Technology and Investment
Vol.3 No.1(2012), Article ID:17464,8 pages DOI:10.4236/ti.2012.31007
Risk Management of IT Service Management Project Implementation with Killer Assumptions*
1Faculty of Business Administration, South China University of Technology, Guangzhou, China
2Institute of Emerging Industrialization Development, South China University of Technology, Guangzhou, China
Email: scutwjp@126.com, jade_go@163.com
Received January 4, 2012; revised February 4, 2012; accepted February 11, 2012
Keywords: IT Service Management; The Laws of Complexity; Killer Assumptions; Grounded Theroy; Project Management; Risk Management
ABSTRACT
Large IT service management (ITSM) project has high complexity and low success in implementation. Five common killer assumptions are selected from Warfield’s 17 Killer Assumptions through empirical analysis. Enterprise interview and questionnaire survey are used to establish and verify the relational model between the root risk factors of implementation of the ITSM project and the six complexity propositions based grounded theory. Finally, risk-averse strategies are put forward to meet the demand for complexity: 1) Identify the individual and pay attention to complexity; 2) Select process carefully; 3) Develop innovative language; 4) Personalized the workspace according to the demand; 5) Enhance the role of senior executives; 6) Appropriate communication. The research goal is to reduce the complexity of ITSM project’s implementation in order to manage the risks.
1. Introduction
Now the IT Service Management (ITSM) project has been concerned deeply by the industry. ITSM is a process-oriented and customer-centric approach. It enhances IT organizational service delivery, service level and the ability by integrating IT service and organizational business [1].
Problematic situations dominated by complexity persist in many organizations, sustained by the combination of the influence on managers of numerous Killer Assumptions carried over from normal practice and organizational inertia. The Killer Assumptions relate to complexity, learning, processes and organization infrastructure [2], and twenty laws of complexity were put forward [3]. A science of complexity integrates all of the material, in order to show both the theory of complexity and the empirical evidence that has been accumulated to show the validity of the theory. A principal outcome of the science of complexity is called the work program of complexity (WPOC) [2]. WPOC was applied by a large cross-functional team of Ford engineers and system developers in the mid-1990s as an enabler to create an enterprise-wide information system [4]. The propositions of complexity of software process, WPOC of software process improvement, software enterprise model and software production support structure are clarified in [5].
This paper is organized in the following: Section 2 is literature review, including killer assumptions, twenty laws of complexity, seven root risk factors of implementation of the ITSM project. Section 3 is empirical analysis of killer assumptions. Section 4 is risk factor analysis based in complexity proposition. Section 5 is risk Averse Strategy. Finally Section 6 is conclusions.
2. Literature Review
2.1. The Classification of Killer Assumptions
The impact of the killer assumptions may be widespread. They may limit the capacity of capable people to perform effectively, and may significantly the quality of whatever outcomes occur from human effort. The impact on individuals in organizations was described by a group of program managers with a term they coined: “structural incompetence”, meaning that individuals who were very competent were reduced to effective incompetence by institutional structure, bureaucratic constraints. The classification of killer assumptions is illustrated in Table 1 [2].
2.2. Twenty Laws of Complexity
Complexity is an attribute of many systems that are of great importance to the society. Over a quarter of a century
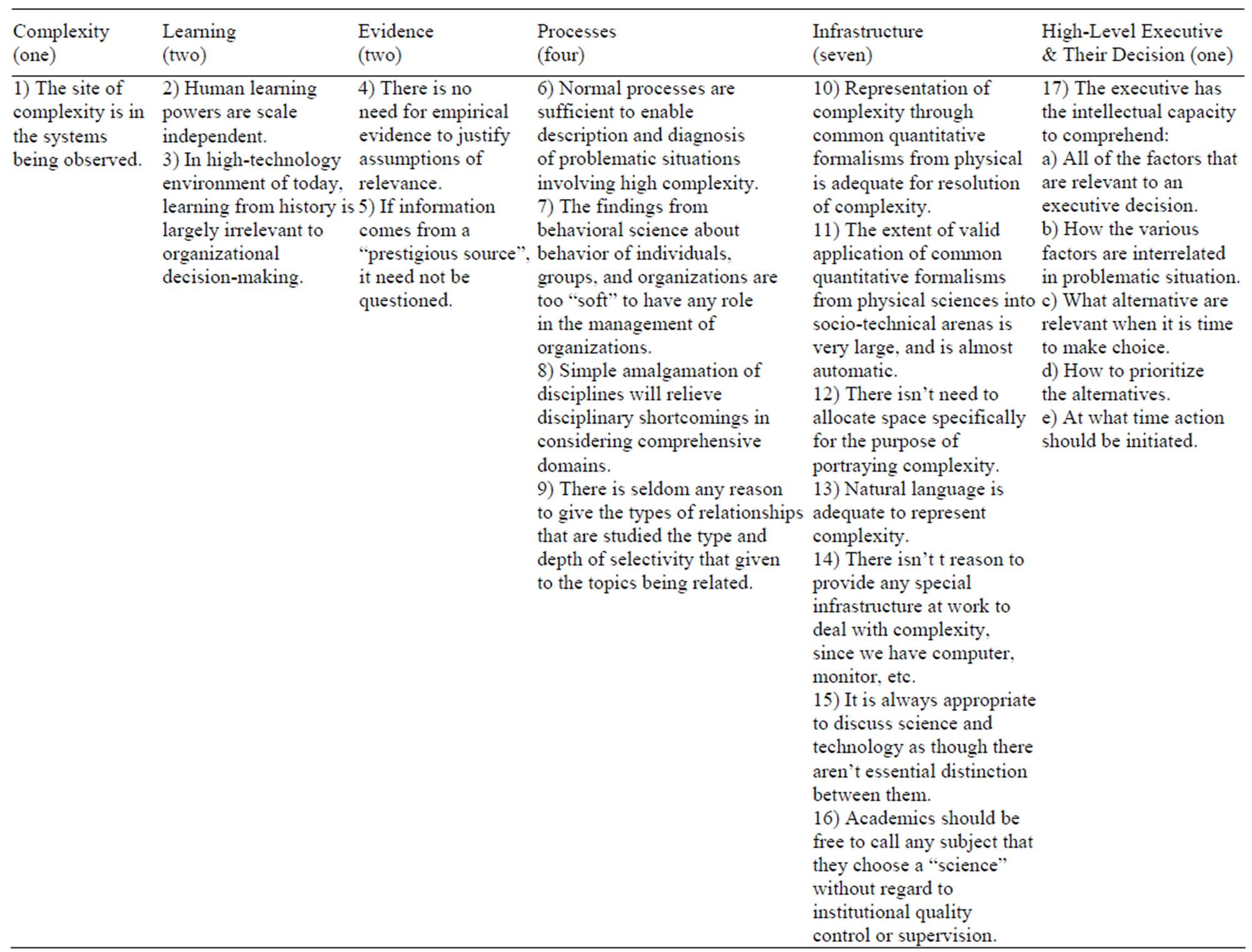
Table 1. The classification of killer assumptions.
