Journal of Service Science and Management
Vol.6 No.2(2013), Article ID:32726,8 pages DOI:10.4236/jssm.2013.62014
Effects of RFID in Retailing on Customer Trust
![]()
Department of Marketing & Distribution Management, National Kaohsiung First University of Science and Technology, Kaohsiung City, Chinese Taipei.
Email: hpyeh2000@gmail.com
Copyright © 2013 Hsiaoping Yeh. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Received April 3rd, 2013; revised May 4th, 2013; accepted May 12th, 2013
Keywords: RFID; Trust; Perceived Risk; Privacy; Business Reputation
ABSTRACT
Radio frequency identification (RFID) has become an increasingly widespread technology. However, there has been limited research on it with regard to customer-related issues. This paper proposes a theoretical model to investigate customer perceptions of privacy risk and trust for the retail stores with all RFID tagged items. The results suggest that customers with high sensitivity to privacy risk have a lower degree of trust in RFID applications. However, benefits to customers are incentives for retailers to both mitigate customer worries about their privacy being invaded and increase their trust in retailers. One way to do this is by implementing strong data security systems. This research thus presents a set of guidelines to help retailers successfully apply this technology in their stores.
1. Introduction
RFID has been widely and successfully adopted in inventory management and implemented large-scale solutions throughout the entire supply chains by a number of world-class retailers and even planning item-level, i.e., for all items, deployment in consumer goods. Retailers claim that such applications can improve customer services, including allowing real-time inventory control and locating, reducing time spent in customer checkout lines, and even providing customized shopping information during and after sales.
However, RFID still has some key differences from other IT applications [1], as the related signals can be easily intercepted and read without authorization, and the data collected can be readily and accurately captured, exchanged and processed, both interand intra-organizationally. As becoming more common in daily life, challenges of RFID yet remain in when it comes to real-time services, adoption, and integration with regard to enterprise architecture, security, and privacy [2]. Therefore, despite the benefits that RFID systems can bring to both public and private enterprises, a number of data security and privacy issues have raised concerns about their adoption (e.g., [3-6]), and there have even been a number of related consumer boycotts [7]. In particular, there are a number of powerful arguments against the more widespread deployment of this technology at sales areas in retailing.
People’s judgments with regard to the risk of possible harm arising from invasions of their privacy affect their willingness of going to retail stores selling RFID-tagged goods [6-8]. However, according to [9], it is the increase in item-level tagging, especially in the apparel industry, that has been driving the growth of RFID in the retail industry. Data security issues continue to be a challenge to the growth of this industry. Successful technology implementations are often heavily dependent on softer management concerns [1], and there is obviously a potential conflict of interest here, as retailers may wish to deploy RFID to provide improved services, while customers may be wary of entering environments and engaging in transactions that could compromise their privacy. Customer trust is thus an important factor for retailers that aim to establish an item-level RFID retail store. Therefore, the purpose of this study is to propose a model which explains the impacts of retail RFID settings on customer trust.
2. Theoretical Background
Privacy is defined as the ability of an individual to control the terms by which their personal information is acquired and used [10]. Also known as information privacy sensitivity [11] or privacy awareness [6] in different contexts, individual perceptions of privacy depends on their personal tolerance [12], and customers thus have different levels of concern with regard to the amount of personal information that is known by businesses [13].
The use of RFID raises many of the same ethical issues as those related to electronic commerce [4]. Since information stored in RFID tags can be accessed by readers without a person’s knowledge, they can thus be tracked, and any information that is collected can be readily duplicated, transmitted, stored and analyzed, and thus there is a risk of inappropriate and unauthorized secondary usages. Security efforts are thus required to protect the collected data from unauthorized access, storage, and manipulation [14]. While the use of RFID in the retail sector enables the development of a ubiquitous retailing environment, [15] noted that this is difficult to achieve if customers are unwilling to provide information about their preferences.
[16] showed that security and privacy have significant effects on consumer acceptance of newness such as online shopping. Technical solutions for data security can help to tackle these problems, such as the privacy enhancing technologies (PETs) of password protection or killing the RFID tag signal, third party certification (e.g., the TRUSTe web tractability certificate), and the individual organization’s privacy or data security policies. Of the essential privacy protection mechanisms, self-regulation is recognized as both most desirable and necessary [17,18] noted that although organizations have responsibility for the security of their customers’ information (e.g., by utilizing encryption, authentication, and firewalls), there is still the possibility of third parties compromising the data when RFID is employed and its tags are kept near to customers. Customers are thus concerned about retailers’ efforts to act in a socially responsible manner [19], and those businesses that have are perceived as having better reputations are expected to place more value on more their perceived level of social responsibility [20]. On a related note, a business with a poor reputation is likely to lose both sales [21] and customer trust [22].
