Technology and Investment
Vol.2 No.3(2011), Article ID:6980,9 pages DOI:10.4236/ti.2011.23019
Analysis on the Mindbugs in Information Technology Service Management Project Implementation*
1Faculty of Business Administration, South China University of Technology, Guangzhou, China
2Institute of Emerging Industrialization Development, South China University of Technology, Guangzhou, China
E-mail: scutwjp@126.com, csjpwan@scut.edu.cn
Received May 6, 2011; revised May 26, 2011; accepted June 5, 2011
Keywords: Complexity, Mindbugs, Root Risk Factors, Information Technology Infrastructure Library (ITIL), Information Technology Service Management (ITSM), Project Management
Abstract
J. N. Warfield identified and classified the mindbugs (cognitive barriers), and put forward the process-based work program of complexity, and argued that the complexity could be managed through design. The eleven kinds of common mindbugs are figured out among the twenty five kinds of mindbugs with questionnaire. The relationship between the six root risk factors of implementation of the information technology service management (ITSM) project and these common mindbugs are also identified. It is found that the influence of mindbugs of habit is most serious in the ITSM project because the implementation of ITSM project would change the original work habits and methods of people. Finally, some recommendations are put forward to mitigate the root risk factors.
1. Introduction
Warfield identified and classified the mindbugs (cognitive barriers), and put forward the process-based work program of complexity, and argued that the complexity could be managed through design. The approaches to manage complexity are design processes, design working environment, special roles trained for managing complexity, leadership and quality control with foresight etc. The science of generic design should clarity the methods to manage complexity through design [1-2].
Now the IT service management (ITSM) project has been concerned deeply by the industry. ITSM is a process-oriented and customer-centric approach. It enhances IT organizational service delivery, service level and the ability by integrating IT service and organizational business [3-6].
This paper is organized in the following: Section 2 is literature review, including, mindbugs and its classification, and ITSM and its research. Section 3 is identification of mindbugs in P. R. China. Section 4 is the relationship between the root risk factors and the mindbugs. Section 5 includes risk mitigation recommendations. Finally, Section 6 is conclusions.
2. Literature Review
2.1. The Identification and Classification of Mindbugs
Warfield have tried to identify and name each distinctive origin of one or more behaviorally-related symptoms (as “mindbugs” to bring the language in line with contemporary computer languages) [1]. So far, twenty-five mindbugs have been identified. These are envisaged as falling within four categories: Mindbugs of Minsinterpretation: those where concepts are misconstrued or misattributed, because of faulty interpretation, Type M; Mindbugs of Clanthink: those where concepts are very widely perceived to be correct, but which are demonstrably incorrect, Type C; Mindbugs of Habit: those which involve ingrained behavior, evinced with essentially no conscious thought, Type H; and mindbugs of Error: just plain mistakes, Type E. It can be summary in Table 1 (where a mindbugs is at least assigned to more than one type, the several types are separately acknowledged).
There are nine mindbugs in the following to be selected for study in software process improvement [2]: confusing Prestige with Authoritativeness (M3), Misconstruing Structural Incompetence as Innate Incompetence (M5), Misattribution of Consensus (M6), Misconstruing Persistence as Validity (M7), Leaping to Misassociation (H4), Insensitivity to Role Distinction (H5), Insensitivity to the Significance of Information Flow Rates (H7), Aversity to Deep Though (H8), and Failure to Distinguish among Context, Context, and Process (H9). The first four mindbugs are in the type of minsinterpretation, and others of habit. The research found that the most common mindbugs of SPI is Misattribution of Consensus (M6), and the finding was consistent with literature review and investigation on spot. It is suggested to resolve the mindbugs in Type M, including M6 in the first place, then framebreak and remodel to resolve the mindbugs of Type H in software process improvement.
2.2. IT Service Management
ITSM based on Information Technology Infrastructure Library (ITIL), which integrates the best practices of global IT management and forms the normative truth standard to reduce effectively cost and improve the quality of service, is applied widely in the world [3]. ITIL, which was developed by the Central Computer and Telecommunications Agency (CCTA, merged with the OGC) of the UK government in the middle of 1980s, is a set of service management standard library which focuses on IT industry. In the past 20 years, the content of ITIL has been updated and renewed. Today the OGC has enacted the ITIL 3.0. ITIL emphasizes on managing IT service from organization business and customer desires, and realizes the integration of service management processes and organization business. The module of service management plays a role of “glue” which makes an organic connection between the business perspective and the technology.
Reference [4] presents an in-depth case study of the implementation. It indicates that the commitment of senior management is crucial to the project’s success as is a project champion and the recognition of the need for an appropriate change management strategy to transform the organizational culture to a service-oriented focus. Maintaining close and forthright relationships with multiple vendors facilitates technology transfer to in-house staff while a benefits realization plan is a valuable tool for tracking and communicating tangible and intangible project benefits to the project stakeholders. An effective project governance and execution process further contributes to the implementation success. Reference [5] is concluded that if the organization wishes to successfully implement ITSM’s customer satisfaction model, it should eliminate the misunderstandings of IT service objectives first, while the adoption of knowledge supporting structure of ITSM can play a multiplier effect.
