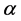Journal of Information Security
Vol.07 No.01(2016), Article ID:63128,13 pages
10.4236/jis.2016.71001
Authentication Method Using a Discrete Wavelet Transform for a Digital Moving Image
Ren Fujii, Yasunari Yoshitomi, Taro Asada, Masayoshi Tabuse
Graduate School of Life and Environmental Sciences, Kyoto Prefectural University, Kyoto, Japan

Copyright © 2016 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 8 January 2016; accepted 24 January 2016; published 28 January 2016
ABSTRACT
Recently, several digital watermarking techniques have been proposed for hiding data in the frequency domain of moving image files to protect their copyrights. However, in order to detect the water marking sufficiently after heavy compression, it is necessary to insert the watermarking with strong intensity into a moving image, and this results in visible deterioration of the moving image. We previously proposed an authentication method using a discrete wavelet transform for a digital static image file. In contrast to digital watermarking, no additional information is inserted into the original static image in the previously proposed method, and the image is authenticated by features extracted by the wavelet transform and characteristic coding. In the present study, we developed an authentication method for a moving image by using the previously proposed method for astatic image and a newly proposed method for selecting several frames in the moving image. No additional information is inserted into the original moving image by the newly proposed method or into the original static image by the previously proposed method. The experimental results show that the proposed method has a high tolerance of authentication to both compressions and vicious attacks.
Keywords:
Authentication, Moving Image, Copyright Protection, Tolerance to Compression, Wavelet Transforms

1. Introduction
Recent progress in digital media technology and distribution systems, such as the Internet and cellular phones, has enabled consumers to easily access, copy, and modify digital content, which includes electric documents, images, audio, and video. Therefore, techniques to protect the copyrights for digital data and to prevent unauthorized duplication or tampering are urgently needed.
Digital watermarking (DW) is a promising method for copyright protection of digital data. Several studies have developed a method in which 1) the DW can be sufficiently extracted from the watermarked digital data, even after compression, and 2) the quality of the digital data remains high after the DW is embedded [1] -[8] . However, a tradeoff generally exists between these two properties. Two important properties of the DW for digital data are imperceptibility of DW-introduced distortion, and robustness to signal processing methods, such as compressions and vicious attacks. However, the data rate and complexity of the DW have attracted attention when discussing the DW performance.
For overcoming the issue of performance, we previously developed authentication methods for digital audio [9] and a static image [10] without inserting a DW into them by using a discrete wavelet transform (DWT). In contrast to the DW, no additional information is inserted into the original digital data by the previous method [10] , and the digital data are authenticated by features extracted by the DWT and characteristic coding [10] .
In the present study, we developed an authentication method for a digital moving image to protect the copy rights by using the previously proposed method [10] for a static image and our newly proposed method for selecting several frames in the moving image. No additional information is inserted into the original moving image by the proposed method or into the original static image by the previously proposed method [10] . The digital moving image is authenticated by features extracted by the DWT and characteristic coding of the proposed method. This paper presents the method and also an analysis of its performance, including the tolerance of authentication to both compressions and vicious attacks.
2. Wavelet Transform
In the present study, we use the authentication method for a static image [10] to authenticate a moving image. First, we briefly describe the procedure of the DWT used in the authentication for a static image.
The original image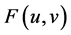 , which is used as the level-0 wavelet decomposition coefficient sequence
, which is used as the level-0 wavelet decomposition coefficient sequence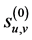 , is decomposed into the multi-resolution representation (MRR) and the coarsest approximation by repeatedly applying the DWT. The wavelet decomposition coefficient matrix
, is decomposed into the multi-resolution representation (MRR) and the coarsest approximation by repeatedly applying the DWT. The wavelet decomposition coefficient matrix 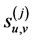 at level j is decomposed into four wavelet decomposition coefficient matrices at the level
at level j is decomposed into four wavelet decomposition coefficient matrices at the level 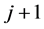 by using (1), (2), (3), and (4).
by using (1), (2), (3), and (4).
