Advances in Pure Mathematics
Vol.05 No.08(2015), Article ID:57682,23 pages
10.4236/apm.2015.58047
Analytic Theory of Finite Asymptotic Expansions in the Real Domain. Part II-C: Constructive Algorithms for Canonical Factorizations and a Special Class of Asymptotic Scales
Antonio Granata
Department of Mathematics and Computer Science, University of Calabria, Cosenza, Italy
Email: antonio.granata@unical.it
Copyright © 2015 by author and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY).
http://creativecommons.org/licenses/by/4.0/



Received 30 April 2015; accepted 27 June 2015; published 30 June 2015
ABSTRACT
This part II-C of our work completes the factorizational theory of asymptotic expansions in the real domain. Here we present two algorithms for constructing canonical factorizations of a disconjugate operator starting from a basis of its kernel which forms a Chebyshev asymptotic scale at an endpoint. These algorithms arise quite naturally in our asymptotic context and prove very simple in special cases and/or for scales with a small numbers of terms. All the results in the three Parts of this work are well illustrated by a class of asymptotic scales featuring interesting properties. Examples and counterexamples complete the exposition.
Keywords:
Asymptotic Expansions, Canonical Factorizations of Disconjugate Operators, Algorithms for Canonical Factorizations, Chebyshev Asymptotic Scales

12. A Third Heuristic Approach to Factorizational Theory
We continue the numbering of sections used in the preceding two parts of this work: Part II-A [1] , and Part II-B [2] . In the survey ([3] , §3) we highlighted two heuristic approaches leading to two Conjectures whose proofs appear in [1] [2] in a completed form. We are going to illustrate another way to arrive at the second Conjecture, ([3] , p. 12), by the elementary use of L’Hospital’s rule. In our endeavor to find sufficient and/or necessary conditions for the validity of an asymptotic expansion
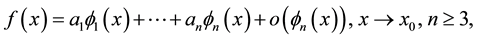 (12.1)
(12.1)
where the asymptotic scale
 (12.2)
(12.2)
is subject to certain Wronskian restrictions, let us try to find out expressions for the coefficients  alternative to the elementary (and rarely useful) iterative formulas:
alternative to the elementary (and rarely useful) iterative formulas:
 (12.3)
(12.3)
where the existence (as finite numbers) of the involved limits characterize the coefficients 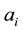 whenever the
whenever the ’s do not vanish on a deleted neighborhood of
’s do not vanish on a deleted neighborhood of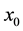 . Let us now heuristically try to evaluate the first few limits above by L’Hospital’s rule:
. Let us now heuristically try to evaluate the first few limits above by L’Hospital’s rule:
 (12.4)
(12.4)
where by (2.35) M1, M2 are the operators defined in (3.3), apart from the signs. By iteration we may conjecture that this heuristic procedure leads to the formulas
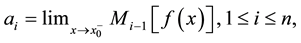 (12.5)
(12.5)
provided the involved limits exist in ; and these formulas are true, apart from the signs, whenever the remainder in (12.1) is identically zero ([1] , Prop. 3.1). Such kind of manipulations may seem artificial and awkward from an elementary viewpoint and it is by no means obvious that iteration of the procedure yields (12.5).
; and these formulas are true, apart from the signs, whenever the remainder in (12.1) is identically zero ([1] , Prop. 3.1). Such kind of manipulations may seem artificial and awkward from an elementary viewpoint and it is by no means obvious that iteration of the procedure yields (12.5).
・ In §13 we show that different organizations of the above calculations give rise to two algorithms for constructing canonical factorizations starting from a given asymptotic scale; the procedures seem quite natural in the context of formal differentiation of an asymptotic expansion and shed a light of “easiness”, so to say, on the formulas of asymptotic differentiability obtained so far and seemingly complicated in themselves.
・ In $14 an example illustrating the two algorithms is given.
・ In §15 a useful class of scales is studied highlighting some pecularities concerning various types of formal differentiabilty and here the idea underlying the two algorithms plays a role even if manipulated differently.
・ The last §16 contains additional remarks on the algorithms.
13. Constructive Algorithms for Canonical Factorizations
The original procedure used by Trench [4] to construct a C.F. of type (I) for a disconjugate operator 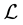 is not an intuitive one but, besides its historical value, it shows the existence of such a factorization separately at each endpoint of the interval of disconjugacy; this fact in turn shows the existence of a basis of ker
is not an intuitive one but, besides its historical value, it shows the existence of such a factorization separately at each endpoint of the interval of disconjugacy; this fact in turn shows the existence of a basis of ker 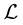 forming an asymptotic scale at each fixed endpoint. But in the theory we have been developing the starting point is different, namely it is such an asymptotic scale. Here we exhibit two easy algorithms to construct both types of C.F.’s starting from an explicit basis of ker
forming an asymptotic scale at each fixed endpoint. But in the theory we have been developing the starting point is different, namely it is such an asymptotic scale. Here we exhibit two easy algorithms to construct both types of C.F.’s starting from an explicit basis of ker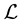 forming an asymptotic scale at one endpoint. The so-obtained factorizations will be proved to coincide with those obtainable by Pólya’s procedure when applied either to the asymptotic scale
forming an asymptotic scale at one endpoint. The so-obtained factorizations will be proved to coincide with those obtainable by Pólya’s procedure when applied either to the asymptotic scale 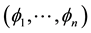 or to the inverted n-tuple
or to the inverted n-tuple 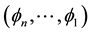 so providing alternative constructive ways to such factorizations. Each step in the algorithms has an asymptotic meaning and the algorithm for a C.F. of type (II) is particularly meaningful as it highlights how the operators
so providing alternative constructive ways to such factorizations. Each step in the algorithms has an asymptotic meaning and the algorithm for a C.F. of type (II) is particularly meaningful as it highlights how the operators 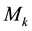 naturally arise from an asymptotic expansion with an identically-zero remainder when one attempts to find out independent expressions for each of its coefficients. Both algorithms may sometimes be quicker to apply than Pólya’s procedure, especially for small values of n, avoiding the explicit use of Wronskians.
naturally arise from an asymptotic expansion with an identically-zero remainder when one attempts to find out independent expressions for each of its coefficients. Both algorithms may sometimes be quicker to apply than Pólya’s procedure, especially for small values of n, avoiding the explicit use of Wronskians.
Let us consider a generic element 