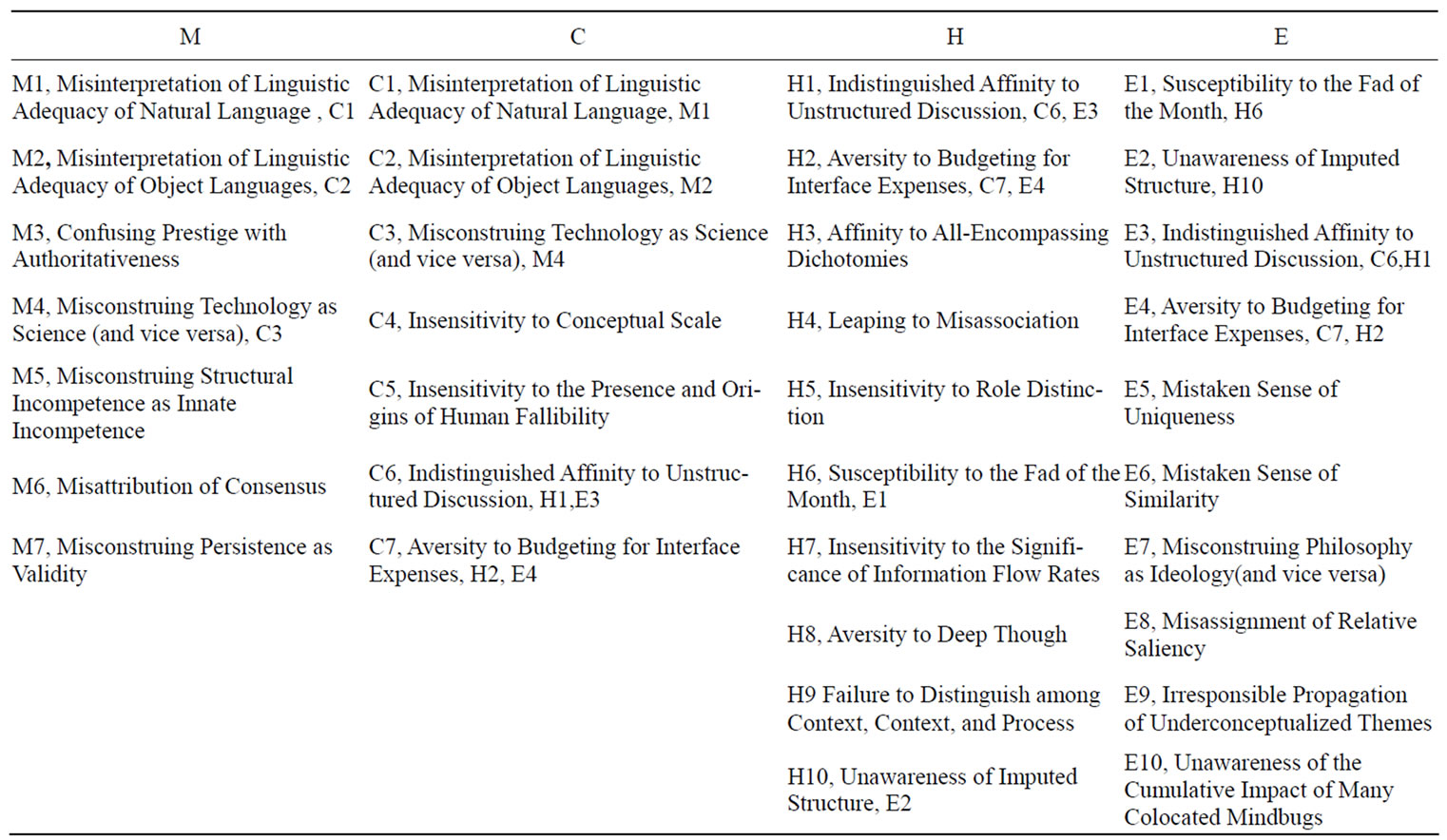
Table 1. The identification and classification of mindbugs.
Reference [6] identifies the risk factors which result in the failure of ITSM project implementation, and they are sorted in accordance with the importance degree of the risk. The most critical twenty risk factors are also identified in the following: (R1) The seniors of the enterprise are impolitic when making decision. (R2) No enough and effective communication among all the related people. (R3) The core members or project managers of external IT company have not relevant experience. (R4) The executive managers don’t attach importance to the project. (R5) Design process without basing on business demand. (R6) Vague responsibility definition is among staffs of two sides. (R7) Process mission and objectives are not clear. (R8) The business demand analysis is not sufficient. (R9) It doesn’t reach a consensus on business process between external IT company and the enterprise. (R10) Customer demands change frequently. (R11) Objectives of the project are not clear. (R12) The mobility of employees in the enterprise is serious. (R13) The company and the client are not consentaneous on the service level. (R14) The business strategy of enterprise is not clear. (R15) The resources which the project needs are not sufficient. (R16) It will produce the sector separatism phenomenon when the enterprise sector conflicts are coming up. (R17) External IT company staffs have not the excellent execution power. (R18) The order of the process implementation is improper. (R19) IT infrastructure planning and design of the enterprise are unreasonable. (R20) The project scale is too large, which increases the management complexity. Then, interpretive structural model (ISM) is applied to determine the twenty risk factors’ causal relationship, and ISM of risk factors of the ITSM project implementation is established. Finally, six root risk factors are identified: R11, R2, R4, R14, R12 and R19. How to solve the six root risk factors effectively? It is the key to implementation of IT service management project.
