Journal of Information Security
Vol.4 No.4(2013), Article ID:37444,9 pages DOI:10.4236/jis.2013.44025
On the Security of Anonymous Authentication Protocol for Mobile Pay-TV
Faculty of Computers and Informatics, Zagazig University, Zagazig, Egypt
Email: wkhedr@zu.edu.eg
Copyright © 2013 Walid I. Khedr. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Received May 27, 2013; revised June 26, 2013; accepted July 4, 2013
Keywords: Authentication; Conditional Access Systems; Mobile Pay-TV Services; Privacy
ABSTRACT
One of the promising multimedia services is the mobile pay-TV service. Due to its wireless nature, mobile pay-TV is vulnerable to attacks especially during hand-off. In 2011, an efficient anonymous authentication protocol for mobile pay-TV is proposed. The authors claim that their scheme provides an anonymous authentication to users by preventing intruders from obtaining users’ IDs during the mutual authentication between mobile subscribers and head end systems. However, after analysis, it was found that the scheme does not provide anonymous authentication and users can be easily tracked while using their anonymous identity. The scheme is also subject to denial of service attack. In this paper the deficiencies of the original scheme are demonstrated, and then a proposed improved scheme that eliminates these deficiencies is presented.
1. Introduction
With the increased integration of pay-TV and wireless communication, multimedia pay service plays an important role in mobile broadcast TV services [1]. As these services are usually delay-sensitive due to high mobility feature and frequent handoffs, a fast and secure authentication scheme for such mobile broadcast TV services should be developed.
In order to reduce the delay introduced by the high mobility features and frequent handoffs and guarantee a secure and convenient access of services by authorized subscribers, a secure access management mechanism is required. This access management is provided by a conditional access system (CAS). A typical model of CAS consists of two parts, a head end system and numerous receivers, and the model is comprised of several important components [2], which include:
• Subscriber Authorization/Management System (SAS/ SMS):subsystems responsible for subscriber authorization and management;its works including key management, user authentication,entitlement messages delivery,subscriber information management and rights management.
• Encrypter: a component for enciphering Control Word (CW), keys, or sensitive information.
• Multiplexer (MUX): a component for multiplexing A/V, data or IP into MPEG-2 transport stream.
• Scrambler: a component for signal scrambling.
• Transmitter: a subsystem for signal transmission.
• Receiver: a subscriber device with a CAS module used for access control.
Several CASs have been proposed to guarantee a secure and convenient access of services by authorized subscribers. Many studies have classified these schemes into symmetrical key-based schemes and public keybased schemes.
Public key-based conditional access system [3-5] may realize privacy preservation and avoid communicating with a third party during the handoff process. These methods suffer the heavy computation burden. In [6], a subscriber first has to register his subscriber information with a signature to a provider by applying public key cryptosystem. When a subscriber wants to subscribe to any programs, he uses his device to send a subscription message to the provider. The provider then sends a receipt with a signature for confirming this subscription to the subscriber. However, the scheme [6] only protects the customers’ privacy, but not the provider’s [2]. In [7], an “e-ticket” scheme for the authentication of pay-TV system is proposed. The scheme employed an encrypted authentication message with a blind and anonymous signature based on RSA public key cryptosystem to do the mutual-authentication to protect the privacy for both customers and service provider. The schemes proposed in [8] and [9] are based on a public-key cryptosystem employing the technique of the multi-key RSA. While transmitting a requested TV program, the multimedia server and proxy server cooperatively encrypt the requested program without collusion attacks. In public-key cryptosystem each user possess a unique public/private key pair, so a multimedia server has to encrypt services with each user’s specific public key which makes them inefficient and not suitable for mobile pay-TV systems.
Symmetrical key-based conditional access system [10-14] suffers from its troublesome key distribution and the involvement of a third party. In [14], an efficient anonymous authentication protocol for mobile pay-TV is proposed. The authors claim that their scheme provides an anonymous authentication to users by preventing intruders from obtaining users IDs during the mutual authentication between mobile subscribers and head end systems. However, after analysis, it was found that the scheme does not provide anonymous authentication and users can be easily tracked while using their anonymous identity. The scheme also is subject to DoS attack.
In this paper an improved scheme that enhances the Chen’s scheme [14] is proposed. The deficiencies of the original scheme are demonstrated, and then a proposed improved scheme that eliminates these deficiencies is presented. The proposed scheme ensures the anonymity of the subscribers during handoffs operations, and ensures the anonymous mutual authentication between subscribers and head end systems with low computation and communication costs. Finally a mechanism that prevents denial of service attack is proposed.
The rest of this paper is organized as follows: Section 2 briefly reviews the Chen’s scheme. Section 3 presents the security analysis of Chen’s scheme. Section 4 presents the improved scheme. The security analysis and performance evaluation of the improved scheme are presented in Section 5. Finally, Section 6 concludes the paper.
2. Review of the Chen’s Scheme
The scheme proposed in [14] introduced an efficient and anonymous mutual authentication protocol that eliminates the high computational cost and prevents security attacks introduced in a previous related protocol [15]. There are four phases in Chen’s scheme, which includes initialization, issue, subscription and hand-off Phase.
2.1. Initialization Phase
This phase is invoked whenever user Ui registers to the subscribers’ database server (DBS) of HES via Subscriber Authorization System and Subscriber Management System (SAS/SMS) and the DBS saves Ui’s identity ID. Both Ui and HES uses a set-top-box (STB) as a secure channel during this phase. The following steps are performed to complete this phase [14]:
1) Ui chooses his IDi and pwi and generates a random number b for calculating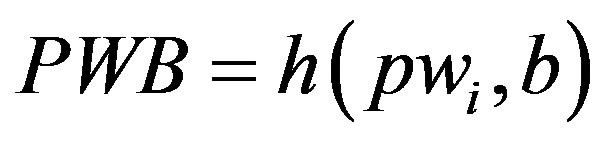 . Then, Ui submits IDi and PWB to the pay-TV system server S.
. Then, Ui submits IDi and PWB to the pay-TV system server S.
2) S checks the database whether his IDi is already in the database or not. If IDi is already in the database, S checks whether Ui performs a re-registration or not. If Ui performs a re-registration then S sets IDi’s registration number N = N + 1 and updates IDi and N in the database otherwise S suggests Ui to choose another IDi. If IDi is not in the database then S sets N = 0 and stores values of IDi and N in the database.
3) S calculates K, UD, Q and K, UD, Q and R, where:
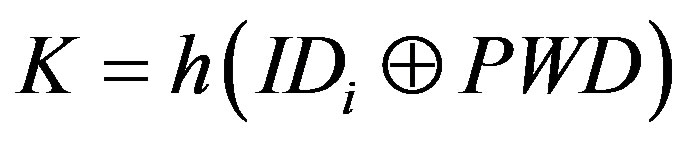 ,
,
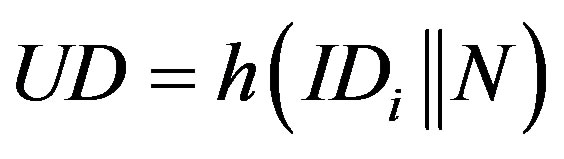 ,
,
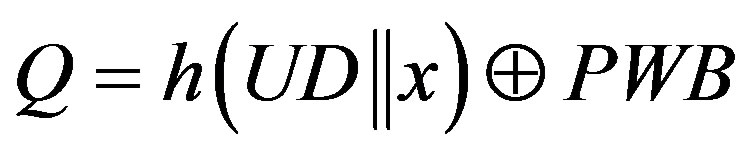 ,
,
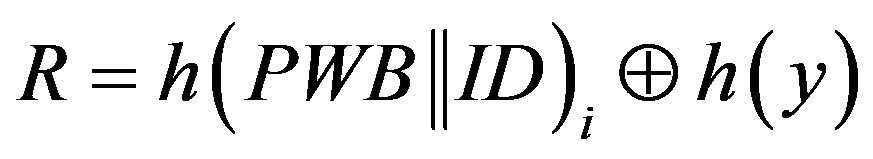 , where y is the secret key of the remote server stored in the hash function and x is the secret key of S.
, where y is the secret key of the remote server stored in the hash function and x is the secret key of S.
4) S issues a smart card containing [K, R, Q] to Ui over a secure channel.
5) Ui stores the random number b on the smart card. Such that the smart card contains [K, R, Q, b].
2.2. Issue Phase
Assume that Ui’s mobile subscriber device (MSi) asks a service Rt and the HES performs this authentication process of issue phase for Ui to obtain a right code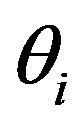 . The statements are described as follows:
. The statements are described as follows:
1) Ui enters his IDi and PWi in order to login for obtaining the service, MSi performs the following computations.
• Calculates 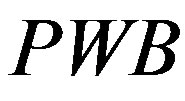 and
and 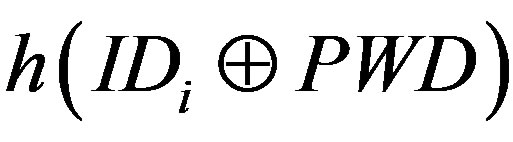 to verify whether
to verify whether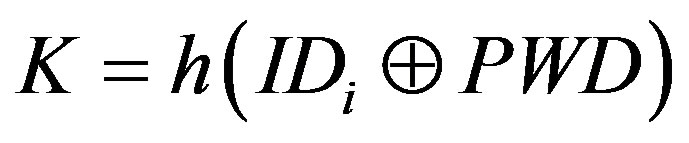 . If it does not hold, MSi terminates the request.
. If it does not hold, MSi terminates the request.
• Calculates 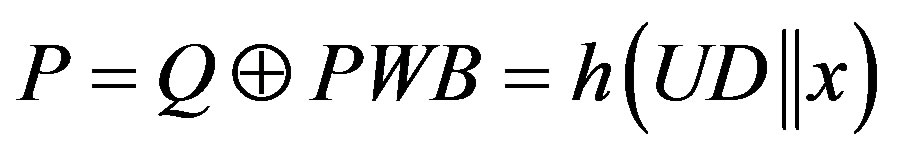 and
and 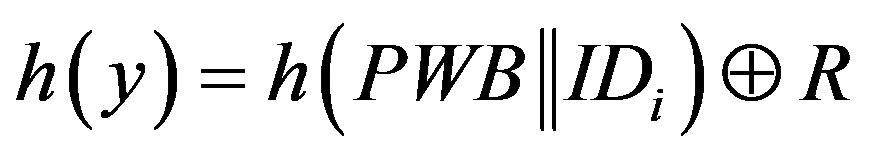
• Generates a random number ni and calculates:
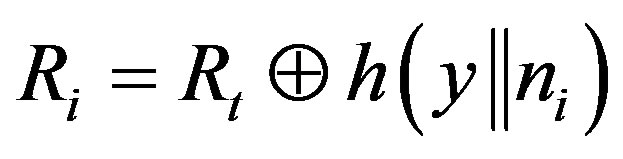 ,
, 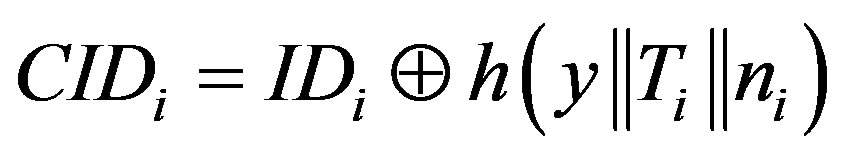
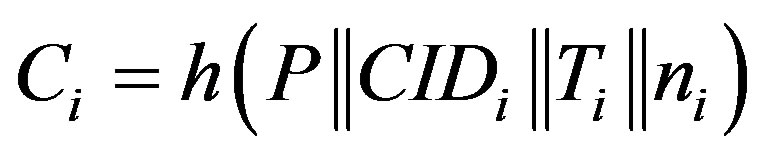 .
.
Here T1 is the current timestamp
• Sends the message 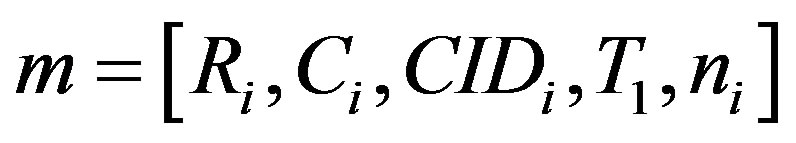 to HES.
to HES.
2) HES receives the message at the timestamp T2 and performs the following computations:
• Checks the validity of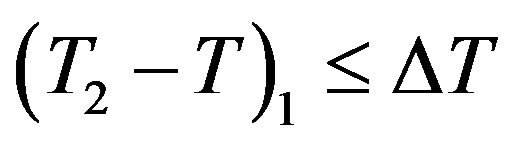 . If it does not hold, HES terminates the request.
. If it does not hold, HES terminates the request.
• Calculates 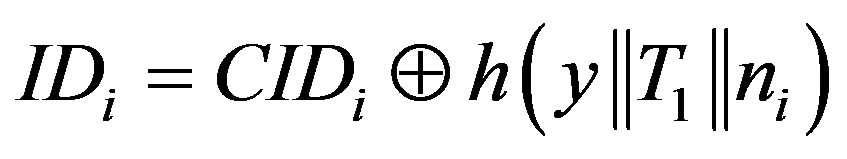 and verifies if IDi is a valid user’s identity. If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates
and verifies if IDi is a valid user’s identity. If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates
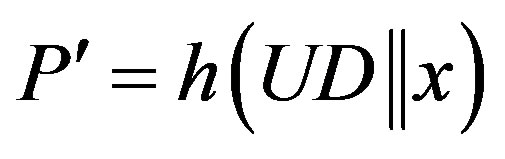 , where
, where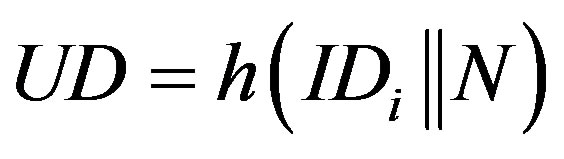 .
.
• Calculates 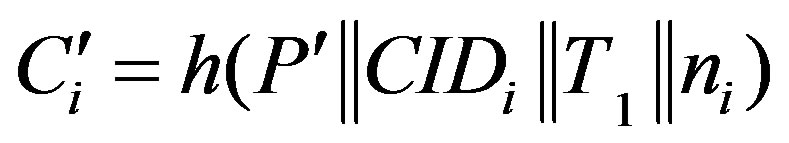 and checks whether
and checks whether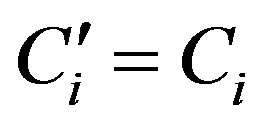 . If they are equal, HES accepts Ui’s request of authentication.
. If they are equal, HES accepts Ui’s request of authentication.