which we interpret as an asymptotic expansion at 
Theorem 13.1 (The algorithm for a special C.F. of type (II)). Let 
al C.F. of 

viding by the first meaningful term on the right, concide with the expansions obtained by applying to (13.1) the operators 


(A) Verbal description of the algorithm.
1st step. Divide both sides of (13.1) by the first term on the right, which is the term with the largest growth- order at

Suppressing the derivative the left-hand side in (13.2) is the operator M0u.
2nd step. Divide both sides of (13.2) by the first term on the right and take derivatives so obtaining

Suppressing the outermost derivative the left-hand side in (13.3) is the operator M1u.
3rd step. Repeat the procedure on (13.3) dividing by the first term on the right and then taking derivatives so getting

Iterating the procedure each of the obtained relation is an identity on 

where the
(B) Schematic description of the algorithm.
Step “1”:
Step “2”:
Step “3”:
Step “4”:
and so on, where the symbol “d & d” stands for the two operations “divide” both sides by the underbraced term on the right and then “differentiate” both sides (the equation in each step being the result of the preceding step).
Theorem 13.2 (The algorithm for the C.F. of type (I)). Let 



(A) Verbal description of the algorithm.
1st step. Divide both sides of (13.1) by the last term on the right, which is the term with the smallest growth- order at

2nd step. Divide both sides of (13.6) by the last term on the right and then take derivatives so obtaining

3rd step. Repeat the procedure on (13.7) dividing by the last term on the right and then taking derivatives so getting

Iterating the procedure each of the obtained relation is an identity on 

where the
(B) Schematic description of the algorithm.
Step “1”:
Step “2”:
Step “3”:
Step “4”:
and so on with the symbol “d & d” reminding of the two operations “divide” both sides by the underbraced term on the right and then “differentiate” both sides (the equation in each step being the result of the preceding step).
Remarks. 1) In order to obtain any C.F. by the above procedures one may simply choose
2) If some operator 


then the algorithm in Theorem 13.2 yields the C.F. of type (I) at x0, valid on the whole given interval 







