Paper Menu >>
Journal Menu >>
 J. Software Engineering & Applications, 2009, 2: 383-387 doi:10.4236/jsea.2009.25051 Published Online December 2009 (http://www.SciRP.org/journal/jsea) Copyright © 2009 SciRes JSEA 383 Information Hiding Method Based on Block DWT Sub-Band Feature Encoding Qiudong SUN, Wenxin MA, Wenying YAN, Hong DAI School of Electronic and Electrical Engineering, Shanghai Second Polytechnic University, Shanghai, China. Email: {qdsun, wxma, wyyan, daihong}@ee.sspu.cn Received August 12th, 2009; revised September 17th, 2009; accepted October 10th, 2009. ABSTRACT For realizing of long text information hiding and covert communication, a binary watermark sequence was obtained firstly from a text file and encoded by a redundant encoding method. Then, two neighboring blocks were selected at each time from the Hilbert scanning sequence of carrier image blocks, and transformed by 1-level discrete wavelet transformation (DWT). And then the double block based JNDs (just noticeable difference) were calculated with a visual model. According to the different codes of each two watermark bits, the average values of two corresponding detail sub-bands were modified by using one of JNDs to hide information into carrier image. The experimental results show that the hidden information is invisible to human eyes, and the algorithm is robust to some common image processing operations. The conclusion is that the algorithm is effective and practical. Keywords: Sub-Band Feature Encoding, Redundant Encoding, Visual Model, Discrete Wavelet Transformation, Information Hiding 1. Introduction With the development of information technology, people have paid more and more attention to the information security. Information hiding in a digital image has be- come the focus of the information security research. For an effective information hiding scheme, three basic re- quirements should be satisfied: transparency, robustness and security. The former two are in conflict with each other. To dissolve this conflict availably, we can consider using the masking characteristic of human visual system (HVS) [1]. Duo to its good time-frequency localization function is similar to the visual masking of HVS, the DWT has been used widely in the field of information hiding [2]. A good hiding technique should also extract the hidden information from stego-image blindly. In recent years, many algorithms based on HVS and DWT had been proposed for information hiding [1–6]. And some [1–3] of them also had implemented the blind extraction of hidden information. But those algorithms are mostly armed at binary iconic watermark. So they are unsuitable for hiding the text information and covert communication. The reference [5] proposed a robust en- cryption technique for text information. Though the transparency, robustness and security of that algorithm were all