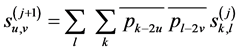 (1)
(1)
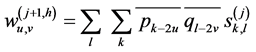 (2)
(2)
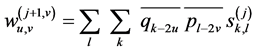 (3)
(3)
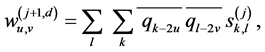 (4)
(4)
where u and v denote the horizontal and vertical directions, respectively, and 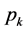 and
and 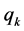 denote the scaling and wavelet sequences, respectively. In addition,
denote the scaling and wavelet sequences, respectively. In addition, 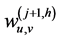 denotes the development coefficient obtained by operating the scaling function in the direction of the horizontal axis and the wavelet in the vertical axis;
denotes the development coefficient obtained by operating the scaling function in the direction of the horizontal axis and the wavelet in the vertical axis; 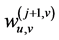 denotes the development coefficient obtained by operating the wavelet in the direction of the horizontal axis and the scaling function in the vertical axis, and;
denotes the development coefficient obtained by operating the wavelet in the direction of the horizontal axis and the scaling function in the vertical axis, and; 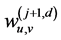 denotes the development coefficient obtained by operating the wavelet in the direction of both the horizontal and vertical axes. The development coefficients at level J are obtained by repeatedly using (1), (2), (3), and (4) from
denotes the development coefficient obtained by operating the wavelet in the direction of both the horizontal and vertical axes. The development coefficients at level J are obtained by repeatedly using (1), (2), (3), and (4) from 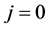 to
to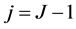 . In this method, the image must be a square composed of
. In this method, the image must be a square composed of 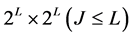
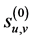
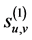
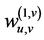
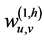
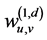
3. Authentication Algorithm for Static Image
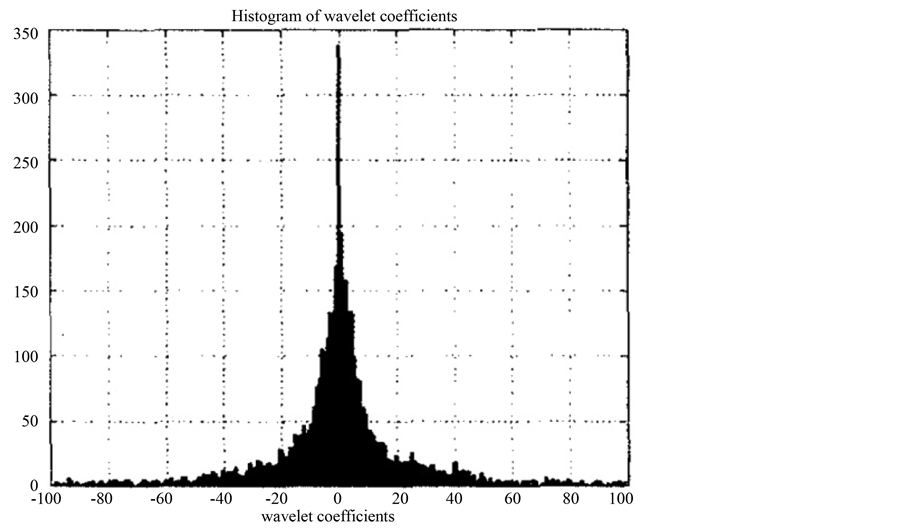
It is known that the histogram of wavelet coefficients of each domain at MRR parts has a distribution in which
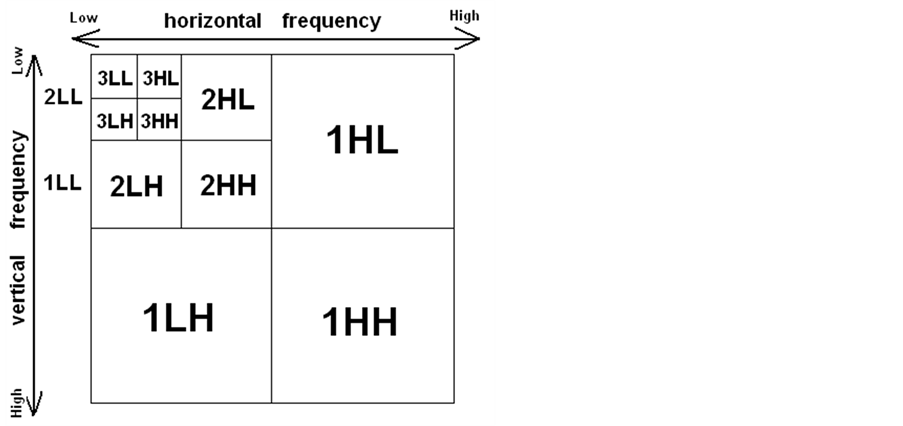
Figure 1. Mallat division [8] .