3. Identification of Mindbugs in P. R. China
3.1. Questionnaire Design and Reclaiming Situation
As mindbugs is a psychological term, which means its concept is abstract and its definition is somewhat esoteric, it is very difficult to understand the meaning for lacking enough education, therefore the survey object is narrowed to people in colleges and universities. Since this study is essentially exploratory research, plus the human, financial, material and time constraints, it is acceptable to choose students studying in the South China University of Technology as the respondents. From June 2007 to January 2008, we received a total of 79 questionnaires, of which 58 were valid. 38 undergraduates were surveyed, accounting for 65.5% and the rest was graduates.
3.2. Reliability and Validity Analysis
We use Cronbach’s α coefficient to examine the questionnaire’s internal consistency reliability. It is 0.874, indicating the internal consistency of measurements in this study is very good. All items adopt the mindbugs by Warfield and the content of the items can well reflect the subject of the survey, so this scale meets the requirements of content validity. In order to ensure that the purpose and contents of the questionnaire can be accurately understood by the respondents, we explained the content of some items which are difficult to understand before sending out the questionnaires, so this scale satisfies the requirements of face validity. Responding to the purpose of this study, the questionnaire can obtain people’s attitude towards mindbugs existence, so this scale also basically meets the construct validity.
3.3. Descriptive Statistics
The results of descriptive statistics of the survey data with 7 levels Likert scale is illustrated in Table 2.
From the results, we can see that:
1) The maximum mean is 5.24 and the minimum is 4.41, which means there are few people strongly denying the existence of these 25 mindbugs in our country.
2) All the means exceed 4, which indicates that people can feel these mindbugs in some degree.
3) We have to choose the ones whose population mean is deduced to be more than 5 in order to find out the mindbugs that people are generally aware of,. Next we will analyze the relationship between the root risk factors of ITSM projects’ implementation and these widely accepted these mindbugs.
3.4. One-Sample T-Test
The precondition of T test is that the sample being tested is subject to normal distribution. The use of one-Sample KS process of SPSS software helps us arrive at the conclusion that the sample data of these 25 mindbugs is subject to normal distribution, indicating that the sample data meets the requirements for T tests.