• Calculates 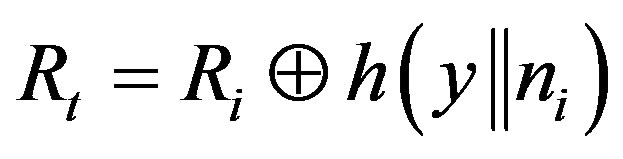
• Then, HES chooses a token 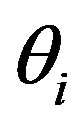 for Ui and stores it into DBS, and calculates:
for Ui and stores it into DBS, and calculates:
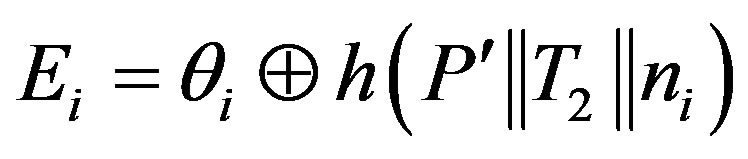
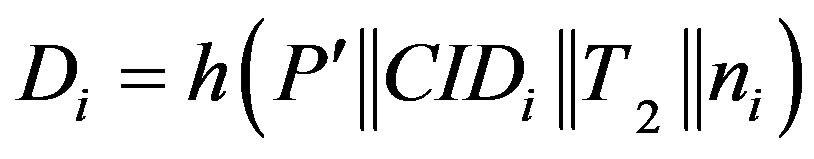 .
.
• Broadcasts the mutual authentication message
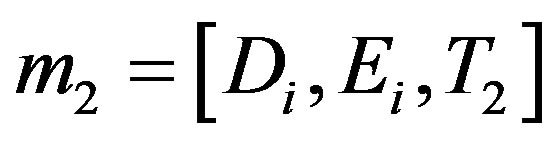 .
.
3) After receiving message m2 at the time T3, Ui checks the validity of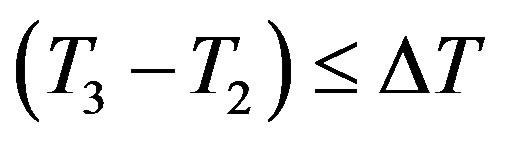 . If it does not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
. If it does not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
• Calculates 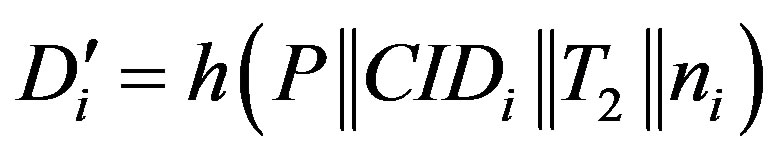 and checks whether
and checks whether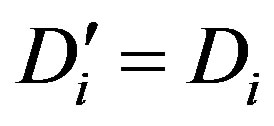 . If they are equal, Ui accepts HES’s request of mutual authentication.
. If they are equal, Ui accepts HES’s request of mutual authentication.
• Ui calculates the certified token
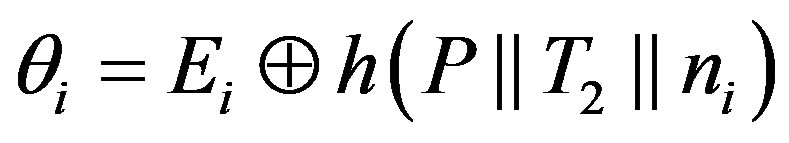 as the authentication session key to get service of the pay-TV system.
as the authentication session key to get service of the pay-TV system.
2.3. Subscription Phase
After obtaining a right code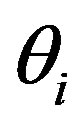 , Ui’s MSi asks a service Rt using
, Ui’s MSi asks a service Rt using 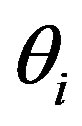 and the HES performs this authentication process. The statements are described as follows:
and the HES performs this authentication process. The statements are described as follows:
1) Ui entries his IDi and PWi in order to login for obtaining the service, MSi performs the following computations.
• Calculates 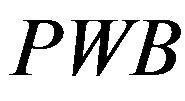 and
and 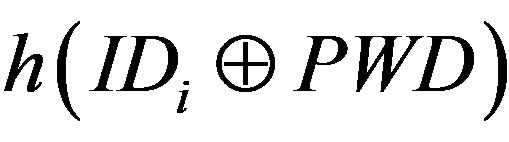 to verify whether
to verify whether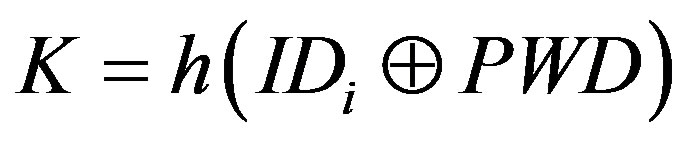 . If it does not hold, MSi terminates the request.
. If it does not hold, MSi terminates the request.
• Calculates 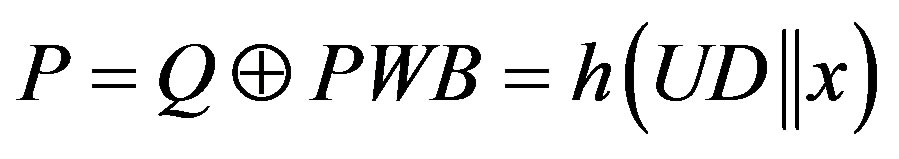 and
and
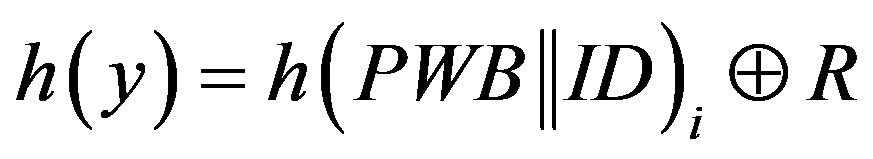 .
.
• Generates a random number ni and calculates:
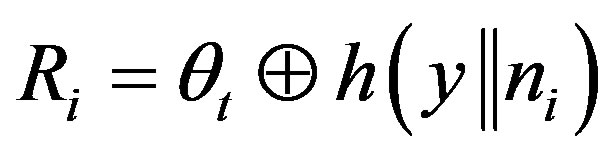 ,
, 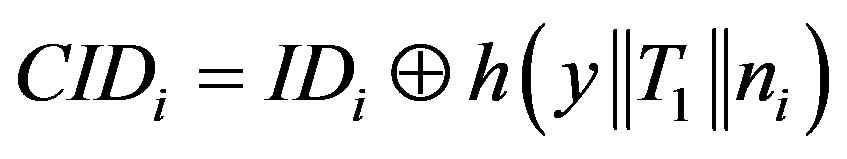
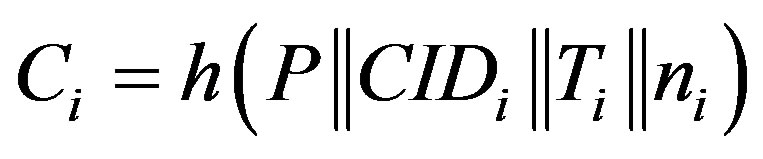 .
.
Here T1 is the current timestamp
• Sends the message 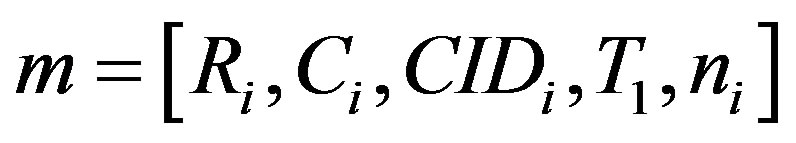 to HES.
to HES.
2) HES receives the message at the timestamp T2 and performs the following computations:
• Checks the validity of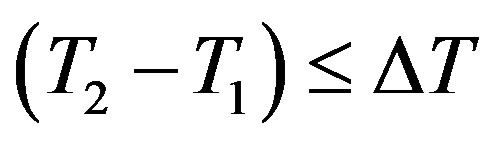 . If it does not hold, HES terminates the request.
. If it does not hold, HES terminates the request.
• Calculates 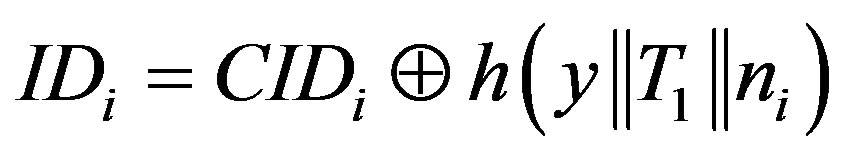 and verifies if IDi is a valid user’s identity. If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates
and verifies if IDi is a valid user’s identity. If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates
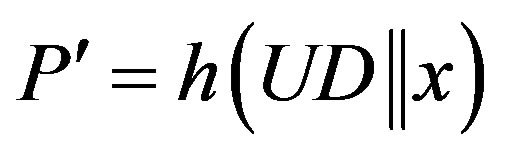 , where
, where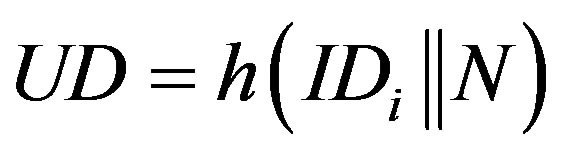 .
.
• Calculates 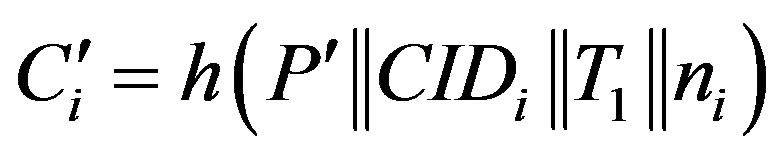 and checks whether
and checks whether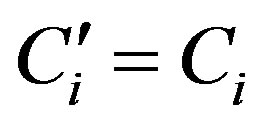 . If they are equal, HES accepts Ui’s request of authentication.
. If they are equal, HES accepts Ui’s request of authentication.
• Calculates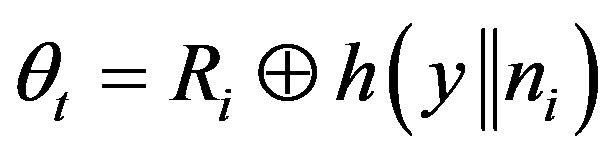 .
.
• Then, HES chooses a token 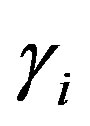 for Ui and calculates
for Ui and calculates
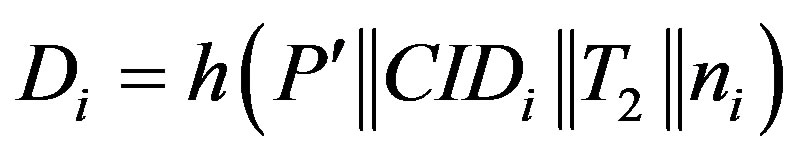 and
and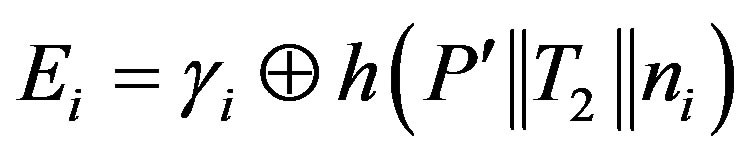 .
.
• Broadcasts the mutual authentication message
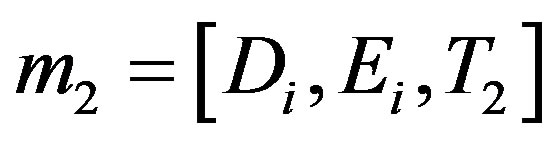 .
.
3) After receiving message m2 at the time T3, Ui checks the validity of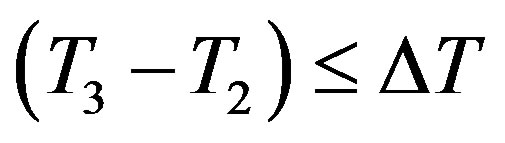 . If it does not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
. If it does not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
• Calculates 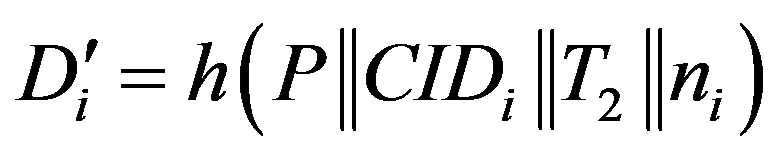 and checks whether
and checks whether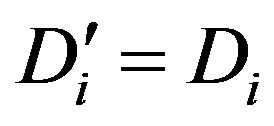 . If they are equal, Ui accepts HES’s request of mutual authentication.
. If they are equal, Ui accepts HES’s request of mutual authentication.
• Ui calculates the certified token
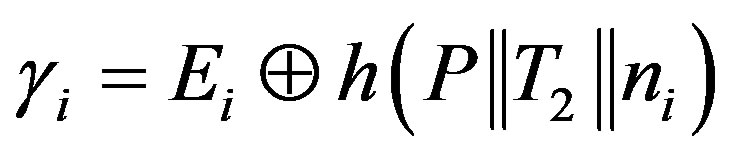 as the authentication session key to get service of the pay-TV system.
as the authentication session key to get service of the pay-TV system.
2.4. Hand-Off Phase
When MSi moves to a new coverage area that older HES cannot support such that a hand-off occurs, MSi needs to performer-authentication without re-login. The statements are described as follows:
1) MSi performs the following computations:
• Generates a random number ni and calculates:
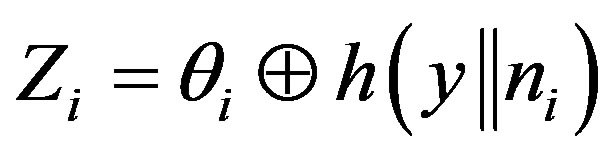 ,
, 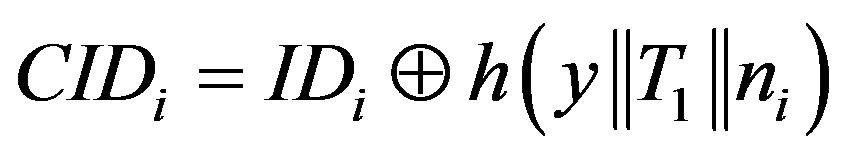
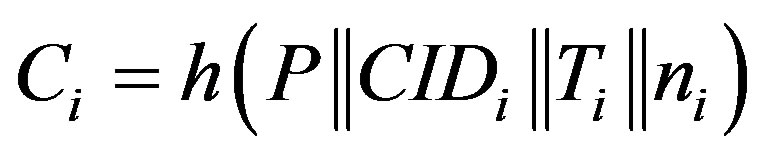 .
.
Here T1 is the current timestamp
• Sends the message 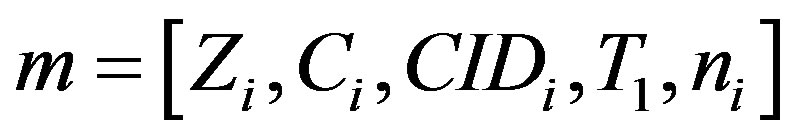 to HES.
to HES.
2) HES receives the message at the timestamp T2 and performs the following computations:
• Checks the validity of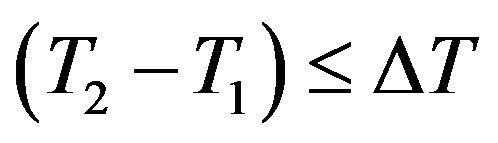 . If it does not hold, HES terminates the request.
. If it does not hold, HES terminates the request.
