Journal of Computer and Communications
Vol.06 No.09(2018), Article ID:87252,10 pages
10.4236/jcc.2018.69005
An Improved Multiple to One Fully Homomorphic Encryption on the Integers
Chaoju Hu, Jianwei Zhao
School of Control & Computer Engineering, North China Electric Power University, Baoding, China
Copyright © 2018 by authors and Scientific Research Publishing Inc.
This work is licensed under the Creative Commons Attribution International License (CC BY 4.0).
http://creativecommons.org/licenses/by/4.0/



Received: August 20, 2018; Accepted: September 9, 2018; Published: September 12, 2018
ABSTRACT
The public key of the integer homomorphic encryption scheme which was proposed by Van Dijk et al. is long, so the scheme is almost impossible to use in practice. By studying the scheme and Coron’s public key compression technique, a scheme which is able to encrypt n bits plaintext once was obtained. The scheme improved the efficiency of the decrypting party and increased the number of encrypting parties, so it meets the needs of cloud computing better. The security of the scheme is based on the approximate GCD problem and the sparse-subset sum problem.
Keywords:
Fully Homomorphic Encryption, Multipart to One Fully Homomorphism Encryption, Approximate GCD Problem, Sparse-Subset Sum Problem

1. Introduction
Full homomorphic encryption (FHE) was proposed by Rivest, Adleman, and Dertouzos in 1978 [1]. This encryption method can perform operations on ciphertext. After decryption, the same operation is performed on the corresponding plaintext. The results are consistent. With such characteristics, the data can be encrypted and handed over to the cloud for processing, which not only utilizes the computing power of the cloud, but also reduces the amount of local computing and ensures the security of the data [2][3].
To this end, many scholars have studied how to construct a homomorphic encryption scheme, and proposed a variety of encryption schemes that satisfy partial homomorphism [4]- [9]. In 2009, Gentry et al. [10]proposed the first true homomorphic encryption scheme based on the ideal lattice on a polynomial ring, but because it is too complicated and inefficient, it has larger difficulty in practical applications. In 2010, Dijk et al. [11]improved the above ideal lattice scheme and proposed an integer homomorphic encryption scheme, namely the DGHV scheme. The public key size of this scheme is . In 2011, Coron et al. [12]optimized the DGHV scheme. For the problem of the large number of public keys in the DGHV scheme, a scheme for generating public key integers in quadratic form was proposed, which shortened the public key length to . The following year, Coron et al. [13]proposed a “public key compression technique” for the problem of excessive public key elements in the DGHV scheme, shortening the public key length to .
Through comparison and research, it is found that the above schemes are composed of one encryption party and also a single decryption party, which is difficult to meet the problem of multi-party interaction in the cloud computing environment. In view of the above problems, this paper studies Coron’s public key compression technology, shortens the size of the public key, expands the plaintext space in the scheme to n bits, and expands the number of encryption parties to achieve multiple encryption methods. A solution composed of a decryption party is more in line with the application needs of actual scenarios such as cloud computing. The public key size of this scheme is .
2. Basic Symbols and Concepts
2.1. Fully Homomorphic Encryption
A compact encryption scheme E encrypts the plaintext according to the encryption method in scheme E. After the obtained ciphertext is arbitrarily operated, the result is decrypted and the result is the same as the plaintext, and the scheme E is fully homomorphic Encryption scheme. Expressed as a mathematical formula as:
Enc is an encryption algorithm, Dec is a decryption algorithm, f is an arbitrary function, cn is ciphertext, and mn is plaintext.
In general, a fully homomorphic encryption algorithm consists of four parts:
Key generation algorithm KeyGen (λ): Generate public key pk, private key sk.
Encryption algorithm Encrypt (pk, m): encrypts the plaintext m with the public key pk to obtain the ciphertext c.
Decryption algorithm Decrypt (sk, c): Decrypt the ciphertext c with the private key sk to obtain the plaintext m.
The ciphertext calculation algorithm Evaluates : the operation of the ciphertext should satisfy:
2.2. DGHV Program
In 2010, Dijk, Gentry et al. proposed an integer homomorphic encryption scheme, namely the DGHV scheme, which is no longer based on ideal lattices but on modular operations on integers.
The encryption algorithm of the DGHV scheme is
where c is ciphertext, m is plaintext, r is random noise interference, p is a private key, and q is a large positive integer generated during the key generation phase.
The decryption algorithm is
The public key size of this scheme is .
In order to ensure security, the approximate maximum common divisor problem is introduced. In the encryption process, some ciphertext encrypted by 0, is added, then reorder so that is the largest and is odd. is an even number, then the public key . When encrypting, a subset of the set is randomly added to the ciphertext, and the encryption algorithm is
.
The addition of the approximate greatest common divisor problem means that the attack on the program is due to an attack on the approximate greatest common divisor problem, so the scheme is safe [14].
