Optics and Photonics Journal
Vol.05 No.11(2015), Article ID:60994,7 pages
10.4236/opj.2015.511029
A Robust Optical Encryption Method for Three-Dimensional Object Based on the Fresnel Transform
Yinghong Liu1,2, Weimin Jin1,2*, Xin Yang3, Di Wu1,2, Hongbo Zhang4
1Institute of Information Optics, Zhejiang Normal University, Jinhua, China
2Key Laboratory of Optical Information Detecting and Display Technology in Zhejiang Province, Jinhua, China
3Institute of Information Optics Engineering, Soochow University, Suzhou, China
4Department of Electrical and Computer Engineering, Virginia Tech, Biacksburg, VA, USA

Copyright © 2015 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).


Received 14 September 2015; accepted 8 November 2015; published 11 November 2015

ABSTRACT
An optical encryption of three-dimensional (3D) object with digital holography was implemented. In the process of encryption, two holograms involved recording key information and 3D object were obtained. In the process of decryption, the 3D object was reconstructed from the two holograms by extracting the object and key information, followed by multiplication of the two holograms and inverse Fresnel transform numerically. The robustness of the method was also tested for different occlusions attacks and Gaussian noises. The results showed that the method was able to encrypt and decrypt the 3D object while being robust under different occlusions attacks and Gaussian noises.
Keywords:
Optical Encryption, Three-Dimensional Object, Digital Holography, Fresnel Diffraction

1. Introduction
Optical encryption is applied in numerous engineering fields for its competitive efficiency, parallel processing capability, and superior information storage capacity [1] -[8] . Mostly, numerical simulation methods have been applied due to the difficulties involved in the precise control of the optical devices alignment requirement. For addressing the problem of optical devices alignment required by the decryption process, less-alignment needed optical devices have been applied in previous research [9] [10] . For example, the joint transform correlator method was utilized for this, where photorefractive was used to record optical information. Though optical device alignment problem was partially addressed, the information storage and transmission was inconvenient with this method.
Optical digital holographic encryption technique was developed and popularized recently owning to its advantages of conveniences of data recording, transmission, and processing [11] - [14] . Various optical digital holographic encryption methods have been in use such as two, three, or four steps phase shift interference methods [15] - [18] . A disadvantage of these methods, however, is that the accuracy of phase shift is difficult to control. Additionally, most of the studies on encryption only involved encrypting two-dimensional image, though encryption of three dimensional (3D) object technique was also available, which utilized complex phase shift interference techniques [19] [20] .
In this research, an encryption of tangible 3D object was proposed. In this new method, two separate off-axis Fresnel holograms were recorded. The first hologram involved recording the 3D object and encryption key, and the second hologram only recorded encryption key. Following the hologram recording, encrypted information of 3D object and encryption key was extracted by the filtering out of zeroth-order information and conjugate information in frequency domain. Similarly, for second hologram, encrypted information of encryption key was extracted through filtering out of zeroth-order information and conjugate information in frequency domain. Multiplication of the first and the conjugate of second extracted information was performed, which followed by inverse Fourier transform to get the 3D object wave on the hologram plane. The Fresnel transform was then used for reconstructing decrypted images in the object domain. Furthermore, the decrypted images with different diffractive distances were also obtained. For reducing the effects of speckle noises on reconstructed images, a speckle noise suppression method was applied by averaging multiple reconstructed images. The robustness of the method was tested against occlusion and noise attacks.
2. Method
2.1. Encryption Process
The encryption process contains two optical paths. The first optical path is used to record a digital hologram IE with 3D object and encryption keys of two random phase masks shown in Figure 1. The He-Ne light is divided into two light beams by BS1. One beam passes through the random phase mask (RPM2), acting as a reference
Figure 1. The optical encryption diagram for recording hologram of 3D object and encryption keys.
wave, which is placed on the front focal plane of lens L4. The combination of lens L3 and L4 with same focus length consists of a 4f optical system. The other beam illuminates the 3D object after being reflected by M3. The reflected wave from the 3D object, acting as a object wave, passes through the random phase mask (RPM1) which is placed on the front focal plane of lens L1. The combination of L1 and L2 is also a 4f system. The hologram IE, which is thus an interference pattern formed by the reference wave and the object wave superim-
position. The object can be treated as a two-dimensional image at different distances 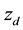 to the RPM1 [19] . Let
to the RPM1 [19] . Let 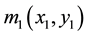 and
and 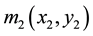 denote the RPM1 and RPM2, respectively. The hologram IE captured by CCD can be written in below:
denote the RPM1 and RPM2, respectively. The hologram IE captured by CCD can be written in below:
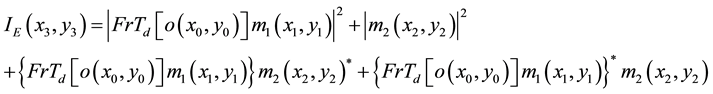 (1)
(1)
where 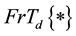 denotes Fresnel transform. d is diffraction distance.
denotes Fresnel transform. d is diffraction distance.  denotes a two-dimensional images at specific distance relative to the RPM1 [19] .
denotes a two-dimensional images at specific distance relative to the RPM1 [19] . 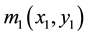 and
and 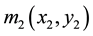 denote the RPM1 and RPM2.
denote the RPM1 and RPM2.
The second optical path is to record a digital hologram of the encryption key IM shown in Figure 2. The hologram, an interference pattern formed by the superimposition of the reference wave which passes through RPM2 and the object wave passing through RPM1. This hologram contains the information of encryption key, which can be expressed with:
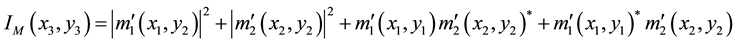 (2)
(2)
where 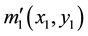 and
and 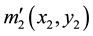 denote the RPM1 and RPM2.
denote the RPM1 and RPM2.
2.2. Decryption Process
In order to extract the encrypted information of 3D object and encryption key, zeroth, first order and conjugate of the hologram in frequency domain have to be separated. As such, the reference beam was slightly inclined planar wave for the separation of them. Following the separation, the two recorded holograms were Fourier transformed to extract the third term on the right hand side of Equation (1) and the fourth term on the right-hand side of Equation (2) [21] . Then the extracting spectrum was inverse Fourier transformed and the extracted items were multiplied. The encrypted 3D object information can be extracted by propagating a distance with Fresnel transformation, which can be expressed as:
Figure 2. The experimental diagram for recording hologram of encryption keys.
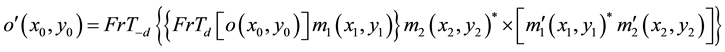 (3)
(3)
When the 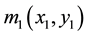 is the same as
is the same as 