Trust is a major determinant in people’s decisionmaking, as well as the adoption of new technology [23]. For example, mutual trust needs to exist between retailers and customers for electronic commerce to take place. Moreover, when facing difficult decisions, customer trust can efficiently reduce the related complexity of this process [24]. Various definitions of trust have been proposed in the literature, with different theoretical perspectives, research interests, and levels of analyses. Trust, however, is generally expressed as the willingness of one party to rely on the behaviors of others, especially when the former is in a potentially vulnerable situation. Moreover, trust always involves accepting a certain level of risk and becoming vulnerable to a trusted party [25]. This acceptance of risk is based on the expectation that the trusted party will perform actions that are important or beneficial to the vulnerable one [8,26]. Therefore, trust is a relative term based on actions between the parties involved [14], and it emerges if all the risks in a system are understood by all the players. Consumer trust can thus be described as a function of the degree of risk involved in a certain situation [27].
Customers’ perceived benefits have been found to influence the ways in which companies have adopted either e-commerce [28], m-commerce [29] or u-commerce [15]. A number of researchers have included characteristics similar to benevolence as a basis for trust (e.g., [30]). Others have considered intentions or motives, in terms of the trustee’s profit motives, as an important factor in the development of trust (e.g., [31]). [32] also suggested that trust in a leader is influenced by the extent to which their behavior is relevant to employee needs and desires.
Moreover, through continued interactions, the two parties in any relationship can accumulate rich information (or knowledge) about each other [33], and people do not develop any attitudes about privacy in a specific context until they have some experience of it [34]. Customer perceptions of whether and how to safeguard their information against being collected and used by firms is thus based on their prior experience with these companies [35]. For example, in comparison to US citizens, people in many European countries have been found to have substantially less concerns about their privacy rights with regard to RFID, since they have had more exposure to this technology—smart cards’ being used to store personal health benefits information in France, PSA (personal service assistant) systems being implemented in Extra Future Stores in Germany, and anti-theft RFID equipped cameras being sold in the UK. In addition, changes in customer trust, even when risks still exist, can be influenced by consumers’ post-consumption experiences, their satisfaction with the services provided, and retailers’ security guarantees [36].
3. Model Development
All of the environmental uncertainties that include the theft and illegal disclosure of personal information are called privacy risks, and these are closely related to fears about invasions of privacy [35]. Such threats are a subjective matter based on how an individual perceives the relevant systems or actions from organizations with regard to privacy protection and on what exactly is seen as constituting an invasion of privacy. [37] pointed out that privacy and security always go hand in hand in digital environments. Prior researchers have found that when people know their personal data and behavior are collected online then they have greater concerns about privacy (e.g., [16] on online trading systems; [38] on ebanking; [39] on both cyber and brick-and-mortar marketing effects). Based on these earlier works, the following hypothesis is proposed.
H1: Customer perceptions of privacy positively affect perceived privacy risk with regard to item-level RFID retail stores.
Individual trust is commonly categorized as trust in both technologies and the transaction parties who adopt them [7,18]. [6] found that people with more sensitivity to their privacy, i.e. with high privacy awareness, show less acceptance of RFID-based information services, and thus less trust in RFID. An RFID system has much greater capacity with regard to storing information and communicating with databases before, during, and after sales than bar-codes do. It has been claimed that consumer trust in RFID-enabled environments would be higher in the pre-sales stage, but then fall due to privacy concerns in the post-sales one, as customer concerns tend to focus on the acceptable use of the data collected, rather than the technology per se [36].
Data security promises with regard to handling customer data could ease worries with regard to risk of privacy invasions, and thus increase customer trust [14]. Within TAM, perceived risk had a direct, although negative, impact on intentions to use the technology, since consumer understandings of the expected usefulness of a technology are based on the sellers behind the system [18]. According to [14], trust is particularly influenced by the level of security that customers with regard to the handling of their private data. Similarly, [40] identified that the privacy and security features of a website, along with shared values, are the key antecedents of trust, which in turn positively influences the behavioral intentions of customers. In this sense, the influence of privacy and security on users’ acceptance of a technology has been supported by several authors in the context of e-banking services [38,41]. Based on these earlier works, the following hypotheses are proposed:
H2: Customer perceptions of privacy negatively affect their trust in item-level RFID retail stores.
H3: Customers’ perceived privacy risk with regard to item-level RFID retail stores negatively affects their trust in such stores.