• Calculates 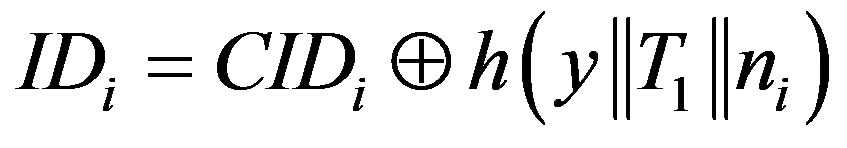 and verifies if IDi is a valid user’s identity. If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates
and verifies if IDi is a valid user’s identity. If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates
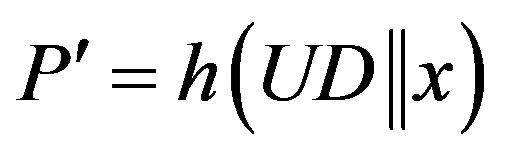 , where
, where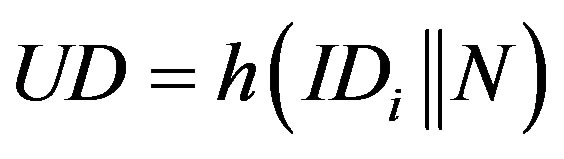 .
.
• Calculates 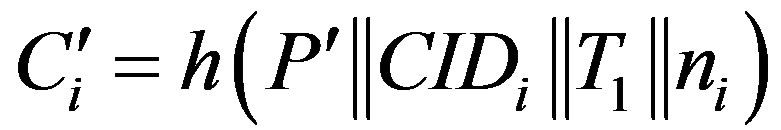 and checks whether
and checks whether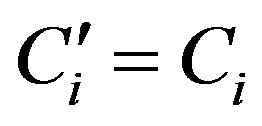 . If they are equal, HES accepts Ui’s request of authentication.
. If they are equal, HES accepts Ui’s request of authentication.
• Calculates 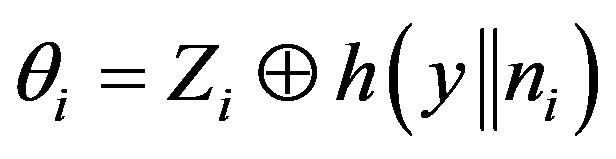
• Then, HES chooses a token 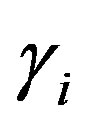 for Ui and calculates
for Ui and calculates
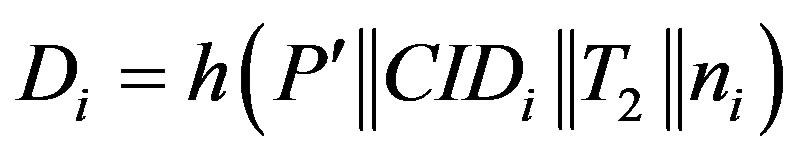 and
and 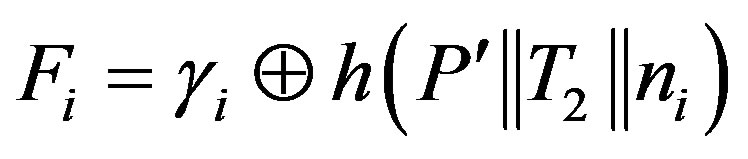
• Broadcasts the mutual authentication message
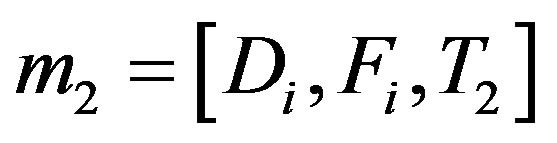
3) After receiving message m2 at the time T3, Ui checks the validity of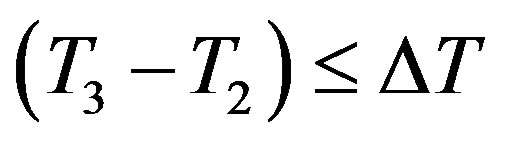 . If it does not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
. If it does not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
• Calculates 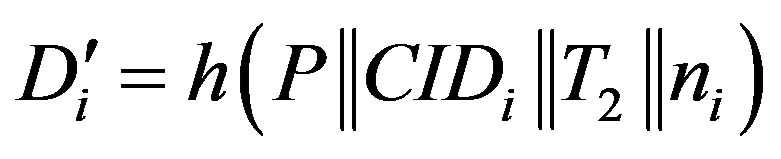 and checks whether
and checks whether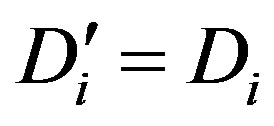 . If they are equal, Ui accepts HES’s request of mutual authentication.
. If they are equal, Ui accepts HES’s request of mutual authentication.
• Ui calculates the certified token
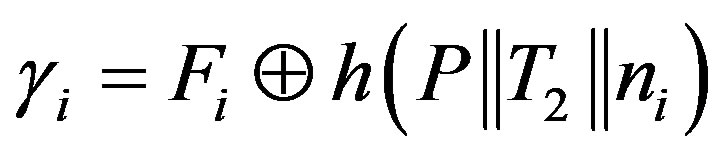 to obtain new HES’s service.
to obtain new HES’s service.
3. Security Analysis of Chen’s Scheme
In [14] the authors claim several security properties such as anonymous service, mutual authentication, resisting replay attacks, resisting man-in-the-middle-attack, and forgery difficulty. However, in this section, it is shown that Chen’s scheme vulnerable to man-in-the-middleattack which leads to DoS attack. It is al so found that the scheme does not provide anonymous service. The aforementioned weaknesses are presented in detail as follows.
3.1. Corrections to Chen’s Scheme
Before we present the weakness of Chen’s scheme, there are some mistakes in the scheme that should be corrected. In step 3 of the initialization phase (Section 2.1), the system server S calculates R using the following equation:
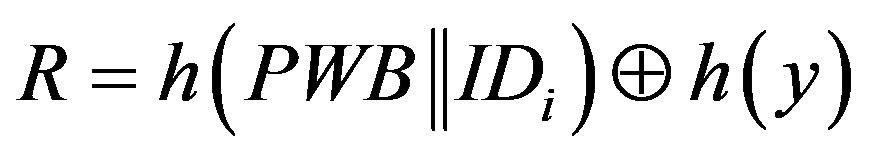 (1)
(1)
Here, y is a secret key of the remote server S which is stored in the hash function and known only to S.
In step 1 of the issue phase (Section 2.2), the mobile subscriber MS extracts 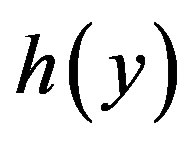 from R by computing
from R by computing
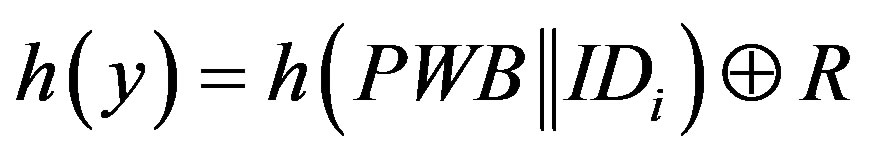 and use it to compute
and use it to compute 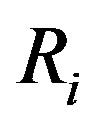
and 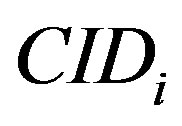 as follows:
as follows:
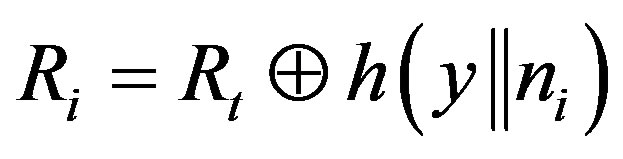 (2)
(2)
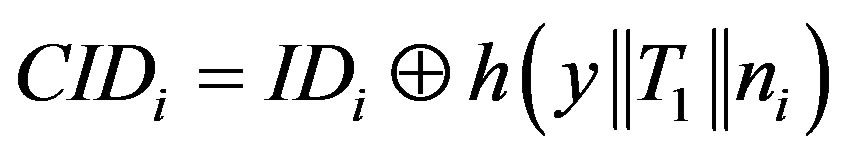 (3)
(3)
As shown in Equations (2) and (3), the authors use
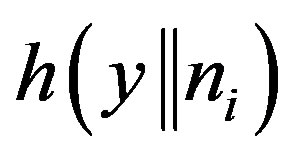 and
and 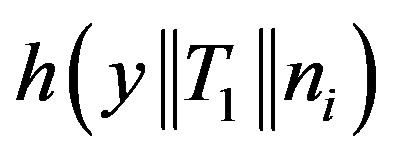 to compute
to compute 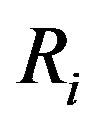 and
and 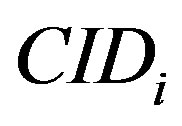
respectively, which is not possible; since the MSi does not know the secret key y to be able to compute
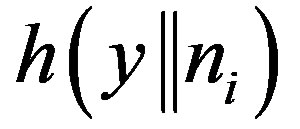 and
and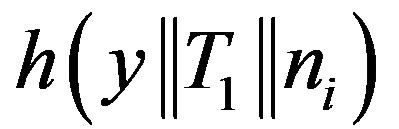 . So, the MS could not compute
. So, the MS could not compute 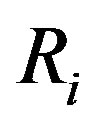 and
and 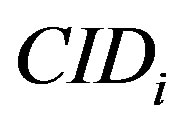 as
as 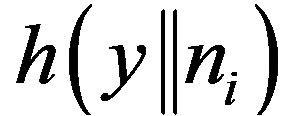 and
and 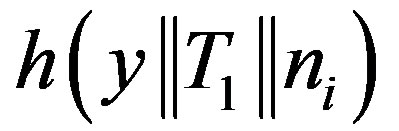 are one way hash functions i.e. it is not possible to extract y from both
are one way hash functions i.e. it is not possible to extract y from both 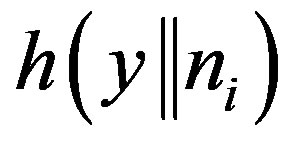 and
and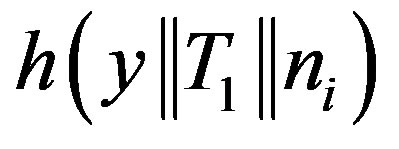 . The same mistake is found in step 1 of the subscription phase (Section 2.3) and step 1 of the hand-off phase (Section 2.4) when computing (
. The same mistake is found in step 1 of the subscription phase (Section 2.3) and step 1 of the hand-off phase (Section 2.4) when computing ( ,
, ) and (
) and (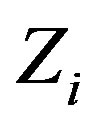 ,
,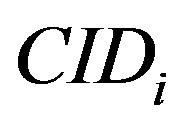 ) respectively. To correct this mistake, the MS should replace y by
) respectively. To correct this mistake, the MS should replace y by 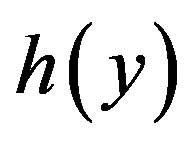 in Equations (2) and (3). This mistake can also be corrected by just replacing
in Equations (2) and (3). This mistake can also be corrected by just replacing 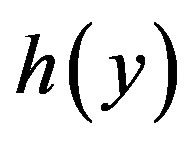 by y in Equation in the initialization phase i.e.
by y in Equation in the initialization phase i.e.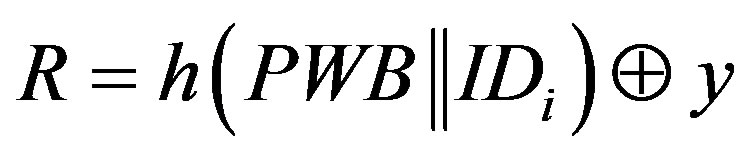 . We chose the second option.
. We chose the second option.
3.2. Attack on Anonymous Service
The Chen’s scheme is subject to MS tracking attack. This attack can be performed as follows:
1) An attacker  registers to the subscribers’ database server (DBS) like any other user and chooses his
registers to the subscribers’ database server (DBS) like any other user and chooses his 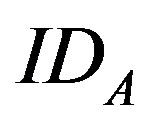 and
and 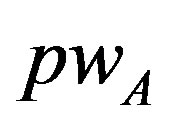 and generates a random number b for calculating
and generates a random number b for calculating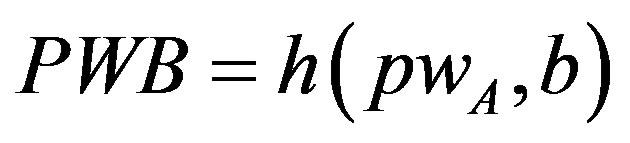 . Then, A submits
. Then, A submits 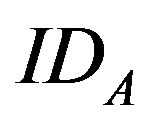 and PWB to the pay-TV system server S.
and PWB to the pay-TV system server S.
2) S calculates:
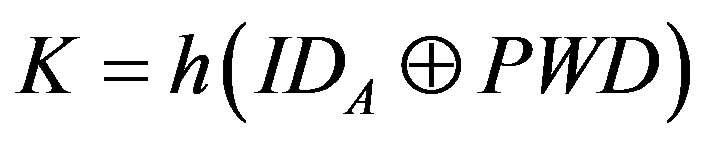
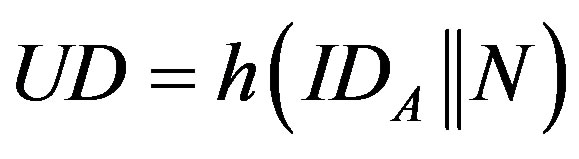
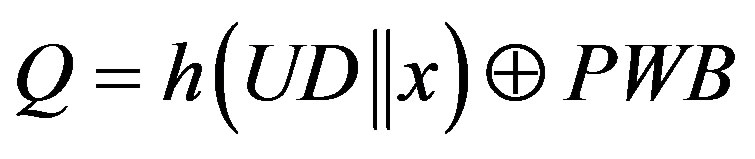
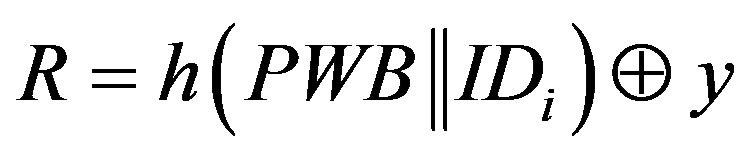 .
.
S issues a smart card containing [K, R, Q] to A over a secure channel.
3) The attacker A reads R from its smart card and compute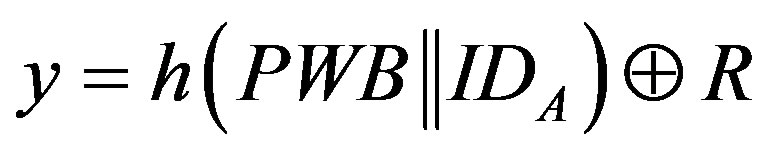 .
.
Note that based on the corrections presented in section 3.1, 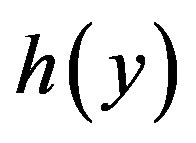 is replaced by
is replaced by 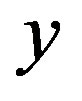 in the step 2. Using the computed
in the step 2. Using the computed 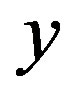 the attacker A can perform MS tracing attack during issue phase, subscription or hand-off phases as follows:
the attacker A can perform MS tracing attack during issue phase, subscription or hand-off phases as follows:
1) The attacker A intercept message m during any of the three phases and extracts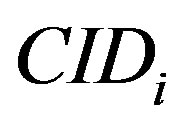 ,
, 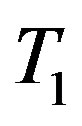 and
and 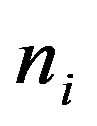 from m. Using these three values and the computed
from m. Using these three values and the computed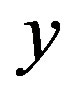 , the attacker can compute the MS’ ID (
, the attacker can compute the MS’ ID ( ) as follows:
) as follows:
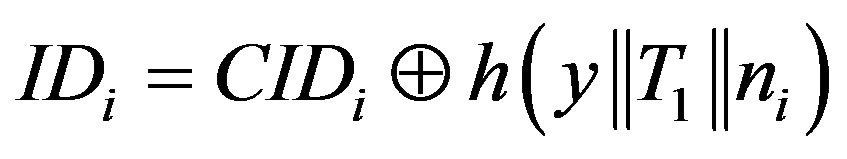 (4)
(4)
This allows the attacker to track MSi; since  is a fixed value for each user Ui.
is a fixed value for each user Ui.