of research on complexity has revealed twenty laws of complexity [2,3], which appear to be applicable to virtually all complex systems that serve the public (Table 2).
2.3. Seven Root Risk Factors of ITSM Project Implementation
Reference [6] was concluded that if the organization wished to successfully implement ITSM’s customer satisfaction model, it should eliminate the misunderstandings of IT service objectives first, while the adoption of knowledge supporting structure of IT service management could play a multiplier effect. Reference [7] was concluded that if the organization wished to successfully implement ITSM’s customer satisfaction model, it should eliminate the misunderstandings of IT service objectives first, while the adoption of knowledge supporting structure of IT service management could play a multiplier effect.
Reference [8,9] identified the risk factors which resulted in the failure of ITSM project implementation, and they are sorted in accordance with the importance degree of the risk. The most critical twenty risk factors were also identified. There are in the following: 1) Objectives of the project are not clear; 2) The senior officials of the enterprise are indecisive; 3) Inadequate and ineffective communication among staff members; 4) The core members or project managers of an external IT company are inexperienced; 5) Senior officials do not give proper priority to the project; 6) Design is not based on business demands; 7) Vague responsibility definition among staff members; 8) Process mission and objectives are not clear; 9) The business demand analysis is not sufficient; 10) The external IT company and the enterprise do not reach consensus on the business processes; 11) Customer demands change frequently; 12) The brain drain on the enterprise is too much; 13) The company and the client are not in agreement on the level of service; 14) The business strategy of the enterprise is vague; 15) The resources allocated to the project are not sufficient; 16) The branch separatism phenomenon occurs when the enterprise encounters branch conflicts; 17) The external
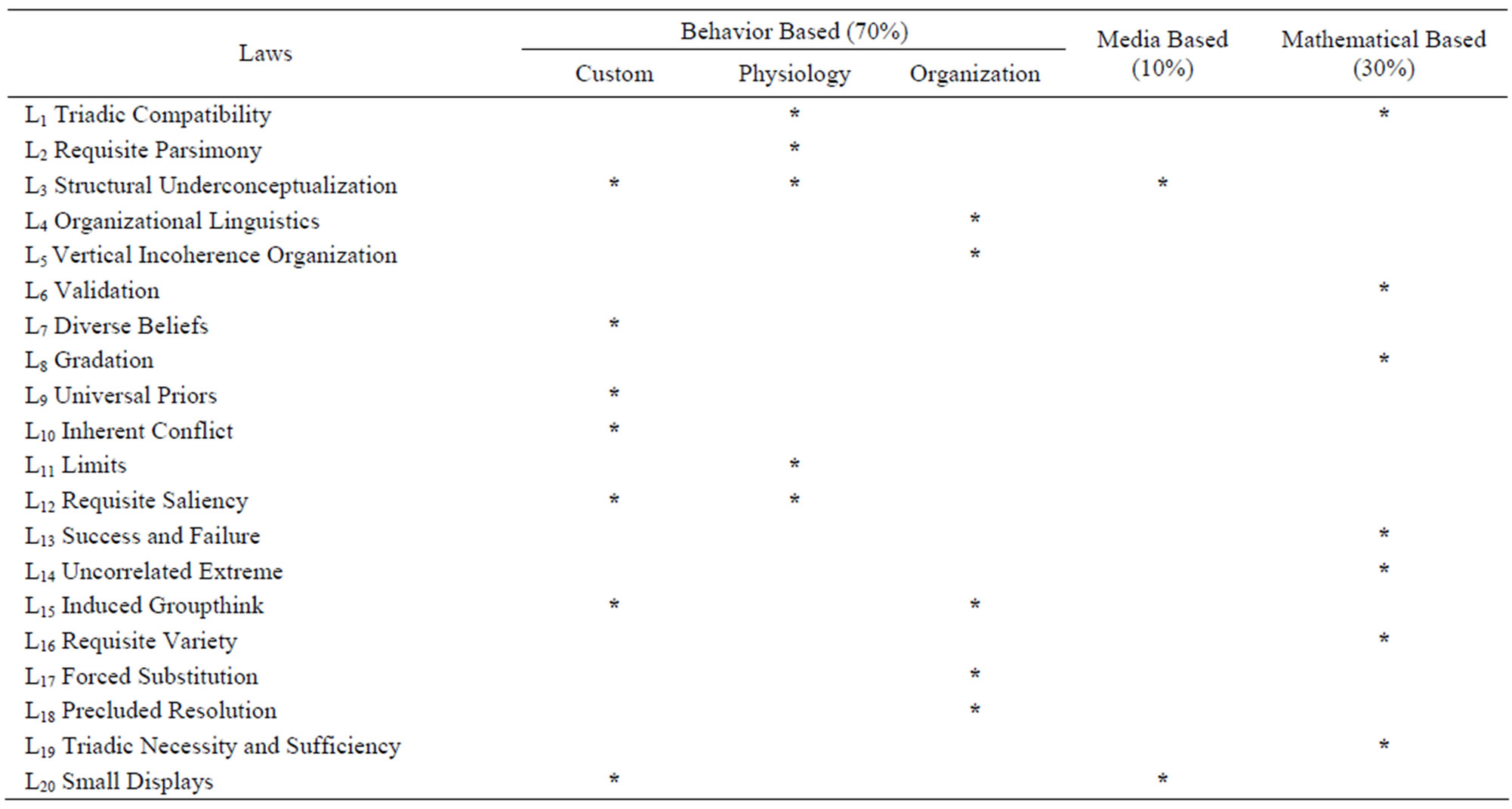
Table 2. The classification of complexity laws.