the center is almost 0 when the DWT is performed on a natural image (Figure 2) [4] . Exploiting this phenomenon, we developed an authentication method for a static image [10] .
3.1. Coding
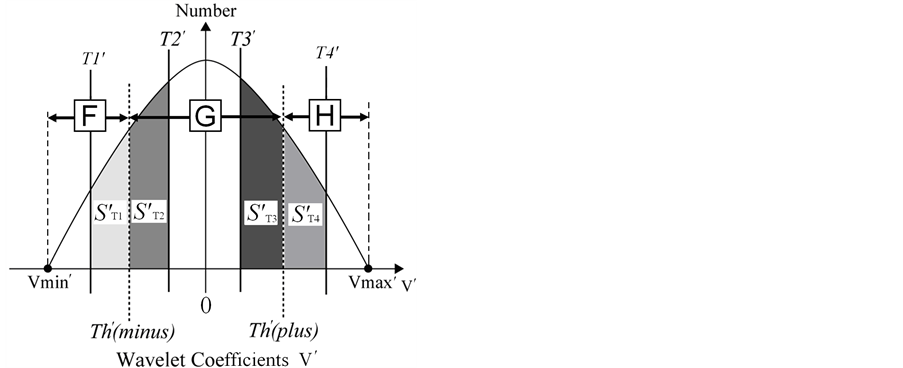
For coding the image, we obtain the histogram of wavelet coefficients V at the selected level of an MRR sequence (Figure 3). As with the DW techniques for images [10] and digital audio [9] , we set the following coding parameters.
The values of Th(minus) and Th(plus) in Figure 3 are chosen such that the non-positive wavelet coefficients (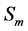
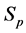
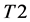
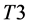
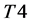
1)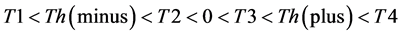
2) The value of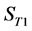
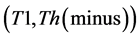
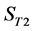
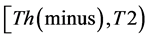
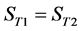
3) The value of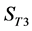
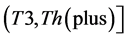
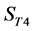
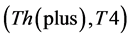
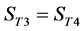
4)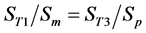
In the present study, the values of both 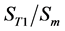
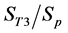
To prepare the coding for authentication, the procedure separates the wavelet coefficients V of an MRR sequence into five sets (hereinafter referred to as A, B, C, D, and E), as shown in Figure 4, by using the following criteria:
・ 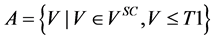
・ 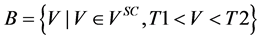
・ 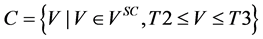
・ 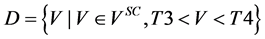
・ 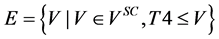
where Vsc is the set of wavelet coefficients in the original image file.
The wavelet coefficients of an MRR sequence are coded according to the following rules, in which 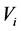
Figure 2. Histogram of the wavelet coefficients [4] .
Figure 3. Schematic diagram of the histogram of MRR wavelet coefficients [9] .