2) The attacker A can also know the service 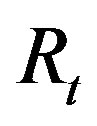 that the MSi asked from HES by intercepting message m during the issue phase and extracting
that the MSi asked from HES by intercepting message m during the issue phase and extracting 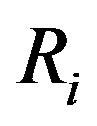 and
and 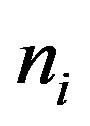 from m. Using these two values and the computed
from m. Using these two values and the computed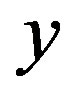 , the attacker can compute
, the attacker can compute 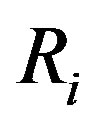 as follows:
as follows:
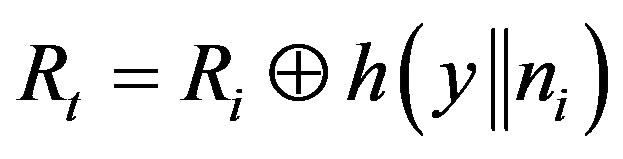 (5)
(5)
3) The attacker A can also know the right code 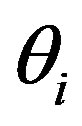 that used by MSi to access service
that used by MSi to access service 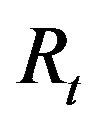 by intercepting message m during the subscription or the hand-off phases and extracting
by intercepting message m during the subscription or the hand-off phases and extracting 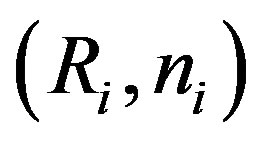 or
or 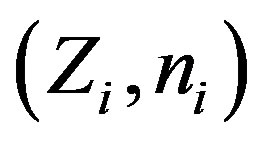 respectively from m. Using either of these two values and the computed
respectively from m. Using either of these two values and the computed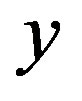 , the attacker can compute
, the attacker can compute 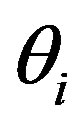 as follows:
as follows:
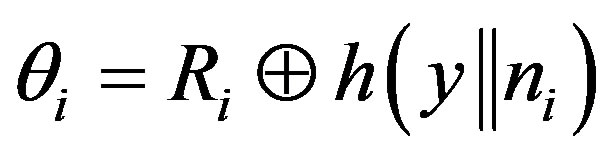 (6)
(6)
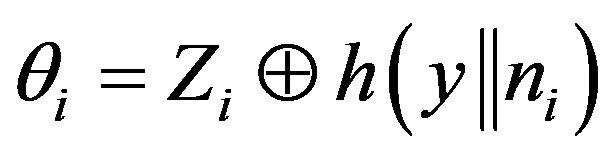 (7)
(7)
3.3. Denial of Service Attack
The scheme is subject to denial of service attack. This attack can be performed through two methods. The first method can be performed during the subscription and hand-off phases by applying man-in-the-middle attack as follows:
1) The attacker A intercept message m2 during any of the two phases and extract:
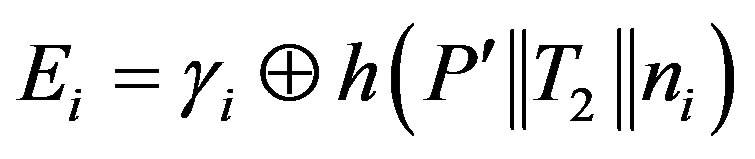 or
or
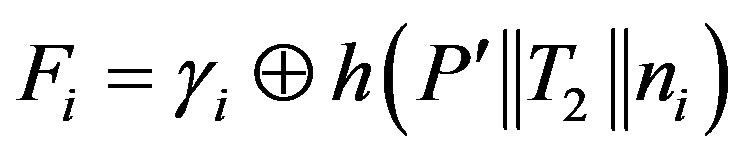 respectively.
respectively.
2) The attacker generates a random session key 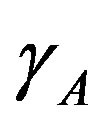 and computes:
and computes:
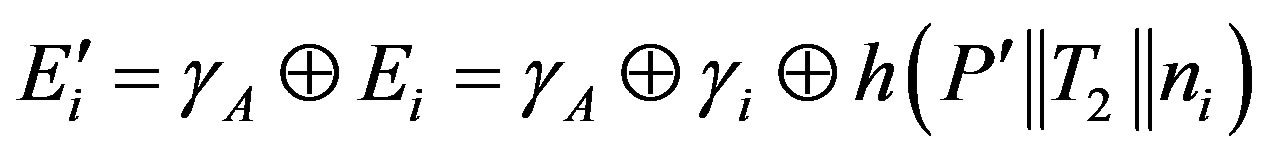
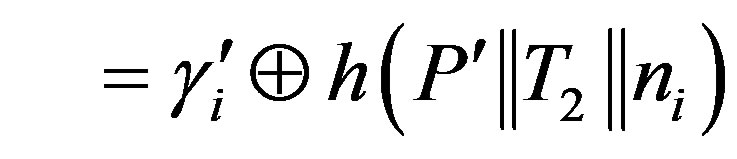 or
or
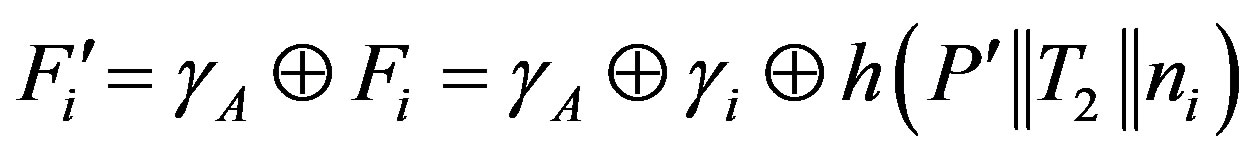
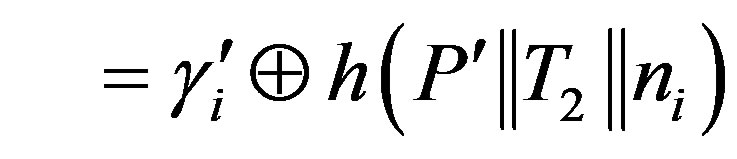
3) After receiving message m2, Ui calculates the session key:
• 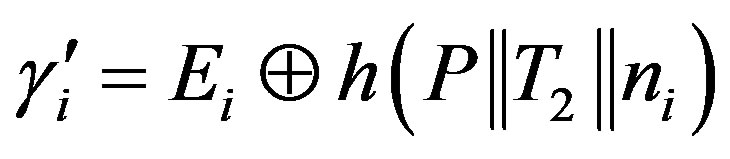 or
or
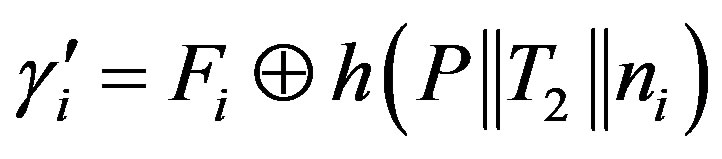
This results in Ui and HES using different session keys (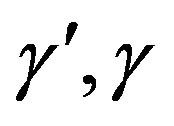 respectively) which prevent Ui from getting the service of the pay-TV system.
respectively) which prevent Ui from getting the service of the pay-TV system.
The second method can be performed during the handoff phase as follows:
1) The attacker uses a rogue HES to transmit messages using a high signal strength in order to force MSi to discard the signal sent by the legitimate HES and roam with the rogue HES.
2) When MSi roam with the rogue HES, it needs to perform re-authentication without re-login by sending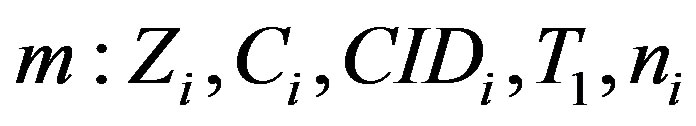 , where:
, where:
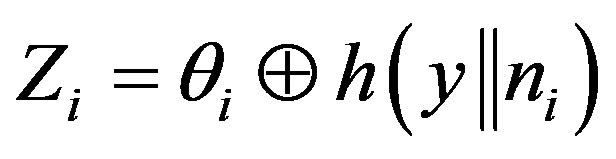
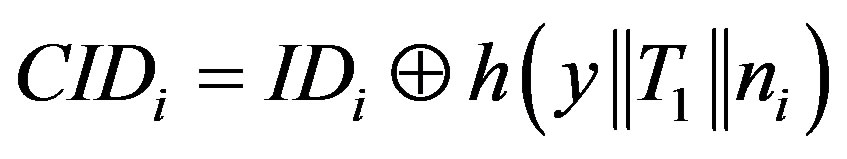
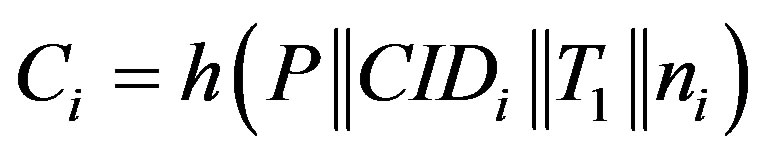 .
.
3) The rogue HES receives the message and immediately reply with message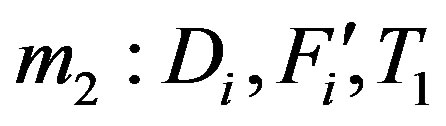 , where
, where
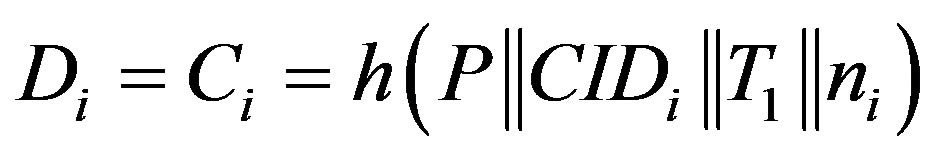 and
and 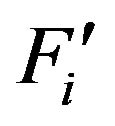 is a random value generated by the rogue HES.
is a random value generated by the rogue HES.
4) After receiving message m2 at the time T3, Ui checks the validity of 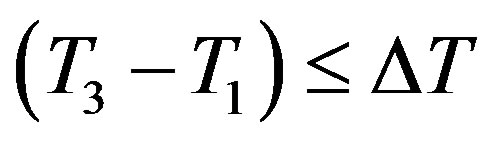 which should hold; since
which should hold; since 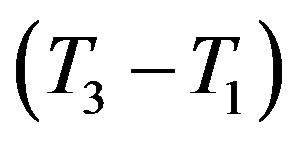 should equal to the round trip time (RTT) between Ui and the rogue HES. Note that
should equal to the round trip time (RTT) between Ui and the rogue HES. Note that 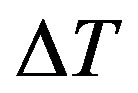 should be less than or equal to 200 milliseconds as stated in [16]. It is clear that the RTT between Ui and the rogue HES is less than 200 milliseconds; since they are within the transmission range of each other.
should be less than or equal to 200 milliseconds as stated in [16]. It is clear that the RTT between Ui and the rogue HES is less than 200 milliseconds; since they are within the transmission range of each other.
5) Ui calculates 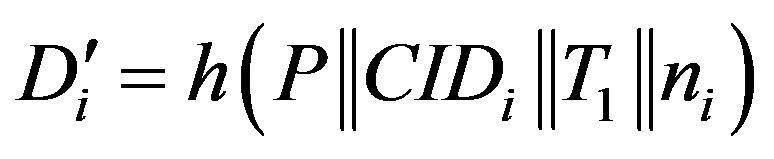 and checks whether
and checks whether 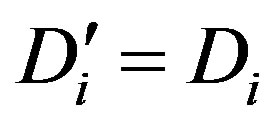 and accepts the rogue HES’s request of mutual authentication.
and accepts the rogue HES’s request of mutual authentication.
6) Ui calculates the false authentication session key
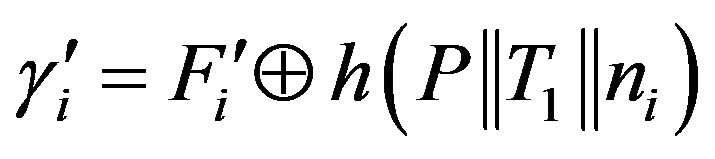 , which prevents Ui from getting the service of the pay-TV system.
, which prevents Ui from getting the service of the pay-TV system.
4. The Improved Scheme
To withstand the above attacks, we propose an improved scheme based on the original Chen’s scheme [14] with lightweight modifications. The improved scheme introduces few modifications to the four phases as follows.
4.1. Initialization Phase
As assumed in [14], both S and its HESs share a secret key x. Both Ui and HES use a set-top-box (STB) as a secure channel during this phase. The following steps are performed to complete this phase:
1) Ui chooses his IDi and pwi and generates a random number b for calculating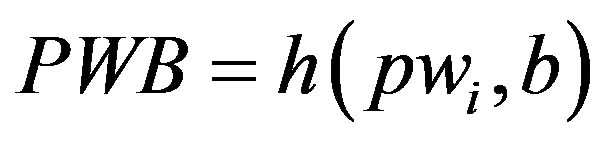 . Then, Ui submits IDi and PWB to the pay-TV system server S.
. Then, Ui submits IDi and PWB to the pay-TV system server S.
2) S checks the database whether his IDi is already in the database or not. If IDi is already in the database, S checks whether Ui performs a re-registration or not. If Ui performs a reregistration then S sets IDi’s registration number N = N + 1 and updates IDi and N in the database otherwise S suggests Ui to choose another IDi. If IDi is not in the database then S sets N = 0 and stores values of IDi and N in the database.
3) S calculates the following values:
• 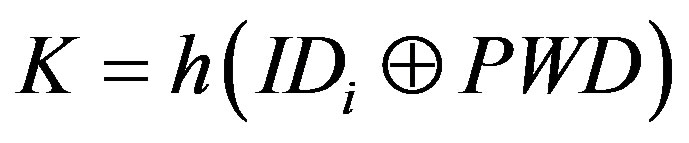
• A user authentication key for each user
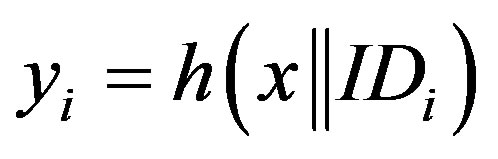 , where x is the secret key of S.
, where x is the secret key of S.
• A new permutation of the MSi’s ID
(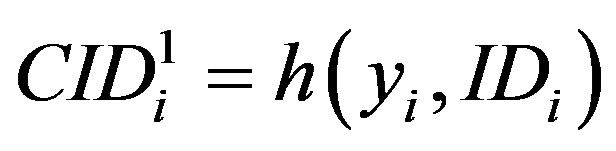 ) to be used by MSi’s as a new ID during the next communication with the HES.
) to be used by MSi’s as a new ID during the next communication with the HES.