IT company staff doesn’t have appropriate authority; 18) Incorrect order of process implementation; 19) IT infrastructure planning and design are unreasonable; 20) The project scale is too large, which increases the complexity of management.
Then, interpretive structural model (ISM) is applied to determine the twenty risk factors’ causal relationship, and ISM of risk factors of the service management project implementation is established. Finally, six root risk factors are identified: 1) Objective of the project is not clear; 2) Inadequate and ineffective communication among staff members; 3) Senior officials don’t give proper priority to the project; 4) The business strategy of the enterprise is vague; 5) The brain drain on the enterprise is too much; 6) The IT infrastructure planning and design in the enterprise is unreasonable. How to solve the six root risk factors effectively? It may be the key to implementation of IT service management project. In our understanding, ITIL 3.0 pays much attention to that the indicators with science; 7) Indicators without science is the seven root risk factor in this paper.
3. Empirical Analysis of Killer Assumptions
Statistics Analysis of Questionnaire
The respondents in this paper are the graduate students in grade three and students of Master of Software Engineering (MSE), most of which are working in IT departments of government, enterprises and research institutions. Before taking the questionnaire, several impalpable definitions were explained to the respondents. There were 105 valid returns out of the 114 questionnaires, collected in February and March in 2011. The respondents’ sex ratio is about 3:2 (61:44) and the age is between 21 and 36. Among them, 41% (sample size 43) is in major of Business Management, 27% (sample size 28) is in administrative decision and 17% (sample size 18) is studying MSE, among which there are two information system managers, two project managers, five experienced information system professionals and 9 information system users, all having good understanding with information system.
The descriptive statistics is illustrated in Table 3.
It can be illustrated in Table 3 that: 1) Mean varies from 1.73 to 3.99, which means killer assumptions do not meet with fierce opposition; 2) Killer assumptions, which sample mean is larger than 3.5, will be selected to find which can be universally recognized.
In order to test whether there is significant difference between sample mean and population mean, we took One Sample T-test with SPSS. The result of 1-Sample K-S showed the sample about the 17 killer assumptions is normal distribution, meaning T-test is viable.
H0: population mean = 3.5; H1: population mean ≠ 3.5. Confidence is 95%, and α = 0.05. Then One-Sample T Test was taken with SPSS (Table 4).
Five killer assumptions were universally recognized: 1) Human learning powers are scale-independent (K2); 2) Simple amalgamation of disciplines will relieve disciplinary shortcomings in considering comprehensive domains (K8); 3) Complex problems can be solved through mathematical models and equations (K10); 4)
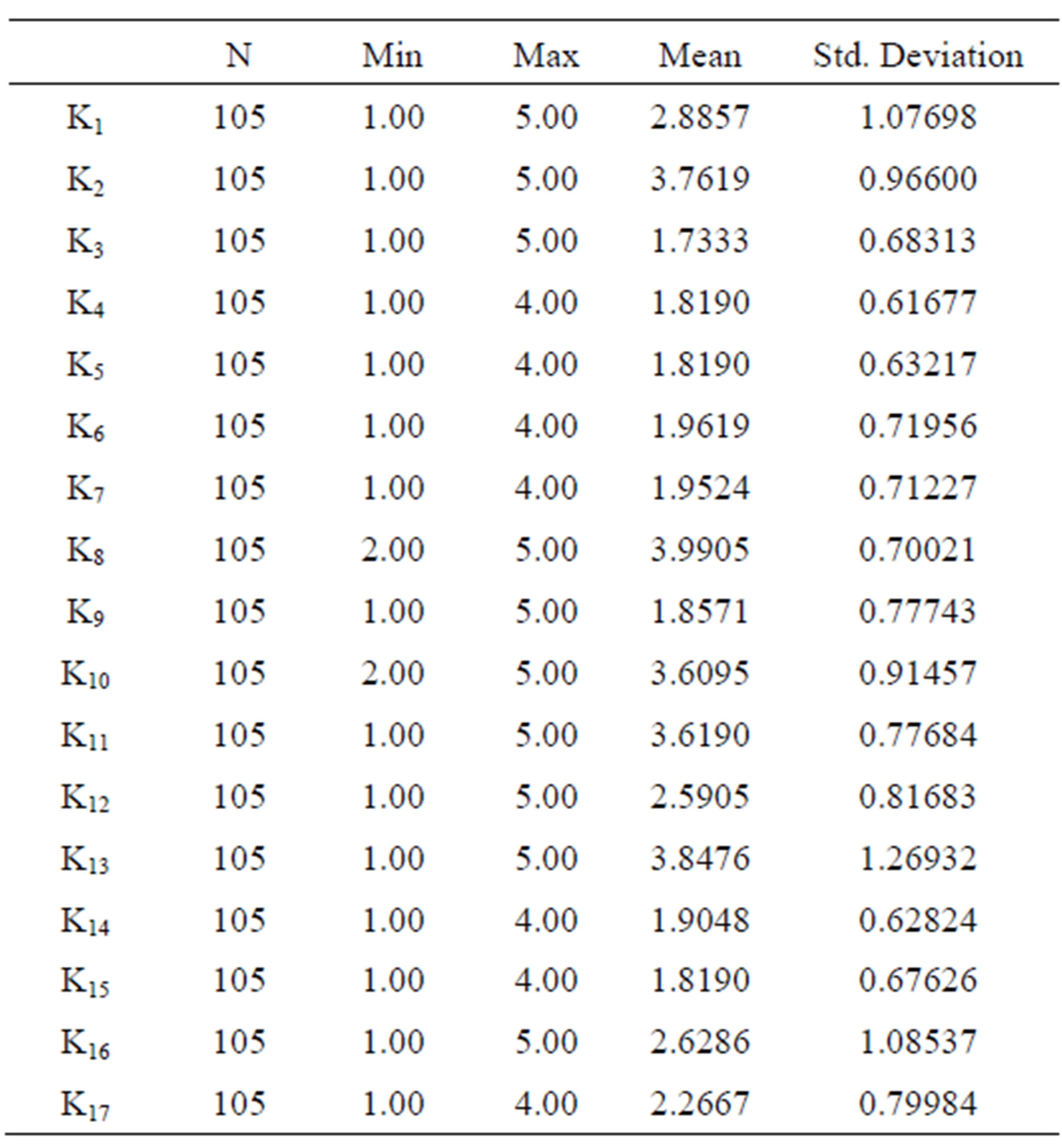
Table 3. Statistics description of questionnaire on killer assumptions.