2.3. Many-to-One Homomorphic Encryption
The many-to-one fully homomorphic encryption scheme [15]contains a plurality of encryption parties and a decryption party P. The plaintext space is M, the public-private key pair of the encrypting party, and the public-private key pair of the decrypting party. And the encryption algorithm E(⋅) and the corresponding decryption algorithm D(⋅). In this model, the plaintext of the encryption side, the generated ciphertext is encrypted by , and needs to satisfy the following properties, where denotes the operator, :
1) Both the encrypting party and the decrypting party can use their own private key to decrypt the message encrypted by their own public key, i.e.
, .
2) The encrypting party i cannot use its own private key to decrypt the message encrypted by the encrypting party j with its own public key , that is,
.
3) The message encrypted by the encrypting party i with its own public key can be decrypted by the decrypting party P with its own private key sk, that is,
.
4) Different messages encrypted by the encrypting party i with its own public key have homomorphism under the operation of the decrypting party P, that is,
.
5) Different messages encrypted by different encrypting party i and encrypting party j have homomorphism under the operation of decrypting party P, that is,
.
3. Improved N-Bit “One-to-One” Homomorphic Encryption Scheme
The DGHV scheme can only encrypt 1 bit of plaintext at a time, and the size of the public key element is too large. This section extends the plaintext space to n bits, and uses the public key compression technique to improve the key generation algorithm, using pseudo-random number generation. The f and the seed se generate a set of integers having the same number of bits as , so that it is not necessary to store the large integer , and it is only necessary to store the difference between and as a public key element.
3.1. Program Establishment
KeyGen: randomly generate a large prime number of length bits, and calculate , where is a random odd number. Initialize the pseudo-random number generator f and the seed se, and generate integers by using , that is, , and calculate
, ,
where , . Then . The public key , private key .
Encrypt: Randomly select the integer vector , randomly select the integer , ciphertext
.
Decrypt: .
In order to ensure the security of the scheme, the parameters in the above method need to meet the following restrictions: to resist violent attacks, select ; in order to make the compressed decryption circuit belong to the permissible circuit, select ; to resist the lattice-based attack, choose ; apply the residual hash theorem to the approximation of the approximate GCD problem, choose ; To ensure correct decryption of ciphertext, select ; second noise parameter . In this scheme, the parameters take , , , , , .
3.2. Proof of Correctness
In which
So the original
3.3. Test of Homomorphism
There are ciphertext and ciphertext , then
4. Improved N-Bit “Many-to-One” Fully Homomorphic Encryption Scheme
Based on the scheme given in Section 3.1, this section changes the key generation algorithm, expands the number of encryption parties, and gives a “many-to-one” fully homomorphic encryption scheme for processing n-bit plaintext, and corrects it. Sex and homomorphism have been proved.
4.1. Program Establishment
KeyGen: There are multiple encryption parties and one decryption party P in this scheme. The decryption party P generates the public key from the 3.1 scheme, the encryption side selects the integer as its own key , then change the order of in the public key randomly to obtain , and then randomly selected integer
,
randomly select integer , such that
, , ,
and is the largest. Then the public key of is
.
Encrypt: Encryption party randomly selects the integer vector
,
randomly selects integer , ciphertext
.
Decrypt: The encryption party can decrypt according to ; the decryption party P can decrypt according to .
4.2. Proof of Correctness
1) is the public-private key pair generated by P. It can be seen from 3.2 that P can perform correct encryption and decryption.
2) can correctly decrypt using the key prove:
Since is the largest, it can be written as
Finishing can get , where
, .
According to the defined parameters, , then
.
So can correctly decrypt using the key .
3) P can correctly decrypt using the key prove:
As can be seen from 2),
According to 3.2, , can be written as , , and , so it is sorted into: , where
,
.
According to the defined parameters, , then . So P can correctly decrypt using the key .
4.3. Test of Homomorphism
1) P has the homomorphism of the decrypted ciphertext. Proof from 3.3 is known.
2) The encrypting party has homomorphism to the encrypted ciphertext. Proof: From 4.2 (2), , with ciphertext and ciphertext , then
Therefore, has homomorphism to the encrypted ciphertext.
3) The decryption party P has homomorphism to the encrypted ciphertext. Proof: From 4.2 (3), , with ciphertext and ciphertext , the
Therefore, the decryption party P has homomorphism to the encrypted ciphertext.
4) The decryption party P has homomorphism for different encryption parties and the ciphertext of the encryption party . Proof: From 4.2 (3), , with ciphertext and ciphertext , then
Therefore, the decryption party P has homomorphism to different encryption parties and the ciphertext of the encryption party .
4.4. Compression and Decryption Circuit
In order to avoid excessive noise generated during the encryption process and affect the correctness of the homomorphic operation, the ciphertext needs to be re-encrypted, and the condition of re-encryption is that the decryption circuit can be operated in the Evaluate algorithm. This requires that the depth of the decryption circuit is less than the maximum depth allowed by the Evaluate algorithm. Therefore, the decryption circuit needs to be compressed to preprocess some of the calculations in the decryption circuit.
KeyGen: With the KeyGen algorithm in Section 4.1, generate
.
On the basis of this, add three parameters , and randomly generate a bit vector with length .Its Hamming weight is .