• 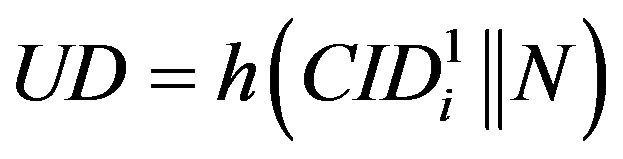 ,
, 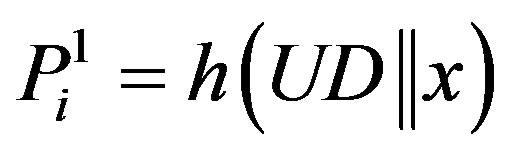 and
and 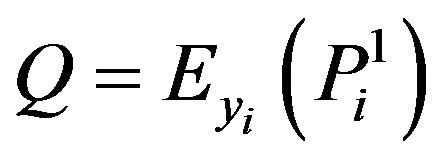
• 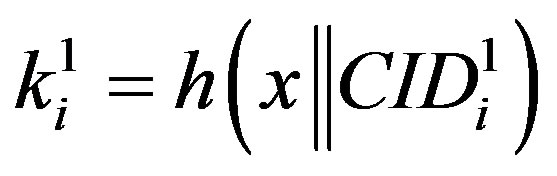 ,
, 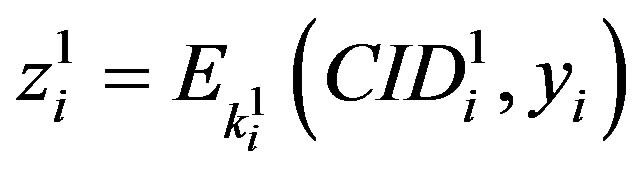 and
and 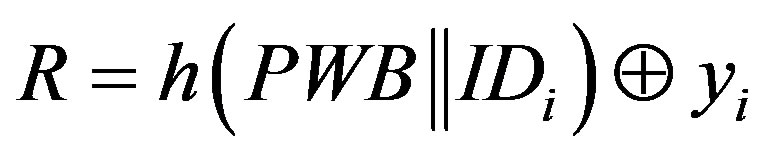
4) S sends 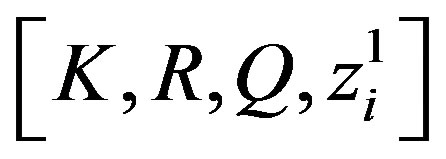 to Ui over the secure channel.
to Ui over the secure channel.
5) Ui computes 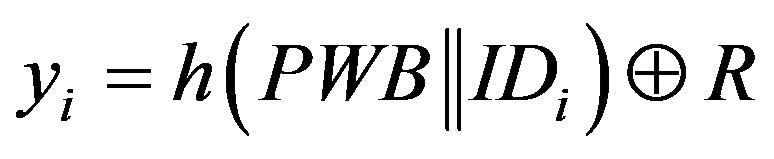 and stores
and stores
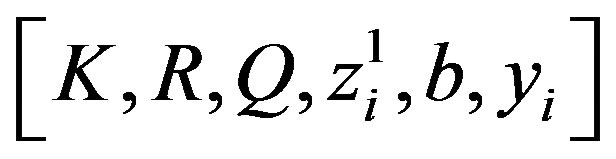 .
.
The user Ui uses 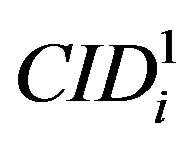 to identify itself to the next HES during the issue phase, the subscription phase or the hand-off phase. This new ID should be known to the next HES to be able to authenticate Ui. So, the current HES encrypt the new ID (
to identify itself to the next HES during the issue phase, the subscription phase or the hand-off phase. This new ID should be known to the next HES to be able to authenticate Ui. So, the current HES encrypt the new ID (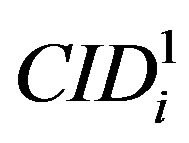 ) along with user authentication key
) along with user authentication key 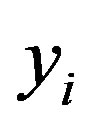 and send it to Ui which sends it to the next HES in the next phase. Note that only HESs can decrypt
and send it to Ui which sends it to the next HES in the next phase. Note that only HESs can decrypt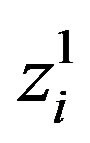 ; since the decryption key
; since the decryption key 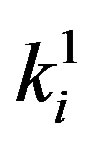 is generated using the secret key x which is only known to the server S and its HESs.
is generated using the secret key x which is only known to the server S and its HESs.
4.2. Issue Phase
Assume that Ui’s mobile subscriber device (MSi) asks a service Rt and the HES performs this authentication process of issue phase for Ui to obtain a right code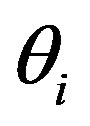 . The statements are described as follows:
. The statements are described as follows:
1) Ui enters his IDi and PWi in order to login for obtaining the service, MSi performs the following computations.
• Calculates 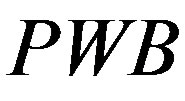 and
and 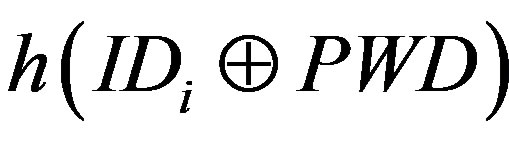 to verify whether
to verify whether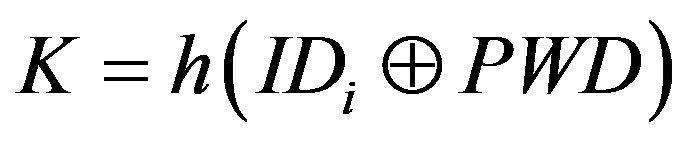 . If it does not hold, MSi terminates the request.
. If it does not hold, MSi terminates the request.
• Calculates 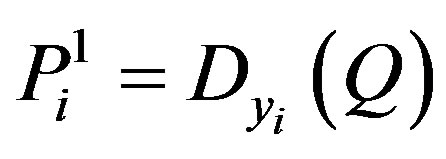
• Generates a random number ni and calculates:
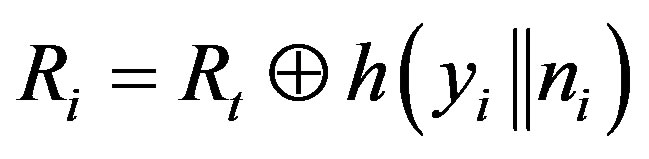
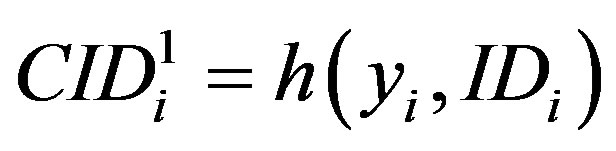
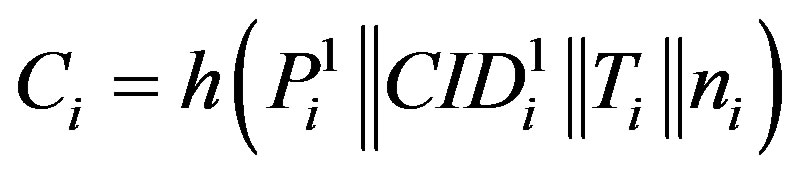 .
.
Here T1 is the current timestamp
• Sends the message m to HES:
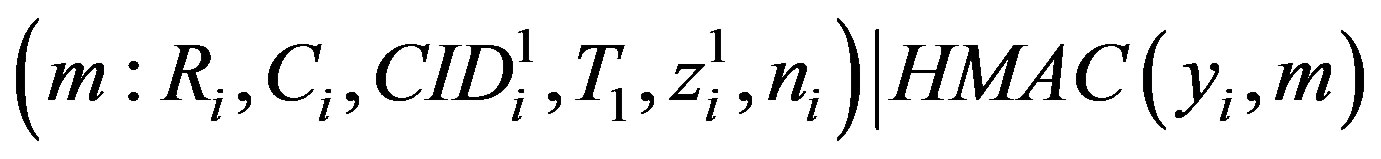
Here 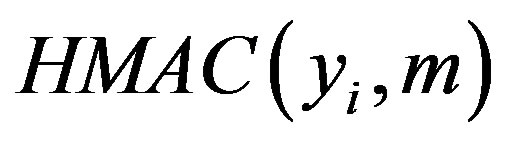 is the HMAC of the message m using the key yi
is the HMAC of the message m using the key yi
2) HES receives the message at the timestamp T2 and performs the following computations:
• Checks the validity of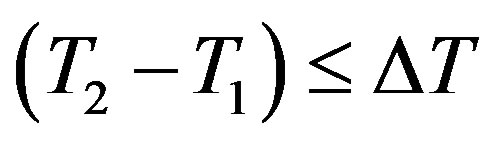 . If it does not hold, HES terminates the request.
. If it does not hold, HES terminates the request.
• To validate the 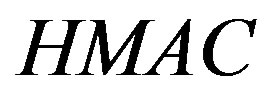 and the new ID (
and the new ID (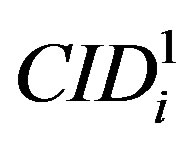 )HES calculates
)HES calculates 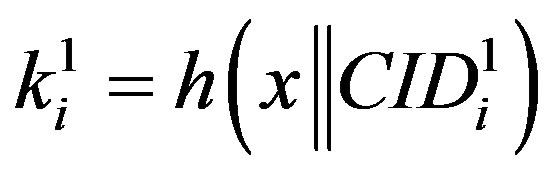 and
and
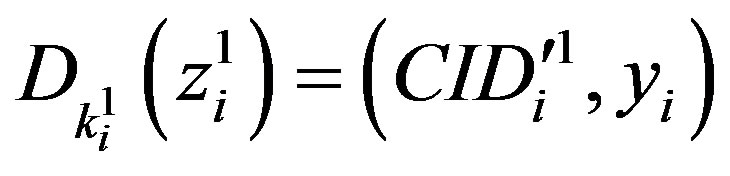 to get the user authentication key yi .
to get the user authentication key yi .
• Uses 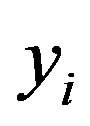 to validate
to validate 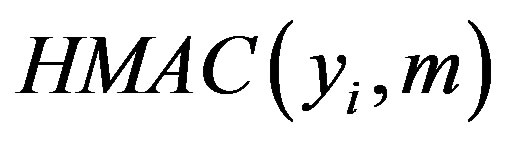 then checks whether the computed
then checks whether the computed 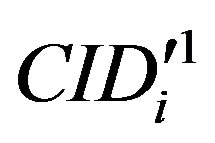 equal to
equal to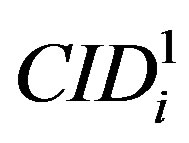 . If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates
. If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates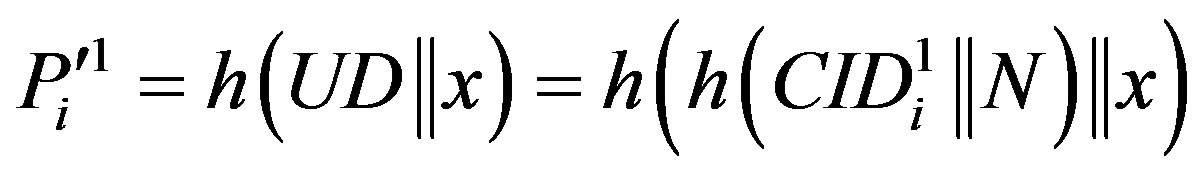 .
.
• Calculates 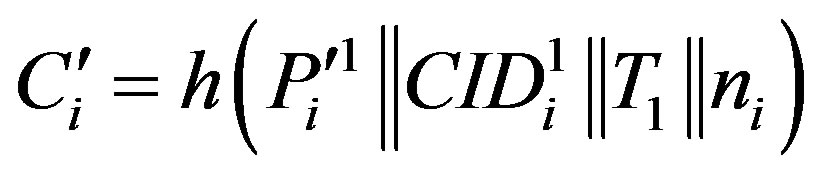 and checks whether
and checks whether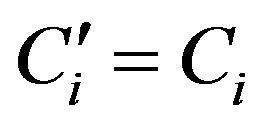 . If they are equal, HES accepts Ui’s request of authentication.
. If they are equal, HES accepts Ui’s request of authentication.
• Calculates 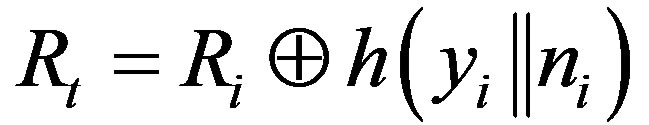
• Then, HES chooses a token 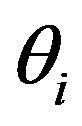 for Ui and stores it into DBS, and calculates:
for Ui and stores it into DBS, and calculates:
• 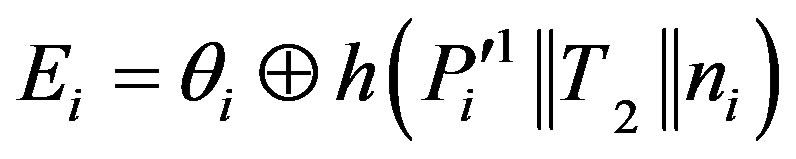
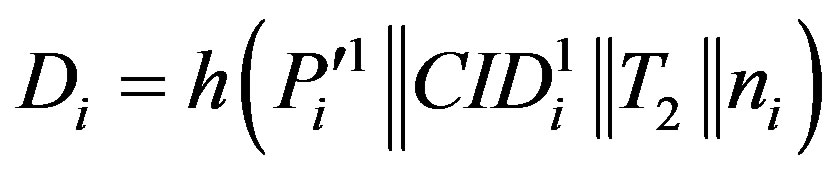
• Computes a new permutation of the MSi’s ID
(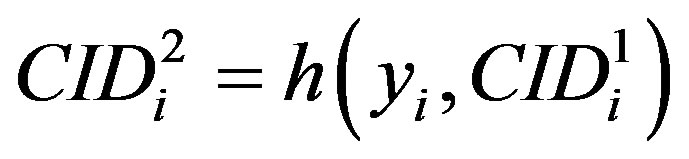 ) to be used by MSi’s as a new ID during the next communication with the HES.
) to be used by MSi’s as a new ID during the next communication with the HES.
• Compute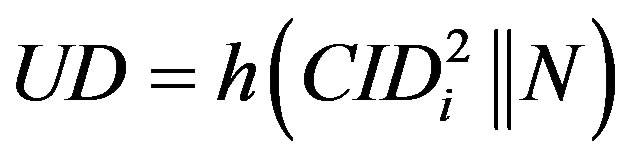 ,
,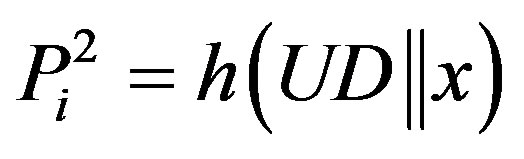 and
and
 .
.
• 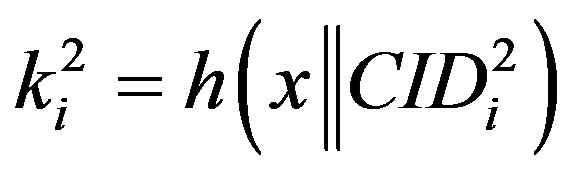 ,
,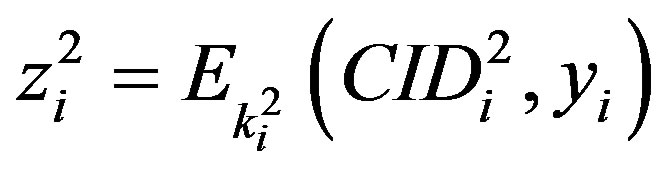 .