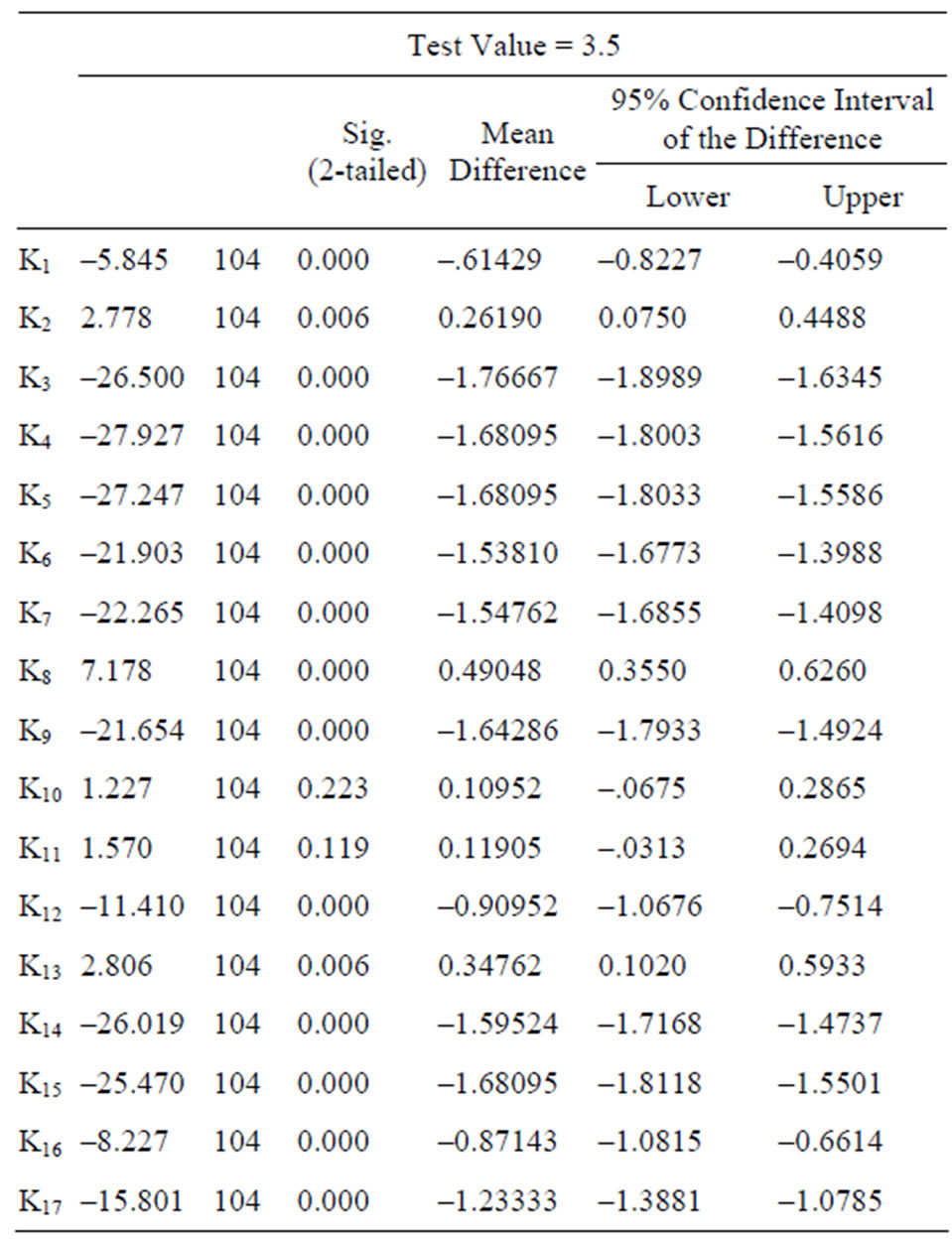
Table 4. The result of One-Sample T-Test.
Quantitative formalisms from physical sciences can be extended into socio-technical arenas (K11); 5) Natural language is adequate to represent complexity (K13).