3) In practical applications of the algorithms there is a fatal pitfall to avoid, namely the temptation at each step of suppressing brackets, cancelling possible opposite terms and rearranging in an aestetically-nicer asymptotic scale. This in general gives rise to a factorization of an operator quite different from
4) The algorithms are of course applicable to obtain C.F.’s at a left endpoint valid on each neighborhood whereon the Wronskians never vanish.
Proof of Theorem 13.1, that of Theorem 13.2 being exactly the same after replacing 






hence it is enough to show that Pólya’s expression for 

It is also clear that the various identities obtained are nothing but those obtained by applying to (13.1) the operators 


Comparing the expressions in (2.37) [1] , and those given by our algorithm we see that the two procedures coincide if the following identity holds true:

We shall show the validity of this identity even if the outermost derivatives are suppressed. Using the elementary formula 

by (13.13) with 
We have also proved that at the k-th step the linear combination on the right, before dividing for the next step, coincides with the expression
which, by (3.8) in Part II-A, is an asymptotic expansion at
14. Examples Illustrating the Two Algorithms
Consider the fourth-order operator L of type (2.1)1,2, [1] , such that

acting on 


the algorithm in Theorem 13.2 yields in sequence:
Hence

and this is “the” global C.F. of L of type (I) at
(The underbraced terms on the right are those by which one must divide and then differentiate.) Hence:

where

Hence (14.4) is a C.F. of L of type (II) at 

which is easily seen to be the interval




In the various steps of the above procedures one must carefully avoid the temptation of rearranging the terms in the right-hand side in (supposedly) nicer asymptotic scales. For instance the first procedure involves quite simple terms and only at the last-but-one step we may split the remaining term on the right by writing
and taking 
This gives a fifth-order operator

distinct from the given fourth-order operator. On the contrary the second procedure offers a great number of temptations! For instance if one rewrites the result of the first step as

and then goes on applying the second algorithm to (14.8) as if the right-hand side would be an asymptotic expansion with three meaningful terms, one gets:

the only difference between the two expressions on the right being the term-grouping. From the upper relation in (14.9), considered as an asymptotic expansion at 
and then

whose left-hand side is a fourth-order operator distinct from our operator. If, instead, one starts from the lower relation in (14.9), considered as an expansion at 
and so forth in an endless process leading nowhere!!
15. A Special Class of Chebyshev Asymptotic Scales
15.1. Preliminaries
We specialize the results of our theory for the special class of Chebyshev asymptotic scales

where

Our assumptions will be:

This class has been cursorily presented in ([3] , §7) but will receive here a detailed treatment highlighting how the ideas of our algorithms may lead to discover new facts about formal differentiability. The class contains meaningful and frequently-used scales exhibited at the end of the section.
To apply our theory we observe that by a proper device it can be given an elementary proof of the formula (which is anyway a classical result):

where 



of the differential operator 
various constant factors appearing in the expressions of the Wronskians. Hence, apart from immaterial constant factors, the functions



Proposition 15.1 (C.F.’s for the asymptotic scale (15.1)). Let 


(I) The “unique” C.F. of type (I) at 

and we denote by

(II) A special C.F. of type (II) at 

and we denote by

The above factorizations may quite simply be obtained via our algorithms as well; for instance starting from

the procedure of the second algorithm yields in sequence:
and so on (15.7) follows. If, as a first step, both sides of (15.9) are divided by 


and no matter how many times we iterate the procedure the right sides is a non-identically zero expression except for special sequences of the exponents such as 




seem natural contingencies quite likely to be encountered. We shall show that the two main sets af expansions characterized in our theory actually are equivalent to expansions involving iterates of the simple operator 



noticing the identities

The second identity in (15.13) is the main operational property of

15.2. Weak and Strong Formal Differentiability
We report only on “complete” asymptotic expansions; for “incomplete” expansions it might be complicated to list all the circumstances concerning estimates of the remainders: see Theorem 9.2-(II) in Part II-B.
Proposition 15.2. (Characterizations of “weak” formal differentiability for the scale (15.1)).
(I) Referring to Theorem 4.5 in [1] we have the equivalence of the following four properties:
1) The set of asymptotic expansions as 


where 

2) The set of asymptotic expansions as 


3) The improper integral

4) For suitable constants 


(II) The linear combinations in the two types of differentiated expansions are explicitly given by

wherein the second sum actually denotes the expression of 




Proposition 15.3. (Characterizations of “strong” formal differentiability for the scale (15.1)).
(I) Referring to Theorem 5.1 in [1] we have the equivalence of the following four properties:
1) The set of asymptotic expansions as 