.
• Broadcasts the mutual authentication message
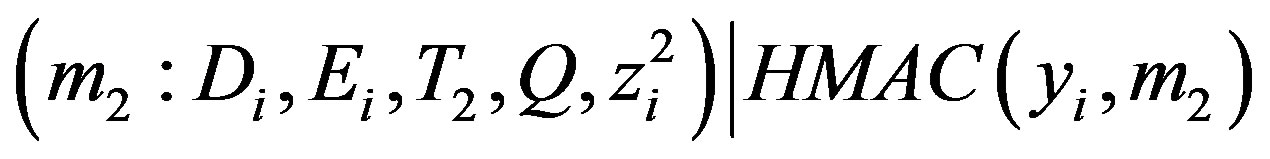 .
.
3) After receiving message m2 at the time T3, Ui checks the validity of 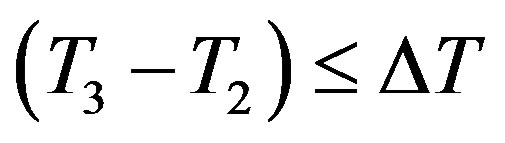 and uses yi to validate the HMAC. If they do not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
and uses yi to validate the HMAC. If they do not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
• Calculates 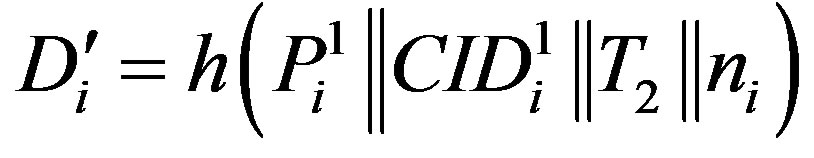 and checks whether
and checks whether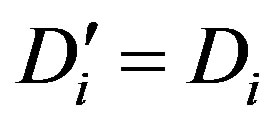 . If they are equal, Ui accepts HES’s request of mutual authentication.
. If they are equal, Ui accepts HES’s request of mutual authentication.
• Ui calculates the certified token
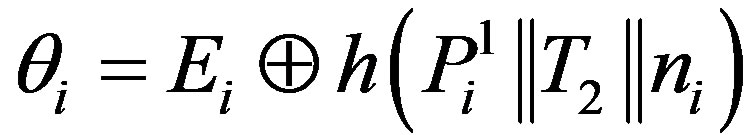 as the authentication session key to get service of the pay-TV system.
as the authentication session key to get service of the pay-TV system.
• Ui stores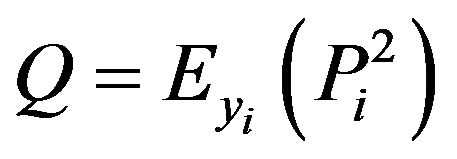 ,
, 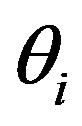 ,
, 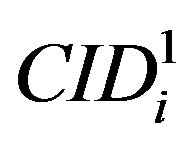 and
and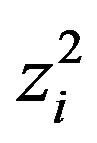 .
.
4.3. Subscription Phase
After obtaining a right code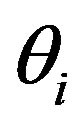 , Ui’s MSi asks a service Rt using
, Ui’s MSi asks a service Rt using 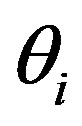 and the HES performs this authentication process. The statements are described as follows:
and the HES performs this authentication process. The statements are described as follows:
1) Ui entries his IDi and PWi in order to login for obtaining the service, MSi performs the following computations.
• Calculates 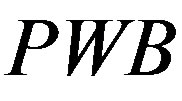 and
and 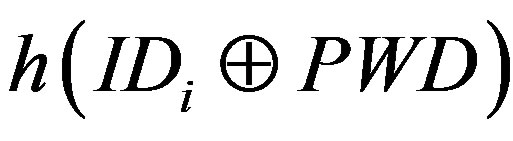 to verify whether
to verify whether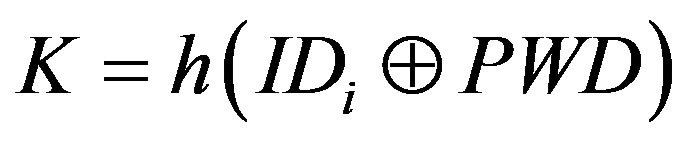 . If it does not hold, MSi terminates the request.
. If it does not hold, MSi terminates the request.
• Calculates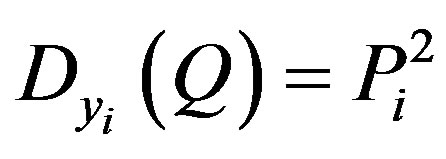 .
.
• Generates a random number ni and calculates
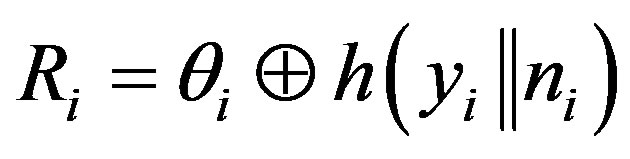 ,
, 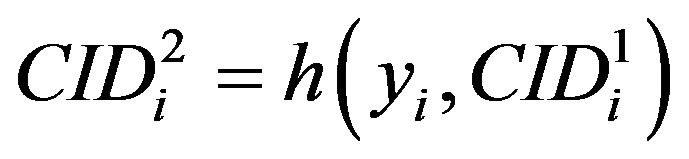 and
and
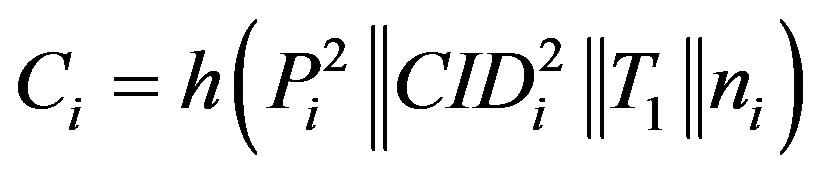 . Here T1 is the current timestamp.
. Here T1 is the current timestamp.
• Sends the message m to HES:
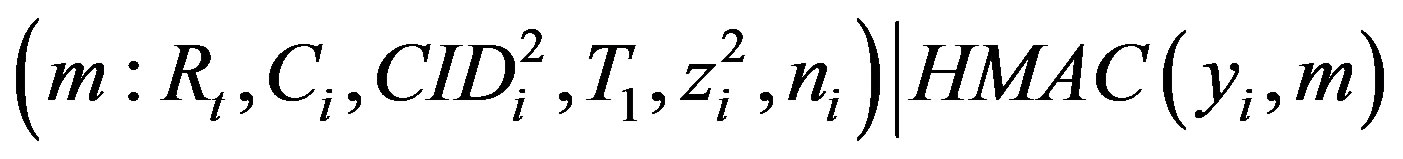 .
.
2) HES receives the message at the timestamp T2 and performs the following computations:
• Checks the validity of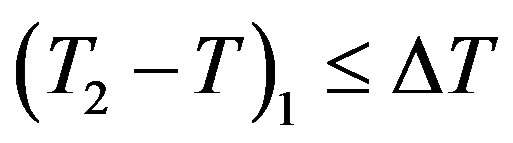 . If it does not hold, HES terminates the request.
. If it does not hold, HES terminates the request.
• To validate the 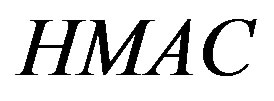 and the new ID (
and the new ID (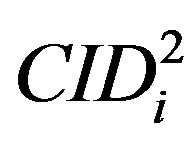 ), HES calculates
), HES calculates 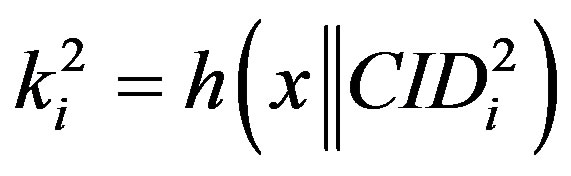 and
and
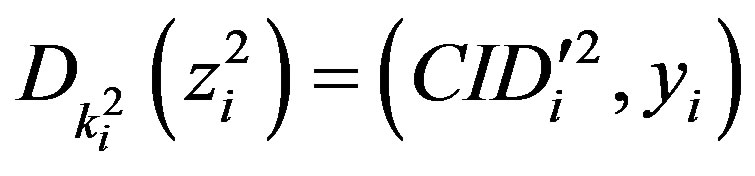 to get the user authentication key yi.
to get the user authentication key yi.
• Uses 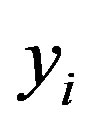 to validate
to validate 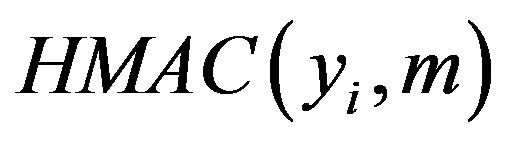 then checks whether the computed
then checks whether the computed 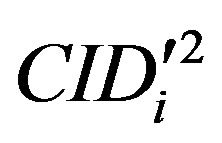 equal to
equal to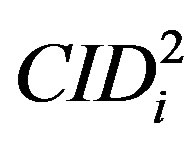 . If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates
. If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates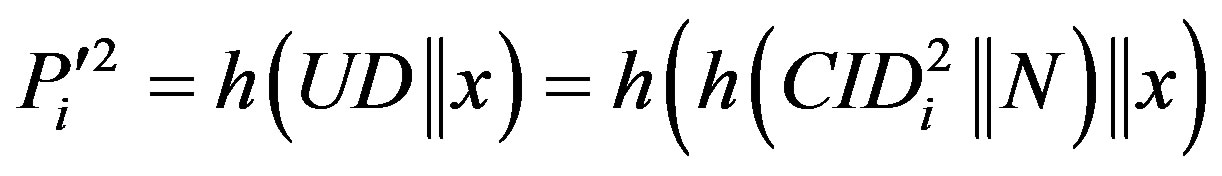 .
.
• Calculates 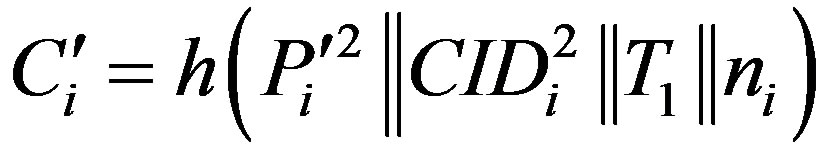 and checks whether
and checks whether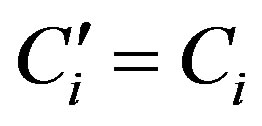 . If they are equal, HES accepts Ui’s request of authentication.
. If they are equal, HES accepts Ui’s request of authentication.
• Calculates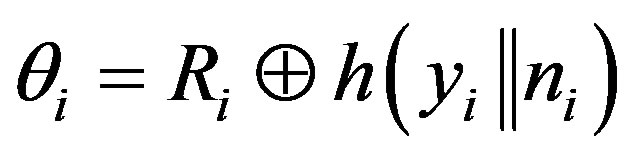 .
.
• Then, HES chooses a token 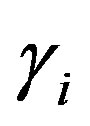 for Ui and calculates
for Ui and calculates 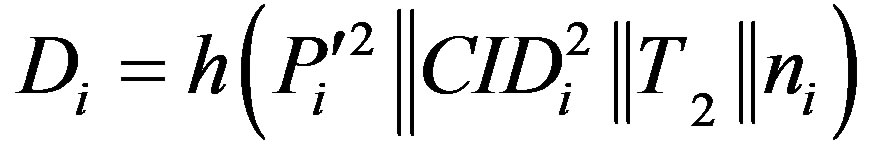 and
and
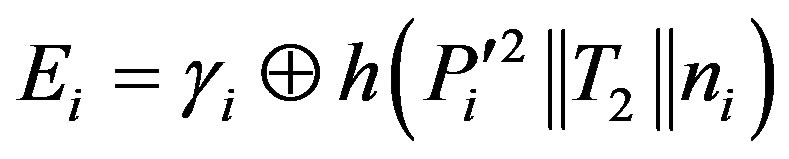 .
.
• Computes a new permutation of the MSi’s ID (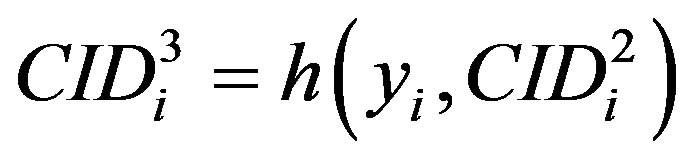 ) to be used by MSi’s as a new ID during the next communication with the HES.
) to be used by MSi’s as a new ID during the next communication with the HES.
• Computes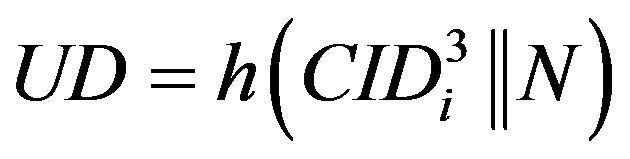 ,
,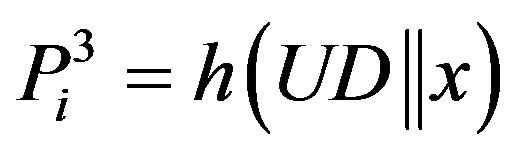 and
and
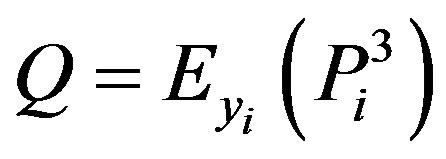 .
.
• 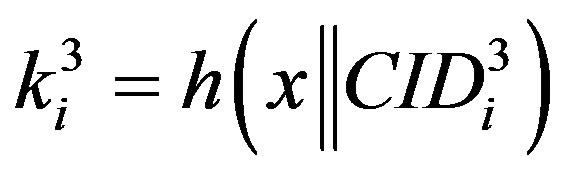 ,
,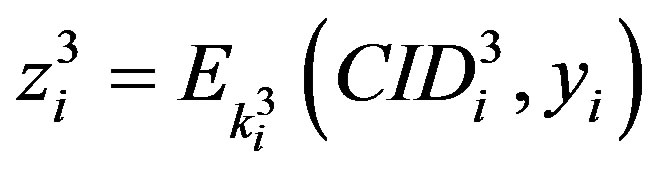 .
.
• Broadcasts the mutual authentication message
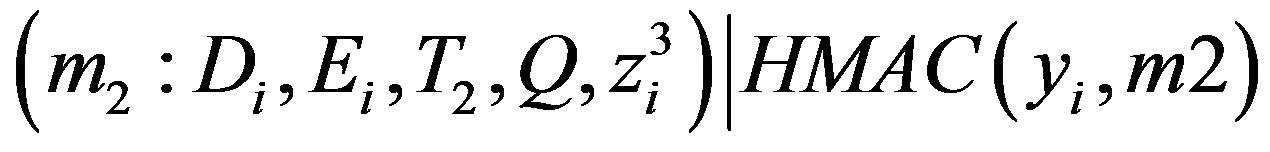 .
.