4. Risk Factor Analysis Based on Complexity Proposition
4.1. Ground Theory Overview
Ground theory to provide the basic knowledge and procedures needed by persons who are about to embark on their first qualitative research projects and who want to build theory at the substantive level. In this paper, the main steps of grounded theory are in the followings [9]: 1) Theoretical sampling; 2) Collecting information; 3) Coding information, and forming the concepts from information; 4) Continually comparing between data, and between conceptions and between data and conceptions; 5) Forming theoretical conceptions ,and establishing the relationships between conceptions; 6) Building theory and judging it.
4.2. Research Questions Generation
The scientific theory of complexity of structured-based school is used to solve the subjective question in the large complex project: what is the relationship between the twenty complexity proposition and root risk factors?
4.3. Data Collection
During the interviews, we listened and paid attention to what the interviewee concerns in the perspective of participant in order to avoid the preconception and guidance. In additional, we used open questions to encourage the interviewee to speak their real ideas.
4.4. Data Procession
After dispersing the data structure, we analyzed in detail, and discussed with relevant experts, compared and screened continuously between data, concept and complexity proposition. Finally, eleven concepts were formed, and seven complexity propositions and killer assumptions corresponding to them were found (Table 5). The concepts from open coding and the corresponding root risk factors were obtained as well (Table 6).
4.5. Theory Building
Theoretical coding refers to the implicit relationship among the concept or the category formed by conceptualizing substantial code, such as coordinative relationship, causal relationship and progressive relation, etc. They are natural emerged to generated the concept, then form a complete theory.
The Law of Requisite Saliency considers group members always have great difference when they evaluate the relative importance of each factor for complex situation and problem. If we do not take further study of the actual situation of the design, it will come up with the ineffective
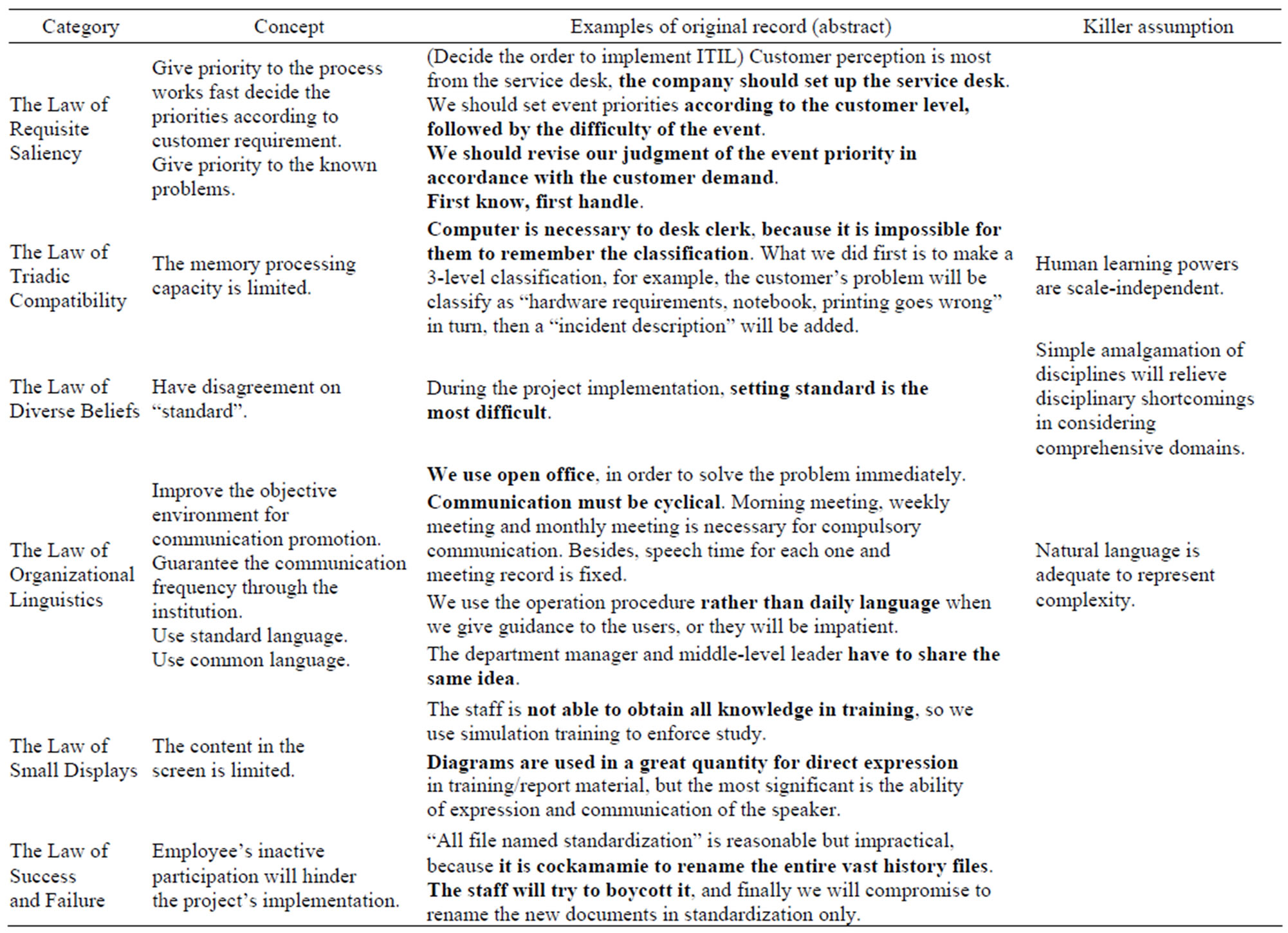
Table 5. The concepts from open coding and the corresponding complexity propositions.