Figure 4. Five sets (A, B, C, D, and E) of the histogram of wavelet coefficients V of an MRR sequence for the assignment of a bit [9] .
one of the wavelet coefficients:
When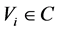
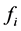
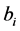
When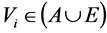
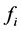
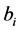
When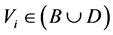
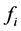
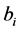
For authentication of the digital image, we use a code 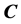
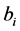
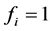
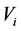
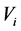
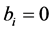
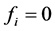
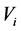
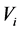
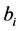
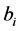
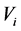
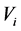
3.2. Authentication
We authenticate not only an original digital image file but also a signal-processed version. Compression, which is one example of signal processing, is often applied to a digital image for the purposes of distribution via the Internet or for saving on a computer. Through the same coding procedure described in Section 3.1, we applied the DWT to a digital image and obtained a histogram of wavelet coefficients 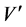
The values of 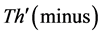
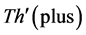
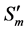
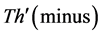
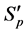
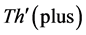
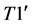
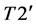
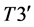
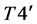
1)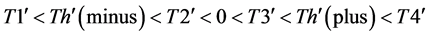
2) The value of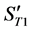
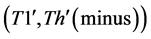
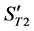
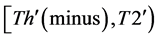
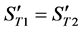
3) The value of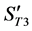
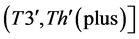
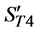
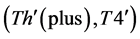
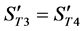
4)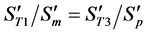
In the present study, the values of both 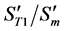
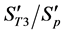
In preparation of the coding for authentication, the procedure separates the wavelet coefficients 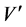
・ 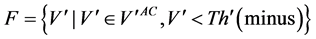
・ 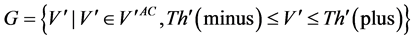
・ 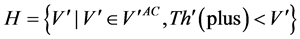
where 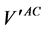
The wavelet coefficients of an MRR sequence are coded according to the following rules, in which 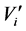
When 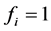
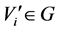
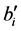
When 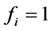
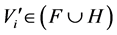
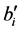
When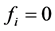
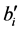
When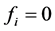
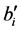
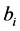
For authentication of the digital image, we use the code 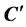
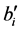
Figure 5. Three sets (F, G, and H), indicated on the histogram, of MRR wavelet coefficients used for authentication [9] .
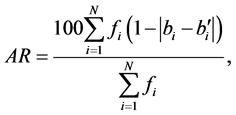
where N is the number of wavelet coefficients assigned flags in the coding for the original image file, described in Section 3.1. According to (5), the values of neither 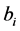
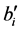
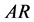
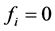
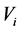
To use the proposed method, we need to store flags 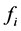
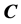
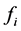
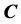
4. Authentication Algorithm for Moving Image
4.1. Coding
We obtain 10 pieces of coding per moving image, which is assumed to have 13 or more frames, in a database as follows.
Step 1: Calculate frame No.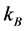
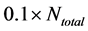
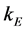
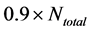
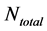
Step 2: Output the images of frame Nos. 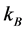
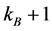
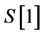
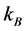
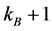
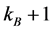
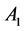
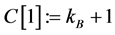
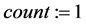
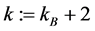
Step 3: If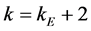
Step 4: Overwrite the image of frame No. k on that of 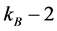
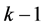
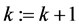
Step 5: If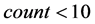
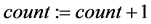
Step 6: Overwrite the array as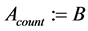
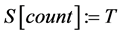
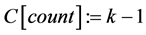
Step 7: Calculate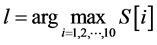
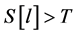
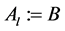
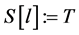
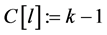
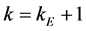
Step 8: Output the arrays 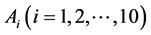
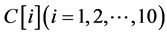
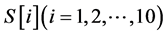
According to our experience, sometimes several consecutive frames including the first or the last frame of a moving image have black for almost all pixels or white for almost all pixels. If such a frame is selected for coding despite that it is neither a representative nor a unique frame for the moving image, the code of the frame might be very detrimental to the authentication of the moving image. Therefore, in Step 1, as the objects for coding, we exclude the first and last 10% of the frames.