3) After receiving message m2 at the time T3, Ui checks the validity of 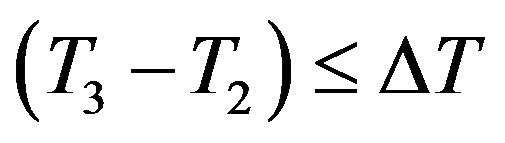 and uses yi to validate the HMAC. If they do not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
and uses yi to validate the HMAC. If they do not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
• Calculates 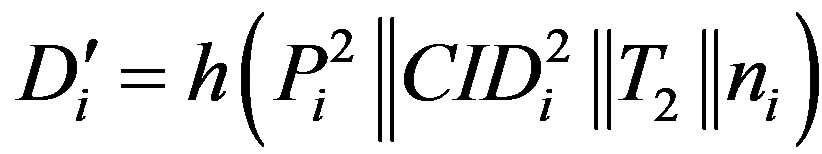 and checks whether
and checks whether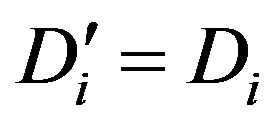 . If they are equal, Ui accepts HES’s request of mutual authentication.
. If they are equal, Ui accepts HES’s request of mutual authentication.
• Ui calculates the certified token
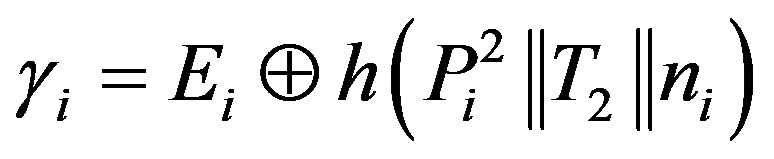 as the authentication session key to get service of the pay-TV system.
as the authentication session key to get service of the pay-TV system.
• Ui stores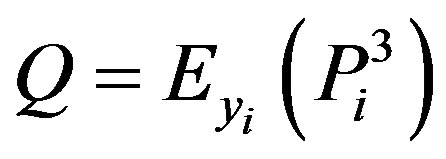 ,
, 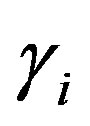 ,
, 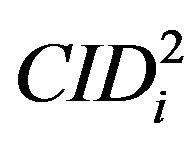 and
and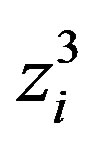 .
.
4.4. Hand-off Phase
When MSi moves to a new coverage area that older HES cannot support such that a hand-off occurs, MSi needs to performer-authentication without re-login. The statements are described as follows:
1) MSi performs the following computations:
• Calculates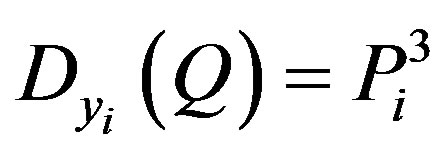 .
.
• Generates a random number ni and calculates
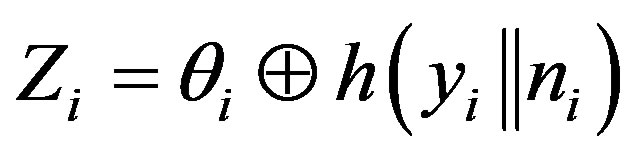 ,
, 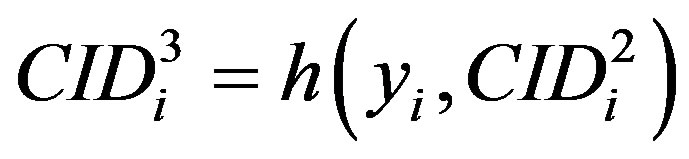 and
and
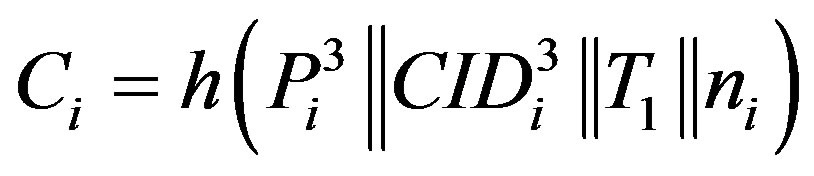 . Here T1 is the current timestamp.
. Here T1 is the current timestamp.
• Sends the message m to HES:
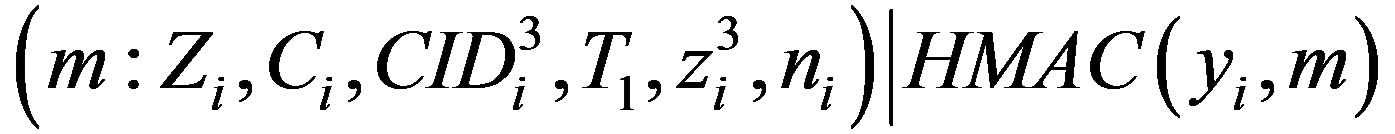 .
.
2) HES receives the message at the timestamp T2 and performs the following computations:
• Checks the validity of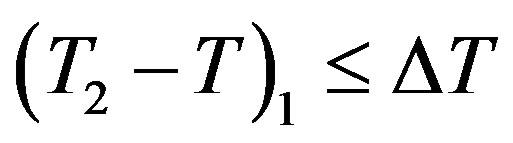 . If it does not hold, HES terminates the request.
. If it does not hold, HES terminates the request.
• To validate the 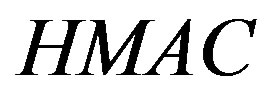 and the new ID (
and the new ID (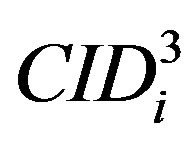 ), HES calculates
), HES calculates 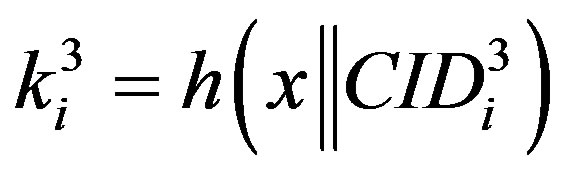 and
and
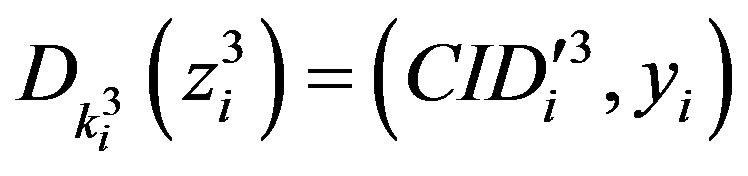 to get the user authentication key yi .
to get the user authentication key yi .
• Uses yi to validate 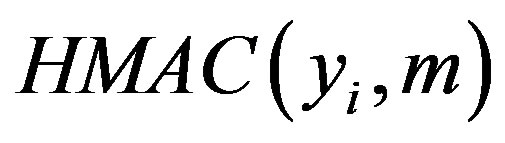 then checks whether the computed
then checks whether the computed 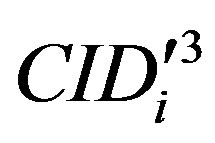 equal to
equal to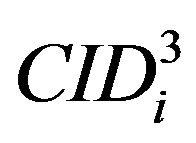 . If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates
. If it does not hold, HES terminates the login request, otherwise HES checks the value of N in the database and calculates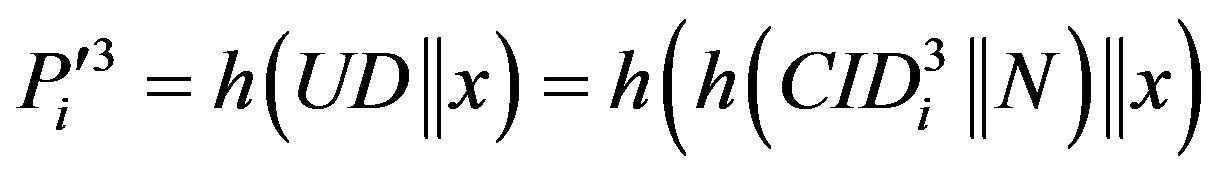 .
.
• Calculates 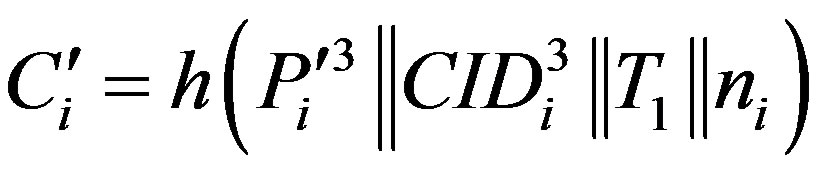 and checks whether
and checks whether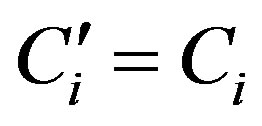 . If they are equal, HES accepts Ui’s request of authentication.
. If they are equal, HES accepts Ui’s request of authentication.
• Calculates 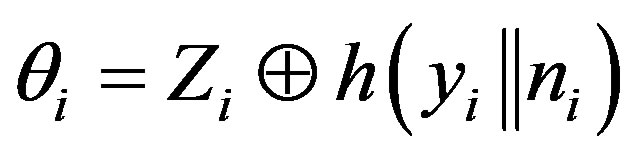
• Then, HES chooses a token 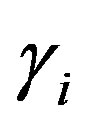 for Ui and calculates
for Ui and calculates 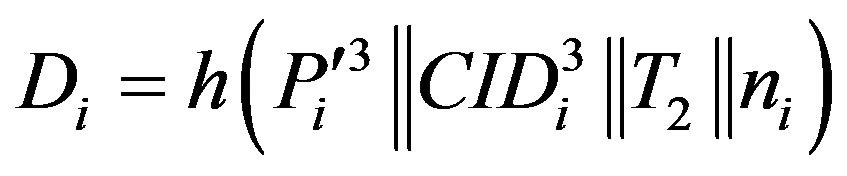 and
and
• 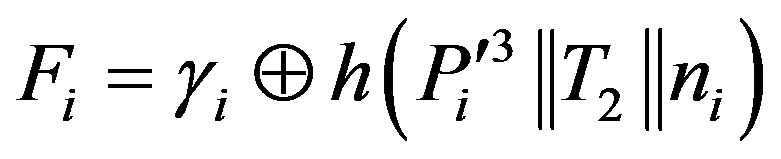
• Computes a new permutation of the MSi’s ID
(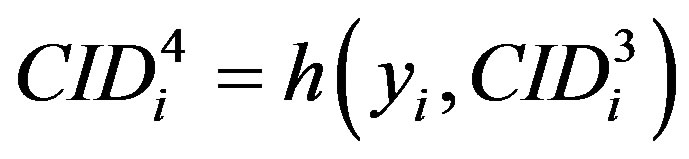 ) to be used by MSi’s as a new ID during the next communication with the HES.
) to be used by MSi’s as a new ID during the next communication with the HES.
• Computes ,
, 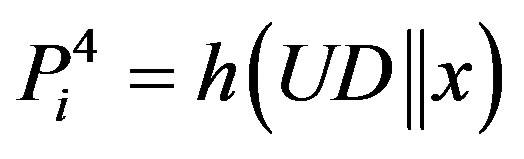 and
and
• 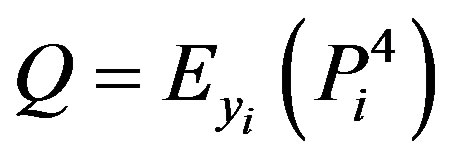
• 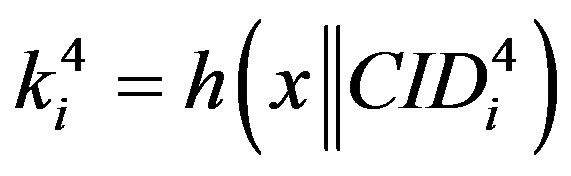 ,
,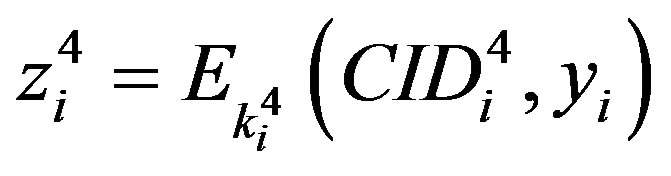 .
.
• Broadcasts the mutual authentication message
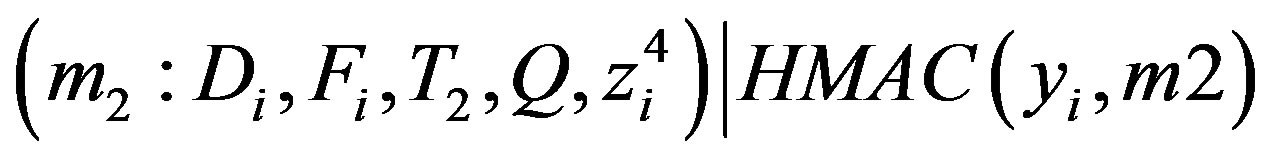 .
.
3) After receiving message m2 at the time T3, Ui checks the validity of 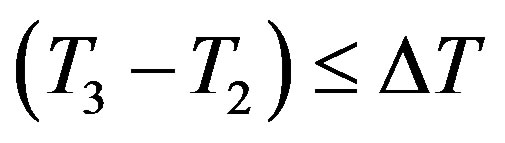 and uses yi to validate the HMAC. If they do not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
and uses yi to validate the HMAC. If they do not hold, Ui terminates the request. Otherwise, Ui executes the following operations to authenticate HES.
• Calculates 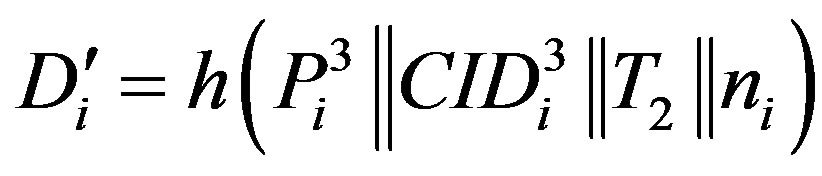 and checks whether
and checks whether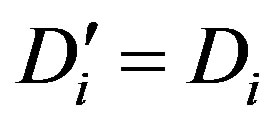 . If they are equal, Ui accepts HES’s request of mutual authentication.
. If they are equal, Ui accepts HES’s request of mutual authentication.
• Ui calculates the certified token
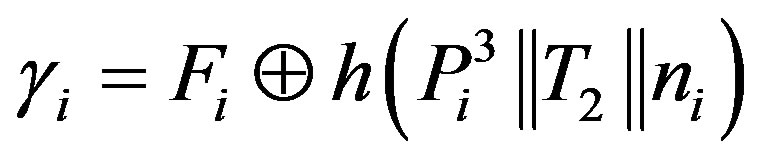 as the authentication session key to get service of the pay-TV system.
as the authentication session key to get service of the pay-TV system.
• Ui stores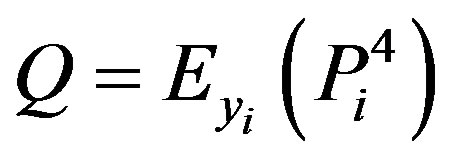 ,
, 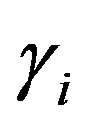 ,
, 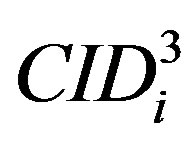 and
and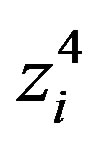 .
.
5. Security and Performance Analysis
In this section, the security of the proposed improved scheme with respect to the resistance to user tracking and denial of service attack is analyzed. This section also evaluates the performance of the proposed scheme.