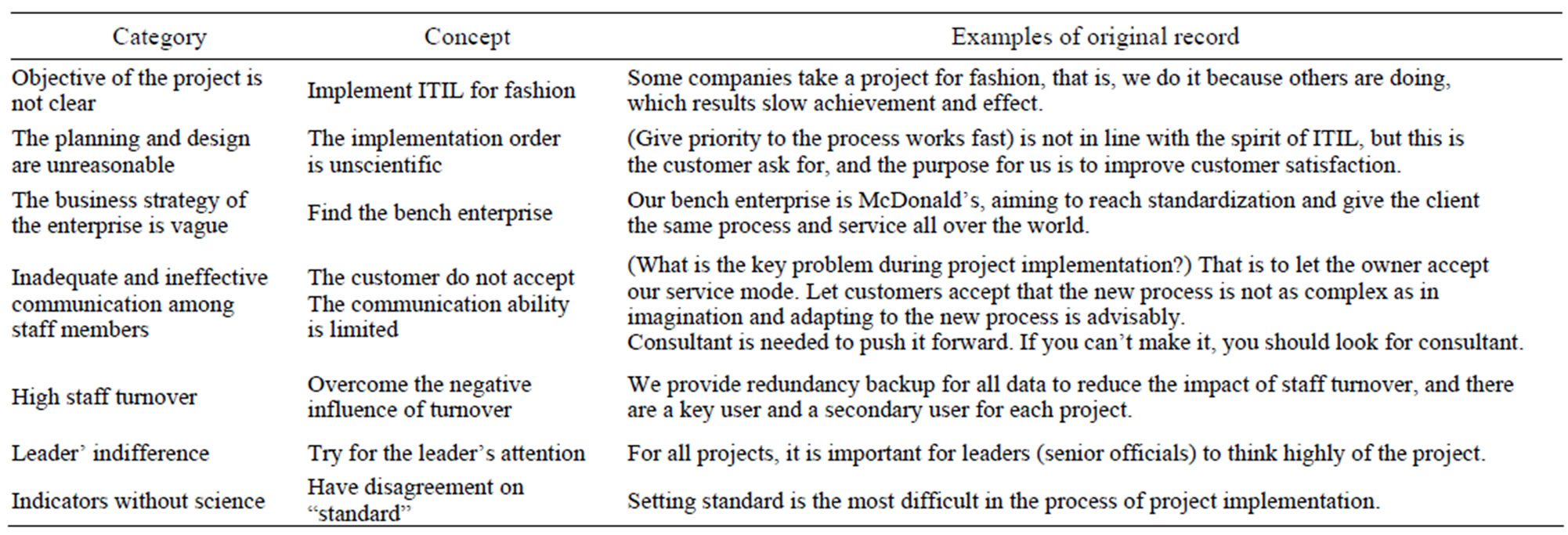
Table 6. The concepts from open coding and the corresponding root risk factors.
conversation, the wrong decision, the arbitrary design and so on.
During ITIL implementation, companies prefer to give priority to implementing the process works fast and solving the known fault, which is not in line with the spirit of ITIL and results in undefined goals and unreasonable planning and design.
The assumptions are put forward as follow:
H1: The Law of Requisite Saliency has significant influence on the undefined goals of the project.
H2: The Law of Requisite Saliency has significant influence on the unreasonable planning and design.
During ITIL planning and design, it is difficult for workers to understand the coupled relation between models, leading to design mistakes.
The assumption is put forward as follow:
H3: The Law of Triadic Compatibility has significant influence on the unreasonable planning and design.
Setting standard is the most difficult in the process of project implementation, that is, to confirm the result we should achieve, which cause business strategy unclear and unscientific indicators.
The assumptions are put forward as follow:
H4: The Law of Diverse Beliefs has significant influence on the unclear business strategy.
H5: The Law of Diverse Beliefs has significant influence on the unscientific indicators.
During ITIL implementation, a serious of actions is taken to make sure that there are enough language domains for the internal communication in company. At first, the group leader makes conclusions in the morning meeting, after that, the event members communicate together. Then the project manager communicates with the general manager. At last, the general manager communicates with customer’s general manager. While the knowledge gap exists between the developer and the client, we should look for the consultant as communication intermediary.
The assumptions are put forward as follow:
H6: The Law of Organizational Linguistics has significant influence on the unclear business strategy.
H7: The Law of Organizational Linguistics has significant influence on the lack of effective communication among different people.
During ITIL training, the staffs are not able to obtain all knowledge, so we should use diagrams in a great quantity for direct expression in materials, and use simulation training to enforce study.
The assumption is put forward as follow:
H8: The Law of Small Displays has significant influence on the lack of effective communication among different people.
The Law of Success and Failure considers the design success consist of 7 key factors, including employee involvement and leader support. And the lack of any one will lead to failure.
Because of the integrated features of ITSM, the implementation of the project involves many departments, which requires executives use authority to help promoting cooperation and coordination among departments.
The assumptions are put forward as follow:
H9: The Law of Success and Failure has significant influence on the high staff turnover.
H10: The Law of Success and Failure has significant influence on indifference of the executives.
4.6. Theory Saturation Verification
The information collected was selected randomly again to verify the theory, but no new category was found. So we can consider that it has reached theory saturation. The deep logic of complexity proposition and root risk factors was illustrated in Figure 1.
4.7. Theory Verification
Twelve experts who have ever implemented ITSM program in Guangzhou were chosen to be respondents. They all had rich experience and had certain understanding of psychology. The relationship between complexity proposition and root risk factors were illustrated in Table 7. The column signed “√” means the complexity in corresponding row will generate the risk factors in corresponding line. Nine assumptions were verified, which means the rationality of using grounded theory to construct assumptions is high. It was found that 1) The Law of Diverse Beliefs had significant influence on the undefined goal of the project; 2) The Law of Success and Failure had significant influence on the unreasonable planning and design, the unclear business strategy and the lack of effective communication among different people.
5. Risk Averse Strategy
If needs of complexity are met, the possibility for human to solve complexity problem will be increased.