Prior experience has an influence of customer attitudes to new technology [42], and this is especially true for online stores [39,43]. In addition, perceptions of privacy risk are also related to a user’s past experiences [44], with more positive past online retail experience leading to less perceived risk with regard to the focal community of sellers [45]. Similarly, the more experience that customers have of RFID applications, the more knowledge they are able to acquire about them, and this can enable them to both recognize and avoid any privacy risks associated with the technology, as well become more willing to let retailers and other organizations collect and use their information. [46] have found that different people from different cultures, with different online experiences, show different levels of perceived risk toward shopping online. Moreover, online customer involvement with a brand and product also affect customers’ risk awareness with regard to buying other brands and products online [47]. Based on this, the fourth hypothesis is presented, as follows:
H4: Customers’ experiences of RFID technology negatively affect their perceived privacy risk with regard to item-level RFID retail stores.
Benefits are related to the extent to which a trustee is believed to want to do well with regard to the trustor, aside from profit motives, and these can increase the level of attachment between both parties [8]. The use of transaction data yields better services and higher quality products, and hence creates substantial customer benefits [35]. By collecting and analyzing customer behavior in stores stocked with RFID-tagged goods and incorporating their personal data (e.g., birthday, address, and so on), profile data (such as hobbies and annual salary), and information about their past purchases, retailers are able to offer more personalized services (such shopping list recommendations, in-store navigation, and comparison shopping), as well as better universal services (e.g., promotional activities, an improved shopping environment, faster checkouts and easier returns) [5].
While people generally do not trust others to safeguard their individual privacy, they are often willing to compromise it in certain business contexts [3,7]. Specifically, they tend to be more willing to give personal information to firms if it is required to participate in promotional activities [6]. Based on this, the following two hypotheses are proposed:
H5: Retailers’ provision of customer benefits positively affects consumer trust in item-level RFID retail stores.
H6: Retailers’ provision of customer benefits negatively affects perceived privacy risk with regard to itemlevel RFID retail stores.
Reputation is a social memory relating to past experiences with an individual or organization. In retailing, reputation is an important factor with regard to the adoption of new technology, especially for novice customers, and also a contributing factor to consumer trust [22,48]. A firm that is able to improve its reputation will increase the level of trust that others have in it [49-52], and thus decrease the level of perceived risk [16], and thus the next two hypotheses are proposed:
H7: Retailer reputation has a positive effect on customer trust in item-level RFID retail stores.
H8: Retailer reputation has a negative effect on customers’ perceived privacy risk with regard to item-level RFID retail stores.
The hypothesized model is depicted in Figure 1. It is posited that customers’ perceived risk of privacy invasion with regard to item-level RFID retail stores is positively influenced by their privacy perceptions, but reduced by a greater amount of RFID-related usage experience, more benefits from retailers, and a higher level of retailer reputation. As with trust, customer willingness to shop at item-level RFID retail stores would be positively influenced by the benefits from the retailers and retailer reputation, but negatively influenced by their privacy perceptions and perceived privacy risk.
4. Methodology
There are currently no fully constructed item-level RFID retail stores to record all the movements of both customers and single goods, and thus it is impossible for individuals to really experience such systems. A simulated item-level RFID retail store, called the Smart Shop Laboratory, was thus developed in the Department of Marketing and Distribution Management at National Kaohsiung First University of Science & Technology (NKFUST), and this is the research setting for this study. In this lab, three smart shelves are equipped with RFID antenna and readers. Integrated with an RFID reader, a smart shopping cart is also equipped with a touch screen computer that assists shoppers, by reciprocally communicating with the back-end main retail system with an AP (access point) device throughout the whole shopping tour, including offering information about directions and store layout, current promotional activities, special offers for members, introductions and comparisons of merchandise, current items in the shopping cart, and so on. The RFID system is able to instantly reflect the actions of customers and movement of goods, although the customers themselves do not know exactly what the system is doing with regard to data collection, storage, and usage. Therefore, some posters describing how the RFID system functions and possible benefits to shoppers could be were placed on the walls and ceiling of the lab. Finally, a wide variety

Figure 1. The research hypothesized model.
of goods were placed on the shelves, from personal hygiene products, such as condoms and sanitary napkins, to food stuffs like crackers and soft drinks, in order to examine the shoppers’ perceived privacy with regard to certain items.
4.1. The Measurement of Variables
The instrument employed was a self-administrated questionnaire which contained five sections to gather the subjects’ RFID-related experience, reactions to retailers’ providing benefits, and levels of perceived trust, perceived privacy and perceived risk. Other than the first section, which was measured by yes-no responses, the items were all measured on a five-point Likert scale, with 1 as “strongly disagree” and 5 as “strongly agree”.
1) Perceived privacy: Customers show different levels of privacy awareness with regard to the collection and usage of their data. In order to evaluate this, the subjects were asked to what extent they agreed that personal and shopping related types of data being gathered by retailers at the pre-, during, and post-shopping stages.
2) Benefits: Items in this section of the questionnaire included both the universal and personal benefits that retailers could provide to customers based on the data obtained by the RFID system.