Original hypothesis H0: the population mean = 5; Alternative hypothesis H1: the population mean ≠ 5. Given 95% confidence degree, that is, the significance level α = 0.05. And then SPSS software is used for one-Sample T Test analysis for these data, and the results are illustrated in Table 3.
From the results, it is concluded that:
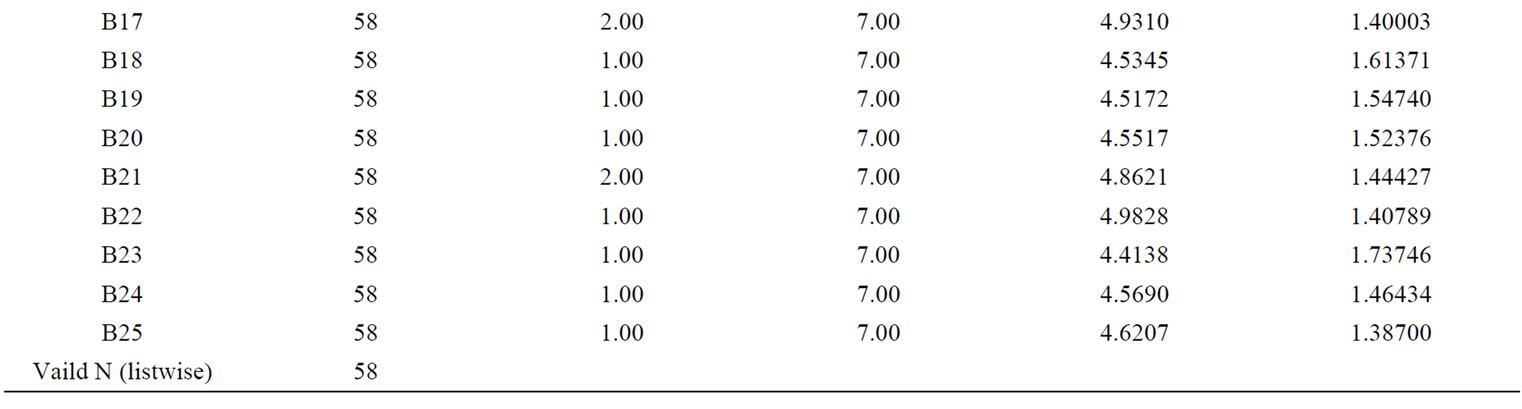
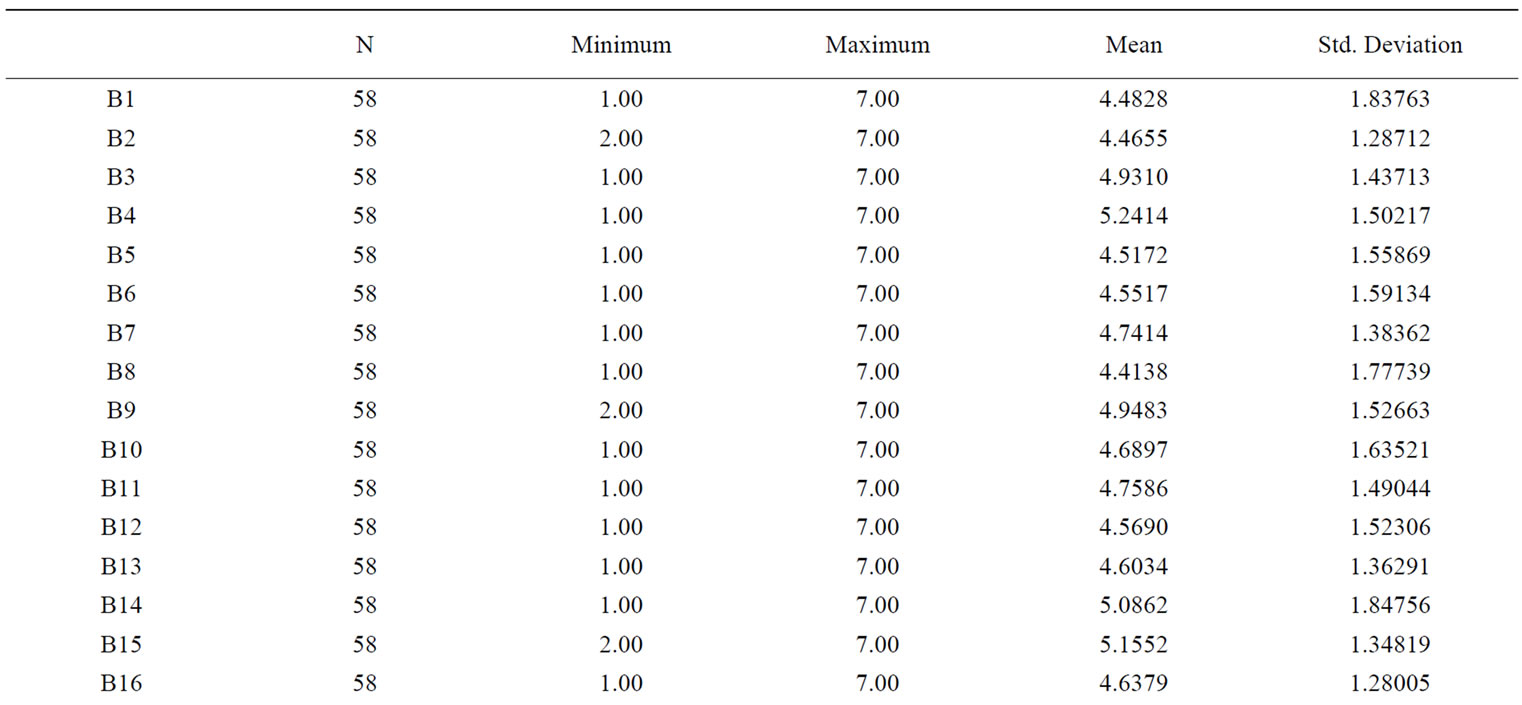
Table 2. The results of descriptive statistics of the mindbugs’ survey data.
1) A total of 14 hypothetical P values are less than 0.05, so the original hypothesis H0 should be rejected. The total mean of these 14 samples is not 5. Meanwhile noting that the confidence interval range of the discrepancy is less than 0, which indicates that the total mean of these samples will be less than 5 (a little support), it is clear that these mindbugs corresponding to these assumptions has not been universally accepted by people. But it is not to deny the existence of these mindbugs, but merely point out that these mindbugs have not been universally supported. These 14 mindbugs are as follows: Affinity to All-Encompassing Dichotomies (B1), Aversity to Budgeting for Interface Expenses (B2), Insensitivity to the Presence and Origins of Human Fallibility (B5), Indistinguished Affinity to Unstructured Discussion (B6), Irresponsible Propagation of Underconceptualized Themes (B8), Leaping to Misassociation (B12), Failure to Distinguish among Context, Content, and Process (B13), Misconstruing philosophy as ideology (B16), Misconstruing technology as science (B18), Misinterpretation of Linguistic Adequacy of Natural Language (B19), Misinterpretation of Linguistic Adequacy of Object Languages (B20), Susceptibility to the Fad of the Month (B23), Unawareness of the Cumulative Impact of Many Colocated mindbugs (B24), Unawareness of Imputed Structure (B25).
2) The other 11 hypothetical P values are over 0.05, so there is not enough evidence to reject the original hypothesis H0 and basically they can be accepted, which means the population means these 11 samples are approximately equal to 5. Therefore, the mindbugs which the 11 hypothesis correspond to are universally accepted. The 11 mindbugs are listed below in the descending order, shown as Table 4.
3.5. Comprehensive Analysis of the Survey
It can be concluded from this survey:
1) People in China don’t strongly oppose to these 25 mindbugs and generally recognize the existence of 11 mindbugs.
2) In terms of the support degree, the top 5 mindbugs would be as follows: confusing prestige with authoritativeness, misconstruing persistence as validity, misattribution of consensus, mistaken sense of uniqueness, insensitivity to role distinction. These 5 mindbugs have the greatest impact on people’s everyday life and are most likely to lead to some erroneous behavior.