1) Identify the individuals and pay more attention to the complexity. We should realize that complexity does exist in mind, not in problematic situations (means system), for individuals and groups, which is a challenge of learning. The organizational training course should include information management concepts, IT implementation knowledge, the principle knowledge on IT application and the training of application, etc. The form of training can be formal training courses, user manuals and the onsite guidance from IT personnel or consultants. We can change the perception of employee and improve their IT knowledge and skills through training, so as to promote the enterprise’s IT absorptive capability. In addition, the clear career development plan and incentives are also important.
2) Select the process carefully. Process selection and design should base in reliable scientific evidence in order to process situation systematically, limit the expand of complexity situation, reduce the individual cognitive burden, eliminate restraining factors of most situation, provide many personal strengthening factors, and support solving the problem of complexity.
3) Apply domain language. We should realize the linear logic fault of natural language and integrate the nonlinear logic into it. During requirement development, comprehensive training is necessary for each subject to communicate under unified language terms. The use of visual language and tools makes the demand easier to understand, for example, UML and Use Case can make
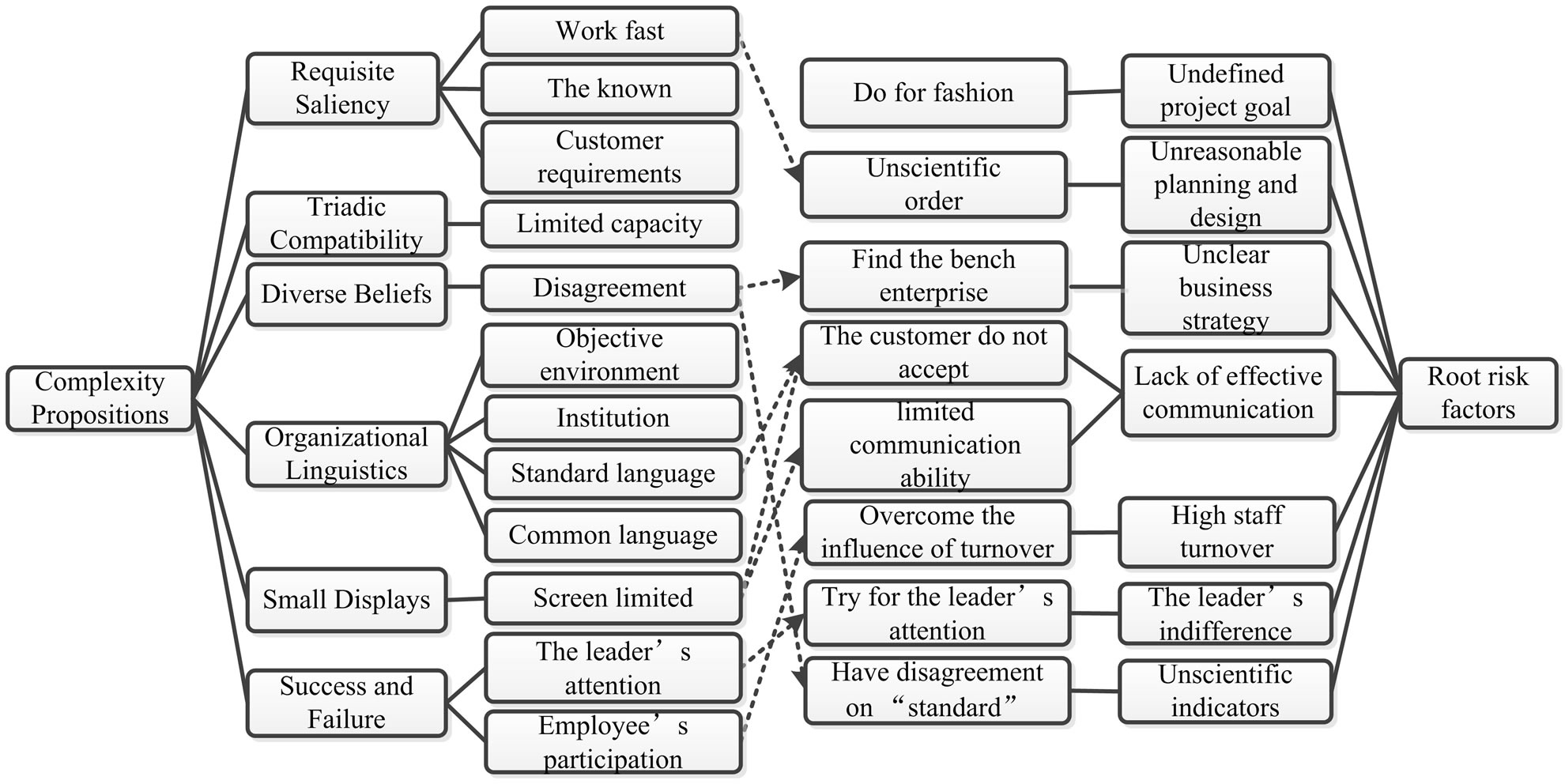
Figure 1. The deep logic of complexity proposition and root risk factors.