good, the embedded capacity was restricted due to only one bit watermark can be hidden in two blocks, whose sizes were settled as 8×8. Use for reference [5] in watermark embedding, we propose an adaptive information hiding method based on average value relation of corresponding DWT sub-bands of two neighboring blocks with double JND thresholds and adjustable block size. As mentioned previously, in order to adjust the input image for transparent water- marks, we employ a visual model [2,5] to calculate the different double block based JND thresholds for deter- mining the intensity of watermarking at the different lo- cation of image. We also give a redundant encoding method for robustness. This paper is organized as follows. In Section 2, we give the JND threshold calculation equation for control- ling the embedding intensity. Section 3 presents the in- formation hiding algorithm and its extraction in detail. Section 4 examines the performance of proposed algo- rithm, and shows that the proposed scheme yields more effective and better performance, both in terms of trans- parency and robustness through simulation. Section 5 gives the conclusion of this paper. 2. JND Threshold Calculation 2.1 Visual Model Under the background gray f, the human eyes relative sensitivity to gray change (f)=f/f, which is a non-linear function of f, can be approximated by the equation as follows [5]:  Information Hiding Method Based on Block DWT Sub-Band Feature Encoding 384 128 1 )256( 1 1 281 ee02.0)( ff f f f (1) where e is the base of natural logarithm. In experiment, we can use the gray mean of K×K image block Buv lo- cated at (u, v) as the background gray f, i.e. f=mean (Buv). 2.2 JND Calculation To ensure the watermark has good transparency and ro- bustness, we can use JND to adjust the intensity of wa- termark-embedding [2,4,5]. The image block Buv is DWT-transformed into an approximate image and three detail sub-band images ( sHH,∈ HL, LH, represent the three detail sub-bands of diagonal, horizontal and vertical directions respectively). The JNDs of three detail sub-bands are represented as follows: s uv D suv s uv FTJ (2) where is the normalized value of uv T uvuv ff ET at the range [a,b], while Euv is the normalized entropy of Buv. When sHH, ∈Fs equals 2, otherwise it is 1 [4]. 3. Adaptive Information Hiding Scheme 3.1 Watermark Embedding Let W represents a watermark sequence, Buv1 and Buv2 are two neighboring image blocks and their DWT-trans- formed detail sub-bands are and (simply marked by D1 and D2, or by a universal symbol Dt, t{1, ∈ 2}). Now we can define the admissible distortion factor of sub-band coefficients of DWT as follows: s uv1 Ds uv2 D 2} {1, ) mean(t t t t D D λ (3) where is a positive number, which is an effect factor of absolute values of detail sub-band coefficients to embed- ding intensity. When the block size is 2×2, whatever the value of is, the Equation (3) is constant and can be simplified to . 