3) In Table 4, each of the 11 mindbugs elicited fall into one type in terms of the original classification by Professor Warfield, indicating that the conclusion of this survey is reasonable by excluding those falling into multiple types of mindbugs, so we can analyze the relationship between the mindbugs and the root risk factors clearly.
4) In Table 4, there are 4 mindbugs of misinterpretation, only 1 of clanthink, three of habit and three of error. Further more, it can be calculated from the data in the table that the respective means of these types are as follows: mindbugs of misinterpretation is 5.1034; mindbugs
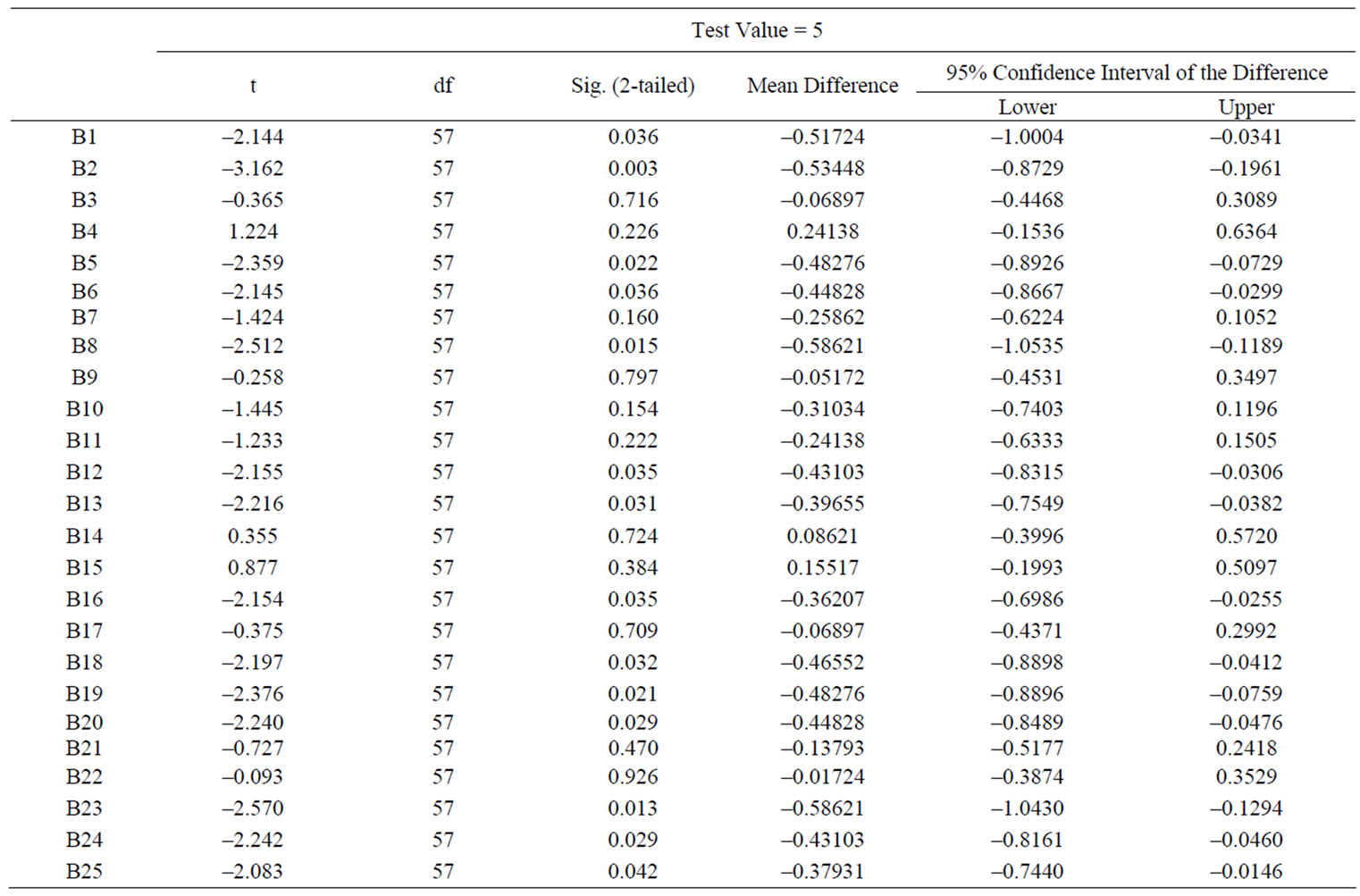
Table 3. One-sample T-test.

Table 4. Universally accepted mindbugs.
of clanthink is 4.7414; mindbugs of habit is 4.8563; mindbugs of error is 4.8678. So, it is concluded that in people’s mind, mindbugs of misinterpretation are the most serious, those of clanthink are the least, while the habit and the error mindbugs are in the same degree.
5) In Table 2, the first three mindbugs all belong to the misinterpretation type, therefore this type is quite serious in China.
4. The Relationship between the Root Risk Factors and the Mindbugs
We investigated 15 IT experts who have been in IT industry for 10 years, and also have some knowledge of psychology with questionnaire. The conclusions on the relationship between the root risk causes and mindbugs are illustrated in Table 5. The cell marked “√” represents that mindbugs in one row will lead to the risk factors in the corresponding column.