2) The set of asymptotic expansions as 


3) The improper integral

4) For suitable constants 


(II) The linear combinations in the two types of differentiated expansions are explicitly given by

wherein the second sum, generally speaking, contains all the terms in the expression of
Comparing (15.16) and (15.21) we see that each remainder in (15.16) has a growth-order greater than the corresponding one in (15.21) hence we may say that (15.16) and (15.21) are obtained from the first expansion in (15.15) by formal differentiation respectively in a “weak” and in a “strong” sense: see Remark and Open Problem at the end of §8 in [2] . From an algebraic viewpoint the estimates of the remainders in (15.21) seem to be the most natural possible but actualy they hold true only under a strong assumption. To visualize, notice that expansions in (15.21) correspond to the formal procedure in (15.11), starting from (15.9) with a remainder inserted, whereas expansions in (15.16) correspond to the following formal procedure

Propositions 15.2 and 15.3 generalize the technical lemmas used in ([7] , Lemmas 7.3, 7.4) for real-power expansions, which is the particular choice
Proposition 15.4. (A case of equidistant exponents). (I) If




be



we have the expansion for f together with the equivalent sets of differentiated expansions

with the coefficients 



we have the expansion for f together with the equivalent sets of differentiated expansions

with the coefficients 
(II) If



quence of exponents as 




we have the expansion for f together with the equivalent sets of differentiated expansions

with the coefficients




we have the expansion for f together with the equivalent sets of differentiated expansions

with the coefficients 


Writing down the first two differentiated expansions for each group may help the reader grasp the different circumstances. In the situation of Proposition 15.4-(I) and in a concise notation let us start from the expansion

Then the three expansions in (15.27) and (15.29) respectively run as follows:



For a quick check of (15.37) the reader is suggested to use the algorithm in Proposition 13.1.
Remark. The above results give a glimpse of the great variety of differentiated expansions that may be encounterd in applications. In the general case of equidistant exponents



15.3. Proofs
The proofs of Propositions 15.2, 15.3 rely on formulas linking the various involved operators.
Lemma 15.5. (I) For weak differentiability the formula linking 


with suitable coefficients 

(II) For strong differentiability the formula linking 


with suitable coefficients 

Proof. Let us prove (15.38). For 

and suppose (15.38) hold true for a certain k; then for 
which is (15.38) with k replaced by 




Due to the linearity of our operators it is enough to prove our claims for the case
Lemma 15.6. With shortened notations we have:


Proof. The equivalence in (15.41) is easily checked for 

We assume this equivalence to hold true for a certain range 



Viceversa suppose that




whence
which is the sought-for estimate. The equivalence in (15.42) is similarly proved using (15.39).
15.4. Examples
We specialize the foregoing results for particular choices of 








where 




Examples for weak differentiability. (I)



And under the restrictions 

they are equivalent to:

But it must be observed that, though the comparison functions appearing in each summation in (15.47) form an asymptotic scale due to the easily-checked relation
the asymptotic expansions in (15.47) are, so to say, impure in so far that neither all the terms in the explicit expressions of 
Under the restrictions 

but not viceversa. The claims about (15.47) follow from the formula

which implies

under conditions (15.46). For generic values of the

(II)



(III)





(IV)




The equivalence between (15.54)2 and (15.54)3 follows from the formula

which implies

(V)




Examples for strong differentiability. (I)


Quite surprisingly we don’t have any characterization in terms of 


wherein all the terms into the summation symbol must be taken into consideration but not all the terms in the explicit expressions of 
(II)



(III)





(IV)




The equivalence between (15.62)2 and (15.63)3 follows easily from (15.55).
(V)