4.2. Authentication
The selection of frames is performed for test moving images with the same method described in Section 4.1. Assuming that the codes and the flags for selective coding for selected frames of moving images in a database were obtained by using the methods described in Section 4.1, the authentication ratios of each selected frame of a test moving image to each selected frame of the moving image in the database are calculated with the method described in Section 3.2. The authentication ratio of a test moving image to a moving image in a database is defined as the highest among all values of authentication ratios of selected frames of the test moving image to selected frames of the moving image in the database. Then, the moving image having the highest authentication ratio among all moving images in the database is found.
5. Experiment
In this section, we describe computer experiments and the results for evaluating the performance of the proposed method.
5.1. Method
The experiment was performed in the following computational environment: the personal computer was a DELL OPTIPLEX3020 (CPU: Intel(R) Core(TM) i5-4570 3.20 GHz, memory: 4.0 GB); the OS was Microsoft Windows 7 Professional; the development language was Microsoft Visual C++6.0.
The process of the experiment was as follows. Obtain 100 sets of codes consisting of ten codes for the Y components, which are obtained by the conversion from RGB components into YCrCb components per moving image from the original 100 MPEG-1 files of MUSCLE-VCD-2007 [11] . Use these sets for the authentication among themselves. Convert three target files, which are selected according to the recording time of the shortest (No. 31: 17 s), the closest to the average recording time (No. 49: 34 min 56 s), and the longest (No. 47: 1 hour 55 min 46 s) among the moving images in the database into MPEG-2 and MPEG-4, followed by the authentication to the converted files. Investigate the tolerance of the authentication ratios to the frame rate of three target files after converting their file format from MPEG-1 with the frame rate of 25 fps to MPEG-4 with the frame rate of 5 to 60 fps. Investigate the tolerance of the authentication ratios to the compression of three selected files by using libjpeg [12] to change the values of the quality of the images obtained from the selected frames and by using FFmpeg [13] to generate moving images with the images modified by libjpeg, Investigate the authentication ratios to the frames whose frame distance from a selected frame of a target file is within 5.
We used FFmpeg to output a BMP file having 24 bits as the gray level and 256 × 256 pixels from the moving image. For the DWT, we use Daubechies wavelets. The 4LH components obtained from the DWT up to Level 4 were chosen for coding and authentication, based on the analysis in the preliminary experiments. Figure 6 shows ten image examples consisting of one frame per moving image.
Several consecutive frames having black for almost all pixels or white for almost all pixels are sometimes inserted in a moving image because they can be useful for scene transitions. If such a frame is selected for coding despite that it is neither a representative nor a unique frame for the moving image, the code of the frame might be very harmful for authentication of the moving image. Therefore, in addition to the exclusion of frames as the objects of coding described in Step 1 in Section 4.1, we used only the frames having an average gray level of
Figure 6. Ten image examples consisting of one frame per moving image of the specified number.
to 250 for the Y component, which has a gray level range of 0 to 255. The value of 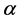
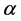
5.2. Results and Discussion
5.2.1. Authentication for MPEG-1 Files
The purpose of authentication is to protect the copyrights on moving image data. In the ten moving images listed in Table 1, when the moving image file targeted for authentication was different from that used for making the code of the original moving image file, the average authentication ratio was 60.2% (more precisely, in the range 40.9% to 81.1%), which was much smaller than the authentications ratios when authenticating the same moving image file as the original moving image file (100% in all cases in this experiment; see Table 1). An authentication ratio of 50% corresponds to the value in the case that randomly generated bits are used for 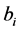
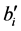
5.2.2. Robustness to Conversion into MPEG-2 or MPEG-4
When the three moving images of Nos. 31, 47, and 49, converted from MPEG-1 to MPEG-2 or MPEG-4, were authenticated by using 100 moving images (MPEG-1) in the database [11] , the authentication ratios was between each pair of different moving images (in the range 43.9% to 79.5%), and were much smaller than the authentications ratios when authenticating the same moving image file as the original moving image file (100% in all cases in this experiment). Therefore, we could conclude that the proposed method has excellent robustness to conversion to MPEG-2 or MPEG-4. Table 2 shows several authentication ratios from this experiment.