3) Perceived privacy risk: The use of RFID in stores could lead to the data being misused by the retailer or obtained by any unauthorized third parties. In order to evaluate consumer perceptions of these threats, items in this section of the questionnaire investigated the subjects’ perceptions regarding the risks of data disclosure.
4) Trust: If customers consider the item-level RFID retail stores to be trustworthy due to the use of reliable privacy protection measures by the retailers, or appreciate the increased convenience that such RFID settings can provide, they are more likely to visit such stores. Therefore, customer trust is a two-fold construction: a) trust in specific retailers who adopt RFID to collect, use, and apply customer data, and b) trust in RFID technology per se.
5) RFID experience: As noted above, it is currently not possible for the subjects to have had any experience in an item-level RFID retail store. However, RFID applications are already widespread in Taiwan, such as in credit cards, pass cards, pet chips, library book locating/ checkout, membership cards, and so on. In addition, due to the similarity to the capability of instant data traceability provided by RFID, the data in this study were gathered based on the respondents’ experiences related to using cellphones and web applications, such as on-line banking, shopping and social networks. Subjects were asked to check items that they had experienced, with more checks representing a greater level of RFID experience. The subjects who checked more than 80% of the items were classified as the most experienced group, while those who checked less than 20% were the least experienced one. Three other groups were in between these two.
6) Retailer reputation: While defining “reputation” as a social memory or impression of an individual or organization, this study chose two supermarket chains in Taiwan to test the influence of retailer reputation on customer trust. One currently has over 200 stores, and is the most widespread supermarket chain on the island, while the other has only 36 stores in central Taiwan. In this study, the former is considered as the retailer with the better reputation, since it is more well-known throughout Taiwan. An equal amount of respondents were assigned to have either one as their subject supermarket chain when answering the questionnaire.
4.2. Data Collection
The participants were NKFUST’s students, staff, and faculty who volunteered by responding to an announcement posted on a few bulletin boards around the campus, as well as people from the local community around the campus who also responded, with a NTD$100 gift certificate given as a reward for participating. After about 10 minutes spent introducing the retail environment in the lab and 10 minutes of experiencing shopping in the lab, participants were asked to fill out the questionnaire. A total of 348 valid data sets were obtained. Cronbach’s α greater than 0.86 for all the sections of the questionnaire confirmed the coefficient reliabilities of the items and variables in the questionnaire.
5. Research Results
Of the 348 valid samples, 174 (50%) are for the more established subject chain store and the others are for the less well-known one. To test the homogeneity of these two sets, the Levene’s test, F = 3.874 and p = 0.073 (not significant), shows that they are not significantly different.
All the Pearson correlation for the variables (absolute values are taken) in the model are in the range of 0.24 - 0.68 (shown in Table 1), and thus no problem with muticollinearity problem exists in variables for SEM analysis. Besides, from the AVE statistics (>0.5), all indicators for variables are valid and reliable (also in Table 1). The SEM results, obtained with AMOS18 and used to test the research model, are illustrated in Figure 2.
Therefore, the hypotheses in this study are all significantly accepted. The path coefficients and tests on the hypotheses are summarized in Table 2.
6. Discussion and Implications
Applying RFID at the sales areas of retail stores enables
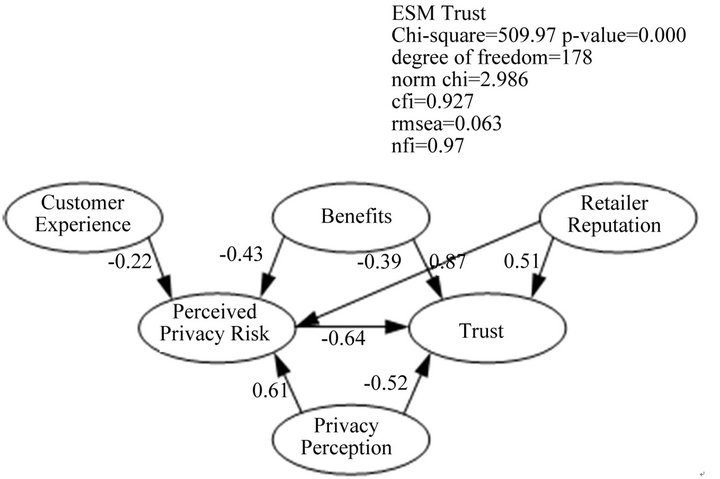
Figure 2. The path analysis for the research model.