1 t λ We assume that is the mean value of JNDs of two neighboring blocks. It is represented by equation as fol- lows: s uv s uv 21 2 1JJ (4) If the crytic normalized range of [a,b] in Equation (2) is set by two different un-overlapped ascend ranges [a0,b0] and [a1,b1], such as [1,2] and [6,7], then we can get two different from Equations (2) and (4). They can be rep- resented by 0and 1, or by a universal symbol r, r∈{0,1}. We also assume that d is the corresponding DWT detail sub-band coefficients difference of two neighbor- ing blocks at same direction, and is the adjustment intensity matrix of detail sub-bands coefficients. They are represented by equations as follows respectively: )mean()mean(Sign12 DDW k d (5) dt k tkt 1 Sign 2 1 W λWε (6) where Sign(·) is a sign function, it is defined as follows: odd 1 even 1 Sign x x x Wk is the k-th element of binary watermark sequence W. If the DWT detail sub-band features of two neighbor- ing blocks after embedded should satisfy the relationship with the consecutive two bits Wk and Wk+1 of watermark sequence as shown in Table 1. We can prove that the watermark embedding rule is as follows: otherwise 0or and 1 if 11 t kktt t d D WWεD D (7) From the embedding rule, we know that each couple corresponding detail sub-bands of two neighboring blocks can be embedded 2 watermark bits. And the two neighboring blocks have three couple corresponding de- tail sub-bands. So, if the size of carrier image is M×N, the information hiding capacity of this algorithm can reach to the value of (3MN)/(K2) bits. It is double than that of [5]. For example, if the size of carrier image is 512×512 and the block size is 2×2, then the full informa- tion hiding capacity is 196608 bits or 24576 bytes. It is large enough to hide information. If applied to hide short text information into a carrier image, this method can bring an enough redundancy to ensure its robustness. 3.2 Watermark Extraction Being the same with watermark embedding, we should select two neighboring blocks B′uv1 and B′uv2 each time from Hilbert scanning sequence of stego-image blocks, and a couple of their DWT detail sub-bands 1 D ˆ and 2 D ˆ. d set th=(b0+a1)/2. Then, we can prove that the wa- termark extraction rule is as follows: An Table 1. The relationship between watermark codes and the DWT detail sub-band features of two neighboring blocks Wk and Wk+1 The size relationship of corresponding DWT detail sub-bands 00 012 )mean()mean( DD 01 112 )mean()mean( DD 10 012 )mean()mean( DD 11 112 )mean()mean( DD Copyright © 2009 SciRes JSEA 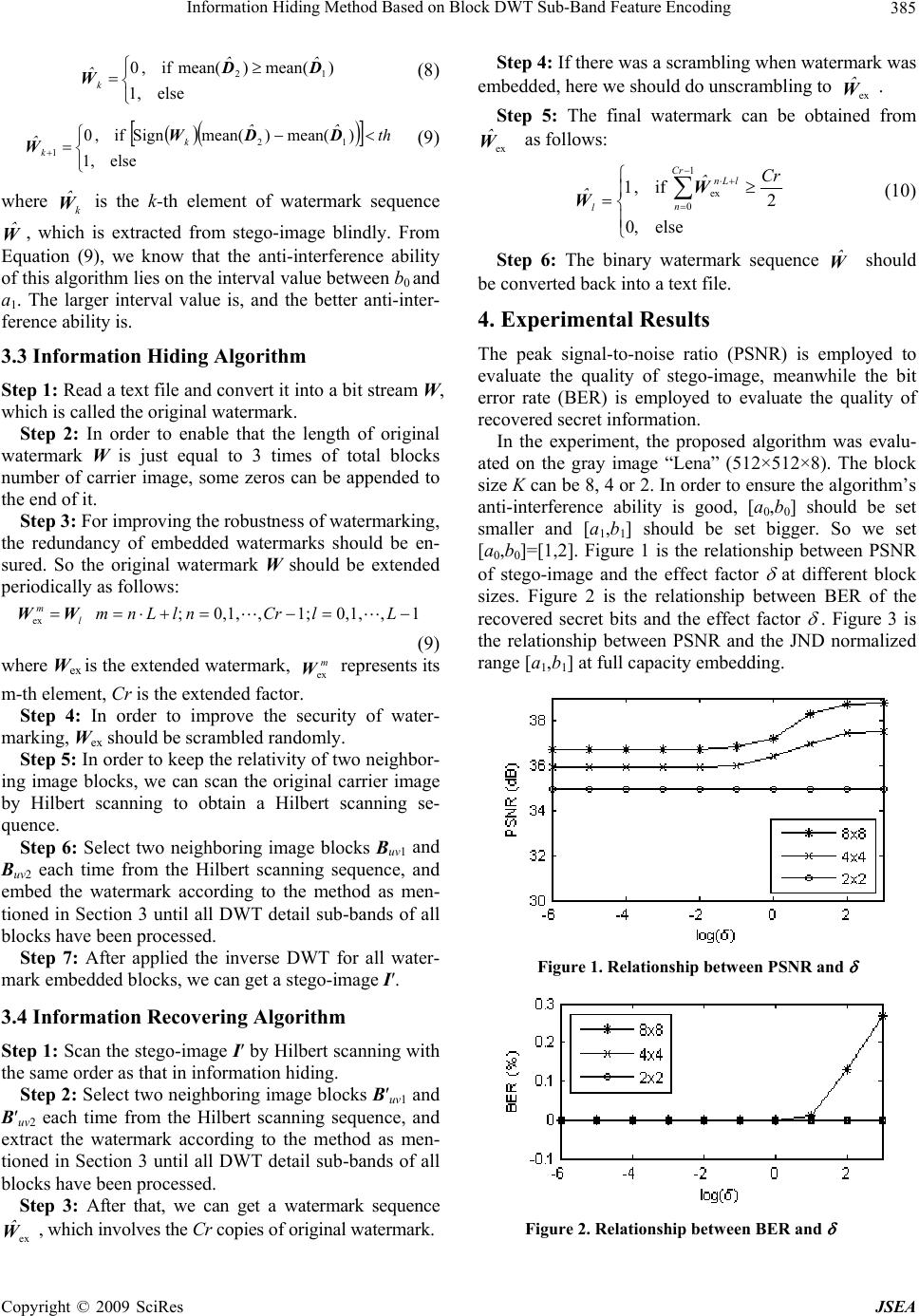 Information Hiding Method Based on Block DWT Sub-Band Feature Encoding385 else 1, )mean()mean( if , 012 DD W ˆˆ ˆk (8) else 1, )mean()mean(Sign if , 012 1 th ˆˆ ˆk k DDW W (9) where is the k-th element of watermark sequence , which is extracted from stego-image blindly. From Equation (9), we know that the anti-interference ability of this algorithm lies on the interval value between b0 and a1. The larger interval value is, and the better anti-inter- ference ability is. k ˆ W W ˆ 3.3 Information Hiding Algorithm Step 1: Read a text file and convert it into a bit stream W, which is called the original watermark. Step 2: In order to enable that the length of original watermark W is just equal to 3 times of total blocks number of carrier image, some zeros can be appended to the end of it. Step 3: For improving the robustness of watermarking, the redundancy of embedded watermarks should be en- sured. So the original watermark W should be extended periodically as follows: 1,0,1,1;,0,1, ; ex LlCrnlLnm l mWW (9) where Wex is the extended watermark, represents its m-th element, Cr is the extended factor. m ex W Step 4: In order to improve the security of water- marking, Wex should be scrambled randomly. Step 5: In order to keep the relativity of two neighbor- ing image blocks, we can scan the original carrier image by Hilbert scanning to obtain a Hilbert scanning se- quence. Step 6: Select two neighboring image blocks Buv1 and Buv2 each time from the Hilbert scanning sequence, and embed the watermark according to the method as men- tioned in Section 3 until all DWT detail sub-bands of all blocks have been processed. Step 7: After applied the inverse DWT for all water- mark embedded blocks, we can get a stego-image I′. 3.4 Information Recovering Algorithm Step 1: Scan the stego-image I′ by Hilbert scanning with the same order as that in information hiding. Step 2: Select two neighboring image blocks B′uv1 and B′uv2 each time from the Hilbert scanning sequence, and extract the watermark according to the method as men- tioned in Section 3 until all DWT detail sub-bands of all blocks have been processed. Step 3: After that, we can get a watermark sequence ex W ˆ , which involves the Cr copies of original watermark. Step 4: If there was a scrambling when watermark was embedded, here we should do unscrambling to ex W ˆ . Step 5: The final watermark can be obtained from ex W ˆ as follows: else ,0 2 if , 1 1 0 ex Cr n lLn l Cr ˆ ˆW W (10) Step 6: The binary watermark sequence should be converted back into a text file. W ˆ 4. Experimental Results The peak signal-to-noise ratio (PSNR) is employed to evaluate the quality of stego-image, meanwhile the bit error rate (BER) is employed to evaluate the quality of recovered secret information. In the experiment, the proposed algorithm was evalu- ated on the gray image “Lena” (512×512×8). The block size K can be 8, 4 or 2. In order to ensure the algorithm’s anti-interference ability is good, [a0,b0] should be set smaller and [a1,b1] should be set bigger. So we set [a0,b0]=[1,2]. Figure 1 is the relationship between PSNR of stego-image and the effect factor at different block sizes. Figure 2 is the relationship between BER of the recovered secret bits and the effect factor Figure 3 is the relationship between PSNR and the JND normalized range [a1,b1] at full capacity embedding. Figure 1. Relationship between PSNR and Figure 2. Relationship between BER and Copyright © 2009 SciRes JSEA 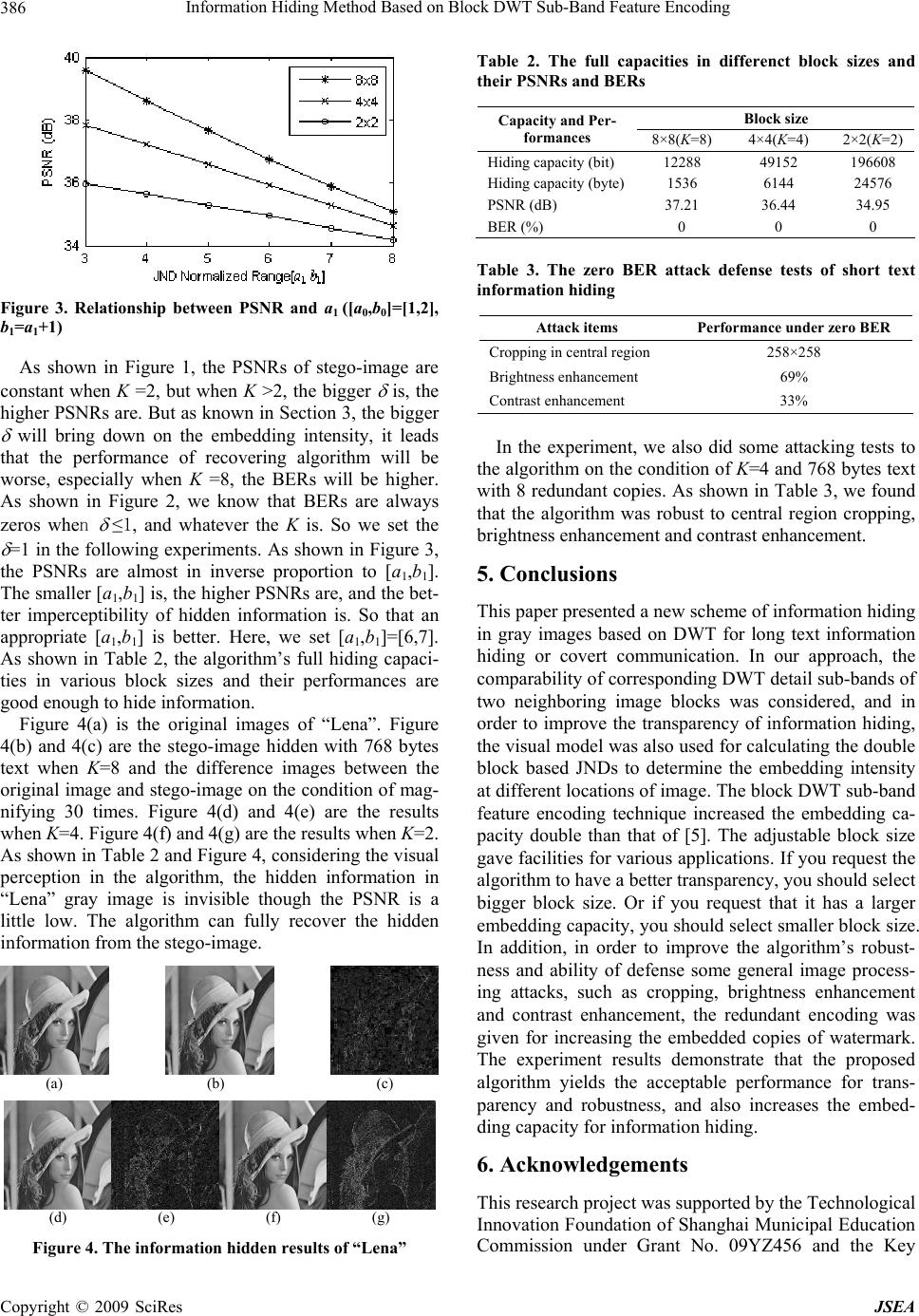 Information Hiding Method Based on Block DWT Sub-Band Feature Encoding 386 Figure 3. Relationship between PSNR and a1 ([a0,b0]=[1,2], b1=a1+1) As shown in Figure 1, the PSNRs of stego-image are constant when K =2, but when K >2, the bigger is, the higher PSNRs are. But as known in Section 3, the bigger will bring down on the embedding intensity, it leads that the performance of recovering algorithm will be worse, especially when K =8, the BERs will be higher. As shown in Figure 2, we know that BERs are always zeros when ≤1, and whatever the K is. So we set the =1 in the following experiments. As shown in Figure 3, the PSNRs are almost in inverse proportion to [a1,b1]. The smaller [a1,b1] is, the higher PSNRs are, and the bet- ter imperceptibility of hidden information is. So that an appropriate [a1,b1] is better. Here, we set [a1,b1]=[6,7]. As shown in Table 2, the algorithm’s full hiding capaci- ties in various block sizes and their performances are good enough to hide information. Figure 4(a) is the original images of “Lena”. Figure 4(b) and 4(c) are the stego-image hidden with 768 bytes text when K=8 and the difference images between the original image and stego-image on the condition of mag- nifying 30 times. Figure 4(d) and 4(e) are the results when K=4. Figure 4(f) and 4(g) are the results when K=2. As shown in Table 2 and Figure 4, considering the visual perception in the algorithm, the hidden information in “Lena” gray image is invisible though the PSNR is a little low. The algorithm can fully recover the hidden information from the stego-image. (a) (b) (c) (d) (e) (f) (g) Figure 4. The information hidden results of “Lena” Table 2. The full capacities in differenct block sizes and their PSNRs and BERs Block size Capacity and Per- formances 8×8(K=8) 4×4(K=4) 2×2(K=2) Hiding capacity (bit) 12288 49152 196608 Hiding capacity (byte)1536 6144 24576 PSNR (dB) 37.21 36.44 34.95 BER (%) 0 0 0 Table 3. The zero BER attack defense tests of short text information hiding Attack items Performance under zero BER Cropping in central region 258×258 Brightness enhancement 69% Contrast enhancement 33% In the experiment, we also did some attacking tests to the algorithm on the condition of K=4 and 768 bytes text with 8 redundant copies. As shown in Table 3, we found that the algorithm was robust to central region cropping, brightness enhancement and contrast enhancement. 