15.5. Estimates of the Remainders in a Case of Incomplete Expansions
To illustrate Theorems 8.3-8.4 in Part II-B we exhibit the estimates of the remainders in a case of incomplete expansions for a generalized convex function with respect to the scale (15.1)-(15.3).
Proposition 15.7. Let 

then the following asymptotic relations hold true as


consistently with Corollary 8.5 in Part II-B.
Proof. Using the expressions of the

with suitable non-zero constants

and by an easy induction the remaining estimates are proved.
16. Remarks on the Algorithms and Formal Differentiability
16.1. A Random Use of the Procedures in the Algorithms
What about applying the above algorithms to (13.1) with a random choice of the term to be factored out at each step? If one carefully checks that at each step one is dividing by a nowhere-vanishing function one may well obtain, after n steps, a factorization valid on a certain subinterval of the given interval but, in general for





and is such that all the possible Wronskians constructed with these three functions do not vanish on
Table 1. Division by the first term.
Table 2. Division by the middle term.
Table 3. Division by the last term.
And here are the 6 so-obtained factorizations arranged in the same order:
(I) 
(II) 
(III) 
all valid on


A few remarks about the factorizations of 








16.2. Some Considerations on Formal Differentiability
Let 



Then by Proposition 2.2 in Part II-A all the possible Wronskians
coinciding



where the functions on the right can be arranged in an asymptotic scale at

Examples of formal differentiability according to canonical or non-canonical factorizations. The function

admits of the expansion

with the remainder explicitly given by



“inferred from the left side of Table 1”;
and it has property I-B if
“inferred from the right side of Table 1”.
Properties II-A, II-B, III-A, III-B are similarly defined looking at Table 2 and Table 3 respectively. Elementary, though tedious, calculations show that:

Separating various cases for 



For 


which, in our case, happens iff




References
- Granata, A. (2015) Analytic Theory of Finite Asymptotic Expansions in the Real Domain. Part II-A: The Factorizational Theory for Chebyshev Asymptotic Scales. Advances in Pure Mathematics, 5, 454-480.
- Granata, A. (2015) Analytic Theory of Finite Asymptotic Expansions in the Real Domain. Part II-B: Solutions of Differential Inequalities and Asymptotic Admissibility of Standard Derivatives. Advances in Pure Mathematics, 5, 481- 502.
- Granata, A. (2015) The Factorizational Theory of Finite Asymptotic Expansions in the Real Domain: A Survey of the Main Results. Advances in Pure Mathematics, 5, 1-20. http://dx.doi.org/10.4236/apm.2015.51001
- Trench, W.F. (1974) Canonical Forms and Principal Systems for General Disconjugate Equations. Transactions of the American Mathematical Society, 189, 319-327. http://dx.doi.org/10.1090/S0002-9947-1974-0330632-X
- Levin, A.Yu. (1969) Non-Oscillation of Solutions of the Equation
. Uspekhi Matematicheskikh Nauk, 24, 43-96; Russian Mathematical Surveys, 24, 43-99. >http://html.scirp.org/file/7-5300897x429.png" class="200" />. Uspekhi Matematicheskikh Nauk, 24, 43-96; Russian Mathematical Surveys, 24, 43-99. http://dx.doi.org/10.1070/RM1969v024n02ABEH001342
- Karlin, S. (1968) Total Positivity, Vol. I. Stanford University Press, Stanford, California.
- Granata, A. (2010) The Problem of Differentiating an Asymptotic Expansion in Real Powers. Part II: Factorizational Theory. Analysis Mathematica, 36, 173-218. http://dx.doi.org/10.1007/s10476-010-0301-3
- Granata, A. (2007) Polynomial Asymptotic Expansions in the Real Domain: The Geometric, the Factorizational, and the Stabilization Approaches. Analysis Mathematica, 33, 161-198. http://dx.doi.org/10.1007/s10476-007-0301-0.












































 . Uspekhi Matematicheskikh Nauk, 24, 43-96; Russian Mathematical Surveys, 24, 43-99. >http://html.scirp.org/file/7-5300897x429.png" class="200" />. Uspekhi Matematicheskikh Nauk, 24, 43-96; Russian Mathematical Surveys, 24, 43-99.
. Uspekhi Matematicheskikh Nauk, 24, 43-96; Russian Mathematical Surveys, 24, 43-99. >http://html.scirp.org/file/7-5300897x429.png" class="200" />. Uspekhi Matematicheskikh Nauk, 24, 43-96; Russian Mathematical Surveys, 24, 43-99.