3. Experimental Setup
The experimental system is shown in Figure 3. It is based on Mach-Zehnder interferometer architecture. A He-Ne laser was used as a coherent light source. BS is a beam splitter, M is mirror and L is lens. The focal length of L1 and L2 is 30 cm and the focal length of L3 and L4 is 40 cm. RPM is random phase mask, which was made from glass corroded by hydrofluoric acid. The 3D object is located at an approximate distance d from the RPM1 in the object wave.
In the experiments, the encrypted target object consists of two dices. The size of the dice in this experiment is 5 mm × 5 mm × 5 mm, with distance between them is 70 mm. A CCD (4M180MCL) camera which recorded hologram with resolution of 2048 × 2048, pixel size of 
4. Secondary Data Reduction and Analysis
The reconstructed image quality was degraded by speckle noise [22] . In order to reduce the effects of noise, a number of independently captured holograms were used for reducing the noise. Following the superposition of these independently captured holograms, it is estimated that the speckle noise of the hologram can be reduced to [22] :

where M is the number of independently captured holograms.
In order to obtain the independent holograms, the diffusing screen was moved continuously perpendicular to the optical axis of a CCD sensor for 15 times and thus 15 uncorrelated holograms are able to be captured by CCD.
The occlusion attacks often exist in data transfer process. For this, the simulation of occlusion attacks was conducted for both IE and IM holograms. Within the simulation, the occlusion area is the length of the hologram and the width of the occlusion is selected as shown in Figure 4(a).
The robustness of encryption of decryption against Gaussian noise was also validated for both the hologram IE and IM. A computer simulated Gaussian noise is used as shown in Figure 4(b).
Figure 3. The photo of optical experimental system.

Figure 4. (a) A hologram of occlusion; (b) A hologram with Gaussian noise.
5. Experimental Results
5.1. Encryption and Decryption Results
The intensities of holograms 

