 Wireless Sensor Network, 2009, 1, 407-416 doi:10.4236/wsn.2009.15049 Published Online December 2009 (http://www.scirp.org/journal/wsn). Copyright © 2009 SciRes. WSN 407 An Energy-Efficient MAC Protocol for Ad Hoc Networks Yongsheng SHI, T. Aaron GULLIVER Department of El ectri cal and C om puter Engineering Universit y of Victori a P.O. Box 3055 STN CSC Victoria, B.C. V8W 3P6 CANADA Email: {yshi, agullive}@ece.uvic.ca Received July 21, 2009; revised August 26, 2009; accepted August 28, 2009 Abstract A mobile ad hoc network (MANET) is a collection of nodes equipped with wireless communications and a networking capability without central network control. Nodes in a MANET are free to move and organize themselves in an arbitrary fashion. Energy-efficient design is a significant challenge due to the characteristics of MANETs such as distributed control, constantly changing network topology, and mobile users with lim- ited power supply. The IEEE 802.11 MAC protocol includes a power saving mechanism, but it has many limitations. A new energy-efficient MAC protocol (EE-MAC) is proposed in this paper. It is shown that EE-MAC performs better than IEEE 802.11 power saving mode and exceeds IEEE 802.11 with respect to balancing network throughput and energy savings. Keywords: Energy-Efficient, MAC Protocol, IEEE 802.11, Ad Hoc Networks 1. Introduction Energy efficiency is a major challenge in wireless net- works. In order to facilitate untethered communication, most wireless network devices are portable and battery- powered and thus operate on an extremely constrained energy budget. However, progress in battery technology shows that only small improvements in battery capacity can be expected in the near future [1]. Furthermore, since recharging or replacing batteries is costly or, under some circumstance, impossible, it is desirable to keep the en- ergy-dissipation level of devices as low as possible. A mobile ad hoc network is a collection of two or more nodes equipped with wireless communications and networking capabilities without central network control, i.e. an infrastructure-less mobile network. Energy-efficient design in MANETs is more important and challenging than with other wireless networks. First, due to the ab- sence of an infrastructure, mobile nodes in a n ad hoc net- work must act as routers and participate in the process of forwarding packets. Therefore, traffic loads in MANETs are heavier than in other wireless networks with fixed access points or base stations and thus MANETs have more energy consumption. Second, energy-efficient de- sign needs to consider the trade-offs between different network performance criteria. For example, routing pro- tocols usually try to find a shortest path from sources to destinations. It is likely that some nodes will over-serve the network and th eir energy will be drained quickly, and thus cause the network to be partitioned. Therefore sim- ple solutions that only consider power constraints may cause a severe performance degradation. Third, no cen- tralized control implies that energy-efficient management in MANETs must be done in a distributed and coopera- tive manner, which is difficult to achiev e. At the wireless interface, energy consumption in idle mode is only slightly less than transmit mode and almost equal to receive mode [2]. Therefore, it is desirable to build a network protocol that maximizes the time the device is in sleep mode (the wireless interface turned off), and also maximizes the number of wireless devices in sleep mode. Many protocols have been proposed to deal with this challenge [3–6]. In this paper, a new energy-efficient MAC protocol, EE-MAC, is proposed. The design is based on the fact that most applications of ad hoc networks are data- driven, which means that the sole purpose of forming an ad hoc ne twork is to co llec t and d isperse data . Hence, keeping all network nodes awake is costly and unnec- essary when some nodes do not have traffic to carry. The proposed protocol conserves energy by turning off the radios of specific nodes in the network. The goal is to reduce energy consumption without significantly reducing network performance. EE-MAC is based on IEEE 802.11 and its power saving mode, and can pro- vide useful information to the network layer for route discovery. The rest of this paper is organized as follows. Section 2 introduces related work and gives an overview of cur- rent energy-efficient protocols for MANETs. Section 3 introduces IEEE 802.11 pow er saving mode (PSM). Sec-  Y. S. SHI ET AL. 408 tion 4 describes the proposed protocol, EE-MAC. In Sec- tion 5, performance results are given and EE-MAC is compared to 802.11 and 802.11 PSM. Finally, some conclusions are given in Section 6. 