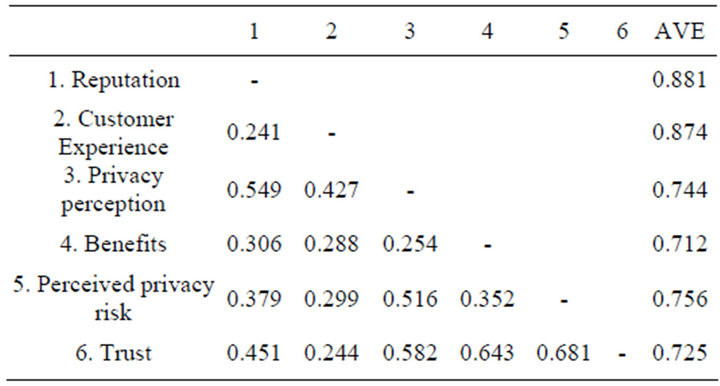
Table 1. Correlation matrix and reliability analysis by AVE.
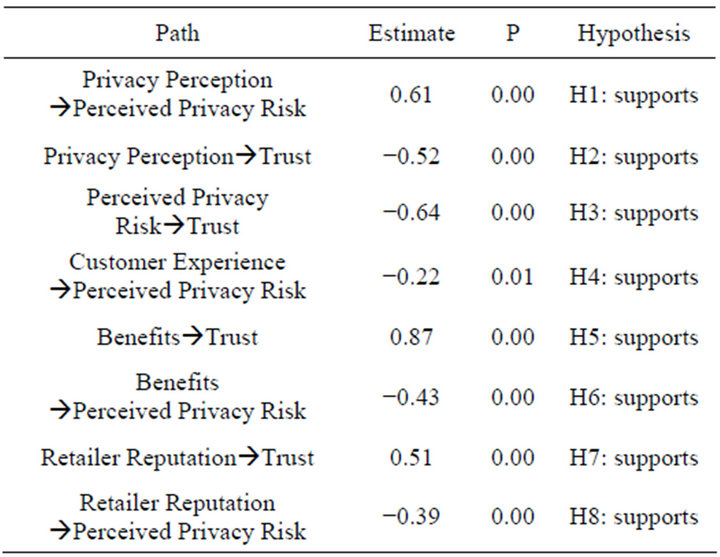
Table 2. Standardized regression weights with point estimations.
the retailers to understand their customers better by tracing details of their shopping from the point of entrance to the checkouts, and even to the returns. One major drawback for customers is the possibility of privacy invasion. Customers’ sensitivity towards this, based on the results of this study, is related to the level of threat they perceive with regard to their personal data being misused or accessed without authorization. Customer trust is based on retailer’s reputation, the benefits offered by the retailer, and customer’s past experience of RFID-related services. Customers who have a higher level of sensitivity to privacy risks tend to have a lower degree of trust. However, benefits are incentives that can both mitigate worries about privacy being invaded and increase trust in both retailers and item-level RFID retail stores.
Research on RFID from managerial and organizational perspectives regarding the adoption and operation of this technology still remains preliminary and exploratory at best [53], and most are technically oriented [54]. So far, there has been limited research on RFID with regard to customer-related issues, more specifically investigating customer perceptions of RFID, and the research that has been conducted has mainly aimed to improve technology or address managerial strategies for coping with customer fears. This study developed a model that empirically describes the impacts on customer trust in the context of retail stores with RFID-tagged goods. To the best of our knowledge, this is the first attempt at such a work in the literature. Since there are currently no fully operational item-level RFID retail stores, instead of showing videos to subjects to explain how these would work [3,6], this study made use of a simulated shopping environment, and thus the collected data can better reflect the real situation.
To date, the numbers of retail firms that have employed RFID are still rather on few functional areas, and even many of the efforts have not gone much beyond the trial stage. As an increasing number of organizations are seriously considering adopting this technology, it is necessary for researchers and practitioners to provide principles that can aid the successful implementations. With regard to item-level RFID retail stores, currently only Germany’s Future Store has adopted this technology, but still only RFID tags on store goods partially. Since there have still been some protests and boycotts against this. The current study suggests that item-level RFID retail shops are likely to emerge worldwide once this technology is fully mature, its costs are acceptable, and customers are less concerned about it. This study suggests a possible positive feedback loop, which is that the more customers shop at such stores, the more understanding of them that retailers can obtain, and thus better the services that they can receive, encouraging their both more trust and more visits to such stores. The retailers who are and will plan such initiatives should put efforts on building customer trust on them and such shopping environment by erasing customer’s worries according to the model of this study.
Many customers have already had hands-on experience with RFID technology without being aware of it, while [55] pointed out that most customers do not grasp how the technology itself works. This echoes the view of [56] that most customers are unaware of RFID as a term, how RFID will affect how products are sold, and what benefits and risks are involved at the customer level. These latter insights add legitimacy to the claim of this study that a more comprehensive research framework is needed to capture the wider context of RFID use and its implications for everyday life.
Finally, one limitation of this work is that in the simulated environment only one shopping cart was used in the lab, and there were very few shelves that could not replicate the variety of goods that actual retail stores offer. Therefore, data collection within a large-scale item-level RFID retail store setting is suggested for future studies.