The reconstructed images at different distances are shown in Figure 6. When the reconstruction distance was 410 mm, the upper dice is out of focus while the lower one is on focus. The focus of this was switched when the reconstruction distance was 480 mm.
5.2. The Robustness against Occlusion and Noise Attacks
The results of robustness against occlusion and noise attacks are presented below. Correlation coefficient (CC) was used to evaluate the decrypted image quality between the reconstructed images without occlusion attacks and the reconstructed images with occlusion attacks.
With speckle noises, the results of reconstructed objects with 70% and 90% occluded Figure 7(a) and Figure 7(b). Without speckle noises, for same occlusions, the results are shown in Figure 7(c) and Figure 7(d). The relationships between CC and occlusion, with and without reducing noises, are shown in Figure 7(e) and Figure 7(f). The CC of reducing the speckle noise is lager when the same occlusion ratio is done from Figure 7(e) and Figure 7(f). As a result, reducing the speckle noise with the method of intensity superposition can mitigate the impact of occlusion on the quality of reconstructed object.
With speckle noises, the reconstructed object from with Gaussian noise of mean 0 and variance 0.0015, mean 0 and variance 0.002 in Figure 8(a) and Figure 8(b). Without speckle noises, the results under same noises are shown in Figure 8(c) and Figure 8(d). The relationships between CC and Gaussian noise with/without reducing speckle noises are shown in Figure 8(e) and Figure 8(f). Reducing the speckle noise with the method of intensity superposition can mitigate the impact of Gaussian noise on the quality of reconstructed object from Figure 8(e) and Figure 8(f).
6. Conclusions
A tangible 3D object information encryption and decryption method was proposed in this research. The encryption process started at recording encrypted 3D object and key holograms. Multiplication of the first and the conjugate of second extracted information from the holograms was performed, which followed by inverse Fourier transform to get the 3D object wave on the hologram plane. The Fresnel transform was then used for reconstructing decrypted images. The robustness of the method was tested against occlusion attacks and Gaussian noises.
Results showed that the 3D objects were successfully encrypted, decrypted, and reconstructed. The speckle noise reduction is evident through the multiple images superposition method. The 3D object can also be reconstructed at different diffraction distances. Additionally, the proposed method is also robust against occlusion attacks and Gaussian noise pollution.
In distinction from the previous research, a tangible 3D object was utilized for encryption and decryption. Only two holograms are needed for encryption, whereas the previous research often involved using multiple

Figure 5. (a) A hologram of 3D object and encryption key information; (b) A hologram of encryption key information; (c) The decrypted image with right key without reducing speckle noises; (d) The decrypted image after reducing the speckle noises; (e) The decryption result when RPM1 is mismatch; (f) The decryption result when RPM2 is mismatch.

Figure 6. The decrypted images with different diffractive distance. (a) d = 410 mm; (b) d = 480mm.

Figure 7. (a) Reconstructed image from the holograms IE and IM with 70% occlusion; (b) Reconstructed image from the holograms IE and IM with 90% occlusion; (c) The reconstructed image after reducing the speckle noises with 70% occlusion; (d) The reconstructed object image after reducing the speckle noises with 90% occlusion; (e) CC values for different occlusion attacks; (f) CC values for different occlusion attacks after reducing the speckle noise.