2. Related Work Energy-efficient protocol design is a cross-layer issue and usually spans the network layer and MAC layer. These two layers have different approaches to dealing with power management. At the network layer, en- ergy-efficient routing is a very active research topic. The aim is to choose routes for unicast sessions so as to maximize the overall network lifetime. Essentially, the design principle of energy-efficient routing is to equally balance energy expenditure among network nodes rather than directly reduce power consumption at each node. On the other hand, the MAC layer approach is to turn off the device network interface when it does not have any traffic. Thus, a design combining routing and MAC con- siderations is appropriate for energy-efficient protocols. We discuss some of the proposed solutions in the re- mainder of this section. Local energy-aware routing (LEAR) [4] is an en- ergy-efficient routing protocol that does not consider the MAC layer, while the dynamic power saving mechanism (DPSM) [3] and the on-demand power management [5] protocols are MAC layer approaches. Geographic adap- tive fidelity (GAF) [6] is a cross-layer design, but it needs geographic position devices to provide location information. LEAR is based on the dynamic source routing (DSR) protocol, where route discovery requires flooding of route-request messages. The basic idea of LEAR is to consider the willingness of each mobile node to partici- pate in the routing and forwarding of data packets on behalf of others. This is based on the local information of a mobile node. When a routing path is being established, each mobile node relies on information on remaining battery power to decide whether or not to participate in the selection process of a route path. When a node’s re- maining battery power is higher than a certain threshold, route-request messages are forwarded and the node joins in the route path selection process; otherwise, the mes- sage is discarded. Thus, all intermediate nodes along the route path have sufficient power and the first arriving route message is considered to have followed an en- ergy-efficient as well as a reasonably short path. If any of the intermediate nodes drop the route-request message, which means no nodes are willing to join the route path, the source will not receive a single reply even though a route may exist. To prevent this, the source node will resend the same route request message with a lower threshold. Observing that the fixed beacon interval in IEEE 802.11 PSM wastes energy, DPSM uses adaptively changed ad hoc traffic indication messages (ATIMs). Coupled with a separate DATA window, DPSM can control the transition to the low-power state in the middle of a beacon interval. Therefore, a node is allowed to en- ter sleep mode after completing any transmissions that are explicitly announced in the ATIM window, and a longer sleep mode time is achieved. On-demand power management for ad hoc networks bases power management decisions on traffic in the net- work. The key idea is that transitio ns from power-saving mode to active mode are triggered by communication events instead of the established beacon interval used in IEEE 802.11 PSM. On the other hand, transitions from active mode to power-saving mode are determined by a soft-state timer which is refreshed by the same commu- nication events that trigg er a transition to active mode. A node uses HELLO messages to track its neighbor’s power management state to decide whether or not to send packets to them. The GAF protocol identifies redundant nodes with re- spect to routing and turns them off without sacrificing routing fidelity. Each node uses location information based on GPS to associate itself with a virtual grid, where nodes in a particular grid square are redundant with respect to forwarding packets. One master node in each grid stays awake to route packets. With GAF, nodes can be in three states, sleep, discov er or active. Initially a node is in the discover state and exchanges discovery messages including grid IDs to find other nodes within the same grid. A node becomes a master if it does not hear any discovery messages for a given period of time. If more than one node can become a master, the one with the longest expected lifetime becomes the master and handles the routing for that grid square. 3. An Overview of IEEE 802.11 Power Saving Mode Power management can achieve great savings in infra- structure networks. All traffic for mobile stations must go through access points, so they are ideal locations to buffer traffic. However, in ad hoc networks, far more of the burden is placed on the sender to ensure that the re- ceiver is active or awake. Receivers must also be more available and cannot sleep for as long as in infrastructure networks. Power management in IEEE 802.11 power saving mode (PSM) is based on traffic indication messages. Nodes use ATIMs to notify other nodes to prepare to receive data. All nodes have to wake up periodically to listen for ATIMs and check whether they have packets to receive. In PSM [7,8], time is divided into beacon intervals and each beacon interval starts with an ATIM window. This Copyright © 2009 SciRes. WSN  Y. S. SHI ET