNIK 16 Figure 23. Unidirectional transmission in a system contain- ing exposed stations – intensity of the operated traffic. Figure 24. Unidirectional transmission in a system contain- ing exposed stations – coefficient of delivered packets. are summarized in Figure 23. The obtained characteristics, as it concerns their shape and values, are very similar to those observed for the total smission rate of both clusters is slightly higher than e effective transmission rate of a single channel. The coefficients of delivered packets are also slightly higher, thanks to a double capacity of the buffers of both nodes (Figure 24) and the average transmission delay time is little longer (Figure 25). Therefore, the presence of ex- posed stations permits to use only the half of transmis- sion resources of each cluster. Nevertheless we should mention that—as opposed to the hidden station—the presence of an exposed node does not result in a com- plete stopping of the transmission in an overloaded sys- tem (see Figure 16 and Figure 18). system consisting of two nodes and realizing the trans- mission towards the coordinator (see Figure 9). The tran th Figure 25. Unidirectional transmission in a system contain- ing exposed stations – average transmission delay time. 4. Summary The main objective of the authors of the IEEE802.15.4 standard was to create a system that could contain an enormous number of nodes (even 264) and in the same protocol very simple to im- plement, guaranteeing minimal energy consumption. The fulfilling of all the abovementioned assumptions proves to be very difficult and—as the realized studies has shown—leads to an important decrease of the available transmission rate of the transmission channel. Important problems result also of the presence of a hidden station. One of several considered possibilities is the implemen- tation of a reservation of the channel by RTS and CTS frames, as it was made in the case of the IEEE802.11 standard [6,7]. Nevertheless, such a solution presents also a significant disadvantage, consisting in an impor- tant increase of the duration of different transactions, by definition used for transmitting little portions of data and using minimal energy. The reservation of the channel becomes particularly difficult in non-synchronized s- ng a tarting transmission. standard shall be subject time using a transmission ys tems, in which in any case the temporarily inactive hid- den stations will not receive information concerni s Certainly, the IEEE802.15.4 to further modifications. We shall presume that its cur- rent version shall be supplemented with mechanisms preventing the effects of the presence of hidden stations, exposed stations and hidden contention, related to the reciprocal movement of the nodes. However, we should answer the question if the implementation of these modi- fications is really necessary. A further development of the transmission protocol can lead to the loss of the idea of a simple and cheap system, using low transmission rates. Copyright © 2010 SciRes. WSN  D. KOŚCIELNIK 17 var, “A comprehensive simulation study of slotted CSMA/CA for IEEE 802.15.4 wireless sensor networks,” IPPHURRAY Research Gro- up, Polytechnic Institute of Porto, http://www.iis.sinica.edu.tw/~cclljj/publication/2006/06_ WCNC_802.15.4.pdf. [3] T. Sun, C. Ling-Jyh, H. Chih-Chieh, G. Yang, and M. Gerla, “Measuring Effective Capacity of IEEE 802.15.4 beaconless mode,” Institute of Information Science, Aca- demia Sinica, 2005. [4] L. Hwang, S. Sheu, Y. Shih, and Y. Cheng, “Grouping ingdom, 2008 , “Analysis of IEEE 802.11e standard in terms of real time application requirements,” Proceedings 5. References [1] A. Herms, G. Lukas, and S. Ivanom, “Realism in design and evaluation of wireless routing protocols,” http://ivs.cs.uni-magdeburg.de/EuK/forschung/publikatio nen/pdf/2006/awdsmspe.pdf. [2] A. Kouba, M. Alves, and M. To strategy for solving hidden node problem in IEEE 802.15.4 LR-WPAN,” Proceedings of IEEE International Symposium of Industrial Electronics, Montreal, Kanada 2006. [5] B. Latré, P. De Mil, I. Moerman, B. Dhoedt, and P. Piet Demeester, “Throughput and Delay Analysis of Unslotted IEEE 802.15.4,” http://www.academypublisher.com/jnw/vol01/no01/jnw0 1012028.pdf. [6] D. Kościelnik, “Simulation study of the influence of hid- den stations for the quality of service in the IEEE802.11e WLAN,” Proceedings of IEEE International Symposium of Industrial Electronics, ISIE08, Cambridge, United K [7] D. Kościelnik of International Conference on Wireless and Mobile Communication, Bukareszt, Rumunia, 2006. C opyright © 2010 SciRes. WSN |