It can be concluded from Table 5 that:
1) “Confusing Prestige with Authoritativeness” would relate to two root risk factors, they are no enough and effective communication among all the related people and unreasonable IT infrastructure planning and design of the enterprise. If an enterprise is over-dependent on an external IT company’s past reputation in the IT industry and let the IT company totally control the ITSM project, the enterprise would spend very little effort in the ITSM projects, which obviously would bring about the lack of adequate communication between the both sides.
2) “Misconstruing Persistence as Validity” would relate to the business strategy of enterprise is not clear. If a wrong or vague enterprise business strategy is widely accepted by the staff for a long time, it will be considered as a proper strategy and be implemented.
3) “Misattribution of Consensus” would relate to no enough and effective communication among all the related people. In team communication, if some team members are reluctant to oppose to those ideas which have been endorsed by the whole team, they would avoid to put forward their own ideas and opinions, which would result in a lack of communication among team members. Further more, it will very likely to generate a common wrong idea on which all members of the team seem to achieve a consensus.
4) “Mistaken Sense of Uniqueness” would relate to no enough and effective communication among all the related people. Members in the ITSM project implementation team seem to incline to view themselves as unique, so they are not willing to discuss the project implementation plan with other members, leading to a lack of active communication in the team.
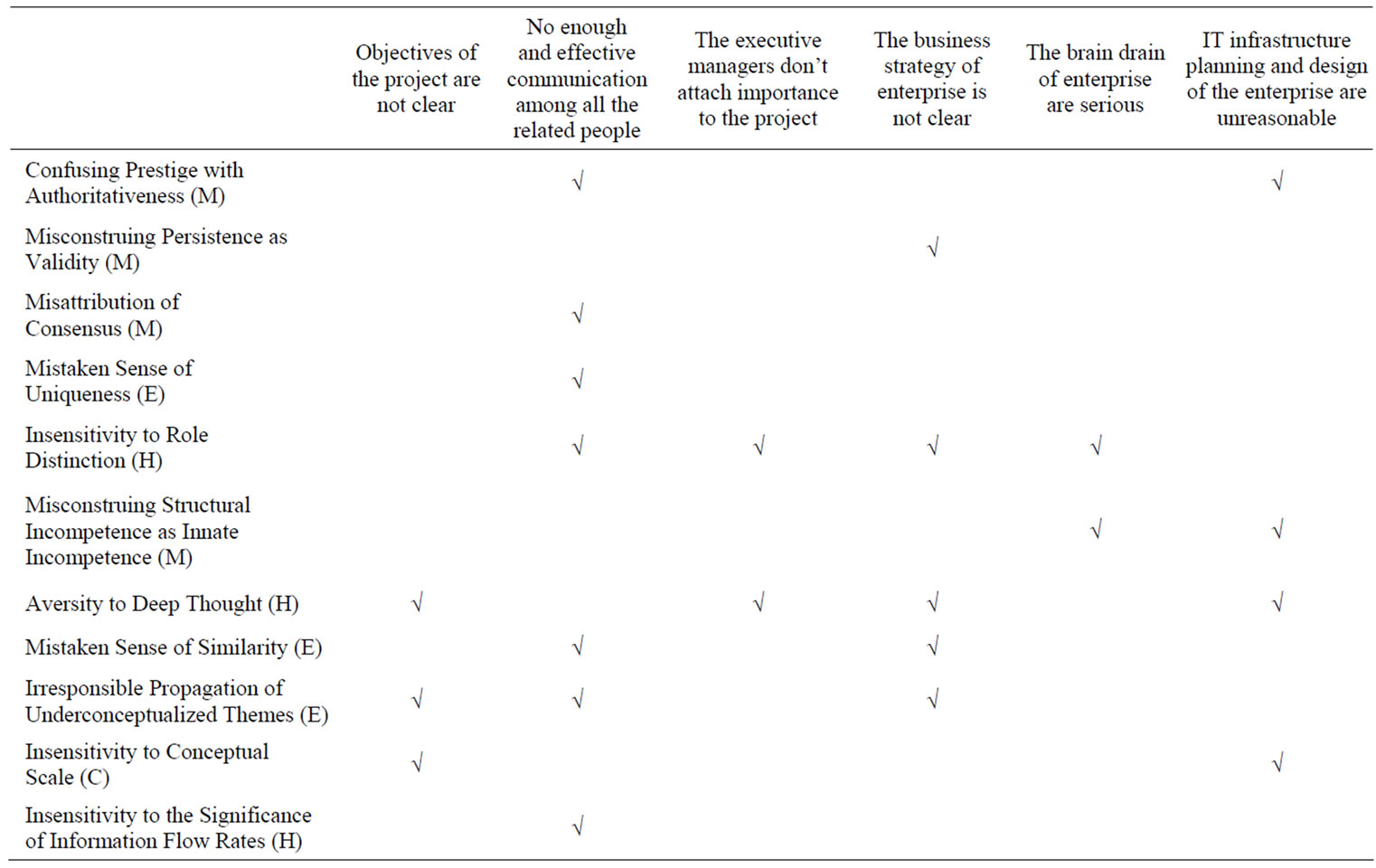
Table 5. The relationship between the root risk factors and the recognized mindbugs in China.