AL.409 window is the period during which nodes must remain active and no stations are permitted to power down their wireless interface. The ATIM window size is a parameter that can be adjusted. Setting it to 0 means no power man- agement is used. There are four possibilities for a nod e in terms of ATIMs: the node has transmitted an ATIM, received an ATIM, neither transmitted nor received, or both transmitted and received. Nodes that transmit ATIM frames do not sleep because this indicates an intent to transmit buffered traffic. Nodes to which an ATIM is addressed must also keep awake so they can receive data packets from the ATIM sender. A node that both trans- mits and receives of course needs to be active. Thus, only those nodes that neither transmit nor receive an ATIM can go to sleep after the ATIM window. Figure 1 illustrates the basic PSM operations. Nod es A and B have advertised packets in the ATIM window by sending ATIMs and receiving ATIM-ACKs, both of which are subject to the DCF rules described earlier. Therefore nodes A and B remain awake for the rest of the beacon interval. The transmission of data packets from nodes A and B takes place during the beacon interval. The node that has no packets to transmit can go into sleep mode at the end of the ATIM window if it does not receive an ATIM during the window. In Figure 1, node C enters sleep mode after the ATIM window, thus saving energy. All sleeping nodes wake up again at the start of the next beacon interval. The beacon and ATIM window sizes can affect the performance of PSM. Since no data packets are trans- mitted in the ATIM window, overhead in terms of en- ergy consumption and bandwidth is incurred. If we use a small ATIM window to improve energy savings, there may not be enough time to advertise all buffered data packets. Conversely, using a large ATIM window may unnecessarily waste bandwidth and not leave enough time to transmit buffered data. Moreover, PSM also suf- fers from long packet delivery latency: for each hop that a packet traverses, the packet is expected to be delayed Figure 1. IEEE 802.11 PSM operation. for at least a beacon period. PSM was originally de- signed for single-hop networks, which means all nodes in the network are fully connected. However, ad hoc net- works are usually multi-hop networks, and thus PSM is not an ideal solution. 4. The Proposed EE-MAC Protocol The key idea of EE-MAC is to elect master nodes from all nodes in the network. Master nodes stay awake all the time and act as a virtual backbone to route packets in the ad hoc network. Other nodes, called slave nodes, remain in an energy-efficient mode and wake up periodically to check whether they have packets to receive. To be fair, a rotation mechanism between masters and slaves is used. EE-MAC uses some features of PSM, such as periodi- cally waking up at the beginning of the beacon interval. EE-MAC can provide knowledge and guidance to the route lookup process, because only master nodes can be selected along a routing path. On the other hand, EE-MAC requires a mechanism to awaken a sleeping node when packet delivery is imminent. This is usually handled by low-level mechanisms at the MAC or physi- cal layers. In EE-MAC, if a node has been asleep for a while, packets addressed to it are not lost but are stored at one of its upstream nodes, usually a master. When the node awakens, the buffered data is sent to it (this is a PSM feature which is used in our protocol). 4.1. Design Criteria We consider the following design criteria. The protocol must ensure enough master nodes are elected to build the backbone of the network so that every node has at least one master in its vicinity. A col- lection of masters can be described as a connected dominating set (CDS). All nodes are either a member of the CDS or a direct neighbor of at least one of the mem- bers of the CDS. Nodes in the CDS serve as the routing backbone and remain active all the time. All other nod es are slave nodes and can choose to sleep. Since slave nodes do not join in the process of route discovery or packet forwarding, network connectivity is decreased. To prevent a dramatic decrease in throughput, an acceptable set of masters is required to maintain global connectivity with some redund ancy. The master node election algorithm is based on lo- cal information, which is a distributed approach. Each node only employs local information to determine whether it will become a master. Due to the characteris- tics of distributed management in ad hoc networks and the two essential requirements, low overhead and fast convergence, the algorithm for finding a CDS should be localized. The election algorithm is given in the next section. Copyright © 2009 SciRes. WSN 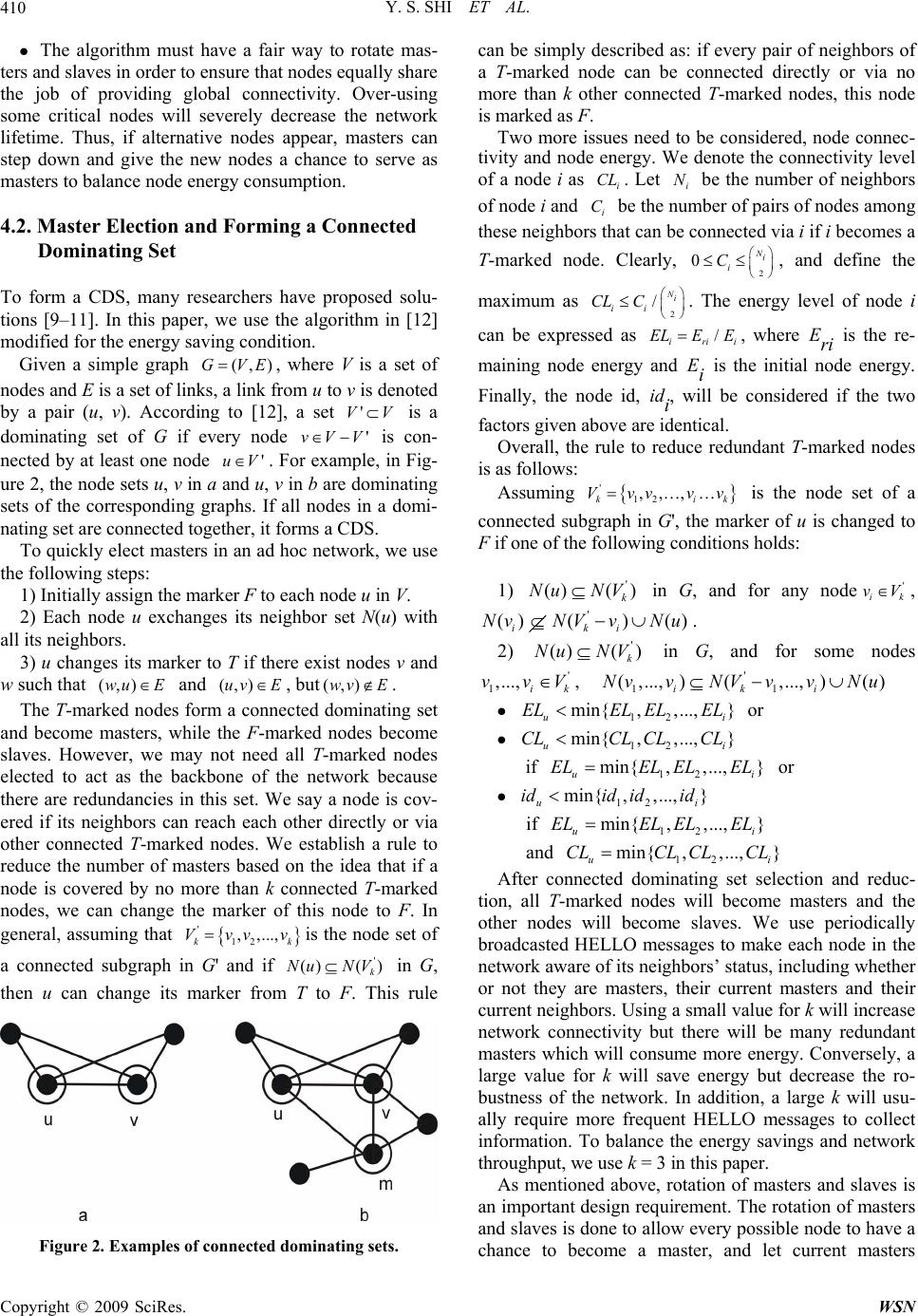 Y. S. SHI ET AL. 410 The algorithm must have a fair way to rotate mas- ters and slaves in order to ensure th at nodes equa lly share the job of providing global connectivity. Over-using some critical nodes will severely decrease the network lifetime. Thus, if alternative nodes appear, masters can step down and give the new nodes a chance to serve as masters to balance node energy consumption. 