REFERENCES
- T. S. H. Toe, S. C. Srivastava, C. Ranganathan and J. W. K. Loo, “A Framework for Stakeholder Oriented Mindfulness: Case of RFID Implementation at YCH Group, Singapore,” European Journal of Information Systems, Vol. 20, No. 2, 2011, pp. 201-220. doi:10.1057/ejis.2010.58
- S. Liu, “IT Professional in 2011,” IT Professional, Vol. 13, No. 1, 2011, pp. 4-5.
- O. Günther and S. Spiekermann, “RFID and the Perception of Control: The Consumer’s View,” Communications of the ACM, Vol. 48, No. 9, 2005, pp. 73-76. doi:10.1145/1081992.1082023
- A. R. Peslak, “An Ethical Exploration of Privacy and Radio Frequency Identification,” Journal of Business Ethics, Vol. 59, No. 4, 2005, pp. 327-345. doi:10.1007/s10551-005-2928-8
- S. Sackmann, J. Struker and R. Accorsi, “Personalization in Privacy-Aware Highly Dynamic Systems,” Communications of the ACM, Vol. 49, No. 9, 2006, pp. 32-38. doi:10.1145/1151030.1151052
- M. Rothensee and S. Spiekermann, “Between Extreme Rejection and Cautious Acceptance: Consumers’ Reactions to RFID-Based IS in Retail,” Social Science Computer Review, Vol. 26, No. 1, 2008, pp. 75-86. doi:10.1177/0894439307307687
- F. Thiesse, “RFID, Privacy and the Perception of Risk: A Strategic Framework,” Journal of Strategic Information Systems, Vol. 16, No. 2, 2007, pp. 214-232. doi:10.1016/j.jsis.2007.05.006
- R. C. Mayer, J. H. Davis and F. D. Schoorman, “An Integrative Model of Organizational Trust,” Academy of Management Review, Vol. 20, No. 3, 1995, pp. 709-734.
- Global Retail RFID Market 2011-2015 Report, “Research and Markets Adds Report: Global Retail RFID Market 2011-2015,” Wireless News, 15 May 2012.
- H. Galanxhi-Janaqi and F. F.-H. Nah, “U-Commerce: Emerging Trends and Research Issues,” Industrial Management & Data Systems, Vol. 104, No. 9, 2004, pp. 744- 755. doi:10.1108/02635570410567739
- R. Angeles, “An Empirical Study of the Anticipated Consumer Response to RFID Product Item Tagging,” Industrial Management & Data Systems, Vol. 107, No. 4, 2007, pp. 461-483. doi:10.1108/02635570710740643
- M. Ohkubo, K. Suzuki and S. Kinoshita, “RFID Privacy Issues and Technical Challenges,” Communications of the ACM, Vol. 48, No. 9, 2005, pp. 66-71. doi:10.1145/1081992.1082022
- E. R. Foxman and P. Kilcoyne, “Information Technology, Marketing Practice, and Consumer Privacy: Ethical Issue,” Journal of Public & Marketing, Vol. 12, No. 1, 1993, pp. 106-119.
- C. Flavián and M. Guinalíu, “Consumer Trust, Perceived Security and Privacy Policy: Three Basic Elements of Loyalty to a Web Site,” Industrial Management & Data Systems, Vol. 106, No. 5, 2006, pp. 601-620. doi:10.1108/02635570610666403
- R. Bennett and S. Savani, “Retailers’ Preparedness for the Introduction of Third Wave (Ubiquitous) Computing Applications: A Survey of UK Companies,” International Journal of Retail & Distribution Management, Vol. 39, No. 5, 2011, pp. 306-325. doi:10.1108/02635570610666403
- M. S. Featherman, A. D. Miyazaki and D. E. Sprott, “Reducing Online Privacy Risk to Facilitate E-Service Adoption: The Influence of Perceived Ease of Use and Corporate Credibility,” The Journal of Services Marketing, Vol. 24, No. 3, 2010, pp. 219-229. doi:10.1108/08876041011040622
- M. Maury and D. Kleiner, “E-Commerce: Ethical Commerce,” Journal of Business Ethics, Vol. 36, No. 1-2, 2002, pp. 21-31. doi:10.1023/A:1014274301815
- P. A. Pavlou, “Consumer Acceptance of Electronic Commerce: Integrating Trust and Risk with the Technology Acceptance Model,” International Journal of Electronic Commerce, Vol. 7, No. 3, 2003, pp. 101-134.