5) “Insensitivity to Role Distinction” would relate to four root risk factors, namely, No enough and effective communication among all the related people, the executive managers don’t attach importance to the project, the mobility of employees in the enterprise is serious, the business strategy of enterprise is not clear. In the ITSM project, if the involved staff are not clear about the responsibilities of each role, a series of problems will occur, including that the information transfer among individual roles is not good, that the seniors are not aware of the importance of their own position and attach little importance to the ITSM project in their work, that nobody will be in charge of the organization business strategy and that staff in the enterprise don’t understand the function of each role and frequently change work posts.
6) “Misconstruing Structural Incompetence as Innate Incompetence” would relate to unreasonable IT infrastructure planning and design of the enterprise and the mobility of employees in the enterprise is serious. Perhaps it is because that the organization structure itself has shortcomings, the staff in certain position within the enterprise can’t bring themselves in play, resulting in more serious enterprise brain drain.
7) “Aversity to Deep Thought” would relate to four root risk factors: unclear project objectives, the business strategy of enterprise is not clear, the executive managers don’t attach importance to the project and unreasonable IT infrastructure planning and design of the enterprise. If members of the ITSM project don’t think deeply about the ITSM, it can affect the entire project in the following aspects: the objectives of the project are not clear; the seniors also won’t recognize the importance of ITSM project; nobody thinks seriously about the organization business strategy; before the implementation of ITSM project, it is seldom considered that whether the existing IT infrastructure planning can or can not satisfy the requirements of ITSM project.
8) “Mistaken Sense of Similarity” would relate to the business strategy of enterprise is not clear and no enough and effective communication among all the related people. If the ITSM project team members treat the ITSM projects as other IT projects, such as the ERP project, they may discreetly copy other IT projects’ solutions to the ITSM projects without discussing with other team members. It is possible to enterprises to follow suit of other enterprises when developing organization’s business strategy. However in reality each enterprise is different, so it is wrong to not have a clear understanding about the organization business strategy.
9) “Irresponsible Propagation of Underconceptualized Themes” would relate to the following three root risk factors: unclear project objectives, the business strategy of enterprise is not clear, no enough and effective communication among all the related people. If a prestigious expert within the company disseminate some misconceptions, such as unclear project objectives and vague organization business strategy, then employees are very likely to easily accept these misconceptions. If ITSM project team members take in a certain team member and believe he must be right, it will reduce the exchange with other team members.
10) “Insensitivity to Conceptual Scale” would relate to unclear project objectives and unreasonable IT infrastructure planning and design of the enterprise. As the size of the project is too large, the project sponsors and managers can not grasp the scope of the project and thus can not identify clear project objectives.
11) “Insensitivity to the Significance of Information Flow Rates” would relate to No enough and effective communication among all the related people. Too fast or too slow information transmission will affect the effects of communication.
The relationship can also be illustrated in Figure 1. It can be concluded in the following:
1) In ITSM projects’ implementation, mindbugs of habit is the most serious one which would lead to six root risk factors. Therefore, ITSM projects’ implementation team members need to remove the old and create the new, eliminate the obsolete thinking in mind and have the courage to accept new concepts of ITSM.
2) Mindbugs of misinterpretation is the second most
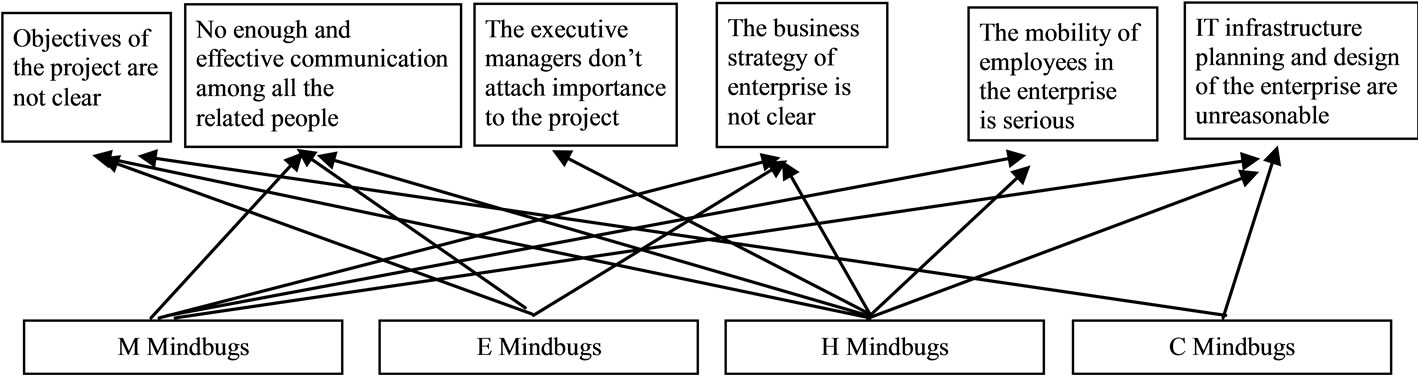
Figure 1. The relationship between the root risk factors and the mindbugs.
serious, which would lead to four root risk factors. Therefore, ITSM implementation team members should reach a consensus on some concepts. Through arranging ITSM training for the relevant personnel, the misconceptions of the team members can be clarified.