4.2. Master Election and Forming a Connected Dominating Set To form a CDS, many researchers have proposed solu- tions [9–11]. In this paper, we use the algorithm in [12] modified for the energy sav ing condition. Given a simple graph , where V is a set of nodes and E is a set of links, a link from u to v is denoted by a pair (u, v). According to [12], a set is a dominating set of G if every node vV is con- nected by at least one node (,)GVE 'uV 'VV 'V . For example, in Fig- ure 2, the node sets u, v in a and u, v in b are dominatin g sets of the corresponding graphs. If all nodes in a domi- nating set are connected together, it forms a CDS. To quickly elect masters in an ad hoc network, we use the following steps: 1) Initially assign the marker F to each node u in V. 2) Each node u exchanges its neighbor set N(u) with all its neighbors. 3) u changes its marker to T if there exist nodes v and w such that and (, , but(,(,)wu E)uv E)wv E . The T-marked nodes form a connected dominating set and become masters, while the F-marked nodes become slaves. However, we may not need all T-marked nodes elected to act as the backbone of the network because there are redundancies in this set. We say a node is cov- ered if its neighbors can reach each other directly or via other connected T-marked nodes. We establish a rule to reduce the number of masters based on the idea that if a node is covered by no more than k connected T-marked nodes, we can change the marker of this node to F. In general, assuming that '12 , ,..., k Vvvvk is the node set of a connected subgraph in G' and if ' ()( ) k uNV in G, then u can change its marker from T to F. This rule Figure 2. Examples of connected dominating sets. can be simply described as: if every pair of neighbors of a T-marked node can be connected directly or via no more than k other connected T-marked nodes, this node is marked as F. Two more issues need to be considered, node connec- tivity and nod e energy. We deno te the connectivity level of a node i as . Let i CL i be the number of neighbors of node i and be the number of pairs of nodes among these neighbors that can be connected via i if i becomes a T-marked node. Clearly, , and define the maximum as . The energy level of node i can be expressed as i C CL 2 Ni i C / irii E 0 2 Ni E / ii C EL , where Eri is the re- maining node energy and Ei is the initial node energy. Finally, the node id, idi, will be considered if the two factors given above are identical. Overall, the rule to reduce redundant T-marked nodes is as follows: Assuming '12 ,,, ki Vvv vv k is the node set of a connected subgraph in G', the marker of u is changed to F if one of the following conditions holds: 1) in G, and for any node ' ()( ) k Nu NV' ik vV , ' ()() () iki NvNV vNu . 2) in G, and for some nodes ' ()( ) k Nu NV ' ik V 1,...,vv , ' 11 ., )(,..., )() ik i vNV vvNu ( ,..Nv 12 min{ ,,...,} ui ELEL ELEL or 12 min{ ,,...,} ui CLCL CLCL if 12 min{ ,,...,} ui ELEL ELEL or 12 min{ ,,...,} ui idid idid if 12 min{ ,,...,} ui ELEL ELEL and 12 min{ ,,...,} ui CLCL CLCL After connected dominating set selection and reduc- tion, all T-marked nodes will become masters and the other nodes will become slaves. We use periodically broadcasted HELLO messages to make each node in the network aware of its neighbors’ status, including whether or not they are masters, their current masters and their current neighbors. Using a small value for k will increase network connectivity but there will be many redundant masters which will consume more energy. Conversely, a large value for k will save energy but decrease the ro- bustness of the network. In addition, a large k will usu- ally require more frequent HELLO messages to collect information. To balance the energy savings and network throughput, we use k = 3 in this paper. As mentioned above, rotation of masters and slaves is an important design requirement. The rotation of masters and slaves is done to allow every possible node to have a chance to become a master, and let current masters Copyright © 2009 SciRes. WSN  Y. S. SHI ET AL.411 change their role to save energy. Each master periodi- cally checks if it should withdraw as a master. The con- ditions to trigger a withdrawal are essentially the same as for CDS reduction given above. However, in order to balance the network load, we force some masters to quit even if the conditions to withdraw are not met. After a node has served as a master for some period of time or if its energy level is below a certain value of ELi and the average of its neighbors, it will withdraw even if there are no masters nearby. The only exception is if some neighbors can only be connected to the network via that node. 4.3. Features of EE-MAC In EE-MAC, since masters do not operate in power sav- ing mode and can forward packets all the time, the packet delivery ratio and packet delay can be improved greatly compared to PSM. In this section, we present the important features of EE-M A C . 