5.2.3. Robustness to Frame Rate
Table 3 shows the robustness of the proposed method according to the frame rate. In the cases of Nos. 31 and 47 moving image files, the authentication ratios were kept at 100% for 5 to 60 fps of the file authenticated when authenticating the moving image file with 5 to 60 fps by using the original moving image file with 25 fps. Moreover, in the case of the No. 49 moving image file, the authentication ratios were kept to 100% only for 20 and 25 fps of the file authenticated when authenticating in the same manner (Table 3). The frame rate of the moving image file could be changed to avoid the copyright protection by the proposed method; it was effectively
Table 1. Authentication ratios in 100 combinations of original moving images expressed by file No. for columns and by authentication targets expressed by file No. for rows.
Table 2. Authentication ratios of target files with MPEG-2 or MPEG-4 formats.
Table 3. Tolerance of authentication ratio to frame rate of target file having a MPEG-4 format.
Figure 7. Images of a pair of similar frames; left figure: selected from No. 73 moving image, right figure: selected from No. 59 moving image [14] .
more beneficial to use the higher authentication ratio between the authentication ratio obtained by using the raw frame rate of the authenticated file and that obtained by converting the frame rate of the authenticated file into the same value as that in the database (Tables 3-5).
5.2.4. Robustness to Compression Rate
Figure 8 illustrates the flow for generating new MPEG-1 files from an original MPEG-1 file through JPEG files with several compression rates. When the moving image file targeted for authentication was different from that used for making the code of the original moving image file, the average authentication ratio was 68.9% (more precisely, in the range 62.9% to 75.0%), which was fairly smaller than the authentications ratios when authenticating the same moving image file as the original moving image file (100% in almost all cases with the JPEG quality of 0 to 100 in this experiment; see Table 6). The image obtained with very low JPEG quality had a very poor appearance (see the left figure in Figure 9). Therefore, we could conclude that the proposed method has excellent robustness to the compression rate when keeping a good image appearance.
5.2.5. Robustness to Frame Exclusion
Table 7 shows authentication ratios for frames near each selected frame. When authenticating the frame near the selected one in the same moving image file by using the code of the selected frame of the original moving image file, the authentication ratio was100% in most cases (Table 7). However, in some cases, the attack of frame extraction effectively avoided the copyright protection by using the proposed method (see the three cases of frames from the bottom of the No. 49 moving image file in Table 7). The three frames in the No. 49 moving image file were within continual frames under the conditions of both rapid rotation and fairly dark appearance. Therefore, the robustness of the proposed method to frame extraction for authentication might be effectively improved by
Table 4. Authentication ratios after the frame rate of target file No. 49 is changed twice to 25 (original file; MPEG-1) → [5 to 60] (MPEG-4) → 25 (MPEG-4) fps.
Table 5. Highest authentication ratios of those in Table 3 and Table 4.
Figure 8. Flow for generating new MPEG-1 files from an original MPEG-1 file through JPEG files, corresponding to all frames of an original MPEG-1 file. The JPEG files have several compression rates.
Figure 9. Example of compressed image of moving image No. 31; left figure: quality 5, right figure: quality 100.
Table 6. Tolerance of authentication ratios to compression of target file.
Table 7. Authentication ratios for frames near each selected one.
selecting frames that do not have a dark appearance, which could be judged by using the information of its gray levels.