3) Mindbugs of error and mindbugs of clanthink can respectively lead to three and two root risk factors. Thus, ITSM project manager need to pay close attention to it to prevent the team members from doing damage to the project due to momentary errors, and to promote team members boldly put forward their own personal beneficial opinion basing on cooperation within the team.
5. Risk Mitigation Recommendations
According to the relationship between the root risk factors and the mindbugs, the risk mitigation recommendations can be established.
1) In order to avoid unclear project objectives, the recommendations are in the following: before the implementation of ITSM projects, make sure to have deep thoughts about all aspects of the project; right conceptions about the enterprise business and ITSM should be carried through to the employees; the scope of the project should be controlled.
2) In order to avoid no enough and effective communication among all the related people, the recommendations are as follows: do not just leave the external IT company to deal with ITSM project, the company should keep informed of the project conditions in time; in the ITSM project team discussion, team members should be encouraged to put forward their own point of view; cooperation should be promoted within the team while reducing the individualism; clarify the responsibilities of each role in the project, and facilitate the correct transmission of information; the differences of ITSM projects and other IT projects must be clearly aware; do not heavily rely on an individual point of view, share opinions with other team members; control the speed of information transmission so that recipients of information can efficiently access them.
3) In order to avoid the executive managers don’t attach importance to the project, the recommendations are as follows: clarify the responsibilities of the senior manager role; senior manager should understand the differences of ITSM projects and other IT projects in a strategic view.
4) In order to avoid the business strategy of enterprise is not clear, the recommendations are as follows: due to the changes in the economic environment, the corporate long-standing business strategy may no longer be suitable for enterprise development and should be reinvented; senior leaders should be responsible for business strategy; senior leaders should have in-depth and long-term thinking about the organization’s business strategy planning; do not just follow suit other company’s business strategy, in stead, companies should establish and maintain their unique competitive advantage; corporate staff should not indiscreetly presume the organization’s business strategy passed on by a prestigious person, but rather to take the ones established by the senior manager as a standard.
5) In order to avoid the serious brain drain in the enterprise, the recommendations are as follows: clarify responsibilities of each post, so that employees can perform their duties in the posts and make continuous progress; if the existing organizational structure is not suitable for the development of employees, then it should be re-adjusted.
6) In order to avoid the unreasonable IT infrastructure planning and design of the enterprise, the recommendations are as follows: the enterprise should not stubbornly believe the existing IT infrastructure is reasonable; the existing IT infrastructure planning should be re-adjusted to meet the company’s future business development needs; a more rational IT infrastructure planning should be developed through in-depth analysis; balance the economy and efficiency trade-off, so that the size of the IT infrastructure could be controlled in a reasonable range.
7) Customer satisfaction model of ITSM, knowledge supporting structure of ITSM of [5] are helpful to risk mitigation and avoidance.
6. Conclusions
The eleven kinds of common mindbugs are figured out among the twenty five kinds of mindbugs with questionnaire. The relationship between the root risk factors of implementation of the ITSM project and these mindbugs are analyzed Of course, there are many limits in our study, 1) 79 questionnaires were too few and were mainly in our students in SCUT, in our understanding, But even more data were collected. The mindbugs were identitied to be challengeable. New approaches should be considered. 2) We just run one-sample T-test without comprehensive analysis of survey. Some necessary hypothesizes should be also pre-presented. 3) Due to the length of article, we couldn’t discuss in greater depth and more specific perspective just as in [5]. 4) Killer assumptions by Prof. Warfield will be considered in another paper in some detail (to be apppeared). Although there is a long way to go, it is sure that the research will helpful for both ITSM theories construction and ITSM practices’ improvement.
7. Acknowledgements
Thanks for helpful discussion with Mr. Cai hua, Mr. Chen Ji, Mr. Zhuo Zhixing and my student Wang Yunfeng hard working.
8. References
[1] J. N. Warfield, “Mentomology: The Identification and Classification of Mindbugs,” September 1995. http://mars.gmu.edu:8080/dspace/bitstream/1920/3199/1/Warfield%20_20_20_A1b.pdf,1995
[2] J. P. Wan, “Research on Software Product Support Structure,” Journal of Software Engineering and Applications, Vol. 2, No. 3, 2009, pp. 174-194. doi:10.4236/jsea.2009.23025
[3] J. van Bon, M. Picper and A. der Veen, “Foundations of IT Service Managementbased on ITIL,” Van Haren Publishing, Zaltbommel, 2005.
[4] W. G. Tan and A. Cater-Stel, “Implementing IT Service Management: A Case Study Focusing on Critical Success Factors,” Journal of Computer Information Systems, Vol. 50, No. 2, 2009, pp. 1-12.
[5] J. P. Wan, H. Zhang and D. Wan, “Evaluation on Information Technology Service Management Process with AHP,” Technology and Investment, Vol. 2, No. 1, 2011, pp. 38-46. doi:10.4236/ti.2011.21005
[6] J. P. Wan, S. Q. Zhu and Y. F. Wang, “Empirical Analysis on Risk Factors of IT Service Management Project Implementation,” IEEE International Conference on Wireless Communications, Networking and Mobile Computing, Dalian, 14-16 October 2008, pp. 1-4.
NOTES
*This research was supported by Key Project of Guangdong Province Education Office under Grant No. 06JDXM63002