4.3.1. Entering Sleep Mode Earlier In the original PSM, a node with packets to transmit will send an ATIM frame to the destination, and both source and destination will stay awake in that beacon interval, no matter how many packets need to be transmitted. While this approach has its advantages, it may result in much higher energy consumption than necessary. For example, if a source only has one packet pending, they have to waste the whole beacon period to deal with this packet. To avoid this, we add the number of data packets remaining at the sender to every data packet sent to the destination. This information allows the destination to know when it has received all pending packets for it. When the source or destination have sent or received all their packets, they can enter sleep mode until the begin- ning of the next beacon interval. 4.3.2. Priority Processing of Packets to Slaves When nodes are trying to send packets, they first deal with those to be sent to slave nodes. After transmitting all packets to slave nodes, packets between masters can be sent. By using this method, slaves can be in sleep mode as long as possible. 4.3.3. Prolonging the Sleep Period for Slaves In EE-MAC, most packets are forwarded by masters and packet routing via slaves is kept to a minimum. To take advantage of this, each slave uses history information to decide their sleep time. When a node observes two con- secutive beacon intervals without any packets addressed to it, it will decide to sleep through the next beacon in- terval. The corresponding master must store this infor- mation since failure to get an ACK does not guarantee a broken link. If the master does not know a slave’s situa- tion, it just buffers the packets to that slave. Only when the master does not hear from a neighboring slave for two consecutive beacon intervals does it discard these packets. 4.3.4. Additi o nal MAC Layer Control Nodes in an ad hoc network may move randomly. Thus, to quickly adapt to network topology changes, a node informs its neighbors of its status, master or slave, by using the power management bit in the MAC header. Since the MAC header can be heard anywhere in the network, including RTS/CTS packets, this information will help neighbors to know each other’s situation. 5. Performance Results 5.1. Simulation Environment Our conclusions are based on the results gathered by extensive simulation of a network model which imple- ments EE-MAC. For the simulations, we used Network Simulator-2 (NS-2) [13,14]. NS-2 is a popular package which has been widely used in mobile ad hoc network studies. For comparison with EE-MAC, we also imple- mented IEEE 802.11 and its PSM mode. We consider 25, 50 and 75 nodes moving in a square area of 500m×500m, 750m×750m and 1000m×1000m based on a mobility model called random waypoint [15]. Initially, each node chooses a random position in the area, chooses a random destination, chooses a speed at random uniformly distributed between 0m/s and 10m/s, and moves towards the destination at the chosen speed. The node then pauses for a period of time before repeating the same process. Longer pause times reflect lower node mobility and shorter pause times reflect higher mobility. Simulations were performed for 400 seconds, so a 400 second pause time means no node mobility. The nodes have 2 Mbps bandwidth and 250m radio range. Each source node generates a Constant-Bit-Rate (CBR) flow to the d estination with 256 byte packets. We vary the number of sources and the number of packets sent per second to change the network load. A network load of 10% means that the total bit rate of all traffic sources is 2×10% = 0.2 Mbps. DSR [16] is used as the routing protocol. For the energy model, we use the data shown in Table 1. All performance results shown in this paper are an aver age of 10 runs. We use the following metrics to evaluate network performance: Data packet delivery ratio: The data packet deliv- ery ratio is the ratio of the number of packets generated at Table 1. Power Consumption Model [2] Transmit ModeReceive Mode Idle Mode Sleep Mode 1400mW 1020mW 890mW 70mW Copyright © 2009 SciRes. WSN  Y. S. SHI ET AL. 412 the sources to the number of packets received by the des- tinations. This metric reflects the network throughput. One of our goals is to design an energy-efficient MAC protocol which can improve energy consumption without suffering a significant capacity loss. Thus, this metric is useful to measure any degradation in network through- put. End-to-end delay: This metric not only includes the delays due to data propagation and transfer, but also those caused by buffering, queuing and retransmitting data packets. Energy efficiency: We define energy efficiency as Energy efficiency= Total bits transmitted Total energy consumed where the total bits transmitted is calculated using appli- cation layer data packets only and total energy consump- tion is the sum of the energy consumption in the nodes during the simulation time. The unit of energy efficiency is bit/Joule and the greater the number of bits per Joule, the better the energy efficiency achieved. 