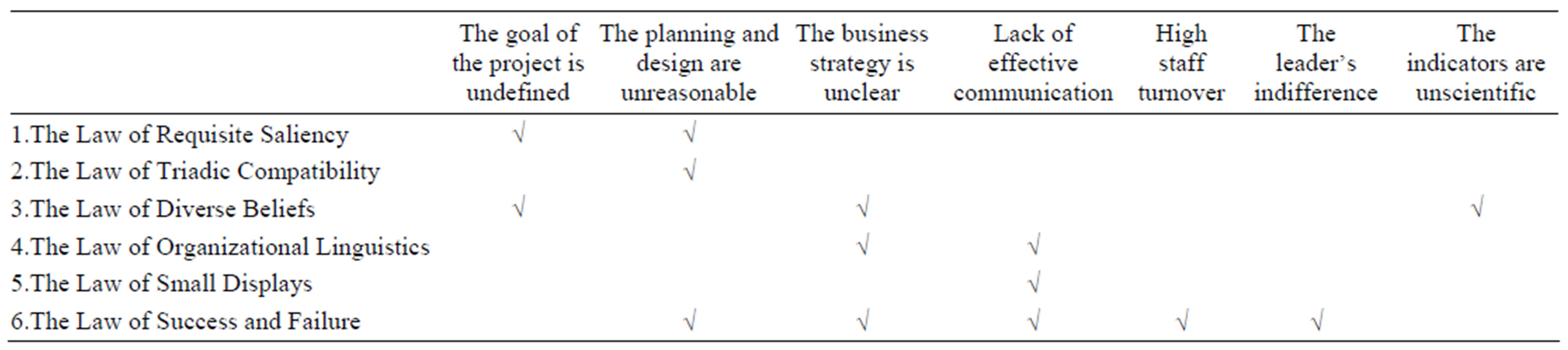
Table 7. The relationship between complexity proposition and root risk factors.
the demand more intuitive. In addition, the prototype is the key technology derived from demand, and the model should be expressed clearly by specific characters and graphs.
4) Design the personalized work space according to the demand to satisfy the need of human learning.
5) Enhance the role of executives. Executives should be offered the key decision information about the problematic situation, and deal with it seriously. Functional departments should to communicate effectively to analyze risk and prevent arbitrary decision-making. In order to strengthen managers’ understanding of information, we can adopt the following methods: hiring external consultants, taking information training and learning the enterprise’s successful information technology experiences.
6) Communicate appropriately. During communication, we have better give up the concept of department and organization. Simile and analogy are allowed in communication under the condition of clear expression and minimal ambiguous case. During requirements development, convening individual and group interviews, brainstorming sessions, key problem seminar, field symposiums and design symposiums are effective. In additional, we should try to use individual communication and face-to-face interaction to choose different communication places and different ways according to similar systems and industry characteristics. We also should try to use collective exchanges and face-to-face interaction, such as brainstorming sessions, key problem seminar, field symposiums and design symposiums during the demand development. In the process of demand combination and systematization, design symposiums and demand simulation test should be conducted as far as possible. When verifying the demand internalization, we should try to use individual communication and virtual interaction, such as demand shows and requirement review symposiums, etc.
6. Conclusions
In this paper,five common Killer Assumptions are selected from Warfield’s 17 killer assumptions through empirical analysis. Enterprise interview and questionnaire survey are used to build and verify the relational model between the root risk factors of implementation of the ITSM project and the six complexity propositions based grounded theory. Finally, risk-averse strategies are generated to meet the demand for complexity.
The primary limitation of this research to date is that the interviews and documents have only involved people who are in China. While it certainly is important to do this work in a specific non-Western culture (i.e., China), for the sake of completeness, it would be similarly useful to apply Warfield version of systems science perspective (WSS) to an ITSM project in a Western setting. We doubt that any differing results will be due to the cultural differences. ITSM started just a few years ago in China. However, this usually involves only ITSM operations, and does not include service strategy, service design, service transition and continual service improvement (as found in ITIL 3.0). In Reference [10], the Work Program of Complexity (WPOC) is applied in managing risks of ITSM projects’ implementation.
Although there is a long way to go, it is sure that the research will helpful for both ITSM theories construction and ITSM practices’ improvement in the view of WSS perspective.
7. Acknowledgements
Thank for the helpful discussion with Mr. Zhixing Zhuo, Mr. Ji Chen, and Mr. Dejie Li.
REFERENCES
- J. V. Bon, M. Picper and A. D. Veen, “Foundations of IT Service Management Based on ITIL,” Van Haren Publishing, Zaltbommel, Netherlands, 2005.
- J. N. Warfield, “Understanding Complexity: Thought and Behavior,” AJAR Publishing Company, USA Palm Harbor, 2002.
- J. N. Warfield, “Twenty Laws of Complexity: Science Applicable in Organizations,” Systems Research and Behavioral Science, Vol. 16, No. 1, 1999, pp. 3-40. doi:10.1002/(SICI)1099-1743(199901/02)16:1<3::AID-SRES241>3.0.CO;2-F
- S. M. Staley and J. N. Warfield, “Enterprise Integration of Product Development Data: Systems Science in Action,” Enterprise Information Systems, Vol. 1, No. 3, 2007, pp. 269-285. doi:10.1080/17517570701507685
- J. P. Wan, “Research on Software Product Support Structure,” Journal of Software Engineering and Applications, Vol. 2, No. 3, 2009, pp. 174-194.
- W. G. Tan, A. C. Stel and M. Toleman, “Implementing IT Service Management: A Case Study Focusing on Critical Success Factors,” Journal of Computer Information Systems, Vol. 50, No. 2, 2009, pp. 1-12.
- J. P. Wan, H. Zhang and D. Wan, “Evaluation on Information Technology Service Management Process with AHP”, Technology and Investment, Vol. 2, No. 1, 2011, pp. 38-46. doi:10.4236/ti.2011.21005
- J. P. Wan, S. Q. Zhu and Y. F. Wang, “Empirical Analysis on Risk Factors of IT Service Management Project Implementation,” IEEE International Conference on Wireless Communications, Networking and Mobile Computing, Dalian, China, 14-16 October, 2008.
- J. Corbin and A. Strauss, “A Basics of Qualitative Research: Techniques and Procedures for Developing Grounded Theory,” Sage, London, 1990.
- J. P. Wan and J. Jones, “Managing ITSM Implementation Complexity: A Warfield Version of Systems Science Perspective,” 2011. http://www.tandfonline.com/doi/abs/10.1080/17517575.2011.625572
NOTES
*This research was supported by Key Project of Guangdong Province Education Office (06JDXM63002), NSF of China (70471091), and QualiPSo (IST-FP6-IP-034763).