5. Conclusions This paper presented a new scheme of information hiding in gray images based on DWT for long text information hiding or covert communication. In our approach, the comparability of corresponding DWT detail sub-bands of two neighboring image blocks was considered, and in order to improve the transparency of information hiding, the visual model was also used for calculating the double block based JNDs to determine the embedding intensity at different locations of image. The block DWT sub-band feature encoding technique increased the embedding ca- pacity double than that of [5]. The adjustable block size gave facilities for various applications. If you request the algorithm to have a better transparency, you should select bigger block size. Or if you request that it has a larger embedding capacity, you should select smaller block size. In addition, in order to improve the algorithm’s robust- ness and ability of defense some general image process- ing attacks, such as cropping, brightness enhancement and contrast enhancement, the redundant encoding was given for increasing the embedded copies of watermark. The experiment results demonstrate that the proposed algorithm yields the acceptable performance for trans- parency and robustness, and also increases the embed- ding capacity for information hiding. 6. Acknowledgements This research project was supported by the Technological Innovation Foundation of Shanghai Municipal Education Commission under Grant No. 09YZ456 and the Key Copyright © 2009 SciRes JSEA  Information Hiding Method Based on Block DWT Sub-Band Feature Encoding Copyright © 2009 SciRes JSEA 387 Disciplines of Shanghai Municipal Education Commis- sion under Grant No. J51801. REFERENCES [1] M. Barni, F. Bartolini, and A. Piva, “Improved wavelet- based watermarking through pixel-wise masking,” IEEE Transactions on Image Processing, Vol. 10, No. 5, pp. 783–791, 2001. [2] H. F. Yang and X. W. Chen, “A robust image-adaptive public watermarking technique in wavelet domain,” Journal of Software, Vol. 14, No. 9, pp. 1652–1660, 2003. [3] J. G. Cao, J. E. Fowler, and N. H. Younan, “An image- adaptive watermark based on a redundant wavelet trans- form,” In: Pitas I, ed. Proceedings of the IEEE Interna- tional Conference on Image Processing, Thessaloniki, pp. 277–280, 2001. [4] Z. M. Wang, Y. J. Zhang, and J. H. Wu, “A wavelet do- main watermarking technique based on human visual system,” Journal of Nanchang University (Natural Sci- ence), Vol. 29, No. 4, pp. 400–403, 2005. [5] Q. D. Sun, W. X. Ma, W. Y. Yan, and H. Dai, “Text en- cryption technique based on robust image watermarking,” Journal of Image and Graphics, Vol. 13, No. 10, pp. 1942–1946, 2008. [6] L. Y. Wu and F. Yang, “An improved digital watermark- ing algorithm based on DWT,” Control and Automation, Vol. 23, No. 6(3), pp. 46–47, 59, 2007. |