5.2. Performance Eval uation We now present our simulation results. The figures in this section show three curves labeled 802.11, PSM and EE-MAC. The curves labeled 802.11 correspond to the IEEE 802.11 pr otocol without u sing power saving mode. The curves labeled PSM indicate the IEEE 802.11 pro- tocol with power saving mode. The curves labeled EE-MAC represent the protocol proposed in this paper. 5.2.1. Impact of the Network Load From the simulation results, we observe that network load has a significant impact on all three protocols. However, we show that varying the network load affects these protocols differently in terms of our performance metrics. In Figures 3 and 4 we show the packet delivery ratio under different network loads from 10% to 40%. When the network load is low (10%), 802.11 performs a little better than EE-MAC while EE-MAC provides a signifi- cant improvement over PSM. As the network load in- creases to 40%, all three protocols become worse due to the higher collision rate. However, the performance dif- ferences between 802.11 and EE-MAC, and EE-MAC and PSM also increase, which means heavier traffic has more impact on EE-MAC than 802.11 because under a heavy network load, the master election algorithm oper- ates more frequently to rotate masters and slaves. Among the three protocols, PSM always performs worst. PSM drops significantly more packets than the others because of the existence of a fixed ATIM window, which wastes bandwidth. When the traffic is high, it is possible that the Figure 3. Packet delivery ratio with 50 nodes and 10 sources in an area of 750m×750m. Figure 4. Packet delivery ratio with 75 nodes and 10 sources in an area of 750m×750m. ATIM window is not long enough to advertise all pend- ing packets, or the buffered data packets cannot all be sent out during a beacon interval. On the other hand, EE-MAC has the advantage of masters which never enter sleep mode, so traffic between masters does not need to be advertised. Coupled with the fact that most of the network traffic is data traffic between masters, EE-MAC can use a shorter ATIM window than PSM and thus pro- vide better performance than PSM. EE-MAC is worse than 802.11 because it still uses an ATIM window in every beacon interval which wastes some bandwidth. Moreover, the overhead of the master election algorithm and using fewer nodes to forward packets also decreases the packet delivery ratio. Copyright © 2009 SciRes. WSN 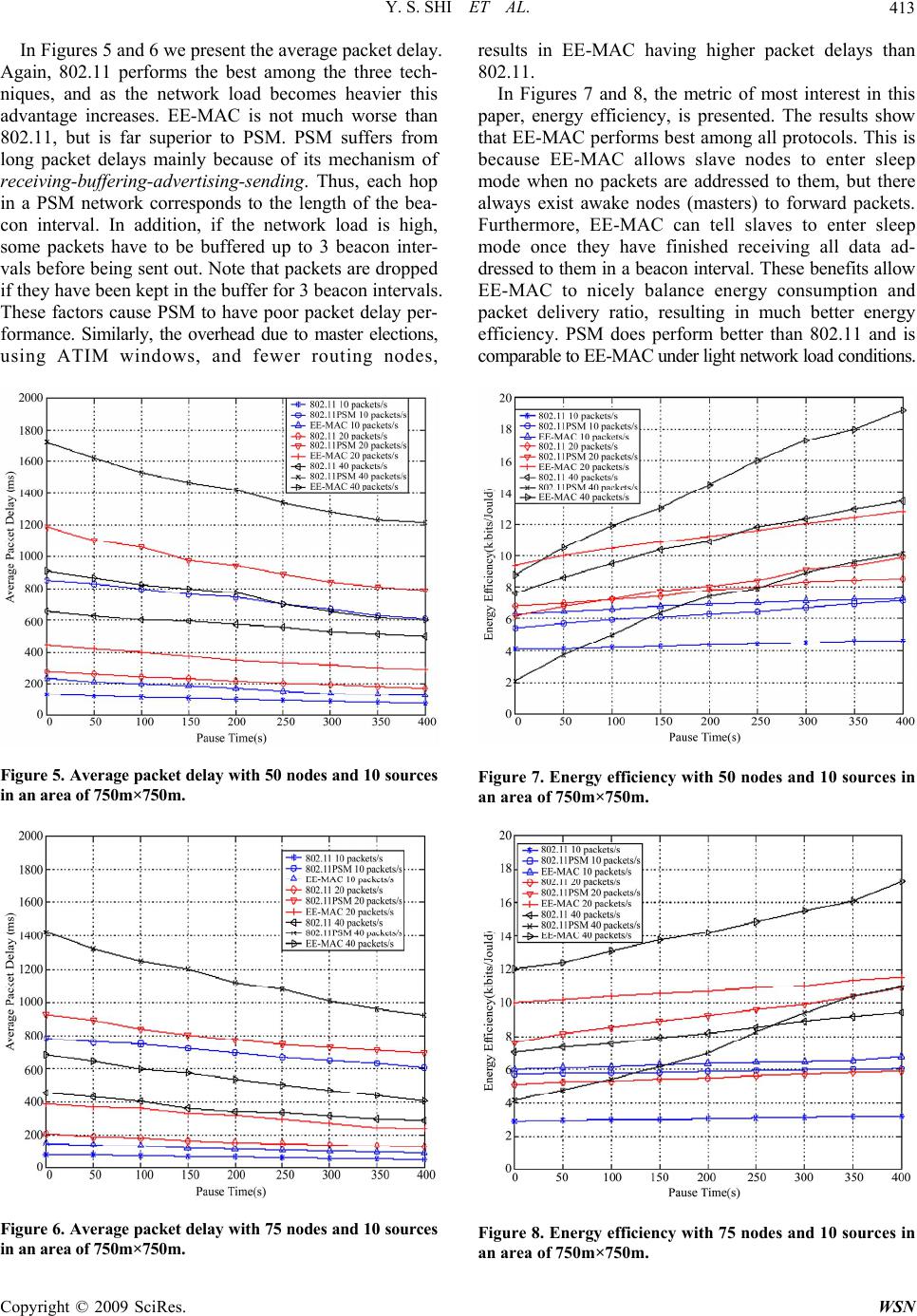 Y. S. SHI ET AL.413 In Figures 5 and 6 we present the average packet delay. Again, 802.11 performs the best among the three tech- niques, and as the network load becomes heavier this advantage increases. EE-MAC is not much worse than 802.11, but is far superior to PSM. PSM suffers from long packet delays mainly because of its mechanism of receiving-buffering-advertising-sending. Thus, each hop in a PSM network corresponds to the length of the bea- con interval. In addition, if the network load is high, some packets have to be buffered up to 3 beacon inter- vals before being sent out. Note that packets are dropped if they have been kept in the buffer for 3 beacon intervals. These factors cause PSM to have poor packet delay per- formance. Similarly, the overhead due to master elections, using ATIM windows, and fewer routing nodes, Figure 5. Average packet delay with 50 nodes and 10 sources in an area of 750m×750m. Figure 6. Average packet delay with 75 nodes and 10 sources in an area of 750m×750m. results in EE-MAC having higher packet delays than 802.11. In Figures 7 and 8, the metric of most interest in this paper, energy efficiency, is presented. The results show that EE-MAC performs best among all protocols. This is because EE-MAC allows slave nodes to enter sleep mode when no packets are addressed to them, but there always exist awake nodes (masters) to forward packets. Furthermore, EE-MAC can tell slaves to enter sleep mode once they have finished receiving all data ad- dressed to them in a beacon interval. These benefits allow EE-MAC to nicely balance energy consumption and packet delivery ratio, resulting in much better energy efficiency. PSM does perform better than 802.11 and is comparable to EE-MAC under light network load conditions. Figure 7. Energy efficiency with 50 nodes and 10 sources in an area of 750m×750m. Figure 8. Energy efficiency with 75 nodes and 10 sources in an area of 750m×750m. Copyright © 2009 SciRes. WSN 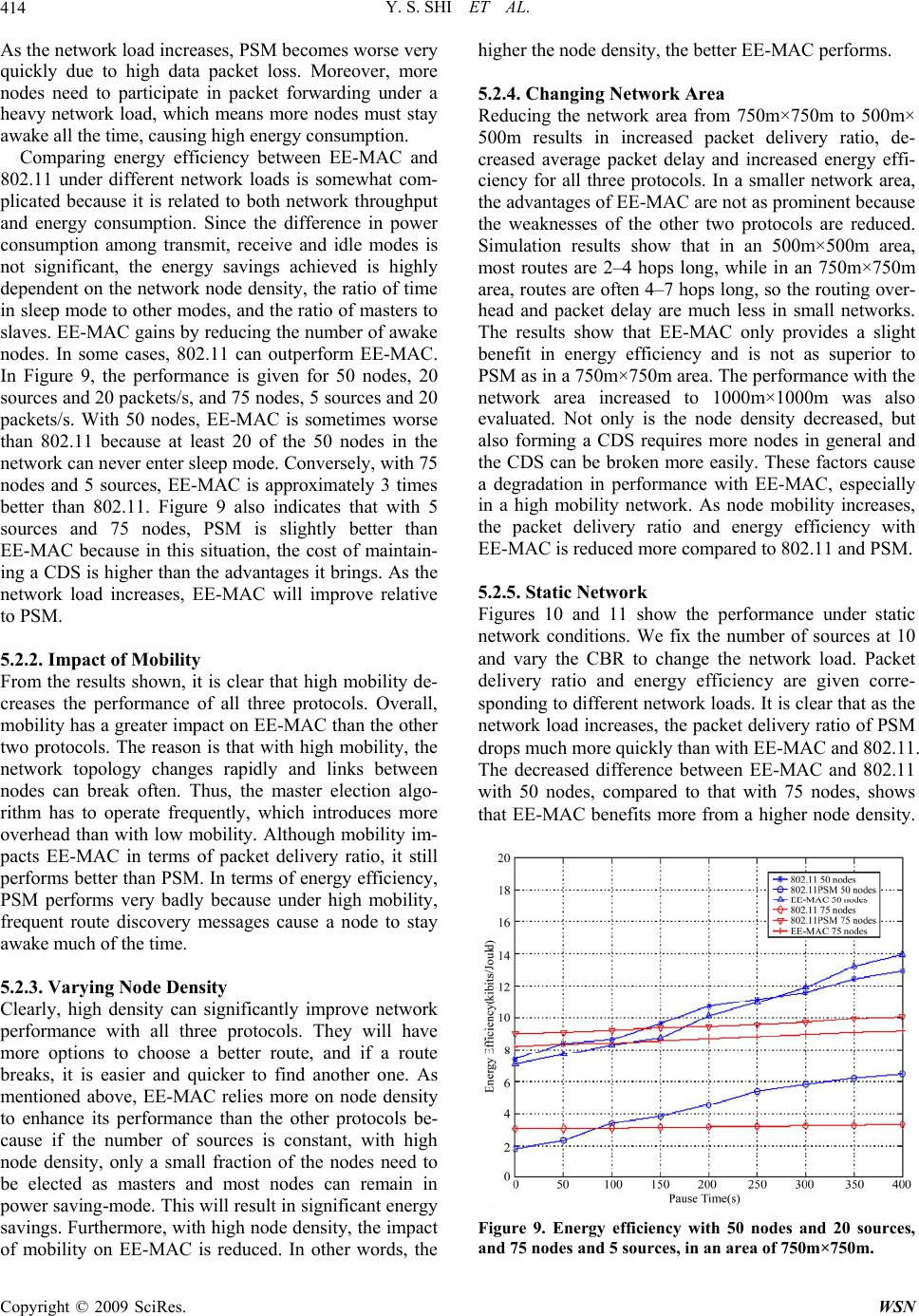 Y. S. SHI ET AL. 414 As the ne twork load in creas es, PS M becomes worse v ery quickly due to high data packet loss. Moreover, more nodes need to participate in packet forwarding under