5.1. Resistance to User Tracking
The proposed improved scheme prevents user tracking by ensuring the anonymity feature of users. As discussed in Section 3.2, an attacker can track a legitimate user by registering himself to the subscribers’ database server (DBS) like any other user, then receives 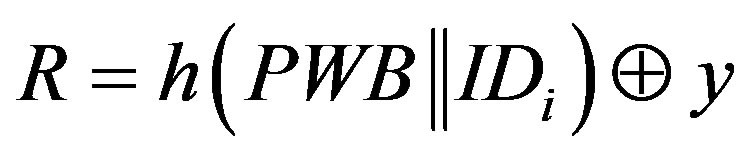 which is used by the attacker to compute
which is used by the attacker to compute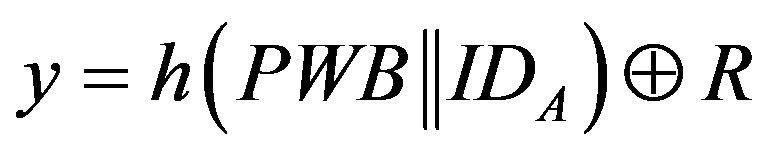 . Using the computed
. Using the computed 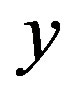 the attacker A can perform MS tracing attack as described in Section 3.2. The attacker is able to perform this attack; because the server S uses the same secret y to compute the R values for all users. So, if the attacker extracts
the attacker A can perform MS tracing attack as described in Section 3.2. The attacker is able to perform this attack; because the server S uses the same secret y to compute the R values for all users. So, if the attacker extracts 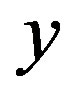 from his R value, he can use the same
from his R value, he can use the same 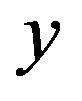 to extract the IDs of other uses.
to extract the IDs of other uses.
In the proposed scheme, the server S generate a unique user authentication key 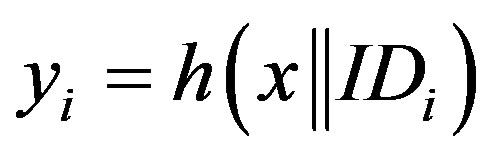 for each user using the hash of the user ID and the server’s own secret key x. This prevent an attacker A form using his user authentication key (
for each user using the hash of the user ID and the server’s own secret key x. This prevent an attacker A form using his user authentication key (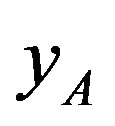 ) to extract the IDs of other uses. The proposed scheme also preserves users’ privacy by using pseudo identity,
) to extract the IDs of other uses. The proposed scheme also preserves users’ privacy by using pseudo identity, 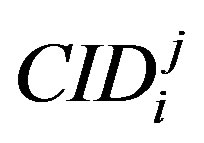 to identify users. This pseudo identity generated using a one-way function combined with the user authentication key,
to identify users. This pseudo identity generated using a one-way function combined with the user authentication key,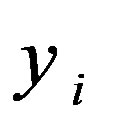 , and the user’s previous
, and the user’s previous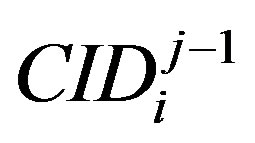 :
: 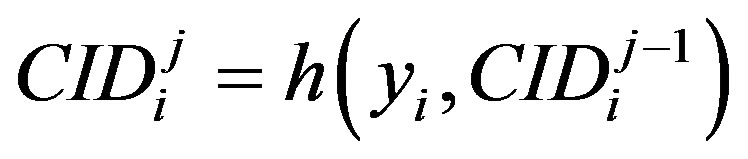 and is updated in each phase. So, it is impossible to anticipate the messages of the user each phase which guarantees indistinguishability. Also the integrity of messages exchanged between users and HES is guaranteed due to the use of timestamps and the HMAC of each message which is included with the message. The HMAC value is computed using the user authentication key (
and is updated in each phase. So, it is impossible to anticipate the messages of the user each phase which guarantees indistinguishability. Also the integrity of messages exchanged between users and HES is guaranteed due to the use of timestamps and the HMAC of each message which is included with the message. The HMAC value is computed using the user authentication key (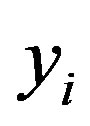 ) which is only known to Ui and HES.
) which is only known to Ui and HES.
5.2. Resistance to Denial of Service Attack
As discussed in Section 3.3, Chen’s scheme is subject to denial of service attack. The attacker can perform this attack because the integrity of message m2 of the subscription and hand-off phases is not guaranteed. So, an attacker can easily modify 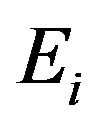 or
or 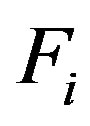 during the subscription or hand-off phases without being detected by Ui which prevents him from getting the service of the payTV system.
during the subscription or hand-off phases without being detected by Ui which prevents him from getting the service of the payTV system.
In the proposed scheme, the integrity of messages exchanged between users and HES is guaranteed due to the use of timestamps and the HMAC of each message which is included with the message. The HMAC value is computed using the user authentication key, (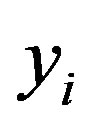 ) which is only known to Ui and HES. This prevents the DoS attack that can be launched against the Chen’s scheme as described in Section 3.3. This also prevents the attacker from making an impersonation attack and replay attacks using the open values and some modified values.
) which is only known to Ui and HES. This prevents the DoS attack that can be launched against the Chen’s scheme as described in Section 3.3. This also prevents the attacker from making an impersonation attack and replay attacks using the open values and some modified values.
5.3. Performance Analysis
This section evaluates the performance of the proposed scheme. To analyze the efficiency of the proposed scheme, the proposed scheme is compared with the Chen’s scheme [14]. The efficiency of the proposed scheme is analyzed with the same metrics used in Chen’s scheme analysis. We define the notation 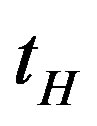 as the hash computation time and
as the hash computation time and 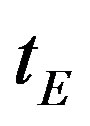 as the symmetric encryption/decryption time. The four phases of both the Chen’s scheme and the proposed scheme are simulated and implemented using OpenSSL library [17] on an Intel DualCore CPU at 2.30 GHz. Table 1 shows a comparison between the Chen’s scheme and the proposed scheme with respect to the hash computation time and the symmetric encryption/ decryption time. Note that we neglect the XOR operation since it is an extremely light-weight one. As shown in Table 1, the proposed scheme takes the following extra operation for each phase:
as the symmetric encryption/decryption time. The four phases of both the Chen’s scheme and the proposed scheme are simulated and implemented using OpenSSL library [17] on an Intel DualCore CPU at 2.30 GHz. Table 1 shows a comparison between the Chen’s scheme and the proposed scheme with respect to the hash computation time and the symmetric encryption/ decryption time. Note that we neglect the XOR operation since it is an extremely light-weight one. As shown in Table 1, the proposed scheme takes the following extra operation for each phase:
• It takes extra 3 hash operations and more two symmetric encryption/decryption about extra 62 μs for the initialization phase.
• It takes extra 6 hash operations and more four symmetric encryption/decryption about extra 81 μs for the issue phase.
• It takes extra 6 hash operations and more four symmetric encryption/decryption about extra 81 μs for the subscription phase.
• It takes extra 8 hash operations and more four symmetric encryption/decryption about extra 89 μs for the hand-off phase.
This indicates that the proposed scheme introduces a minor increase in computation overhead, which is the cost to enhance the security of the original scheme.
6. Conclusion
Recently, an efficient anonymous authentication protocol for mobile pay-TV is proposed [14]. However, the scheme is vulnerable to user tracking attack and denial of service attack. An improved scheme is proposed to prevent these two attacks by lightweight modifications and, thus, can be applied in environments requiring a high level of security. The improved scheme introduces a minor increase in computation overhead and maintains the
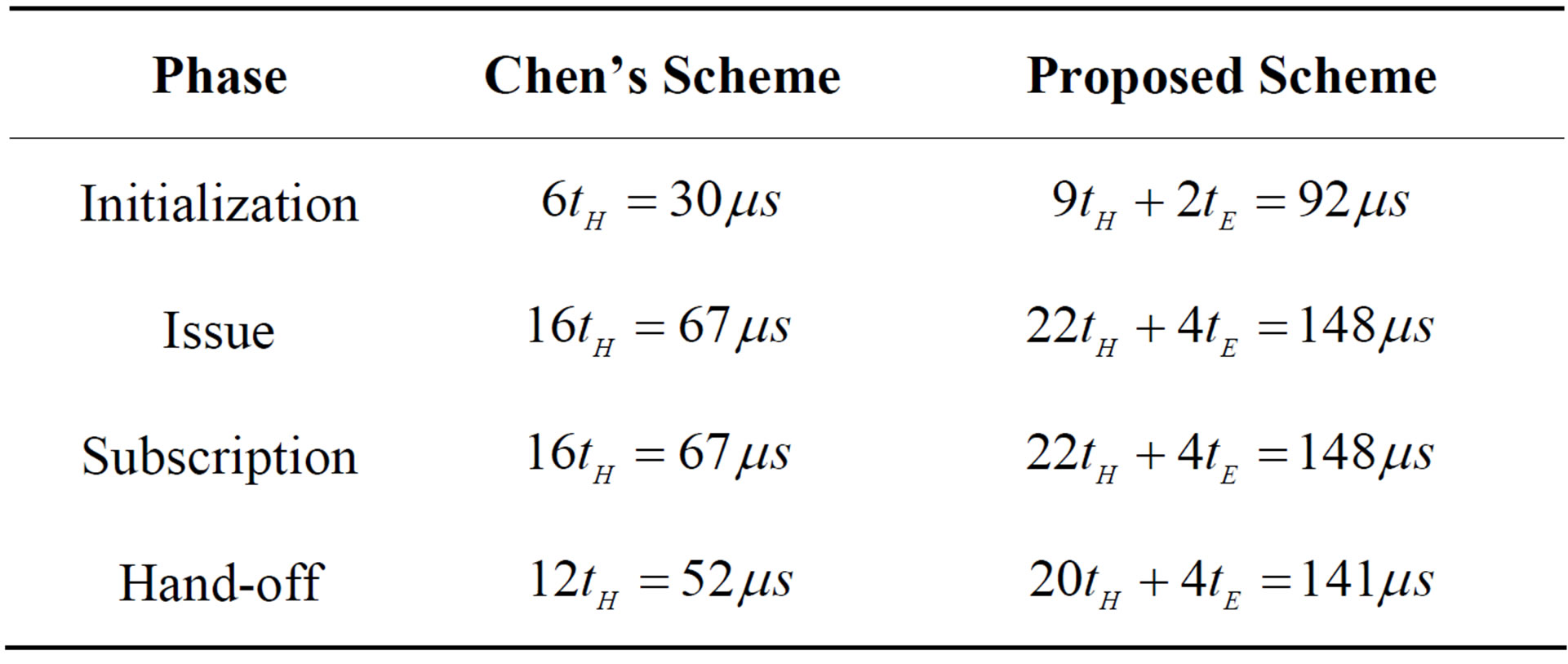
Table 1. Performance comparison.
same number of messages of the original scheme.
REFERENCES
- H. S. L. Pequeno, G. A. M. Gomes, R. M. C. Andrade, J. N. de Souza and M. F. de Castro, “FrameIDTV: A Framework for Developing Interactive Applications on Digital Television Environments,” Journal of Network and Computer Applications, Vol. 33, No. 4, 2010, pp. 503- 511.
- H.-M. Sun and M.-C. Leu, “An Efficient Authentication Scheme for Access Control in Mobile Pay-TV Systems,” IEEE Transactions on Multimedia, Vol. 11, No. 5, 2009, pp. 947-959. http://dx.doi.org/10.1109/TMM.2009.2021790
- X. Li, J. Niu, M. Khurram Khan and J. Liao, “An Enhanced Smart Card Based Remote User Password Authentication Scheme,” Journal of Network and Computer Applications, Vol. 36, No. 5, 2013, pp. 1365-1371.
- X. Li, Y. Xiong, J. Ma and W. Wang, “An Efficient and Security Dynamic Identity Based Authentication Protocol for Multi-Server Architecture Using Smart Cards,” Journal of Network and Computer Applications, Vol. 35, No. 2, 2012, pp. 763-769.
- Z. Tan, “A Lightweight Conditional Privacy-Preserving Authentication and Access Control Scheme for Pervasive Computing Environments,” Journal of Network and Computer Applications, Vol. 35, No. 6, 2012, pp. 1839-1846.
- N.-Y. Lee, C.-C. Chang, C.-L. Lin and T. Hwang, “Privacy and Non-Repudiation on Pay-TV Systems,” IEEE Transactions on Consumer Electronics, Vol. 46, No. 1, 2000, pp. 20-27. http://dx.doi.org/10.1109/30.826376
- R. Song and L. Korba, “Pay-TV System with Strong Privacy and Non-Repudiation Protection,” IEEE Transactions on Consumer Electronics, Vol. 49, No. 2, 2003, pp. 408-413. http://dx.doi.org/10.1109/TCE.2003.1209533
- S. F. Yeung, J. C. Lui and D. K. Yau, “A Multikey Secure Multimedia Proxy Using Asymmetric Reversible Parametric Sequences: Theory, Design and Implementation,” IEEE Transactions on Multimedia, Vol. 7, No. 2, 2005, pp. 330-338. http://dx.doi.org/10.1109/TMM.2005.843361
- H. Roh and S. Jung, “An Authentication Scheme for Consumer Electronic Devices Accessing Mobile IPTV Service From Home Networks,” 2011 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, 9-12 January 2011, pp. 717-718.
- Y.-L. Huang, S. Shieh, F.-S. Ho and J.-C. Wang, “Efficient Key Distribution Schemes for Secure Media Delivery in Pay-TV Systems,” IEEE Transactions on Multimedia, Vol. 6, No. 5, 2004, pp. 760-769. http://dx.doi.org/10.1109/TMM.2004.834861
- H.-M. Sun, C.-M. Chen and C.-Z. Shieh, “Flexible-Payper-Channel: A New Model for Content Access Control in Pay-TV Broadcasting Systems,” IEEE Transactions on Multimedia, Vol. 10, No. 5, 2008, pp. 1109-1120. http://dx.doi.org/10.1109/TMM.2008.2001381
- R. Di Pietro and R. Molva, “An Optimal Probabilistic Solution for Information Confinement, Privacy, and Security in RFID Systems,” Journal of Network and Computer Applications, Vol. 34, No. 3, 2011, pp. 853-863.
- W. I. Khedr, “SRFID: A Hash-Based Security Scheme for Low Cost RFID Systems,” Egyptian Informatics Journal, Vol. 14, No. 1, 2013, pp. 89-98.
- T.-H. Chen, Y.-C. Chen, W.-K. Shih and H.-W. Wei, “An Efficient Anonymous Authentication Protocol for Mobile Pay-TV,” Journal of Network and Computer Applications, Vol. 34, No. 4, 2011, pp. 1131-1137.
- J.-H. Yang and C.-C. Chang, “An ID-Based Remote Mutual Authentication with Key Agreement Scheme for Mobile Devices on Elliptic Curve Cryptosystem,” Computers & Security, Vol. 28, No. 3-4, 2009, pp. 138-143. http://dx.doi.org/10.1016/j.cose.2008.11.008
- WMF-T33-107-R020v02, “Architecture, detailed Protocols and Procedures,” 2012.
- OpenSSL, “OpenSSL 1.0.1e,” 2013.