6. Conclusions
We have proposed an authentication method for a moving image by using our previously proposed method for a static image and a newly developed method for selecting several frames in the moving image. No additional information is inserted into the original moving image by the proposed method or in the previously proposed method for the original static image. The experimental results show that the proposed method has high tolerance of authentication to both compressions and vicious attacks.
To use the proposed method, we need to store in a database 1) flags used for selective coding, and 2) an original code for several selected frames of each moving image file whose copyright we want to protect. In calculating the authentication ratio for authentication of an original moving image file, we do not need an original moving image file, but we do need 1) the flags, and 2) the original code for several selected frames of the original moving image file.
Cite this paper
RenFujii,YasunariYoshitomi,TaroAsada,MasayoshiTabuse, (2016) Authentication Method Using a Discrete Wavelet Transform for a Digital Moving Image. Journal of Information Security,07,1-13. doi: 10.4236/jis.2016.71001
References
- 1. Cox, I.J., Kilian, J., Leighton, T. and Shamoon, T. (1997) Secure Spread Spectrum Watermarking for Multimedia. IEEE Transactions on Image Process, 6, 1673-1687.
http://dx.doi.org/10.1109/83.650120 - 2. Inoue, H., Miyazaki, A., Miyamoto, A. and Katsura, T. (1988) A Digital Watermark Based on the Wavelet Transform and Its Robustness on Image Compression. 1998 International Conference on Image Processing, 2, 391-395.
- 3. Kundur, D. and Hatzinakos, D. (1997) A Robust Digital Image Watermarking Method Using Wavelet-Based Fusion. International Conference on Image Processing, 1, 544-547.
http://dx.doi.org/10.1109/ICIP.1997.647970 - 4. Shino, M., Choi, Y. and Aizawa, K. (2000) Wavelet Domain Digital Watermarking Based on Threshold-Variable Decision. Technical Report of IEICE, DSP2000-86, 100, 29-34. (In Japanese)
- 5. Swanson, M.D., Zhu, B. and Tewfik, A.H. (1996) Transparent Robust Image Watermarking. International Conference on Image Processing, 3, 211-214.
http://dx.doi.org/10.1109/ICIP.1996.560421 - 6. Tsai, M.J., Yu, K.Y. and Chen, Y.Z. (2000) Joint Wavelet and Spatial Transformation for Digital Watermarking. IEEE Transactions on Consumer Electronics, 46, 241-245.
- 7. Xia, X.G., Boncelent, C.G. and Arce, G.R. (1997) A Multiresolusion Watermark for Digital Image. International Conference on Image Processing, 1, 548-551.
http://dx.doi.org/10.1109/ICIP.1997.647971 - 8. Inoue, D. and Yoshitomi, Y. (2009) Watermarking Using Wavelet Transform and Genetic Algorithm for Realizing High Tolerance to Image Compression. Journal of the IIEEJ, 38, 136-144.
- 9. Yoshitomi, Y., Asada, T., Kinugawa, Y. and Tabuse, M. (2011) An Authentication Method for Digital Audio Using a Discrete Wavelet Transform. Journal of Information Security, 2, 59-68.
http://dx.doi.org/10.4236/jis.2011.22006 - 10. Asada, T., Yoshitomi, Y. and Tabuse, M. (2010) A Verification Method for a Digital Image File Using a Discrete Wavelet Transform. Journal of IIEEJ, 39, 1088-1094. (In Japanese)
- 11. MUSCLE-VCD-2007. http://www-rocq.inria.fr/imedia/civrbench/index.html
- 12. Libjpeg (2015) http://www.ijg.org/
- 13. FFmpeg (2015) http://ffmpeg.org/
- 14. Fujii, R., Noguchi, T., Tamura, M., Yoshitomi, Y., Asada, T. and Tabuse, M. (2014) A Verification Method for a Moving Image File Using a Discrete Wavelet Transform. Proceedings of Forum on Information Technology, 3, 195-196. (In Japanese)