a heavy network load, which means more nodes must stay awake all the time, causing high energy consumption. Comparing energy efficiency between EE-MAC and 802.11 under different network loads is somewhat com- plicated because it is related to both network throughput and energy consumption. Since the difference in power consumption among transmit, receive and idle modes is not significant, the energy savings achieved is highly dependent on the network node density, the ratio of time in sleep mode to other modes, and the ratio of masters to slaves. EE-MAC gains by reducing the number of awake nodes. In some cases, 802.11 can outperform EE-MAC. In Figure 9, the performance is given for 50 nodes, 20 sources and 20 packets/s, and 75 nodes, 5 sources and 20 packets/s. With 50 nodes, EE-MAC is sometimes worse than 802.11 because at least 20 of the 50 nodes in the network can never enter sleep mode. Conversely, with 75 nodes and 5 sources, EE-MAC is approximately 3 times better than 802.11. Figure 9 also indicates that with 5 sources and 75 nodes, PSM is slightly better than EE-MAC because in this situation, the cost of maintain- ing a CDS is higher than the advantages it brings. As the network load increases, EE-MAC will improve relative to PSM. 5.2.2. Impact of Mobility From the results shown, it is clear that high mobility de- creases the performance of all three protocols. Overall, mobility has a greater impact on EE-MAC than the other two protocols. The reason is that with high mobility, the network topology changes rapidly and links between nodes can break often. Thus, the master election algo- rithm has to operate frequently, which introduces more overhead than with low mobility. Although mobility im- pacts EE-MAC in terms of packet delivery ratio, it still performs better than PSM. In terms of energy efficiency, PSM performs very badly because under high mobility, frequent route discovery messages cause a node to stay awake much of the time. 5.2.3. Varyi ng Node Density Clearly, high density can significantly improve network performance with all three protocols. They will have more options to choose a better route, and if a route breaks, it is easier and quicker to find another one. As mentioned above, EE-MAC relies more on node density to enhance its performance than the other protocols be- cause if the number of sources is constant, with high node density, only a small fraction of the nodes need to be elected as masters and most nodes can remain in power saving-mode. This will result in significant energy savings. Furthermore, with high node density, the impact of mobility on EE-MAC is reduced. In other words, the higher the node density, the better EE-MAC performs. 5.2.4. Chan ging Network Area Reducing the network area from 750m×750m to 500m× 500m results in increased packet delivery ratio, de- creased average packet delay and increased energy effi- ciency for all three protocols. In a smaller network area, the advantages of EE-MAC are not as prominent because the weaknesses of the other two protocols are reduced. Simulation results show that in an 500m×500m area, most routes are 2–4 hops long, while in an 750m×750m area, routes are often 4–7 hops long, so the routing over- head and packet delay are much less in small networks. The results show that EE-MAC only provides a slight benefit in energy efficiency and is not as superior to PSM as in a 750m×750m area. The performance with the network area increased to 1000m×1000m was also evaluated. Not only is the node density decreased, but also forming a CDS requires more nodes in general and the CDS can be broken more easily. These factors cause a degradation in performance with EE-MAC, especially in a high mobility network. As node mobility increases, the packet delivery ratio and energy efficiency with EE-MAC is reduced more compared to 802.11 and PSM. 5.2.5. Static N e tw ork Figures 10 and 11 show the performance under static network conditions. We fix the number of sources at 10 and vary the CBR to change the network load. Packet delivery ratio and energy efficiency are given corre- sponding to different network loads. It is clear that as the network load increases, the packet delivery ratio of PSM drops much mor e quickly than with EE-MAC and 802.11. The decreased difference between EE-MAC and 802.11 with 50 nodes, compared to that with 75 nodes, shows that EE-MAC benefits more from a higher node density. Figure 9. Energy efficiency with 50 nodes and 20 sources, and 75 nodes and 5 sources, in an area of 750m×750m. Copyright © 2009 SciRes. WSN 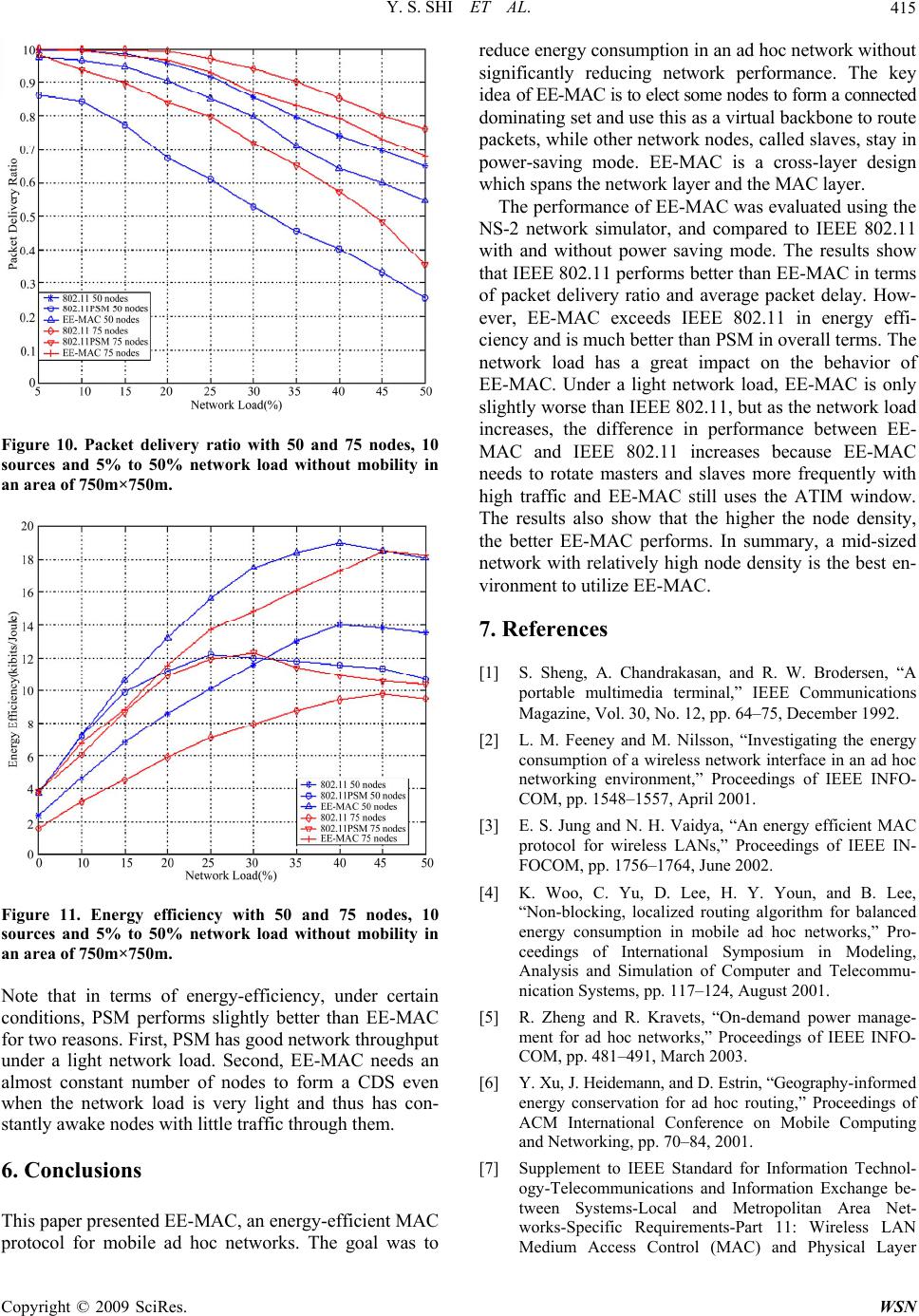 Y. S. SHI ET AL.415 Figure 10. Packet delivery ratio with 50 and 75 nodes, 10 sources and 5% to 50% network load without mobility in an area of 750m×750m. Figure 11. Energy efficiency with 50 and 75 nodes, 10 sources and 5% to 50% network load without mobility in an area of 750m×750m. Note that in terms of energy-efficiency, under certain conditions, PSM performs slightly