- S. Sen and C.B. Bhattacharya, “Does Doing Good Always Lead to Doing Better? Consumer Reactions to Corporate Social Responsibility,” Journal of Marketing Research, Vol. 38, No. 2, 2001, 225-243. doi:10.1509/jmkr.38.2.225.18838
- T. J. Brown and P. A. Dacin, “The Company and the Product: Corporate Associations and Consumer Product Responses,” Journal of Marketing, Vol. 61, No. 1, 1997, pp. 68-84. doi:10.2307/1252190
- J. T. Resnick, “Corporate Reputation: Managing Corporate Reputation-Applying Rigorous Measures to a Key Asset,” The Journal of Business Strategy, Vol. 25, No. 6, 2004, pp. 30-38. doi:10.1108/02756660410569175
- L. Mui, M. Mohtashemi and A. Halberstadt, “A Computational Model of Trust and Reputation,” Proceedings of the 35th Hawaii International Conference on System Sciences, Big Island, 7-10 January 2002, pp. 2431-2439. doi:10.1109/HICSS.2002.994181
- D. B. Turban and D. M. Cable, “Firm Reputation and Application Pool Characteristics,” Journal of Organizational Behavior, Vol. 24 No. 6, 2003, pp. 733-751. doi:10.1002/job.215
- E. Aivaloglou and S. Gritzalis, “Hybrid Trust and Reputation Management for Sensor Networks,” Wireless Network, Vol. 16, No. 5, 2010, pp. 1493-1510. doi:10.1007/s11276-009-0216-8
- R. Cohen and R. Kerr, “TREET: The Trust and Reputation Experimentation and Evaluation Tested,” Electronic Commerce Research, Vol. 10, No. 3-4, 2010, pp. 271-290. doi:10.1007/s10660-010-9056-y
- F. G. Mármol and G. M. Pérez, “Trust and Reputation Models Comparison,” Internet Research, Vol. 21, No. 2, 2011, pp. 138-153. doi:10.1108/10662241111123739
- Z. Noorian and M. Ulieru, “The State of the Art in Trust and Reputation Systems: A Framework for Comparison,” Journal of Theoretical and Applied Electronic Commerce Research, Vol. 5, No. 2, 2010, pp. 97-117. doi:10.4067/S0718-18762010000200007
- F. Fukuyama, “Social Capital and Global Economy,” Foreign Affairs, Vol. 74, No. 5, 1995, pp. 89-103. doi:10.2307/20047302
- D. L. Hoffman, T. Novak and M. A. Peralta, “Information Privacy in the Marketspace: Implications for the Commercial Uses of Anonymity on the Web,” Information Society, Vol. 15, No. 2, 1999, pp. 129-139. doi:10.1080/019722499128583
- L. T. Hosmer, “Trust: The Connection Link between Organizational Theory and Philosophical Ethics,” The Academy of Management Review, Vol. 20, No. 2, 1995, pp. 337-362.
- M. I. Eid, “Determinants of E-Commerce Customer Satisfaction, Trust, and Loyalty in Saudi Arabia,” Journal of Electronic Commerce Research, Vol. 12, No. 1, 2011, pp. 78-93.
- M. Koller, “Risk as a Determinant of Trust,” Basic and Applied Social Psychology, Vol. 9, No. 4, 1988, pp. 265- 276. doi:10.1207/s15324834basp0904_2
- J. Zheng, E. Bakker and L. Knight, “A Strategic Case for E-Adoption in Healthcare Supply Chains,” International Journal of Information Management, Vol. 26, No. 4, 2006, pp. 290-301. doi:10.1016/j.ijinfomgt.2006.03.010
- M. A. Islam, M. A. Khan, T. Ramayah and M. M. Hossain, “The Adoption of Mobile Commerce Service among Employed Mobile Phone Users in Bangladesh: Self-Efficacy as a Moderator,” International Business Research, Vol. 4, No. 2, 2011, pp. 80-89. doi:10.5539/ibr.v4n2p80
- R. Larzelere and T. Huston, “The Dyadic Trust Scale: Toward Understanding Interpersonal Trust in Close Relationships,” Journal of Marriage and the Family, Vol. 42, No. 3, 1980, pp. 595-604. doi:10.2307/351903
- J. Cook and T. Wall, “New Work Attitude Measures of Trust, Organizational Commitment, and Personal Need Nonfulfillment,” Journal of Occupational Psychology, Vol. 53, No. 1, 1980, pp. 39-52. doi:10.1111/j.2044-8325.1980.tb00005.x
- A. P. Jones, L. R. James and J. R. Bruni, “Perceived Leadership Behavior and Employee Confidence in the Leader as Moderated by Job Involvement,” Journal of Applied Psychology, Vol. 60, No. 1, 1975, pp. 146-149. doi:10.1037/h0076359
- R. Gulati, “Does Familiarity Breed Trust? The Implications of Repeated Ties for Contractual Choice in Alliances,” Academy of Management Journal, Vol. 38, No. 1, 1995, pp. 85-112. doi:10.2307/256729