Figure 8. (a) Reconstructed image with Gaussian noise of average 0 and variance 0.0015; (b) Reconstructed image with Gaussian noise of average 0 and variance 0.002; (c) The reconstructed image after reducing the speckle noise using Gaussian polluted hologram(0.0015); (d) The reconstructed object after reducing the speckle noise using Gaussian polluted hologram (0.002); (e) CC values for different Gaussian noises; (f) CC values for different Gaussian noises after reducing the speckle noise.
holograms. Additionally, this method encrypts both object and reference light wave, which can possibly increase the security of the encryption. Potentially, the results of this research can find its applications in real 3D encryption and decryption.
Limitations also exist in this study. The proposed method is still not able to be used to encrypt large 3D object due to the limited resolution of CCD camera used for recording holograms. Furthermore, we have not yet analyzed the 3D coordinates of the objects, which can be investigated in the future.
Acknowledgements
This work was supported by National Natural Science Foundation of China (No. 61377010)
Cite this paper
YinghongLiu,WeiminJin,XinYang,DiWu,HongboZhang, (2015) A Robust Optical Encryption Method for Three-Dimensional Object Based on the Fresnel Transform. Optics and Photonics Journal,05,313-319. doi: 10.4236/opj.2015.511029
References
- 1. Vilardy, J.M., Millán, M.S. and Pérez-Cabré, E. (2014) Nonlinear Optical Security System Based on a Joint Transform Correlator in the Fresnel Domain. Applied Optics, 53, 1674-1682. http://dx.doi.org/10.1364/AO.53.001674
- 2. Nelleri, A., Joseph, J. and Singh, K. (2007) Digital Fresnel Field Encryption for Three-Dimensional Information Security. Optical Engineering, 46, Article ID: 045801. http://dx.doi.org/10.1117/1.2727377
- 3. Liu, J., Jin, H.Z., Ma, L.H., Li, Y. and Jin, W.M. (2013) Optical Color Image Encryption Based on Computer Generated Hologram and Chaotic Theory. Optics Communications, 307, 76-79. http://dx.doi.org/10.1016/j.optcom.2013.06.009
- 4. Mehra, I., Rajput, S.K. and Nishchal, N.K. (2013) Collision in Fresnel Domain Asymmetric Cryptosystem Using Phase Truncation and Authentication Verification. Optical Engineering, 52, Article ID: 028202. http://dx.doi.org/10.1117/1.OE.52.2.028202
- 5. Liu, S. and Sheridan, J.T. (2013) Optical Encryption by Combining Image Scrambling Techniques in Fractional Fourier Domains. Optics Communications, 287, 73-80. http://dx.doi.org/10.1016/j.optcom.2012.09.033
- 6. Koppa, P. (2007) Phase-to-Amplitude Data Page Conversion for Holographic Storage and Optical Encryption. Applied Optics, 46, 3561-3571. http://dx.doi.org/10.1364/AO.46.003561
- 7. Zhu, N., Wang, Y.T., Liu, J., Xie, J.H. and Zhang, H. (2009) Optical Image Encryption Based on Interference of Polarized Light. Optics Express, 17, 13418-13424. http://dx.doi.org/10.1364/OE.17.013418
- 8. Han, Y.J. and Zhang, Y.H. (2010) Optical Image Encryption Based on Two Beams’ Interference. Optics Communications, 283, 1690-1692. http://dx.doi.org/10.1016/j.optcom.2009.12.060
- 9. Nomura, T. and Javidi, B. (2000) Optical Encryption Using a Joint Transform Correlator Architecture. Optical Engineering, 39, 2031-2035. http://dx.doi.org/10.1117/1.1304844
- 10. Lu, D. and Jin, W.M. (2011) Color Image Encryption Based on Joint Fractional Fourier Transform Correlator. Optical Engineering, 50, Article ID: 068201. http://dx.doi.org/10.1117/1.3590724
- 11. Marron, J.C., Kendrick, R.L., Seldomridge, N.S., Grow, T.D. and Hoft, T.A. (2009) Atmospheric Turbulence Correction Using Digital Holographic Detection: Experimental Results. Optics Express, 17, 11638-11651. http://dx.doi.org/10.1364/oe.17.011638
- 12. Yamaguchi, I. and Zhang, T. (1997) Phase-Shifting Digital Holography. Optics Letters, 22, 1268-1270. http://dx.doi.org/10.1364/OL.22.001268
- 13. Barrera, J.F., Tebaldi, M., Ríos, C., Rueda, E., Bolognini, N. and Torroba, B. (2012) Experimental Multiplexing of Encrypted Movies Using a JTC Architecture. Optics Express, 20, 3388-3393. http://dx.doi.org/10.1364/OE.20.003388
- 14. Rueda, E., Ríos, C., Barrera, J.F. and Torroba, B. (2012) Master Key Generation to Avoid the Use of an External Reference Wave in an Experimental JTC Encrypting Architecture. Applied Optics, 51, 1822-1827. http://dx.doi.org/10.1364/AO.51.001822
- 15. Wang, X.G. and Zhao, D.M. (2006) Image Encryption Based on Anamorphic Fractional Fourier Transform and Three-Step Phase-Shifting Interferometry. Optics Communications, 268, 240-244. http://dx.doi.org/10.1016/j.optcom.2006.07.024
- 16. He, M.Z., Cai, L.Z., Liu, Q. and Yang, X.L. (2005) Phase-Only Encryption and Watermarking Based on Phase-Shifting Interferometry. Applied Optics, 44, 2600-2606. http://dx.doi.org/10.1364/AO.44.002600
- 17. Meng, X.F., Cai, L.Z., Xu, X.F., Yang, X.L., Shen, X.X., Dong, G.Y. and Wang, Y.R. (2006) Two-Step Phase-Shifting Interferometry and Its Application in Image Encryption. Optics Letters, 31, 1414-1416. http://dx.doi.org/10.1364/OL.31.001414
- 18. Tajahuerce, E., Matoba, O., Verrall, S.C. and Javidi, B. (2000) Optoelectronic Information Encryption with Phase-Shifting Interferometry. Applied Optics, 39, 2313-2320. http://dx.doi.org/10.1364/AO.39.002313
- 19. Tajahuerce, E. and Javidi, B. (2000) Encrypting Three-Dimensional Information with Digital Holography. Applied Optics, 39, 6595-6601. http://dx.doi.org/10.1364/AO.39.006595
- 20. Kim, H., Kim, D.H. and Lee, Y.H. (2004) Encryption of Digital Hologram of 3D Object by Virtual Optics. Optics Express, 12, 4912-4921. http://dx.doi.org/10.1364/OPEX.12.004912
- 21. Javidi, B. and Nomura, T. (2000) Securing Information by Use of Digital Holography. Optics Letters, 25, 28-30. http://dx.doi.org/10.1364/OL.25.000028
- 22. Tian, Q. (2007) Speckle Reduction and Three-Dimensional Reconstruction Image of Digital Holography (in Chinese). MS Thesis, Zhejiang Normal University, Jinhua, 16-22.
NOTES
*Corresponding author.