better than EE-MAC for two reasons. Firs t, PSM has good network th ro ughpu t under a light network load. Second, EE-MAC needs an almost constant number of nodes to form a CDS even when the network load is very light and thus has con- stantly awake nodes with little traffic through them. 6. Conclusions This paper presented EE-MAC, an energy-efficient MAC protocol for mobile ad hoc networks. The goal was to reduce ener g y consu mption in an ad hoc networ k withou t significantly reducing network performance. The key i d ea of EE-MAC is to elect some nodes to form a connected dominating set and use this as a virtual backbone to route packets, while other network nodes, called slaves, stay in power-saving mode. EE-MAC is a cross-layer design which spans the network layer and the MAC layer. The performance of EE-MAC was evaluated using the NS-2 network simulator, and compared to IEEE 802.11 with and without power saving mode. The results show that IEEE 802.11 p erforms better than EE-MAC in terms of packet delivery ratio and average packet delay. How- ever, EE-MAC exceeds IEEE 802.11 in energy effi- ciency and is much better than PSM in overall terms. The network load has a great impact on the behavior of EE-MAC. Under a light network load, EE-MAC is only slightly worse than IEEE 802.11, but as the network load increases, the difference in performance between EE- MAC and IEEE 802.11 increases because EE-MAC needs to rotate masters and slaves more frequently with high traffic and EE-MAC still uses the ATIM window. The results also show that the higher the node density, the better EE-MAC performs. In summary, a mid-sized network with relatively high node density is the best en- vironment to utilize EE-MAC. 7. References [1] S. Sheng, A. Chandrakasan, and R. W. Brodersen, “A portable multimedia terminal,” IEEE Communications Magazine, Vol. 30, No. 12, pp. 64–75, December 1992. [2] L. M. Feeney and M. Nilsson, “Investigating the energy consumption of a wireless network interface in an ad hoc networking environment,” Proceedings of IEEE INFO- COM, pp. 1548–1557, April 2001. [3] E. S. Jung and N. H. Vaidya, “An energy efficient MAC protocol for wireless LANs,” Proceedings of IEEE IN- FOCOM, pp. 1756–1764, June 2002. [4] K. Woo, C. Yu, D. Lee, H. Y. Youn, and B. Lee, “Non-blocking, localized routing algorithm for balanced energy consumption in mobile ad hoc networks,” Pro- ceedings of International Symposium in Modeling, Analysis and Simulation of Computer and Telecommu- nication Systems, pp. 117–124, August 2001. [5] R. Zheng and R. Kravets, “On-demand power manage- ment for ad hoc networks,” Proceedings of IEEE INFO- COM, pp. 481–491, March 2003. [6] Y. Xu, J. Heideman n, and D. E st rin, “ Geog raphy-i nfo rme d energy conservation for ad hoc routing,” Proceedings of ACM International Conference on Mobile Computing and Networking, pp. 70–84, 2001. [7] Supplement to IEEE Standard for Information Technol- ogy-Telecommunications and Information Exchange be- tween Systems-Local and Metropolitan Area Net- works-Specific Requirements-Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer Copyright © 2009 SciRes. WSN  Y. S. SHI ET AL. Copyright © 2009 SciRes. WSN 416 (PHY) Specifications: High-speed Physical Layer Exten- sion in 2.4 GHz Band, IEEE Std 802.11b, 2000. [8] M. S. Gast, 802.11 Wireless Networks: The Definitive Guide, O’Reilly & Associates, 2002. [9] P. J. Wan, K. M. Alzoubi, and O. Frieder, “Distributed construction of connected dominating set in wireless ad hoc networks,” Mobile Networks and Applications, Vol. 9, No. 2, pp. 141–149, April 2004. [10] Y. P. Chen and A. L. Liestman, “Approximating mini- mum size weakly-connected dominating sets for cluster- ing mobile ad hoc networks,” Proceedings of ACM In- ternational Symposium on Mobile Ad Hoc Networking and Computing, pp. 165–172, June 2002. [11] J. Wu and H. Li, “On calculating connected dominating set for efficient routing in ad hoc wireless networks,” Proceedings of ACM International Workshop on Discrete Algorithms and Methods for Mobile Computing and Communication, pp. 7–14, August 1999. [12] J. Wu and H. Li, “Domination and its applications in ad hoc wireless networks with unidirectional links,” Pro- ceedings of IEEE International Conference on Parallel Processing, pp. 189–197, August 2000. [13] UCB LBNL VINT Group, Network simulator (V. 2), http://www.isi.edu/nsnam/ns. [14] K. Fall and K. Varadhan, Network Simulator Notes and Documentation, The VINT Project, UC Berkeley, USC/ ISI, LBL and Xerox PARC, 1999, http:// www.isi.edu/nsnam/ns. [15] J. Broth, D. Maltz, D. Johnson, Y. C. Hu, and J. Jetcheva, “A performance comparison of multi-hop wireless ad hoc network routing protocols,” Proceedings of International Conference on Mobile Computing and Networking, pp. 85–97, October 1998. [16] D. Johnson, D. Maltz, and Y. C. Hu, “The dynamic source routing protocol for mobile ad hoc networks (DSR),” IETF draft, July 2004, http://www.ietf.org/ rfc/rfc3684.txt.
|