- M. J. Culnan, “Consumer Awareness of Name Removal Procedures: Implications for Direct Marketing,” Journal of Direct Marketing, Vol. 9, No. 2, 1995, pp. 10-19. doi:10.1002/dir.4000090204
- M. J. Culnan and P. K. Armstrong, “Information Privacy Concerns, Procedural Fairness, and Impersonal Trust: An Empirical Investigation,” Organization Science, Vol. 10, No. 1, 1999, pp. 104-115. doi:10.1287/orsc.10.1.104
- S. M. Lee, S.-H. Park, S. N. Yoon and S.-J. Yeon, “RFID Based Ubiquitous Consumer Trust,” Industrial Management & Data Systems, Vol. 107, No. 5, 2007, pp. 605-617. doi:10.1108/02635570710750381
- K.-P. Wiedmann, N. Hennigs, D. Varelmann and M.-O. Reeh, “Determinants of Consumers’ Perceived Trust in IT-Ecosystems,” Journal of Theoretical and Applied Electronic Commerce Research, Vol. 5, No. 2, 2010, pp. 137- 154. doi:10.4067/S0718-18762010000200009
- L. V. Casaló, C. Flavián and M. Guinaliíu, “The Role of Security, Privacy, Usability and Reputation in the Development of Online Banking,” Online Information Review, Vol. 31, No. 5, 2007, pp. 583-603. doi:10.1108/14684520710832315
- M. V. Nepomuceno, M. Laroche, R. Marie-Odile and A. Eggert, “Relationship between Intangibility and Perceived Risk: Moderating Effect of Privacy, System Security and General Security Concerns,” The Journal of Consumer Marketing, Vol. 29, No. 3, 2012, pp. 176-189. doi:10.1108/07363761211221701
- M. Eurich, N. Oertel and R. Boutellier, “The Impact of Perceived Privacy Risks on Organizations’ Willingness to Share Item-level Event Data across the Supply Chain,” Electronic Commerce Research, Vol. 10, No. 3-4, 2010, pp. 423-440. doi:10.1007/s10660-010-9062-0
- M. Taleghani, A. S. Sharifi and S. Gilaninia, “The Role of Key Factors in E-Banking for New Enterprises (Concepts & Applications),” Interdisciplinary Journal of Contemporary Research in Business, Vol. 3, No. 3,
 2011, pp. 999-1006.
2011, pp. 999-1006. - S. Taylor and P. A. Todd, “Assessing IT Usage: The Role of Prior Experience,” MIS Quarterly, Vol. 19, No. 4, 1995, pp. 561-570. doi:10.2307/249633
- M. T. Elliott and S. Speck, “Factors that Affect Attitude toward a Retail Web Site,” Journal of Marketing Theory and Practice, Vol. 13, No. 1, 2005, pp. 40-51.
- L. S. Strickland and L. E. Hunt, “Technology, Security, and Individual Privacy: New Tools, New Threats, and New Public Perceptions,” Journal of the American Society for Information Science and Technology, Vol. 56, No. 3, 2005, pp. 221-234. doi:10.1002/asi.20122
- P. A. Pavlou and D. Gefen, “Building Effective Online Marketplaces with Institution-Based Trust,” Information Systems Research, Vol. 15, No. 1, 2004, pp. 37-59. doi:10.1287/isre.1040.0015
- M. Alkailani and R. Kumar, “Investigating Uncertainty Avoidance and Perceived Risk for Impacting Internet Buying: A Study in Three National Cultures,” International Journal of Business and Management, Vol. 6, No. 5, 2011, pp. 76-92.
- Y.-J. Hu, “Exploring the Relationship between Customer Involvement, Brand Equity, Perceived Risk and Customer Loyalty: The Case of Electrical Consumer Products,” The International Journal of Organizational Innovation, Vol. 4, No. 1, 2011, pp. 111-127.
- S. H. Lim and C. E. Koh, “RFID Implementation Strategy: Perceived Risks and Organizational Fits,” Industrial Management & Data Systems, Vol. 109, No. 8, 2009, pp. 1017-1036. doi:10.1108/02635570910991274
- E. W. T. Ngai, K. K. L. Moon, F. J. Riggins and Y. Y. Candace, “RFID Research: An Academic Literature Review (1995-2005) and Future Research Directions,” International Journal of Production Economics, Vol. 112, No. 2, 2008, pp.510-520. doi:10.1016/j.ijpe.2007.05.004
- L. Lee, “RFID for Everyday People,” Perspectives in Business, Vol. 3, No. 2, 2005, pp. 25-31.
- R. L. Juban and D. C. Wyld, “Would You Like Chips with That? Consumer Perspectives of RFID,” Management Research News, Vol. 27, No. 11-12, 2004, pp. 29-44. doi:10.1108/01409170410784653