The pseudo random number generator and the seed are initialized, and an integer , is generated by using .
,
where = ⌈2κ/pi⌋. Let .
Initialize pseudo-random number generator
and seed
, use
to generate integer
, and randomly generate integer
,  , calculate
, calculate
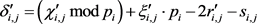 ,
,
then the result of the vector s is encrypted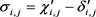 . The public key
. The public key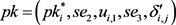 , and the private key
, and the private key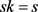 .
.
Encrypt: Encrypt the plaintext  with an encryption algorithm to obtain the ciphertext
with an encryption algorithm to obtain the ciphertext , and find
, and find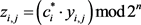 . The ciphertext
. The ciphertext 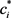 and the extended ciphertext
and the extended ciphertext  are the output.
are the output.
Decrypt: Decrypt, output secret civilization
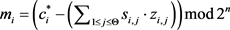 .
.
This results in a fully homomorphic encryption scheme.
5. Conclusion
Based on the DGHV scheme and the public key compression technology of Coron et al., this paper improves the encryption process, expands the number of encryption parties, and builds a multi-party encryption with a smaller public key size. The integer-homomorphic encryption scheme can encrypt the n-bit plaintext at a time, which is more in line with the needs of practical applications such as cloud computing. Whether it can further reduce the amount of calculation, whether it can achieve “multi-party encryption, multi-party decryption” will be the direction that will be improved in the future.
Conflicts of Interest
The authors declare no conflicts of interest regarding the publication of this paper.
Cite this paper
Hu, C.J. and Zhao, J.W. (2018) An Improved Multiple to One Fully Homomorphic Encryption on the Integers. Journal of Computer and Communications, 6, 50-59. https://doi.org/10.4236/jcc.2018.69005
References
- 1. Rivest, R.L., Adleman, L. and Dertouzos, M.L. (1978) On Data Banks and Privacy Homomorphisms. In: Foundations of Secure Computation, Academia Press, Ghent, 169-179.
- 2. Chen, Z.-G., Wang, J. and Song, X.-X. (2014) Survey on Fully Homomorphic Encryption. Application Research of Computers, 31, 1624-1631.
- 3. Lin, C., Su, W.-B., Meng, K., Liu, Q. and Liu, W.-D. (2013) Cloud Computing Security: Architecture, Mechanism and Modeling. Chinese Journal of Computers, 36, 1765-1784.
- 4. Elgamal, T. (1984) A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms. IEEE Transactions on Information Theory, 31, 469-472.
- 5. Fellows, M.R. and Koblitz, N. (1994) Combinatorial Cryptosystems Galore! Contemporary Mathematics, 168, 51-62. https://doi.org/10.1090/conm/168/01688
- 6. Benaloh, J. (1994) Dense Probabilistic Encryption. Proceedings of the Workshop on Selected Areas of Cryptography, Kingston, 1994, 120-128.
- 7. Okamoto, T. and Uchiyama, S. (1998) A New Public-Key Cryptosystem as Secure as Factoring. In: Nyberg, K., Ed., International Conference on the Theory and Applications of Cryptographic Techniques, Springer, Berlin, Heidelberg, 308-318.
- 8. Naccache, D. and Stern, J. (1998) A New Public Key Cryptosystem Based on Higher Residues. Proceedings of the 5th ACM Conference on Computer and Communications Security, San Francisco, CA, USA, 2-5 November 1998, 59-66. https://doi.org/10.1145/288090.288106
- 9. Damgard, I. and Jurik, M. (2001) A Generalisation, a Simplication and Some Applications of Paillier’s Probabilistic Public-Key System. In: International Workshop on Practice and Theory in Public Key Cryptography: Public Key Cryptography, Springer-Verlag, Berlin, 119-136.
- 10. Gentry, C. (2009) Fully Homomorphic Encryption Using Ideal Lattices. ACM Symposium on Theory of Computing, STOC 2009, Bethesda, MD, USA, 31 May-2 June 2009, 169-178.
- 11. Dijk, M.V., Gentry, C., Halevi, S., et al. (2010) Fully Homomorphic Encryption over the Integers. Lecture Notes in Computer Science, 6110, 24-43. https://doi.org/10.1007/978-3-642-13190-5_2
- 12. Coron, J.S., Mandal, A., Naccache, D., et al. (2011) Fully Homomorphic Encryption over the Integers with Shorter Public Keys. In: Rogaway, P., Ed., CRYPTO 2011. LNCS, Vol. 6841, 487-504.
- 13. Coron, J., Naccache, D. and Tibouchi, M. (2012) Public Key Compression and Modulus Switching for Fully Homomorphic Encryption over the Integers. In: David, P. and Thomas, J., Eds., Advances in Cryptology-EUROCRYPT 2012, Springer, Berlin, Heidelberg, 446-464.
- 14. Tang, Q.-Y. and Ma, C.-G. (2014) Feedback Attack against Fully Homomorphic Encryption System. Computer Engineering, 40, 79-84.
- 15. Xia, C. (2013) Research of Homomorphic Encryption Technology and Application. Anhui University, Hefei.

